Secure Engineering & Data Privacy
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the SEDP is to help answer common questions we receive.
What Is The Secure Engineering & Data Privacy (SEDP) Program?
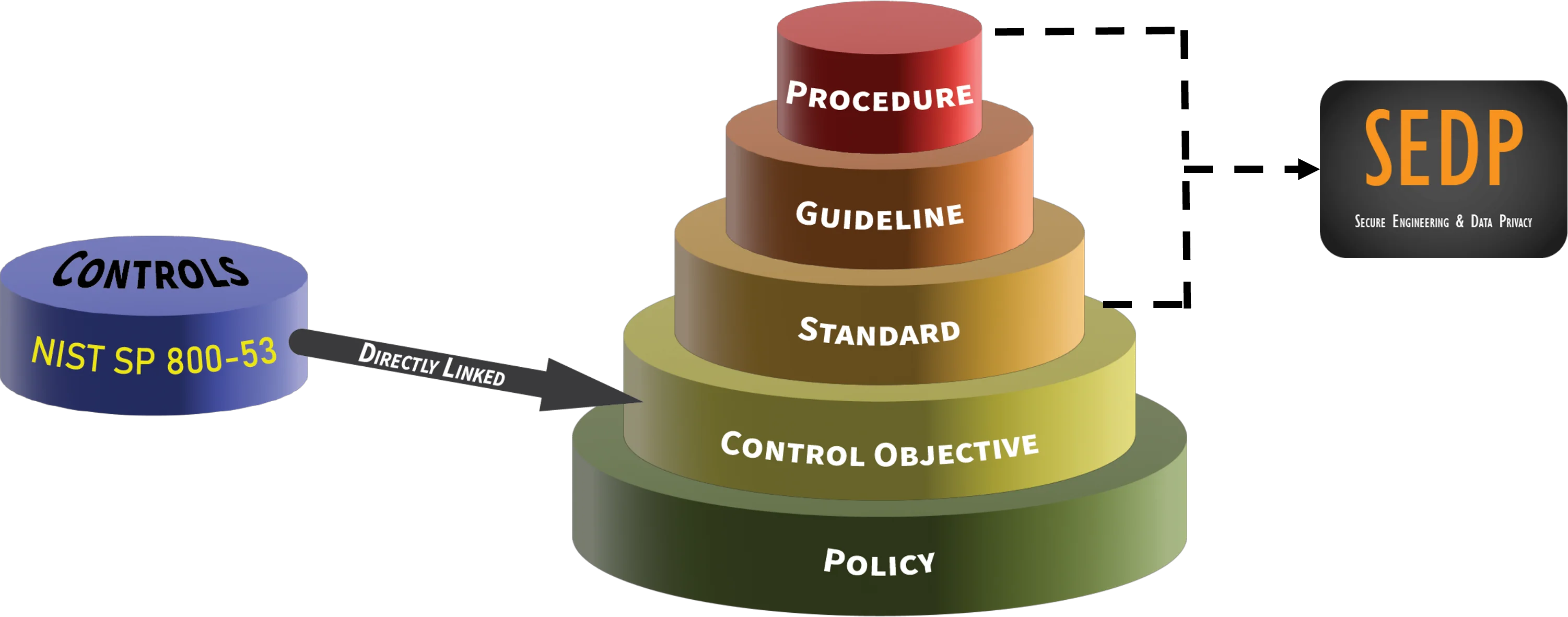
With the European Union General Data Protection Regulation (EU GDPR) effective in 2016 and the California Consumer Privacy Act (CCPA) of 2020, which is now the California Privacy Rights Act (CPRA), companies have an obligation to demonstrate they implement both Security by Design (SbD) and Privacy by Design (PbD). Unfortunately, most businesses lack the knowledge and experience to undertake such documentation efforts. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with this compliance requirement. In either situation, it is not a good place to be. The good news is that ComplianceForge developed a viable cybersecurity and privacy program that is based on NIST 800-160 guidance for security by design and OASIS for privacy by design.
The SEDP Program is designed to support your company’s existing policies and standards. Our solution is focused at the procedural and guideline levels, where it straddles the territory between an organization's centrally-managed policies/standards and its decentralized, stakeholder-executed procedures. The SEDP Program serves as expert-level guidance that is meant to run a specific capability or function within an organization's cybersecurity department to help communicate user needs and system characteristics to developers, integrators, sponsors, funding decision makers and other stakeholders.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The SEDP Program comes in both editable Microsoft Word and Excel formats. The SEDP Program is capable of scaling for any sized company.
