Secure Controls Framework (SCF) "Premium Content" - Editable Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the DSP is to help answer common questions we receive.
What Is The Digital Security Program (DSP)?
The DSP is an enterprise-class solution for cybersecurity & data privacy documentation consisting of thirty-three (33) domains that defines a modern, digital security program. Specifically:
- Policies
- Control objectives
- Standards
- Guidelines
- Controls (Secure Controls Framework)
- Metrics
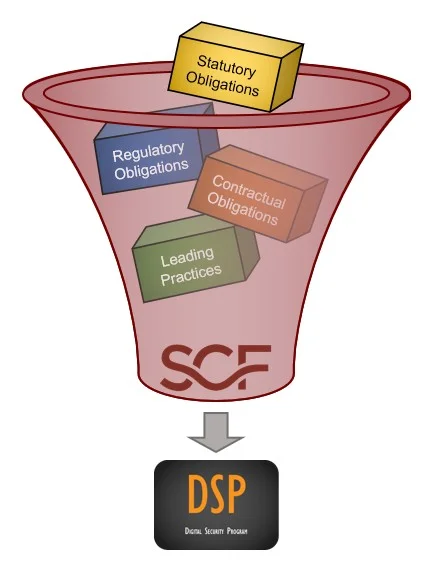
Nested within these thirty-three (33) policies are the control objectives, standards, guidelines, metrics & more that enable you to govern your cybersecurity & data privacy program. The DSP was developed to meet the need for growing organizations that want to avoid being locked into alignment with a single framework or have complex compliance requirements that span multiple frameworks. This approach is a "best in class" hybrid framework structure that provides you with the ability to align with multiple frameworks in an efficient and scalable manner.
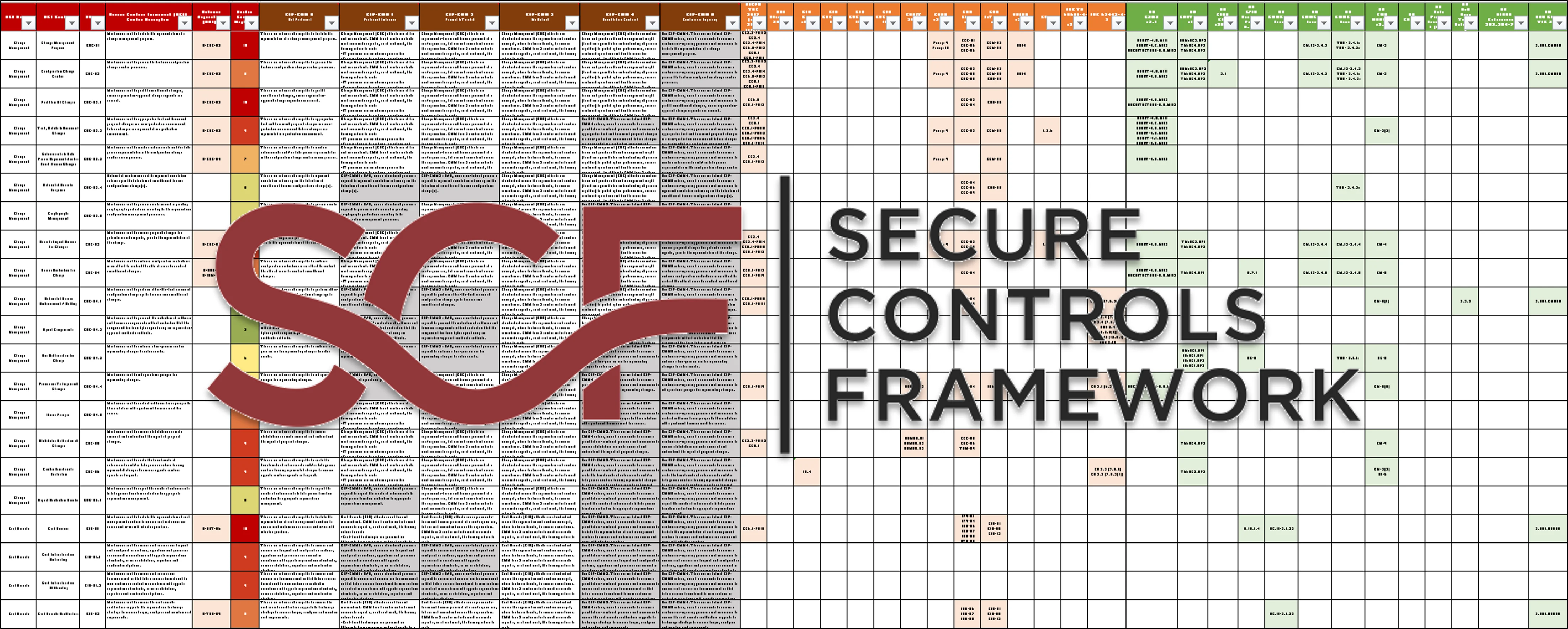
The DSP leverages the Secure Controls Framework (SCF), which is a metaframework that map to over 100 cybersecurity & data privacy laws, regulations and frameworks. The SCF's integration into the DSP provides mapped risks, threats, maturity criteria and much more to make it the most robust solution on the market!

ComplianceForge Is A SCF Licensed Content Provider (SCF LCP)
|
ComplianceForge is a Licensed Content Provider (LCP) by the SCF. This means ComplianceForge is authorized to sell cybersecurity and data protection policies, standards and procedures based on SCF controls. The DSP's policies & standards have direct, 1-1 mapping to the SCF's controls. The DSP leverages several key SCF components to provide “more than just policies & standards” by incorporating maturity criteria, a threat catalog, a risk catalog and more! The DSP provides invaluable content to operationalize several of the SCF's notable capabilities: |
|
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "90% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The DSP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The DSP is an efficient method to obtain comprehensive security policies, standards, controls and metrics for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security policies and standards. Requirements range from PCI DSS to HIPAA to NIST 800-171. The DSP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The DSP's standards provides mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies and standards. The DSP provides this evidence!
How Does the DSP Solve These Problems?
- Clear Documentation - The DSP provides comprehensive documentation to prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The DSP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The DSP is written to support over one hundred laws, regulations and industry frameworks!
The DSP and its corresponding Cybersecurity Operating Procedures (CSOP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. They cover GRC policies, GRC standards, GRC metrics and more. The following documents are valuable resources to justify purchasing the DSP to advance your GRC practices:
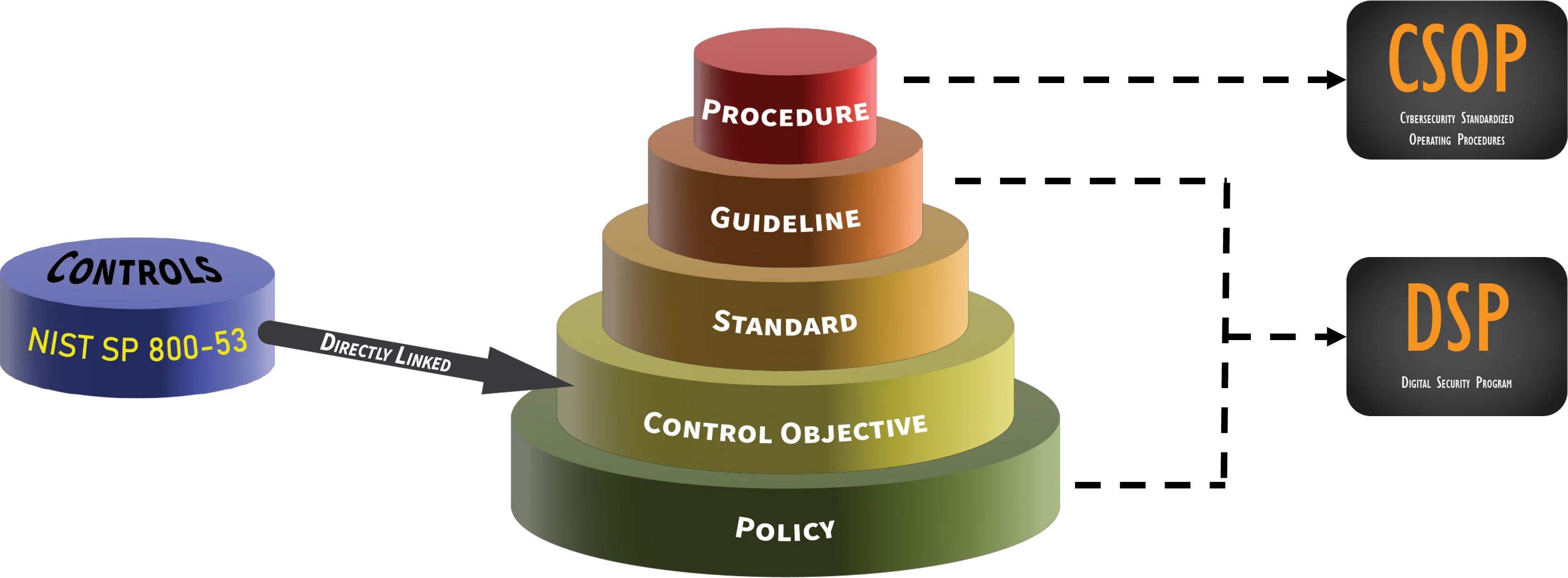
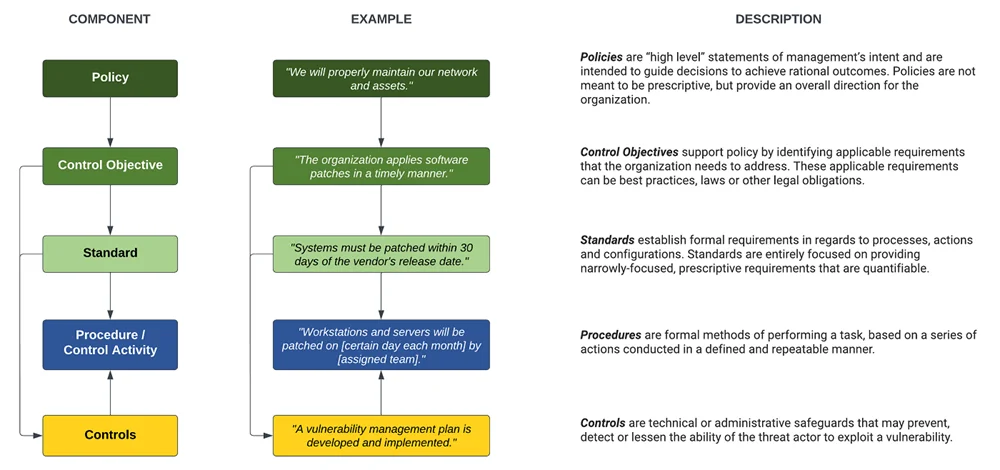
- ComplianceForge Reference Model – Hierarchical Cybersecurity Governance Framework – Level setting on how the various types of documentation support each other. This provides insights into the definitions used, since there is a tendency within the industry to abuse definitions around policy, standard, procedure, etc. This is the hierarchical structure we follow to build our content so it is scalable and based on industry practices.
