NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the C-SCRM is to help answer common questions we receive.
What Is The Supply Chain Risk Management (C-SCRM SIP)?
The C-SCRM SIP is an editable Microsoft Word document that is intended to operationalize a C-SCRM Program that can enforce security across your supply chain (e.g., service providers, vendors, contractors, etc.).
- The C-SCRM SIP is based on NIST SP 800-161 R1 to develop a C-SCRM Program, that can apply across the entire organization.
- The text for specific flow-down requirements identified in the C-SCRM SIP can be used in contract a addendum.
- Includes a "SCRM Plan" that is based on NIST SP 800-161 R1 and DI-MGMT-82256A formats that specify content for a SCRM Plan (e.g., requirement in NIST SP 800-171 R3, requirement 3.17.1).
- This product addresses the “how?” questions for how your company manages risk with third parties.
- Managing third-party risk through third-party risk management (TPRM) is now a common requirement in statutory, regulatory and contractual obligations.
- The C-SCRM SIP helps provide evidence of due care in how your company informs third parties about their cybersecurity obligations.
ComplianceForge developed an editable C-SCRM template for a C-SCRM strategy and implementation plan. This is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the ground running" with C-SCRM operations that are aligned with NIST SP 800-161 Rev 1, which is the current "gold standard" for authoritative C-SCRM guidance.
