Steps To Upgrade To NIST SP 800-171 Rev 3
Upgrading to NIST SP 800-171 Rev 3 does not have to be scary, but you do have to approach it with a "project management" mindset to ensure you separate facts from assumptions. This concept of approaching it from a risk-based, prioritized project plan equally applies to an organization that is upgrading from NIST SP 800-171 Rev 2 as it does to an organization just starting out new to NIST 800-171 with no legacy NIST 800-171 R2 involvement. Arguably, the “heaviest lift” items in a transition to NIST 800-171 Rev 3 include:
- The migration of Non-Federal Organization (NFO) controls into Controlled Unclassified Information (CUI) controls increases the amount of governance practices that organizations will need to address; and
- Not only developing a Supply Chain Risk Management (SCRM) Plan, but implementing C-SCRM practices (e.g., having the evidence of due diligence and due care to prove the SCRM Plan is operational and works as advertised).
The information on this page is designed to help you understand what is expected to upgrade from NIST 800-171 Rev 2 to NIST 800-171 Rev 3. While every organization is different, this provides commonalities that all organizations will run into with a migration to NIST 800-171 Rev 3.
What Changed Between NIST 800-171 Rev 2 and NIST 800-171 Rev 3?
At the Assessment Objective (AO), when you look at the differences between NIST 800-171 Rev 2 and NIST 800-171 Rev 3 you will find:
- MINIMAL EFFORT - Approximately one-third (1/3) of the NIST 800-171 Rev 3 AOs should require minimal effort, due to clear and direct mapping to NIST 800-171 Rev 2 AOs;
- MODERATE EFFORT - Approximately one-fifth (1/5) of the NIST 800-171 Rev 3 AOs will require a moderate effort, due to indirect mapping to NIST 800-171 Rev 2 AOs; and
- SIGNIFICANT EFFORT - Approximately half (1/2) of the NIST 800-171 Rev 3 AOs will require a significant effort, due to either (1) no clear mapping to NIST 800-171 Rev 2 AOs or (2) the AOs are new to NIST 800-171 Rev 3.
Prioritized Steps To Implement NIST SP 800-171 Rev 3
Based on the NIST 800-171 R3 Kill Chain, there are twenty-two (22) prioritized phases an organization should take to implement NIST 800-171 Rev 3. It is important to note that this transition plan to NIST 800-171 Rev 3 frontloads a lot of cybersecurity governance processes, since those governance practices will help prevent controls from being reworked:
- ESTABLISH CONTEXT FOR CYBERSECURITY & DATA PROTECTION. This phase has four (4) sub-components:
- Define the organization's applicable statutory, regulatory and contractual obligations for cybersecurity and data protection (e.g., DFARS, FAR, ITAR, etc.).
- Define what Controlled Unclassified Information (CUI) and/or Federal Contract Information (FCI) is for your specific business case (based on the contract).
- Identify the necessary People, Processes, Technology, Data & Facilities (PPTDF) that are necessary and appropriately sized.
- Develop & implement a resource plan (e.g., business plan, budget, road map, etc.) to meet the organization's unique compliance obligations.
- IMPLEMENT GOVERNANCE PRACTICES. This phase has two (2) sub-components:
- Develop, implement and maintain policies and standards to address applicable statutory, regulatory and contractual obligations.
- Prioritize objectives from the resource plan for People, Processes, Technology, Data & Facilities (PPTDF) requirements.
- ESTABLISH THE COMPLIANCE SCOPE. This phase has five (5) sub-components:
- Create a Data Flow Diagram (DFD) that shows how CUI flows from the DoD all the way down to subcontractors.
- Create and maintain a detailed asset inventory for all systems, applications and services for both in-scope and out-of-scope assets.
- Create a detailed network diagram that includes where CUI is stored, transmitted and/or processed.
- Inventory External Service Providers (ESP) to determine ESP access to CUI and/or in-scope systems, applications and/or services.
- Define roles and responsibilities for internal and external systems, applications and services.
- RISK MANAGEMENT PRACTICES. This phase has five (5) sub-components:
- Develop & implement an organization-wide Risk Management Program (RMP) to identify, assess and remediate risk. POA&M deficiencies to prioritize, resource and remediate.
