NIST SP 800-171 R3 Compliance (DFARS 252.204-7012)
NIST SP 800-171 Rev 3 refers to the Third Revision (Rev 3) of National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171):
- Publication Title: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
- Published Date: May 2024
What Is NIST SP 800-171 Rev 3?
NIST SP 800-171 Rev 2 is focused on the protection of Controlled Unclassified Information (CUI) resident in nonfederal systems and organizations (e.g., defense contractors). NIST SP 800-171 provides US federal agencies (including the US Department of Defense (DoD)) with recommended cybersecurity requirements to protect the confidentiality and integrity of CUI in nonfederal systems and organizations. NIST SP 800-171 was first published in 2015 and the current version (Rev3) was released in May 2024.
NIST SP 800-171 is designed to require contractors to adhere with reasonably-expected security requirements that have been in use by the US government for years. NIST 800-171 establishes a basic set of expectations and maps these requirements to NIST 800-53, which is the de facto standard for US government cybersecurity controls. NIST 800-171 creates a standardized and uniform set of requirements for all Controlled Unclassified Information (CUI) security needs. This is designed to address common deficiencies in managing and protecting unclassified information by that is being stored, transmitted or processed by private businesses.
While NIST SP 800-171 Rev 3 is the current version of NIST SP 800-171, the DoD issued a class deviation in May 2024 for DFARS Clause 252.204-7012 to indefinitely require DoD contractors to comply with NIST SP 800-171 Rev 2. DFARS Clause 252.204-7012 mandates defense contactors to
- Safeguard CUI;
- Report cyber incidents; and
- Comply with NIST SP 800-171.
Why Do I Need To Upgrade From NIST SP 800-171 Rev 2 To NIST SP 800-171 Rev 3?
The Office of Management and Budget (OMB) requires organizations to adopt the most current version of NIST publications one year after its the new version's public release. From a NIST 800-171 perspective, this means NIST 800-171 Rev 3 is expected to be required in contracts no later than May 2025, at which time NIST 800-171 Rev 2 is deprecated (outdated).
Per OMB in CIRCULAR NO. A-130: "For legacy information systems, agencies are expected to meet the requirements of, and be in compliance with, NIST standards and guidelines within one year of their respective publication dates unless otherwise directed by OMB. The one-year compliance date for revisions to NIST publications applies only to new or updated material in the publications. For information systems under development or for legacy systems undergoing significant changes, agencies are expected to meet the requirements of, and be in compliance with, NIST standards and guidelines immediately upon deployment of the systems."
Who Needs To Comply With NIST SP 800-171 Rev 3?
An organization that stores, processes and/or transmits CUI as part of a contract with the US government is required to comply with NIST SP 800-171. Examples of these organizations that may store, process and/or transmit CUI as part of a contract include, but are not limited to:
- Department of Defense (DoD) contractors;
- US federal contractors;
- Technology companies;
- Managed Service Providers (MSPs) / Managed Security Services Providers (MSSP);
- Systems integrators (e.g., professional services, consultants, etc.);
- Manufacturers;
- Higher education (e.g., colleges and universities);
- Healthcare providers; and
- Research institutions.
What Is The Source of NIST SP 800-171 Rev 3 Requirements?
The requirements in NIST SP 800-171 Rev 2 are based on the 32 CFR Part 2002 and are derived from:
- Federal Information Processing Standards (FIPS) Publication 200 (FIPS 200); and
- The moderate security control baseline in NIST SP 800-53 Rev 5.
NIST determined the requirements in NIST SP 800-171 Rev 3 provide the necessary protection for federal information and systems that are covered under the Federal Information Security Modernization Act (FISMA). NIST applied tailoring criteria from FIPS 200 requirements for NIST SP 800-53 Rev 5 controls to come up with five (5) types of requirements, listed in Appendix C of NIST SP 800-171 Rev 3:
- NCO;
- FED;
- ORC
- N/A; and
- CUI.
Note: Non-Federal Organization (NFO) requirements were removed from NIST SP 800-171 Rev 3
What Are NCO Requirements?
