NIST 800-171 Rev 2 & Rev 3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the NCP is to help answer common questions we receive.
What Is The NIST 800-171 Compliance Program (NCP)?
The NCP is a collection of several editable Microsoft Word, Excel and PowerPoint templates - there are no blanks to fill in, since these are professionally-written documents that enable you to customize for your specific needs. There is no software to install and it is a one-time purchase. You get the following material as part of the NCP:
- Updated Coverage For Both NIST 800-171 R2 & R3 (mapped to the Assessment Objective level of NIST 800-171A)
- Cybersecurity Policies (policies specific to NIST 800-171 and CMMC 2.0 L2)
- Cybersecurity Standards (standards that are specific to NIST 800-171 and CMMC 2.0 L2)
- Cybersecurity Standardized Operating Procedures (SOP) (procedures that are specific to NIST 800-171 and CMMC 2.0 L2)
- - NIST 800-171 R3 ADDITION - Supply Chain Risk Management (SCRM) Plan
- Risk Assessment Worksheet & Report Template (perform a risk & threat assessment using Microsoft Word and Excel)
- System Security Plan (SSP) Template
- Plan of Action & Milestones (POA&M) Template
- Provides coverage for related compliance requirements found in:
- Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7008, 252.204-7012, 252.204-7019, 252.204-7020 and 252.204-7021
- Federal Acquisition Regulation (FAR) 52.204-21, 52.204-27 and Section 889
- International Traffic in Arms Regulation (ITAR)
- Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7008, 252.204-7012, 252.204-7019, 252.204-7020 and 252.204-7021
- A Considerable Number of Reference Documents and Other Templates:
- Risk catalog
- Threat catalog
- Evidence Request List (ERL)
- Incident Response Plan (IRP) template
- Business Impact Analysis (BIA) template
- Business Continuity / Disaster Recovery (BC/DR) template
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- Mobile device usage guidelines
- Risk management guidelines
- System hardening guidelines
- and more!
The NCP is "battle tested" - our clients have successfully passed DIBCAC assessments with this documentation, including a CMMC Third-Party Assessment Organization (C3PAO). You receive a lifetime license to use the NCP at your company and the purchase price includes one year of updates. After the first year, you can choose to subscribe to updates or not.
The NCP is designed to fit the needs of small to medium businesses in need of a “square peg for a square hole” to singularly address NIST 800-171 and CMMC compliance requirements. The NCP provides coverage for all Controlled Unclassified Information (CUI) and Non-Federal Organization (NFO) controls found in Appendix E of NIST 800-171, as well as the Assessment Objectives (AOs) from NIST 800-171A (note - if you are unclear what NFO controls are, ComplianceForge has a page on its website that is dedicated to the topic that is worth reading). Given the coverage of NIST 800-171 and 800-171A, the NCP also provides necessary coverage for CMMC Level 1 and Level 2 controls.
The core NCP documents include:
- Cybersecurity & Data Protection Program (CDPP) – cybersecurity policies & standards tailored for NIST 800-171 & CMMC 2.0
- Cybersecurity Standardized Operating Procedures (CSOP) – cybersecurity procedures tailored for NIST 800-171 & CMMC 2.0
- System Security Plan (SSP)
- Plan of Action & Milestones (POA&M)
- Third-Party Security Management (TPSM) - third-party Cybersecurity Supply Chain Risk Management (C-SCRM) guidance
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "90% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
What Problems Does The NCP Solve?
- Lack of In House Security Experience - Most smaller contractors lack expertise in NIST 800-171. Tasking your managers, IT personnel or security staff to research and write comprehensive documentation is not a wise use of their time. The NCP is an efficient method to obtain comprehensive compliance documentation that can be implemented by either your in-house staff or outsourced IT vendor. Most small contractors cannot afford tens of thousands of dollars in consultant fees to help become compliant with NIST 800-171, so the NCP is designed with affordable compliance in mind to give your business the NIST 800-171 compliance documentation it needs.
- Compliance Requirements - NIST 800-171 is a reality for companies in scope for DFARS and FAR. The NCP is designed with compliance in mind, since it focuses on reasonably-expected security requirements to address the NIST 800-171 controls. The documentation contained in the NCP gives you everything you need to comply with NIST 800-171 from policies to standards to procedures to templates for your System Security Plan (SSP) and Plan of Action & Milestones (POA&M).
- Audit Failures - Without being able to demonstrate compliance with NIST 800-171, your organization will likely lose government contracts - it is as simple as that. The NCP is a tool that can jump start your organization towards being compliant with NIST 800-171 requirements.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies and standards. The NCP can provide this evidence!
We listened to our customers and created the NIST 800-171 Compliance Program (NCP), based on the growing demand from small and medium businesses that want a simplified approach to NIST 800-171 & Cybersecurity Maturity Model Certification (CMMC) compliance. The NCP is a set of editable cybersecurity documentation templates that are tailored for small and medium businesses to address NIST 800-171 / CMMC 2.0 compliance. The NCP is streamlined to singularly focus on what is required to comply with NIST 800-171 R2 and CMMC 2.0. Both the policies & standards document (CDPP) and procedures document (CSOP) have footnotes to clearly identify which NIST 800-171, NIST 800-171A and/or CMMC requirement is addressed. The NCP is meant to provide coverage for the “who, what, when, how & why” considerations for your cybersecurity program that address scoping from your strategic, operational and tactical needs. We've performed the heavy lifting to build these documentation templates and you (or your IT consultants) just need to fill in the details that only you will know. We do have consulting services available, if you need assistance.
How Does The NCP Solve These Problems?
- Clear Documentation - The NCP comes in editable Microsoft Office format (e.g., Word, Excel and PowerPoint), so it is customizable for your needs.
- Time Savings - The time savings are immense, as compared to writing something equivalent of the NCP yourself or hiring a consultant to write it for you!
- Alignment With Leading Practices - The NCP has direct mapping to several leading cybersecurity frameworks, including:
- NIST 800-53
- ISO 27002
- NIST Cybersecurity Framework (CSF)
- NIST 800-160
- Secure Controls Framework (SCF)
The NCP is a bundle of editable documentation templates that is designed to save your organization hundreds of hours in labor. These are the policy sections that address the 14 sections of CUI from NIST 800-171 (as well as Non-Federal Organization (NFO) controls from Appendix E) and the 17 sections of CMMC that overlap what is in NIST 800-171. Most people forget or ignore the NFO controls component, which is a basic expectation of being compliant with NIST 800-171 but we include NFO, CUI and CMMC requirements in the NCP
There is no getting around the necessity to read and be familiar with NIST 800-171 and CMMC - that can’t be avoided. One of the best things you can to start off is make yourself a pot of coffee and familiarize yourself with the CMMC Kill Chain since you really need to have a prioritized plan to address NIST 800-171 / CMMC requirements. This is the process we recommend for using the NCP:
- Familiarize yourself with all the documents that come as part of the NCP. At least read through the table of contents and appendices to see what is contained so you understand where to find things.
- Start with the policies & standards – that is a relatively easy win and establishes requirements that other practices will be expected to meet.
- Understand the scope of your CUI environment:
- Make a network diagram and data flow diagram
- Leverage the scoping guide to identify what is in scope: https://www.unified-scoping-guide.com/
- Based on finalizing your policies and standards, start working through the “low hanging fruit” in the SSP since those are the items already known and can be documented. The SSP is a living document so add to it as you work through requirements.
- From a procedural perspective, you have to identify the stakeholders and work with them to document their procedures.
- The CSOP serves as the “buffet table” for those stakeholders to cut & paste procedure templates for the controls they are responsible for so they have a defined starting point to document how they implement control.
- Stakeholders are the subject matter experts and only they know how the processes function and they are the ones who need to document the procedures.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the NCP! |
|
|
The NIST 800-171 Compliance Program (NCP) Is Built On Industry-Leading Practices & Definitions
|
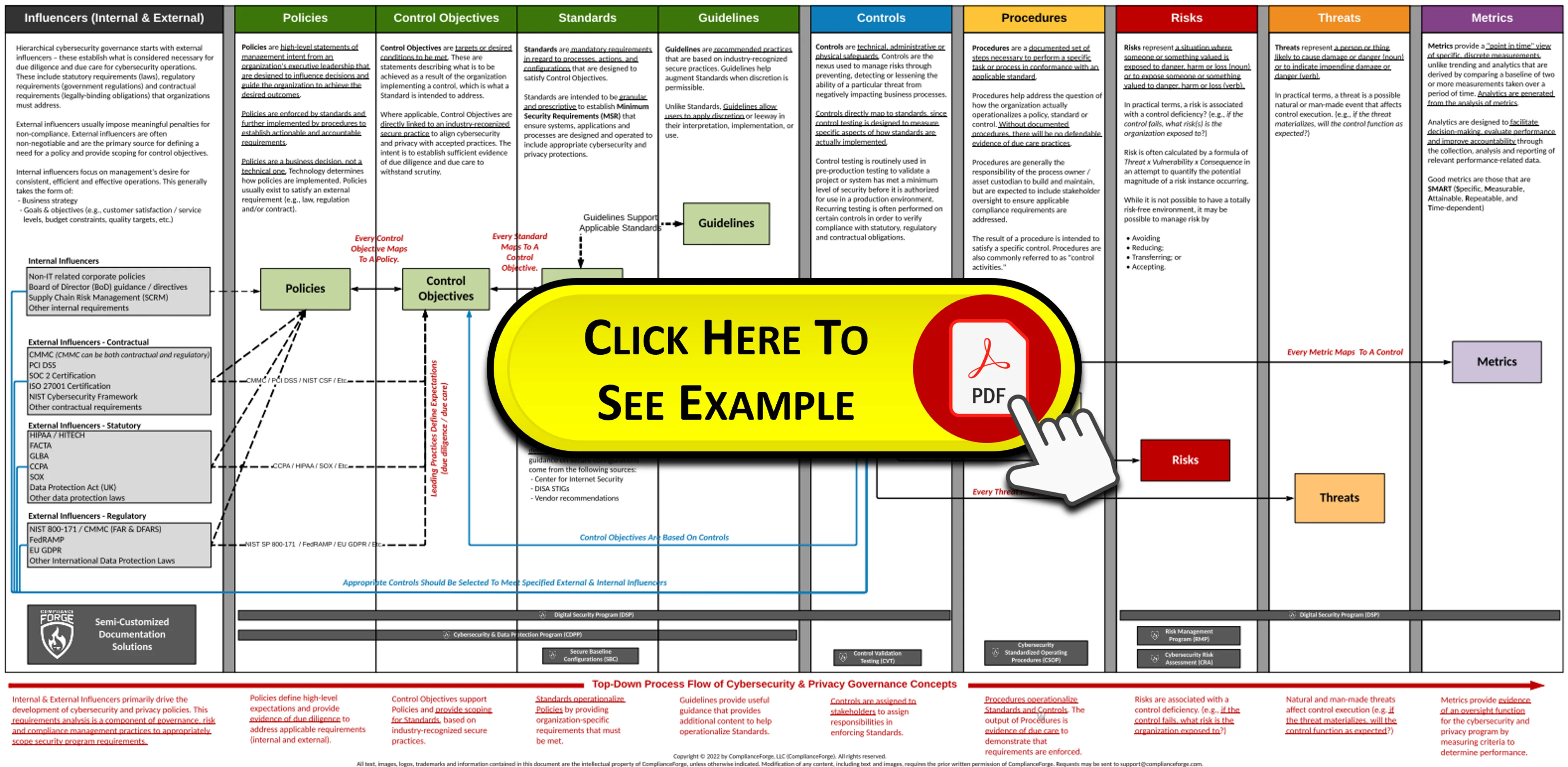
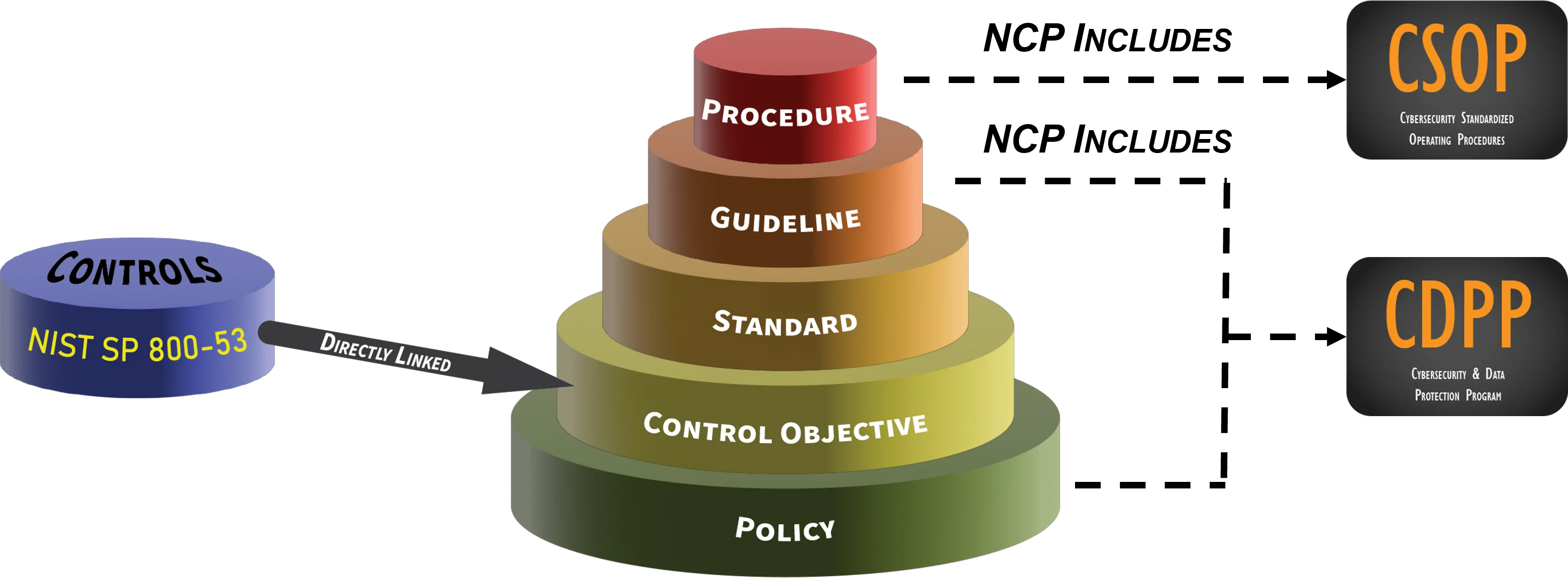
We recognize there are other options on the market for "NIST 800-171 & CMMC documentation" and we strive to make the highest-quality products on the market. Our obsession with making quality documentation can be demonstrated in the architecture we use to create our documentation. As shown in the swimlane diagram below, the Hierarchical Cybersecurity Governance Framework (HCGF) is the "ComplianceForge Reference Model" of cybersecurity and privacy documentation. The HCGF is a documentation model that leverages industry-recognized terminology to logically arrange these documentation components into their rightful order. This model creates an approach to architecting documentation that is concise, scalable and comprehensive. When that is all laid out properly, an organization's cybersecurity and data protection documentation should be hierarchical and linked from policies all the way through metrics. |
|
Does the NCP Include Coverage For Both NIST 800-171 Rev2 & Rev3?
Yes. The NCP comes with three (3) different versions to meet the current and future needs of our clients (all included with the purchase of the NCP):
- NCP R2 is tailored for organizations that want to focus entirely on only NIST SP 800-171 R2.
- NCP R3 is tailored for organizations that want to focus entirely on only NIST SP 800-171 R3.
- NCP Combined R2 & R3 is tailored for organizations that want to address both NIST SP 800-171 R2 & R3
The latest version of the NCP is focused on addressing changes associated with the recent release of 32 CFR Part 170 and updated CMMC 2.0 L2 scoping guidance. The biggest issue with 32 CFR Part 170 is the DoD cites NIST SP 800-171 R2 in this final rule, even though NIST SP 800-171 R3 was released earlier this year and per OMB NIST 800-171 R2 will be considered a deprecated standard in May 2025. The DoD’s reason for focusing on the old version of NIST SP 800-171 includes the time needed:
- For industry preparation to implement; and
- To prepare the CMMC ecosystem to perform assessments against the new version.
Does The NCP Help Clients Comply With NIST 800-171 R3?