- The SEDP Program is an editable Microsoft Word document that providers program-level guidance to directly supports your company's policies and standards for ensuring secure engineering and privacy principles are operationalized.
- This product addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- It is a reality that most companies have either weak or non-existent guidance on how security or privacy principles are implemented.
- The lack of operationalized security & privacy principles can lead to compliance deficiencies with many statutory, regulatory and contractual obligations.
- NIST 800-160 is the "gold standard" on how to build security into the System Development Life Cycle (SDLC)
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements.
- The SEDP Program provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The Integrated Incident Response Plan (IIRP) is based on numerous frameworks, but the core principles are based on NIST 800-160 and the Generally Accepted Privacy Principles (GAPP) which are the de facto standards on security and privacy design principles.
The SEDP Program Excel checklists provide a wealth of experience to bake in security and privacy principles by establishing methodical and repeatable processes.
- Logically-organized phases
- Task focus (How tasks support the lifecycle phases)
- Task #
- Activity Description
- Reasonable Task Deliverables
- Mapping to leading practices:
- NIST 800-160 R1
- NIST 800-53
- ISO 27002
- OASIS PMRM
- Level of Effort (expectation for basics or enhanced requirements)
- Stakeholder RACI Matrix (Responsible, Accountable, Consulted, Informed)
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
What Problems Does The SEDP Program Solve?
- Lack of In House Security Experience - Writing cybersecurity & privacy documentation is a skill that most cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive procedure documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The SEDP Program is an efficient method to obtain comprehensive guidance documentation to implement cybersecurity and privacy principles within your organization!
- Compliance Requirements - EU GDPR requires companies that store, process or transmit the personal information of EU citizens to ensure that both cybersecurity and privacy principles are built into processes by default. Can you prove how cybersecurity & privacy principles are implemented?
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The SEDP Program provide mapping to leading security and privacy frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies, standards and procedures. With EU GDPR, vendors and other partners will be expected to demonstrate evidence of compliance with the EU GDPR.
Please keep in mind that security & privacy engineering principles are widely expected activities:
- European Union General Data Protection Regulation (EU GDPR)
- NIST 800-53
- NIST Cybersecurity Framework
- ISO 27002
- Defense Federal Acquisition Regulations Supplement (DFARS) 252.204-7012 (NIST 800-171)
- Federal Acquisition Regulations (FAR) 52.204-21 - 4
- National Industrial Security Program Operating Manual (NISPOM)
- SOC2
- New York State Department of Financial Service (DFS)
- Payment Card Industry Data Protection Standard (PCI DSS)
- Center for Internet Security Critical Security Controls (CIS CSC)
- Generally Accepted Privacy Principles (GAPP)
How Does The SEDP Program Solve These Problems?
- Clear Documentation - The SEDP Program provides a comprehensive approach to operationalizing both cybersecurity and privacy principles. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The SEDP Program can provide your organization with a templated solution that requires minimal resources to fine tune for your organization's specific cybersecurity and privacy needs.
- Alignment With Leading Practices - The SEDP Program is written to support leading cybersecurity and privacy frameworks!
The SEDP Program can serve as a foundational element in your organization's privacy program. It can stand alone or be paired with other specialized products we offer.
Cybersecurity and privacy do not need to be hard. The Secure Engineering & Data Privacy (SEDP Program) document is meant to simplify how security and privacy can be operationalized in a “paint by numbers” approach. This product is comprised of editable Microsoft Word and Excel documentation so you can customize it for your specific needs.
Product Example - Secure Engineering & Data Privacy (SEDP Program)
The SEDP Program addresses program-level guidance on HOW to actually manage cybersecurity and privacy principles, so that secure processes are designed and implemented by default. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW privacy and security principles are actually planned and managed. The SEDP Program provides this middle ground between high-level policies and the actual procedures of how developers, PMs, system integrators and system admins do their jobs to design, implement and maintain technology solutions.