The reality is organizations depend on a global supply chain to provide a variety of products and services that enable the achievement of its strategic and operational objectives. Given the global scope of identifying cybersecurity and data protection risks, threats and vulnerabilities throughout the supply chain are complicated due to the information asymmetry that exists between acquiring enterprises and their suppliers and service providers:
- Acquirers often lack visibility and understanding of how acquired technology is developed, integrated and deployed and how the services that they acquire are delivered.
- Acquirers with inadequate or absent C-SCRM processes, procedures and practices may experience increased exposure cybersecurity risks throughout the supply chain.
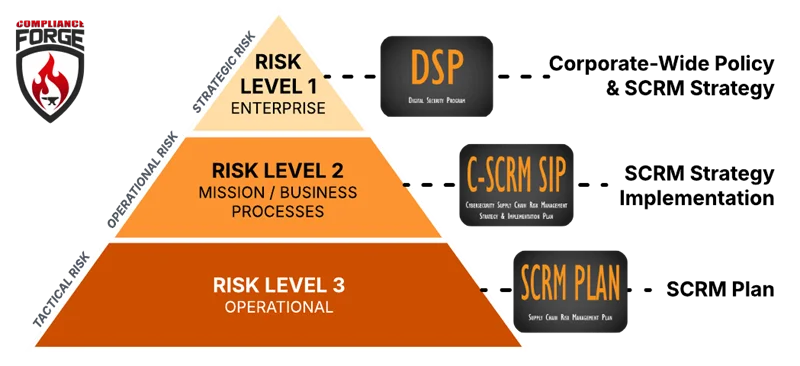
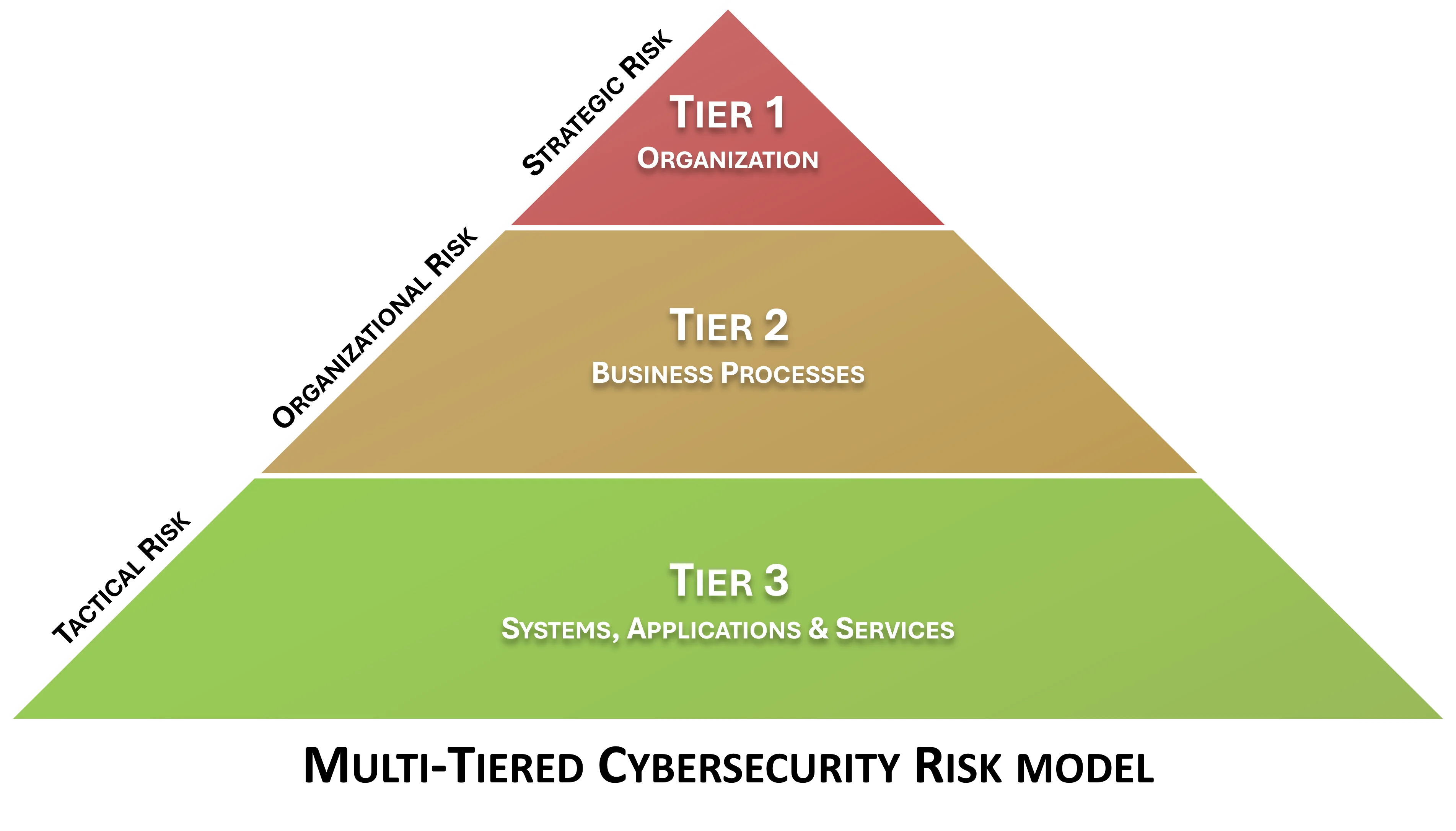
Defining The Hierarchy of Risk Management
Risk management actions primarily exist at different business levels (e.g., strategic risk, operational risk and tactical risk). Each has its own focus and practices.
- At the enterprise level (strategic), there you are going to find corporate-wide policies and a risk management strategy, including defining:
- Risk tolerance; and
- Risk appetite.
- At the mission / business process level (operational), you are going to find risk management practices and strategy implementation, including standardized processes for:
- Risk identification;
- Risk assessment;
- Risk tracking (e.g., risk register); and
- Risk remediation.
- At the team / project / individual contributor level (tactical), you are going to find actionable practices on how to reduce and remediate risk. Evidence of how these risks are managed are often in the form of documented:
- SCRM Plans; and/or
- System Security Plans (SSPs).
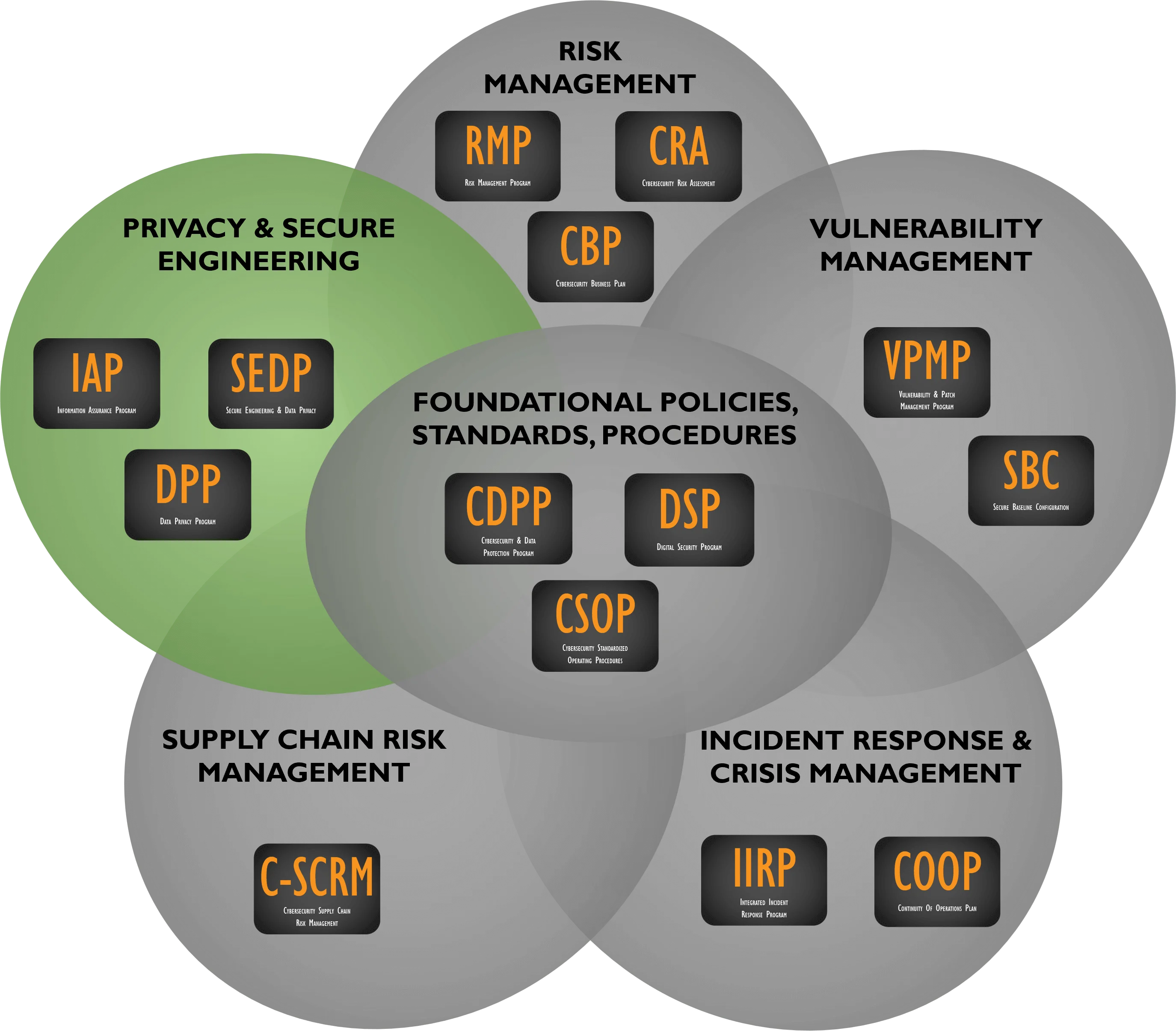
