NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CDPP is to help answer common questions we receive.
What Is The Cybersecurity & Data Protection Program (CDPP)?
Does your organization need NIST 800-53 High policies & standards documentation? The NIST SP 800-53 rev5 Low, Moderate & High Baseline-based Cybersecurity & Data Protection Program (CDPP-LMH) is our latest set of NIST-based cybersecurity policies and standards that is based on NIST SP 800-53 Rev5. This is a comprehensive, editable, easily implemented document that contains the policies, control objectives, standards and guidelines that your company needs to establish a world-class cybersecurity program. Being Microsoft Word documents, you have the ability to make edits, as needed. For companies that need to be compliant with NIST SP 800-171 and CMMC, the CDPP-LMH provides coverage for NIST SP 800-53 rev5 Low, Moderate & High baseline controls so you could implement the CDPP-LMH for your NIST SP 800-171 and CMMC compliance needs (CMMC 2.0 Levels 1-3).

When you look at NIST SP 800-53 as it compares to other cybersecurity frameworks, it is on the more robust side of the spectrum, based on the topics it covers. NIST SP 800-53 rev5 consists of 20 different families of cybersecurity and privacy controls. The NIST SP 800-53 rev5 Low, Moderate & High NIST SP 800-53 CDPP has a security policy for each of these 20 families of controls and standards to address the LOW, MODERATE & HIGH baseline controls of this framework.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The CDPP contains NIST SP 800-53 based cybersecurity policies & standards in an editable Microsoft Word format:
- Each of the NIST SP 800-53 rev5 families has a policy associated with it, so there is a total of 26 policies.
- Under each of the policies are standards that support the NIST SP 800-53 rev5 Low, Moderate & High baselines.
- The CDPP covers the Low, Moderate & High baseline control sets from NIST SP 800-53 rev 4 and FedRAMP.
- The CDPP addresses the “why?” and “what?” questions in an audit, since policies and standards form the foundation for your cybersecurity program.
- The CDPP provides the underlying cybersecurity standards that must be in place, as stipulated by statutory, regulatory and contractual requirements.
- Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the CDPP does this from a cybersecurity perspective.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problem Does The CDPP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The NIST-based CDPP is an efficient method to obtain comprehensive NIST SP 800-53 based security policies and standards for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security policies and standards. Requirements range from PCI DSS to HIPAA to NIST SP 800-171. The CDPP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements. The CDPP maps to several leading compliance frameworks so you can clearly see what is required!
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The CDPP's standards provides mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies and standards. The CDPP provides this evidence!
How Does the CDPP Solve It
- Clear Documentation - The CDPP provides comprehensive documentation to prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The CDPP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The NIST-based CDPP is written to align your organization with NIST SP 800-53 rev5!
ComplianceForge provides businesses with exactly what they need to protect themselves - professionally written policies, procedures, standards and guidelines at a very affordable cost. Similar documentation standards can be found in Fortune 500 company that have dedicated IT Security staff. All information security policies and standards are backed up by documented leading-industry practices. You can see example of the FedRAMP High policies and standards below, as well as a product walkthrough video.
Product Example - NIST SP 800-53 R5 Low, Moderate & High Baseline Cybersecurity Policies & Standards (CDPP-LMH)
At ComplianceForge, we provide "NIST 800-53 High policy templates". This version of the Cybersecurity & Data Protection Program (CDPP) is based on the NIST SP 800-53 rev5 framework. It contains cybersecurity policies and standards that align with NIST SP 800-53 (including NIST SP 800-171 requirements). You get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs.
Some of our customers ask if we have any "NIST cybersecurity policy examples", and the short answer to this question is yes, we do. However, we first have to clarify which framework they are trying to comply with, as each framework is different. To understand the differences between the NIST SP 800-53, ISO 27002 and NIST CSF versions of the CDPP, please visit here for more details.