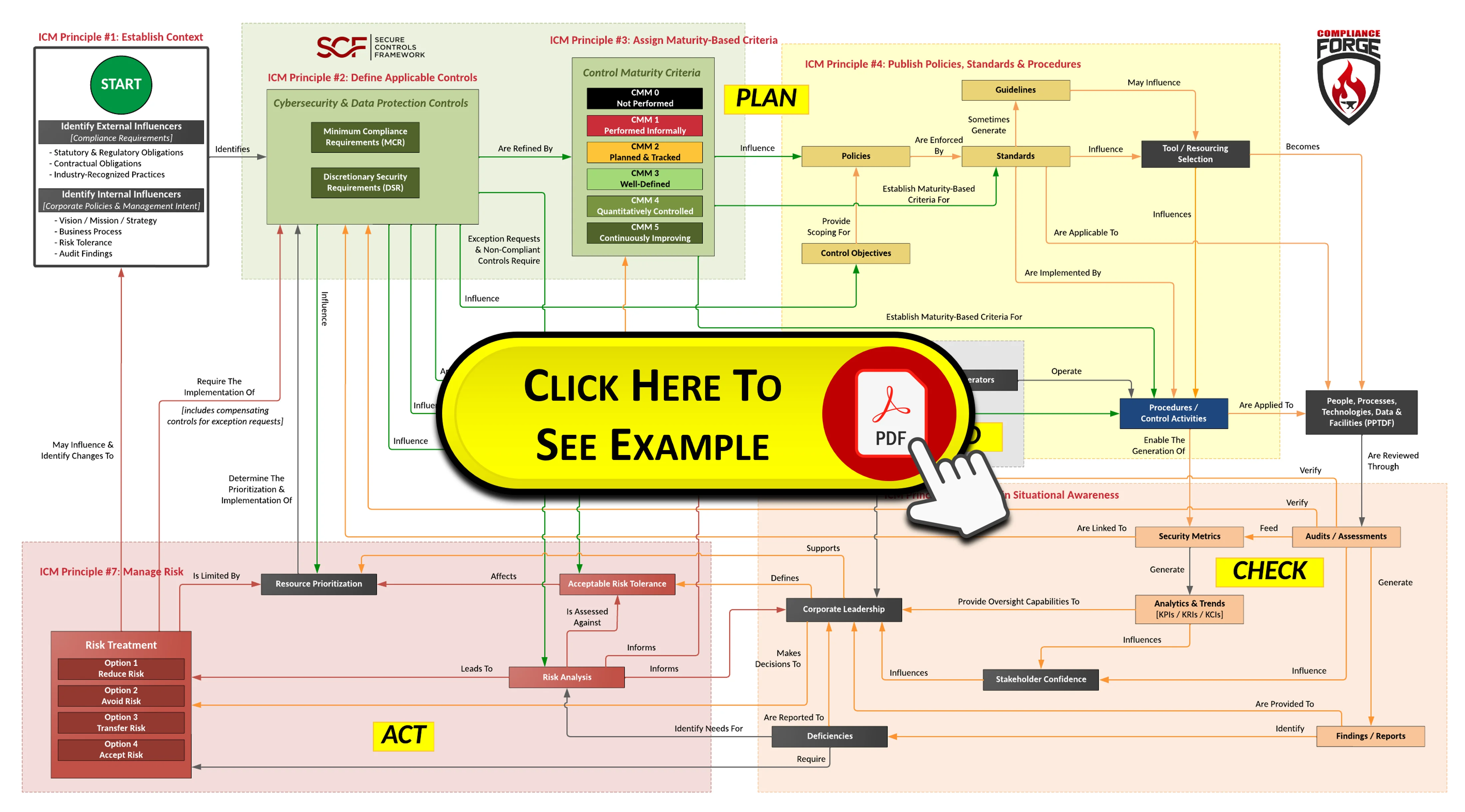
- Integrated Controls Management (ICM) - This is a "how to GRC playbook" that can help you establish the steps necessary to design, build and implement viable GRC processes. These are the steps we will tell you to follow if we were brought in to provide professional services. This helps explain further integration between the policies and standards within the DSP, corresponding procedures within the CSOP and controls from the SCF.
- Instructions & Best Practices For Using The DSP – This is a "start here" guide for using the DSP that provides a baseline for what the DSP's documentation components are and how to tailor the DSP for your specific needs.
- Security Metrics Reporting Model (SMRM) – This is the metrics model we developed as a way to leverage the built-in metrics that come as part of the DSP.
- DSP & CSOP Content Examples - This is a content example that shows two side-by-side examples from policies all the way to metrics.
- Unified Scoping Guide (USG) – Understanding control applicability is important and this scoping guide is designed to address any type of sensitive or regulated data so the appropriate controls can be applied.
Similar to our framework-specific Cybersecurity & Data Protection Program (CDPP) products, the DSP provides alignment with the underlying cybersecurity standards that must be complied with, as stipulated by statutory, regulatory and contractual requirements. However, the DSP provides robust coverage for over 100 laws, regulations and other cybersecurity and privacy frameworks. The DSP is essentially a "superset" of ISO 27002, NIST CSF, NIST 800-171, NIST 800-53 and other frameworks for organizations that do not want to be locked into alignment with just one framework [scroll to the bottom of the page to see a list of everything the DSP currently maps to].
Accelerating Your Business - Mapped To Over 100 Leading Cybersecurity & Data Privacy Laws, Regulations & Frameworks!
Leveraging the Secure Controls Framework (SCF), the DSP maps over 100 cybersecurity and data privacy laws, regulations and frameworks! This includes the most common statutory, regulatory and contractual requirements that are expected from a cybersecurity & data protection program. The DSP provides the necessary policies, control objectives, standards, guidelines and metrics to operationalize the SCF for your organization!
Cybersecurity & Data Privacy Policies, Standards, Controls & Metrics For A Modern Company - Hierarchical & Scalable!
ComplianceForge provides organizations with exactly what they need to protect themselves - professionally written cybersecurity policies, control objectives, standards, controls, procedures and guidelines at a very affordable cost. The DSP can be found in medium and large organizations that range from Fortune 500 companies, to US and international government agencies, universities and other organizations that have complex compliance requirements and need an efficient, scalable solution for their Governance, Risk & Compliance (GRC) needs.
The Digital Security Program (DSP) is footnoted to provide authoritative references for the statutory, regulatory and contractual requirements that need to be addressed. Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the DSP does this from a cybersecurity perspective.
The Cybersecurity Standardized Operating Procedures (CSOP) is available that provides mapped procedures to the DSP's standards. This is a 1-1 mapping with a procedure for each standard.
Operationalize Cybersecurity & Data Privacy By Design
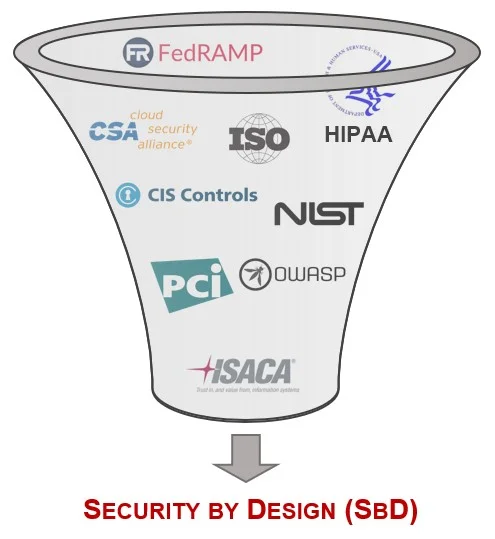
It is possible to visualize the Digital Security Program (DSP) as a buffet of cybersecurity and privacy policies, standards, controls and metrics. Once you determine what statutory, regulatory and contractual obligations are applicable to your organization, it is straightforward to identify a customized control set that is specific to your unique compliance obligations. This idea of building in cybersecurity and privacy requirements into your governance program is Security by Design (SbD) and Privacy by Design (PbD), where the obligations are understood before projects/initiatives commence, so that secure solutions can be designed, implemented and maintained. The DSP forms the cornerstone of your security and privacy program.
 |
|
Security by Design (SbD) requirements come from numerous sources. In this context, some of the most important cybersecurity frameworks are:
|
 |
|
Similar to SbD, Privacy by Design (PbD) requirements come from numerous sources. In this context, some of the most important privacy frameworks are:
|
Understanding "How To GRC" With The Digital Security Program (DSP) & Secure Controls Framework (SCF)
 |
ComplianceForge, in conjunction with the Secure Controls Framework (SCF), literally wrote the book on "how to do GRC" by establishing the Integrated Controls Management (ICM) that is a principle-based approach to Governance, Risk & Compliance (GRC) operations. The ICM Overview document (shown below) is a great starting place to understand how the DSP can help your organization to designing, implementing and managing a security and privacy program that incorporates requirements to be both secure and compliant. This approach leverages the "Deming Cycle" of Plan, Do, Check and Act (PDCA) for continuous improvement. Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
|
|
There are eight (8) principles associated with ICM that are fully-supported by the DSP to develop, implement and maintain a secure and compliant security and privacy program:
The structure of the Digital Security Program is scalable to make it is easy to add or remove policy sections, as your business needs change. The same concept applies to standards – you can simply add/remove content to meet your specific needs. The DSP addresses the “why?” and “what?” questions, since policies and standards form the foundation for your cybersecurity program. The following two documents shown below are well worth the time to make a pot of coffee and read through, since you will be able to understand both the structure of the documentation and how you can customize it for your specific needs. |
|
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the DSP! While the DSP does come in Microsoft Word like the CDPP, the included Excel version of the DSP comes with the following content so it is easy to import into a GRC/IRM solution:
|
|
|
Getting Started With The DSP
The DSP is our recommended solution if you are currently using or plan to use a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) solution. The DSP is ready to import into your GRC/IRM instance, since it comes in both Microsoft Word and Excel formats. This makes the import from Excel straightforward and that allows you to then do you any customization and collaboration directly from your GRC portal.
| Guide To Using The DSP & SCF |
Understanding "How To GRC" |
|
 |
Example Digital Security Program (DSP)
Our customers choose the Digital Security Program (DSP) because they need a scalable and comprehensive solution. The DSP is a hybrid, "best in class" approach to cybersecurity documentation that covers dozens of statutory, regulatory and contractual frameworks to create a comprehensive set of cybersecurity policies, standards, controls and metrics. The DSP has a 1-1 mapping relationship with the Secure Controls Framework (SCF) so it maps to over 100 leading practices! To understand the differences between the DSP and CDPP, please visit here for more details.
