Third-Party Risk Management (TPRM) Program
Vetting suppliers, vendors and other third-parties for cybersecurity risk is no longer optional for most organizations. The reality is every company needs to conduct cybersecurity-focused Third-Party Risk Management (TPRM). However, there is a big issue - most companies do not know where to start. To help solve this issue, ComplianceForge provides an affordable, editable solution that is applicable to organizations of any size or industry.
Organizations tend to face the same challenge with TPRM, where the common options are to:
- Build TPRM documentation and questionnaires from scratch;
- Piece together free resources that lack depth, consistency and legal defensibility; or
- Leverage a “canned” TPRM module in a Governance, Risk and Compliance (GRC) platform.
Each of these three options introduces unnecessary risk. That’s why it makes sense to invest in expert-derived TPRM documentation from ComplianceForge, an industry leader in cybersecurity documentation solutions - trusted across industries for producing high-quality, professionally-written cybersecurity and compliance-focused documentation.
What Is A Third-Party Risk Management (TPRM) / Supply Chain Risk Management (SCRM) Solution?
The terms "Third-Party Risk Management" and "Supply Chain Risk Management" are often used interchangeably. In the US Government, it tends to be referred to as variants of SCRM (e.g., C-SCRM or ICT-SCRM). In private industry, it tends to be referred to as TPRM. The term used mainly depends on the industry. Regardless of the terminology used, TPRM / SCRM should be viewed as a slice of a larger risk management pie.
It is a common misunderstanding that an organization can just make up TPRM / SCRM practices in a silo and expect those to keep an organization secure, compliant or resilient. TPRM / SCRM are not functions that are able to stand alone, since they nest within an organization's broader risk management practices that define how risk is to be addressed across the entire organization, not just with third-parties.
For the average person, TPRM and SCRM are synonymous terms. However, when you get into technicalities, TPRM differs from SCRM because it focuses on risks associated with immediate third-parties (e.g., risks associated with external suppliers, external vendors, service providers, etc.), while SCRM focused on the broader view of risks associated with the entire supply chain (e.g., suppliers, vendors service providers, materials sourcing, subcontractors, geopolitical influences, etc.). While it is nuanced, there is a difference.
Cybersecurity Risk Management Framework
ComplianceForge’s cybersecurity risk management solutions range from:
- Organization-level cybersecurity Risk Management Program (RMP);
- Supply chain-focused documentation:
- Due diligence-focused TPRM Program to handle assessing and managing Third-Party Service Providers (TPSP).
These TPRM / SCRM solutions are developed by industry experts with deep experience in risk management. These materials are not generic templates - they are high-quality templates that are designed to align with leading cybersecurity frameworks and regulatory expectations. ComplianceForge documentation helps ensure that your organization’s TPRM program is defensible, audit-ready and capable of standing up to scrutiny from regulators, customers and business partners.
Enterprise Risk Management (ERM) vs Cybersecurity Risk Management vs Third-Party Risk Management (TPRM)
|
The relationship between Enterprise Risk Management (ERM), Cybersecurity Risk Management and Third-Party Risk Management (TPRM) is akin to Russian nesting dolls, also referred to as Matryoshka dolls, which contain a series of increasingly smaller wooden figures, each tucked securely within the other. Comparing risk management to Matryoshka dolls, the TPRM would be the smallest doll, since it deals specifically with third-party risk associated with vendors, suppliers, and partners. Cybersecurity risk management would be the next layer of Matryoshka dolls, since it deals with risk associated with protecting information, systems, and technology assets. Finally, ERM is the outermost Matryoshka doll, because in addition to encompassing both cybersecurity risk management and TPRM, it goes beyond and deals with organizational risk, including financial, operational, strategic, reputational, regulatory, and more. Just like with nesting dolls, you can’t get to the innermost layer without considering the outer ones. If the outermost doll is cracked, every layer inside is exposed to risk. In other words, this means that if the supply chain is compromised, the organization itself will be impacted. |
 |
TPRM Is More Than Just A Risk Assessment Questionnaire
Third-Party Risk Management (TPRM) is more than just a risk assessment questionnaire because. In addition to the risk assessment questionnaire being a key component, TPRM also focuses on the entirety of the third-party risk management lifecycle.