- Document and maintain a Cybersecurity Supply Chain Risk Management (C-SCRM) Plan that is specific to the CUI environment.
- Develop and implement acquisition strategies, contract tools, and procurement methods to operationalize the C-SCRM Plan
- Enforce C-SCRM requirements across the supply chain.
- Establish a process for identifying and addressing weaknesses or deficiencies in the supply chain elements and processes.
- DOCUMENT THE CUI AND/OR FCI ENVIRONMENT. This phase has three (3) sub-components:
- Start populating the System Security Plan (SSP). POA&M deficiencies to prioritize, resource and remediate.
- Create and maintain a Plan of Action & Milestone (POA&M) to track and remediate deficiencies.
- Perform a gap assessment from applicable statutory, regulatory and contractual obligations. POA&M deficiencies to prioritize, resource and remediate.
- IDENTIFY COMPLIANCE STAKEHOLDERS. This has two subcomponent steps:
- Identify compliance stakeholders (including control owners and control operators) and formally assign those individuals roles and responsibilities. From a governance perspective, this can be simplified in a Responsible, Accountable, Supporting, Consulted and Informed (RASCI) matrix.
- Work with Human Resources (HR) to ensure personnel security requirements are integrated into HR operations. POA&M deficiencies to prioritize, resource and remediate.
- Define and implement processes to securely handle CUI wherever CUI is stored, processed and/or transmitted
- Ensure control owners / operators develop, implement and maintain procedures to operationalize the organization's policies & standards.
- POA&M deficiencies to prioritize, resource and remediate.
- DATA PROTECTION PRACTICES. This involves developing and implementing data protection practices to limit logical and physical access to CUI and/or FCI. POA&M deficiencies to prioritize, resource and remediate.
- SEGMENTED NETWORK ARCHITECTURE. This involves implementing a network architecture that ensures it is built on secure engineering principles and enclaves to protect sensitive information (e.g., FCI/CUI). POA&M deficiencies to prioritize, resource and remediate.
- CHANGE MANAGEMENT (CM). This involves developing and implementing Change Management (CM) practices, including a Change Control Board (CCB). POA&M deficiencies to prioritize, resource and remediate.
- INCIDENT RESPONSE (IR). This involves developing and implementing Incident Response (IR) capabilities to detect, respond and recover from incidents (e.g., Incident Response Plan (IRP)). POA&M deficiencies to prioritize, resource and remediate.
- SITUATIONAL AWARENESS (SA). This involves developing and implementing Situational Awareness (SA) capabilities through threat intelligence, log collection and analysis (e.g., SIEM, XDR, etc.). POA&M deficiencies to prioritize, resource and remediate.
- SECURE BASELINE CONFIGURATIONS (SBC). This involves developing and implementing Secure Baseline Configurations (SBC) (e.g., hardening standards) for all technology platforms (e.g., servers, workstations, network gear, applications, databases, etc.). POA&M deficiencies to prioritize, resource and remediate.
- IDENTITY & ACCESS MANAGEMENT (IAM). This involves developing and implementing Identity & Access Management (IAM) capabilities to address "least privilege" and Role-Based Access Control (RBAC). POA&M deficiencies to prioritize, resource and remediate.
- PROACTIVE MAINTENANCE. This involves developing and implementing proactive maintenance practices. POA&M deficiencies to prioritize, resource and remediate.
- ATTACK SURFACE MANAGEMENT (ASM). This involves developing and implementing Attack Surface Management (ASM) practices to identify and remediate vulnerabilities. POA&M deficiencies to prioritize, resource and remediate.
- IT ASSET MANAGEMENT (ITAM). This involves developing and implementing IT Technology Asset Management (ITAM) practices. POA&M deficiencies to prioritize, resource and remediate.
- LAYERED NETWORK DEFENSES. This involves developing and implementing layered network security for Defense-in-Depth (DiD) practices. POA&M deficiencies to prioritize, resource and remediate.
- BUSINESS CONTINUITY & DISASTER RECOVERY (BC/DR). This involves developing and implementing Business Continuity / Disaster Recovery (BC/DR) capabilities. POA&M deficiencies to prioritize, resource and remediate.
- CRYPTOGRAPHIC KEY MANAGEMENT. This involves developing and implementing cryptographic key management and data encryption capabilities. POA&M deficiencies to prioritize, resource and remediate.
