Secure Baseline Configurations For Technology Assets
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the SBC is to help answer common questions we receive.
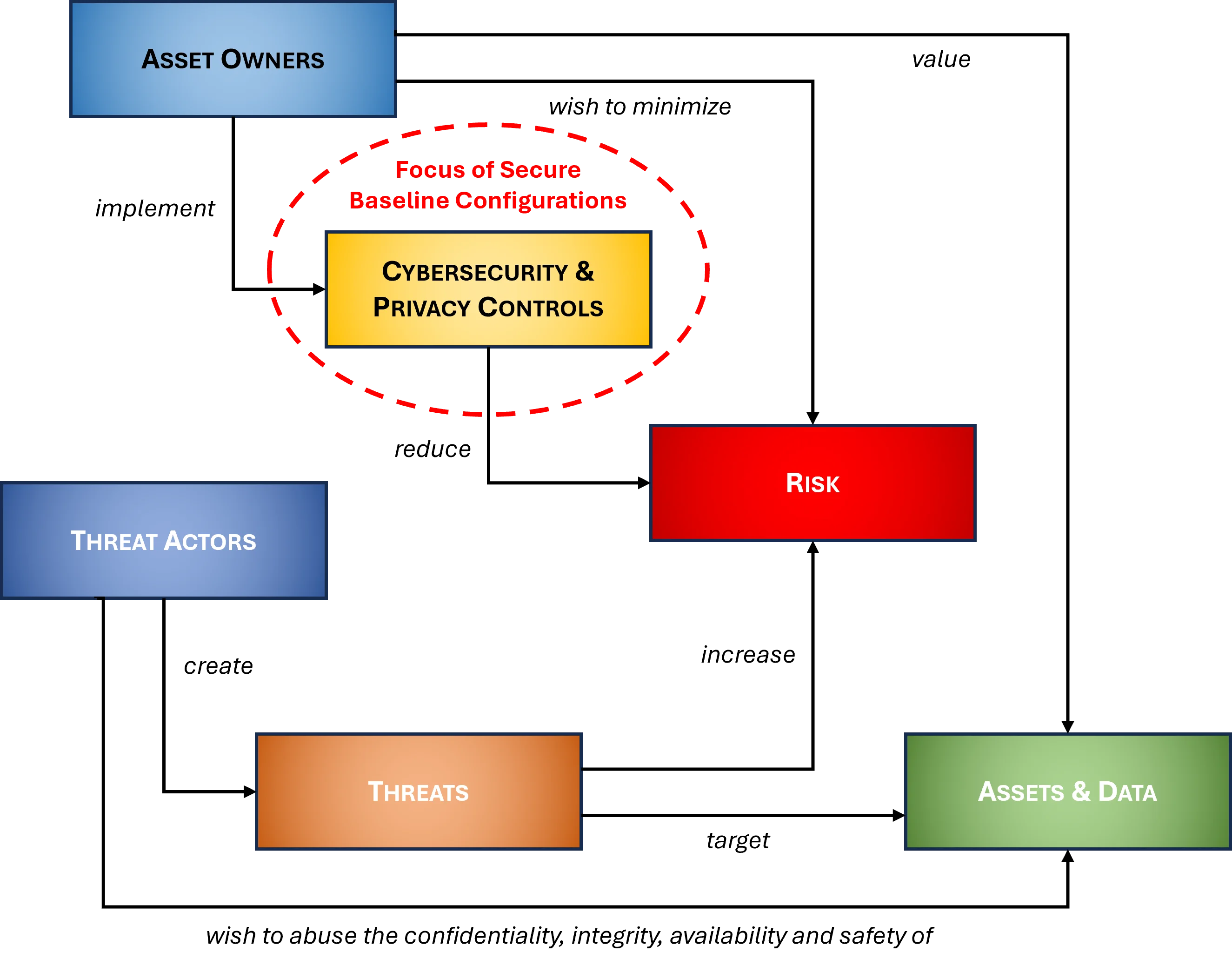
What Is The Secure Baseline Configurations (SBC)?
The Secure Baseline Configurations (SBC) is a documentation solution to efficiently document what constitutes a "hardened" system in your organization. This is applicable to operating systems, applications and services.
Many IT and cyber professionals mistakenly focus only on hardening the operating system (e.g., Windows 10) and fail to document all the technology platforms that require secure configurations (e.g., applications, HVAC systems, mobile devices, VoIP, etc.). The SBC does not re-invent the wheel, but leverages leading practices such as CIS Benchmarks and DISA STIGs. Unless it is a small organization with just a few laptops and a server, it is not feasible to say "we harden everything according to CIS Benchmarks". since CIS does not contain a complete coverage for all technology platforms and the same weakness can be said for using the DISA STIGs. This is where the SBC brings together a variety of options for hardening and creating technical security standards that include CIS, DISA, OEM recommendations and more!
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The SBC Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The CVT is an efficient method to obtain comprehensive system hardening documentation.
- Compliance Requirements - There are numerous requirements (several listed at the top of this page) that require secure configurations to be developed and implemented. The SBC is designed with compliance in mind, since it focuses on leading "best practices" for securing systems, applications and services to address reasonably-expected security requirements for hardening.
- Audit Failures - A lack of documented secure hardening requirements is a common audit failure. The SBC covers a wide array of common technologies that can both make an organization secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program, including secure configurations. The SBC provides this evidence!
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product!
How Does the SBC Solve These Problems?
|
Clear Documentation - The SBC provides comprehensive hardened baseline configuration documentation to prove that your security is more than just a set of policies and standards.
