Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk Management (C-SCRM):
- Cybersecurity & Data Protection Program (CDPP) - NIST CSF, ISO 27001/2 or NIST 800-53 R5 Moderate
- Cybersecurity Standardized Operating Procedures (CSOP) - NIST CSF, ISO 27001/2 or NIST 800-53 R5 Moderate
- NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)
- Risk Management Program (RMP)
- Cybersecurity Risk Assessment Template (CRA)
- Vulnerability & Patch Management Program (VPMP)
- Integrated Incident Response Program (IIRP)
- Continuity of Operations Plan (COOP)
- Secure Baseline Configurations (SBC)
- Information Assurance Program (IAP)
- Secure Engineering & Data Privacy (SEDP)
- Cybersecurity Business Plan (CBP)
- Data Protection Program (DPP)
NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
ComplianceForge developed an editable template for a C-SCRM Strategy and Implementation Plan (SIP). This is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the ground running" with C-SCRM operations that are aligned with NIST SP 800-161 Rev 1, which is the current "gold standard" for authoritative C-SCRM guidance.
|
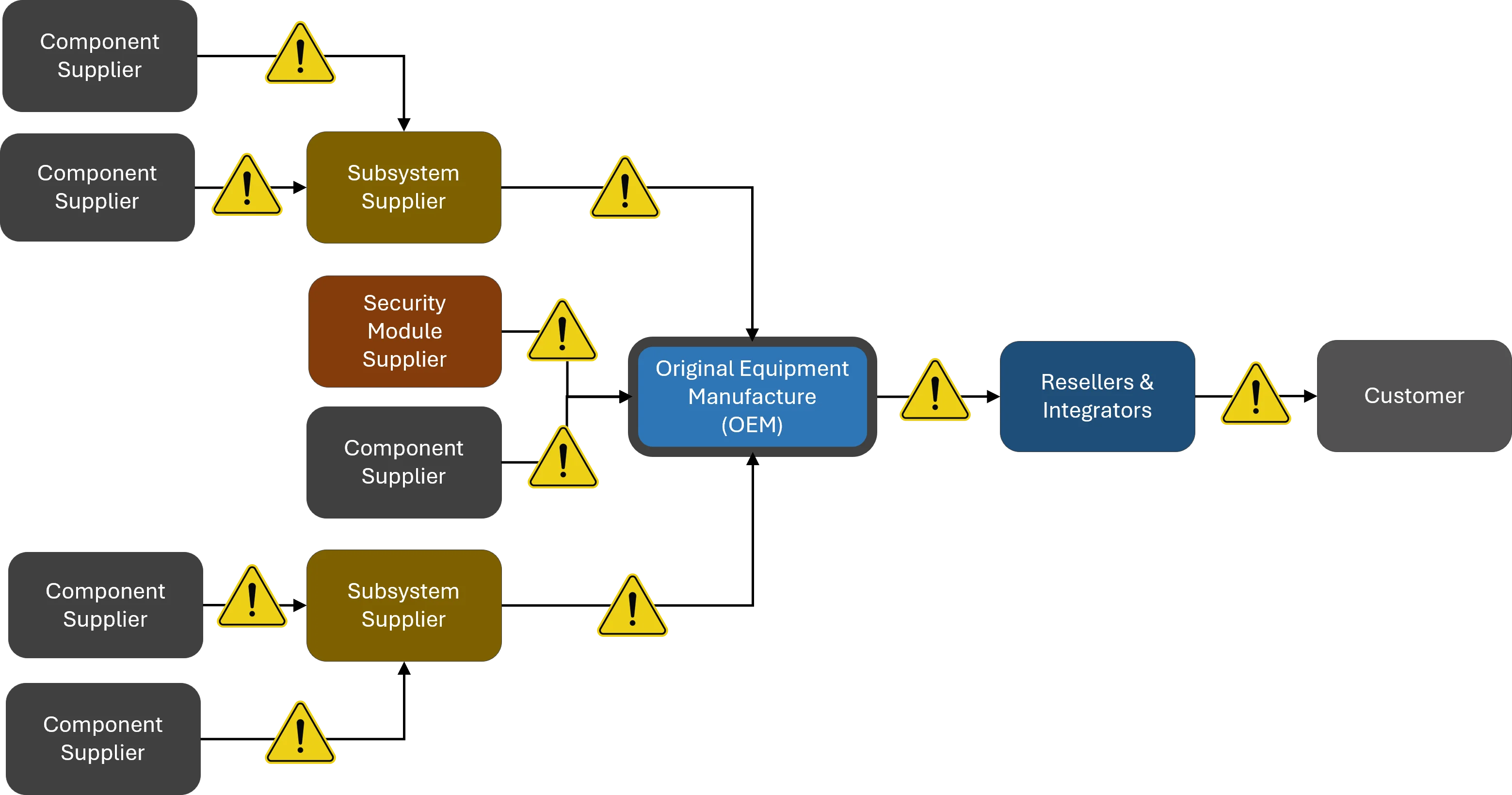