View Product Examples
If you would like to view examples of ComplianceForge's NIST 800-53 Low, Moderate & High Baseline Cybersecurity & Data Protection Program (CDPP), please click any of the images below:
What Is Included With The CDPP (NIST 800-53 Low, Moderate & High Baseline)?
Creating A Cybersecurity Program Based To Align With NIST SP 800-53 rev High Baseline Controls
At its core, this version of the NIST SP 800-53 R5 Cybersecurity & Data Protection Program (CDPP-LMH) is designed to align with "high baseline" controls from NIST SP 800-53 R5. Since our clients tend to have additional needs in this space, the NIST SP 800-53 R5 CDPP-LMH has complete coverage for these core frameworks:
- NIST SP 800-53 R5 (low, moderate, high & privacy baselines - as defined in NIST SP 800-53B)
- Federal Risk and Authorization Management Program (FedRAMP R5) (low, moderate, high & Li-SaaS baselines)
- Federal Acquisition Regulation (FAR) 52.204-21 (cybersecurity requirements)
- DoD Cybersecurity Maturity Model Certification (CMMC) v2.0 (Levels 1, 2 & 3)
- NIST SP 800-171 R2 (CUI & NFO controls)
- NIST SP 800-172 - (controls to protect against Advanced Persistent Threats (APTs))
The following leading practices are mapped to the corresponding NIST SP 800-53 rev5 CDPP-LMH standards. This mapping is in the corresponding Excel spreadsheet that is included as part of your purchase:
- AICPA Trust Services Criteria (TSC) (commonly referred to as SOC 2 controls)
- CERT Resilience Management Model (CERT RMM) v1.2
- Center for Internet Security Critical Security Controls (CIS CSC) v7.1 (commonly referred to as the SANS Top 20)
- Fair & Accurate Credit Transactions Act (FACTA)
- Generally Accepted Privacy Principles (GAPP)
- Gramm-Leach-Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
- ISO 27002:2013
- IRS 1075
- MA 201 CMR 17.00
- North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP)
- National Industrial Security Program Operating Manual (NISPOM)
- NIST Cybersecurity Framework (NIST CSF) v1.1
- NY 23 NYCRR 500
- Oregon Consumer Identity Theft Protection Act (OR 646A)
- Payment Card Industry Data Security Standard (PCI DSS) v3.2.1
- Secure Controls Framework (SCF)
- UK Cyber Essentials
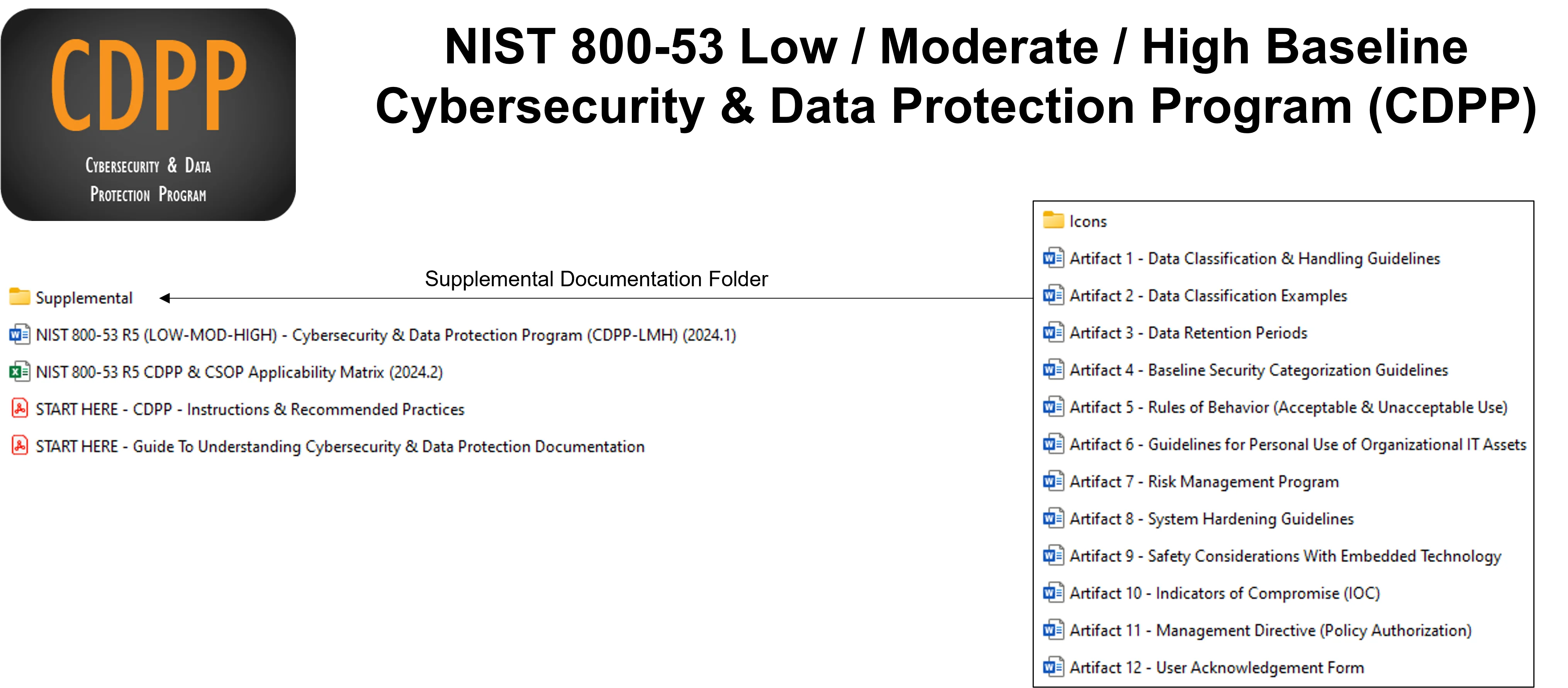
In addition to NIST-based Cybersecurity Policies & Standards, the NIST SP 800-53 R5 CDPP-LMH Comes With These Supplemental Cybersecurity Resources
As an extra bonus, we include the following supplemental documentation at no additional cost:
- Excel spreadsheet that maps the standards to multiple statutory, regulatory and contractual frameworks
- Customizable cybersecurity awareness training presentation in Microsoft PowerPoint for information security awareness training ($260 value)
- Cybersecurity awareness training form
- Customizable Incident Response Plan (IRP) template