- PHYSICAL SECURITY. This involves developing and implementing physical security practices. POA&M deficiencies & document procedures.
- SECURITY AWARENESS TRAINING. This involves developing and implementing training & awareness to ensure a security-minded workforce. POA&M deficiencies & document procedures. POA&M deficiencies to prioritize, resource and remediate.
- INTERNAL AUDIT (IA). This involves developing and implementing an "internal audit" or Information Assurance (IA) capability to govern controls. POA&M deficiencies & document procedures. POA&M deficiencies to prioritize, resource and remediate.
What Is NIST SP 800-171 Rev 3?
NIST SP 800 171 Rev 3 is the third iteration of the NIST SP 800-171 series of documents and was released on 14 May 2024. This new release contains significant changes from NIST 800-171 Rev 2. While there is a significant increase in the volume of controls between NIST 800-171 R2 and NIST 800-171 R3, the transition is far more complicated than just looking at simple control counts. What matters in NIST 800-171 / CMMC compliance is the implementation of the controls at the AO level. Additionally, the governance component of Non-Federal Organization (NFO) controls were incorporated into new CUI controls in NIST 800-171 R3.
| Types of Controls |
NIST SP 800-171 Rev 2 |
NIST SP 800-171 Rev 3 |
| CUI |
110 |
97 (core requirements)
287 (discrete requirements)
|
| NFO |
61 |
0 |
There is a roughly 11% drop in the number of CUI controls, but the actual number of discrete requirements under the NIST 800-171 R3 CUI controls is 287, which represents an increase of 177 discrete requirements (260% increase). Additionally, NIST 800-171A R3 has a 59% increase in the number of unique requirements at the AO level.
| Assessment Objectives (AOs) |
NIST SP 800-171A |
NIST SP 800-171A Rev 3 |
| CUI |
320 |
510 |
| NFO |
0 |
+59% |
What Types of Controls Does NIST 800-171 Rev 3 Cover?
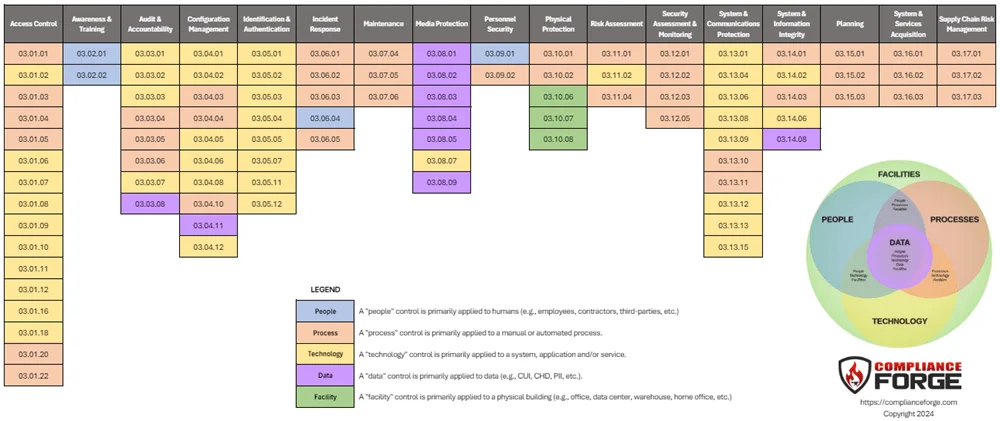
The graphic show below helps depict NIST 800-171 Rev 3 requirements from People, Process, Technology, Data and Facility (PPTDF) perspective. This can help better visualize what the various requirements are (e.g., administrative, technical solutions, configurations, etc.). You can download the PDF version here and you can read more about the concept of PPTDF here.
- PEOPLE - A "people" control is primarily applied to humans (e.g., employees, contractors, third-parties, etc.).
- PROCESS - A "process" control is primarily applied to a manual or automated process.
- TECHNOLOGY - A "technology" control is primarily applied to a system, application and/or service.
- DATA - A "data" control is primarily applied to data (e.g., CUI, CHD, PII, etc.).
- FACILITY - A "facility" control is primarily applied to a physical building (e.g., office, data center, warehouse, home office, etc.).