Yes. The NCP has complete coverage for NIST 800-171 R3 and NIST 800-171A R3.
|
|
|
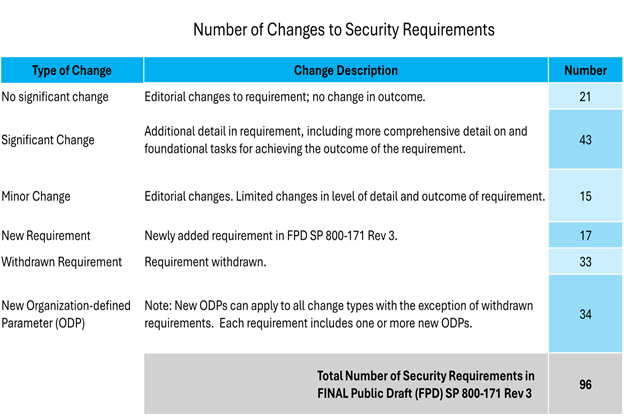
NIST 800 171 Rev 3 was released on 14 May 2024 and it contains significant changes from the NIST 800-171 Rev 2. As stated by Ron Ross from NIST, the official government requirements from the Office of Management and Budget (OMB) requires organizations to adopt the most current version of NIST one year after its release. From a NIST 800-171 perspective, this means NIST 800-171 Rev3 will be used for contracts going forward and at that time NIST 800-171 Rev 2 will be deprecated (outdated). Therefore, it is essential for businesses to start now to implement required controls to comply with NIST 800-171 Rev 3. Seeing is believing when you look at the differences between NIST 800-171 R2 and R3. The new content in R3 is expected to be a heavy lift by many in the Defense Industrial Base (DIB), but ComplianceForge's NIST 800-171 Compliance Program (NCP) is an affordable and editable collection documentation templates that can help ease the transition to R3. |
|
The following graphic to the right is a summarized version of the differences between NIST 800-171 Rev 2, NIST 800-171A, NIST 800-171 Rev 3 and CMMC 2.0. Please click the graphic to view an extended version of all the differences that the NCP covers. The latest version of the NCP has "backwards compatibility” for NIST 800-171 R2 & CMMC 2.0. The current version of the NCP covers both NIST 800-171 R3 and NIST 800-171 R2 (including CMMC 2.0) and this means you have the ability to:
|
|
What makes the NCP great is that it saves you time and money! The NCP was designed to make it less painful to upgrade to the latest version of NIST 800-171. One of its key features of the NCP is that it is backwards compatible with NIST 800-171 Rev 2, in addition to providing coverage for NIST 800-171 Rev 3. This is beneficial, since you can demonstrate coverage for the current version of NIST 800-171 (Rev 2), while you implement the new controls from NIST 800-171 Rev 3.
Does The NCP Provide Coverage For NIST 800-171 Rev 3 Organization-Defined Parameters (ODP)?
Yes. The NCP provides coverage for DoD-provided OPD criteria for NIST 800-171 Rev 3. The NIST 800-171 Rev 3 version of the NCP's standards and procedures are updated to provide the ODP criteria.
“DIBCAC Battle Tested” Policies, Standards & Procedures - NIST 800-171, NIST 800-171A & CMMC 2.0 Compliance
ComplianceForge’s NIST 800-171 / CMMC documentation has been used successfully by multiple companies during DIBCAC assessments to efficiently and effectively generate the necessary artifact documentation to demonstrate compliance with NIST 800-171 controls and NIST 800-171A control objectives. This battle tested documentation includes the necessary policies, standards, procedures, SSP, POA&M, Incident Response Plan (IRP) and other documentation that are expected to exist to successfully pass a third-party assessment, be it DIBCAC or a C3PAO.
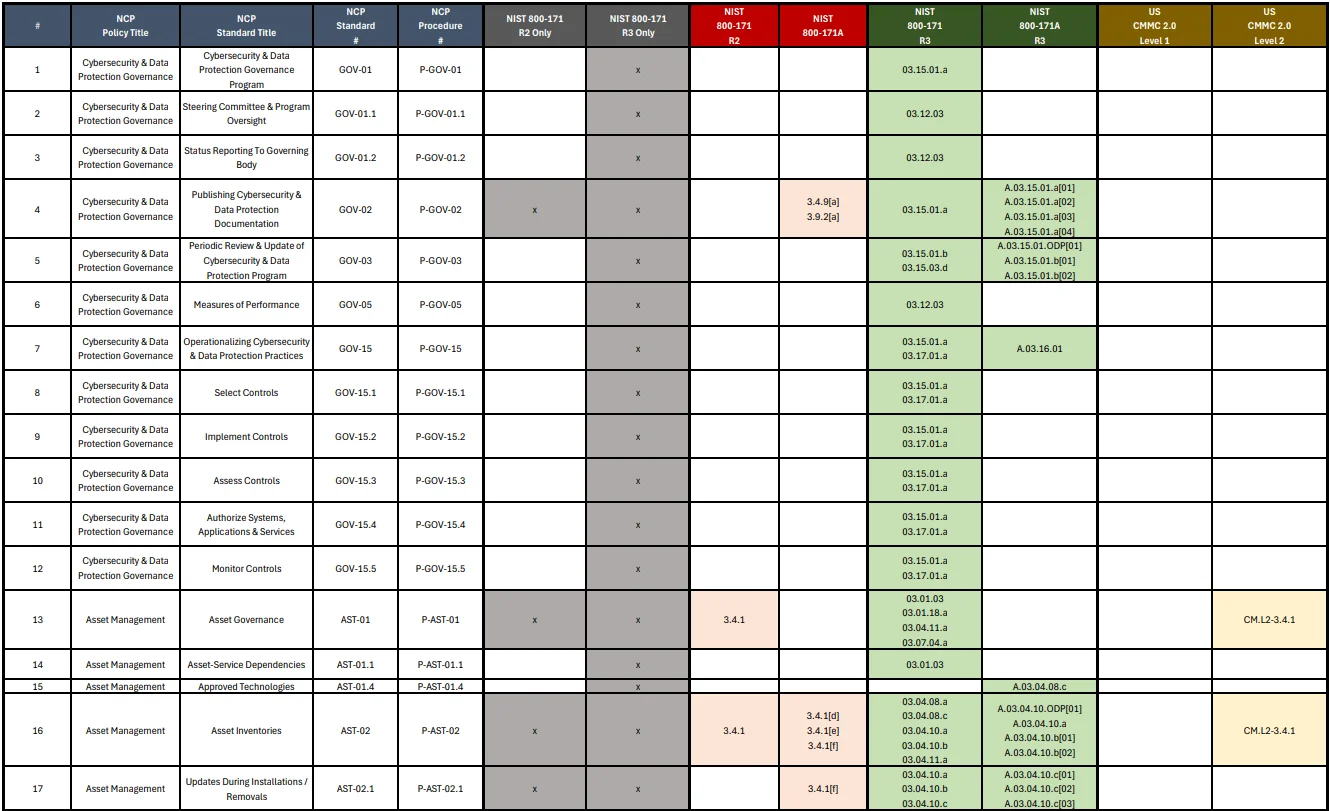
The Excel crosswalk spreadsheet that comes with the NCP maps the standards to the controls and Assessment Objectives (AOs), so it is straightforward to understand why a requirement in the NCP exists.
NIST 800-171 R2 / R3 & CMMC 2.0 Level 2 (Advanced) Policies, Standards, Procedures, SSP & POA&M Templates and More!
In simple terms, the NCP gives you everything you need to comply with NIST 800-171 & CMMC v2.0 - cybersecurity policies, standards, procedures, a System Security Plan (SSP) and a Plan of Action & Milestones (POA&M). As depicted in the graphic below, the NCP is its own bundle of products that makes up the documentation you need to demonstrate compliance with NIST 800-171 and CMMC:
Frequently Asked Questions (FAQs) On The NCP
Below are some common questions that we receive about the NCP so we decided to help provide further transparency to help with your purchasing decision:
- How does the NCP address CMMC v2.0 Level 2 (Advanced)?
- The NCP was specifically written to address all NFO & CUI controls in NIST 800-171 R2, as well as CMMC v2.0 Level 2 (Advanced) controls. The NCP is our "easy button" solution for CMMC 2.0 L2.
- The NCP contains editable policies, standards, procedures, SSP & POA&M templates, and much more. Continue reading to the "What Does The NIST 800-171 Compliance Program (NCP) Contain?" section about all that the NCP contains.
- How is the NCP different from CMMC Bundle #2?
- CMMC Bundle #2 is similar to the NIST 800-171 Compliance Program (NCP), in that both products cover CMMC 2.0 levels 1-2. Both equally cover CMMC 2.0 1-2 and NIST 800-171 requirements. However, the main differences are in coverage and framework alignment.
- The NCP is a pared-down version of the Digital Security Program (DSP), our flagship product. The NCP is tailored to be a "square peg for a square hole" to address only CMMC 2.0 L1-2 and NIST 800-171 requirements in the most efficient manner we can provide.
- CMMC Bundle #2 is based on the NIST 800-53 R5 framework, so it is great if you need to "speak NIST 800-53" or have other US government-based requirements (e.g., FISMA, RMF, HIPAA, etc.) that are based on NIST 800-53. This bundle is aligned with NIST 800-53 (low & moderate baseline coverage) so that is ideal for an organization that wants to align its policies and standards directly with NIST 800-53.
- If you are just looking for CMMC & NIST 800-171 coverage, then the NCP is a better fit.
- Why does the NCP leverage Secure Controls Framework (SCF) controls?
- The hierarchical and scalable structure of the Secure Controls Framework (SCF) makes it an ideal choice to address NIST 800-171 / CMMC compliance, so that is why the NCP leverages this structure.
- The SCF is a “metaframework” that maps to over 100 cybersecurity and privacy-related laws, regulations and frameworks, including NIST CSF, ISO 27001/2, NIST 800-53, NIST 800-171 and CMMC. The SCF is logically organized into thirty-three (33) domains. ComplianceForge’s Digital Security Program (DSP) has 1-1 mapping to the SCF and the NCP is merely a pared-down version of the DSP to focus specifically on the CUI and NFO controls from NIST 800-171, AOs from NIST 800-171 and CMMC 2.0 controls.
- The NIST OLIR Program will has SCF to NIST 800-171 R2 mappings, so that is another benefit to leveraging the SCF to structure the NCP’s policies, standards and procedures. You can read more about that here - https://csrc.nist.gov/projects/olir/informative-reference-catalog/details?frameworkVersionId=87
- Can you provide us with examples of the documentation & templates that are part of the NCP?
- Yes! If you scroll about 1/3 down the NCP product page, you will see the “Product Example - NIST 800-171 Compliance Criteria (NCP)” that contains examples of policies, standards, procedures, etc.
- What are the gaps in the NCP for CMMC 2.0 Level 2 once we purchase this?
- The NCP provides fully-mapped requirements within the policies, standards, procedures, etc. Therefore, any "gaps" in coverage are specific to your implementation of the requirements to become compliant with NIST 800-171 & CMMC.
- We are "tool makers" that provide you with templates that identify the Minimum Security Requirements (MSR) in an editable, efficient template format. You have to implement those requirements to be considered compliant with NIST 800-171 & CMMC.
- There are no professional service hours included in the purchase of the NCP, but we do have consultants that are available for customization/consulting via a separate Statement of Work (SOW).
- How often is the NCP updated?
- As NIST 800-171 & CMMC change, we update the NCP. There is no set schedule for updates, since we update products based on new guidance from the DoD, NIST and CMMC-AB.
- The NCP comes with one-year of updates, so as long as you have an active subscription you will receive updated versions of the documentation, along with errata that identifies what changed.
- After the first year, you can purchase updates for $900/yr, as described on our updates page.
- Is the NCP a subscription? How long does a license last?
- The NCP is perpetual and a single-site license. However, if you want to keep getting updates, you just have to pay for updates after the first year.
- NIST 800-171 & CMMC evolve, so that is why we offer updates. It takes considerable effort for us to develop and maintain this documentation, so that is why we charge for updates.
- Can I upgrade to a different bundle if my needs change?
- Yes! We can credit your purchase towards an upgraded bundle if your business needs change and you have to address CMMC 2.0 L3 requirements.
Product Example - NIST 800-171 Compliance Program (NCP)
Our customers choose the NIST 800-171 Compliance Program (NCP) because they:
- Need an efficient way to comply with NIST 800-171 / CMMC and make the process as simple as possible
- Need to be able to edit the document to their specific needs
- Need an affordable solution
Don't take our word for it - take a look at the examples below to see for yourself the level of professionalism and detail that went into making these products:
Cost Savings Estimate - NIST 800-171 Compliance Program (NCP)
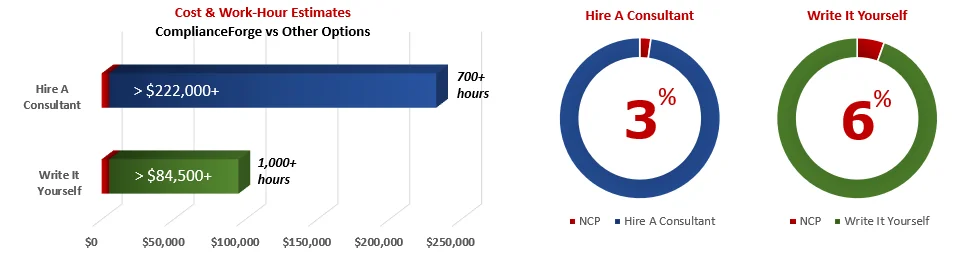
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the NCP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 1,000 internal staff work hours, which equates to a cost of approximately $90,000 in staff-related expenses. This is about 9-18 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 700 consultant work hours, which equates to a cost of approximately $227,500. This is about 4-12 months of development time for a contractor to provide you with the deliverable.
- The NCP is approximately 3% of the cost for a consultant or 6% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the NCP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
What Is Included With The NCP?
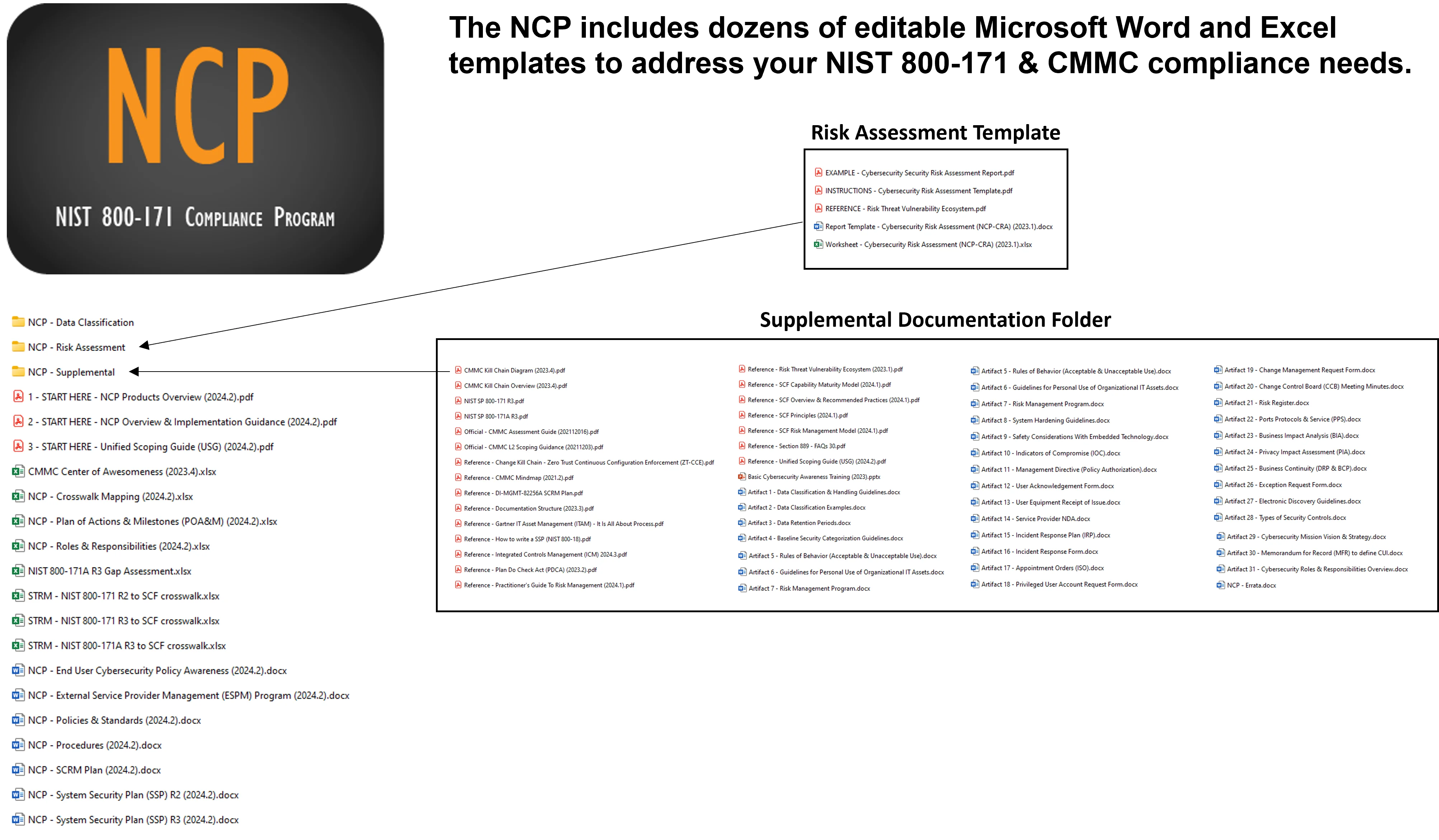
What Does The NIST 800-171 Compliance Program (NCP) Contain?