The reality is organizations depend on a global supply chain to provide a variety of products and services that enable the achievement of its strategic and operational objectives. Given the global scope of identifying cybersecurity and data protection risks, threats and vulnerabilities throughout the supply chain are complicated due to the information asymmetry that exists between acquiring enterprises and their suppliers and service providers:
|
 |
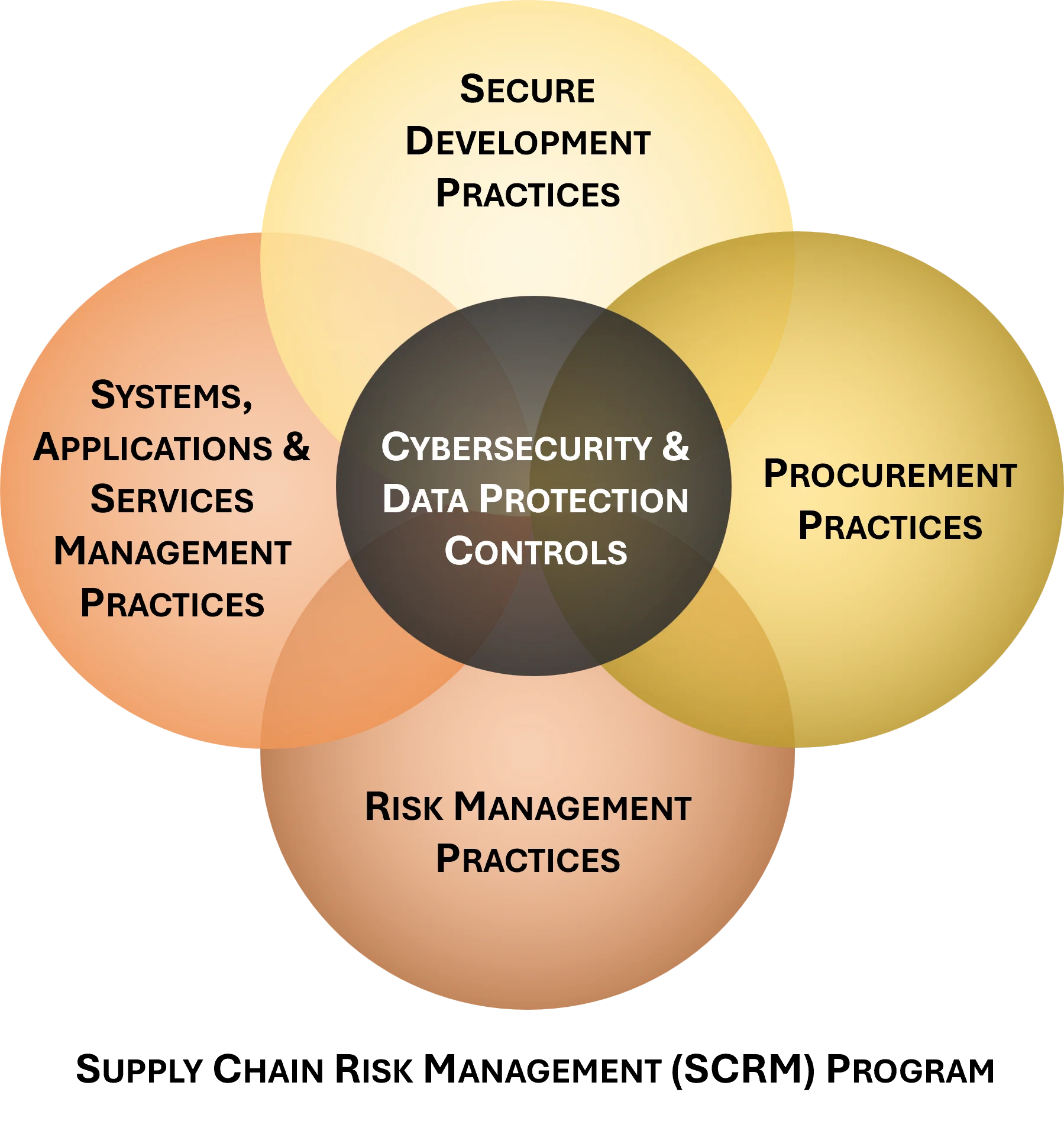
Reducing Risk Is Central To Supply Chain Risk Management
|
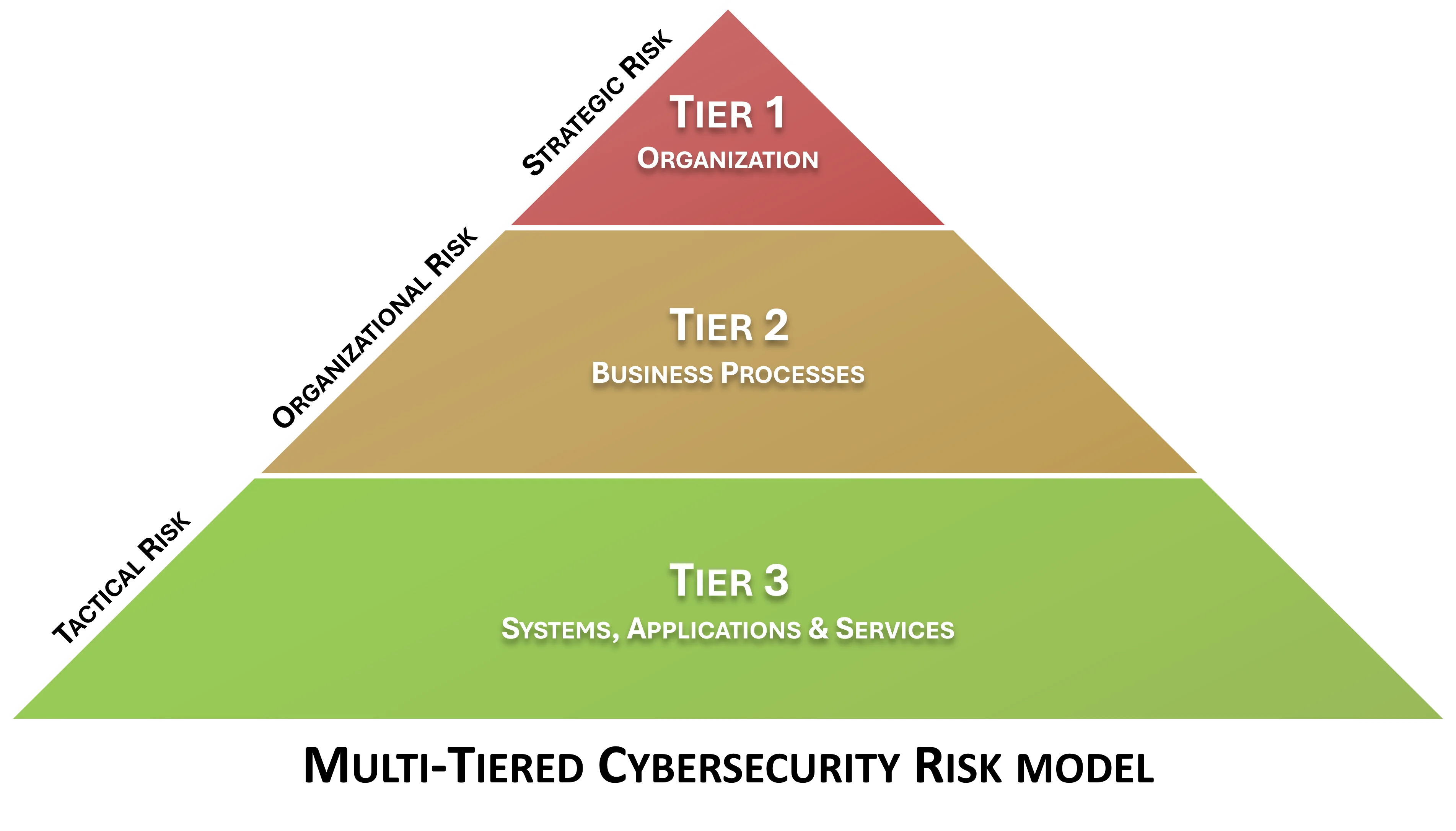
Having a Supply Chain Risk Management (C-SCRM SIP) is focused on minimizing risk to your company, your partners and your customers. There is traditionally low level-risk (tactical) that is focused on weaknesses pertaining to routine systems and data. There is mid-level risk (operational) that is focused on weaknesses pertaining to business process. There is also high-level (strategic) risk that impacts at an organizational level. Having a secure vendor relationship can address risk at all three of these levels. The C-SCRM SIP product is designed to implement a C-SCRM Program, as well as deliver an efficient and cost-effective method to develop a C-SCRM strategy and implement actionable steps to operationalize the C-SCRM strategy. |
 |
|
|
Suppliers, Integrators and Service Providers (SISP) are in scope for C-SCRM operations, where the term SISP includes Original Equipment Manufacturers (OEMs), vendors, contractors, consultants and other entities that make up the supply chain. This scope of operations for the C-SCRM SIP includes all entities that:
Product highlights of the C-SCRM SIP include:
|
NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
This bundle is designed for organizations that need to comply with the European Union General Data Protection Regulation (EU GDPR) and the pending California Consumer Privacy Act (CCPA). This is beyond just cybersecurity policies and standards and a standard SCRM plan. This is addresses the unique compliance needs for privacy and cybersecurity to manage risk in a coordinated effort. The end result is a comprehensive, customizable, easily implemented set of documentation that your company needs to establish a cybersecurity and privacy program. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just contact us with your needs and we will generate a quote for you.