View Product Examples
If you would like to view examples of ComplianceForge's Secure Engineering & Data Privacy (SEDP) program, please click any of the images below:
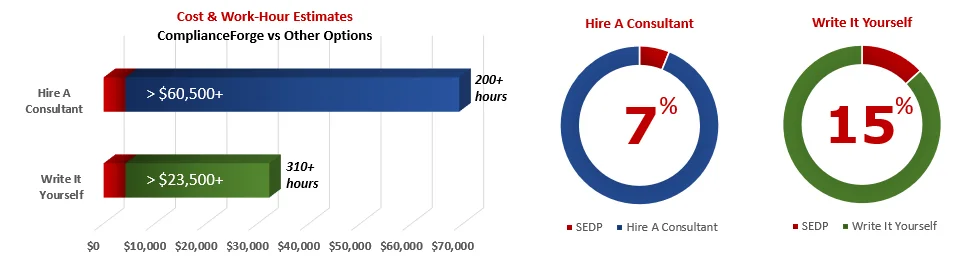
Cost Savings Estimate - Secure Engineering & Data Privacy (SEDP Program)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the SEDP Program from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 310 internal staff work hours, which equates to a cost of approximately $28,000 in staff-related expenses. This is about 4-8 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 200 consultant work hours, which equates to a cost of approximately $65,000. This is about 3-4 months of development time for a contractor to provide you with the deliverable.
- The SEDP Program is approximately 7% of the cost for a consultant or 15% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the SEDP Program the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the SEDP! |
|
|
Secure Engineering & Data Privacy - Program Level Privacy & Security Documentation
Reducing Risk Through Cybersecurity For Privacy by Design (C4P)
The Secure Engineering & Data Privacy (SEDP) document supports your company’s existing policies and standards. Our solution is focused at the procedural and guideline levels. The SEDP Program document is focused on understanding risk associated with cybersecurity and privacy so that risk can be:
- Reduced;
- Avoided;
- Transferred; or
- Accepted.
Implementing both Security by Design (SbD) and Privacy by Design (PbD) principles is a systematic way to find and address weaknesses, flaws and risks to your company.
- Repeatable, methodical processes that seek out both security and privacy risk reduces the chance of surprises.
- Addressing security issues in an orderly manner gives your company a better assurance that gaps have been closed properly and as quickly as possible.
Work Smarter! Leverage Common Touch Points Between Cybersecurity & Privacy