The NCP is architected so that each of the policies shown below are supported by granular standards that directly map to NIST 800-171 R2 & R3, as well as CMMC 2.0 requirements:
- Cybersecurity & Data Privacy Governance (GOV) Policy
- Asset Management (AST) Policy
- Business Continuity & Disaster Recovery (BCD) Policy
- Change Management (CHG) Policy
- Cloud Security (CLD) Policy
- Compliance (CPL) Policy
- Configuration Management (CFG) Policy
- Continuous Monitoring (MON) Policy
- Cryptographic Protections (CRY) Policy
- Data Classification & Handling (DCH) Policy
- Endpoint Security (END) Policy
- Human Resources Security (HRS) Policy
- Identification & Authentication (IAC) Policy
- Incident Response (IRO) Policy
- Information Assurance (IAO) Policy
- Maintenance (MNT) Policy
- Mobile Device Management (MDM) Policy
- Network Security (NET) Policy
- Physical & Environmental Security (PES) Policy
- Project & Resource Management (PRM) Policy
- Risk Management (RSK) Policy
- Secure Engineering & Architecture (SEA) Policy
- Security Operations (OPS) Policy
- Security Awareness & Training (SAT) Policy
- Technology Development & Acquisition (TDA) Policy
- Third-Party Management (TPM) Policy
- Threat Management (THR) Policy
- Vulnerability & Patch Management (VPM) Policy
The NIST 800-171 R2/R3 version of the NCP comes with the following policies, standards and procedures that map directly to the NIST 800-171 R2 & R3 controls and Assessment Objectives (AOs), as well as CMMC 2.0 controls. You can download this crosswalk mapping spreadsheet here.
| # | NCP Policy Title |
NCP Standard Title |
NCP Standard # |
NIST Controls |
NIST Assessment Objectives (AOs) |
NIST Controls |
NIST Assessment Objectives (AOs) |
| 1 | Cybersecurity & Data Protection Governance | Cybersecurity & Data Protection Governance Program | GOV-01 | 03.15.01.a | |||
| 2 | Cybersecurity & Data Protection Governance | Steering Committee & Program Oversight | GOV-01.1 | 03.12.03 | |||
| 3 | Cybersecurity & Data Protection Governance | Status Reporting To Governing Body | GOV-01.2 | 03.12.03 | |||
| 4 | Cybersecurity & Data Protection Governance | Publishing Cybersecurity & Data Protection Documentation | GOV-02 | 3.4.9[a] 3.9.2[a] |
03.15.01.a | A.03.15.01.a[01] A.03.15.01.a[02] A.03.15.01.a[03] A.03.15.01.a[04] |
|
| 5 | Cybersecurity & Data Protection Governance | Periodic Review & Update of Cybersecurity & Data Protection Program | GOV-03 | 03.15.01.b 03.15.03.d |
A.03.15.01.ODP[01] A.03.15.01.b[01] A.03.15.01.b[02] |
||
| 6 | Cybersecurity & Data Protection Governance | Measures of Performance | GOV-05 | 03.12.03 | |||
| 7 | Cybersecurity & Data Protection Governance | Operationalizing Cybersecurity & Data Protection Practices | GOV-15 | 03.15.01.a 03.17.01.a |
A.03.16.01 | ||
| 8 | Cybersecurity & Data Protection Governance | Select Controls | GOV-15.1 | 03.15.01.a 03.17.01.a |
|||
| 9 | Cybersecurity & Data Protection Governance | Implement Controls | GOV-15.2 | 03.15.01.a 03.17.01.a |
|||
| 10 | Cybersecurity & Data Protection Governance | Assess Controls | GOV-15.3 | 03.15.01.a 03.17.01.a |
|||
| 11 | Cybersecurity & Data Protection Governance | Authorize Systems, Applications & Services | GOV-15.4 | 03.15.01.a 03.17.01.a |
|||
| 12 | Cybersecurity & Data Protection Governance | Monitor Controls | GOV-15.5 | 03.15.01.a 03.17.01.a |
|||
| 13 | Asset Management | Asset Governance | AST-01 | 3.4.1 | 03.01.03 03.01.18.a 03.04.11.a 03.07.04.a |
||
| 14 | Asset Management | Asset-Service Dependencies | AST-01.1 | 03.01.03 | |||
| 15 | Asset Management | Approved Technologies | AST-01.4 | A.03.04.08.c | |||
| 16 | Asset Management | Asset Inventories | AST-02 | 3.4.1 | 3.4.1[d] 3.4.1[e] 3.4.1[f] |
03.04.08.a 03.04.08.c 03.04.10.a 03.04.10.b 03.04.11.a |
A.03.04.10.ODP[01] A.03.04.10.a A.03.04.10.b[01] A.03.04.10.b[02] |
| 17 | Asset Management | Updates During Installations / Removals | AST-02.1 | 3.4.1[f] | 03.04.10.a 03.04.10.b 03.04.10.c |
A.03.04.10.c[01] A.03.04.10.c[02] A.03.04.10.c[03] |
|
| 18 | Asset Management | Component Duplication Avoidance | AST-02.3 | NFO - CM-8(5) | |||
| 19 | Asset Management | Approved Baseline Deviations | AST-02.4 | 03.04.02.b 03.04.06.a |
|||
| 20 | Asset Management | Data Action Mapping | AST-02.8 | 03.04.11.a 03.04.11.b |
A.03.04.11.a[01] A.03.04.11.a[02] A.03.04.11.a[03] A.03.04.11.b[01] A.03.04.11.b[02] |
||
| 21 | Asset Management | Configuration Management Database (CMDB) | AST-02.9 | 03.04.08.a 03.04.10.a 03.04.10.b 03.04.10.c |
|||
| 22 | Asset Management | Asset Ownership Assignment | AST-03 | 03.09.02.a.03 | |||
| 23 | Asset Management | Accountability Information | AST-03.1 | 03.09.02.a.03 | |||
| 24 | Asset Management | Network Diagrams & Data Flow Diagrams (DFDs) | AST-04 | 03.01.03 03.04.11.a 03.04.11.b |
|||
| 25 | Asset Management | Asset Scope Classification | AST-04.1 | 03.04.11.a 03.04.11.b |
|||
| 26 | Asset Management | Control Applicability Boundary Graphical Representation | AST-04.2 | 03.04.11.a 03.04.11.b 03.15.02.a.04 |
|||
| 27 | Asset Management | Compliance-Specific Asset Identification | AST-04.3 | 03.01.03 | |||
| 28 | Asset Management | Security of Assets & Media | AST-05 | NFO - MP-1 | 03.07.04.a | ||
| 29 | Asset Management | Secure Disposal, Destruction or Re-Use of Equipment | AST-09 | 03.07.04.c 03.08.03 |
|||
| 30 | Asset Management | Return of Assets | AST-10 | 03.09.02.a.03 | A.03.09.02.a.03 | ||
| 31 | Asset Management | Use of Personal Devices | AST-12 | 03.01.18.a | |||
| 32 | Asset Management | Use of Third-Party Devices | AST-13 | 03.01.18.a | |||
| 33 | Asset Management | Usage Parameters | AST-14 | 03.01.18.a | |||
| 34 | Asset Management | Bring Your Own Device (BYOD) Usage | AST-16 | 03.01.18.a | |||
| 35 | Asset Management | Prohibited Equipment & Services | AST-17 | 03.11.01.a 03.16.01 |
|||
| 36 | Asset Management | Travel-Only Devices | AST-24 | 03.04.12.a 03.04.12.b |
A.03.04.12.a | ||
| 37 | Asset Management | Re-Imaging Devices After Travel | AST-25 | 03.04.12.b | A.03.04.12.b | ||
| 38 | Asset Management | Jump Server | AST-27 | 03.01.12.a 03.01.12.c |
|||
| 39 | Asset Management | Asset Categorization | AST-31 | 03.01.03 | |||
| 40 | Business Continuity & Disaster Recovery | Data Backups | BCD-11 | 3.8.9 | 3.8.9 | 03.08.09.a | |
| 41 | Business Continuity & Disaster Recovery | Cryptographic Protection | BCD-11.4 | 3.8.9 | 3.8.9 | 03.08.09.a 03.08.09.b |
A.03.08.09.a A.03.08.09.b |
| 42 | Change Management | Change Management Program | CHG-01 | 3.4.3 | 03.04.02.b 03.04.03.a |
A.03.04.03.d[01] A.03.04.03.d[02] |
|
| 43 | Change Management | Configuration Change Control | CHG-02 | 3.4.3 | 3.4.3[a] 3.4.3[b] 3.4.3[c] 3.4.3[d] |
03.04.02.b 03.04.03.a 03.04.03.b 03.04.03.c |
A.03.04.03.a A.03.04.03.c[01] |
| 44 | Change Management | Prohibition Of Changes | CHG-02.1 | 03.04.02.b 03.04.03.a |
A.03.04.03.b[02] A.03.04.05[05] |
||
| 45 | Change Management | Test, Validate & Document Changes | CHG-02.2 | NFO - CM-3(2) | 03.04.03.b 03.04.03.c 03.04.04.a 03.04.11.b |
A.03.04.03.c[02] | |
| 46 | Change Management | Cybersecurity & Data Privacy Representative for Asset Lifecycle Changes | CHG-02.3 | 03.04.04.a | |||
| 47 | Change Management | Security Impact Analysis for Changes | CHG-03 | 3.4.4 | 3.4.4 | 03.04.03.b 03.04.04.a 03.04.11.b |
A.03.04.03.b[01] A.03.04.04.a |
| 48 | Change Management | Access Restriction For Change | CHG-04 | 3.4.5 | 3.4.5[a] 3.4.5[b] 3.4.5[c] 3.4.5[d] 3.4.5[e] 3.4.5[f] 3.4.5[g] 3.4.5[h] |
03.04.02.b 03.04.05 |
|
| 49 | Change Management | Permissions To Implement Changes | CHG-04.4 | 03.04.05 | A.03.04.05[06] | ||
| 50 | Change Management | Stakeholder Notification of Changes | CHG-05 | NFO - CM-9 | 03.04.11.b | A.03.04.11.b[01] A.03.04.11.b[02] |
|
| 51 | Change Management | Control Functionality Verification | CHG-06 | 03.04.04.b | A.03.04.04.b | ||
| 52 | Cloud Security | Cloud Services | CLD-01 | NFO – PL-8 | |||
| 53 | Cloud Security | Cloud Security Architecture | CLD-02 | NFO – PL-8 | |||
| 54 | Cloud Security | Cloud Infrastructure Security Subnet | CLD-03 | 3.13.2 NFO – PL-8 |
|||
| 55 | Compliance | Statutory, Regulatory & Contractual Compliance | CPL-01 | NFO - PL-1 | 03.04.11.a 03.12.01 |
||
| 56 | Compliance | Non-Compliance Oversight | CPL-01.1 | 03.12.02.a.01 | |||
| 57 | Compliance | Compliance Scope | CPL-01.2 | 03.04.11.a 03.15.02.a.04 |
|||
| 58 | Compliance | Cybersecurity & Data Protection Controls Oversight | CPL-02 | 3.12.1 3.12.3 |
3.12.1[a] 3.12.1[b] 3.12.3 |
03.12.01 03.12.03 |
A.03.12.03[01] A.03.12.03[03] A.03.12.03[04] |
| 59 | Compliance | Internal Audit Function | CPL-02.1 | 3.12.1 | 03.12.01 | A.03.12.01.ODP[01] | |
| 60 | Compliance | Cybersecurity & Data Protection Assessments | CPL-03 | 3.12.1 | 03.12.01 03.12.03 |
A.03.12.01 | |
| 61 | Compliance | Independent Assessors | CPL-03.1 | NFO - CA-7(1) | |||
| 62 | Compliance | Functional Review Of Cybersecurity & Data Protection Controls | CPL-03.2 | 03.04.08.c 03.12.03 |
A.03.12.03[02] | ||
| 63 | Configuration Management | Configuration Management Program | CFG-01 | NFO - CM-1 NFO - CM-9 |
03.04.01.a | A.03.04.03.a | |
| 64 | Configuration Management | System Hardening Through Baseline Configurations | CFG-02 | 3.4.1 3.4.2 |
3.4.1[a] 3.4.1[b] 3.4.1[c] 3.4.2[a] 3.4.2[b] |
03.01.01.h 03.01.08.a 03.01.08.b 03.01.09 03.01.10.a 03.01.10.b 03.01.10.c 03.01.11 03.01.12.a 03.01.16.a 03.01.18.a 03.04.01.a 03.04.02.a 03.04.06.a 03.04.06.b 03.04.06.d 03.05.07.d 03.05.07.e 03.05.07.f 03.05.12.d 03.08.07.a 03.13.12.b |
A.03.01.03[01] A.03.01.16.a[03] A.03.01.16.c A.03.01.18.a[02] A.03.03.08.a[02] A.03.04.01.a[01] A.03.04.01.a[02] A.03.04.02.a[01] A.03.04.02.a[02] A.03.04.06.ODP[01] A.03.04.06.ODP[02] A.03.04.06.ODP[03] A.03.04.06.ODP[04] A.03.04.06.ODP[05] A.03.04.06.b[01] A.03.04.06.b[02] A.03.04.06.b[03] A.03.04.06.b[04] A.03.04.06.b[05] A.03.05.04[01] A.03.05.04[02] A.03.05.07.c A.03.05.07.d A.03.05.07.e A.03.05.07.f A.03.07.05.b[02] |
| 65 | Configuration Management | Reviews & Updates | CFG-02.1 | NFO - CM-2(1) | 03.04.01.b 03.04.02.b |
A.03.04.01.ODP[01] A.03.04.01.b[01] A.03.04.01.b[02] A.03.04.01.b[03] A.03.04.01.b[04] A.03.04.06.c |
|
| 66 | Configuration Management | Automated Central Management & Verification | CFG-02.2 | 03.04.02.b 03.04.03.d |
A.03.04.03.d[01] A.03.04.03.d[02] |
||
| 67 | Configuration Management | Configure Systems, Components or Services for High-Risk Areas | CFG-02.5 | NFO - CM-2(7) | 03.04.01.a 03.04.02.a 03.04.06.a 03.04.06.b 03.04.06.d 03.04.12.a |
A.03.04.12.ODP[01] A.03.04.12.ODP[02] |
|
| 68 | Configuration Management | Approved Configuration Deviations | CFG-02.7 | 03.04.01.a 03.04.02.b |
A.03.04.02.b[01] A.03.04.02.b[02] |
||
| 69 | Configuration Management | Baseline Tailoring | CFG-02.9 | 03.03.02.b 03.04.01.a 03.04.02.a 03.04.02.b 03.04.06.a 03.04.08.a 03.04.12.a 03.13.11 |
A.03.03.02.b | ||
| 70 | Configuration Management | Least Functionality | CFG-03 | 3.4.6 | 3.4.6[a] 3.4.6[b] |
03.04.02.a 03.04.06.a 03.04.06.b 03.04.06.d 03.04.08.a |
A.03.04.02.ODP[01] A.03.04.06.d |
| 71 | Configuration Management | Periodic Review | CFG-03.1 | 3.4.7 | 3.4.7[a] 3.4.7[b] 3.4.7[c] 3.4.7[d] 3.4.7[e] 3.4.7[f] 3.4.7[g] 3.4.7[h] 3.4.7[i] 3.4.7[j] 3.4.7[k] 3.4.7[l] 3.4.7[m] 3.4.7[n] 3.4.7[o] |
03.04.06.c 03.04.08.c |
A.03.04.06.ODP[06] |
| 72 | Configuration Management | Prevent Unauthorized Software Execution | CFG-03.2 | 3.4.7 | 03.04.08.b | ||
| 73 | Configuration Management | Explicitly Allow / Deny Applications | CFG-03.3 | 3.4.8 | 3.4.8[a] 3.4.8[b] 3.4.8[c] |
03.04.08.a 03.04.08.b 03.13.13.a 03.13.13.b |
A.03.04.08.ODP[01] A.03.04.08.a A.03.04.08.b A.03.13.13.b[03] |
| 74 | Configuration Management | Split Tunneling | CFG-03.4 | 3.13.7 | 3.13.7 | ||
| 75 | Configuration Management | Software Usage Restrictions | CFG-04 | 03.13.13.b | |||
| 76 | Configuration Management | Open Source Software | CFG-04.1 | 03.13.13.b | |||
| 77 | Configuration Management | User-Installed Software | CFG-05 | 3.4.9 | 3.4.9[b] 3.4.9[c] |
03.13.13.b | |
| 78 | Configuration Management | Configuration Enforcement | CFG-06 | 03.04.02.a 03.04.02.b 03.04.03.a |
|||
| 79 | Configuration Management | Sensitive / Regulated Data Access Enforcement | CFG-08 | 03.01.02 | A.03.01.02[01] | ||
| 80 | Continuous Monitoring | Continuous Monitoring | MON-01 | NFO - AU-1 | 03.03.01.a 03.12.03 03.14.06.a |
A.03.14.06.a.01[01] A.03.14.06.a.01[02] A.03.14.06.a.02 |
|
| 81 | Continuous Monitoring | Intrusion Detection & Prevention Systems (IDS & IPS) | MON-01.1 | 03.13.01.a | |||
| 82 | Continuous Monitoring | Inbound & Outbound Communications Traffic | MON-01.3 | 3.14.6 | 3.14.6[a] 3.14.6[b] 3.14.6[c] |
03.13.01.a 03.14.06.c |
A.03.13.01.a[01] A.03.13.01.a[03] A.03.14.06.c[01] A.03.14.06.c[02] |
| 83 | Continuous Monitoring | System Generated Alerts | MON-01.4 | NFO - SI-4(5) | 03.03.01.a 03.03.03.a 03.14.06.a.01 03.14.06.b 03.14.06.c |
A.03.03.02.a.01 A.03.03.03.a |
|
| 84 | Continuous Monitoring | Reviews & Updates | MON-01.8 | 3.3.3 3.14.3 |
3.3.3[a] 3.3.3[b] 3.3.3[c] 3.14.3[a] 3.14.3[b] 3.14.3[c] |
03.03.01.b 03.03.05.a |
A.03.03.01.ODP[02] A.03.03.01.b[01] A.03.03.05.ODP[01] A.03.03.05.a |