- Business Impact Assessment (BIA) template
- Business Continuity Plan (BCP) & Disaster Recovery (DR) template
- Service provider indemnification & Non-Disclosure Agreement (NDA) template
- User acknowledgement form
- Change management request form
- Risk assessment methodology template
- Appointment orders for an Information Security Officer (ISO)
This documentation saves hundreds of hours by not having to make it on your own!
NIST SP 800-53 R5 Written IT Security Documentation - Robust Approach To Cybersecurity
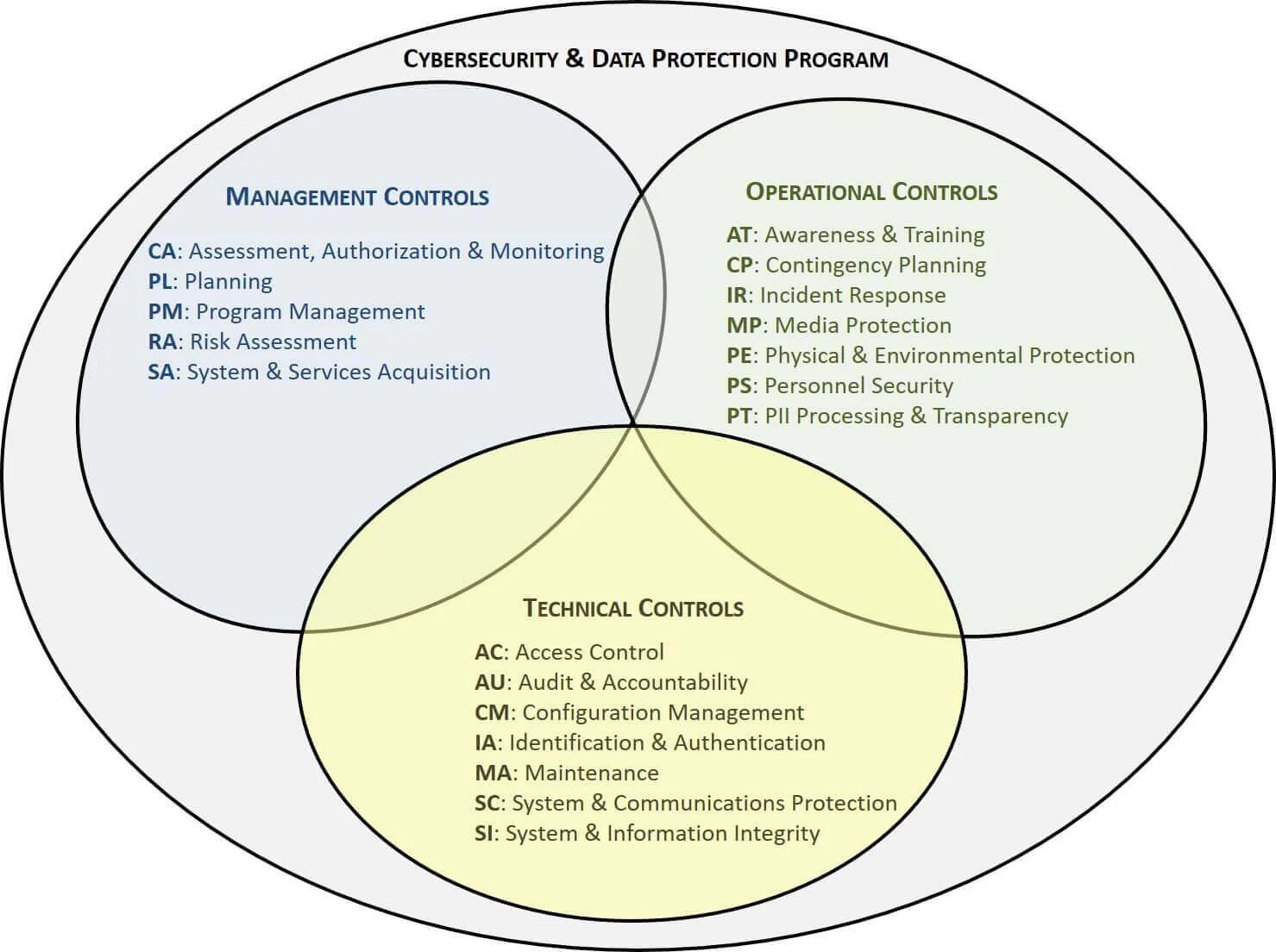
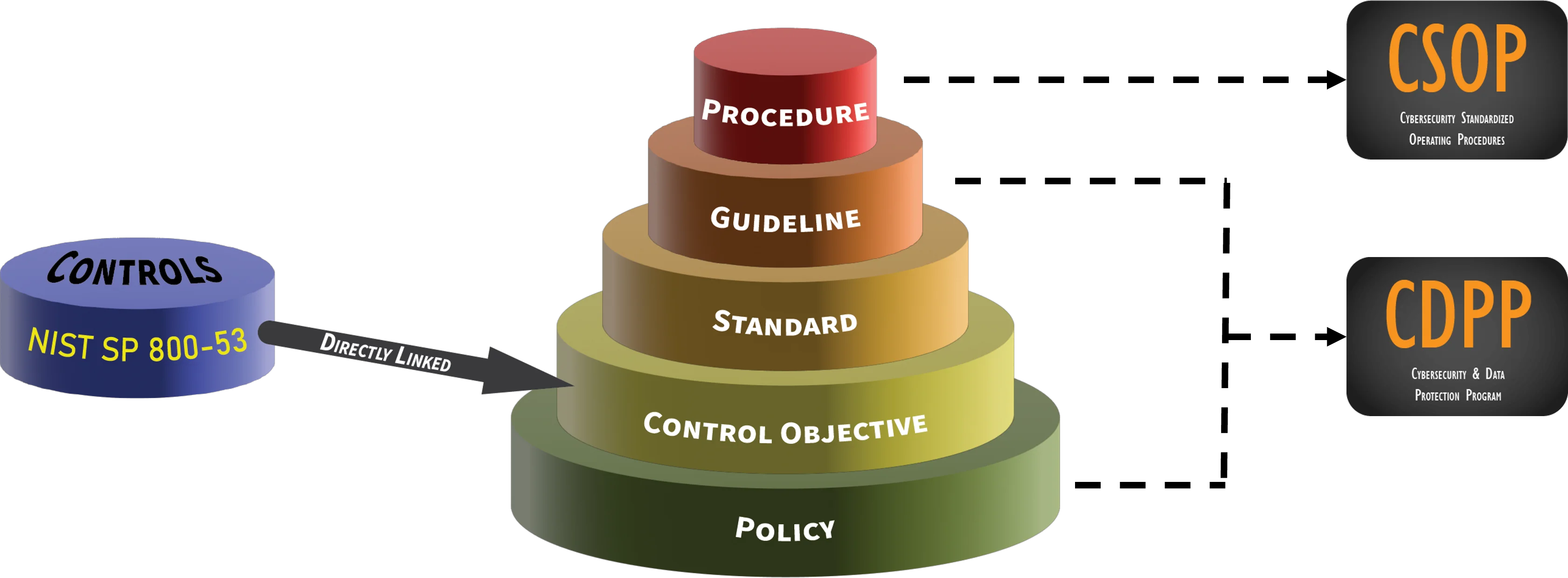
To understand the NIST SP 800-53 R5 CDPP-LMH, we took the controls from NIST SP 800-53 R5 and transformed those controls into a viable set of policies and standards that are directly tied to NIST SP 800-53 R5. The twenty (20) families of controls found in NIST SP 800-53 R5 equate to the twenty (20) policies in the Cybersecurity & Data Protection Program (CDPP) and this creates a comprehensive cybersecurity framework, since the standards in the CDPP-LMH map directly to the low, moderate and high controls in NIST SP 800-53 R5. To help organize the CDPP to make it easier for readers, the CDPP-LMH organizes the families of NIST SP 800-53 R5 according to FIPS 199 Management, Operational & Technical categories:
- Access Control (AC) policy
- Assessment, Authorization & Monitoring (CA) policy