With ComplianceForge, you can obtain not just a risk questionnaires that maps directly to authoritative frameworks like NIST, ISO and the Secure Controls Framework (SCF), but you get a process that makes sense to govern the lifecycle of the contract. The TPRM Program documentation provides the basis an organization needs to establish a scalable and dynamic TPRM capability. This provides your organization with a clear line of sight between requirements, controls and vendor due diligence.
The benefit is two-fold:
- Accelerated Readiness. Instead of spending months developing your own program, you can rapidly operationalize a robust SCRM solution built on proven best practices.
- Credibility & Consistency. Third-party vendors take questionnaires more seriously when they see that the assessment is based on a professional, standards-based framework rather than an improvised spreadsheet.
Why You Should Take A Phased Approach To Third-Party Risk Management (TPRM)
A phased approach to governing the TPRM lifecycle is considered a best practice, since business relationships follow a lifecycle, where there is a beginning, middle and an end. This phased approach to TPRM involves:
This concept mirrors the lifecycle of a vendor relationship while ensuring that risk is managed consistently, proportionately and in alignment with an organization’s compliance obligations. Each phase plays a distinct role and taken together, they provide a structured, repeatable and defensible framework for vendor due diligence. |
 |
How Much Customization Is Remaining?
Regardless of where you buy a template from, there will always be some need to tailor the documentation for your specific needs. The reason for this is only you know the specific technologies and resources available to perform TRPM activities. However, we designed the TPRM template to be approximately a "80% solution" where we did all the heavy lifting and you just need to tailor it with details that only you know. ComplianceForge does offer consulting services, so we can help with that finalization if you need assistance - it is what we do, so we would be happy to help you.

What Problems Does The TPRM Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The TPRM is an efficient method to obtain comprehensive risk management documentation for your organization!
- Compliance Requirements - Requirements such as PCI DSS, HIPAA, MA 201 CMR 17.00 and NIST 800-171 establish a mandate to formally manage risk. The TPRM addresses these compliance requirements!
- Audit Failures - Similar to vulnerability management, most organizations run into trouble in audits when asked HOW risk is managed, since they cannot provide documentation beyond policies and standards. The TPRM addresses the HOW for you!
- Vendor Requirements - It is very common for clients and partners to request evidence of a risk management program during their due diligence. The TPRM provides this evidence!
How Does The TPRM Solve These Problems?
- Clear Documentation - The TPRM provides the comprehensive documentation to prove that your risk program exists.
- Time Savings - The TPRM provides actionable guidance on what steps can be taken to categorize, calculate and manage risk in a sustainable manner.
- Alignment With Leading Practices - The TPRM is written to support COSO, COBIT, NIST and ISO frameworks that provide you with significant flexibility.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The TPRM is an editable Microsoft Word document that providers program-level guidance to directly supports your organization's policies and standards for managing cybersecurity risk. Unfortunately, most companies lack a coherent approach to managing risks across the enterprise:
- When you look at getting audit ready, your policies and standards only cover the "why?" and "what?" questions of an audit. This product addresses the “how?” questions for how your company manages risk.
- The TPRM provides clear, concise documentation that provides a "paint by numbers" approach to how risk is managed.
- The TPRM addresses fundamental needs when it comes to what is expected in cybersecurity risk management:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential the impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The TPRM is based on leading frameworks, such as NIST Risk Management Framework (NIST 800-37 rev2), NIST 800-39, ISO 31010 and COSO 2013.
Why Is ComplianceForge's TPRM Template The Best Available?
ComplianceForge’s TPRM Program template is the best solution, since it offers actionable guidance you can follow. This enables you to build a TPRM program since it includes a TPRM policy, a phased approach to managing Third-Party Service Providers (TPSP) across the entire vendor lifecycle and a TPRM questionnaire that you can use to assess TPSP. In other words, ComplianceForge’s TPRM Program offers the entire pie for TPRM, unlike other companies who offer only a single piece of the pie.
Product Example - TPRM Program Template
Regardless if your cybersecurity program aligns with NIST, ISO, SCF, CIS or another framework, the TPRM is designed to address the strategic, operational and tactical components of third-party risk management to provide cybersecurity risk management governance. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW risk is actually managed. The TPRM provides this middle ground between high-level policies and the actual procedures of how risk is managed on a day-to-day basis by those individual contributors who execute risk-based controls.