Enterprise Risk Management (ERM) vs Cybersecurity Risk vs SCRM vs C-SCRM
For the purposes of common compliance requirements for a SCRM Plan (e.g., GSA, NIST SP 800-171 Rev 3, etc.), the terms "Supply Chain Risk Management (SCRM)" and "Cybersecurity Supply Chain Risk Management (C-SCRM)" should be considered equivalent. However, if you really wanted to get into the weeds on terminology from a technicality perspective, C-SCRM is a subset of SCRM since SCRM has a broader view of supply chain risks than just cybersecurity where:
- C-SCRM is a subset of broader SCRM practices;
- SCRM is a subset of broader ERM practices.
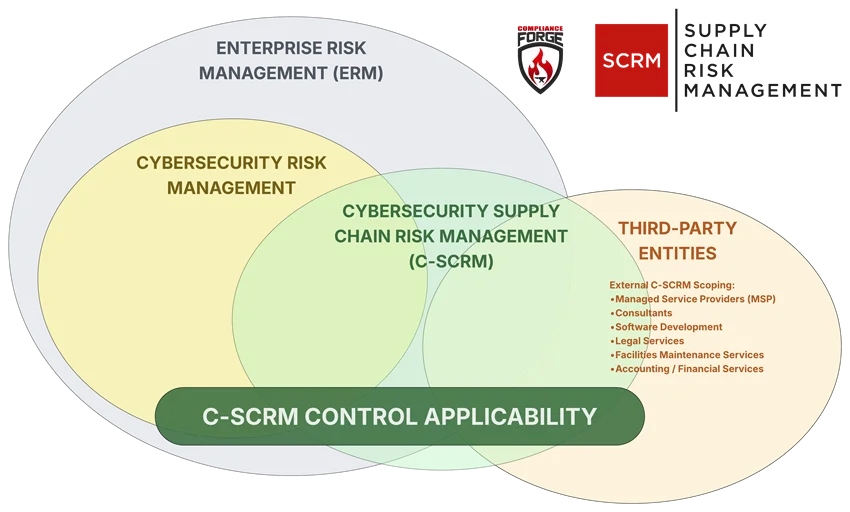
When you look at current usage of the terminology, even authoritative sources such as the DoD, GSA, NIST and other bodies use the terminology interchangeably:
- NIST calls it a "SCRM" in NIST SP 800-171 Rev 3;
- NIST calls it a "C-SCRM" in NIST SP 800-161 Rev 1;
- GSA calls it a "SCRM" in OASIS+ requirements, even when focused on cybersecurity-related matters; and
- DoD calls it a "SCRM" in DI-MGMT-82256A.
In NIST's Glossary, it does not provide a definition for C-SCRM, but does provide a definition for SCRM as, "the implementation of processes, tools or techniques to minimize the adverse impact of attacks that allow the adversary to utilize implants or other vulnerabilities inserted prior to installation in order to infiltrate data, or manipulate information technology hardware, software, operating systems, peripherals (information technology products) or services at any point during the life cycle."
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The C-SCRM SIP Solve?
