
Secure Controls Framework (SCF) CORE Fundamentals - Policies & Standards
The Secure Controls Framework (SCF) created the Cybersecurity Oversight, Resilience and Enablement (CORE) initiative as a means to help an organization tailor cybersecurity and data protection controls for its specific needs. The SCF CORE Fundamentals, a tailored set of sixty-eight (68) controls that are specifically designed for smaller organizations to protect People, Processes, Technologies, Data and Facilities (PPTDF) against common threats. The SCF CORE Fundamentals Policies & Standards consists of:
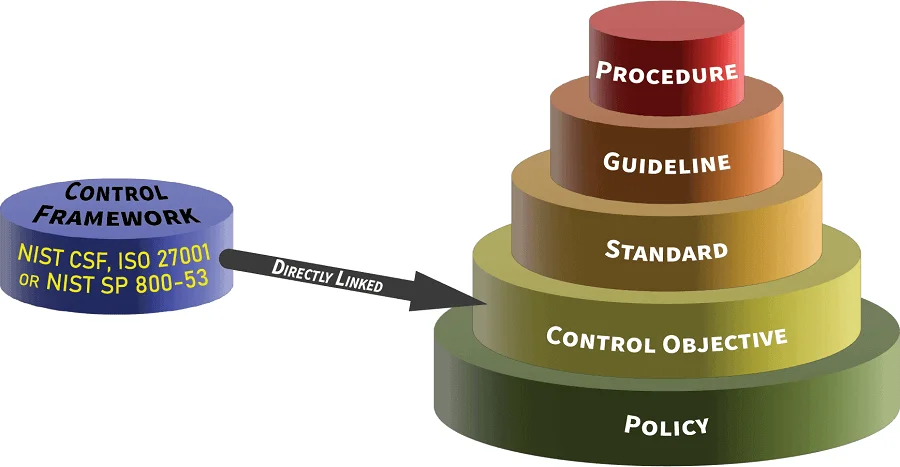
- Policies
- Control objectives
- Standards
- Guidelines
- Controls (Secure Controls Framework)
The SCF CORE Fundamentals policies & standards covers:
- Twenty (20) domains from the SCF, so there are twenty (20) policies included in the SCF CORE Fundamentals Policies & Standards.
- Sixty-eight (68) controls, so there is a standard written for each control.
Designed To Address Texas SB 2610 Compliance & State Cybersecurity Safe Harbor Laws
The genesis of the SCF CORE Fundamentals came from Texas SB 2610 that named the SCF as one of a select few cybersecurity frameworks with adequacy to provide necessary security coverage. The SCF created the SCF CORE Fundamentals as a SMB-focused control set to address this law and others that may follow. Texas SB 2610 is latest in a line of US State-level “cybersecurity safe harbor” laws that provide legal protection for businesses if at the time of the incident the business can prove it implemented reasonable cybersecurity practices. This type of legislation is meant to encourage SMBs to invest in cybersecurity to reduce legal exposure and this incentivization can enhance business resilience that benefits the everyone.
The controls in the SCF CORE Fundamentals are scoped for SMBs and are designed to meet the requirements in Texas SB 2610:
- Contain administrative, technical, and physical safeguards for the protection of personal identifying information and sensitive personal information (Section 542.004(1));
- Protect the security of personal identifying information and sensitive personal information (Section 542.004(3)(a));
- Protect against any threat or hazard to the integrity of personal identifying information and sensitive personal information (Section 542.003(4)(b)); and
- Protect against unauthorized access to or acquisition of personal identifying information and sensitive personal information that would result in a material risk of identity theft or other fraud to the individual to whom the information relates (Section 542.004(3)(c)).
Implementing cybersecurity has to be attainable for Small and Medium Businesses (SMB) and the SCF CORE Fundamentals is designed to enable SMBs to successfully implement and maintain fundamental cybersecurity practices. This control set includes many of the requirements found in the NIST Cybersecurity Framework 2.0 (NIST CSF 2.0), so the SCF CORE Fundamentals can be an excellent starting point towards a path of maturity towards NIST CSF 2.0 alignment. SMBs have to start somewhere and the SCF CORE Fundamentals makes for an achievable objective in cybersecurity.