Cost Savings Estimate - C-SCRM Bundle #1 (Cybersecurity & Data Protection Program (CDPP) version)
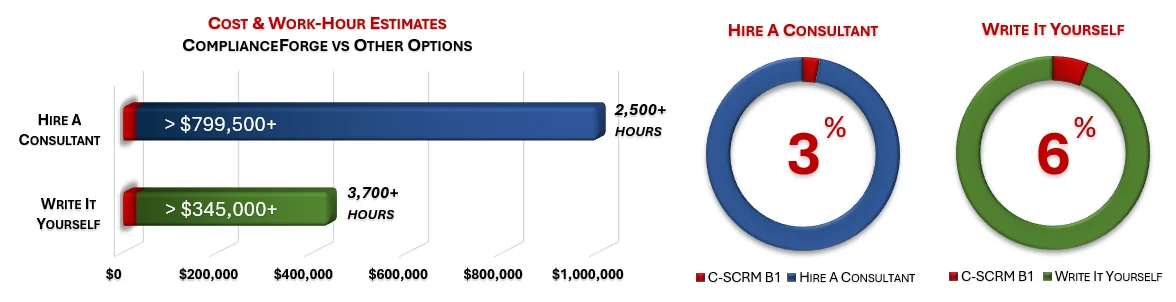
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 3,700 internal staff work hours, which equates to a cost of approximately $369,000 in staff-related expenses. This is about 30-40 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 2,500 contractor work hours, which equates to a cost of approximately $823,500. This is about 18-30 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 6% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
Products Included in C-SCRM Bundle #1 (CDPP version)
The Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle 1 uses the Cybersecurity & Data Protection Program (CDPP) and C-SCRM Bundle #2 uses the Digital Security Program (DSP). The DSP is targeted for larger, enterprise environments, but more differences between the CDPP and DSP can be read about here. The CDPP comes in either NIST CSF, ISO 27001/2 or NIST 800-53 moderate.
|
|
Cybersecurity & Data Protection Program (CDPP) (NIST CSF, ISO 27001 & 27002 or NIST SP 800-53 Moderate version) Framework-specific cybersecurity policies & standards in an editable Microsoft Word format.
|
 |
NIST SP 800-161 Rev 1-Based Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP) The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable C-SCRM implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
 |
Cybersecurity Standardized Operating Procedures Template (CSOP) - CDPP version
|
 |
Integrated Incident Response Program (IIRP) The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
|
 |
Risk Management Program (RMP) The RMP addresses the “how?” questions for how your company manages risk.
|
 |
Cybersecurity Risk Assessment (CRA) Template The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
|
 |
Vulnerability & Patch Management Program (VPMP) The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
|
 |
Secure Engineering & Data Privacy (SEDP) The SEDP addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
|
 |
Continuity of Operations Program (COOP) The COOP addresses the “how?” questions for how your company plans to respond to disasters to maintain business continuity.
|
 |
Secure Baseline Configurations (SBC) The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
|
 |
Information Assurance Program (IAP) The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
|
 |
Cybersecurity Business Plan (CBP) The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
|
 |
Data Protection Program (DPP)
|
Please note that if you want a customized bundle, we are happy to create one for you. Just contact us with your needs and we will generate a quote for you.