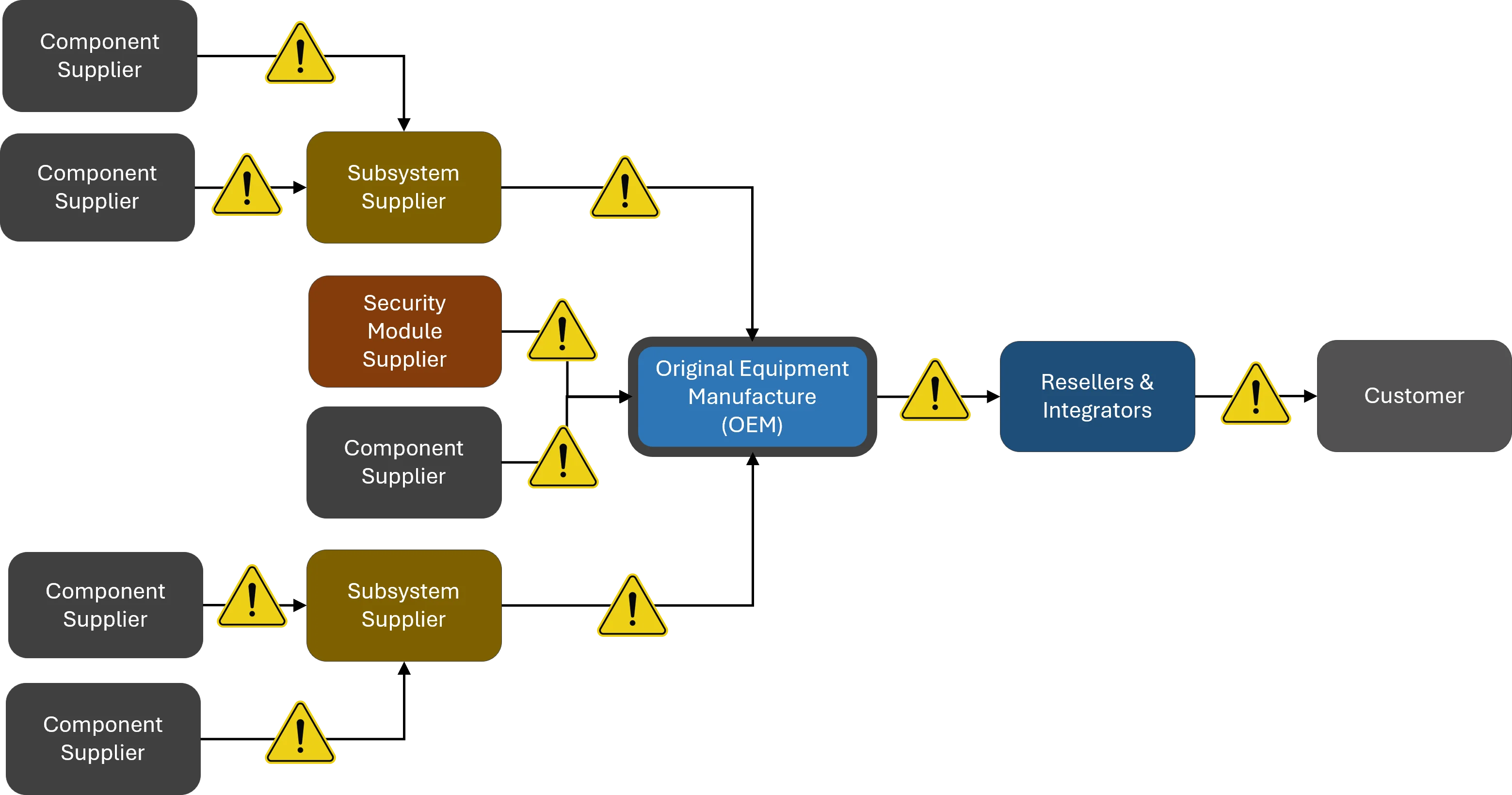
Procuring Information and Communications Technology (ICT) and Operational Technology (OT) products from suppliers establishes a direct relationship between those suppliers and the acquirers. This relationship is also usually guided by a legally-binding, contractual agreement between the acquirer and the supplier. However, commercial ICT/OT developed by suppliers are typically designed for general purposes for a global market and are not tailored to an individual customer’s specific operational or threat environments. Commercial Off The Shelf (COTS) ICT/OT have some shared vulnerabilities to bespoke products, applications and services, but the opaqueness of the components and modules that make up COTS creates its own issues.
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The C-SCRM SIP is an efficient method to obtain documentation to build a C-SCRM Program!
- Compliance Requirements - It is becoming increasingly common for organizations, regardless of industry, to be required to govern its supply chain for cybersecurity and privacy threats and risks.
- Audit Failures - Many organizations run into trouble in audits when asked HOW third-party or supply chain risk is managed, since they cannot provide documentation beyond policies and standards. The C-SCRM SIP addresses the HOW for you!
- Vendor Requirements - It is very common for clients and partners to request evidence of third-party cybersecurity governance. The C-SCRM SIP provides this evidence!
How Does The C-SCRM SIP Solve These Problems?
- Clear Documentation - The C-SCRM SIP provides the documentation to prove that your vendor compliance program exists.
