Cybersecurity & Data Privacy Control Validation Testing
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the IAP is to help answer common questions we receive.
What Is The Information Assurance Program (IAP)?
Is your organization looking for a cybersecurity assurance program? ComplianceForge's Information Assurance Program (IAP) is focused on pre-production testing and based on established processes used by the US Government (e.g., FISMA, DIACAP, DIARMF) to validate the existence and functionality of controls, prior to a system, application or service going into production. In US Government language, this is commonly referred to as Certification & Accreditation (CA) or Security Testing & Evaluation (ST&E). We "civilianized" this concept of CA/ST&E to create a method to enable cybersecurity and privacy personnel to work with your organization's existing System Development Life Cycle (SDLC) / Project Development Life Cycle (PDLC) to ensure privacy and cybersecurity principles are designed and built-into your systems, applications and services!
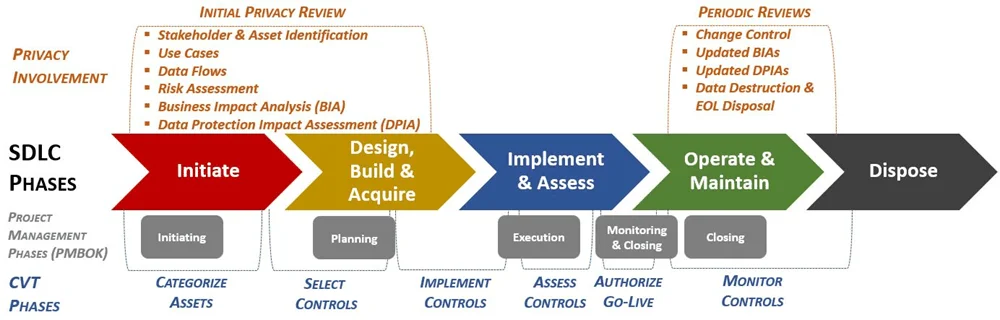
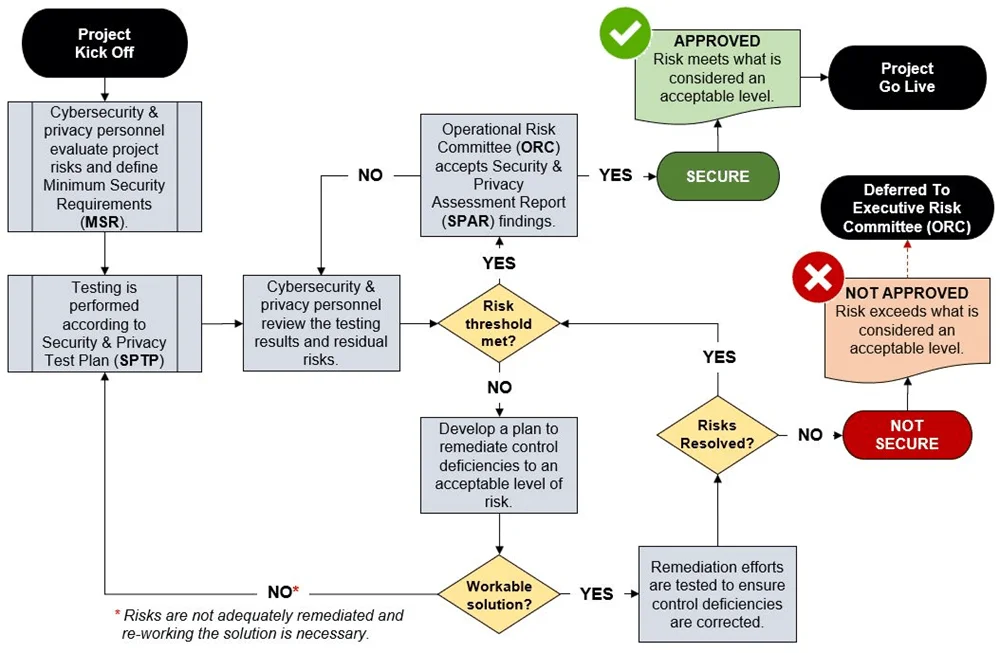
The end state with control validation testing is:
- Removal of "security roadblocks" by embedding cybersecurity and privacy into the SDLC/PDLC from project kick-off through the "go live" data.
- Having evidence of both cybersecurity and privacy principles being identified and implemented by design (e.g., EU GDPR compliance)
- Utilizing a customized control sets that defines Minimum Security Requirements (MSR) specific to the project undergoing review.
- A data-centric view across systems, applications, services and third-parties that enables situational awareness of both cybersecurity and privacy risks.