View Product Examples
If you would like to view examples of ComplianceForge's Digital Security Program (DSP), please click any of the images below:
The PDF document shown below provides two, side-by-side examples from policies all the way through metrics, so you can see what the actual content looks like.
What Is Included With The DSP?
Cost Savings Estimate For The Digital Security Program (DSP) - A Fraction Of The Time & Expense
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DSP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 900 internal staff work hours, which equates to a cost of approximately $90,000 in staff-related expenses. This is about 12-24 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 800 consultant work hours, which equates to a cost of approximately $260,000. This is about 6-12 months of development time for a contractor to provide you with the deliverable.
- The DSP is approximately 4% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the DSP the same day you place your order.
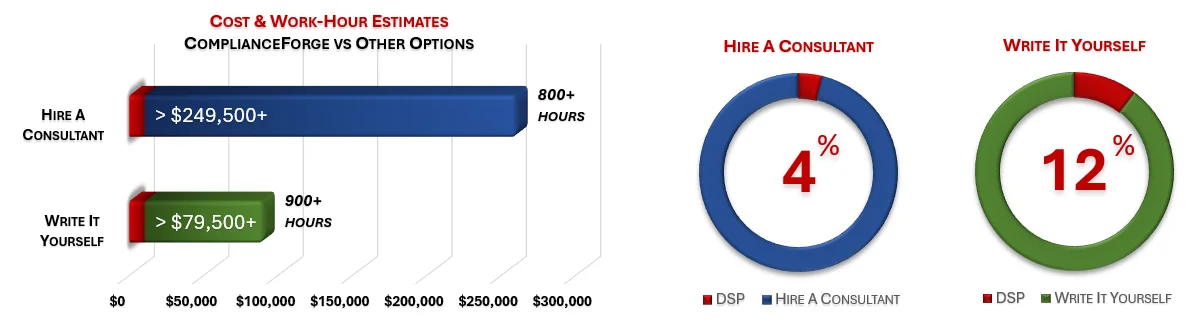
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
33 Domains - One Policy For Each Domain
The DSP contains thirty-three (33) unique domains that cover a modern cybersecurity & privacy program. Each of these 33 policies are supported by standards that provide the granular requirements necessary to enforce these standards (examples of what these policy and standards look like are available in the next section below this chart). The 32 policies that make up the DSP are:
| Policy # |
DSP Policy | Identifier | DSP Policy Intent |
| 1 | Security & Privacy Governance | GOV | The Security & Privacy (GOV) policy is focused on helping an organization specify the development of an organization’s security and privacy programs, including criteria to measure success, to ensure ongoing leadership engagement and risk management. |
| 2 | Artificial Intelligence & Autonomous Technologies | AAT |
The Artificial Intelligence & Autonomous Technologies (AAT) domain is designed to minimize emergent properties or unintended consequences through stringent governance practices that result in AI and autonomous technologies that are reliable, safe, fair, secure, resilient, transparent, explainable and privacy-enhanced. |
| 3 | Asset Management | AST | The Asset Management (AST) policy is focused on helping an organization ensure technology assets are properly managed throughout the lifecycle of the asset, from procurement through disposal, ensuring only authorized devices are allowed to access the organization’s network and to protect the organization’s data that is stored, processed or transmitted on its assets. |
| 4 | Business Continuity & Disaster Recovery | BCD | The Business Continuity & Disaster Recovery (BCD) policy is focused on helping an organization establish processes that will help the organization recover from adverse situations with the minimal impact to operations, as well as provide the ability for e-discovery. |
| 5 | Capacity & Performance Planning | CAP | The Capacity & Performance Planning (CAP) policy is focused on helping an organization prevent avoidable business interruptions caused by capacity and performance limitations by proactively planning for growth and forecasting, as well as requiring both technology and business leadership to maintain situational awareness of current and future performance. |
| 6 | Change Management | CHG | The Change Management (CHG) policy is focused on helping an organization ensure both technology and business leadership proactively manage change. This includes the assessment, authorization and monitoring of technical changes across the enterprise so as to not impact production systems uptime, as well as allow easier troubleshooting of issues. |
| 7 | Cloud Security | CLD | The Cloud Security (CLD) policy is focused on helping an organization govern the use of private and public cloud environments (e.g., IaaS, PaaS and SaaS) to holistically manage risks associated with third-party involvement and architectural decisions, as well as to ensure the portability of data to change cloud providers, if needed. |
| 8 | Compliance | CPL | The Compliance (CPL) policy is focused on helping an organization ensure controls are in place to be aware of and comply with applicable statutory, regulatory and contractual compliance obligations, as well as internal company standards. |
| 9 | Configuration Management | CFG | The Configuration Management (CFG) policy is focused on helping an organization establish and maintain the integrity of systems. Without properly documented and implemented configuration management controls, security features can be inadvertently or deliberately omitted or rendered inoperable, allowing processing irregularities to occur or the execution of malicious code. |
| 10 | Continuous Monitoring | MON | The Continuous Monitoring (MON) policy is focused on helping an organization establish and maintain ongoing situational awareness across the enterprise through the centralized collection and review of security-related event logs. Without comprehensive visibility into infrastructure, operating system, database, application and other logs, the organization will have “blind spots” in its situational awareness that could lead to system compromise, data exfiltration, or unavailability of needed computing resources. |
| 11 | Cryptographic Protections | CRY | The Cryptographic Protections (CRY) policy is focused on helping an organization ensure the confidentiality of the organization’s data through implementing appropriate cryptographic technologies to protect systems and data. |
| 12 | Data Classification & Handling | DCH | The Data Classification & Handling (DCH) policy is focused on helping an organization ensure that technology assets, both hardware and media, are properly classified and measures implemented to protect the organization’s data from unauthorized disclosure, regardless if it is being transmitted or stored. Applicable statutory, regulatory and contractual compliance requirements dictate the minimum safeguards that must be in place to protect the confidentiality, integrity and availability of data. |
| 13 | Embedded Technology | EMB | The Embedded Technology (EMB) policy is focused on helping an organization specify the development, proactive management and ongoing review of security embedded technologies, including hardening of the “stack” from the hardware, to firmware, software, transmission and service protocols used for Internet of Things (IoT) and Operational Technology (OT) devices. |
| 14 | Endpoint Security | END | The Endpoint Security (END) policy is focused on helping an organization ensure that endpoint devices are appropriately protected from security threats to the device and its data. Applicable statutory, regulatory and contractual compliance requirements dictate the minimum safeguards that must be in place to protect the confidentiality, integrity, availability and safety considerations. |
| 15 | Human Resources Security | HRS | The Human Resources Security (HRS) policy is focused on helping an organization create a security and privacy-minded workforce and an environment that is conducive to innovation, considering issues such as culture, reward and collaboration. |
| 16 | Identification & Authentication | IAC | The Identification & Authentication (IAC) policy is focused on helping an organization implement the concept of “least privilege” through limiting access to the organization’s systems and data to authorized users only. |