NCO requirements are not directly related to protecting the confidentiality of CUI. NCO requirements are not mandatory to be implemented to comply with NIST SP 800-171 Rev 3.
What Are FED Requirements?
FEDrequirements are “uniquely federal” and primarily the responsibility of the US federal government. FED requirements are not mandatory to be implemented to comply with NIST SP 800-171 Rev 3.
What Are ORC Requirements?
ORC requirements are based on NIST SP 800-53 R4 security controls to provide a comprehensive set of security capabilities needed to protect organizational systems and support the concept of defense in depth. Some of the security controls may address similar or overlapping security topics that are covered by other related controls. These controls have been designated as ORC in the tailoring criteria. ORC requirements are not mandatory to be implemented to comply with NIST SP 800-171 Rev 3.
What Are N/A Requirements?
N/A requirements are not applicable to protecting CUI (e.g., Program Management (PM) and PII Processing and Transparency (PT) controls from NIST SP 800-53 R5). N/A requirements are not mandatory to be implemented to comply with NIST SP 800-171 Rev 3.
What Are CUI Requirements?
CUI requirements protect the confidentiality and/or integrity of assets that store, process and/or transmit CUI. CUI requirements must be implemented to comply with NIST SP 800-171 Rev 3.
Are NIST SP 800-171 Rev 3 Requirements Considered “Best Practices” For Cybersecurity?
No. NIST SP 800-171 requirements are not “best practices” and are better described as reasonable cybersecurity practices to protect sensitive and/or regulated data. NIST SP 800-171 Rev 3 only protects against unauthorized disclosure and modification of CUI. It does not contain security controls that are considered “best practices” in cybersecurity.
Is NIST SP 800-171 Rev 3 A Contractual Obligation?
Yes. Organizations must implement NIST SP 800-171 Rev 3 requirements as part of a contractual obligation with the US Government. Contractors (including subcontractors) that store, process and/or transmit CUI must comply with NIST SP 800-171.
What Is The Scope of NIST SP 800-171 Rev 3 Compliance?
From Section 1.1of NIST SP 800-171 Rev 3 that defines the scope of NIST SP 800-171 Rev 3 compliance efforts, “The security requirements in this publication are only applicable to components of nonfederal systems that process, store, or transmit CUI or that provide protection for such components. System components include workstations, servers, notebook computers, smartphones, tablets, input and output devices, network components, operating systems, virtual machines, database management systems, and applications.” The requirements in NIST SP 800-171 Rev 3 are intended to be used by US federal agencies in contractual vehicles or other agreements between those agencies and nonfederal organizations (e.g., contractors).
While NIST does not provide additional scoping guidance for NIST SP 800-171 Rev 3, the DoD provides scoping for CMMC Level 2 environments. Additionally, ComplianceForge’s Unified Scoping Guide (USG) provides scoping guidance for CUI and other types of sensitive/regulated data. The USG can be useful to help scope NIST SP 800-171 Rev 3, due to the “or that provide protection for such components” addition in the scoping guidance.
What Is Controlled Unclassified Information (CUI) For NIST SP 800-171 Rev 3 Compliance?
According to the US National Archives (NARA) that runs the US Government’s CUI Program, CUI is broadly defined as “information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act.”
In the context of cybersecurity, one of the more common forms of CUI is Controlled Technical Information (CTI) that broadly includes:
- Research and engineering data;
- Engineering drawings, and associated lists, specifications, standards, process sheets, manuals, technical reports, technical orders, catalog-item identifications, data sets, studies and analyses and related information, and
- Computer software executable code and source code.
Is Controlled Unclassified Information (CUI) Classified?
No. While CUI is sensitive information, it is not classified. CUI replaces For Official Use Only (FOUO) to protect unclassified, yet sensitive, data to prevent adverse national security and economic consequences.
Executive Orders (EO) 12356 and 13526 established the foundation for what "classified" data is, while EO 13556 established the foundation for CUI.
There are two (2) types of Unclassified data from the US Government's perspective:
- Controlled Unclassified Information (CUI):
- CUI Basic; and
- CUI Specified.