- A Project Risk Register (PRR) that tracks risks and the associated remediation actions (e.g., Plan of Action & Milestones (POA&M)).
- A formal method of getting stakeholder accountability for residual risk.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The IAP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The IAP is an efficient method to obtain comprehensive system hardening documentation.
- Compliance Requirements - There are numerous requirements (several listed at the top of this page) that require pre-production security testing to be performed and documented. The IAP is designed with compliance in mind, since it focuses on leading "best practices" for ensuring systems, applications and services are verified to address reasonably-expected requirements for cybersecurity and privacy exist and function accordingly.
- Audit Failures - A lack of documented pre-production security testing is a common audit failure. The IAP covers traditional SDLC/PDLC models that include Agile, Waterfall and other approaches to project management. This is designed to integrate with your existing processes to bake in cybersecurity and privacy principles.
- Vendor Requirements - It is getting more common for clients and partners to request evidence of secure processes, including SDLC/PDLC security and privacy efforts. The IAP provides this evidence!
How Does the IAP Solve These Problems?
- Clear Documentation - The IAP provides comprehensive cybersecurity and privacy pre-production testing to prove that your security is more than just a set of policies and standards.
- Time Savings - The IAP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The IAP is written to align your organization with leading practices for secure engineering processes.
Why Should I Buy The IAP? What Actually Requires "Pre-Production Testing" To Be Performed?
As a CISO or CPO, performing IAP is not only the right thing to do from a security and privacy perspective, but it is serious job security. When things go bad and fingers get pointed, do you have a "get out of jail free card" that you can use? If not, keep reading.
|
A CISO or CPO should never make the decision to "sign off" and own risk, since it is ultimately a business decision and that director/VP of the business unit should be accepting the risk for their projects, services and vendors needed to operate. It is the responsibility of the CISO and CPO to have a data-centric view of risk from the application, system, service and supply chain perspective. With this understanding of the risks, the CISO and CPO need to educate the business process owners if minimum security requirements are/are not met and if the risk falls within the organization's risk appetite. This is where the CRO role defines what is acceptable risk and works with the business units to get them to hopefully make the correct GO/NO GO decision. If they do choose to do something outside of the risk appetite, the CRO/CISO/CPO has evidence to demonstrate due care in their analysis. A lot of this requires a mature pre-production control validation testing process, which is absent in many organizations beyond a rudimentary security gate for change control. |
|
|
The following are common statutory, regulatory and contractual requirements that expect “pre-production testing” or "information assurance" activities to be performed:
- ISO 27002 – 14.2.8
- European Union General Data Protection Regulation (EU GDPR) – Article 25
- NIST 800-171 – 3.12.1, 3.12.3 & Non-Federal Organization (NFO)
- NIST Cybersecurity Framework – PR.IP-2, PR.IP-5 & DE.DP-3
- Federal Risk and Authorization Management Program (FedRAMP) – Security Assessment & Authorization (CA) controls
- AICPA Trust Services Principles (TSP) SOC2 – CC7.4
- Center for Internet Security Critical Security Controls (CIS CSC) – 18.2, 18.4 & 18.8
- Cloud Security Alliance Cloud Controls Matrix (CSA CCM) – CCC-03