- Time Savings - The C-SCRM SIP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The C-SCRM SIP is aligned with NIST SP 800-161, which is the "gold standard" for supply chain risk management practices.
|
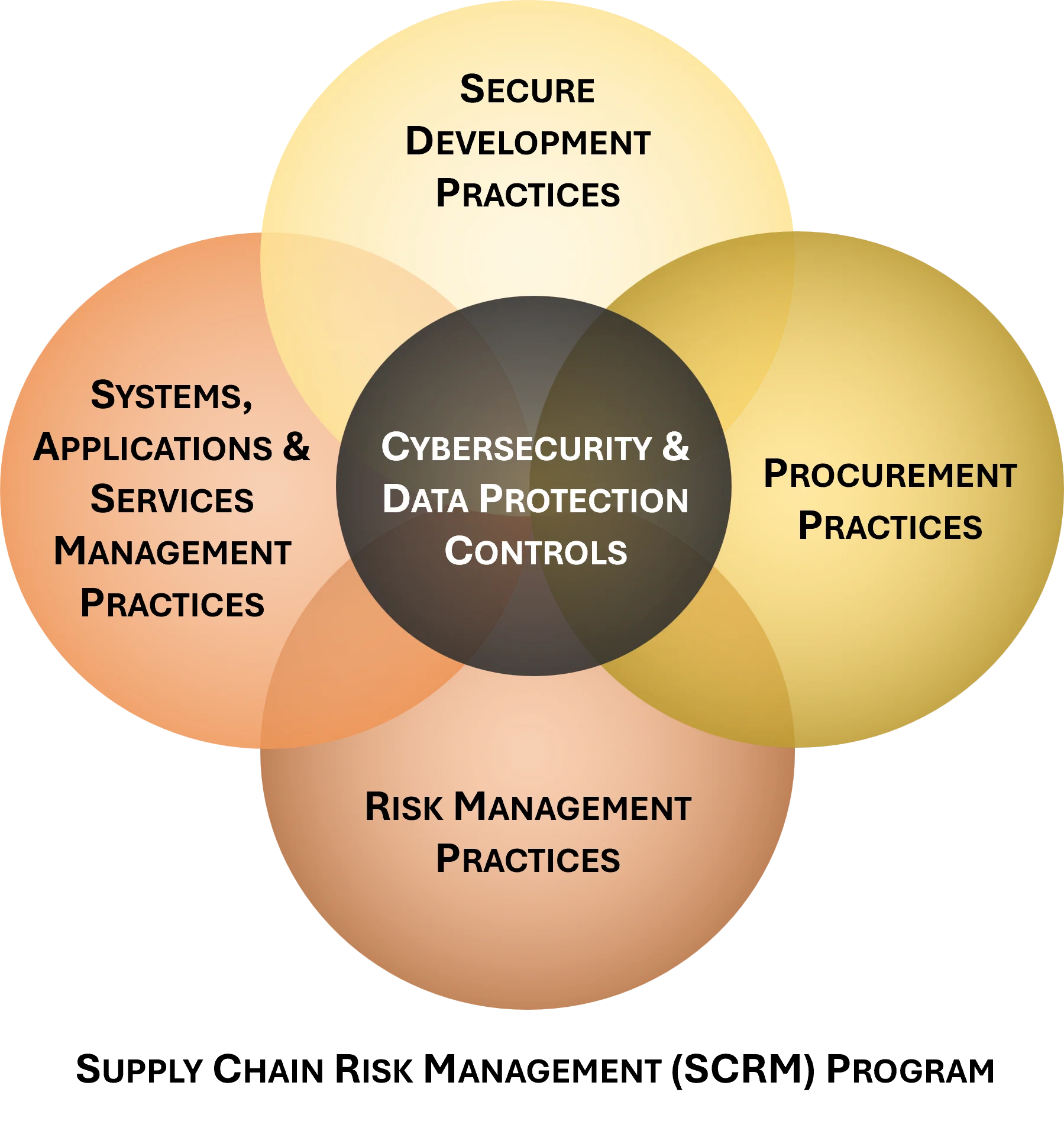
The C-SCRM SIP product is designed to implement a C-SCRM Program, as well as deliver an efficient and cost-effective method to develop a C-SCRM strategy and implement actionable steps to operationalize the C-SCRM strategy. Suppliers, Integrators and Service Providers (SISP) are in scope for C-SCRM operations, where the term SISP includes Original Equipment Manufacturers (OEMs), vendors, contractors, consultants and other entities that make up the supply chain. This scope of operations for the C-SCRM SIP includes all entities that:
Product highlights of the C-SCRM SIP include:
|
|
|
- Cost-effective solution to quickly generate documentation for a C-SCRM strategy and implementation plan.
- Example flow-down contract requirements for suppliers, vendors, subcontractors, etc. (DFARS/CMMC, ISO 27001, NIST CSF, NIST 800-53, FAR, PCI DSS, and EU GDPR/CCPA).