| 85 | Continuous Monitoring | Automated Alerts | MON-01.12 | 03.03.04.a 03.03.05.b |
A.03.03.05.b | ||
| 86 | Continuous Monitoring | Privileged User Oversight | MON-01.15 | 03.01.07.b | |||
| 87 | Continuous Monitoring | Centralized Collection of Security Event Logs | MON-02 | 3.3.1 3.3.3 3.3.5 3.3.6 3.3.8 3.3.9 |
03.03.05.a 03.03.05.c |
A.03.03.05.ODP[01] A.03.03.05.a A.03.03.05.c[01] |
|
| 88 | Continuous Monitoring | Correlate Monitoring Information | MON-02.1 | 3.3.5 3.14.7 |
3.3.5[a] 3.3.5[b] 3.14.7[a] 3.14.7[b] |
03.03.05.a 03.03.05.c |
A.03.03.05.c[02] |
| 89 | Continuous Monitoring | Central Review & Analysis | MON-02.2 | 03.03.01.b 03.03.05.a 03.03.05.c |
|||
| 90 | Continuous Monitoring | Integration of Scanning & Other Monitoring Information | MON-02.3 | 03.03.05.c | |||
| 91 | Continuous Monitoring | System-Wide / Time-Correlated Audit Trail | MON-02.7 | 03.03.01.a | |||
| 92 | Continuous Monitoring | Content of Event Logs | MON-03 | 3.3.2 | 3.3.1[a] 3.3.1[b] 3.3.1[d] 3.3.2[a] 3.3.2[b] |
03.03.01.a 03.03.02.a 03.03.02.a.01 03.03.02.a.02 03.03.02.a.03 03.03.02.a.04 03.03.02.a.05 03.03.02.a.06 03.03.02.b |
A.03.03.01.ODP[01] A.03.03.01.a A.03.03.01.b[02] A.03.03.02.a.02 A.03.03.02.a.03 A.03.03.02.a.04 A.03.03.02.a.05 A.03.03.02.a.06 A.03.03.02.b |
| 93 | Continuous Monitoring | Sensitive Audit Information | MON-03.1 | 3.3.8 | |||
| 94 | Continuous Monitoring | Audit Trails | MON-03.2 | 3.3.2[a] 3.3.1[c] |
03.03.01.a | ||
| 95 | Continuous Monitoring | Privileged Functions Logging | MON-03.3 | 03.01.07.b | A.03.01.07.b | ||
| 96 | Continuous Monitoring | Database Logging | MON-03.7 | 3.3.2[a] | |||
| 97 | Continuous Monitoring | Response To Event Log Processing Failures | MON-05 | 3.3.4 | 3.3.4[a] 3.3.4[b] 3.3.4[c] |
03.03.04.b | A.03.03.04.ODP[01] A.03.03.04.ODP[02] A.03.03.04.a A.03.03.04.b |
| 98 | Continuous Monitoring | Monitoring Reporting | MON-06 | 3.3.6 | 3.3.6[a] 3.3.6[b] |
03.03.05.b 03.03.06.a |
A.03.03.05.b A.03.03.06.a[01] A.03.03.06.a[02] A.03.03.06.a[03] A.03.03.06.a[04] |
| 99 | Continuous Monitoring | Time Stamps | MON-07 | 3.3.7[a] 3.3.7[b] |
03.03.02.a.02 03.03.07.a |
A.03.03.07.ODP[01] A.03.03.07.a A.03.03.07.b[01] |
|
| 100 | Continuous Monitoring | Synchronization With Authoritative Time Source | MON-07.1 | 3.3.7 | 3.3.7[b] 3.3.7[c] |
03.03.07.b | A.03.03.07.b[02] |
| 101 | Continuous Monitoring | Protection of Event Logs | MON-08 | 3.3.8 | 3.3.8[a] 3.3.8[b] 3.3.8[c] 3.3.8[d] 3.3.8[e] 3.3.8[f] |
03.03.03.b 03.03.06.b 03.03.08.a |
A.03.03.03.b A.03.03.06.b[01] A.03.03.06.b[02] A.03.03.08.a[01] A.03.03.08.b |
| 102 | Continuous Monitoring | Event Log Backup on Separate Physical Systems / Components | MON-08.1 | 03.03.08.a | |||
| 103 | Continuous Monitoring | Access by Subset of Privileged Users | MON-08.2 | 3.3.9 | 3.3.9[a] 3.3.9[b] |
03.03.08.a 03.03.08.b |
A.03.03.08.b |
| 104 | Continuous Monitoring | Cryptographic Protection of Event Log Information | MON-08.3 | 03.03.08.a | |||
| 105 | Continuous Monitoring | Event Log Retention | MON-10 | 3.3.1 | 3.3.1[e] 3.3.1[f] |
03.03.03.b | A.03.03.03.b |
| 106 | Continuous Monitoring | Monitoring For Information Disclosure | MON-11 | 03.01.22.b | |||
| 107 | Continuous Monitoring | Monitoring for Indicators of Compromise (IOC) | MON-11.3 | 03.14.06.a.01 03.14.06.a.02 03.14.06.b 03.14.06.c |
|||
| 108 | Continuous Monitoring | Anomalous Behavior | MON-16 | 03.01.01.e 03.03.05.a 03.14.06.a.01 03.14.06.a.02 03.14.06.b 03.14.06.c |
A.03.14.06.b | ||
| 109 | Cryptographic Protections | Use of Cryptographic Controls | CRY-01 | 3.13.11 | 3.13.8[a] 3.13.11 |
03.13.08 03.13.11 |
A.03.13.08[01] A.03.13.08[02] A.03.13.11 A.03.13.11.ODP[01] |
| 110 | Cryptographic Protections | Alternate Physical Protection | CRY-01.1 | 3.13.8 | 3.13.8[b] 3.13.8[c] |
03.13.08 | |
| 111 | Cryptographic Protections | Cryptographic Cipher Suites and Protocols Inventory | CRY-01.5 | 03.13.11 | |||
| 112 | Cryptographic Protections | Transmission Confidentiality | CRY-03 | 3.13.8 | 3.13.8[a] 3.13.11 |
03.13.08 | A.03.13.08[01] A.03.13.11 A.03.13.11.ODP[01] |
| 113 | Cryptographic Protections | Transmission Integrity | CRY-04 | NFO - SI-1 | |||
| 114 | Cryptographic Protections | Encrypting Data At Rest | CRY-05 | 3.8.6 | 3.8.6 | 03.13.08 | A.03.13.08[02] A.03.13.11 A.03.13.11.ODP[01] |
| 115 | Cryptographic Protections | Storage Media | CRY-05.1 | 03.13.08 | |||
| 116 | Cryptographic Protections | Wireless Access Authentication & Encryption | CRY-07 | 03.01.16.a | |||
| 117 | Cryptographic Protections | Public Key Infrastructure (PKI) | CRY-08 | 3.13.10 | 3.13.10[a] 3.13.10[b] |
03.13.10 | |
| 118 | Cryptographic Protections | Cryptographic Key Management | CRY-09 | 3.13.10 | 3.13.10[a] 3.13.10[b] |
03.13.10 | A.03.13.10.ODP[01] A.03.13.10[01] A.03.13.10[02] |
| 119 | Cryptographic Protections | Cryptographic Key Loss or Change | CRY-09.3 | 03.13.10 | |||
| 120 | Cryptographic Protections | Control & Distribution of Cryptographic Keys | CRY-09.4 | 03.13.10 | |||
| 121 | Data Classification & Handling | Data Protection | DCH-01 | 3.8.1 NFO - MP-1 |
3.8.1[a] 3.8.1[b] 3.8.1[c] 3.8.1[d] |
03.01.01.d.01 03.01.01.d.02 03.08.01 |
|
| 122 | Data Classification & Handling | Data Stewardship | DCH-01.1 | 03.08.01 03.08.05.a |
|||
| 123 | Data Classification & Handling | Sensitive / Regulated Data Protection | DCH-01.2 | 03.01.01.d.01 03.01.01.d.02 03.01.02 03.01.20.a 03.01.20.b 03.01.20.c.01 03.01.20.d 03.06.05.d 03.08.01 03.08.02 03.08.05.a 03.17.01.c |
|||
| 124 | Data Classification & Handling | Sensitive / Regulated Media Records | DCH-01.3 | 03.08.05.c | |||
| 125 | Data Classification & Handling | Defining Access Authorizations for Sensitive/Regulated Data | DCH-01.4 | 03.01.02 03.01.03 03.01.04.b 03.08.01 03.08.02 03.10.01.a 03.15.02.c 03.17.01.c |
A.03.15.02.c A.03.17.01.c |
||
| 126 | Data Classification & Handling | Data & Asset Classification | DCH-02 | 03.04.11.a 03.08.01 03.08.04 |
|||
| 127 | Data Classification & Handling | Media Access | DCH-03 | 3.1.3 3.8.2 |
3.1.3[c] 3.8.2 |
03.01.03 03.08.01 03.08.02 |
A.03.08.02 |
| 128 | Data Classification & Handling | Disclosure of Information | DCH-03.1 | 03.01.22.a 03.15.02.c 03.17.01.c |
A.03.15.02.c A.03.17.01.c |
||
| 129 | Data Classification & Handling | Media Marking | DCH-04 | 3.8.4 | 3.8.4[a] 3.8.4[b] |
03.08.04 | A.03.08.04[01] A.03.08.04[02] A.03.08.04[03] |
| 130 | Data Classification & Handling | Media Storage | DCH-06 | 3.8.1 | 03.08.01 | A.03.08.01[01] A.03.08.01[02] |
|
| 131 | Data Classification & Handling | Physically Secure All Media | DCH-06.1 | 03.08.01 | |||
| 132 | Data Classification & Handling | Sensitive Data Inventories | DCH-06.2 | 03.04.11.a 03.04.11.b |
|||
| 133 | Data Classification & Handling | Making Sensitive Data Unreadable In Storage | DCH-06.4 | 03.08.01 | |||
| 134 | Data Classification & Handling | Media Transportation | DCH-07 | 3.8.5 | 3.8.5[a] 3.8.5[b] |
03.08.05.a 03.08.05.b |
A.03.08.05.a[01] A.03.08.05.a[02] A.03.08.05.b A.03.08.05.c |
| 135 | Data Classification & Handling | Custodians | DCH-07.1 | 03.08.05.a 03.08.05.b |
|||
| 136 | Data Classification & Handling | Encrypting Data In Storage Media | DCH-07.2 | 03.08.05.a | |||
| 137 | Data Classification & Handling | Physical Media Disposal | DCH-08 | 03.08.03 | |||
| 138 | Data Classification & Handling | System Media Sanitization | DCH-09 | 3.7.3 3.8.3 |
3.7.3 3.8.3[a] 3.8.3[b] |
03.07.04.c 03.08.03 |
A.03.08.03 |
| 139 | Data Classification & Handling | Media Use | DCH-10 | 3.8.7 | 3.8.7 | 03.08.07.a | A.03.08.07.ODP[01] A.03.08.07.a |
| 140 | Data Classification & Handling | Prohibit Use Without Owner | DCH-10.2 | 3.8.8 | 3.8.8 | 03.08.07.b | A.03.08.07.b |
| 141 | Data Classification & Handling | Removable Media Security | DCH-12 | 03.08.07.a | |||
| 142 | Data Classification & Handling | Use of External Information Systems | DCH-13 | 3.1.20 | 3.1.20[a] 3.1.20[b] 3.1.20[c] 3.1.20[d] 3.1.20[e] 3.1.20[f] |
03.01.20.a 03.01.20.b 03.01.20.c.01 03.01.20.c.02 03.01.20.d |
A.03.01.20.ODP[01] A.03.01.20.a A.03.01.20.b A.03.01.20.c.01 A.03.01.20.c.02 |
| 143 | Data Classification & Handling | Limits of Authorized Use | DCH-13.1 | 3.1.20 | 03.01.20.a 03.01.20.b 03.01.20.c.01 03.01.20.c.02 03.01.20.d |
||
| 144 | Data Classification & Handling | Portable Storage Devices | DCH-13.2 | 3.1.21 | 3.1.21[a] 3.1.21[b] 3.1.21[c] |
03.01.20.a 03.01.20.d |
A.03.01.20.d |
| 145 | Data Classification & Handling | Protecting Sensitive Data on External Systems | DCH-13.3 | 03.01.20.b 03.01.20.c.01 |
|||
| 146 | Data Classification & Handling | Non-Organizationally Owned Systems / Components / Devices | DCH-13.4 | 03.01.20.a 03.01.20.c.01 03.01.20.d |
|||
| 147 | Data Classification & Handling | Transfer Authorizations | DCH-14.2 | 03.01.20.b 03.01.20.c.02 03.12.05.a |
|||
| 148 | Data Classification & Handling | Data Access Mapping | DCH-14.3 | 03.01.03 03.01.20.c.02 03.12.05.a |
|||
| 149 | Data Classification & Handling | Publicly Accessible Content | DCH-15 | 3.1.22 | 3.1.22[a] 3.1.22[b] 3.1.22[c] 3.1.22[d] 3.1.22[e] |
03.01.22.a 03.01.22.b |
A.03.01.22.a A.03.01.22.b[01] A.03.01.22.b[02] |
| 150 | Data Classification & Handling | Ad-Hoc Transfers | DCH-17 | 03.01.20.a | |||
| 151 | Data Classification & Handling | Media & Data Retention | DCH-18 | 03.01.20.c.02 03.14.08 |
A.03.14.08[01] A.03.14.08[02] A.03.14.08[03] A.03.14.08[04] |
||
| 152 | Data Classification & Handling | Geographic Location of Data | DCH-19 | 03.04.11.a 03.04.11.b |
|||
| 153 | Data Classification & Handling | Information Disposal | DCH-21 | 03.08.03 | |||
| 154 | Data Classification & Handling | Information Location | DCH-24 | A.03.04.11.a[01] | |||
| 155 | Endpoint Security | Endpoint Security | END-01 | 3.4.1[a] 3.4.1[b] 3.4.1[c] 3.4.2[a] 3.4.2[b] |
03.14.02.a | A.03.01.03[01] | |
| 156 | Endpoint Security | Endpoint Protection Measures | END-02 | 3.13.16 | 3.13.16 | ||
| 157 | Endpoint Security | Prohibit Installation Without Privileged Status | END-03 | 3.4.9 | |||
| 158 | Endpoint Security | Governing Access Restriction for Change | END-03.2 | 3.4.5[a] 3.4.5[b] 3.4.5[c] 3.4.5[d] 3.4.5[e] 3.4.5[f] 3.4.5[g] 3.4.5[h] |
|||
| 159 | Endpoint Security | Malicious Code Protection (Anti-Malware) | END-04 | 3.14.2 | 3.14.2[a] 3.14.2[b] 3.14.5[a] 3.14.5[b] 3.14.5[c] |
03.14.02.c 03.14.02.c.01 03.14.02.c.02 |
A.03.14.02.ODP[01] A.03.14.02.a[01] A.03.14.02.a[02] A.03.14.02.c.02 |
| 160 | Endpoint Security | Automatic Antimalware Signature Updates | END-04.1 | 3.14.4 | 3.14.4 | 03.14.02.b | A.03.14.02.b |
| 161 | Endpoint Security | Centralized Management of Antimalware Technologies | END-04.3 | 03.14.02.a | |||
| 162 | Endpoint Security | Always On Protection | END-04.7 | 3.14.5 | 3.14.5[c] | 03.14.02.a 03.14.02.c.01 03.14.02.c.02 |
A.03.14.02.c.01[01] A.03.14.02.c.01[02] |
| 163 | Endpoint Security | Host Intrusion Detection and Prevention Systems (HIDS / HIPS) | END-07 | 03.14.06.a.01 03.14.06.a.02 03.14.06.b 03.14.06.c |
|||
| 164 | Endpoint Security | Mobile Code | END-10 | 3.13.13 | 3.13.13[a] 3.13.13[b] |
03.13.13.a 03.13.13.b |
A.03.13.13.a[01] A.03.13.13.a[02] A.03.13.13.b[01] A.03.13.13.b[02] A.03.13.13.b[03] |
| 165 | Endpoint Security | Collaborative Computing Devices | END-14 | 3.13.12 | 3.13.12[a] 3.13.12[b] 3.13.12[c] |
03.13.12.a | A.03.13.12.ODP[01] A.03.13.12.a |
| 166 | Endpoint Security | Explicit Indication Of Use | END-14.6 | 03.13.12.b | A.03.13.12.b | ||
| 167 | Human Resources Security | Human Resources Security Management | HRS-01 | NFO - PS-1 | 3.2.2[a] 3.2.2[b] 3.2.2[c] 3.9.2[a] |
03.01.01.g.02 03.15.03.a 03.15.03.d |
A.03.01.01.ODP[01] A.03.01.01.ODP[02] A.03.01.01.ODP[03] A.03.01.01.ODP[04] |
| 168 | Human Resources Security | Position Categorization | HRS-02 | 03.01.01.c.01 03.01.01.c.02 03.01.01.d.01 03.01.01.d.02 03.01.02 03.09.01.a 03.09.01.b |
|||
| 169 | Human Resources Security | Users With Elevated Privileges | HRS-02.1 | 03.01.02 | |||
| 170 | Human Resources Security | Roles & Responsibilities | HRS-03 | 03.01.22.a 03.06.04.a 03.06.05.d 03.07.06.a 03.08.02 03.15.03.b 03.16.03.b |
A.03.06.05.d | ||
| 171 | Human Resources Security | User Awareness | HRS-03.1 | 03.01.22.a 03.15.03.b |
|||
| 172 | Human Resources Security | Competency Requirements for Security-Related Positions | HRS-03.2 | 03.07.06.d | |||
| 173 | Human Resources Security | Personnel Screening | HRS-04 | 3.9.1 | 3.9.1 | 03.09.01.a | A.03.09.01.ODP[01] A.03.09.01.a A.03.09.01.b |
| 174 | Human Resources Security | Roles With Special Protection Measures | HRS-04.1 | 03.01.22.a 03.02.02.a.01 03.09.01.a 03.09.01.b |
A.03.09.01.ODP[01] | ||
| 175 | Human Resources Security | Formal Indoctrination | HRS-04.2 | 03.01.22.a 03.02.02.a.01 03.06.04.a 03.06.04.a.01 03.15.03.b |
|||
| 176 | Human Resources Security | Terms of Employment | HRS-05 | NFO - PL-4 | 03.01.01.h 03.01.22.a 03.15.03.a |
A.03.15.03.b | |
| 177 | Human Resources Security | Rules of Behavior | HRS-05.1 | NFO - PL-4 | 03.01.12.a 03.01.18.a 03.01.22.a 03.15.03.a |
A.03.15.03.ODP[01] A.03.15.03.a A.03.15.03.d[01] A.03.15.03.d[02] |
|
