
SEC Final Rule - Cybersecurity Compliance & Cybersecurity Materiality
The Security and Exchanges Commission (SEC) recently published its Final Rule: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure that will force publicly traded companies to adjust practices for ongoing cybersecurity governance and incident response. The SEC, Generally Accepted Accounting Principles (GAAP) and International Financial Reporting Standards (IFRS) lack specificity in defining the criteria for materiality. Therefore, organizations generally have leeway to define it on their own. The lack of authoritative definition for materiality is not unique, since the concept of risk appetite, risk tolerance and risk threshold also suffer from nebulous definitions by statutory and regulatory authorities.
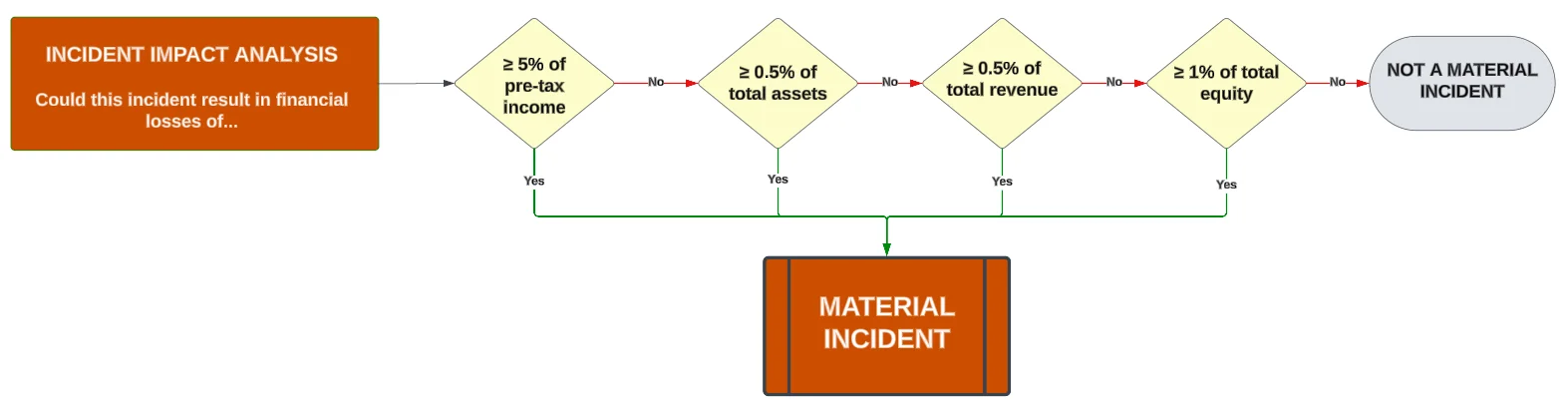
How Do You Determine SEC Cybersecurity Rule Materiality?
For an item to be considered material, the control deficiency, risk, threat or incident (singular or a combination) generally must meet one, or more, of the following criteria where the potential financial impact is:
- ≥ 5% of pre-tax income;
- ≥ 0.5% of total assets;
- ≥ 1% of total equity (shareholder value); and/or
- ≥ 0.5% of total revenue.
This materiality determination can be visualized with this infographic with the callout for publicly traded companies having a requirement to publicly disclose material cybersecurity incidents:
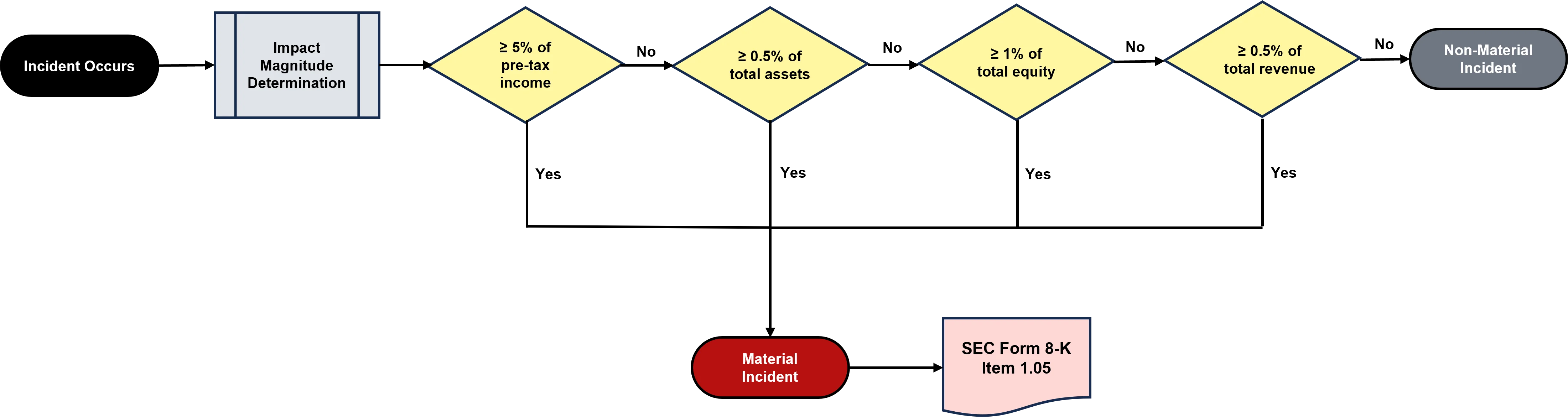
Material Risk vs Material Threat vs Material Incident
With evolving regulatory requirements for public disclosures, it is increasingly important to understand the nuances between material weakness vs material risk vs material threat vs material incident, since they have specific meanings:
SEC Cybersecurity Rule - Material Weakness
A material weakness is a deficiency, or a combination of deficiencies, in an organization's cybersecurity and/or data privacy controls (across its supply chain) where it is probable that reasonable threats will not be prevented or detected in a timely manner that directly, or indirectly, affects assurance that the organization can adhere to its stated risk tolerance.