- Uncontrolled Unclassified Information (UUI):
- General UUI (not publicly released or FCI);
- Federal Contract Information (FCI); and
- Information that has been cleared for public release.
There are three (3) types of Classified data from the US Government's perspective:
- Confidential;
- Secret; and
- Top Secret.
What Are The NIST SP 800-171 Rev 3 Requirements Use To Protect CUI?
While NIST SP 800-171 Rev 3 contains 97 core requirements, the total number of discrete requirements is 297. As for Assessment Objectives (AOs) in NIST SP 800-171A Rev 3, there are 510 AOs that must be used to evaluate the requirements from NIST SP 800-171 R3. The requirement to use NIST SP 800-171A AOs was first defined by NARA’s Information Security Oversight Office (ISOO) in 2020 with CUI Notice 2020-04.
NIST SP 800-171 Rev 3 organizes the requirements according to 17 families. The requirements in NIST SP 800-171 Rev 3 all have a “3.X” prefix due to the requirements being in Chapter 3 of NIST SP 800-171.
The NIST SP 800-171 Rev 3 families are:
3.1 Access Control
This family of NIST SP 800-171 Rev 3 requirements focuses on logical access control.
3.2 Awareness and Training
This family of NIST SP 800-171 Rev 3 requirements focuses on end user training, specifically for personnel who handle CUI or administer technologies that support and/or protect CUI.
3.3 Audit and Accountability
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related event logging to maintain situational awareness of the CUI environment.
3.4 Configuration Management
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related configuration management practices to secure the CUI environment.
3.5 Identification and Authentication
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related Identity and Access Management (IAM) practices to securely limit access to only those people and processes with a legitimate business need.
3.6 Incident Response
This family of NIST SP 800-171 Rev 3 requirements focuses on incident response practices associated with the CUI environment.
3.7 Maintenance
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related maintenance activities within CUI environment.
3.8 Media Protection
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related media protection and handling practices.
3.9 Personnel Security
This family of NIST SP 800-171 Rev 3 requirements focuses on personnel-related management practices to ensure only necessary individuals have access to the CUI environment.
3.10 Physical Protection
This family of NIST SP 800-171 Rev 3 requirements focuses on physical security-related practices to physically secure the CUI environment.
3.11 Risk Assessment
This family of NIST SP 800-171 Rev 3 requirements focuses on risk management practices associated with the CUI environment.
3.12 Security Assessment and Monitoring
This family of NIST SP 800-171 Rev 3 requirements focuses on System Development Lifecycle (SDLC) practices to ensure the security of the CUI environment as technologies and processes change and evolve.
3.13 System and Communications Protection
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related network security aspects of the CUI environment.
3.14 System and Information Integrity
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related event monitoring to maintain situational awareness of the CUI environment.
3.15 Planning
This family of NIST SP 800-171 Rev 3 requirements focuses on the organization’s strategic plans to govern cybersecurity risks and threats to protect the CUI environment.
3.16 System and Services Acquisition
This family of NIST SP 800-171 Rev 3 requirements focuses on technology-related development and acquisition processes to maintain the confidentiality and integrity of the CUI environment.
3.17 Supply Chain Risk Management
This family of NIST SP 800-171 Rev 3 requirements focuses on Cybersecurity Supply Chain Risk Management (C-SCRM)-related practices to operationalize concepts from NIST SP 800-161 Rev 1 to protect the CUI environment.
What Does It Mean To Comply With NIST SP 800-171 Rev 3?
The DoD has a third-party assessment methodology in place to provide conformity assessments for NIST SP 800-171 Rev 2, which is the Cybersecurity Maturity Model Certification (CMMC). Eventually, the DoD will release a “CMMC 3.0” model that provides coverage for NIST SP 800-171 Rev 3.
For non-DoD contactors, compliance with NIST SP 800-171 Rev 2 is “on the honor system” similar to compliance with HIPAA, PCI DSS, GDPR and other common compliance obligations that organizations must comply with.
What Are The Penalties For Non-Compliance With NIST 800-171 Rev 3?