| 178 | Human Resources Security | Social Media & Social Networking Restrictions | HRS-05.2 | NFO - PL-4(1) | 03.15.03.a | A.03.15.03.a | |
| 179 | Human Resources Security | Use of Communications Technology | HRS-05.3 | 03.01.01.h 03.01.12.a 03.01.18.a 03.15.03.a |
A.03.15.03.a | ||
| 180 | Human Resources Security | Use of Critical Technologies | HRS-05.4 | 03.15.03.a | |||
| 181 | Human Resources Security | Use of Mobile Devices | HRS-05.5 | 03.01.18.a 03.15.03.a |
A.03.15.03.a | ||
| 182 | Human Resources Security | Policy Familiarization & Acknowledgement | HRS-05.7 | 03.15.03.b 03.15.03.c 03.15.03.d |
A.03.15.03.c | ||
| 183 | Human Resources Security | Access Agreements | HRS-06 | NFO - PS-6 | 03.01.18.a 03.12.05.a 03.15.03.b 03.15.03.c |
||
| 184 | Human Resources Security | Confidentiality Agreements | HRS-06.1 | 03.12.05.a 03.15.03.c |
|||
| 185 | Human Resources Security | Personnel Sanctions | HRS-07 | NFO - PS-8 | 3.9.2[a] 3.9.2[b] 3.9.2[c] |
03.01.01.f.04 03.01.01.f.05 |
|
| 186 | Human Resources Security | Workplace Investigations | HRS-07.1 | 03.01.01.f.04 03.01.01.f.05 |
|||
| 187 | Human Resources Security | Personnel Transfer | HRS-08 | 3.9.2 | 3.9.2[a] 3.9.2[b] 3.9.2[c] |
03.01.01.g.02 03.09.02.a 03.09.02.b.01 |
A.03.09.02.ODP[01] A.03.09.02.b.01[01] A.03.09.02.b.01[02] A.03.09.02.b.02 |
| 188 | Human Resources Security | Personnel Termination | HRS-09 | 3.9.2 | 3.9.2[a] 3.9.2[b] 3.9.2[c] |
03.01.01.f.03 03.01.01.g.02 03.09.02.a 03.09.02.a.03 03.09.02.b.01 |
A.03.09.02.ODP[01] A.03.09.02.a.01 A.03.09.02.a.02[01] A.03.09.02.a.02[02] A.03.09.02.a.03 |
| 189 | Human Resources Security | Asset Collection | HRS-09.1 | 03.09.02.a.03 | A.03.09.02.a.03 | ||
| 190 | Human Resources Security | High-Risk Terminations | HRS-09.2 | 03.09.02.a.01 03.09.02.a.02 03.09.02.b.01 |
|||
| 191 | Human Resources Security | Automated Employment Status Notifications | HRS-09.4 | 03.01.01.g.02 03.09.02.a.01 03.09.02.a.02 |
|||
| 192 | Human Resources Security | Third-Party Personnel Security | HRS-10 | NFO - PS-7 | 03.16.03.b | ||
| 193 | Human Resources Security | Separation of Duties (SoD) | HRS-11 | 3.1.4 | 3.1.4[a] 3.1.4[b] 3.1.4[c] |
03.01.04.a | A.03.01.04.a |
| 194 | Human Resources Security | Incompatible Roles | HRS-12 | 03.01.04.a | |||
| 195 | Identification & Authentication | Identity & Access Management (IAM) | IAC-01 | NFO - AC-1 NFO- IA-1 |
03.01.01.a 03.01.18.b 03.05.01.a 03.05.05.a 03.05.12.e |
||
| 196 | Identification & Authentication | Authenticate, Authorize and Audit (AAA) | IAC-01.2 | 03.05.01.a 03.05.02 03.05.05.d 03.05.07.a 03.05.07.b 03.05.07.c 03.05.07.d 03.05.07.e 03.05.12.d 03.05.12.f 03.07.05.a |
A.03.01.01.d.01 A.03.01.01.d.02 A.03.01.16.b A.03.05.01.a[01] A.03.05.01.a[02] |
||
| 197 | Identification & Authentication | Identification & Authentication for Organizational Users | IAC-02 | 3.5.1 3.5.2 |
3.5.1[a] 3.5.1[b] 3.5.1[c] 3.5.2[a] 3.5.2[b] 3.5.2[c] |
03.05.01.a | A.03.05.01.a[03] |
| 198 | Identification & Authentication | Replay-Resistant Authentication | IAC-02.2 | 3.5.4 | 3.5.4 | 03.05.04 03.07.05.b |
A.03.05.04[01] A.03.05.04[02] A.03.07.05.b[02] |
| 199 | Identification & Authentication | Identification & Authentication for Non-Organizational Users | IAC-03 | 03.05.01.a | |||
| 200 | Identification & Authentication | Identification & Authentication for Devices | IAC-04 | 3.5.2 | 03.01.18.b 03.05.02 |
A.03.05.02.ODP[01] A.03.05.02[01] A.03.05.02[02] |
|
| 201 | Identification & Authentication | Identification & Authentication for Third Party Systems & Services | IAC-05 | 03.05.01.a 03.05.02 |
|||
| 202 | Identification & Authentication | Privileged Access by Non-Organizational Users | IAC-05.2 | 03.07.05.a | |||
| 203 | Identification & Authentication | Multi-Factor Authentication (MFA) | IAC-06 | 3.5.3 | 03.05.03 03.07.05.b |
A.03.05.03[01] A.03.05.03[02] A.03.07.05.b[01] |
|
| 204 | Identification & Authentication | Network Access to Privileged Accounts | IAC-06.1 | 3.5.3 | 3.5.3[a] 3.5.3[c] |
03.05.03 | |
| 205 | Identification & Authentication | Network Access to Non-Privileged Accounts | IAC-06.2 | 3.5.3 | 3.5.3[d] | 03.05.03 | |
| 206 | Identification & Authentication | Local Access to Privileged Accounts | IAC-06.3 | 3.5.3 | 3.5.3[a] 3.5.3[b] |
03.05.03 | |
| 207 | Identification & Authentication | Out-of-Band Multi-Factor Authentication | IAC-06.4 | A.03.05.03[01] A.03.05.03[02] |
|||
| 208 | Identification & Authentication | User Provisioning & De-Provisioning | IAC-07 | 03.01.01.g.01 03.01.01.g.02 03.01.01.g.03 03.05.05.a 03.09.02.a.01 03.09.02.a.02 |
A.03.01.01.b[01] A.03.01.01.b[02] A.03.01.01.b[03] A.03.01.01.b[04] A.03.01.01.b[05] A.03.05.05.a |
||
| 209 | Identification & Authentication | Change of Roles & Duties | IAC-07.1 | 03.01.01.g.01 03.01.01.g.02 03.01.01.g.03 03.05.05.a 03.09.02.b.02 |
|||
| 210 | Identification & Authentication | Termination of Employment | IAC-07.2 | 03.09.02.a.01 03.09.02.a.02 |
|||
| 211 | Identification & Authentication | Role-Based Access Control (RBAC) | IAC-08 | 3.1.1 3.1.3 |
3.1.3[c] | 03.01.01.c.01 03.01.01.c.02 03.01.01.c.03 03.01.02 03.01.05.b 03.01.06.a 03.01.12.a 03.03.08.b 03.04.05 03.06.05.d 03.07.06.a |
A.03.01.01.c.02 A.03.01.01.c.03 A.03.01.05.ODP[01] A.03.01.05.ODP[02] A.03.01.05.b[01] A.03.01.05.b[02] A.03.04.05[04] A.03.06.05.d |
| 212 | Identification & Authentication | Identifier Management (User Names) | IAC-09 | 3.5.5 | 3.5.5[a] 3.5.5[b] |
03.05.05.b 03.05.05.c 03.05.05.d |
A.03.05.05.ODP[01] A.03.05.05.b[01] A.03.05.05.b[02] A.03.05.05.c |
| 213 | Identification & Authentication | User Identity (ID) Management | IAC-09.1 | 03.05.05.b | |||
| 214 | Identification & Authentication | Identity User Status | IAC-09.2 | 03.05.05.d | A.03.05.05.ODP[02] A.03.05.05.d |
||
| 215 | Identification & Authentication | Privileged Account Identifiers | IAC-09.5 | 03.01.07.b 03.05.05.d |
|||
| 216 | Identification & Authentication | Authenticator Management | IAC-10 | 3.5.8 3.5.9 |
3.5.8[a] 3.5.8[b] 3.5.9 |
03.05.07.a 03.05.07.b 03.05.07.c 03.05.07.d 03.05.07.e 03.05.07.f 03.05.12.a 03.05.12.b 03.05.12.c 03.05.12.d 03.05.12.e 03.05.12.f |
A.03.05.12.ODP[01] A.03.05.12.ODP[02] A.03.05.12.a A.03.05.12.b A.03.05.12.c[01] A.03.05.12.c[02] A.03.05.12.c[03] A.03.05.12.c[04] A.03.05.12.c[05] A.03.05.12.c[06] A.03.05.12.d A.03.05.12.e A.03.05.12.f[01] A.03.05.12.f[02] |
| 217 | Identification & Authentication | Password-Based Authentication | IAC-10.1 | 3.5.7 | 3.5.7[a] 3.5.7[b] 3.5.7[c] 3.5.7[d] |
03.05.07.e 03.05.07.f 03.05.12.b 03.05.12.c 03.05.12.d 03.05.12.e 03.05.12.f |
A.03.05.07.ODP[02] A.03.05.07.f |
| 218 | Identification & Authentication | In-Person or Trusted Third-Party Registration | IAC-10.3 | 03.05.12.a | |||
| 219 | Identification & Authentication | Automated Support For Password Strength | IAC-10.4 | 03.05.07.a 03.05.07.b |
A.03.05.07.ODP[01] A.03.05.07.a[01] A.03.05.07.a[02] A.03.05.07.a[03] A.03.05.07.b |
||
| 220 | Identification & Authentication | Protection of Authenticators | IAC-10.5 | 3.5.10 | 3.5.10[a] 3.5.10[b] |
03.05.07.c 03.05.07.d 03.05.12.f |
A.03.05.07.c A.03.05.07.d A.03.05.12.f[01] A.03.05.12.f[02] |
| 221 | Identification & Authentication | No Embedded Unencrypted Static Authenticators | IAC-10.6 | 03.05.07.d | |||
| 222 | Identification & Authentication | Vendor-Supplied Defaults | IAC-10.8 | 03.05.07.e 03.05.12.d |
|||
| 223 | Identification & Authentication | Password Managers | IAC-10.11 | 03.05.07.a 03.05.07.b 03.05.07.c 03.05.07.d 03.05.07.f |
A.03.05.07.ODP[01] A.03.05.07.a[01] A.03.05.07.a[02] A.03.05.07.a[03] A.03.05.07.b |
||
| 224 | Identification & Authentication | Authenticator Feedback | IAC-11 | 3.5.11 | 3.5.11 | 03.05.11 | A.03.05.11 |
| 225 | Identification & Authentication | Re-Authentication | IAC-14 | 03.05.01.b | A.03.05.01.ODP[01] A.03.05.01.b |
||
| 226 | Identification & Authentication | Account Management | IAC-15 | 3.1.2 | 3.1.2[a] 3.1.2[b] |
03.01.01.a 03.01.01.b 03.01.01.c.01 03.01.01.c.02 03.01.01.d.01 03.01.01.d.02 03.01.01.e 03.01.01.f.01 03.01.01.f.03 03.01.01.f.04 03.01.01.f.05 03.01.01.g.01 03.01.01.g.02 03.01.01.g.03 03.01.02 03.01.05.b 03.01.05.c 03.01.05.d |
A.03.01.01.ODP[01] A.03.01.01.a[01] A.03.01.01.a[02] A.03.01.01.c.01 A.03.01.01.e A.03.01.01.f.01 A.03.01.01.f.02 A.03.01.01.f.03 A.03.01.01.f.04 A.03.01.01.f.05 A.03.01.01.g.01 A.03.01.01.g.02 A.03.01.01.g.03 A.03.05.07.e |
| 227 | Identification & Authentication | Automated System Account Management (Directory Services) | IAC-15.1 | 3.1.1 | 03.05.05.b 03.05.05.c 03.05.05.d 03.05.07.c 03.05.07.d 03.05.07.e 03.05.07.f 03.05.12.d 03.05.12.e 03.05.12.f |
||
| 228 | Identification & Authentication | Disable Inactive Accounts | IAC-15.3 | 3.5.6 | 3.5.6[a] 3.5.6[b] |
03.01.01.f.02 | A.03.01.01.f.02 |
| 229 | Identification & Authentication | Restrictions on Shared Groups / Accounts | IAC-15.5 | 03.01.01.c.01 | |||
| 230 | Identification & Authentication | Account Disabling for High Risk Individuals | IAC-15.6 | 03.01.01.f.04 03.01.01.f.05 |
|||
| 231 | Identification & Authentication | System Account Reviews | IAC-15.7 | 03.01.01.e 03.01.05.c |
A.03.01.01.a[01] A.03.01.01.a[02] A.03.01.01.b[01] A.03.01.01.b[02] A.03.01.01.b[03] A.03.01.01.b[04] A.03.01.01.b[05] A.03.01.01.c.01 |
||
| 232 | Identification & Authentication | Privileged Account Management (PAM) | IAC-16 | 3.1.5 | 03.01.06.a 03.01.07.a 03.01.07.b |
||
| 233 | Identification & Authentication | Privileged Account Inventories | IAC-16.1 | 3.1.5 | |||
| 234 | Identification & Authentication | Periodic Review of Account Privileges | IAC-17 | 03.01.01.g.03 03.01.05.c 03.01.05.d 03.10.01.c 03.10.01.d |
A.03.01.05.ODP[03] A.03.01.05.c A.03.01.05.d |
||
| 235 | Identification & Authentication | Access Enforcement | IAC-20 | 3.1.1 | 3.1.1[a] 3.1.1[b] 3.1.1[c] 3.1.1[d] 3.1.1[e] 3.1.1[f] |
03.01.01.c.03 03.01.01.d.01 03.01.01.d.02 03.01.02 03.01.03 03.01.04.b 03.01.05.a 03.01.05.b 03.01.06.a 03.09.02.b.02 |
|
| 236 | Identification & Authentication | Access To Sensitive / Regulated Data | IAC-20.1 | 03.01.01.c.03 03.01.01.d.01 03.01.01.d.02 03.01.02 03.01.03 03.01.04.b 03.01.05.a 03.06.05.d 03.10.01.a |
A.03.01.05.b[01] A.03.01.05.b[02] A.03.06.05.d |
||
| 237 | Identification & Authentication | Least Privilege | IAC-21 | 3.1.5 | 3.1.5[a] 3.1.5[b] 3.1.5[c] 3.1.5[d] |
03.01.01.c.03 03.01.01.d.01 03.01.01.d.02 03.01.04.b 03.01.05.a 03.01.05.b 03.01.06.a 03.01.07.a 03.03.08.a 03.03.08.b 03.04.05 |
A.03.01.02[02] A.03.01.05.a |
| 238 | Identification & Authentication | Authorize Access to Security Functions | IAC-21.1 | 3.1.5 | |||
| 239 | Identification & Authentication | Non-Privileged Access for Non-Security Functions | IAC-21.2 | 3.1.6 | 3.1.6[a] 3.1.6[b] |
03.01.06.b | A.03.01.06.b |
| 240 | Identification & Authentication | Privileged Accounts | IAC-21.3 | 3.1.5 | 03.01.06.a 03.01.07.a |
A.03.01.06.ODP[01] A.03.01.06.a |
|
| 241 | Identification & Authentication | Auditing Use of Privileged Functions | IAC-21.4 | 3.1.7 | 03.01.07.b | ||
| 242 | Identification & Authentication | Prohibit Non-Privileged Users from Executing Privileged Functions | IAC-21.5 | 3.1.7 | 3.1.7[a] 3.1.7[b] 3.1.7[c] 3.1.7[d] |
03.01.07.a | A.03.01.07.a |
| 243 | Identification & Authentication | Account Lockout | IAC-22 | 3.1.8 | 3.1.8[a] 3.1.8[b] |
03.01.08.a 03.01.08.b |
A.03.01.08.ODP[01] A.03.01.08.ODP[02] A.03.01.08.ODP[03] A.03.01.08.ODP[04] A.03.01.08.a A.03.01.08.b |
| 244 | Identification & Authentication | Session Lock | IAC-24 | 3.1.10 | 3.1.10[a] 3.1.10[b] 3.1.10[c] |
03.01.10.a 03.01.10.b |
A.03.01.10.ODP[01] A.03.01.10.ODP[02] A.03.01.10.a A.03.01.10.b |
| 245 | Identification & Authentication | Pattern-Hiding Displays | IAC-24.1 | 3.1.10 | 03.01.10.c | A.03.01.10.c | |
| 246 | Identification & Authentication | Session Termination | IAC-25 | 3.1.11 | 3.1.11[a] 3.1.11[b] |
03.01.11 03.07.05.c |
A.03.01.01.ODP[05] A.03.01.01.ODP[06] A.03.01.01.h A.03.01.11 A.03.01.11.ODP[01] A.03.07.05.c[01] A.03.07.05.c[01] |
| 247 | Identification & Authentication | Identity Proofing (Identity Verification) | IAC-28 | 03.05.12.a 03.05.12.c |
|||
| 248 | Identification & Authentication | Management Approval For New or Changed Accounts | IAC-28.1 | 03.01.01.b 03.05.05.a |
|||
| 249 | Incident Response | Incident Response Operations | IRO-01 | NFO - IR-1 | 3.6.1[a] 3.6.1[b] 3.6.1[c] 3.6.1[d] 3.6.1[e] 3.6.1[f] |
03.06.01 | A.03.06.01[01] |
| 250 | Incident Response | Incident Handling | IRO-02 | 3.6.1 3.6.2 |
3.6.1[a] 3.6.1[b] 3.6.1[c] 3.6.1[d] 3.6.1[e] 3.6.1[f] 3.6.1[g] 3.6.2[a] 3.6.2[b] 3.6.2[c] 3.6.2[d] 3.6.2[e] 3.6.2[f] |
03.03.04.b 03.06.01 03.06.02.a 03.06.02.b 03.06.02.c 03.06.02.d |
A.03.06.01[02] A.03.06.01[03] A.03.06.01[04] A.03.06.01[05] A.03.06.01[06] A.03.06.02.b |
| 251 | Incident Response | Incident Response Plan (IRP) | IRO-04 | NFO - IR-8 | 03.06.01 03.06.05.a 03.06.05.a.01 03.06.05.a.02 03.06.05.a.03 03.06.05.a.04 03.06.05.a.05 03.06.05.a.06 03.06.05.b |
A.03.06.02.ODP[01] A.03.06.02.ODP[02] A.03.06.05.a.01 A.03.06.05.a.02 A.03.06.05.a.03 A.03.06.05.a.04 A.03.06.05.a.05 A.03.06.05.a.06 A.03.06.05.b[01] A.03.06.05.b[02] |
|
| 252 | Incident Response | IRP Update | IRO-04.2 | NFO - IR-1 | 03.06.04.b 03.06.05.c |
