The Secure Controls Framework (SCF) Is The Common Controls Framework (CCF)
The Secure Controls Framework (SCF) is a comprehensive cybersecurity and data privacy control framework designed to help organizations implement and manage information security, risk management and compliance requirements. The SCF is a metaframework that is a "framework of frameworks" made up of over 100 cybersecurity and data privacy laws, regulations and frameworks. The end result is a comprehensive control framework that contains over 1,300 controls and is logically organized into 33 domains. There are multiple benefits to using the SCF:
- There is no cost to use the SCF and quite a few Governance, Risk and Compliance (GRC) platforms natively support the SCF as a built-in control set. The latest version of the SCF can be downloaded directly from the SCF website at: https://securecontrolsframework.com;
- The structure of the SCF normalizes disparate control language into something that is usable across technology, cybersecurity, privacy and other departments where they can share the same control language;
- The SCF enables not only intra-organization standardization, but inter-organization standardization where control GOV-03 means the same thing to one organization to any other organization using the SCF;
- The SCF is a more efficient way to operationalize cybersecurity and data privacy operations by simplifying the underlying controls that power an organization’s cybersecurity program; and
- The SCF provides a straightforward and scalable method to define those “must have” and “nice to have” requirements into a holistic control set to operationalize cybersecurity operations, risk management and third-party governance.
The “sweet spot” for the SCF is medium to large organizations, but it has been successfully used by small organizations. Any organization with complex compliance requirements can benefit from using the SCF. SCF is used by organizations to:
- Align cybersecurity and data protection controls with an expansive catalog of laws, regulations and frameworks;
- Provide a streamlined set of actionable security controls to address its specific compliance, security and resiliency needs; and
- Support risk management and continuous monitoring programs.
The SCF is much more than just a cybersecurity control set, since the SCF has:
- Control weighting to help understand risk, since not all controls are the same;
- A built-in risk catalog and threat catalog, where those risks and threats are mapped to SCF controls;
- A capability maturity model to help define what right looks like for your organization;
- A risk management model to enable holistic risk management practices at the control level;
- An Evidence Request List (ERL) to define expected assessment artifacts that would be reasonably expected to satisfy controls; and
- Assessment Objectives (AOs) to help provide objective criteria that can be used to assess controls.
What Is The Secure Controls Framework (SCF)?
|
If you are not familiar with the Secure Controls Framework (SCF), it was developed with the ambitious goal of providing a comprehensive catalog of cybersecurity and privacy control guidance to cover the strategic, operational and tactical needs of organizations, regardless of its size, industry or country of origin. By using the SCF, your IT, cybersecurity, legal and project teams can speak the same language about controls and requirement expectations! The SCF is an open source project that provides free cybersecurity and privacy controls for business. The SCF focuses on internal controls, which are the cybersecurity and privacy-related policies, standards, procedures and other processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected and corrected. |
 |
Where Can I Find Editable SCF-Based Policies, Standards & Procedures?

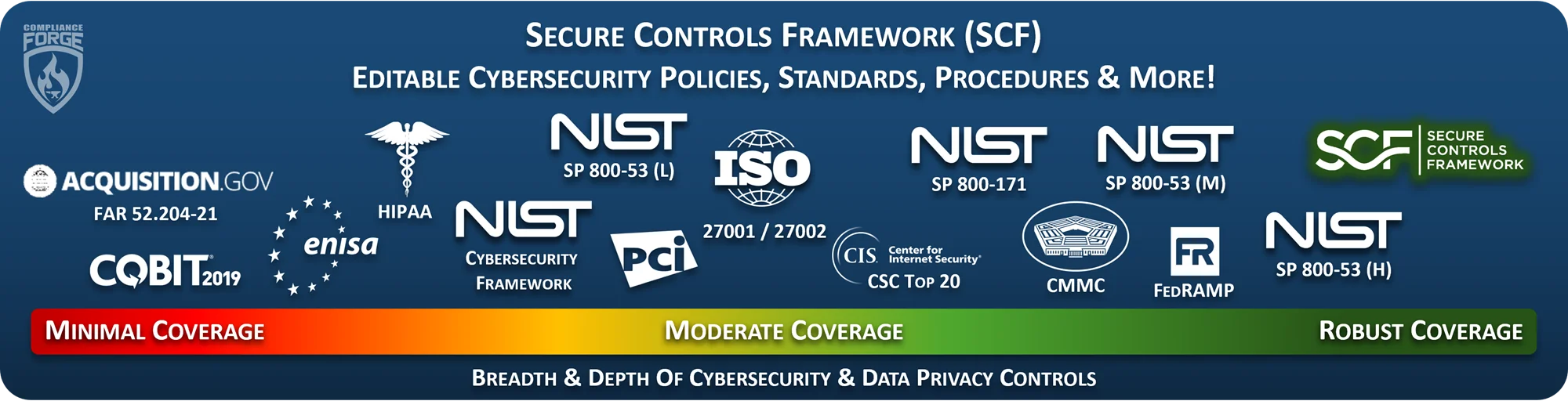
If you use the SCF, you will want to buy one of these bundles, since the Digital Security Program (DSP) has 1-1 mapping between the SCF and the DSP. We sell the policies, standards, procedures & more that will compliment the SCF controls that you use! The DSP provides you with SCF-aligned policies, standards, guidelines, metrics, controls and capability maturity criteria. The Cybersecurity Standardized Operating Procedures (CSOP) provides you with SCF-aligned procedures/control activities. These two products alone can save you hundreds of hours of document writing and can help your organization hit the ground running with the SCF.