Non-compliance with NIST SP 800-171 Rev 2 could be a False Claims Act (FCA) violation and the US Department of Justice (DOJ) is taking FCA violations seriously. Additional penalties for non-compliance with NIST 800-171 Rev 2 include, but are not limited to:
- Contract Termination. It is reasonably expected that the U.S. Government will terminate contracts with prime contractors over non-compliance with DFARS / NIST 800-171 requirements since it is a failure to uphold contract requirements. Subcontractor non-compliance will cause a prime contractor to be non-compliant, as a whole.
- Criminal Fraud. If a company states it is compliant when it knowingly is not compliant, that is misrepresentation of material facts. This is a criminal act that is defined as any act intended to deceive through a false representation of some fact, resulting in the legal detriment of the person who relies upon the false information (e.g., False Claims Act).
- Breach of Contract Lawsuits. Both prime contractors and subcontractors could be exposed legally. A tort is a civil breach committed against another in which the injured party can sue for damages. The likely scenario for a DFARS / NIST 800-171-related tort would be around negligence on behalf of the accused party by not maintaining a specific code of conduct (e.g., DFARS / NIST 800-171 cybersecurity controls).
As you can see from those examples, the cost of non-compliance is quite significant. As always, seek competent legal counsel for any pertinent questions on your specific compliance obligations.
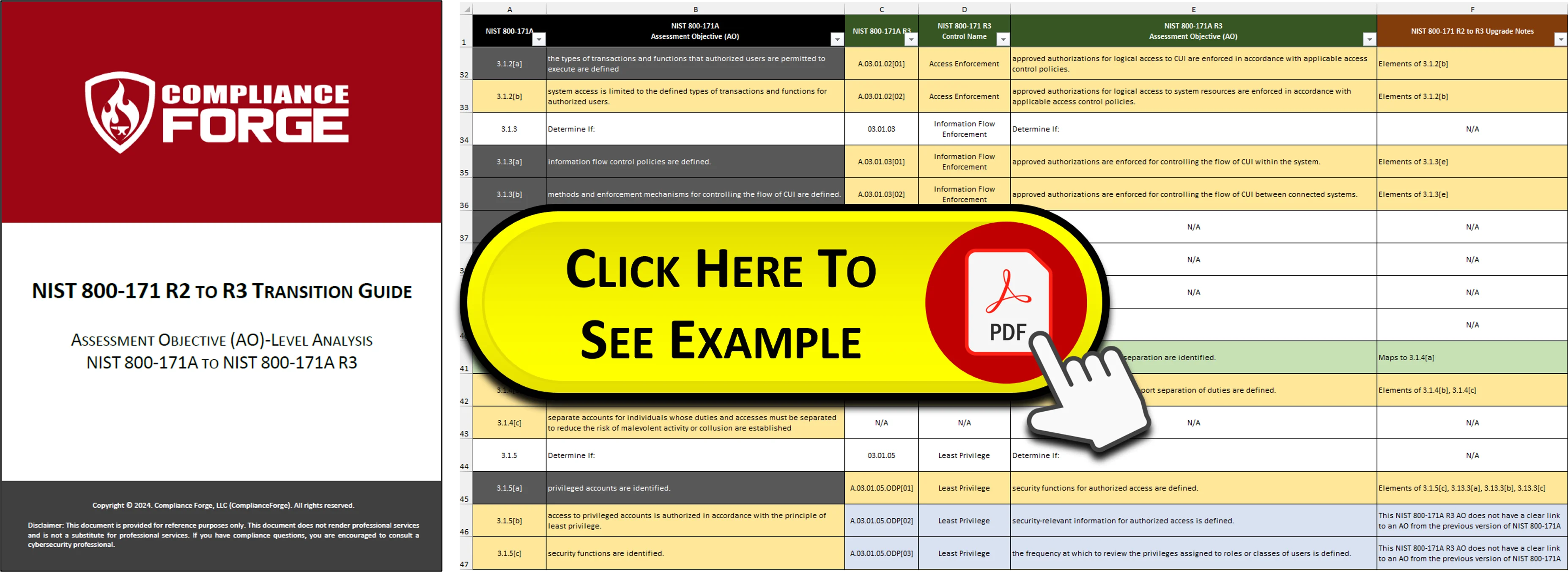
How Do I Upgrade To NIST 800-171 Rev 3?