|
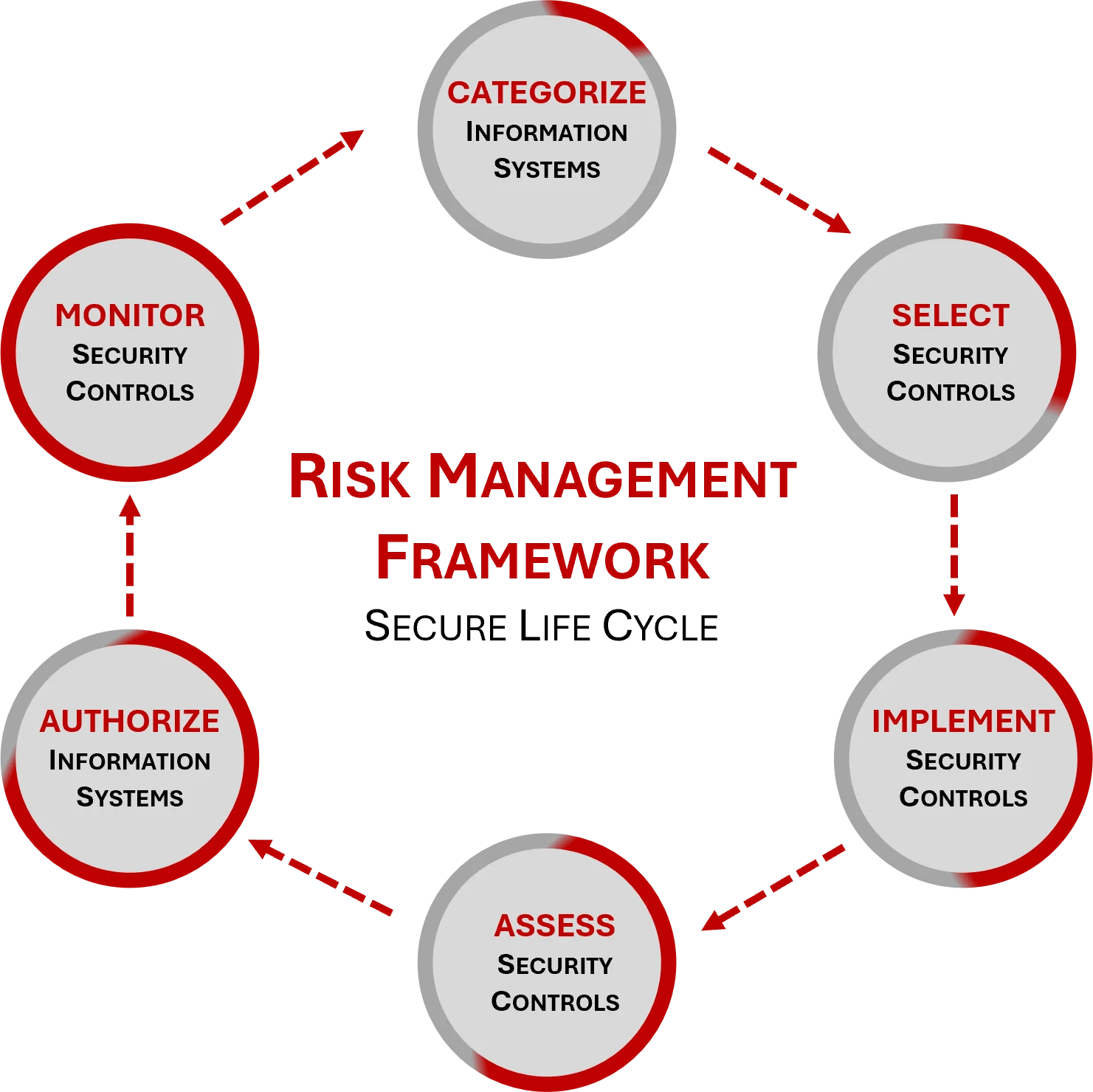
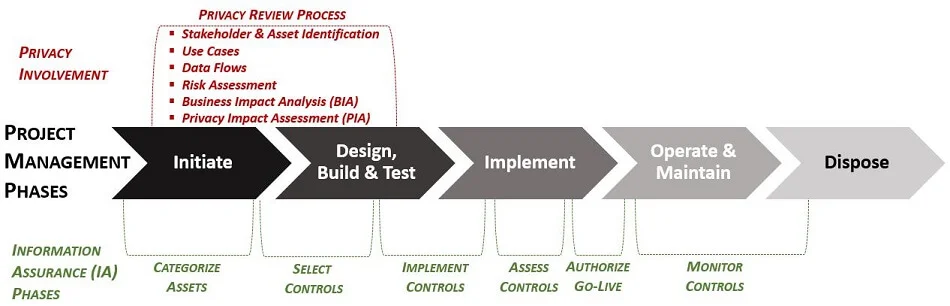
Systems security engineering delivers systems deemed adequately secure by stakeholders. The fundamental relationships among assets, an asset-dependent interpretation of loss, and the corresponding loss consequences are central to any discussion of system security. This is where aligning your company’s Security by Design (SbD) efforts with the Risk Management Framework (RMF) (e.g., NIST 800-37) can be very beneficial, since the RMF provides a well-established format to securely engineer and maintain systems throughout the entire life cycle of the asset. Utilizing common linkages, Privacy by Design (PbD) is incorporated into the RMF cycle. The graphic to the right depicts the Risk Management Framework's Secure Life Cycle. |
|
|
Paint By Numbers - Cybersecurity & Privacy Requirements
What we've done is take on the heavy lifting to integrate security and privacy controls into standard project management processes. This allows your teams to have a "paint by numbers" approach to demonstrating that both cybersecurity and privacy principles are baked into the process! We identified the stages where both cybersecurity and privacy requirements are expected as part of project development. This can enable your teams to work more effectively together and reduce the negative effect of teams working in silos.
All too often, when projects are commenced, involvement from key stakeholders is siloed, as compared to operating as a cohesive team. We want to help your company avoid the following security & privacy pitfalls where:
- Project / application teams work in a vacuum, unaware of security or privacy concerns;
- Privacy and security conduct their own assessments without any information sharing or collaboration; and
- Security involvement is viewed as a final hurdle to overcome, just prior to “go live” for the project.