| 17 | Incident Response | IRO | The Incident Response (IRO) policy is focused on helping an organization establish and maintain a capability to guide the organization’s response when security or privacy-related incidents occur and to train users how to detect and report potential incidents. |
| 18 | Information Assurance | IAO | The Information Assurance (IAO) policy is focused on helping an organization ensure the adequately of security and controls are appropriate in both development and production environments. |
| 19 | Maintenance | MNT | The Maintenance (MNT) policy is focused on helping an organization ensure that technology assets are properly maintained to ensure continued performance and effectiveness. Maintenance processes apply additional scrutiny to the security of end-of-life or unsupported assets. |
| 20 | Mobile Device Management | MDM | The Mobile Device Management (MDM) policy is focused on helping an organization govern risks associated with mobile devices, regardless if the device is owned by the organization, its users or trusted third-parties. Wherever possible, technologies are employed to centrally manage mobile device access and data storage practices. |
| 21 | Network Security | NET | The Network Security (NET) policy is focused on helping an organization ensure sufficient security and privacy controls are architected to protect the confidentiality, integrity, availability and safety of the organization’s network infrastructure, as well as to provide situational awareness of activity on the organization’s networks. |
| 22 | Physical & Environmental Security | PES | The Physical & Environmental Security (PES) policy is focused on helping an organization minimize physical access to the organization’s systems and data by addressing applicable physical security controls and ensuring that appropriate environmental controls are in place and continuously monitored to ensure equipment does not fail due to environmental threats. |
| 23 | Privacy | PRI | The Privacy (PRI) policy is focused on helping an organization align privacy engineering decisions with the organization’s overall privacy strategy and industry-recognized leading practices to secure Personal Information (PI) that implements the concept of privacy by design and by default. |
| 24 | Project & Resource Management | PRM | The Project & Resource Management (PRM) policy is focused on helping an organization ensure that security-related projects have both resource and project/program management support to ensure successful project execution. |
| 25 | Risk Management | RSK | The Risk Management (RSK) policy is focused on helping an organization ensure that security and privacy-related risks are visible to and understood by the business unit(s) that own the assets and / or processes involved. The security and privacy teams only advise and educate on risk management matters, while it is the business units and other key stakeholders who ultimately own the risk. |
| 26 | Secure Engineering & Architecture | SEA | The Secure Engineering & Architecture (SEA) policy is focused on helping an organization align cybersecurity engineering and architecture decisions with the organization’s overall technology architectural strategy and industry-recognized leading practices to secure networked environments. |
| 27 | Security Operations | OPS | The Security Operations (OPS) policy is focused on helping an organization ensure appropriate resources and a management structure exists to enable the service delivery of cybersecurity operations. |
| 28 | Security Awareness & Training | SAT | The Situational Awareness & Training (SAT) policy is focused on helping an organization develop a security and privacy-minded workforce through continuous education activities and practical exercises, in order to refine and improve on existing training. |
| 29 | Technology Development & Acquisition | TDA | The Technology Development & Acquisition (TDA) policy is focused on helping an organization ensure that security and privacy principles are implemented into any products/solutions that are either developed internally or acquired to make sure that the concepts of “least privilege” and “least functionality” are incorporated. |
| 30 | Third-Party Management | TPM | The Third-Party Management (TPM) policy is focused on helping an organization ensure that security and privacy risks associated with third-parties are minimized and enable measures to sustain operations should a third-party become defunct. |
| 31 | Threat Management | THR | The Threat Management (THR) policy is focused on helping an organization establish a capability to proactively identify and manage technology-related threats to the security and privacy of the organization’s systems, data and business processes. |
| 32 | Vulnerability & Patch Management | VPM | The Vulnerability & Patch Management (VPM) policy is focused on helping an organization proactively manage the risks associated with technical vulnerability management that includes ensuring good patch and change management practices are utilized. |
| 33 | Web Security | WEB | The Web Security (WEB) policy is focused on helping an organization address the risks associated with Internet-accessible technologies by hardening devices, monitoring system file integrity, enabling auditing, and monitoring for malicious activities. |
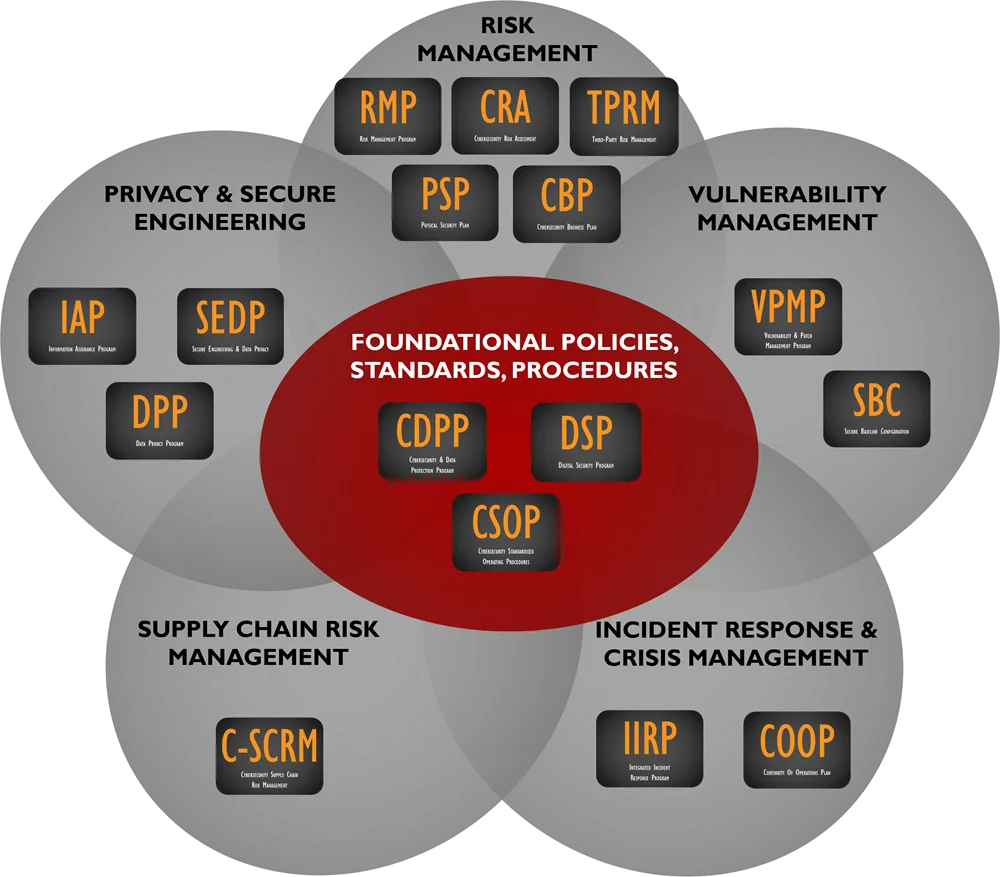
Before You "Can Move The Needle" You Need A Needle - Metrics Are Included In The DSP!
 |
|
The DSP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer. In addition to being a hybrid model that is made up of leading security frameworks, we also added in features that are not available in the Cybersecurity & Data Protection Program (CDPP), namely mapped controls and metrics. This equates to a potential time savings of hundreds of hours, based on how much work goes into not only creating controls and worthwhile metrics, but mapping those back into your organizations policies and standards. One special aspect of the DSP is while it comes in Microsoft Word format, it also comes in Microsoft Excel so that it is easy to import into a GRC solution (e.g., SCFConnect, Ostendio, ZenGRC (RiskOptics), SimpleRisk, LogicGate, Ignyte Assurance Platform, Archer, RSAM, MetricStream, etc.)! This is an ideal solution for companies that either currently use a GRC solution or are exploring the use of one. The time savings can equate to a saving of tens of thousands of dollars in customizing "out of the box" documentation from these tools. If you are interested in learning more, there is a product walk-through video and other helpful documentation, so keep reading or contact us so we can help answer your specific questions. |
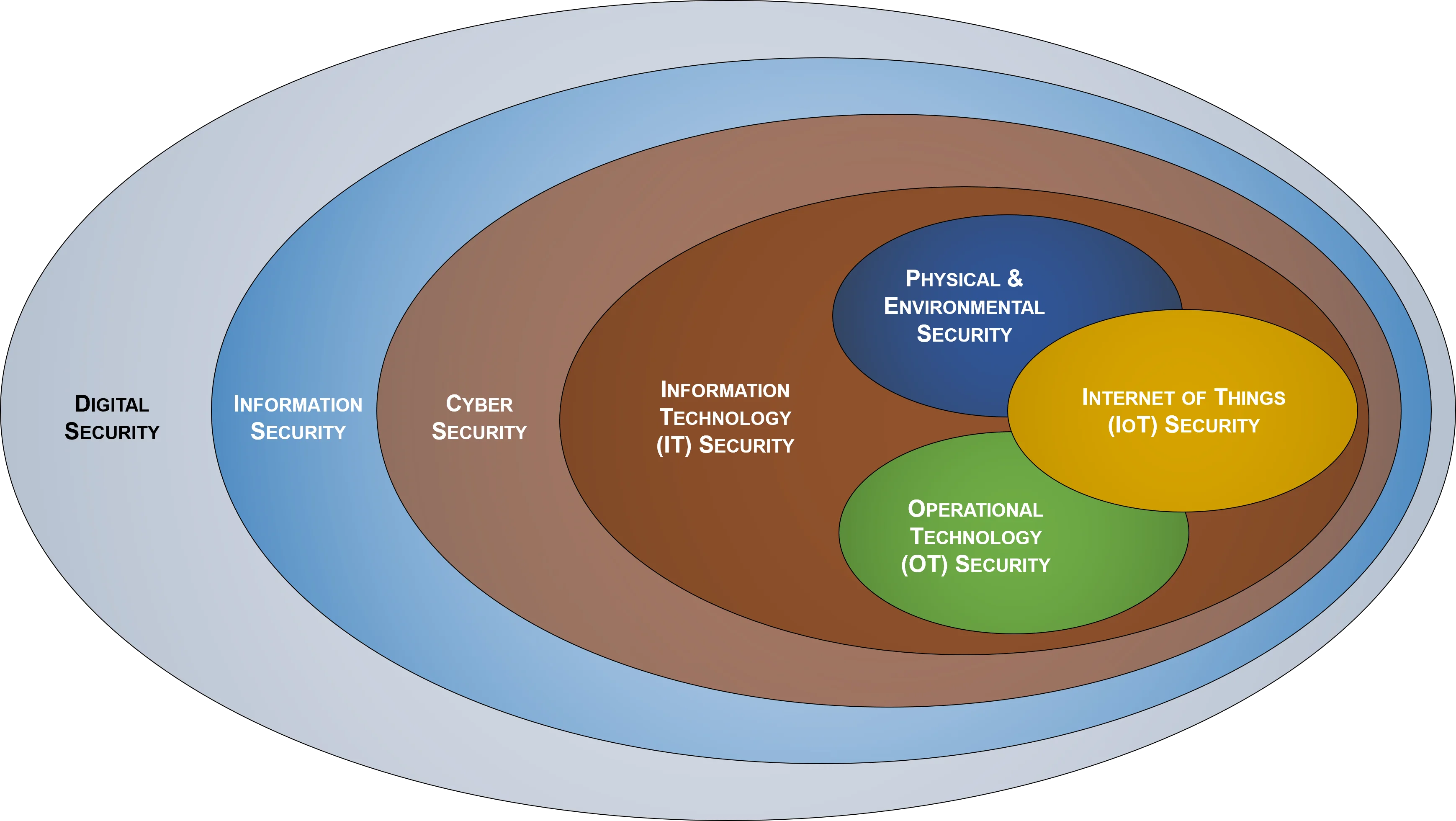
Digital Security - The Evolution of Security
|
If you are reading this, you are likely familiar with how “IT Security,” “Information Security,” and “Cybersecurity” are used interchangeably by most people. However, these terms do have meaning and as you “peel back the onion” on terminology you will see that “Digital Security” is the new leading terminology to describe the entire security ecosystem. This term has evolved to be all-encompassing, since it addresses technology, information, physical security, privacy and safety. |
 |
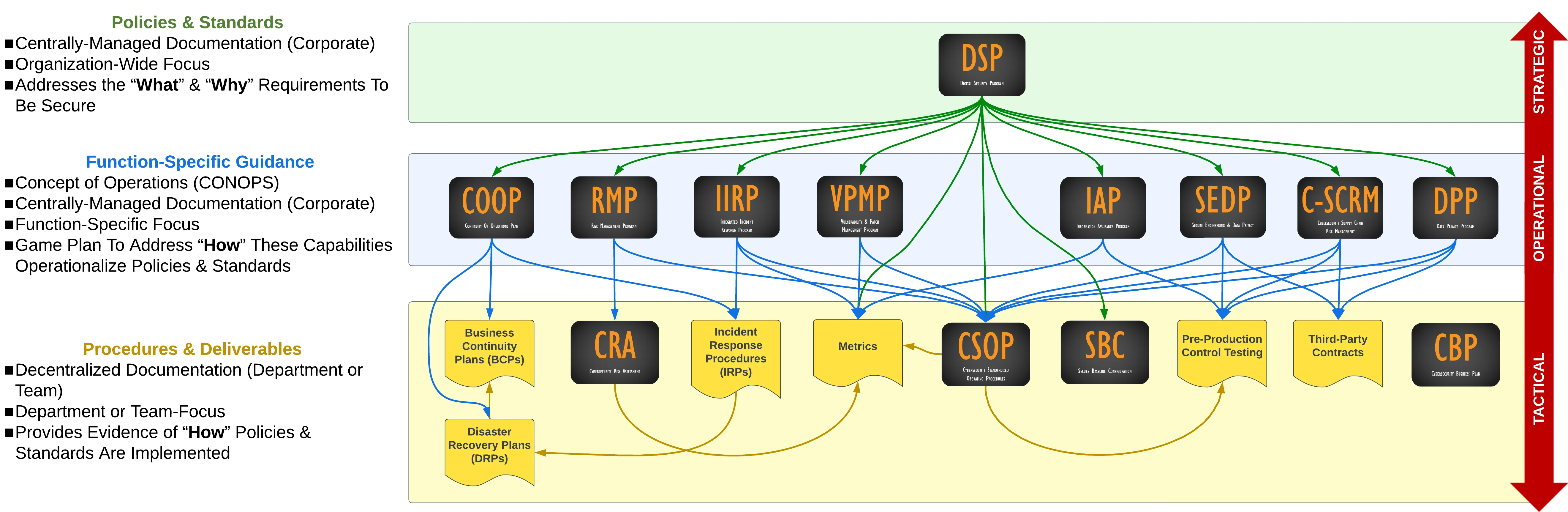
Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.