- When there is an existing deficiency (e.g., control deficiency) that poses a material impact, that is a material weakness (e.g., inability to maintain access control, lack of situational awareness to enable the timely identification and response to incidents, lacking pre-production control validation testing, etc.).
- A material weakness will be identified as part of a gap assessment, audit or assessment as a finding due to one or more control deficiencies.
- A material weakness should be documented in an organization's Plan of Action & Milestones (POA&M), risk register, or similar tracking mechanism used for remediation purposes.
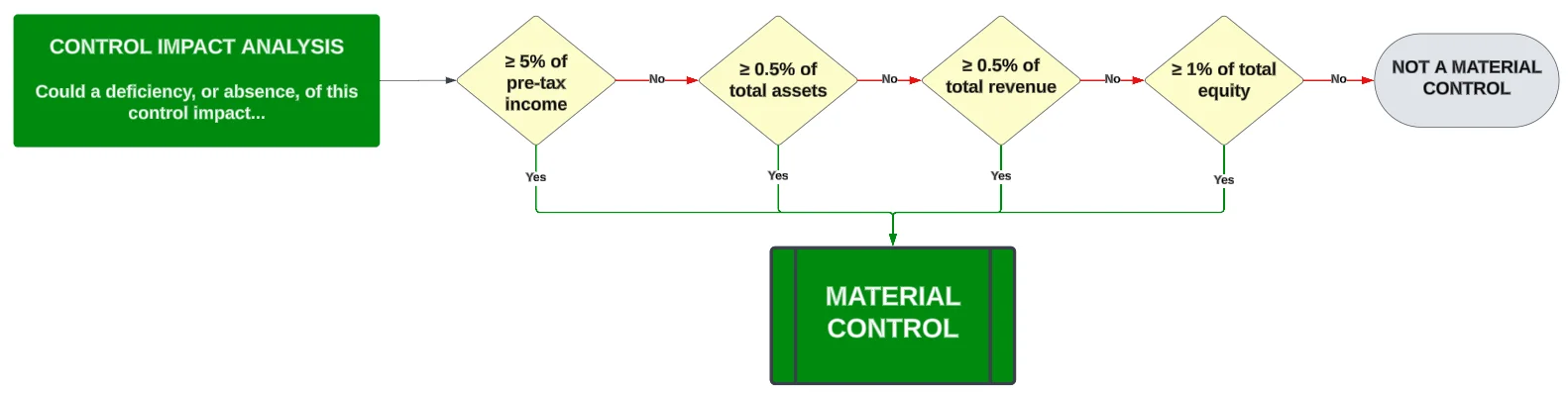
SEC Cybersecurity Rule - Material Risk
A risk is a situation where (1) someone or something valued is exposed to danger, harm or loss (noun); or (2) to expose someone or something valued to danger, harm or loss (verb).
- When there is an identified risk that poses a material impact, that is a material risk.
- A material risk is a quantitative or qualitative scenario where the exposure to danger, harm or loss has a material impact (e.g., potential class action lawsuit, death related to product usage, etc.)
- A material risk should be identified and documented in an organization's "risk catalog" that chronicles the organization's relevant and plausible risks.