ComplianceForge Is A SCF Licensed Content Provider (SCF LCP)
|
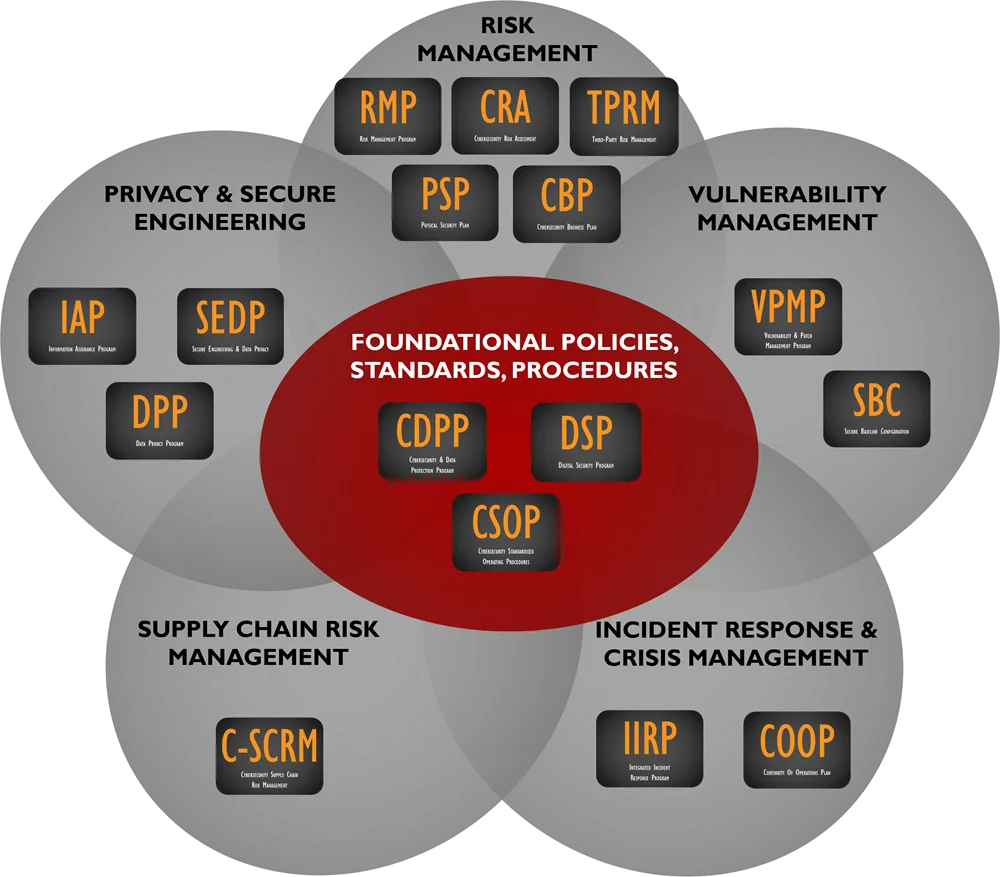
ComplianceForge is a Licensed Content Provider (LCP) by the SCF. This means ComplianceForge is authorized to sell cybersecurity and data protection policies, standards and procedures based on SCF controls. The CORE Fundamentals' policies & standards have direct, 1-1 mapping to the SCF's controls. The CORE Fundamentals leverages several key SCF components to provide “more than just policies & standards” by incorporating maturity criteria, a threat catalog, a risk catalog and more! The CORE Fundamentals provides invaluable content to operationalize several of the SCF's notable capabilities: |
|
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "90% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The CORE Fundamentals Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The CORE Fundamentals is an efficient method to obtain comprehensive security policies, standards, controls and metrics for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security policies and standards. Requirements range from PCI DSS to HIPAA to NIST 800-171. The CORE Fundamentals is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The CORE Fundamentals' standards provides mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies and standards. The CORE Fundamentals provides this evidence!
How Does the CORE Fundamentals Solve These Problems?
- Clear Documentation - The CORE Fundamentals provides comprehensive documentation to prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The CORE Fundamentals can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The CORE Fundamentals is written to support over one hundred laws, regulations and industry frameworks!