A.03.06.05.c | |
| 253 | Incident Response | Continuous Incident Response Improvements | IRO-04.3 | 03.06.04.b | |||
| 254 | Incident Response | Incident Response Training | IRO-05 | 3.6.1 | 03.06.04.a 03.06.04.a.03 |
A.03.06.04.ODP[01] A.03.06.04.ODP[02] A.03.06.04.ODP[03] A.03.06.04.ODP[04] A.03.06.04.a.01 A.03.06.04.b[01] A.03.06.04.b[02] A.03.06.04.b[03] A.03.06.04.b[04] |
|
| 255 | Incident Response | Incident Response Testing | IRO-06 | 3.6.3 | 3.6.3 | 03.06.03 | A.03.06.03 A.03.06.03.ODP[01] |
| 256 | Incident Response | Integrated Security Incident Response Team (ISIRT) | IRO-07 | A.03.06.02.b A.03.06.02.d |
|||
| 257 | Incident Response | Situational Awareness For Incidents | IRO-09 | 03.06.02.a 03.06.02.b |
A.03.06.02.a[01] A.03.06.02.a[02] |
||
| 258 | Incident Response | Incident Stakeholder Reporting | IRO-10 | 03.06.02.b 03.06.02.c |
A.03.06.02.ODP[01] A.03.06.02.b A.03.06.02.c A.03.06.02.d |
||
| 259 | Incident Response | Cyber Incident Reporting for Sensitive Data | IRO-10.2 | 03.06.02.b 03.06.02.c |
A.03.06.02.ODP[02] | ||
| 260 | Incident Response | Incident Reporting Assistance | IRO-11 | 03.06.02.d | A.03.06.02.d | ||
| 261 | Incident Response | Information Spillage Response | IRO-12 | 03.06.01 | A.03.01.22.b[02] | ||
| 262 | Incident Response | Root Cause Analysis (RCA) & Lessons Learned | IRO-13 | NFO - IR-1 | 03.06.04.b | ||
| 263 | Incident Response | Regulatory & Law Enforcement Contacts | IRO-14 | 03.06.02.c | A.03.06.02.ODP[02] | ||
| 264 | Information Assurance | Information Assurance (IA) Operations | IAO-01 | NFO - CA-1 | 03.12.01 | ||
| 265 | Information Assurance | Assessment Boundaries | IAO-01.1 | 03.12.01 | |||
| 266 | Information Assurance | Assessments | IAO-02 | 3.12.1 | |||
| 267 | Information Assurance | Assessor Independence | IAO-02.1 | NFO - CA-2(1) | |||
| 268 | Information Assurance | System Security & Privacy Plan (SSPP) | IAO-03 | 3.12.4 | 3.12.4[a] 3.12.4[b] 3.12.4[c] 3.12.4[d] 3.12.4[e] 3.12.4[f] 3.12.4[g] 3.12.4[h] |
03.04.11.b 03.15.02.a 03.15.02.a.01 03.15.02.a.02 03.15.02.a.03 03.15.02.a.04 03.15.02.a.05 03.15.02.a.06 03.15.02.a.07 03.15.02.a.08 03.15.02.b |
A.03.04.11.a[02] A.03.04.11.a[03] A.03.04.11.b[01] A.03.04.11.b[02] A.03.15.02.ODP[01] A.03.15.02.a.01 A.03.15.02.a.02 A.03.15.02.a.03 A.03.15.02.a.04 A.03.15.02.a.05 A.03.15.02.a.06 A.03.15.02.a.07 A.03.15.02.a.08 A.03.15.02.b[01] A.03.15.02.b[02] A.03.15.02.c |
| 269 | Information Assurance | Plan / Coordinate with Other Organizational Entities | IAO-03.1 | NFO - PL-2(3) | |||
| 270 | Information Assurance | Adequate Security for Sensitive / Regulated Data In Support of Contracts | IAO-03.2 | 3.12.4 | |||
| 271 | Information Assurance | Plan of Action & Milestones (POA&M) | IAO-05 | 3.12.2 | 3.12.2[a] 3.12.2[b] 3.12.2[c] |
03.04.11.b 03.12.02.a 03.12.02.a.01 03.12.02.a.02 03.12.02.b 03.12.02.b.01 03.12.02.b.02 03.12.02.b.03 03.14.01.a |
A.03.12.02.a.01 A.03.12.02.a.02 A.03.12.02.b.01 A.03.12.02.b.02 A.03.12.02.b.03 |
| 272 | Maintenance | Maintenance Operations | MNT-01 | NFO - MA-1 | 03.04.03.c 03.07.04.a 03.07.06.a |
||
| 273 | Maintenance | Controlled Maintenance | MNT-02 | 3.7.1 | 3.7.1 | 03.04.03.c 03.07.04.a 03.07.05.a |
A.03.04.03.c[01] |
| 274 | Maintenance | Timely Maintenance | MNT-03 | 03.07.04.a | |||
| 275 | Maintenance | Preventative Maintenance | MNT-03.1 | 03.07.04.a | |||
| 276 | Maintenance | Maintenance Tools | MNT-04 | 3.7.2 | 3.7.2[a] 3.7.2[b] 3.7.2[c] 3.7.2[d] |
03.07.04.a | A.03.07.04.a[01] A.03.07.04.a[02] A.03.07.04.a[03] |
| 277 | Maintenance | Inspect Tools | MNT-04.1 | 3.7.1 | 03.07.04.b | ||
| 278 | Maintenance | Inspect Media | MNT-04.2 | 3.7.4 | 3.7.4 | A.03.07.04.b | |
| 279 | Maintenance | Prevent Unauthorized Removal | MNT-04.3 | 03.07.04.c | A.03.07.04.c | ||
| 280 | Maintenance | Remote Maintenance | MNT-05 | 3.7.5 | 3.7.5[a] 3.7.5[b] |
03.01.12.d 03.07.05.a 03.07.05.b 03.07.05.c |
A.03.07.05.a[01] A.03.07.05.a[02] |
| 281 | Maintenance | Auditing Remote Maintenance | MNT-05.1 | 03.07.05.a | |||
| 282 | Maintenance | Remote Maintenance Notifications | MNT-05.2 | NFO - MA-4(2) | |||
| 283 | Maintenance | Remote Maintenance Cryptographic Protection | MNT-05.3 | 03.07.05.b | A.03.07.05.b[02] | ||
| 284 | Maintenance | Remote Maintenance Disconnect Verification | MNT-05.4 | 03.07.05.c | A.03.07.05.c[01] | ||
| 285 | Maintenance | Remote Maintenance Pre-Approval | MNT-05.5 | 03.07.05.a | |||
| 286 | Maintenance | Authorized Maintenance Personnel | MNT-06 | 3.7.6 | 3.7.6 | 03.07.06.a 03.07.06.b 03.07.06.c 03.07.06.d |
A.03.07.06.a A.03.07.06.b A.03.07.06.c A.03.07.06.d[01] A.03.07.06.d[02] |
| 287 | Maintenance | Maintenance Personnel Without Appropriate Access | MNT-06.1 | 03.07.06.a 03.07.06.c 03.07.06.d |
A.03.07.06.c | ||
| 288 | Maintenance | Non-System Related Maintenance | MNT-06.2 | 03.07.06.a 03.07.06.c |
A.03.07.06.c | ||
| 289 | Maintenance | Off-Site Maintenance | MNT-09 | 03.07.04.a | |||
| 290 | Mobile Device Management | Centralized Management Of Mobile Devices | MDM-01 | 3.1.18 | 03.01.18.a 03.01.20.d |
A.03.01.18.a[01] | |
| 291 | Mobile Device Management | Access Control For Mobile Devices | MDM-02 | 3.1.18 | 3.1.18[a] 3.1.18[b] 3.1.18[c] |
03.01.18.a 03.01.18.b |
A.03.01.18.b |
| 292 | Mobile Device Management | Full Device & Container-Based Encryption | MDM-03 | 3.1.19 | 3.1.19[a] 3.1.19[b] |
03.01.18.c | A.03.01.18.c |
| 293 | Mobile Device Management | Mobile Device Tampering | MDM-04 | 03.04.12.b | |||
| 294 | Mobile Device Management | Personally-Owned Mobile Devices | MDM-06 | 3.1.18 | 03.01.18.a 03.01.18.b |
||
| 295 | Mobile Device Management | Organization-Owned Mobile Devices | MDM-07 | 3.1.18 | 03.01.18.a 03.01.18.b 03.01.20.d |
||
| 296 | Mobile Device Management | Restricting Access To Authorized Devices | MDM-11 | 03.01.18.b | |||
| 297 | Network Security | Network Security Controls (NSC) | NET-01 | NFO - SC-1 | 03.01.12.a 03.01.16.a 03.01.16.b 03.01.18.a 03.13.01.a |
||
| 298 | Network Security | Layered Network Defenses | NET-02 | 03.13.01.b | |||
| 299 | Network Security | Boundary Protection | NET-03 | 3.13.1 | 3.13.1[a] 3.13.1[b] 3.13.1[c] 3.13.1[d] 3.13.1[e] 3.13.1[f] 3.13.1[g] 3.13.1[h] |
03.01.12.a 03.13.01.a 03.13.01.b 03.13.01.c |
A.03.01.18.a[03] A.03.13.01.a[02] A.03.13.01.a[04] A.03.13.01.c |
| 300 | Network Security | Limit Network Connections | NET-03.1 | NFO - SC-7(3) | |||
| 301 | Network Security | External Telecommunications Services | NET-03.2 | NFO - SC-7(4) | |||
| 302 | Network Security | Separate Subnet for Connecting to Different Security Domains | NET-03.8 | 03.13.01.b | |||
| 303 | Network Security | Data Flow Enforcement – Access Control Lists (ACLs) | NET-04 | 3.1.3 | 3.1.3[a] 3.1.3[b] 3.1.3[c] 3.1.3[d] 3.1.3[e] |
03.01.03 03.13.01.a 03.13.01.c |
A.03.01.03[02] |
| 304 | Network Security | Deny Traffic by Default & Allow Traffic by Exception | NET-04.1 | 3.13.6 NFO - CA-3(5) |
3.13.6[a] 3.13.6[b] |
03.13.01.a 03.13.06 |
A.03.13.06[01] A.03.13.06[02] |
| 305 | Network Security | Interconnection Security Agreements (ISAs) | NET-05 | NFO - CA-3 | 03.01.03 03.01.20.c.02 03.12.05.a 03.12.05.b |
A.03.01.03[02] A.03.12.05.ODP[01] A.03.12.05.ODP[02] A.03.12.05.a[01] A.03.12.05.a[02] A.03.12.05.b[01] A.03.12.05.b[02] A.03.12.05.b[03] A.03.12.05.c[01] A.03.12.05.c[02] |
|
| 306 | Network Security | Internal System Connections | NET-05.2 | NFO - CA-9 | 03.01.03 03.12.05.a 03.12.05.b 03.12.05.c |
||
| 307 | Network Security | Network Segmentation (macrosegementation) | NET-06 | 3.13.5 | 3.13.5[a] 3.13.5[b] |
03.13.01.b | A.03.13.01.b |
| 308 | Network Security | Sensitive / Regulated Data Enclave (Secure Zone) | NET-06.3 | 03.13.01.b | |||
| 309 | Network Security | Network Connection Termination | NET-07 | 3.13.9 | 3.13.9[a] 3.13.9[b] 3.13.9[c] |
03.13.09 | A.03.07.05.c[02] A.03.13.09 A.03.13.09.ODP[01] |
| 310 | Network Security | Network Intrusion Detection / Prevention Systems (NIDS / NIPS) | NET-08 | 3.14.6 | 03.13.01.a 03.14.06.c |
||
| 311 | Network Security | DMZ Networks | NET-08.1 | 03.13.01.b | |||
| 312 | Network Security | Session Integrity | NET-09 | 3.13.15 | 3.13.15 | 03.13.15 | A.03.13.15 |
| 313 | Network Security | Domain Name Service (DNS) Resolution | NET-10 | NFO - SC-20 | |||
| 314 | Network Security | Architecture & Provisioning for Name / Address Resolution Service | NET-10.1 | NFO - SC-22 | |||
| 315 | Network Security | Secure Name / Address Resolution Service (Recursive or Caching Resolver) | NET-10.2 | NFO - SC-21 | |||
| 316 | Network Security | Electronic Messaging | NET-13 | 3.13.14 | 3.13.14[a] 3.13.14[b] |
||
| 317 | Network Security | Remote Access | NET-14 | 3.1.12 | 03.01.12.a 03.01.12.b 03.01.12.c 03.01.12.d |
A.03.01.12.a[01] A.03.01.12.a[02] A.03.01.12.a[03] A.03.01.12.a[04] A.03.01.12.b A.03.01.12.c[01] A.03.01.12.c[02] A.03.01.12.d[1] A.03.01.12.d[2] |
|
| 318 | Network Security | Automated Monitoring & Control | NET-14.1 | 3.1.12 | 3.1.12[a] 3.1.12[b] 3.1.12[c] 3.1.12[d] |
03.01.12.b | |
| 319 | Network Security | Protection of Confidentiality / Integrity Using Encryption | NET-14.2 | 3.1.13 | 3.1.13[a] 3.1.13[b] |
03.01.12.a | |
| 320 | Network Security | Managed Access Control Points | NET-14.3 | 3.1.14 | 3.1.14[a] 3.1.14[b] |
03.01.12.b 03.01.12.c |
|
| 321 | Network Security | Remote Privileged Commands & Sensitive Data Access | NET-14.4 | 3.1.15 | 3.1.15[a] 3.1.15[b] 3.1.15[c] 3.1.15[d] |
03.01.12.d | A.03.01.12.d[1] A.03.01.12.d[2] |
| 322 | Network Security | Work From Anywhere (WFA) - Telecommuting Security | NET-14.5 | 3.1.12 3.10.6 |
03.01.12.a 03.01.12.c 03.10.06.a 03.10.06.b |
A.03.10.06.ODP[01] A.03.10.06.a A.03.10.06.b |
|
| 323 | Network Security | Wireless Networking | NET-15 | 3.1.16 | 3.1.16[a] 3.1.16[b] |
03.01.16.a 03.01.16.b |
A.03.01.16.a[01] A.03.01.16.a[02] A.03.01.16.a[04] |
| 324 | Network Security | Authentication & Encryption | NET-15.1 | 3.1.17 | 3.1.17[a] 3.1.17[b] |
03.01.16.a 03.01.16.b 03.01.16.d |
A.03.01.16.d[01] A.03.01.16.d[02] |
| 325 | Network Security | Disable Wireless Networking | NET-15.2 | 03.01.16.c | |||
| 326 | Network Security | Restrict Configuration By Users | NET-15.3 | 03.01.16.a 03.01.16.c |
|||
| 327 | Network Security | DNS & Content Filtering | NET-18 | 3.1.3 | 03.14.06.c | ||
| 328 | Physical & Environmental Security | Physical & Environmental Protections | PES-01 | 3.10.2 NFO - PE-1 |
3.10.2[a] 3.10.2[b] 3.10.2[c] 3.10.2[d] |
03.08.01 03.08.02 03.10.01.a 03.10.07.a |
|
| 329 | Physical & Environmental Security | Physical Access Authorizations | PES-02 | 3.10.1 | 3.10.1[a] 3.10.1[b] 3.10.1[c] 3.10.1[d] |
03.08.01 03.08.02 03.10.01.a 03.10.01.b 03.10.01.c 03.10.01.d 03.10.07.a |
A.03.04.05[02] A.03.10.01.ODP[01] A.03.10.01.a[01] A.03.10.01.a[02] A.03.10.01.a[03] A.03.10.01.c A.03.10.01.d A.03.10.07.a.01 |
| 330 | Physical & Environmental Security | Role-Based Physical Access | PES-02.1 | 03.08.01 03.08.02 03.10.01.b 03.10.01.d |
A.03.04.05[01] A.03.10.01.ODP[01] A.03.10.01.b |
||
| 331 | Physical & Environmental Security | Physical Access Control | PES-03 | 3.10.5 | 3.10.5[a] 3.10.5[b] 3.10.5[c] |
03.10.02.a 03.10.07.a 03.10.07.a.01 03.10.07.a.02 03.10.07.d |
A.03.04.05[03] A.03.10.07.a.02 A.03.10.07.d |
| 332 | Physical & Environmental Security | Controlled Ingress & Egress Points | PES-03.1 | 03.10.02.a 03.10.07.a 03.10.07.a.02 |
|||
| 333 | Physical & Environmental Security | Physical Access Logs | PES-03.3 | 3.10.4 NFO - PE-8 |
3.10.4 | 03.10.02.a 03.10.07.b |
A.03.10.07.b |
| 334 | Physical & Environmental Security | Access To Information Systems | PES-03.4 | 03.10.07.a.01 03.10.07.a.02 |
|||
| 335 | Physical & Environmental Security | Physical Security of Offices, Rooms & Facilities | PES-04 | 3.10.5 | 03.08.01 03.08.02 03.10.07.a.01 03.10.07.a.02 03.10.07.d |
||
| 336 | Physical & Environmental Security | Working in Secure Areas | PES-04.1 | 03.08.01 03.08.02 03.10.07.a.01 03.10.07.a.02 03.10.07.d |
|||
| 337 | Physical & Environmental Security | Monitoring Physical Access | PES-05 | 3.10.2 | 03.10.02.a 03.10.02.b |
A.03.10.02.ODP[01] A.03.10.02.ODP[02] A.03.10.02.a[01] A.03.10.02.a[02] A.03.10.02.b[01] A.03.10.02.b[02] |
|
| 338 | Physical & Environmental Security | Intrusion Alarms / Surveillance Equipment | PES-05.1 | 3.10.2 NFO - PE-6(1) |
03.10.02.a 03.10.02.b |
||
| 339 | Physical & Environmental Security | Monitoring Physical Access To Information Systems | PES-05.2 | 3.10.2 | 03.10.02.a 03.10.02.b |
||
| 340 | Physical & Environmental Security | Visitor Control | PES-06 | 3.10.3 | 3.10.3[a] 3.10.3[b] |
03.10.02.b 03.10.07.c |
A.03.10.07.c[01] A.03.10.07.c[02] |
| 341 | Physical & Environmental Security | Identification Requirement | PES-06.2 | 03.10.07.c | |||
| 342 | Physical & Environmental Security | Restrict Unescorted Access | PES-06.3 | 3.10.3 | 3.10.3[a] 3.10.3[b] |
03.10.07.c | A.03.10.07.c[01] A.03.10.07.c[02] |
| 343 | Physical & Environmental Security | Visitor Access Revocation | PES-06.6 | 03.10.07.c | |||
| 344 | Physical & Environmental Security | Supporting Utilities | PES-07 | 03.10.08 | |||
| 345 | Physical & Environmental Security | Delivery & Removal | PES-10 | NFO - PE-16 | |||