|
|
The SCF is designed to empower organizations to design, implement and manage both cybersecurity and privacy principles to address strategic, operational and tactical guidance. It is far more than building for compliance - we know that if you build-in security and privacy principles, complying with statutory, regulatory and contractual obligations will come naturally. It is comprised of thirty-two (32) domains that cover the high-level topics that are expected to be addressed by cybersecurity and privacy-related statutory, regulatory and contractual obligations. These bundles can help you operationalize your cybersecurity and privacy programs by efficiently mapping to over 100 statutory, regulatory and contractual frameworks. This will allow your cyber and privacy teams to speak the same language and more efficiently manage risks. |
ComplianceForge Is A SCF Licensed Content Provider (LCP)
|
ComplianceForge is able to sell cybersecurity and data protection policies, standards and procedures based on the Secure Controls Framework (SCF) as a SCF Licensed Content Provider (LCP). The benefit ComplianceForge brings to operationalizing the SCF is (1) decreased cost and (2) increased speed of adoption. ComplianceForge's SCF-based policies, standards and procedures can save an organization a significant amount of money from the labor-related costs to research, write and refine cybersecurity documentation. ComplianceForge's SCF-based documentation can also be obtained the same day you purchase it, so the time savings is immense. |
 |
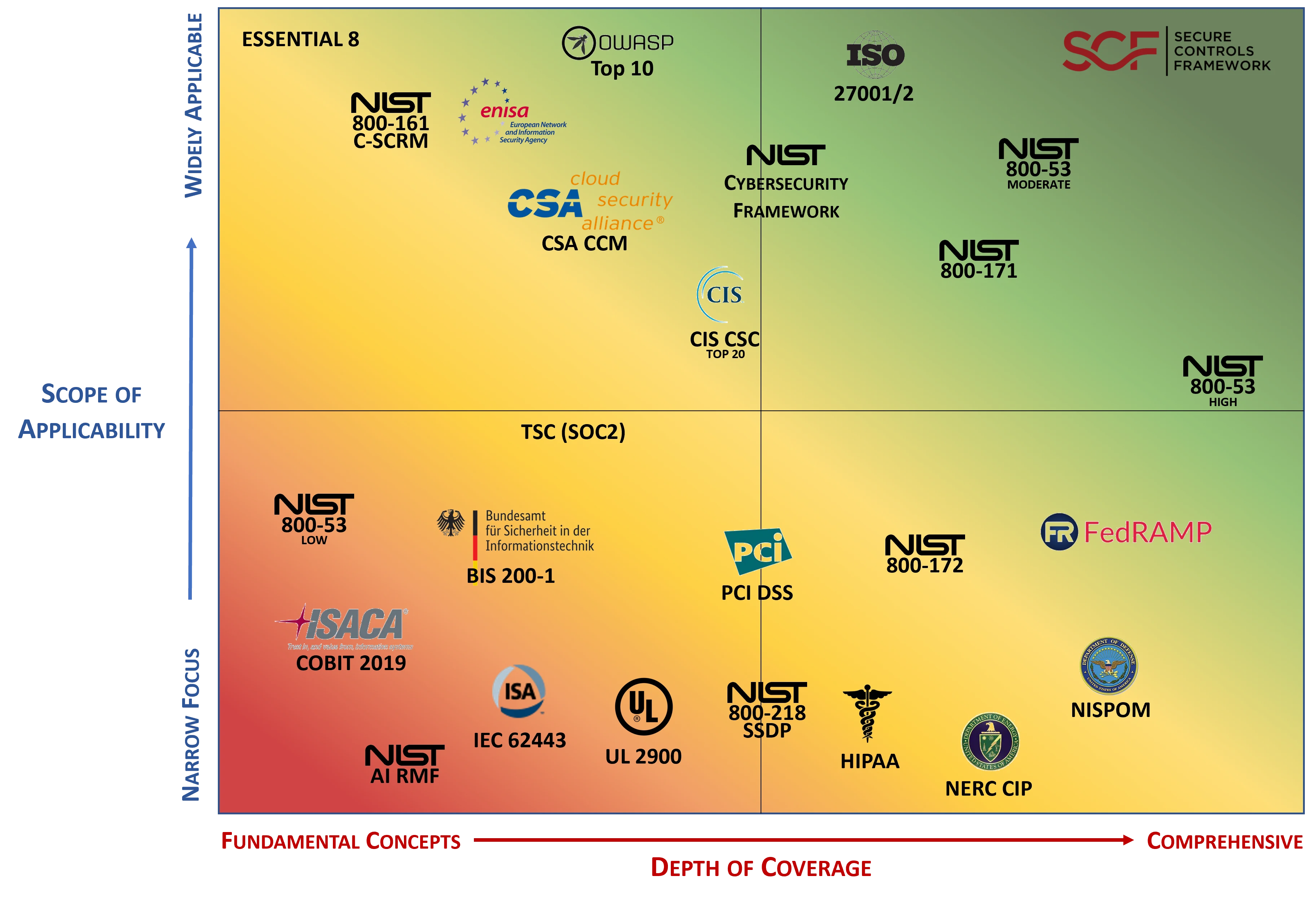
Best-In-Class Coverage
|
|
Where the SCF is truly unique is its industry-agnostic focus on both security and privacy controls that creates a hybrid that makes up for shortcomings by leading frameworks: The SCF is designed to empower organizations to design, implement and manage both cybersecurity and privacy principles to address strategic, operational and tactical guidance. It is far more than building for compliance - we know that if you build-in security and privacy principles, complying with statutory, regulatory and contractual obligations will come naturally. Controls are often a missing piece in a company's cybersecurity program or controls exist in "compliance islands" where the controls are only applicable to certain compliance requirements, such as SOX, PCI DSS or NIST 800-171. That might be easy from a compliance perspective, but it is not good security. The SCF is designed to help companies be both secure and compliant. |
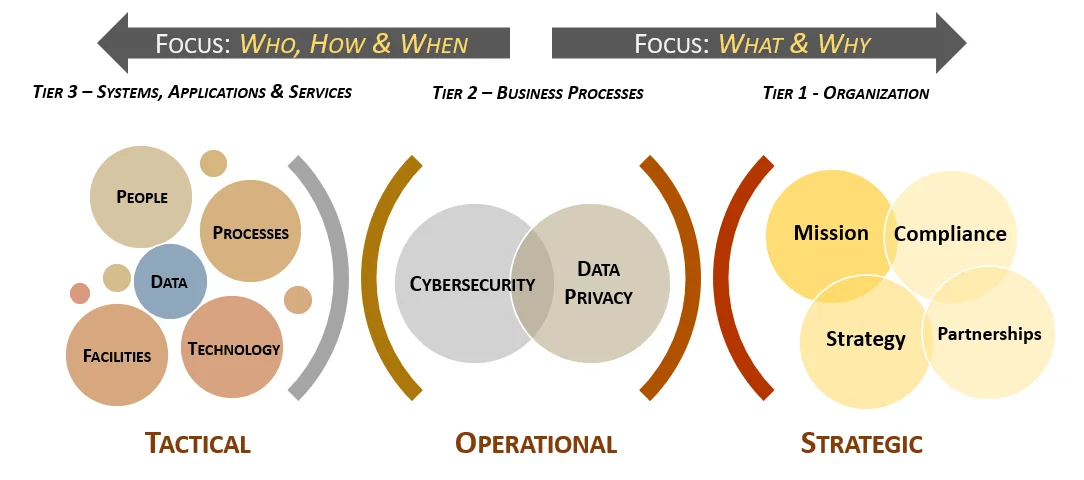
Focus On What Matters - Data-Centric Approach To Governing People, Processes & Technology
|
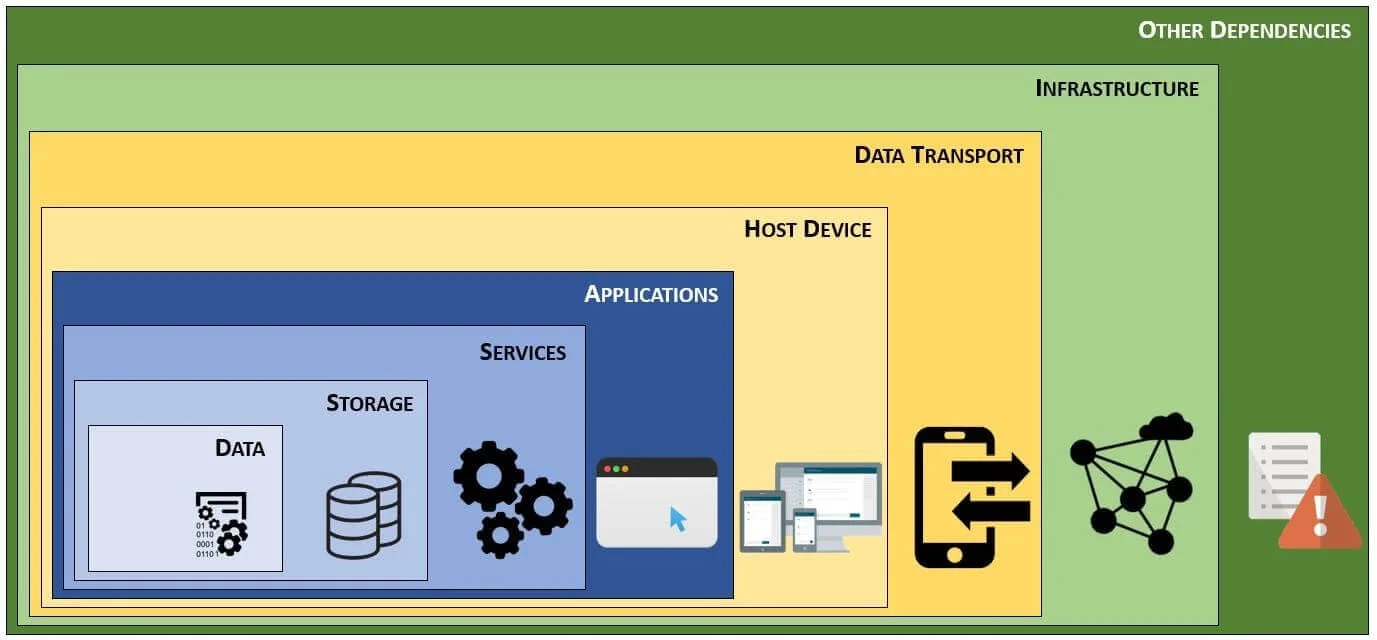
It is important to understand that controls exist to protect an organization’s data. In support of this concept of being data-centric, look at the example of asset management requirements in terms of cybersecurity and privacy – those