Safety Component - One Benefit of Thinking Digital
|
For years, the “CIA Triad” stood as the foundation for what a security program was designed to address – the Confidentiality, Integrity and Availability of both systems and data. That has now changed, since there are real-world safety considerations from Operational Technology (OT) and the Internet of Things (IoT). This has caused the evolution of the CIA Triad into the Confidentiality, Integrity, Availability and Safety (CIAS) model. The DSP is designed around the CIAS model by adopting the best of leading security frameworks. |
|
|
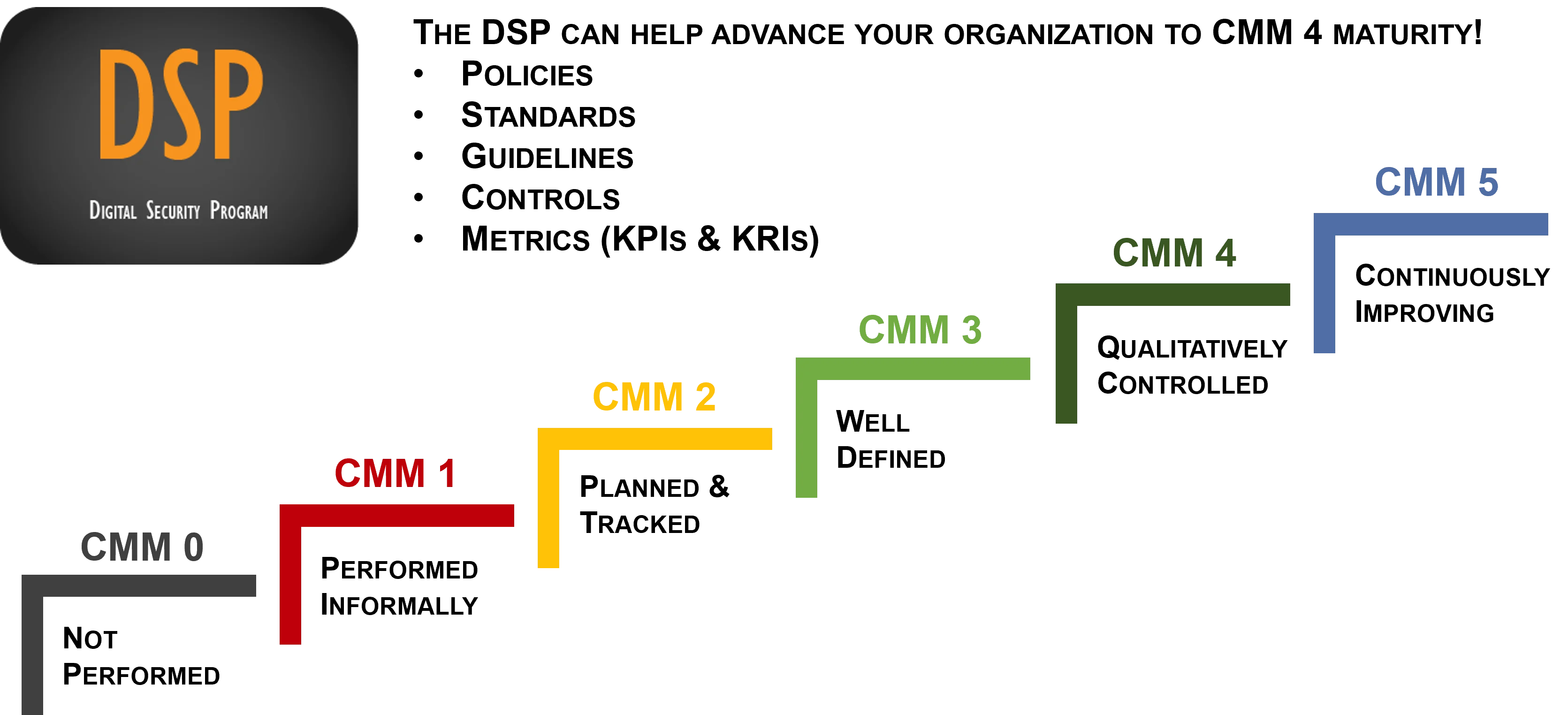
Steps To Using The DSP To Obtain CMM4 Maturity (Metrics-Driven)
 |
|
It is a simple fact that technology and cybersecurity departments are not revenue-generating. These cost centers must continuously demonstrate value to justify current and future budgets. While many boards of directors and executive management provide initial security budget funding based on Fear, Uncertainty & Doubt (FUD), there is an eventual need to demonstrate a Security Return on Investment (SROI). Without this return on investment, budgets are hard to justify and capabilities suffer. The most common ways for a security program to justify budget needs is through metrics reporting. The DSP can help you leverage the Systems Security Engineering Capability Maturity Model (SSE-CMM) with the Secure Control Framework's Cybersecurity & Data Privacy Capability Maturity Model (C|P-CMM). We avoided re-inventing the wheel and simply created an enterprise-class product that can help your organization rapidly advance its capability maturity to a CMM 4 level or beyond! |
Hierarchical Approach - Built To Scale & Evolve With Your Business
Our experience has proven that when it comes to Information Security policies, a standard is a standard for a reason. With that in mind, our Cybersecurity & Data Protection Program (CDPP) is based on industry-recognized best practices and Information Security standards so that you can meet your legal requirements.
|
Unlike some competitor sites that offer “Bronze, Silver or Gold” packages that may leave you critically exposed, we offer a comprehensive Information Security solution to meet your specific compliance requirements. Why is this? It is simple - in the real world, compliance is penalty-centric. Courts have established a track record of punishing businesses for failing to perform “reasonably expected” steps to meet compliance with known standards. The Cybersecurity & Data Protection Program (CDPP) follows a hierarchical approach to how the structure is designed so that standards map to control objectives and control objectives map to policies. This allows for the standards to be logically grouped to support the policies. |
 |
Security Metrics Reporting Model
 |
|
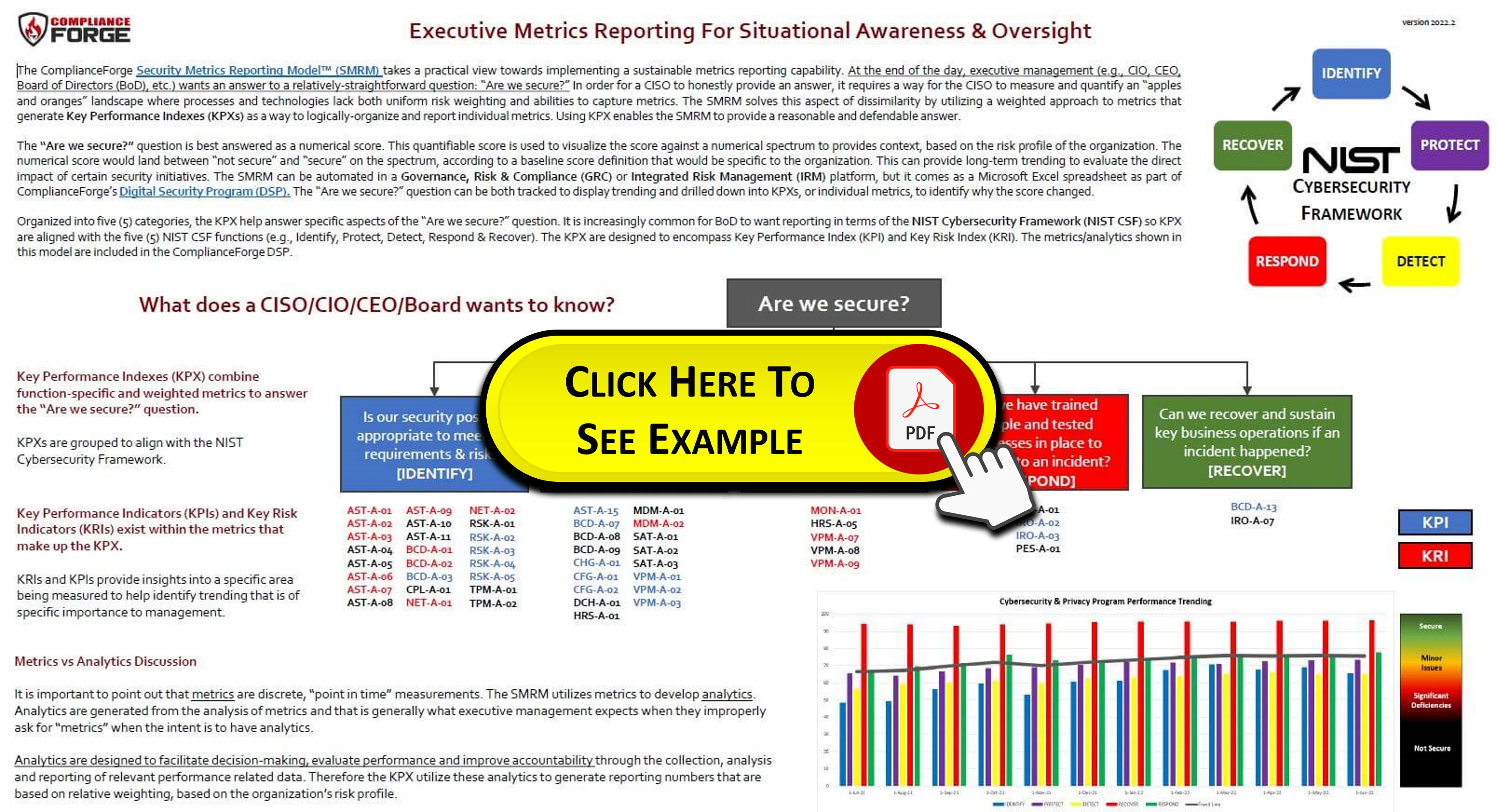
The ComplianceForge Security Metrics Reporting Model™ (SMRM) takes a practical view towards implementing a sustainable metrics reporting capability. At the end of the day, executive management (e.g., CIO, CEO, Board of Directors (BoD), etc.) want an answer to a relatively-straightforward question: “Are we secure?” In order for a CISO to honestly provide an answer, it requires a way for the CISO to measure and quantify an “apples and oranges” landscape where processes and technologies lack both uniform risk weighting and abilities to capture metrics. The SMRM helps solve this aspect of dissimilarity by utilizing a weighted approach to metrics that generate Key Performance Indexes (KPXs) as a way to logically-organize and report individual metrics. Using KPX enables the SMRM to provide a reasonable and defendable answer. |
Key Performance Indexes (KPXs)
KPXs are logical groupings of KPIs that allow an organization to monitor an index of metrics about a specific capability or team.