| 346 | Physical & Environmental Security | Alternate Work Site | PES-11 | 3.10.6 | 3.10.6[a] 3.10.6[b] |
03.10.06.a 03.10.06.b |
A.03.10.06.ODP[01] A.03.10.06.a A.03.10.06.b |
| 347 | Physical & Environmental Security | Equipment Siting & Protection | PES-12 | 3.10.1 | 03.10.07.e 03.10.08 |
||
| 348 | Physical & Environmental Security | Transmission Medium Security | PES-12.1 | 3.10.1 | 03.10.08 | A.03.10.08 | |
| 349 | Physical & Environmental Security | Access Control for Output Devices | PES-12.2 | 3.10.1 | 03.10.07.e | A.03.10.07.e | |
| 350 | Project & Resource Management | Cybersecurity & Data Privacy Portfolio Management | PRM-01 | NFO - PL-1 | 03.16.01 | ||
| 351 | Project & Resource Management | Allocation of Resources | PRM-03 | NFO - SA-2 | |||
| 352 | Project & Resource Management | Cybersecurity & Data Privacy Requirements Definition | PRM-05 | 03.16.01 | |||
| 353 | Project & Resource Management | Secure Development Life Cycle (SDLC) Management | PRM-07 | NFO - SA-3 | |||
| 354 | Risk Management | Risk Management Program | RSK-01 | NFO - RA-1 | 03.11.01.a 03.17.01.a |
A.03.17.03.b | |
| 355 | Risk Management | Risk Framing | RSK-01.1 | 03.11.01.a | A.03.11.01.a | ||
| 356 | Risk Management | Risk-Based Security Categorization | RSK-02 | 03.11.01.a | |||
| 357 | Risk Management | Impact-Level Prioritization | RSK-02.1 | 03.11.01.a 03.14.03.b |
|||
| 358 | Risk Management | Risk Identification | RSK-03 | 03.11.01.a | A.03.11.01.a | ||
| 359 | Risk Management | Risk Catalog | RSK-03.1 | 03.15.02.a.03 | A.03.11.01.a | ||
| 360 | Risk Management | Risk Assessment | RSK-04 | 3.11.1 | 3.11.1[a] 3.11.1[b] |
03.11.01.a | A.03.11.01.a A.03.11.01.b |
| 361 | Risk Management | Risk Register | RSK-04.1 | 03.12.02.a.01 03.12.02.a.02 |
|||
| 362 | Risk Management | Risk Ranking | RSK-05 | 03.11.01.a | |||
| 363 | Risk Management | Risk Remediation | RSK-06 | 3.11.3 | 03.11.02.b 03.12.02.a.02 |
||
| 364 | Risk Management | Risk Response | RSK-06.1 | 03.11.02.b 03.11.04 |
A.03.11.04[01] A.03.11.04[02] A.03.11.04[03] |
||
| 365 | Risk Management | Compensating Countermeasures | RSK-06.2 | 03.11.02.b | |||
| 366 | Risk Management | Risk Assessment Update | RSK-07 | 03.11.01.b | A.03.11.01.ODP[01] A.03.11.01.b |
||
| 367 | Risk Management | Supply Chain Risk Management (SCRM) Plan | RSK-09 | 03.11.01.a 03.17.01.a 03.17.01.b 03.17.03.a 03.17.03.b |
A.03.11.01.a A.03.17.01.ODP[01] A.03.17.01.a[01] A.03.17.01.a[02] A.03.17.01.a[03] A.03.17.01.a[04] A.03.17.01.a[05] A.03.17.01.a[06] A.03.17.01.a[07] A.03.17.01.a[08] A.03.17.01.a[09] A.03.17.01.a[10] A.03.17.01.b[01] A.03.17.01.b[02] A.03.17.01.c A.03.17.03.ODP[01] A.03.17.03.a[01] A.03.17.03.a[02] A.03.17.03.b |
||
| 368 | Risk Management | Supply Chain Risk Assessment | RSK-09.1 | 03.11.01.a 03.11.01.b 03.17.03.a |
|||
| 369 | Secure Engineering & Architecture | Secure Engineering Principles | SEA-01 | 3.13.2 | 3.13.2[a] 3.13.2[c] 3.13.2[d] 3.13.2[f] |
03.01.12.a 03.01.16.a 03.01.16.b 03.01.16.c 03.01.18.a 03.13.01.c 03.16.01 |
A.03.16.01.ODP[01] |
| 370 | Secure Engineering & Architecture | Alignment With Enterprise Architecture | SEA-02 | NFO - PL-8 | 03.01.12.a 03.01.16.a 03.01.18.a 03.13.01.c 03.16.01 |
||
| 371 | Secure Engineering & Architecture | Defense-In-Depth (DiD) Architecture | SEA-03 | 3.13.2 | |||
| 372 | Secure Engineering & Architecture | Application Partitioning | SEA-03.2 | 3.13.3 | 3.13.3[a] 3.13.3[b] 3.13.3[c] |
||
| 373 | Secure Engineering & Architecture | Process Isolation | SEA-04 | NFO - SC-39 | |||
| 374 | Secure Engineering & Architecture | Information In Shared Resources | SEA-05 | 3.13.4 | 3.13.4 | 03.13.04 | A.03.13.04[01] A.03.13.04[02] |
| 375 | Secure Engineering & Architecture | Predictable Failure Analysis | SEA-07 | NFO - SA-3 | 03.16.02.b | ||
| 376 | Secure Engineering & Architecture | Technology Lifecycle Management | SEA-07.1 | NFO - SA-3 | 03.16.02.a 03.16.02.b |
||
| 377 | Secure Engineering & Architecture | Memory Protection | SEA-10 | NFO - SI-16 | |||
| 378 | Secure Engineering & Architecture | System Use Notification (Logon Banner) | SEA-18 | 3.1.9 | 3.1.9[a] 3.1.9[b] |
03.01.09 | A.03.01.09 |
| 379 | Secure Engineering & Architecture | Standardized Microsoft Windows Banner | SEA-18.1 | 3.1.9 | 3.1.9[a] 3.1.9[b] |
03.01.09 | A.03.01.09 |
| 380 | Secure Engineering & Architecture | Truncated Banner | SEA-18.2 | 3.1.9 | 3.1.9[a] 3.1.9[b] |
03.01.09 | A.03.01.09 |
| 381 | Secure Engineering & Architecture | Clock Synchronization | SEA-20 | 3.3.7 | |||
| 382 | Security Operations | Operations Security | OPS-01 | 03.15.01.a 03.15.01.b |
|||
| 383 | Security Operations | Standardized Operating Procedures (SOP) | OPS-01.1 | 03.15.01.a | A.03.15.01.a[03] A.03.15.01.a[04] A.03.15.01.b[01] A.03.15.01.b[02] |
||
| 384 | Security Operations | Service Delivery (Business Process Support) |
OPS-03 | 03.15.01.b | |||
| 385 | Security Awareness & Training | Cybersecurity & Data Privacy-Minded Workforce | SAT-01 | NFO - AT-1 | 03.02.01.a | A.03.02.01.ODP[01] A.03.02.01.ODP[02] A.03.02.01.a.01[01] A.03.02.01.a.01[02] |
|
| 386 | Security Awareness & Training | Cybersecurity & Data Privacy Awareness Training | SAT-02 | 3.2.1 | 3.2.1[a] 3.2.1[b] 3.2.1[c] 3.2.1[d] |
03.01.22.a 03.02.01.a.01 03.02.01.a.02 03.02.01.a.03 03.02.01.b 03.06.04.a.03 |
A.03.02.01.ODP[03] A.03.02.01.ODP[04] |
| 387 | Security Awareness & Training | Social Engineering & Mining | SAT-02.2 | 03.02.01.a.03 | A.03.02.01.a.03[03] A.03.02.01.a.03[04] A.03.02.01.a.03[05] A.03.02.01.a.03[06] |
||
| 388 | Security Awareness & Training | Role-Based Cybersecurity & Data Privacy Training | SAT-03 | 3.2.2 | 3.2.2[a] 3.2.2[b] 3.2.2[c] |
03.01.22.a 03.02.01.a.01 03.02.01.a.02 03.02.02.a 03.02.02.a.01 03.02.02.a.02 03.02.02.b 03.06.04.a 03.06.04.a.01 03.06.04.a.02 03.06.04.b |
A.03.02.02.ODP[01] A.03.02.02.ODP[02] A.03.02.02.ODP[03] A.03.02.02.ODP[04] A.03.02.02.a.01[01] A.03.02.02.a.01[02] A.03.02.02.a.01[03] A.03.02.02.a.02 A.03.02.02.b[01] A.03.02.02.b[02] A.03.06.04.a.01 A.03.06.04.a.02 A.03.06.04.a.03 |
| 389 | Security Awareness & Training | Sensitive Information Storage, Handling & Processing | SAT-03.3 | 03.01.22.a 03.02.01.a.01 03.02.02.a.01 |
|||
| 390 | Security Awareness & Training | Privileged Users | SAT-03.5 | 03.02.01.a.01 03.02.02.a.01 |
|||
| 391 | Security Awareness & Training | Cyber Threat Environment | SAT-03.6 | 03.02.01.a.01 03.02.01.a.02 03.02.01.a.03 03.02.01.b 03.02.02.a.01 03.02.02.a.02 03.02.02.b 03.06.04.a.02 |
A.03.02.01.a.02 A.03.02.01.b[01] A.03.02.01.b[02] |
||
| 392 | Security Awareness & Training | Continuing Professional Education (CPE) - Cybersecurity & Data Privacy Personnel | SAT-03.7 | 03.06.04.b | |||
| 393 | Security Awareness & Training | Cybersecurity & Data Privacy Training Records | SAT-04 | NFO - AT-4 | |||
| 394 | Technology Development & Acquisition | Technology Development & Acquisition | TDA-01 | NFO - SA-4 | 03.12.01 03.12.03 03.14.01.a 03.16.01 03.17.02 |
A.03.16.01.ODP[01] A.03.17.02[04] A.03.17.02[05] A.03.17.02[06] |
|
| 395 | Technology Development & Acquisition | Product Management | TDA-01.1 | 03.12.03 | |||
| 396 | Technology Development & Acquisition | Minimum Viable Product (MVP) Security Requirements | TDA-02 | NFO - SA-4 | |||
| 397 | Technology Development & Acquisition | Ports, Protocols & Services In Use | TDA-02.1 | NFO - SA-4(9) | |||
| 398 | Technology Development & Acquisition | Information Assurance Enabled Products | TDA-02.2 | NFO - SA-4(10) | |||
| 399 | Technology Development & Acquisition | Development Methods, Techniques & Processes | TDA-02.3 | 03.16.01 | |||
| 400 | Technology Development & Acquisition | Pre-Established Secure Configurations | TDA-02.4 | 03.16.01 | |||
| 401 | Technology Development & Acquisition | Commercial Off-The-Shelf (COTS) Security Solutions | TDA-03 | 03.16.01 | |||
| 402 | Technology Development & Acquisition | Documentation Requirements | TDA-04 | NFO - SA-5 | |||
| 403 | Technology Development & Acquisition | Functional Properties | TDA-04.1 | NFO - SA-4(1) NFO - SA-4(2) |
|||
| 404 | Technology Development & Acquisition | Developer Architecture & Design | TDA-05 | 03.16.01 | |||
| 405 | Technology Development & Acquisition | Secure Coding | TDA-06 | NFO - SA-1 | 3.13.2[b] 3.13.2[e] |
03.16.01 | |
| 406 | Technology Development & Acquisition | Separation of Development, Testing and Operational Environments | TDA-08 | 3.4.5 | |||
| 407 | Technology Development & Acquisition | Cybersecurity & Data Privacy Testing Throughout Development | TDA-09 | NFO - SA-11 | 03.12.01 03.12.03 03.14.01.a |
||
| 408 | Technology Development & Acquisition | Continuous Monitoring Plan | TDA-09.1 | 03.12.03 | |||
| 409 | Technology Development & Acquisition | Developer Configuration Management | TDA-14 | NFO - SA-10 | |||
| 410 | Technology Development & Acquisition | Unsupported Systems | TDA-17 | 03.16.02.a | A.03.16.02.a | ||
| 411 | Technology Development & Acquisition | Alternate Sources for Continued Support | TDA-17.1 | 03.16.02.b | A.03.16.02.b | ||
| 412 | Third-Party Management | Third-Party Management | TPM-01 | NFO - SA-4 | 03.01.20.a 03.01.20.b 03.01.20.c.01 03.07.06.a 03.16.01 03.16.03.a |
A.03.17.03.ODP[01] | |
| 413 | Third-Party Management | Third-Party Inventories | TPM-01.1 | 03.07.06.a | |||
| 414 | Third-Party Management | Third-Party Criticality Assessments | TPM-02 | 03.11.01.a 03.17.03.a |
|||
| 415 | Third-Party Management | Supply Chain Protection | TPM-03 | 03.11.01.a 03.17.01.a 03.17.03.a 03.17.03.b |
|||
| 416 | Third-Party Management | Acquisition Strategies, Tools & Methods | TPM-03.1 | 03.17.01.a 03.17.02 03.17.03.a 03.17.03.b |
A.03.17.02[01] A.03.17.02[02] A.03.17.02[03] |
||
| 417 | Third-Party Management | Limit Potential Harm | TPM-03.2 | 03.17.03.a 03.17.03.b |
|||
| 418 | Third-Party Management | Processes To Address Weaknesses or Deficiencies | TPM-03.3 | 03.17.03.a 03.17.03.b |
|||
| 419 | Third-Party Management | Third-Party Services | TPM-04 | NFO -SA-9 | 03.16.03.a 03.16.03.c 03.17.02 03.17.03.a 03.17.03.b |
||
| 420 | Third-Party Management | Third-Party Risk Assessments & Approvals | TPM-04.1 | 03.11.01.a 03.17.02 03.17.03.a 03.17.03.b |
A.03.17.03.a[01] | ||
| 421 | Third-Party Management | External Connectivity Requirements - Identification of Ports, Protocols & Services | TPM-04.2 | NFO - SA-9(2) | |||
| 422 | Third-Party Management | Third-Party Processing, Storage and Service Locations | TPM-04.4 | 03.16.03.a | |||
| 423 | Third-Party Management | Third-Party Contract Requirements | TPM-05 | 3.1.1 | 03.01.20.b 03.01.20.c.01 03.01.20.c.02 03.07.06.a 03.16.03.a 03.16.03.b 03.16.03.c 03.17.02 03.17.03.b |
A.03.16.03.ODP[01] A.03.16.03.a |
|
| 424 | Third-Party Management | Security Compromise Notification Agreements | TPM-05.1 | 03.17.02 | |||
| 425 | Third-Party Management | Contract Flow-Down Requirements | TPM-05.2 | 3.1.1 | 03.16.03.a 03.16.03.b 03.16.03.c 03.17.02 03.17.03.b |
A.03.16.03.ODP[01] | |
| 426 | Third-Party Management | Responsible, Accountable, Supportive, Consulted & Informed (RASCI) Matrix | TPM-05.4 | 03.07.06.a 03.16.03.b |
A.03.16.03.b | ||
| 427 | Third-Party Management | Third-Party Scope Review | TPM-05.5 | 03.16.03.c 03.17.02 03.17.03.a 03.17.03.b |
A.03.16.03.c | ||
| 428 | Third-Party Management | First-Party Declaration (1PD) | TPM-05.6 | 03.01.20.c.01 03.16.03.c |
A.03.16.03.c | ||
| 429 | Third-Party Management | Break Clauses | TPM-05.7 | 03.17.01.a 03.17.02 03.17.03.b |
|||
| 430 | Third-Party Management | Third-Party Attestation | TPM-05.8 | 03.01.20.a 03.01.20.b 03.01.20.c.01 03.16.03.a 03.16.03.c |
A.03.16.03.c | ||
| 431 | Third-Party Management | Review of Third-Party Services | TPM-08 | 03.16.03.c 03.17.02 |
A.03.16.03.c | ||
| 432 | Third-Party Management | Third-Party Deficiency Remediation | TPM-09 | 03.17.02 | |||
| 433 | Third-Party Management | Managing Changes To Third-Party Services | TPM-10 | NFO - SA-4 | 03.16.01 03.17.02 |
||
| 434 | Threat Management | Threat Intelligence Program | THR-01 | 3.12.3 3.14.3 |
03.11.02.a 03.14.03.a |
||
| 435 | Threat Management | Threat Intelligence | THR-03 | 3.14.3 | 03.02.01.a.02 03.02.01.a.03 03.02.01.b 03.02.02.b 03.11.02.a 03.14.03.a |
A.03.14.03.a | |
| 436 | Threat Management | Threat Intelligence Reporting | THR-03.1 | 03.14.03.b | A.03.14.03.b[01] A.03.14.03.b[02] |
||
| 437 | Threat Management | Insider Threat Awareness | THR-05 | 3.2.3 | 3.2.3[a] 3.2.3[b] |
03.02.01.a.03 | A.03.02.01.a.03[01] A.03.02.01.a.03[02] |
| 438 | Threat Management | Threat Catalog | THR-09 | 03.15.02.a.03 | |||
| 439 | Threat Management | Threat Analysis | THR-10 | 03.14.03.b | |||
| 440 | Vulnerability & Patch Management | Vulnerability & Patch Management Program (VPMP) | VPM-01 | 3.14.1 | 3.14.1[a] 3.14.1[b] 3.14.1[c] 3.14.1[d] 3.14.1[e] 3.14.1[f] |
03.11.02.a 03.14.01.a |
A.03.11.02.ODP[03] |
| 441 | Vulnerability & Patch Management | Attack Surface Scope | VPM-01.1 | 03.11.02.a 03.14.01.a |
A.03.11.02.a[01] | ||
| 442 | Vulnerability & Patch Management | Vulnerability Remediation Process | VPM-02 | 3.11.3[a] 3.11.3[b] |
03.11.02.b 03.12.02.a.02 03.14.01.a |