SCF CORE Fundamentals Policies & Standards
The CORE Fundamentals provides the following editable policies & standards:
- Cybersecurity & Data Protection Governance Policy (GOV)
- GOV-02. Publishing Cybersecurity & Data Protection Documentation
- GOV-04. Assigned Cybersecurity & Data Protection Responsibilities
- GOV-15. Operationalizing Cybersecurity & Data Protection Practices
- Asset Management Policy (AST)
- AST-02. Asset Inventories
- AST-02.8. Data Action Mapping
- AST-04. Network Diagrams & Data Flow Diagrams (DFDs)
- AST-09. Secure Disposal, Destruction or Re-Use of Equipment
- AST-16. Bring Your Own Device (BYOD) Usage
- Business Continuity & Disaster Recovery Policy (BCD)
- BCD-04. Contingency Plan Testing & Exercises
- BCD-11. Data Backups
- Change Management Policy (CHG)
- CHG-02. Configuration Change Control
- CHG-03. Security Impact Analysis for Changes
- Cloud Security Policy (CLD)
- CLD-01. Cloud Services
- CLD-10. Sensitive Data In Public Cloud Providers
- Compliance Policy (CPL)
- CPL-01. Statutory, Regulatory & Contractual Compliance
- Configuration Management Policy (CPL)
- CFG-02. System Hardening Through Baseline Configurations
- CFG-03. Least Functionality
- Continuous Monitoring Policy (MON)
- MON-01.8. Security Event Monitoring
- MON-03. Content of Event Logs
- MON-16. Anomalous Behavior
- Cryptographic Protections Policy (CRY)
- CRY-03. Transmission Confidentiality
- CRY-05. Encrypting Data At Rest
- CRY-09. Cryptographic Key Management
- Data Classification & Handling Policy (DCH)
- DCH-01.2. Sensitive / Regulated Data Protection
- DCH-01.4. Defining Access Authorizations for Sensitive/Regulated Data
- DCH-02. Data & Asset Classification
- DCH-13. Use of External Information Systems
- DCH-17. Ad-Hoc Transfers
- Endpoint Security Policy (END)
- END-04. Malicious Code Protection (Anti-Malware)
- END-08. Phishing & Spam Protection
- Human Resources Security Policy (HRS)
- HRS-04. Personnel Screening
- HRS-05. Terms of Employment
- Identification & Authentication Policy (IAC)
- IAC-01.3. User & Service Account Inventories
- IAC-06. Multi-Factor Authentication (MFA)
- IAC-07. User Provisioning & De-Provisioning
- IAC-08. Role-Based Access Control (RBAC)
- IAC-10. Authenticator Management
- IAC-10.8. Default Authenticators
- IAC-15. Account Management
- IAC-16. Privileged Account Management (PAM)
- IAC-17. Periodic Review of Account Privileges
- IAC-21. Least Privilege
- Incident Response Policy (IRO)
- IRO-02. Incident Handling
- IRO-04. Incident Response Plan (IRP)
- Network Security Policy (NET)
- NET-02. Layered Network Defenses
- NET-02.2. Guest Networks
- NET-03. Boundary Protection
- NET-04. Data Flow Enforcement – Access Control Lists (ACLs)
- NET-14. Remote Access
- NET-14.5. Work From Anywhere (WFA) - Telecommuting Security
- NET-15. Wireless Networking
- NET-18. DNS & Content Filtering
- Physical & Environmental Security Policy (PES)
- PES-02. Physical Access Authorizations
- PES-03. Physical Access Control
- PES-06. Visitor Control
- Risk Management Policy (RSK)
- RSK-03. Risk Identification
- RSK-04. Risk Assessment
- RSK-04.1. Risk Register
- RSK-06. Risk Remediation
- Security Awareness & Training Policy (SAT)
- SAT-02. Cybersecurity & Data Privacy Awareness Training
- Third-Party Management Policy (TPM)
- TPM-01.1. Third-Party Inventories
- TPM-03. Supply Chain Risk Management (SCRM)
- TPM-05. Third-Party Contract Requirements
- TPM-05.4. Responsible, Accountable, Supportive, Consulted & Informed (RASCI) Matrix
- TPM-08. Review of Third-Party Services
- Vulnerability & Patch Management Policy (VPM)
- VPM-02. Vulnerability Remediation Process
- VPM-05. Software & Firmware Patching
- VPM-06. Vulnerability Scanning
Small Business Cybersecurity & Data Privacy Policies, Standards & Controls - Hierarchical & Scalable!
ComplianceForge provides organizations with exactly what they need to protect themselves - professionally written cybersecurity policies, control objectives, standards, controls, procedures and guidelines at a very affordable cost. The CORE Fundamentals can be found in smaller organizations within unregulated industries that do not need to comply with more of the rigorous requirements within certain laws.
The CORE Fundamentals is footnoted to provide authoritative references for the statutory, regulatory and contractual requirements that need to be addressed. Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the CORE Fundamentals does this from a cybersecurity perspective.