- Cloud Computing Compliance Controls Catalogue (C5) – BEI-02
- Monitory Authority of Singapore Technology Risk Management (MAS TRM) Guidelines - 6.0.1, 6.2.2, 6.2.3, 6.2.4, 6.3.4, 6.4.2, 6.4.3, 6.4.4, A.1.1 & A.1.2
- European Union Agency for Network and Information Security (ENISA) Technical Guideline of Security Measures – SO23
- National Industry Security Program Operating Manual (NISPOM) – 8-610 & 8-302
- Criminal Justice Information Services (CJIS) Security Policy – 5.10.4.1, 5.11.1.1, 5.11.1.2, 5.11.2 & 5.13.4.1
- Massachusetts MA 201 CMR 17.00 – 17.03(2)(d)(B)(i) & 17.03(2)(h)
- New York Department of Financial Services (23 NYCRR 500) – 500.02
- Oregon Consumer Identity Theft Protection Act (OCITPA) – 622(2)(B)(i)-(iv)
- Underwriters Laboratories (UL) 2900-1 – Section 12
- Payment Card Industry Data Security Standard (PCI DSS) – Requirement 6
- Motion Picture Association of America (MPAA) Content Security Program – MS-2.0
Product Example - IAP
The IAP is based on leading security engineering practices, including NIST 800-160 and NIST 800-37. You get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs. Please review the examples below to see for yourself:
View Product Examples
If you would like to view examples of ComplianceForge's Information Assurance Program (IAP), please click any of the images below:
Cost Savings Estimate - Information Assurance Program (IAP)
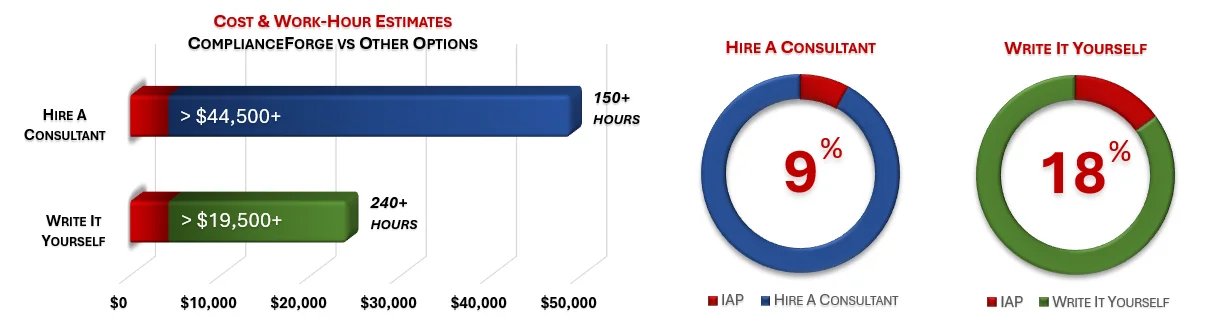
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 270 internal staff work hours, which equates to a cost of approximately $24,000 in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work. This assumes you have staff that has performed IA/ST&E work who can even develop this documentation.
- If you hire a consultant to generate this documentation, it would take them an estimated 150 contractor work hours, which equates to a cost of approximately $48,750. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- It is approximately 9% of the cost for a consultant or 18% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the IAP! |
|
|
What Does the IAP Come With?
The IAP comes with everything you need to stand up a process to do pre-production security & privacy testing:
- Core Word document that is the program-level guidance on the Information Assurance Program (IAP) at your organization;
- Editable Excel spreadsheets that contain mappings to leading practices and other helpful charts to clarify requirements;
- Security & Privacy Test Plan (SPTP) template to document the plan to perform IAP for a specific project;
- Security & Privacy Plan (SPP) is essentially a traditional System Security Plan (SSP) with privacy added into it;
- Project Risk Register (PRR) template to document risks and remediation actions; and
- Security & Privacy Assessment Report (SPAR) template to write up the overall risk report for the project.
All of these documents come together to enable you to hit the ground running with IAP operations!
What Controls Does the IAP Rely On?
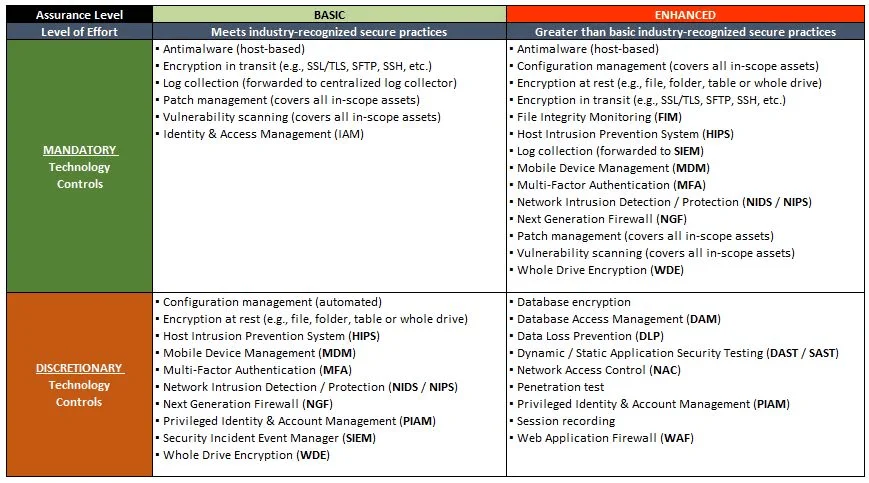
The IAP is very flexible for the control set that you might want to use for IAP. Assuming you do not have something to use "out of the box" we have that covered with the ability to use the Secure Controls Framework (SCF). If you are not familiar with the SCF, it is a robust set of cybersecurity and privacy controls that maps to over 100 statutory, regulatory and contractual frameworks, so it is a great, free tool for businesses to use! The IAP comes with instructions on paring down the SCF to define just the right "level of effort" for the control set, based on the pertinent compliance needs and risk appetite of your organization.
If you have any questions on the IAP, please contact us since we are happy to do a demo or answer your questions in greater detail.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.