- KPXs are used to answer the question, “Is the XYZ capability operating effectively?” where that capability is an aggregation of multiple individual metrics.
- KPXs may be weighted to highlight risk-heavy topics of concern.
- KPXs may be nested underneath other KPXs to report the hierarchical nature of metrics that help answer the question of “Are we secure?”
KPIs and KRIs are not hierarchical metrics, but are individual metrics that are deemed important to monitor, based on the specific risk or value associated with that metric:
Key Performance Indicators (KPIs)
- KPIs are “rearward facing” and focus on historical trending to evaluate performance.
- KPIs should not be weighted.
- KPIs are indicators that enable an organization to monitor its progress towards achieving its defined performance targets.
- KPIs are used to answer the question, “Are we achieving our desired levels of performance?” for a specific control.
Key Risk Indicators (KRIs)
- KRIs are “forward facing” and focus on identifying a future-looking trend that impacts risk.
- KRIs should not be weighted.
- KRIs are indicators that enable an organization to define its risk profile and monitor changes to that profile.
- KRIs are used to answer the question, “Are we within our desired risk tolerance level?” for a specific control.
The metrics shown in this model are included in DSP. ComplianceForge does not sell the SMRM, KPIs, KRIs on their own, since the metrics are part of the DSP solution. With the 1-1 mapping relationship between the DSP and the Secure Controls Framework (SCF), the DSP can help operationalize the SCF controls in a meaningful and efficient manner, so that is something to consider for organizations that want to fully adopt the SCF as its control structure and maximize its effectiveness.
Being transparent on the subject, the entire point of a "canned solution" for metrics is to provide a starting point where someone else does the heavy lifting for you to get to a 70-80% solution that someone within your organization can then run with to customize for your specific needs. This is where ComplianceForge is a business accelerator - we enable you to hit the ground running with your cybersecurity documentation that can takes months or years to create on your own. The "heavy lifting" of the equation is what we provide, not the finalized metrics product. That is really where the demarcation is between what ComplianceForge offers for metrics and how an organization would customize the remaining since you have the organization-specific knowledge side of the metrics equation that cannot be templatized.
More Examples
While nearly all organizations have “security policies” in place, it is a sad reality that many are outdated, improperly scoped, and inadvertently add to technical debt. Quite simply, most security policies were never designed to scale as the organization grows or technologies evolve and are more of a liability than benefit. If that is your organization, the DSP can be a “quick win” to dramatically advance the maturity of your security program.
|
The DSP is a different animal – it is built to scale and adapt to the needs of the organization. The modular nature of the DSP means that each policy has its own standards, all the way down to controls and metrics. This hierarchical nature makes mapping metrics to policies a breeze, due to the logical organization of the documentation. You can view an example of the laws and authoritative sources the DSP maps to, you can click the image to the right, and it will open a .pdf in a new tab. You can also view the example by following this link - https://complianceforge.com/content/pdf/example-dsp-grc-import-ready-policies-standards-controls-metrics.pdf |
 |
“GOLDILOCKS” CONTROLS – NOT TOO BIG AND NOT TOO SMALL. JUST RIGHT.
The DSP uses the NIST Cybersecurity Controls Framework (CSF) version 1.1 for its metrics reporting model, so the controls are aligned with a leading framework for expected security controls. Key controls are identified from this control set and metrics are mapped to these controls. Again, since it is an Excel document, it is completely editable for your needs.
Creating A Cybersecurity Program Based On Multiple Leading Frameworks Is Achievable With A Metaframework!
The DSP uses the latest version of the Secure Controls Framework (SCF) for mapping to leading cybersecurity & data privacy laws, regulations and frameworks. The DSP comes with an Excel spreadsheet that provides the mapping for the standards to these references. The DSP currently maps to well over 100 frameworks that includes mapped coverage of the following cybersecurity and data privacy-related statutory, regulatory and contractual frameworks:
| Geography | Framework | Source |
Authoritative Source - Statutory / Regulatory / Contractual Framework |
Version |
| Universal | AICPA TSC 2017 (SOC 2) |
AICPA | Service Organization Control - Trust Services Criteria (TSC) - SOC2 | 2017 |
| Universal | BSI Standard 200-1 |
BSI | Standard 200-1 | 2022 |
| Universal | CIS CSC v8.0 |
CIS | Critical Security Controls (CSC) | 8.0 |
| Universal | COBIT 2019 |
ISACA | Control Objectives for Information and Related Technologies (COBIT) | 2019 |
| Universal | COSO v2017 |
COSO | Committee of Sponsoring Organizations (COSO) 2017 Framework | 2017 |
| Universal | CSA CCM v4 |
CSA | Cloud Controls Matrix (CCM) | v4 |
| Universal | CSA IoT SCF v2 |
CSA | CSA IoT Security Controls Framework v2 | v2 |
| Universal | ENISA v2.0 |
EU | European Union Agency for Network and Information Security (ENISA) | 2.0 |
| Universal | GAPP | AICPA | Generally Accepted Privacy Principles (GAPP) | N/A |
| Universal | IEC 62443-4-2 | IEC | IEC 62443-4-2:2019 - Security for industrial automation and control systems Part 4-2: Technical security requirements for IACS components |
2019 |
| Universal | ISO 22301 v2019 |
ISO | 22301 - Security and resilience — Business continuity management systems — Requirements | 2019 |
| Universal | ISO 27001 v2013 |
ISO | 27001 - Information Security Management Systems (ISMS) - Requirements | 2013 |
| Universal | ISO 27001 v2022 |
ISO | 27001 - Information Security Management Systems (ISMS) - Requirements | 2022 |
| Universal | ISO 27002 v2013 |
ISO | 27002 - Code of Practice for Information Security Controls | 2013 |
| Universal | ISO 27002 v2022 |
ISO | 27002 - Information security, cybersecurity and privacy protection - Information security controls | 2022 |
| Universal | ISO 27017 v2015 |
ISO | 27017 - Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services | 2015 |
| Universal | ISO 27018 v2014 |
ISO | 27018 - Code of Practice for PI in Public Clouds Acting as PI Processors | 2014 |
| Universal | ISO 27701 v2019 |
ISO | 27701 - Security techniques - Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management — Requirements and guidelines | 2019 |
| Universal | ISO 29100 v2011 |
ISO | 29100 - Privacy Framework | 2011 |
| Universal | ISO 31000 v2009 |
ISO | 31000 - Risk Management | 2009 |
| Universal | ISO 31010 v2009 |
ISO | 31010 - Risk Assessment Techniques | 2009 |
| Universal | MITRE ATT&CK 10 |
MITRE | MITRE ATT&CK - NIST 800-53 mappings | N/A |
| Universal | MPA Content Security Program v5.1 |
MPA | MPA Content Security Best Practices Common Guidelines | 5.1 |
| Universal | NIAC Insurance Data Security Model Law (MDL-668) |
NAIC | Insurance Data Security Model Law (MDL-668) | N/A |
| Universal | NIST Privacy Framework v1.0 |
NIST | NIST Privacy Framework | 1.0 |
| Universal | NIST SSDF |
NIST | Secure Software Development Framework (SSDF): Mitigating the Risk of Software Vulnerabilities by Adopting a Secure Software Development Framework (SSDF) |
N/A |
| Universal | NIST 800-37 rev 2 |
NIST | SP 800-37 - Guide for Applying the RMF to Federal Information Systems rev2 | 2 |
| Universal | NIST 800-39 |
NIST | SP 800-39 - Managing Information Security Risk | N/A |
| Universal | NIST 800-53 rev4 |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations | 4 |
| Universal | NIST 800-53 rev4 [low] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (low baseline) | 4 |
| Universal | NIST 800-53 rev4 [moderate] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (moderate baseline) | 4 |
| Universal | NIST 800-53 rev4 [high] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (high baseline) | 4 |
| Universal | NIST 800-53 rev5 |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations | 5 |
| Universal | NIST 800-53 rev5 [privacy] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations Privacy Baseline |
5 |
| Universal | NIST 800-53 rev5 [low] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations Low Baseline |
5 |
| Universal | NIST 800-53 rev5 [moerate] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations Moderate Baseline |
5 |
| Universal | NIST 800-53 rev5 [high] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations High Baseline |
5 |
| Universal | NIST 800-53 rev5 [NOC] |
NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations Select Not Otherwise Categorized (NOC) controls |
5 |
| Universal | NIST 800-63B [partial mapping] |