Sooner, rather than later, the US Government's global supply chain will have to transition to NIST 800-171 Rev 3. ComplianceForge provides a free resource for organizations migrating from NIST 800-171 Rev 2 to Rev 3. This guide provides an Assessment Objective (AO)-level analysis to address differences:
- Over 1/3 are minimal effort (clear, direct mapping);
- Approximately 1/5 are moderate effort (indirect mapping); and
- Approximately 1/2 are significant effort (no clear mapping or new AOs).
How Do I Comply With NIST SP 800-171 Rev 3?
ComplianceForge has been on the forefront of developing editable policies, standards, procedures and other templates to address NIST 800-171 compliance since 2016 when it was first released. As Department of Defense (DoD) requirements evolved to include third-party attestation through the Cybersecurity Maturity Model Certification (CMMC), so did ComplianceForge’s solutions, where we offer affordable, editable cybersecurity policies, standards, procedures and other templates to address NIST 800-171 Rev 2 & Rev 3.
NIST 800-171 compliance starts with documentation for the very simple fact that when it comes to cybersecurity compliance, if it is not documented then it does not exist. That is the reality of how audits/assessments work and non-existent or weak documentation can lead to non-compliance. We've been involved in NIST 800-171 compliance since 2016, where we have a long track record of successfully supporting our clients with quality documentation and support.
When it comes to NIST 800-171 compliance, ComplianceForge's editable policies, standards, procedures and other templates are a business accelerator - our products can save you time and significantly reduce the labor costs that are traditionally associated with researching and developing NIST 800-171 policies, standards and procedures on your own or by hiring a consultant to do it for you. These are not "fill in the blanks" templates - while they are expected to be edited for your specific needs, these policies, standards and procedures templates are written to address leading secure practices. ComplianceForge documentation can be scoped to address multiple environments (e.g., on-premises and/or in a hosted environment).
Affordable, Editable NIST 800-171 Rev 3 Compliance Documentation For DFARS 252.204-7012 Compliance
We listened to our customers and we created several products that are specific to NIST 800-171 compliance. We had an overwhelming request from companies to help them become NIST 800-171 compliant and most told us they do not know where to start, but they just know that this is a requirement they cannot run from.
What Problem Does ComplianceForge's NIST SP 800-171 Rev 3 Documentation Solve?
We sell cybersecurity documentation - policies, standards, procedures and more! Our documentation is meant to help companies become audit-ready!
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive NIST 800-171 compliance documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. ComplianceForge offers NIST 800-171 documentation solutions that can save your organization significant time and money!
- Compliance Requirements - The reality of non-compliance with NIST 800-171 requirements means lost business and potential fines. In addition to losing contracts, charges of fraud may be leveled on companies that claim to be compliant with NIST 800-171 but cannot provide evidence. Our documentation can help you become and stay compliant with NIST 800-171 where you have documented evidence to prove it!
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. Our documentation provides mapping to NIST 800-53 and other leading security frameworks to show you exactly what is required to both stay secure and compliant. Being editable documentation, you are able to easily maintain it as your needs or technologies change.
How Does ComplianceForge Help Me Comply With NIST SP 800-171 Rev 2?
We take a holistic approach to creating comprehensive cybersecurity documentation that is both scalable and affordable. This is beyond just generic policies and allows you to build out an audit-ready cybersecurity program for your organization!
- Clear Documentation - In an audit, clear and concise documentation is half the battle. ComplianceForge provides comprehensive documentation that can prove your NIST 800-171 compliant security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - Time is money! Our cybersecurity documentation addresses DFARS and FAR requirements and this can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - We did the heavy lifting. Our documentation is mapped to the NIST 800-53, as well as other leading security frameworks!