Understanding Privacy & Security Starts With Defining Requirements
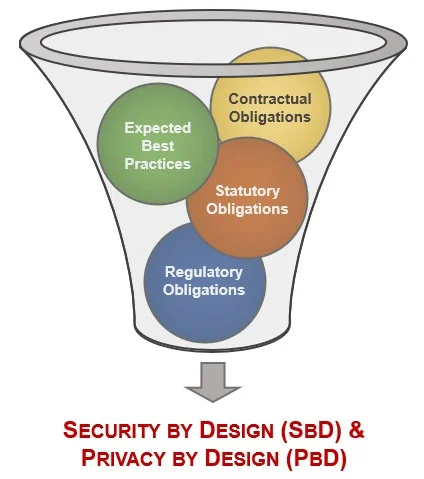
Understanding the requirements for both Security by Design (SbD) and Privacy by Design (PbD) principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations to right-size the approach, since every organization is unique:
|
 |
|
Security by Design (SbD) |
Privacy by Design (PbD)
|
|
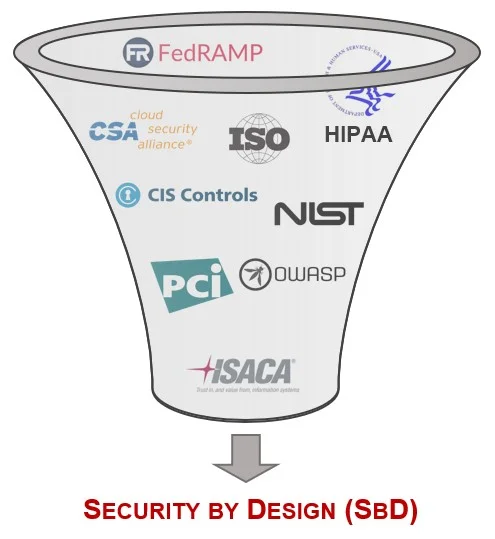
Security by Design (SbD) requirements come from numerous sources. In this context, the most important are:
|
Privacy by Design (PbD) requirements come from numerous sources. In this context, the most important are:
|
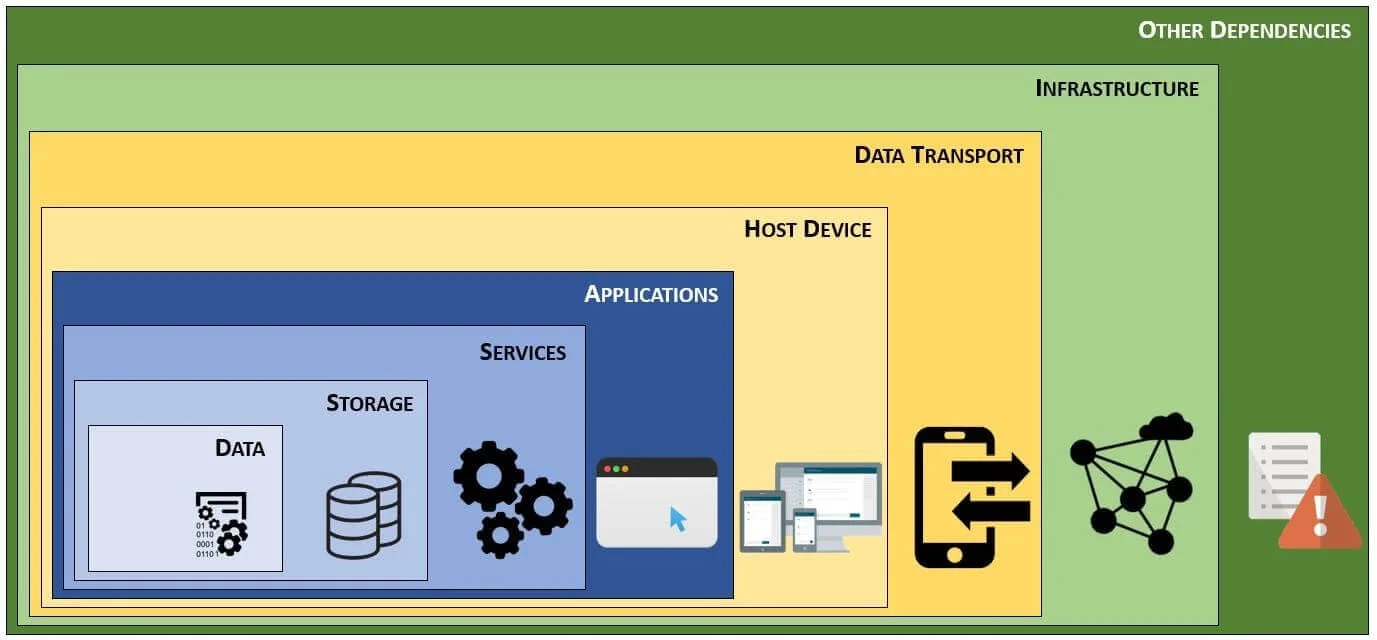
Data-Centric Security (DCS) = Defense-In-Depth Approach To Security
Thinking in terms of data, or information, it is your company’s most valuable asset. Therefore, being "data-centric" is how we approach our defense-in-depth concept. When you look at the diagram below, if you envision data protection as a set of concentric rings, at the center of the protection is your data.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.