NIST | SP 800-63B - Digital Identity Guidelines (partial mapping) | June 2017 |
| Universal | NIST 800-82 rev2 Low Impact ICS Overlay |
NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST 800-82 rev2 Moderate Impact ICS Overlay |
NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST 800-82 rev2 High Impact ICS Overlay |
NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST 800-160 |
NIST | NIST SP 800-160 - Systems Security Engineering | N/A |
| Universal | NIST 800-161 rev 1 |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-161 rev 1 C-SCRM Baseline |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-161 rev 1 Flow Down |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-161 rev 1 Level 1 |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-161 rev 1 Level 2 |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-161 rev 1 Level 3 |
NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST 800-171 rev 2 |
NIST | SP 800-171 - Protecting CUI in Nonfederal Systems and Organizations | 2 |
| Universal | NIST 800-171A |
NIST | SP 800-171A - Assessing Security Requirements for Controlled Unclassified Information | N/A |
| Universal | NIST 800-172 |
NIST | SP 800-172 - Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations: Enhanced Security Requirements for Critical Programs and High Value Assets | N/A |
| Universal | NIST 800-218 v1.1 |
NIST | SP 800-218 - Secure Software Development Framework (SSDF) Version 1.1: | v1.1 |
| Universal | NIST CSF v1.1 |
NIST | Cybersecurity Framework (CSF) | 1.1 (Apr 19) |
| Universal | NIST CSF v2.0 IPD |
NIST | Cybersecurity Framework (CSF) 2.0 Initial Public Draft (IPD) | 2.0 IPD |
| Universal | OWASP Top 10 v2021 |
OWASP | Top 10 Most Critical Web Application Security Risks | 2021 |
| Universal | PCI DSS v3.2 |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) | 3.2 |
| Universal | PCIDSS v4.0 |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) | 4.0 |
| Universal | PCIDSS v4.0 SAQ A |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ A | 4.0 |
| Universal | PCIDSS v4.0 SAQ A-EP |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ A-EP | 4.0 |
| Universal | PCIDSS v4.0 SAQ B |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ B | 4.0 |
| Universal | PCIDSS v4.0 SAQ B-IP |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ B-IP | 4.0 |
| Universal | PCIDSS v4.0 SAQ C |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ C | 4.0 |
| Universal | PCIDSS v4.0 SAQ C-VT |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ C-VT | 4.0 |
| Universal | PCIDSS v4.0 SAQ D Merchant |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ D Merchant | 4.0 |
| Universal | PCIDSS v4.0 SAQ D Service Provider |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ D Service Provider | 4.0 |
| Universal | PCIDSS v4.0 SAQ P2PE |
PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ P2PE | 4.0 |
| Universal | Shared Assessments SIG 2023 | Shared Assessments | Shared Assessments Standard Information Gathering Questionnaire (SIG) | 2023 |
| Universal | SWIFT CSF v2023 |
SWIFT | SWIFT Customer Security Controls Framework | 2021 |
| Universal | TISAX ISA v5.1.0 |
TISAX | TISAX ISA | 5.1.0 |
| Universal | UL 2900-1 |
UL | 2900-1 - Software Cybersecurity for Network-Connectable Products | N/A |
| Universal | UN R155 |
United Nations | UN Regulation No. 155 | N/A |
| US | US C2M2 v2.1 |
Federal | Cybersecurity Capability Maturity Model v2.1 | 2.1 |
| US | US CERT RMM v1.2 |
Federal | CERT Resilience Management Model | 1.2 |
| US | US CISA CPG v2022 |
Federal | CISA Cross-Sector Cybersecurity Performance Goals (CPG) | 2022 |
| US | US CJIS Security Policy 5.9 |
Federal | US DOJ / FBI - Criminal Justice Information Services (CJIS) Security Policy | 5.9 |
| US | US CMMC 2.0 Level 1 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US CMMC 2.0 Level 2 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US CMMC 2.0 Level 3 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US CMMC 2.1 (draft) Level 1 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US CMMC 2.1 (draft) Level 2 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US CMMC 2.1 (draft) Level 3 |
Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US CMS MARS-E v2.0 |
Federal | US Centers for Medicare & Medicaid Services MARS-E Document Suite, Version 2.0 | 2.0 |
| US | US COPPA |
Federal | Children's Online Privacy Protection Act (COPPA) | N/A |
| US | US DFARS Cybersecurity |
Federal | Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7008 - 7012 | 252.204-7008 |
| US | US FACTA |
Federal | Fair & Accurate Credit Transactions Act (FACTA) / Fair Credit Reporting Act (FCRA) | N/A |
| US | US FAR 52.204-21 |
Federal | Federal Acquisition Regulation (FAR) | 52.204-21 |
| US | US FAR Section 889 |
Federal | Federal Acquisition Regulation (FAR) - Section 889 | 889 |
| US | US FDA 21 CFR Part 11 |
Federal | Food & Drug Administration (FDA) | 21 CFR Part 11 |
| US | US FedRAMP |
Federal | Federal Risk and Authorization Management Program (FedRAMP) | R4 |
| US | US FedRAMP [low] |
Federal | Federal Risk and Authorization Management Program (FedRAMP) (low baseline) | R4 |
| US | US FedRAMP [moderate] |
Federal | Federal Risk and Authorization Management Program (FedRAMP) (moderate baseline) | R4 |
| US | US FedRAMP [high] |
Federal | Federal Risk and Authorization Management Program (FedRAMP) (high baseline) | R4 |
| US | US FedRAMP [LI-SaaS] |
Federal | Federal Risk and Authorization Management Program (FedRAMP) (Li-SAAS) baseline) | R4 |
| US | US FedRAMP R5 |
Federal | Federal Risk and Authorization Management Program (FedRAMP) R5 | R5 |
| US | US FedRAMP R5 (low) |
Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (low baseline) | R5 |
| US | US FedRAMP R5 (moderate) |
Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (moderate baseline) | R5 |
| US | US FedRAMP R5 (high) |
Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (high baseline) | R5 |
| US | US FedRAMP R5 (LI-SaaS) |
Federal | Federal Risk and Authorization Management Program (FedRAM R5P) (Li-SAAS) baseline) | R5 |
| US | US FERPA |
Federal | Family Educational Rights and Privacy Act (FERPA) | N/A |
| US | US FFIEC |
Federal | Federal Financial Institutions Examination Council (FFIEC) | N/A |
| US | US FINRA |
Federal | Financial Industry Regulatory Authority (FINRA) | N/A |
| US | US FTC Act |
Federal | Federal Trade Commission (FTC) Act | N/A |
| US | US GLBA CFR 314 |
Federal | Gramm Leach Bliley Act (GLBA) | CFR 314 |
| US | US HIPAA |
Federal | Health Insurance Portability and Accountability Act (HIPAA) | N/A |
| US | HIPAA - HICP Small Practice |
Federal | Health Industry Cybersecurity Practices (HICP) - Small Practice | N/A |
| US | HIPAA - HICP Medium Practice |
Federal | Health Industry Cybersecurity Practices (HICP) - Medium Practice | N/A |
| US | HIPAA - HICP Large Practice |
Federal | Health Industry Cybersecurity Practices (HICP) - Large Practice | N/A |
| US | US IRS 1075 |
Federal | Internal Revenue Service (IRS) 1075 | N/A |
| US | ITAR Part 120 [limited] |
Federal | International Traffic in Arms Regulation (ITAR) [limited to Part 120] | N/A |
| US | US NERC CIP |
Federal | North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) | N/A |
| US | US NISPOM |
Federal | National Industrial Security Program Operating Manual (NISPOM) | N/A |
| US | US NNPI (unclass) |
Federal | Naval Nuclear Propulsion Information (NNPI) | N/A |
| US | US NSTC NSPM-33 |
Federal | National Science & Technology Council (NSTC) NSPM-33 | N/A |
| US | US Privacy Shield |
Federal | Privacy Shield | N/A |
| US | US SEC Cybersecurity Rule |
Federal | Cybersecurity Final Rule (Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure) - 17 CFR Parts 229, 232, 239, 240, and 249 | N/A |
| US | US SOX |
Federal | Sarbanes Oxley Act (SOX) | N/A |
| US | US SSA EIESR v8.0 |
Federal | Social Security Administration (SSA) Electronic Information Exchange Security Requirements | 8.0 |
| US | StateRAMP Low Category 1 |
State | StateRAMP Low (Category 1) | N/A |
| US | StateRAMP Low+ Category 2 |
State | StateRAMP Low+ (Category 2) | N/A |
| US | StateRAMP Moderate Category 3 |
State | StateRAMP Moderate (Category 3) | N/A |
| US | US - AK PIPA |
State | AK - Alaska Personal Information Protection Act (PIPA) | N/A |
| US | US - CA SB327 |
State | CA - SB327 | N/A |
| US | US-CA CPRA (Nov 2022) |
State | California Privacy Rights Act (CPRA) - November 2022 version | November 2022 |
| US | US - CA SB1386 |
State | CA - SB1386 | N/A |
| US | US - CO Colorado Privacy Act |
State | CO - Colorado Privacy Act | N/A |
| US | US - IL BIPA |
State | Illinois Biometric Information Privacy Act (PIPA) | N/A |
| US | US - IL IPA |
State | Illinois Identity Protection Act (IPA) | N/A |
| US | US - IL PIPA |
State | IL - Illinois Personal Information Protection Act (PIPA) | N/A |
| US | US - MA 201 CMR 17.00 |
State | MA - 201 CMR 17.00 | N/A |
| US | US - NV SB220 |
State | NV - SB220 | N/A |
| US | US - NY DFS 23 NYCRR500 |
State | NY - NY DFS 23NYCRR500 | N/A |
| US | US - NY SHIELD Act S5575B |