- Audit & Accountability (AU) policy
- Awareness & Training (AT) policy
- Configuration Management (CM) policy
- Contingency Planning (CP) policy
- Identification & Authentication (IA) policy
- Incident Response (IR) policy
- Maintenance (MA) policy
- Media Protection (MP) policy
- Personally Identifiable Information (PII) Processing & Transparency (PT) policy
- Personnel Security (PS) policy
- Physical & Environmental Protection (PE) policy
- Planning (PL) policy
- Program Management (PM) policy
- Risk Assessment (RA) policy
- Supply Chain Risk Management (SR) policy
- System & Communications Protection (SC) policy
- System & Information Integrity (SI) policy
- System & Services Acquisition (SA) policy
The Most Comprehensive NIST SP 800-53 R5-Based IT Security Documentation Available Online
Cost Savings Estimate - NIST SP 800-53 rev5 Low, Moderate & High Baseline Cybersecurity & Data Protection Program (CDPP-LMH)
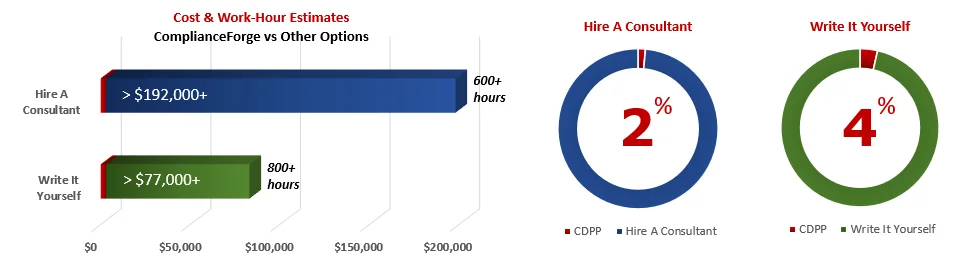
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CDPP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 800 work hours, which equates to a cost of approximately $80,000 in staff-related expenses. This is about 9-15 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 600 work hours, which equates to a cost of approximately $195,000. This is about 4-8 months of development time for a contractor to provide you with the deliverable.