ComplianceForge Has “DIBCAC Battle Tested” Policies, Standards & Procedures For NIST SP 800-171
ComplianceForge’s NIST 800-171 / CMMC documentation has been used successfully by multiple companies during DIBCAC assessments to efficiently and effectively generate the necessary artifact documentation to demonstrate compliance with NIST SP 800-171 controls and NIST SP 800-171A control objectives. This battle tested documentation includes the necessary policies, standards, procedures, SSP, POA&M, Incident Response Plan (IRP) and other documentation that are expected to exist to successfully pass a third-party assessment, be it DIBCAC or a C3PAO.
When you look at NIST 800-171 as it compares to other cybersecurity requirements, it is requiring companies to have a relatively-strong set of cybersecurity controls in place that range from administrative processes to protective technologies. We help customers that range from the Fortune 500 down to small and medium-sized businesses comply with this DFARS requirement. Our products are scalable, professionally-written and affordable.
Editable NIST SP 800-171 R3 Policies, Standards, Procedures Templates
ComplianceForge has policies, standards, procedures and other documentation (e.g., SCRM plan) necessary to comply with NIST 800-171 Rev 3. This includes mapping procedures down to the Assessment Objective (AO)-level in NIST 800-171A R3 to ensure that there is comprehensive coverage for your compliance needs.
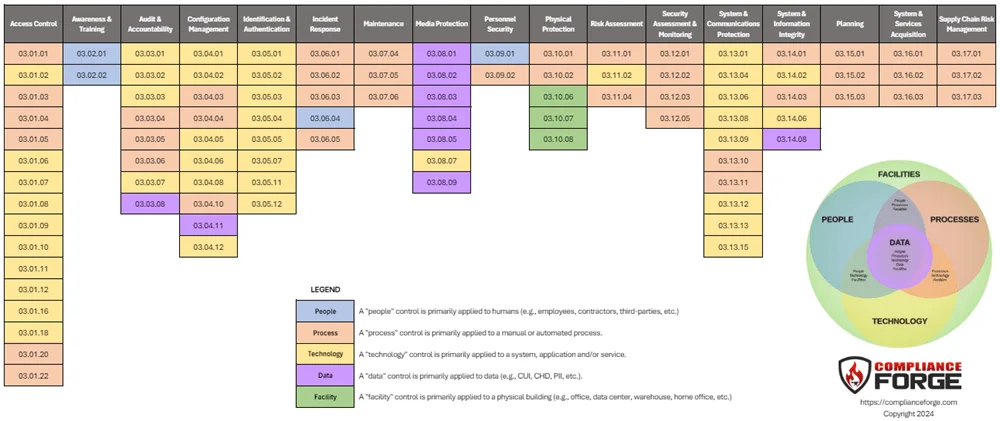
The "NIST 800-171 in a nutshell" graphic show below helps depict NIST 800-171 R3 requirements from Peope, Process, Technology, Data and Facility (PPTDF) perspective. This can help better visualize what the various requirements are (e.g., administrative, technical solutions, configurations, etc.). You can download the PDF version here and you can read more about the concept of PPTDF here.
- PEOPLE - A "people" control is primarily applied to humans (e.g., employees, contractors, third-parties, etc.).
- PROCESS - A "process" control is primarily applied to a manual or automated process.
- TECHNOLOGY - A "technology" control is primarily applied to a system, application and/or service.
- DATA - A "data" control is primarily applied to data (e.g., CUI, CHD, PII, etc.).
- FACILITY - A "facility" control is primarily applied to a physical building (e.g., office, data center, warehouse, home office, etc.).
NIST SP 800-171 Rev 3Documentation Done Right - Scalable, Comprehensive & Efficient
ComplianceForge is an industry leader in NIST 800-171 compliance. We specialize in cybersecurity compliance documentation and our products include the policies, standards, procedures and POA&M/SSP templates that companies (small, medium and large) need to comply with NIST 800-171. We've been writing cybersecurity documentation since 2005 and we've been writing documentation specific to NIST 800-171 since 2016. We are here to help make NIST 800-171 compliance as easy and as affordable as possible!
