
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the VPMP is to help answer common questions we receive.
What Is The Vulnerability & Patch Management Program (VPMP)?
Is your organization looking for a patch and vulnerability management program? ComplianceForge's Vulnerability & Patch Management Progam (VPMP) is an editable Microsoft Word document that provides program-level guidance to directly supports your company's policies and standards for managing vulnerabilities. This product addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations. Answering how vulnerabilities are managed is one of the most common deficiencies in audits, so this product fills a very crucial gap in most cybersecurity programs. The VPMP addresses fundamental needs when it comes to reasonably-expected vulnerability management requirements:
- Who is responsible for managing vulnerabilities?
- What is in scope for patching and vulnerability management?
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance.
- Information Assurance (IA) guidance to support secure engineering activities.
Some of our customers claim they are looking for a vulnerability management program framework that aligns with some of the leading frameworks. Our VPMP is framework-independent (e.g., ISO, NIST, COBIT, etc.), and it can serve as the cornerstone in your organization's technical vulnerability management program. It can stand alone or be paired with other specialized products we offer. The VPMP was one of the most challenging documents we've developed over the last decade. The reason for this is the need to address and unify various components that are complex on their own - patching systems, vulnerability scanning, remediation activities and penetration testing. What this program-level document establishes is the framework to provide direction to and govern those functions, regardless of who is actually doing the work. Depending on the makeup of the organization, it can be pure IT, cybersecurity personnel, outsourced staffing or a combination of all. Given the cost associated with the effort to create a documented vulnerability management program from scratch, the VPMP priced to be affordable to all organizations.
In no order of preference, these are the most common buyers for the VPMP:
- A new contract/regulation specifically calls out a vulnerability management capability and the vendor can't meet that requirement (e.g., NIST 800-171);
- A company is going to get audited soon by an external party and is scrambling for documentation its staff can easily implement;
- A company just failed an external audit and its staff is scrambling to implement a program to make up for the deficiency in the audit;
- Recent leadership changes uncovered internal program weaknesses that need to be remediated;
- An annual internal review of IT General Controls (ITGC) pointed to deficient processes within vulnerability management; and
- A risk assessment identified remediation efforts as deficient and the issue needs to be remediated to remove it from the risk register.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The VPMP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. It is not uncommon for organizations to spent hundreds of man-hours on this type of documentation effort and only have it end in failure.
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security policies and standards. Requirements range from PCI DSS to HIPAA to NIST 800-171. The CDPP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements. The CDPP maps to several leading compliance frameworks so you can clearly see what is required!
- Audit Failures - Similar to risk management, most organizations run into trouble in audits when asked HOW vulnerabilities and patches are managed, since they cannot provide documentation beyond policies and standards. The VPMP addresses the HOW for you!
- Vendor Requirements - Requirements such as PCI DSS, MA 201 CMR 17.00 and NIST 800-171 establish a mandate to formally manage vulnerabilities. The VPMP addresses these compliance requirements!
Once again, our customers spoke and we listened - our customers needed documentation to help them prove the existence of a "vulnerability management program" to address this common requirement in vendor contracts and newer regulations. Similar to the other cybersecurity documentation we sell, many of our customers tried and failed to create their own program-level documentation. It is not uncommon for organizations to spent hundreds of man-hours on this type of documentation effort and only have it end in failure. That is why we are very excited about this product, since it fills a void at most organizations, both large and small.
How Does The VPMP Solve These Problems?
- Clear Documentation - The VPMP provides the comprehensive documentation to prove that your vulnerability and patch management program exists.
- Time Savings - The VPMP provides actionable guidance on what steps can be taken to proactively address risk and keep systems patched in a sustainable manner.
- Alignment With Leading Practices - The VPMP is written to support leading practices for patching, vulnerability scanning, penetration testing and vulnerability remediation.
