
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing the Secure Controls Framework (SCF):
- Digital Security Program (DSP)
- Cybersecurity Standardized Operating Procedures (CSOP)
- NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)
- Risk Management Program (RMP)
- Cybersecurity Risk Assessment Template (CRA)
- Vulnerability & Patch Management Program (VPMP)
- Integrated Incident Response Program (IIRP)
- Continuity of Operations Plan (COOP)
- Secure Baseline Configurations (SBC)
- Information Assurance Program (IAP)
- Secure Engineering & Data Privacy (SEDP)
- Cybersecurity Business Plan (CBP)
- Data Protection Program (DPP)
This bundle builds on the core documentation that comes in DSP bundle #2 and adds much-needed tactical and operational guidance including a Continuity of Operations Plan (COOP), Secure Baseline Configurations (SBC) to harden your systems, Information Assurance Program (IAP) to govern pre-production security testing, Secure Engineering & Data Privacy (SEDP) to help ensure privacy and cybersecurity principles are designed and managed properly, a Cybersecurity Business Plan (CBP) template to help formalize a strategy for the cybersecurity department, and a Data Protection Program (DPP) that helps accelerate the adoption and implementing of a privacy program at your organization.
The DSP and its corresponding Cybersecurity Operating Procedures (CSOP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices by providing GRC policies and GRC procedures. Not only do you get the policies, standards, controls, procedures and metrics that form the basis of security and privacy operations, but you get program-level guidance that addresses common areas of compliance and business risk. The end result with this DSP bundle is a comprehensive, customizable, easily-implemented set of documentation that your company needs to establish a scalable, "best in class" cybersecurity and privacy program. Please note that if you want a customized bundle, we are happy to create one for you. Just contact us with your needs and we will generate a quote for you.


Cost Savings Estimate - DSP Bundle #3
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 4,100 internal staff work hours, which equates to a cost of approximately $404,000 staff-related expenses. This is about 36-48 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 3,100 contractor work hours, which equates to a cost of approximately $969,750. This is about 24-36 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 7% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.

Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.
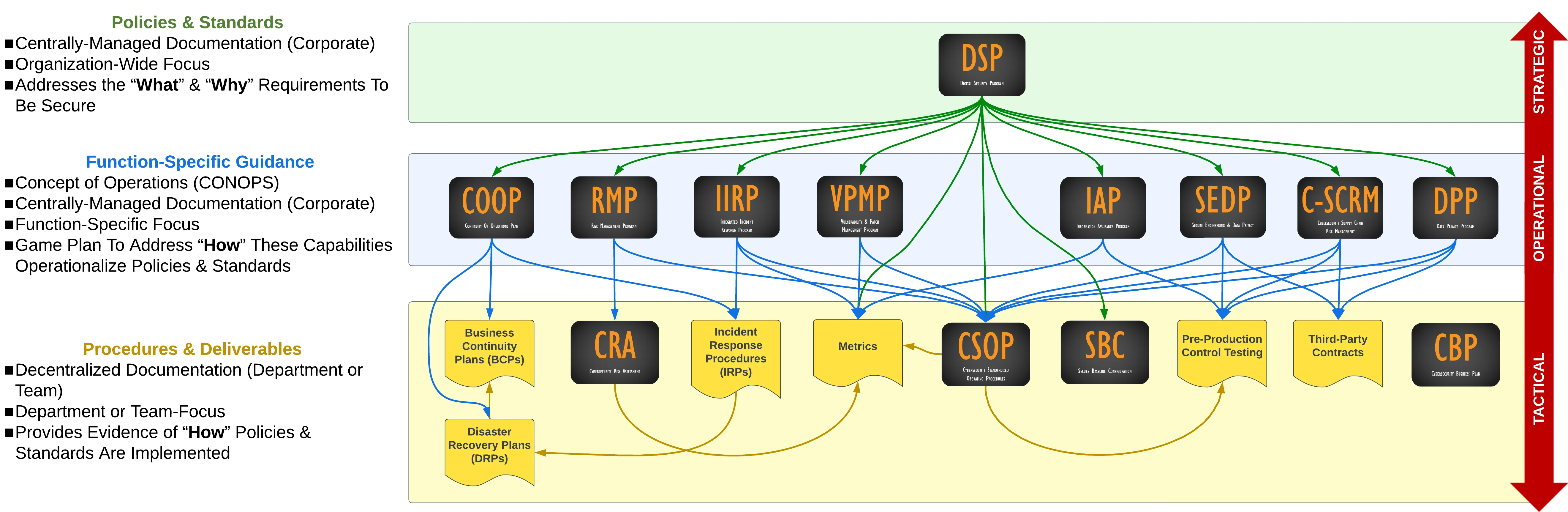
Products Included in DSP Bundle #3
|

|
Digital Security Program (DSP)
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the Secure Controls Framework (SCF), so you can easily align your policies, standards and metrics with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates
|
 |
Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements.
|
 |
Integrated Incident Response Program (IIRP)
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team (ISIRT) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise (IoC).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response.
|
 |
Risk Management Program (RMP)
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as NIST 800-37, NIST 800-39, ISO 31010 and COSO 2013.
|
 |
Cybersecurity Risk Assessment (CRA) Template
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports.
|
 |
Vulnerability & Patch Management Program (VPMP)
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance.
|
 |
NIST SP 800-161 Rev 1-Based Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
 |
Secure Engineering & Data Privacy (SEDP)
The SPBD addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SPBD provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SPBD is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering.
|
 |
Continuity of Operations Program (COOP)
The COOP addresses the “how?” questions for how your company plans to respond to disasters to maintain business continuity.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP's policies and standards for disaster recovery and business continuity operations.
- The concept of “continuity operations” spans incident response to disaster recovery to business continuity operations. This is a very common requirement in numerous statutory, regulatory and contractual requirements. The COOP provides your organization with the documentation to prove it addresses both disaster recovery and business continuity.
- The COOP is based on numerous frameworks to provide a holistic approach to DR and BC operations.
|
 |
Secure Baseline Configurations (SBC)
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization.
|
 |
Information Assurance Program (IAP)
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E).
|
 |
Cybersecurity Business Plan (CBP)
The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization.
|
 |
Data Protection Program (DPP)
The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles.
|
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.



