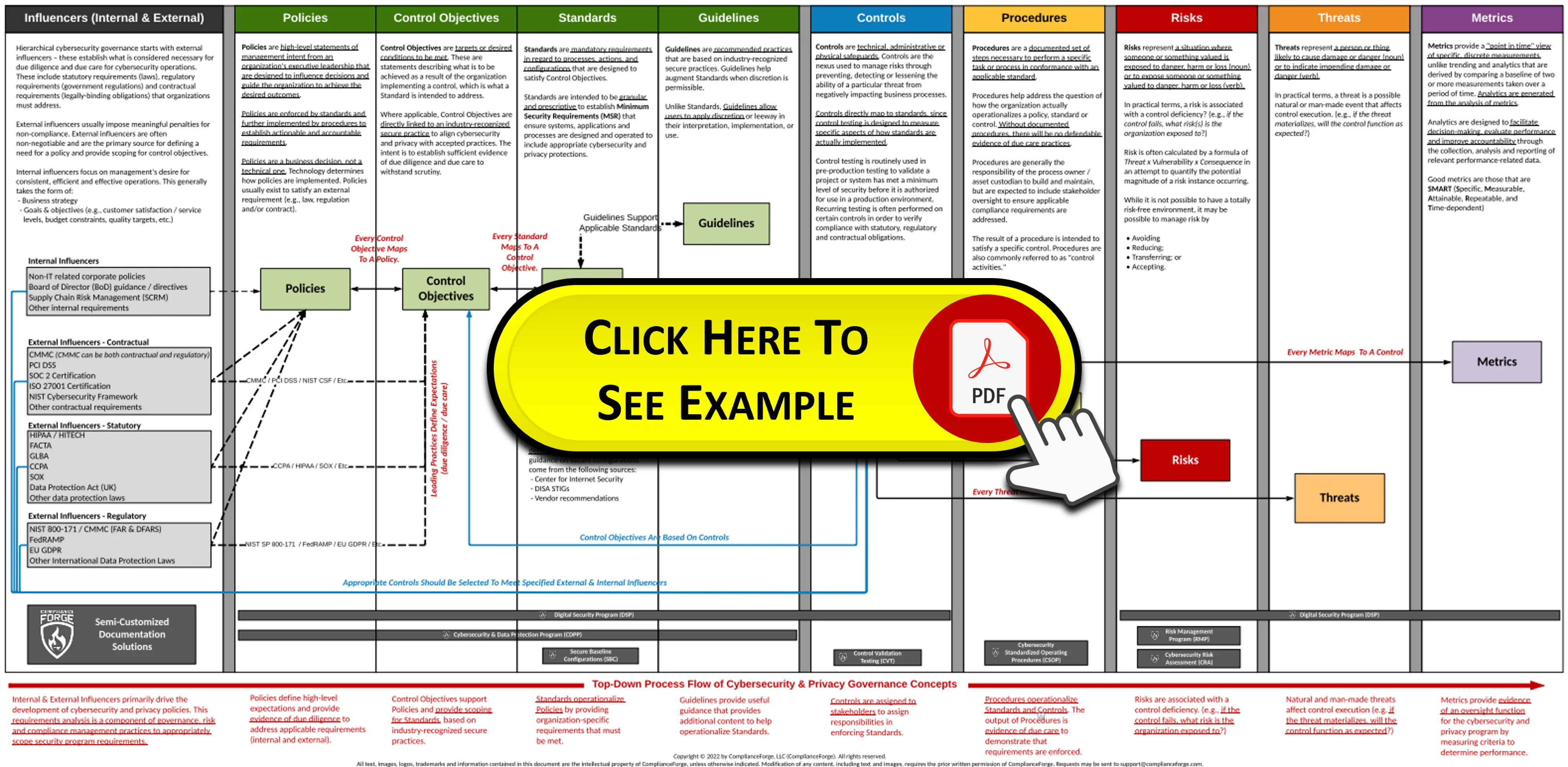
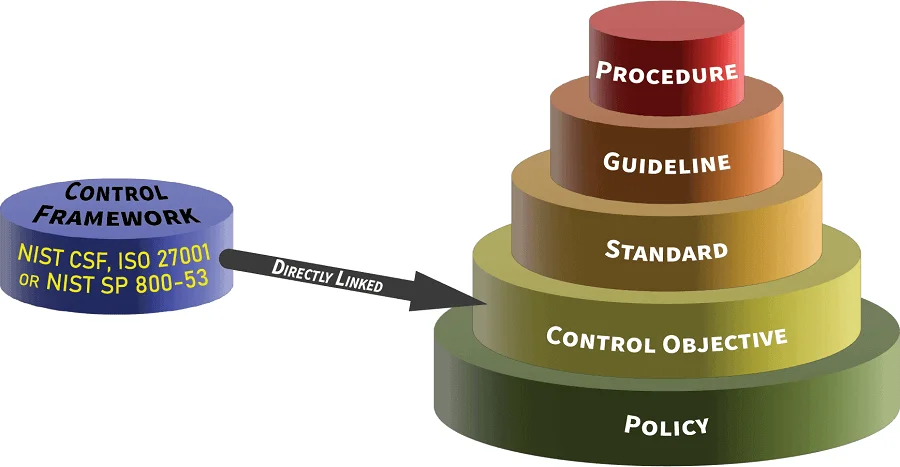
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hierarchical nature of cybersecurity documentation is needed to demonstrate the unique nature of these components, as well as the dependencies that exist. ComplianceForge created a reference model that is designed to encourage clear communication by defining cybersecurity documentation components and how those are linked. This model is based on industry-recognized terminology from NIST, ISO, ISACA and AICPA to addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, assessment objectives, risks, threats, procedures & metrics. This also addresses what SSPs, POA&Ms and secure configurations are and how those integrate into an organization's existing cybersecurity documentation.
We leverage the Hierarchical Cybersecurity Governance Framework to develop the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care for our clients. This methodology towards documentation acknowledges the interconnectivity that exists between policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. Essentially, ComplianceForge simplified the concept of the hierarchical nature of cybersecurity and privacy documentation that you can see in the downloadable diagram shown below. This helps demonstrate the unique nature of these components, as well as the dependencies that exist. You can download the example to better understand how we write our documentation that links policies all the way down to metrics. This is a great solution for any organization currently using or migrating to a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) platform to help automate their governance practices. Click on the image below to download the PDF:
As a quick summary of your requirements to comply with NIST 800-171, you are expected to have several different "documentation artifacts" to prove that your cybersecurity program exists. The reality with compliance assessments is that if something is not documented, you cannot prove it exists. Given that reality, you need to ensure your company has the proper cybersecurity documentation in place:
- NIST SP 800-171 specific policies, standards & procedures;
- System Security Plan (SSP);
- Supply Chain Risk Management (SCRM) Plan; and
- Plan of Action & Milestones (POA&M).
When it comes to being "audit ready" for a company with NIST 800-171, there is no such thing as "Bronze, Silver or Gold" levels of compliance since a standard is a standard for a reason. This is where documentation is king, since in cybersecurity compliance audits, if it is not documented then it does not exist.
ComplianceForge can provide you with the documentation you need to demonstrate evidence of due care and due diligence to be considered compliant (e.g., policies, standards, procedures, SSP & POA&M). Our affordable solutions range from cybersecurity policies & standards documentation, to NIST 800-171 compliance checklists, to program-level documentation, such as "turn key" incident response, risk management or vulnerability management program documents. Our focus is on helping you become audit ready!
Is Your Organization Assessment Ready for NIST 800-171?
When you "peel back the onion" and prepare for a NIST 800-171 audit, there is a need to address "the how" for certain topics. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW it gets done. We did the heavy lifting and created several program-level documents to address this need and they integrate with either the Cybersecurity & Data Protection Program (CDPP) or Digital Security Program (DSP) to provide your organization with a set of robust documentation to prepare for your audit. This gives you a full stack of documentation that covers your needs for policies, standards, procedures, System Security Plan (SSP) and a Plan of Action & Milestones (POA&M).
There are no products listed under this category.