- The CDPP is approximately 2% of the cost for a consultant or 4% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CDPP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CDPP! |
|
|
Comprehensive NIST SP 800-53 rev 5 Low, Moderate & High Baseline-Based Documentation
|
|
The CDPP-LMH can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer. This NIST SP 800-53 rev5 Low, Moderate & High baseline-based CDPP is a comprehensive, customizable, easily-implemented Microsoft Word document that contains the NIST SP 800-53 rev5 Low, Moderate & High baseline-based policies, control objectives, standards and guidelines that your company needs to establish a robust cybersecurity program. Being a Microsoft Word document, you have the ability to make edits to suit your company's specific needs. NIST SP 800-53 is the de facto standard for cybersecurity requirements that is issued by the US government. Therefore, government agencies, defense contractors, telecom service providers, health care providers, financial companies or any organizations that contract with the government tend to adopt NIST-based best practices over all other frameworks, based on regulatory requirements. Unlike some of our competition that sell “bronze, silver and gold” levels of documentation, we understand that a standard is a standard for a reason. We take out the guesswork associated with picking an appropriate package level - we focus on providing documentation that offers a straightforward solution to provide the appropriate coverage you need. This focus on providing the best solution for our clients makes us proud that we are providing the best set of IT security policies and standards available. Saving a few dollars on a cheap solution can easily leave you with a false sense of security and gaping holes in your documentation that can leave you liable. |
|
FAR vs DFARS (NIST SP 800-171) Implications
NIST SP 800-171 isn’t just for Department of Defense (DoD) contractors. Representatives from the National Institute of Standards and Technology (NIST) and DoD officials have recently been putting this information out in webinars and other training seminars on NIST SP 800-171. Many of our clients who need to address DFARS 252.204-7012 also have to address FAR 52.204-21. One common question we receive from clients pertains to aligning with the correct security framework to ensure they have the proper coverage for compliance. This generally revolves around aligning with ISO 27001/27002, the NIST Cybersecurity Framework or NIST SP 800-53, since those are the most common security frameworks.
The bottom line is that utilizing the NIST Cybersecurity Framework or ISO 27001/27002 as a security framework does not directly meet the requirements of NIST SP 800-171. In fact, NIST SP 800-171 (Appendix D) maps out how the CUI security requirements of NIST SP 800-171 relate to NIST SP 800-53 and ISO 27001/27002 security controls. This includes callouts where the ISO 27001/27002 framework does not fully satisfy the requirements of NIST SP 800-171. Therefore, policies and standards based on NIST SP 800-53 are what is needed to comply with NIST SP 800-171.
This means that only the NIST SP 800-53 framework is going to meet FAR requirements of NIST 800171 - ISO 27002 and the NIST Cybersecurity Framework are going to be insufficient in coverage.

This Is How NIST SP 800-53 Cybersecurity Documentation Is Meant To Be Structured!
The CDPP can be reffered to as a written information security program, a "WISP". ComplianceForge provides businesses with exactly what they need to protect themselves - professionally written policies, procedures, standards and guidelines at a very affordable cost. Similar documentation standards can be found in Fortune 500 company that have dedicated IT Security staff. All information security policies and standards are backed up by documented best practices.