If you would like to view examples of ComplianceForge's Third-Party Risk Management (TPRM) Program, please click the image below:
Cost Savings Estimate - Third-Party Risk Management (TPRM) Program
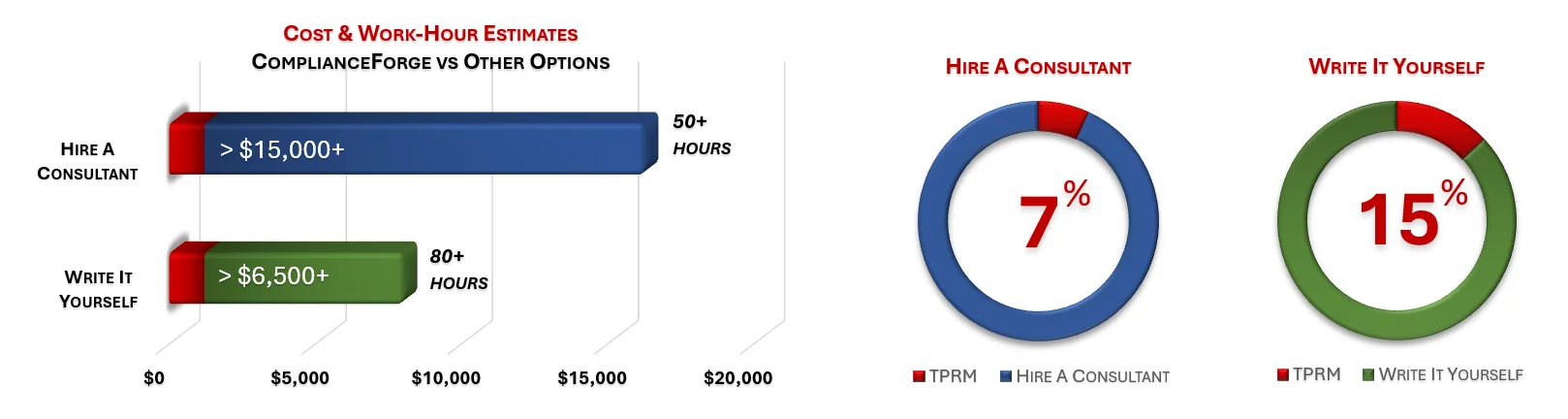
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the TPRM from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 80 internal staff work hours, which equates to a cost of approximately $8,000 in staff-related expenses. This is about 2-3 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 50 consultant work hours, which equates to a cost of approximately $20,000. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- The TPRM is approximately 7% of the cost for a consultant or 15% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the TPRM the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the TPRM! |
|
|
Cybersecurity Third-Party Risk Management (TPRM) Program Framework - Based on NIST 800-37 Rev2, COSO, COBIT & ISO 31010 Best Practices!
The TPRM is an editable Microsoft Word document that contains the requirements needed to establish a risk management program. Quite simply, the Cybersecurity Third-Party Risk Management (TPRM) Program provides your company with evidence that a documented vendor risk management program exists to address operational risks associated with information and technology. The TPRM addresses the due care component of getting an organization to a mature level for managing risk:
- Determine the Potential Likelihood of Threat Occurrence. Organizations must take into account the probability of potential risks, since that identifies the legitimate threat landscape. The results of this assessment, combined with the initial list of threats, will influence the determination of which threats require protection against because those are “reasonably anticipated” based on your unique situation.
- Determine the Potential Impact of Threat Occurrence. Organizations must consider the “criticality,” or impact, of potential risks to confidentiality, integrity, and availability of their data and information systems. Not all systems are equal – some systems could go down and no one would be impacted, but some systems could bring your business operations to an immediate halt. The TPRM helps assess the magnitude of the potential impact resulting from a threat triggering or exploiting a specific vulnerability. This can be qualitative, quantitative or a combination of the two methods to measure the impact on your organization.
- Determine the Level of Risk. From likelihood and potential impact, organizations can assign risk levels for all threat and vulnerability combinations identified during the risk analysis. The TPRM allows you to assign a level of risk by analyzing the values assigned to the likelihood of threat occurrence and resulting impact of threat occurrence.