The SBC addresses a common control to reduce risk, the need for ensuring that systems, applications and services are hardened according to recommended practices. The SBC provides a way to efficiently manage all of these common technology platforms to document and educate system/network admins and other system integrators about what "secure configurations" and "cybersecurity baselines" are at your organization: |
|
|
- Server-class systems
- Microsoft
- Linux
- Unix
- Other
- Workstation-class systems
- Microsoft
- Apple
- Linux
- Network devices
- Firewalls
- Routers
- Wireless Access Points (WAPs) & controllers
- Multi-Function Devices (MFDs)
- Voice & Video over Internet Protocol (VVoIP)
- Mobile devices
- Apple
- Windows
- Databases
- Microsoft SQL
- MySQL
- Oracle
- PostgreSQL
- IBM DB2
- MongoDB
- Major applications
- Microsoft Active Directory (AD)
- Microsoft Exchange
- Microsoft SharePoint
- Microsoft Internet Information Services (IIS)
- Domain Naming Services (DNS)
- Apache Tomcat
- Apache HTTP server
- VMware
- Centralized log management (e.g., SIEM)
- Intrusion Detection / Prevention Systems (IDS/IPS)
- Minor applications
- Microsoft Office
- Microsoft Internet Explorer (IE)
- Google Chrome
- Mozilla Firefox
- Apple Safari
- Adobe
- AJAX
- .NET
- WordPress
- Cloud-based applications
- Microsoft Office 365
- Microsoft Azure
- Amazon Web Services (AWS)
- Google Cloud Computing
- Docker
- Kubernetes
- Embedded technology
- Microsoft Windows-based devices
- Heating, Ventilation & Air Conditioning (HVAC)
- Physical Access Control (PAC)
- Video surveillance
- Burglar / fire alarm systems
Why Should I Buy The SBC? What Actually Requires "Secure Configurations" To Be Documented?
The following are common statutory, regulatory and contractual requirements that expect “secure configurations” or "system hardening" for an organization's technology assets. If your organization is in scope for any of those, you should buy the SBC:
- AICPA Trust Services Principles (TSP) SOC2 – CC7.1 & CC8.1
- Center for Internet Security Critical Security Controls (CIS CSC) – 5.1, 5.2, 5.3, 5.5, 6.2, 8.3, 8.4, 8.5, 8.6, 9.1, 9.2, 11.1, 14.8, 15.6, 15.7, 15.8 & 15.9
- COBIT 5 - BAI10.02
- Cloud Security Alliance Cloud Controls Matrix (CSA CCM) – GRM-01 & IVS-07
- ISO 27002 – 14.1.1
- Motion Picture Association of America (MPAA) Content Security Program – DS-1.5, DS-1.12, DS-3.3, DS-3.5, DS-3.7, DS-3.8, DS-6.5, DS-6.9, DS-6.10, DS-7.3 & DS-7.8
- NIST 800-37 - I-2
- NIST 800-53 / FedRAMP - CM-2, CM-6 & SA-8
- NIST 800-160 - 3.4.7 & 3.4.8
- NIST 800-171 – 3.4.1 & 3.4.2
- NIST Cybersecurity Framework – PR.IP-1 & PR.IP-3
- Payment Card Industry Data Security Standard (PCI DSS) – 1.1, 1.1.1 & 2.2-2.2.4
- National Industry Security Program Operating Manual (NISPOM) – 8-202, 8-311 & 8-610
- Criminal Justice Information Services (CJIS) Security Policy – 5.7.1, 5.7.1.1, 5.7.2 & 5.13.4
- Cloud Computing Compliance Controls Catalog (C5) – RB-22
Product Example - SBC
When you buy the SBC, you get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs. The example below provides a good look at what you will get when you purchase the SBC.
View Product Example
If you would like to view an example of ComplianceForge's Secure Baseline Configuration (SBC), please click the image below:
 Policies & Standards |
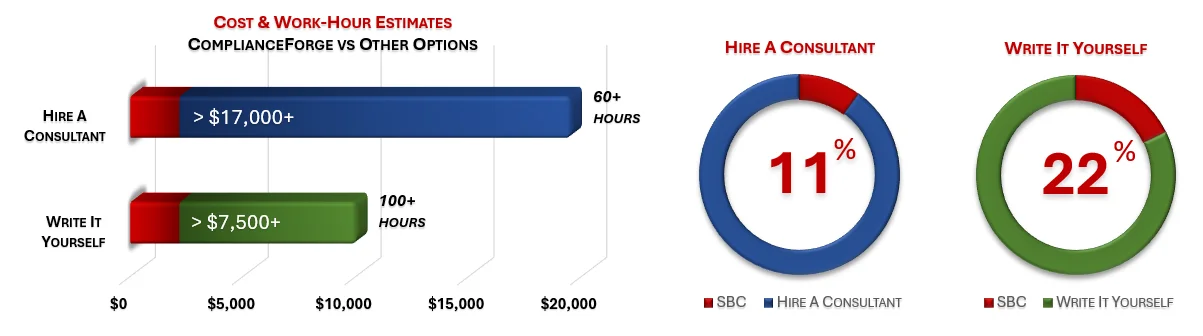
Cost Savings Estimate - Secure Baseline Configurations (SBC)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 110 internal staff work hours, which equates to a cost of approximately $10,000 in staff-related expenses. This is about 1-3 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 60 contractor work hours, which equates to a cost of approximately $19,500. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- It is approximately 11% of the cost for a consultant or 22% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the SBC! |
|
|
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.