The CORE Fundamentals Procedures is available that provides mapped procedures to the CORE Fundamentals' standards. This is a 1-1 mapping with a procedure for each standard.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CORE Fundamentals! |
|
|
Small & Medium Business (SMB) Tailored Cybersecurity Documentation
Unlike some of our competition that sell “bronze, silver and gold” levels of documentation, we understand that a standard is a standard for a reason. We take out the guesswork associated with picking an appropriate package level - we focus on providing documentation that offers a straightforward solution to provide the appropriate coverage you need. This focus on providing the best solution for our clients makes us proud that we are providing the best set of IT security policies and standards available. Saving a few dollars on a cheap solution can easily leave you with a false sense of security and gaping holes in your documentation that can leave you liable.
 |
|
The CORE Fundamentals Policies & Standards can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer. This product is an editable, easily implemented document that contains the policies, standards and guidelines that your company can use to establish a cybersecurity program. Being Microsoft Word documentation, you have the ability to make edits to the documentation. Our documentation is meant to address your requirements from strategic concepts all the way down to day-to-day deliverables you need to demonstrate compliance with common statutory, regulatory and contractual obligations. We offer up to 40% discounts on our documentation bundles, so please be aware that you have benefit from significant savings by bundling the documentation you need. You can see the available bundles here. We are here to help make comprehensive cybersecurity documentation as easy and as affordable as possible. We serve businesses of all sizes, from the Fortune 500 all the way down to small businesses, since our cybersecurity documentation products are designed to scale for organizations of any size or level of complexity. Our affordable solutions range from Cybersecurity Policies & Standards documentation, to NIST 800-171 compliance checklists, to program-level documentation, such as "turn key" Incident Response, risk management or vulnerability management program documents. Our focus is on helping you become audit ready! |
Example CORE Fundamentals Policies & Standards
Our customers choose the CORE Fundamentals Policies & Standards because they need a scalable and affordable solution from a reputable company. The CORE Fundamentals is a hybrid, "best in class" approach to cybersecurity documentation to create a foundational set of cybersecurity policies, standards and controls. The CORE Fundamentals Policies & Standards has a 1-1 mapping relationship with the Secure Controls Framework (SCF) so it maps to over 100 leading practices!
View Product Examples
If you would like to view examples of ComplianceForge's CORE Fundamentals Policies & Standards, please click any of the images below:
|
|
The PDF document shown below provides two, side-by-side examples from policies all the way through metrics, so you can see what the actual content looks like.
Cost Savings Estimate For The CORE Fundamentals - A Fraction Of The Time & Expense
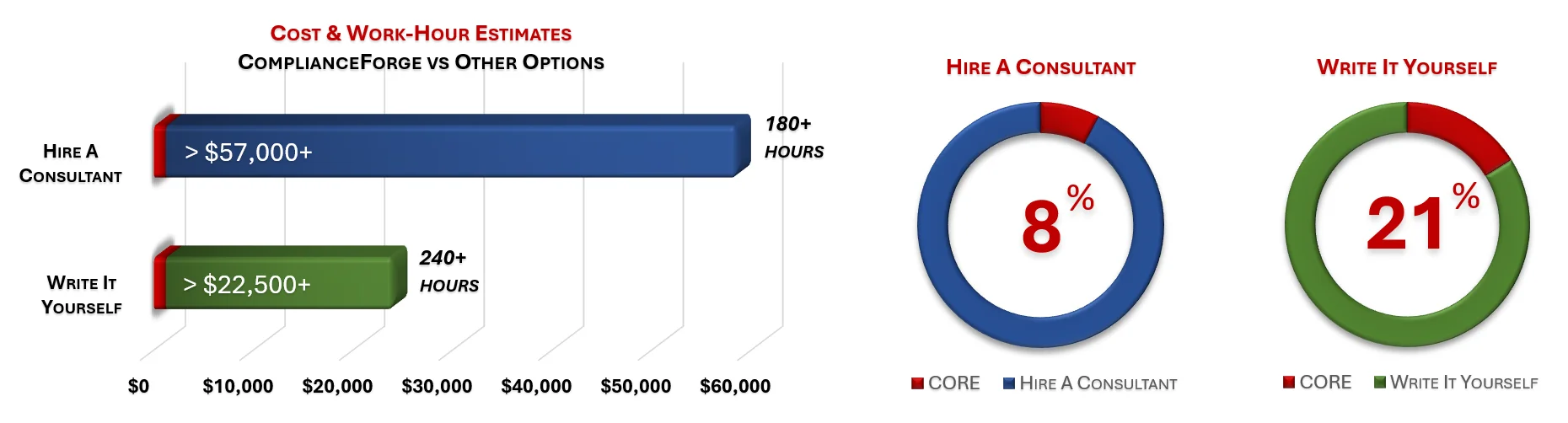
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CORE Fundamentals from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 240 internal staff work hours, which equates to a cost of approximately $24,000 in staff-related expenses. This is about 4-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 180 consultant work hours, which equates to a cost of approximately $58,500. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The CORE Fundamentals is approximately 8% of the cost for a consultant or 21% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CORE Fundamentals the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.