Which Product Is Right For You?
Our documentation is meant to address your requirements from strategic concepts all the way down to day-to-day deliverables you need to demonstrate compliance with common statutory, regulatory and contractual obligations. We offer up to 45% discounts on our documentation bundles, so please be aware that you have benefit from significant savings by bundling the documentation you need. You can see the available bundles here.
We are here to help make comprehensive cybersecurity documentation as easy and as affordable as possible. We serve businesses of all sizes, from the Fortune 500 all the way down to small businesses, since our cybersecurity documentation products are designed to scale for organizations of any size or level of complexity. Our affordable solutions range from cybersecurity policies & standards documentation, to NIST 800-171 compliance checklists, to program-level documentation, such as "turn key" incident response, risk management or vulnerability management program documents. Our focus is on helping you become audit ready!
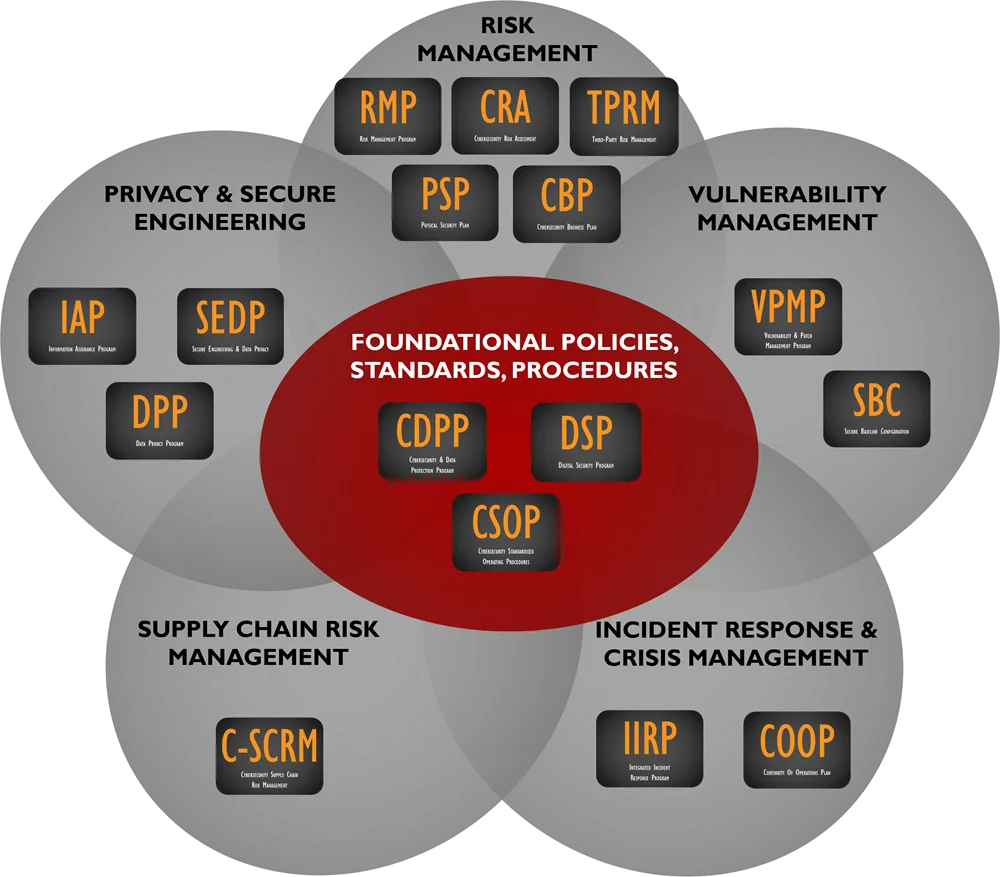
As you see in the graphic below, the CDPP serves as a foundational component of your cybersecurity & data protection program. The CDPP addresses the "What" & "Why" requirements to be secure. Other ComplianceForge documentation can help speed up the effort to operationalize any requirements you have. Those additional documents help address the "How" of running a cybersecurity & data protection program.