The Cybersecurity Third-Party Risk Management (TPRM) Program provides best-practices guidance on risk management at the strategic, operational and tactical levels! This is important, since this hybrid or "best of breed" approach to third-party risk management takes advantage of the strengths of each best practice model (e.g., COSO, COBIT, ISO & NIST). This allows you to have a considerable amount of flexibility to conduct risk management operations.
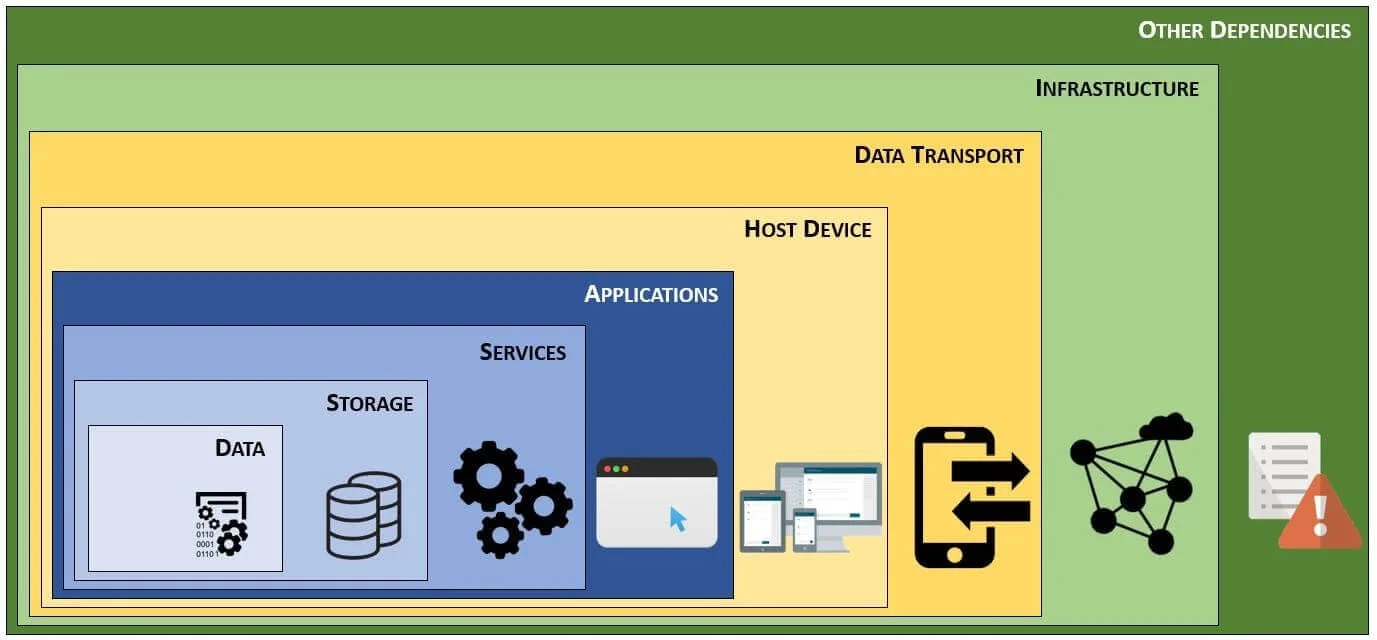
Make Assessing Risk More Efficient - Understanding Layers of Risk
Dependencies are of critical importance when assessing risk, since risk can have a cascading effect. Ideally, a risk assessment at a tactical level (e.g., assessment of a specific application or host) should leverage existing risk assessments that address “upstream” risks.
|
For example, a well-designed and securely-coded application could be compromised if the host system it is running on is insecure. Similarly, the application could be made unavailable if the datacenter lacks measures to ensure uptime against natural or man-made threats. As part of overall risk management, your company should perform several formal risk assessments, which are meant to be used as references for more detailed project-specific risk assessments. At a minimum, risk assessments should exist for commonly-leveraged aspects of your company's IT environment:
By being able to leverage those existing risk assessments, it will allow for more efficient assessments of applications. The TPRM helps build this foundation for efficient risk management by framing risk according to the following concepts: |
|
|
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.