State | NY - SHIELD Act (SB S5575B) | N/A |
| US | US - OR 646A |
State | OR - ORS 646A | N/A |
| US | US - SC Insurance Data Security Act |
State | SC - South Carolina Insurance Data Security Act | N/A |
| US | US - TX BC521 |
State | TX - BC521 | N/A |
| US | US-TX Cybersecurity Act |
State | TX - Cybersecurity Act | N/A |
| US | US-TX DIR Control Standards 2.0 | State | TX - DIR Security Control Standards Catalog | 2.0 |
| US | US-TX TX-RAMP |
State | TX - Texas Risk & Authorization Management Program (TX-RAMP) | N/A |
| US | US-TX SB820 |
State | TX - 2019 - SB820 | N/A |
| US | US-VA CDPA 2023 |
State | Virginia Consumer Data Protection Act | 2023 |
| US | US-VT Act 171 of 2018 |
State | VT - Act 171 of 2018 (Data Broker Registration Act) | N/A |
| EMEA | EMEA EU EBA GL/2019/04 |
EU | European Banking Authority (EBA) Guidelines on ICT and security risk management | N/A |
| EMEA | EMEA EU DORA |
EU | EU Digital Operational Resilience Act (DORA) | 2023 |
| EMEA | EMEA EU ePrivacy [draft] |
EU | ePrivacy Directive | draft |
| EMEA | EMEA EU GDPR |
EU | General Data Protection Regulation (GDPR) | N/A |
| EMEA | EMEA EU NIS2 |
EU | ENISA NIS2 (Directive (EU) 2022/2555) | N/A |
| EMEA | EMEA EU PSD2 |
EU | Second Payment Services Directive (PSD2) | N/A |
| EMEA | EMEA EU EU-US Data Privacy Framework |
EU | EU-US Data Privacy Framework | N/A |
| EMEA | EMEA Austria |
Austria | Federal Act concerning the Protection of Personal Data (DSG 2000) | N/A |
| EMEA | EMEA Belgium |
Belgium | Act of 8 December 1992 | N/A |
| EMEA | EMEA Czech Republic |
Czech Republic | Act No. 101/2000 on the Protection of Personal Data | N/A |
| EMEA | EMEA Denmark |
Denmark | Act on Processing of Personal Data (Act No. 429 of May 31, 2000) | N/A |
| EMEA | EMEA Finland |
Finland | Personal Data Act (986/2000) | N/A |
| EMEA | EMEA France |
France | 78 17 / 2004 8021 - Information Technology, Data Files & Civil Liberty | N/A |
| EMEA | EMEA Germany |
Germany | Federal Data Protection Act | N/A |
| EMEA | EMEA Germany C5:2020 |
Germany | Cloud Computing Compliance Controls Catalogue (C5) | 2020 |
| EMEA | EMEA Greece |
Greece | Protection of Individuals with Regard to the Processing of Personal Data (2472/1997) | N/A |
| EMEA | EMEA Hungary |
Hungary | Informational Self-Determination and Freedom of Information (Act CXII of 2011) | N/A |
| EMEA | EMEA Ireland |
Ireland | Data Protection Act (2003) | N/A |
| EMEA | EMEA Israel CDMO v1.0 |
Israel | Cybersecurity Methodology for an Organization | 1.0 |
| EMEA | EMEA Israel |
Israel | Protection of Privacy Law, 5741 – 1981 | N/A |
| EMEA | EMEA Italy |
Italy | Personal Data Protection Code | N/A |
| EMEA | EMEA Kenya DPA 2019 |
Kenya | Kenya Data Protection Act | 2019 |
| EMEA | EMEA Luxembourg |
Luxembourg | Protection of Personals with Regard to the Processing of Personal Data | N/A |
| EMEA | EMEA Netherlands |
Netherlands | Personal Data Protection Act | N/A |
| EMEA | EMEA Nigeria DPR 2019 |
Nigeria | Nigeria Data Protection Regulation | 2019 |
| EMEA | EMEA Norway |
Norway | Personal Data Act | N/A |
| EMEA | EMEA Poland |
Poland | Act of 29 August 1997 on the Protection of Personal Data | N/A |
| EMEA | EMEA Portugal |
Portugal | Act on the Protection of Personal Data | N/A |
| EMEA | EMEA Qatar PDPPL |
Qatar | Personal Data Privacy Protection Law (PDPPL) | N/A |
| EMEA | EMEA Russia |
Russia | Federal Law of 27 July 2006 N 152-FZ | N/A |
| EMEA | EMEA Saudi Arabia Critical Security Controls |
Saudi Arabia | Saudi Arabian Monetary Authority - Cyber Security Framework | Version 1.0 (May 2017) |
| EMEA | EMEA Saudi Arabia SACS-002 |
Saudi Arabia | SACS-002 - Third Party Cybersecurity Standard | N/A |
| EMEA | EMEA Saudi Arabia SAMA CSFv1.0 |
Saudi Arabia | Saudi Arabian Monetary Authoirty (SAMA) Cyber Security Framework (CSF) | 2017 v1 |
| EMEA | EMEA Saudi Arabia ECC-1 2018 |
Saudi Arabia | Essential Cybersecurity Controls (ECC – 1 : 2018) | 2018 |
| EMEA | EMEA Saudi Arabia OTCC-1 2022 |
Saudi Arabia | Operational Technology Cybersecurity Controls (OTCC -1: 2022) | 2022 |
| EMEA | EMEA Serbia 87/2018 |
Servia | Act of 9 November 2018 on Personal Data Protection (Official Gazette No. 87/18) | N/A |
| EMEA | EMEA Slovak Republic |
Slovak Republic | Protection of Personal Data (122/2013) | N/A |
| EMEA | EMEA South Africa |
South Africa | Protection of Personal Information Act (POPIA) | N/A |
| EMEA | EMEA Spain |
Spain | Royal Decree 1720/2007 (protection of personal data) | N/A |
| EMEA | EMEA Spain CCN-STIC 825 |
Spain | ICT Security Guide CCN-STIC 825 | N/A |
| EMEA | EMEA Sweden |
Sweden | Personal Data Act | N/A |
| EMEA | EMEA Switzerland |
Switzerland | Federal Act on Data Protection (FADP) | N/A |
| EMEA | EMEA Turkey |
Turkey | Regulation on Protection of Personal Data in Electronic Communications Sector | N/A |
| EMEA | EMEA UAE |
UAE | Data Protection Law No. 1 of 2007 | N/A |
| EMEA | EMEA UK CAF v3.1 |
United Kingdom | Cyber Assessment Framework | 3.1 |
| EMEA | EMEA UK CAP 1850 |
United Kingdom | Cyber Assessment Framework (CAF) for Aviation Guidance (CAP1850) | N/A |
| EMEA | EMEA UK Cyber Essentials |
United Kingdom | Cyber Essentials | N/A |
| EMEA | EMEA UK DPA |
United Kingdom | Data Protection Act | N/A |
| EMEA | EMEA UK GDPR |
United Kingdom | UK General Data Protection Regulation | N/A |
| APAC | APAC Australia Essential 8 ML 1 |
Australia | Australia Essential Eight | N/A |
| APAC | APAC Australia Essential 8 ML 2 |
Australia | Australia Essential Eight | N/A |
| APAC | APAC Australia Essential 8 ML 3 |
Australia | Australia Essential Eight | N/A |
| APAC | APAC Australia Privacy Act |
Australia | Privacy Act of 1998 | N/A |
| APAC | APAC Australia ISM 2022 |
Australia | Australian Government Information Security Manual (ISM) | December 2022 |
| APAC | APAC Australia IoT Code of Practice |
Australia | Australia - Code of Practice - Securing the Internet of Things for Consumers | N/A |
| APAC | APAC Australia Prudential Standard CPS 234 |
Australia | Prudential Standard CPS 234 Information Security | N/A |
| APAC | APAC Australia Privacy Principles |
Australia | Australia Privacy Principles | N/A |
| APAC | APAC China DNSIP |
China | Decision on Strengthening Network Information Protection | N/A |
| APAC | APAC Hong Kong |
Hong Kong | Personal Data Ordinance | N/A |
| APAC | APAC India ITR |
India | Information Technology Rules (Privacy Rules) | N/A |
| APAC | APAC Indonesia |
Indonesia | Government Regulation No. 82 of 2012 | N/A |
| APAC | APAC Japan APPI |
Japan | Act on the Protection of Personal Information | June 2020 |
| APAC | APAC Japan ISMAP |
Japan | Japan Information System Security Management and Assessment Program (ISMAP) | N/A |
| APAC | APAC Malaysia |
Malaysia | Personal Data Protection Act of 2010 | N/A |
| APAC | APAC New Zealand Health ISF |
New Zealand | NZ Health Information Security Framework | N/A |
| APAC | APAC New Zealand NZISM 3.6 |
New Zealand | New Zealand Information Security Manual (NZISM) | 3.6 |
| APAC | APAC New Zealand Privacy Act of 2020 |
New Zealand | Privacy Act of 2020 | 2020 |
| APAC | APAC Philippines |
Philippines | Data Privacy Act of 2012 | N/A |
| APAC | APAC Singapore |
Singapore | Personal Data Protection Act of 2012 | N/A |
| APAC | APAC Singapore Cyber Hygiene Practice |
Singapore | Cyber Hygiene Practice | N/A |
| APAC | APAC Singapore MAS TRM 2021 |
Singapore | Monitory Authority of Singapore (MAS) Technology Risk Management (TRM) Guidelines | 2021 |
| APAC | APAC South Korea |
South Korea | Personal Information Protection Act | N/A |
| APAC | APAC Taiwan |
Taiwan | Personal Data Protection Act | N/A |
| Americas | Americas Argentina |
Argentina | Protection of Personal Law No. 25,326 | N/A |
| Americas | Americas Argentina Reg 132/2018 |
Argentina | Protection of Personal Data - MEN-2018-147-APN-PTE | N/A |
| Americas | Americas Bahamas |
Bahamas | Data Protection Act | N/A |
| Americas | Americas Bermuda BMA CCC |
Bermuda | Bermuda Monetary Authority Cyber Code of Conduct | N/A |
| Americas | Americas Brazil |
Brazil | General Data Protection Law (LGPD) | N/A |
| Americas | Americas Canada CSAG |
Canada | Office of the Superintendent of Financial Institutions Canada (OSFI) - Cyber Security Self-Assessment Guidance | N/A |
| Americas | Americas Canada OSFI B-13 |
Canada | B-13 | N/A |
| Americas | Americas Canada PIPEDA |
Canada | Personal Information Protection and Electronic Documents Act (PIPEDA) | N/A |
| Americas | Americas Chile |
Chile | Act 19628 - Protection of Personal Data | N/A |
| Americas | Americas Colombia |
Colombia | Law 1581 of 2012 | N/A |
| Americas | Americas Costa Rica |
Costa Rica | Protection of the Person in the Processing of His Personal Data | N/A |
| Americas | Americas Mexico |
Mexico | Federal Law on Protection of Personal Data held by Private Parties | N/A |
| Americas | Americas Peru |
Peru | Personal Data Protection Law | N/A |
| Americas | Americas Uruguay |
Uruguay | Law No. 18,331 - Protection of Personal Data and Action "Habeas Data" | N/A |
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.