A.03.11.02.ODP[03] | |
| 443 | Vulnerability & Patch Management | Vulnerability Ranking | VPM-03 | 03.11.02.a | |||
| 444 | Vulnerability & Patch Management | Continuous Vulnerability Remediation Activities | VPM-04 | 03.11.02.b 03.14.01.a 03.14.01.b |
A.03.11.02.b | ||
| 445 | Vulnerability & Patch Management | Software & Firmware Patching | VPM-05 | 3.11.3 | 03.11.02.b 03.12.02.a.02 03.14.01.a 03.14.01.b |
A.03.11.02.b A.03.14.01.ODP[01] A.03.14.01.ODP[02] A.03.14.01.a[01] A.03.14.01.a[02] A.03.14.01.a[03] A.03.14.01.b[01] A.03.14.01.b[02] |
|
| 446 | Vulnerability & Patch Management | Vulnerability Scanning | VPM-06 | 3.11.2 | 3.11.2[a] 3.11.2[b] 3.11.2[c] 3.11.2[d] 3.11.2[e] |
03.11.02.a | A.03.11.02.ODP[01] A.03.11.02.ODP[02] A.03.11.02.ODP[04] A.03.11.02.a[01] A.03.11.02.a[02] A.03.11.02.a[03] A.03.11.02.a[04] A.03.11.02.c[01] A.03.11.02.c[02] |
| 447 | Vulnerability & Patch Management | Update Tool Capability | VPM-06.1 | NFO - RA-5(1) NFO - RA-5(2) |
03.11.02.c | A.03.11.02.ODP[04] A.03.11.02.c[01] A.03.11.02.c[02] |
|
| 448 | Vulnerability & Patch Management | Privileged Access | VPM-06.3 | 3.11.2 |
Supplemental Documentation - Annexes, Templates & References
The NCP also contains the following in the “supplemental documentation” attachment that we provide as part of the NCP:
- Artifact 1: Data Classification & Handling Guidelines
- Artifact 2: Data Classification Examples
- Artifact 3: Data Retention Periods
- Artifact 4: Baseline Security Categorization Guidelines
- Artifact 5: Rules of Behavior (Acceptable & Unacceptable Use)
- Artifact 6: Guidelines for Personal Use of Organizational IT Resources
- Artifact 7: Risk Management Framework (RMF)
- Artifact 8: System Hardening
- Artifact 9: Safety Considerations With Embedded Technology
- Artifact 10: Indicators of Compromise (IoC)
- Artifact 11: Management Directive (Policy Authorization)
- Artifact 12: User Acknowledgement Form
- Artifact 13: User Equipment Receipt of Issue
- Artifact 14: Service Provider Non-Disclosure Agreement (NDA)
- Artifact 15: Incident Response Plan (IRP)
- Artifact 16: Incident Response Form
- Artifact 17: Appointment Orders (Information Security Officer)
- Artifact 18: Privileged User Account Request Form
- Artifact 19: Change Management Request Form
- Artifact 20: Change Control Board (CCB) Meeting Minutes
- Artifact 21: Plan of Action & Milestones (POA&M) / Risk Register
- Artifact 22: Ports, Protocols & Services (PPS)
- Artifact 23: Business Impact Analysis (BIA)
- Artifact 24: Privacy Impact Assessment (PIA)
- Artifact 25: Disaster Recovery Plan (DRP) & Business Continuity Plan (BCP)
- Artifact 26: Exception Request Form
- Artifact 27: Electronic Discovery (eDiscovery) Guidelines
- Artifact 28: Types of Security Controls
- Artifact 29: Cybersecurity Mission, Vision & Strategy
- Artifact 30: Memorandum for Record (MFR) to Define CUI
- Artifact 31: Cybersecurity Roles & Responsibilities Overview
In addition to that, we include the following documentation to aide in your implementation of the NCP:
- NIST NICE Cybersecurity Workforce-based Cybersecurity Roles & Responsibilities
- Data Classification Icons (PowerPoint template)
- Guide to Writing Procedures
- NIST 800-171 Scoping Guide
Affordable NIST 800-171 R2 / R3 & CMMC 2.0 Compliance Documentation
ComplianceForge took existing documentation and pared it down for smaller organizations that do not need or want the complexity of NIST 800-53 when complying with NIST 800-171. The NCP includes the following documents as part of its own unique bundle:
- NIST 800-171 Compliance Program - Microsoft Word document that addresses NIST 800-171 policies and standards.
- Cybersecurity Standardized Operating Procedures (CSOP) - Microsoft Word document that contains cybersecurity procedures that correspond to the policies and standards.
- System Security Plan (SSP) - Microsoft Word document that is a simplified version of our SSP product.
- NIST 800-171 Cybersecurity Program Mapping - Microsoft Excel document that contains several components:
- Plan of Action & Milestones (POA&M) template.
- Mapping from the NCP to NIST 800-171, NIST 800-53, NIST 800-160, ISO 27002 and NIST CSF.
- Methods to comply with NIST 800-171 (essentially a pared down NIST 800-171 Compliance Criteria (NCC) spreadsheet)
- Roles and responsibilities (corresponds to the Cybersecurity Standardized Operating Procedures)
- Cybersecurity Awareness Training - Microsoft PowerPoint template to provide cybersecurity awareness training.
The official overview of CMMC 2.0 can be read at https://dodcio.defense.gov/CMMC/. As you can see from the infographic show below, CMMC evolved from 5 levels to 3 levels. If you store, transmit or process Controlled Unclassified Information (CUI) then you are CMMC v2.0 Level 2 (Advanced). ComplianceForge's NIST 800-171 Compliance Program (NCP) is specifically designed as the "easy button" for CMMC v2.0 Level 2 (Advanced). CMMC v2.0 Level 2 (Advanced) removes the CMMC v1.02 practices and processes. The focus is on NIST 800-171 R2 CUI and NFO controls.
FAR vs DFARS Implications for NIST 800-171 R2 / R3
NIST 800-171 isn’t just for Department of Defense (DoD) contractors. In addition to DoD contractors that had to comply with NIST 800-171 by the end of 2017, US Federal contractors are increasingly being required to comply with NIST 800-171. We often hear from DoD and US Government contractors that they do not know where to start, but they just know that NIST 800-171 is a requirement they cannot run from. Both DFARS and FAR point to NIST 800-171 as the expectation for contractors to implement a minimum set of cybersecurity capabilities.
The NCP addresses both Controlled Unclassified Information (CUI) and Non-Federal Organization (NFO) requirements. Many people overlook the NFO requirements that are listed in Appendix E of NIST 800-171, but the NCP includes both CUI and NFO controls so that you have complete coverage for NIST 800-171 compliance documentation.
Work Smarter and Not Harder - NIST 800-171 R2 / R3 Scoping Considerations
NIST 800-171 allows contractors to limit the scope of the CUI security requirements to those particular systems or components that store, process or transmit CUI. Isolating CUI into its own security domain by applying architectural design principles or concepts (e.g., implementing subnetworks with firewalls or other boundary protection devices) may be the most cost-effective and efficient approach for non-federal organizations to satisfy the requirements and protect the confidentiality of CUI. Security domains may employ physical separation, logical separation, or a combination of both.
|
Click here for a FREE GUIDE |
We put together a guide to help companies scope their computing environment to help identify what is in scope for NIST 800-171 and was falls outside of scope. When you look at NIST 800-171 compliance, it has some similarities to the Payment Card Industry Data Security Standard (PCI DSS). If scoping is done poorly, a company's Cardholder Data Environment (CDE) can encompass the enterprise's entire network, which means PCI DSS requirements would apply uniformly throughout the entire organization. In these scenarios, PCI DSS compliance can be prohibitively expensive or even technically impossible. However, when the network is intelligently designed with security in mind, the CDE can be a small fraction of the company's network, which makes compliance much more achievable and affordable. NIST 800-171 should be viewed in the very same manner. We feel that NIST 800-171 should be viewed in the very same manner. This guide is meant to help companies identify assets within scope for NIST 800-171 and potentially find ways to minimize scope through isolation or controlled access. |
Frequently Asked Questions
Where can I see an example NCP?
How is the NCP different from other editable templates that can be found on the Internet?
You get what you pay for. ComplianceForge specializes in cybersecurity documentation and has been writing quality cybersecurity documentation since 2005. We’ve been writing NIST 800-171-related compliance documentation since 2016, so we have nearly a decade of experience and refinements that make up the NIST 800-171 Compliance Program (NCP).
The NCP is "battle tested" - our clients have successfully passed DIBCAC assessments with this documentation, including a CMMC Third-Party Assessment Organization (C3PAO). Our clients choose us, since ComplianceForge understands that “a standard is a standard for a reason” where we follow industry-recognized practices for building our documentation solutions. This Hierarchical Cybersecurity Governance Framework can be read about here, where you can see how the structure follows terminology established by NIST, ISO, ISACA and AICPA for what right looks like for cybersecurity documentation. Look at examples of the NCP to see the quality difference for yourself.
How can I get a quote to purchase a NCP?
If you need a formal quote for a NIST 800-171 Compliance Program (NCP), please use the “Add To Quote” feature on the product page. This will allow us to generate a formal quote for you.
Can I buy the NCP with a Purchase Order (PO) or an offline invoice?
Yes. In addition to accepting all major credit cards, ComplianceForge can process orders for the NIST 800-171 Compliance Program (NCP) through offline invoicing. Please note that for non-credit card orders, we only process the order once payment is received, while credit card purchases are processed generally the same business day.
To place a non-credit card order, select the Invoice / Purchase Order (PO) payment option during the checkout process, since that ensures the order is in the system and that we can generate an invoice for you. You can reference the PO# in the comments section of the order checkout processes, which will ensure the PO# is included on the invoice. You will receive a separate email with the invoice that contains check or ACH payment instructions.
How will I receive the NCP product files?
The NIST 800-171 Compliance Program (NCP) files are available via a ShareFile download link that we send you. We manually process our orders to customize the documentation and then email you the link to download the documentation.
Is the NCP editable?
Yes. The NIST 800-171 Compliance Program (NCP) is fully editable for your needs. The NCP is delivered in editable Microsoft Office formats (e.g., Word, Excel and PowerPoint). These are editable documents that you are able to modify for your organization's unique needs. There is no software to install - it is just templatized documentation that you can edit for your needs.
If you have a logo, have it ready at the time of purchase since you will be prompted to upload it. The cover page of the documentation will have your company's logo prominently displayed. The rest of the document will have your company name throughout, so anyone reading the document will get the feel it was custom created and tailored to your company.
If you do not have a logo, that is no problem. We just leave the logo off. The documentation will still look very professional, even without your logo on the front page.
Is the NCP a software or a subscription service?
Neither. The NIST 800-171 Compliance Program (NCP) is a one-time purchase and no software needs to be installed, since these are editable Microsoft Office documents (e.g., Microsoft Word, Excel and PowerPoint). The NCP does come with one (1) year of product updates. After the first year, you can choose to renew updates to stay current on changes (e.g., NIST 800-171 R3, CMMC 3.0, etc.).
When we send out new versions of the NCP, it comes with highlighted changes and errata. This helps you identify what has changed between the versions. Every organization handles its internal change control and review processes differently, so we do our best to make it as easy as possible to track version changes to help our clients.
How quickly can I receive my NCP order?
Generally, we process NIST 800-171 Compliance Program (NCP) orders the same day they are received. However, depending on the volume of orders, it may be processed the following business day.
Turnaround time is generally the same business day for orders placed by credit card, but we give a buffer of 1-2 business days. Upon completing the online transaction, you will receive a confirmation e-mail. The completed product will be delivered to the e-mail address used to register at the time of purchase. If you pay by PO/Invoice, we do not process the order until payment is received.
Can I get additional customization of the NCP?
Yes. ComplianceForge, or its partners, can offer professional services to provide additional customization. However, it is added cost involved due to labor incurred. Please review the Partners page for consultants who you want to work with for any professional services. There are also CMMC Practitioners listed on the CMMC Center of Awesomeness page that have experience with customizing the NIST 800-171 Compliance Program (NCP).
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.