The following statutory, regulatory and contractual sources specifically have requirements surrounding patching, vulnerability remediation, vulnerability scanning and penetration testing:
Vulnerability Management - Including Patch / Flaw Management
- NIST 800-53 rev 4 - SI-2 & SA-11
- NIST 800-171 - 3.14.1, 3.14.2 & 3.14.3
- PCI DSS - 6.1, 6.2 & 6.6
- ISO 27002 - 12.6.1 & 16.1.3
- NIST Cybersecurity Framework - ID.RA-1 & PR.IP-12
- CIS Critical Security Controls - 4.5, 4.7 & 16.6
- MA 201 CMR 17.00 - 17.04(6)
- OR 646A - 622(2)(d)(B)(iii)
Vulnerability Remediation Processes
- NIST 800-53 rev 4 - PM-04
- NIST 800-171 - 3.11.3 & 3.12.2
- ISO 27002 - 12.6.1
- NIST Cybersecurity Framework - ID.RA-6
- CIS Critical Security Controls - 4.7, 4.8 & 18.1
- MA 201 CMR 17.00 - 17.03(2)(j)
- OR 646A - 622(2)(d)(B)(iii)
- CIS Critical Security Controls - 18.1
Vulnerability Scanning
- NIST 800-53 rev 4 - RA-5
- NIST 800-171 - 3.11.2
- PCI DSS - 11.2
- ISO 27002 - 12.6.1 & 18.2.3
- HIPAA - 164.308(a)(1)(ii)(A)
- NIST Cybersecurity Framework - ID.RA-1, PR.IP-12, DE.CM-8, DE.DP-4, DE.DP-5, RS.CO-3 & RS.MI-3
- CIS Critical Security Controls - 4.1-4.8 & 15.2
- OR 646A - 622(2)(B)(iii) & 622(2)(d(A)(iii)
Penetration Testing
- NIST 800-53 rev 4 - CA-8
- NIST 800-171 - 3.12.1
- PCI DSS - 11.3-11.3.3
- NIST Cybersecurity Framework - ID.RA-1
- CIS Critical Security Controls - 20.1-20.8
Product Example - Vulnerability & Patch Management Program (VPMP)
The VPMP addresses program-level guidance on HOW to actually manage patching and vulnerability management, including vulnerability scanning and penetration testing. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW vulnerabilities are actually managed. The VPMP provides this middle ground between high-level policies and the actual procedures of how systems are patched, systems scanned, etc. on a day-to-day basis by those individual contributors who execute vulnerability management tasks.
View Product Example
If you would like to view an example of ComplianceForge's Vulnerability & Patch Management Program (VPMP), please click the image below:
 Policies & Standards |
Cost Savings Estimate - Vulnerability & Patch Management Program (VPMP)
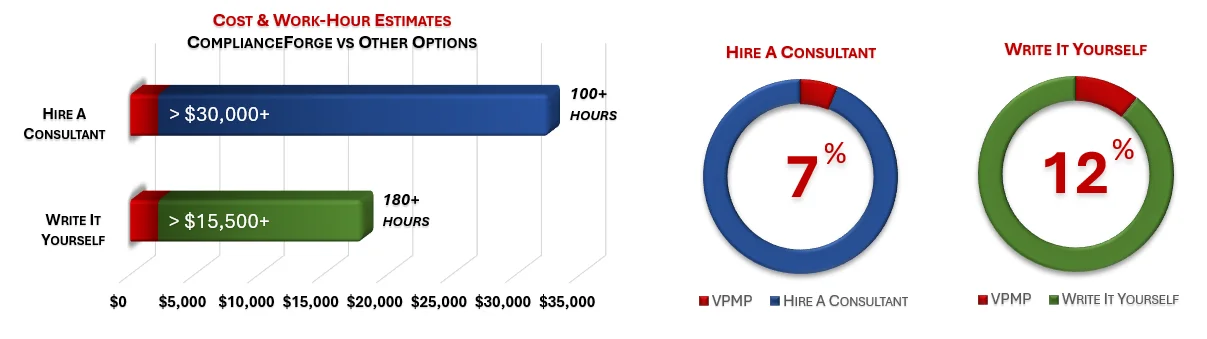
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the VPMP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 200 internal staff work hours, which equates to a cost of approximately $18,000 in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 100 consultant work hours, which equates to a cost of approximately $32,500. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The VPMP is approximately 7% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the VPMP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the VPMP! |
|
|
Cybersecurity Vulnerability & Patch Management Documentation
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.