Hierarchical Approach - Built To Scale & Evolve With Your Business
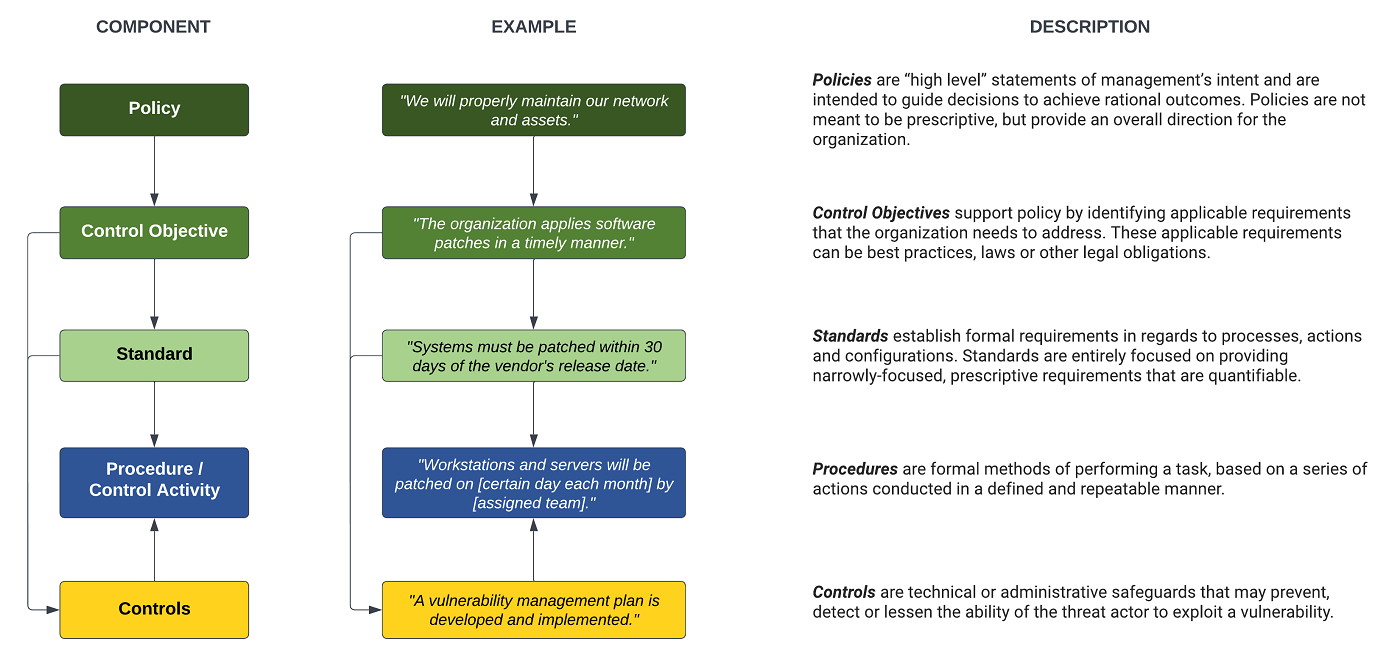
Our experience has proven that when it comes to Information Security policies, a standard is a standard for a reason. With that in mind, our Cybersecurity & Data Protection Program (CDPP) is based on industry-recognized best practices and Information Security standards so that you can meet your legal requirements. Unlike some competitor sites that offer “Bronze, Silver or Gold” packages that may leave you critically exposed, we offer a comprehensive Information Security solution to meet your specific compliance requirements. Why is this? It is simple - in the real world, compliance is penalty-centric. Courts have established a track record of punishing businesses for failing to perform “reasonably expected” steps to meet compliance with known standards.
The Cybersecurity & Data Protection Program (CDPP) follows a hierarchical approach to how the structure is designed so that standards map to control objectives and control objectives map to policies. This allows for the standards to be logically grouped to support the policies.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.