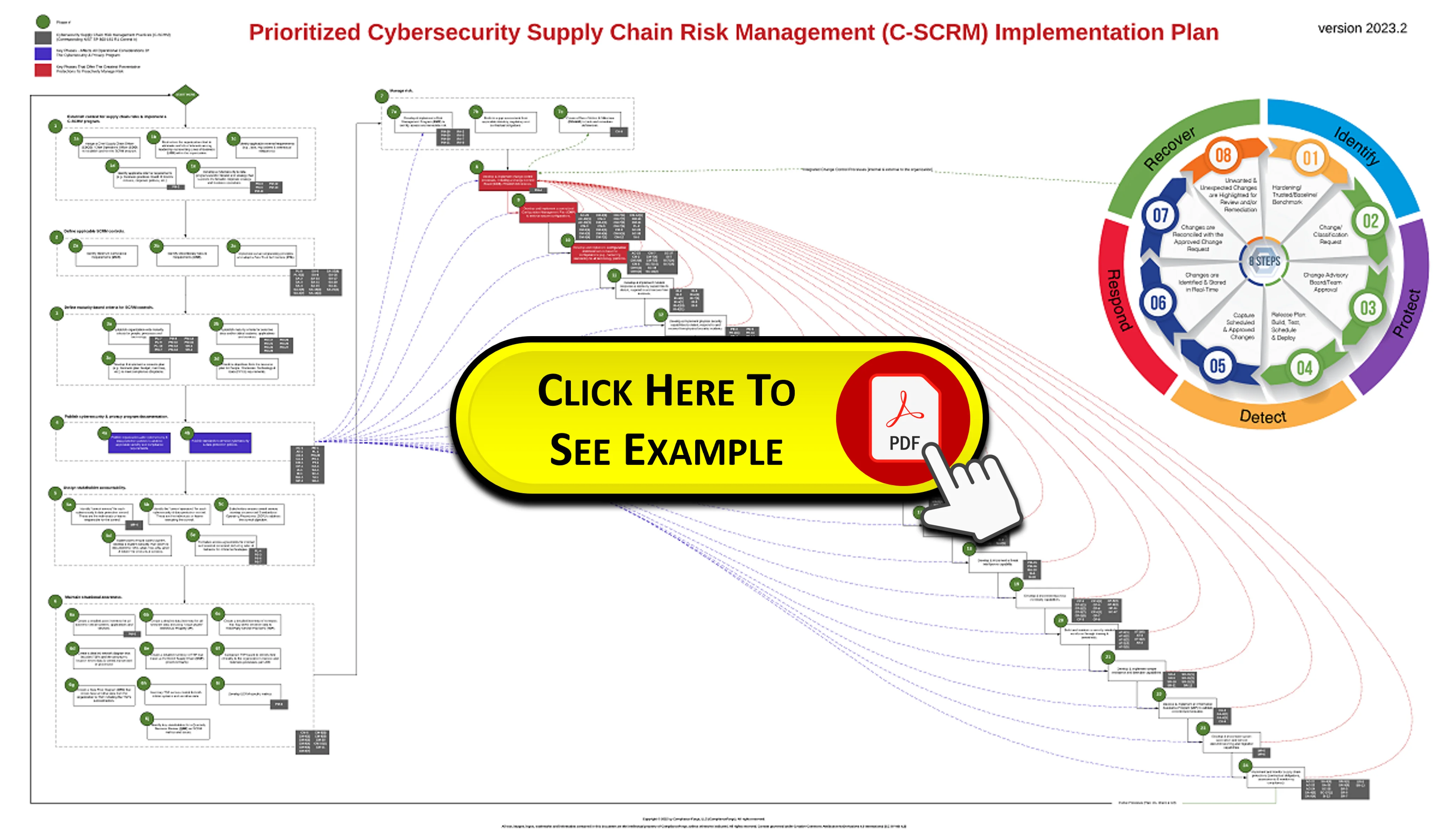
Prioritized C-SCRM Implementation Plan (NIST SP 800-161 R1 Mapping)
|
|
The C-SCRM SIP contains a prioritized implementation plan that takes the controls identified in NIST SP 800-161 R1 and assigns the controls to one of twenty-four prioritized phases. This is designed to help prioritize controls that can prevent re-work during the control implementation process. This is one of the many helpful components that comes with the C-SCRM SIP product. To view the example, click on the image to the left, and it will open a new tab containing the .pdf file for the Prioritized C-SCRM Implementation Plan. You can also access it via this link - https://complianceforge.com/content/pdf/example-cybersecurity-scrm-prioritized-implementation-plan.pdf.