administrative, technical and physical security controls do not primarily exist to protect the inherent value of the asset, but the data it contains, because assets are merely data containers. Assets, such as laptops, servers and network infrastructure are commodities that can be easily replaced, but the data cannot. This mindset of being data-centric is crucial to understand when developing, implementing and governing a cybersecurity and privacy program. While most organizations do not have a Data Centric Architecture (DCA), based on technical debt and legacy processes, it is possible to implement Data Centric Security (DCS) that can put the organization on a path to building a DCA. This all comes down to designing, implementing and managing the appropriate cybersecurity and privacy controls that govern people, processes and technology. This is where the DSP and SCF can be invaluable. |
 |
 |
|
|
|
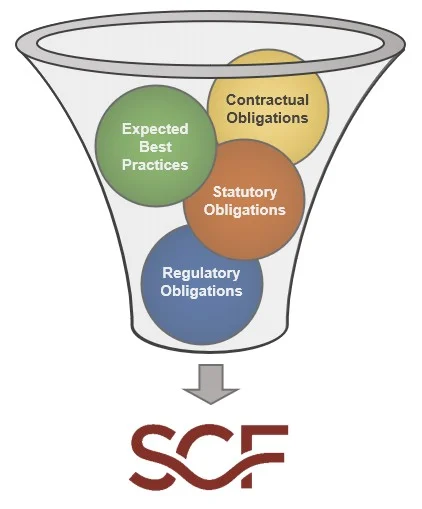
Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
|
 |
|
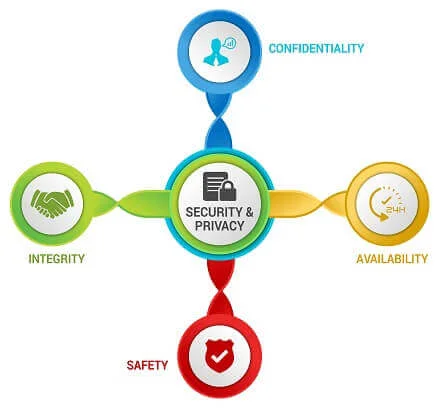
For years, the "CIA Triad" defined the pillars of cybersecurity. Things have changed and it is now the "CIAS Quadrant" that governs the reasons for implementing cybersecurity and privacy controls. These four pillars are Confidentiality, Integrity, Availability and Safety. The DSP & SCF can help you implement these four principles of cybersecurity and privacy in your organization!
|
There are no products listed under this category.