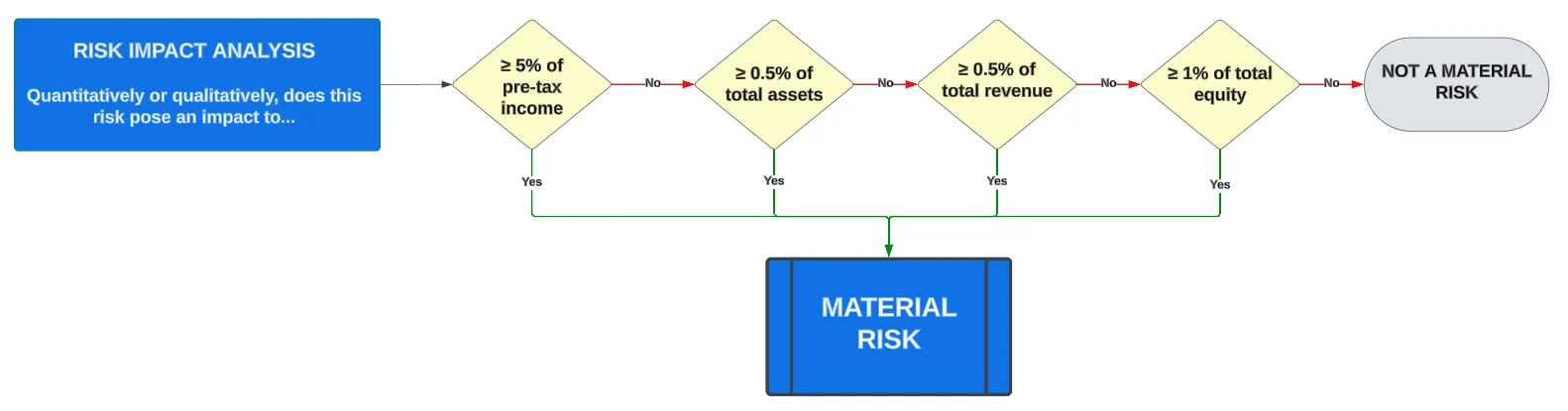
SEC Cybersecurity Rule - Material Threat
A threat is (1) a person or thing likely to cause damage or danger (noun); or (2) to indicate impending damage or danger (verb).
- When there is an identified threat that poses a material impact, that is a material threat.
- A material threat is a vector that causes damage or danger that has a material impact (e.g., poorly governed Artificial Intelligence (AI) initiatives, nation state hacking operations, dysfunctional internal management practices, etc.).
- A material threat should be identified and documented in an organization's "threat catalog" that chronicles the organization's relevant and plausible threats.
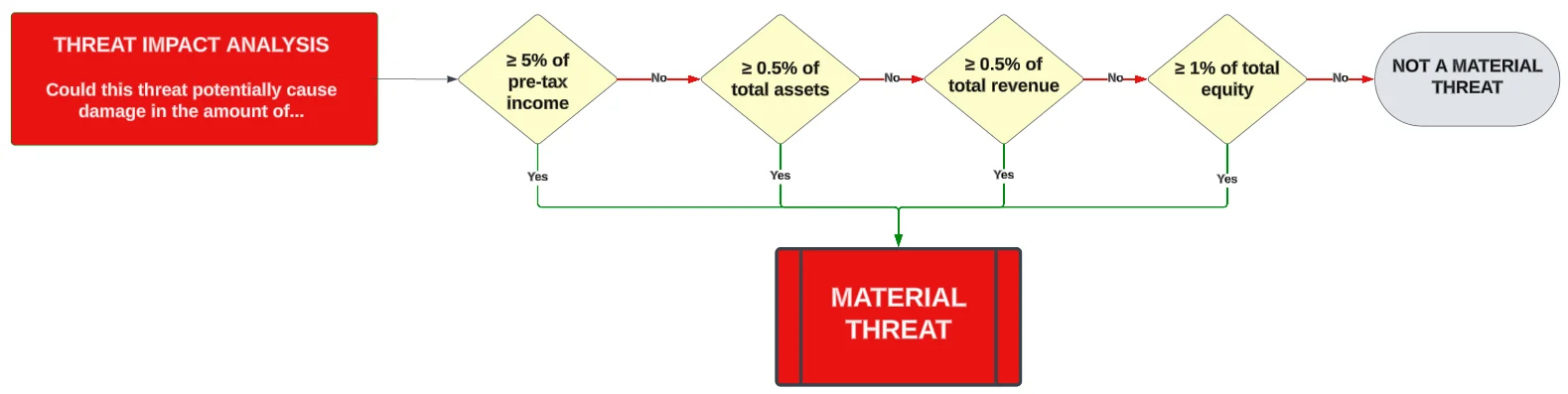
SEC Cybersecurity Rule - Material Incident
An incident is an occurrence that actually or potentially (1) jeopardizes the Confidentiality, Integrity, Availability or Safety (CIAS) of a system, application, service or the data that it processes, stores and/or transmits; or (2) constitutes a violation or imminent threat of violation of an organization's policies, procedures or acceptable use practices.
- When there is an incident that poses a material impact, that is a material incident.
- A material incident is an occurrence that does or has the potential to (1) affect the CIAS of systems, applications, services or data; or (2) a violation of organizational practices that has a material impact (e.g., malware on sensitive/regulated systems, emergent AI actions, illegal conduct, business interruption, etc.).
- A material incident should be identified and documented in an organization's Incident Response Plan (IRP) that chronicles the organization's relevant and plausible incidents, so there are appropriate steps in place to identify, respond to and recover from such incidents.
SEC Final Rule Cybersecurity Risk Management
In collaboration with the Secure Controls Framework (SCF), ComplianceForge authored a white paper on this subject of aligning risk appetite, risk tolerance and risk thresholds with your organization's strategic, operational and tactical business planning activities. You'll find the SEC Final Rule discussed in the document, as well as how to address cybersecurity governance from a strategic, operational and tactical perspective.
Enterprise Risk Management (ERM): A Practitioner’s Guide To Risk Management
There are no products listed under this category.