|
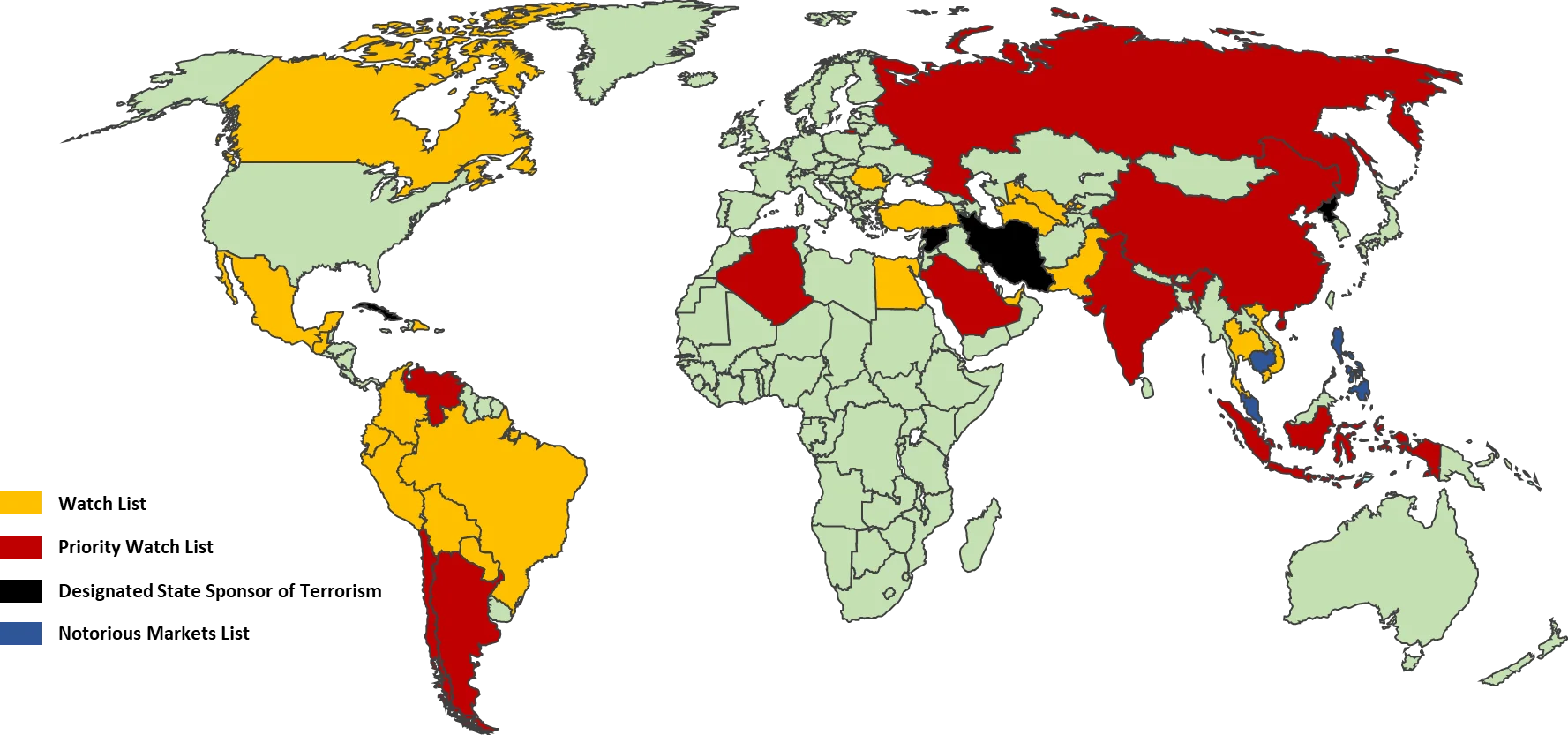
Country-Based C-SCRM Approach
To properly manage supply chain-related threats, your organization must evaluate country-based threats posed by its supply chain. This review must cover the geographic concerns where your products, services and support originate from or transit through:
Within the C-SCRM SIP, that criteria for geographic-specific threat management is refined by guidance from:
|
|
 |
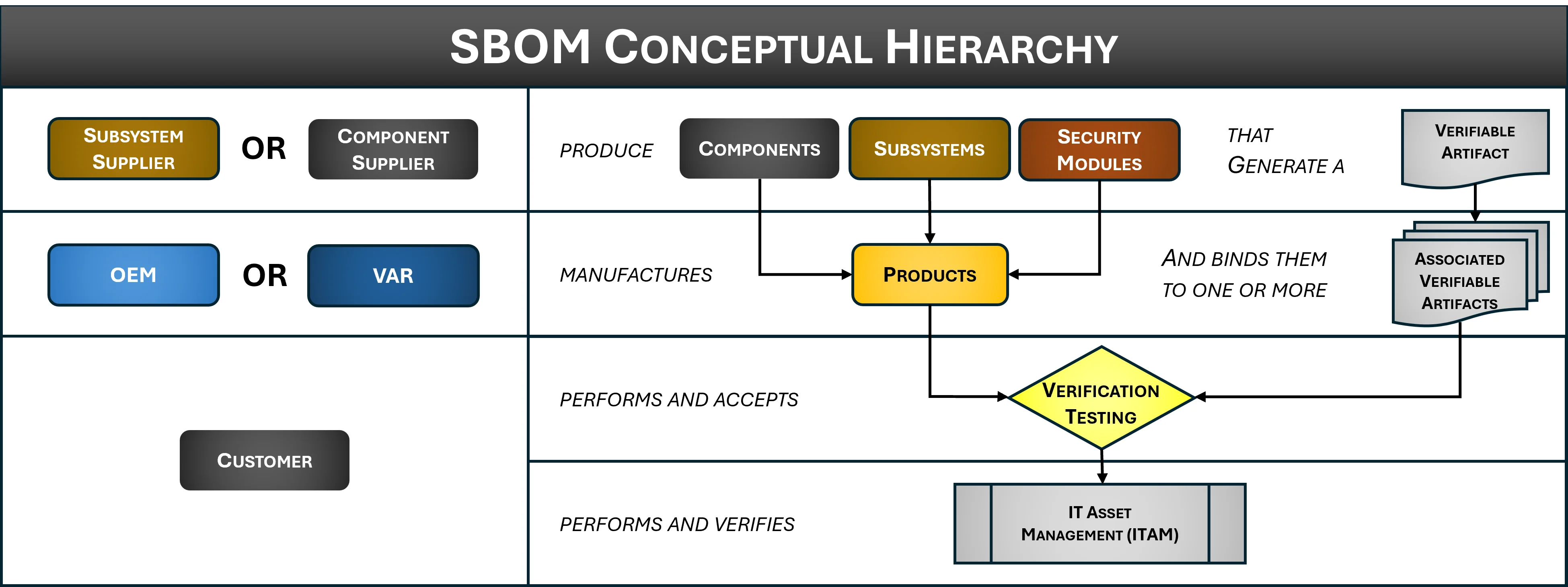
Software Bill of Materials (SBOM) Guidance To Address EO 14028
Executive Order 14028, Executive Order on Improving the Nation’s Cybersecurity, is the driving factor for application security within C-SCRM, due to several, recent high-profile cybersecurity incidents. Specific to C-SCRM application security as it affects private industry, EO 14028 directs US Government agencies to develop plans to:
- Share information by removing barriers to share threat information;
- Modernize cybersecurity capabilities; and
- Enhance software supply chain security.
Due to the nature of how contract requirements flow down through the global supply chain, the ramifications of EO 14028 will be felt across all industries. The requirement that has the most potential to disrupt “business as usual” is expectations that software and services will be expected to have a Software Bill of Materials (SBOM).
Product Example - Cybersecurity Supply Chain Risk Management (C-SCRM) Strategy & Implementation Plan
The Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP) is based significantly on "best practices" from NIST SP 800-161. It contains necessary components to implement a C-SCRM Program and operationalize a C-SCRM strategy with the provided implementation plan guidance. You get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs.
View Product Examples
If you would like to view examples of ComplianceForge's Cybersecurity Supply Chain Risk Management (C-SCRM) Plan documentation, please click any of the images below:
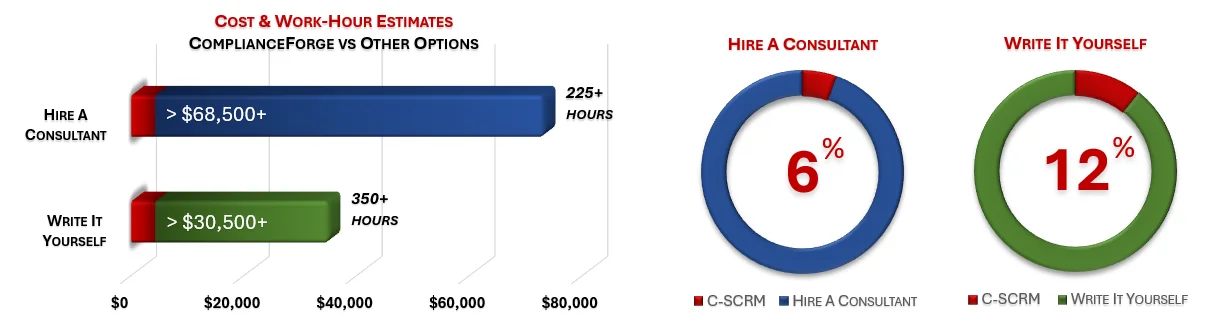
Cost Savings Estimate - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the C-SCRM SIP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 350 internal staff work hours, which equates to a cost of approximately $35,000 in staff-related expenses. This is about 4-8 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 225 consultant work hours, which equates to a cost of approximately $73,125. This is about 3-6 months of development time for a contractor to provide you with the deliverable.
- The C-SCRM SIP is approximately 6% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the C-SCRM SIP the same day you place your order.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the C-SCRM! |
|
|
Cybersecurity Supply Chain Risk Management (C-SCRM) Program
The first step to address that risk is to let your vendors know what is required from them - this addresses due care. The next step is to hold your vendors accountable to meet your requirements - that is due diligence. You owe it to your clients to ensure your risks are addressed across your organization and that is where our Supply Chain Risk Management (C-SCRM SIP) helps.
|
|
|
With requirements like the CMMC, EAR/ITAR, PCI DSS, etc., there is a need for a simple way for a company to inform its service providers of expectations when it comes to managing information security risks. It is a common-sense requirement that businesses should have in place, so that is why there is a push to reduce risk with service providers. In light of the recent breaches at major corporations, it is likely that a crackdown will follow for businesses to follow better cybersecurity. One of the most important points to remember when it comes to compliance is that if you cannot prove you are compliant (e.g., documented policies & standards) then your business will be unlikely to count on business insurance to cover the expense of a breach. The C-SCRM SIP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer. |
Reducing Risk Is Central To The Supply Chain Risk Management
Having a Supply Chain Risk Management (C-SCRM SIP) is focused on minimizing risk to your company, your partners and your customers. There is traditionally low level-risk (tactical) that is focused on weaknesses pertaining to routine systems and data. There is mid-level risk (operational) that is focused on weaknesses pertaining to business process. There is also high-level (strategic) risk that impacts at an organizational level. Having a secure vendor relationship can address risk at all three of these levels.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.