Cybersecurity Risk Management Program (RMP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the RMP is to help answer common questions we receive.
What Is The Risk Management Program (RMP)
|
Is your organization looking for a risk management template? ComplianceForge's RIsk Management Program (RMP) is essentially a "risk management playbook" for how your organization addresses the broader concepts of risk management that are not provided by a policy or standard. These are the details that explain how risk is actually managed. Risk, threat and vulnerability management practices are meant to achieve a minimum level of protection - this equates to a reduction in the total risk due to the protections offered by implemented controls. These ecosystem components have unique meanings that need to be understood to reasonably protect people, processes, technology and data. Understanding the context of how these components integrate can lead to more meaningful and practical risk management practices. |
|
All companies have a need to manage risk. Most companies are compelled to manage risk and these requirements come from a broad range of sources. Regardless of your industry, there are likely requirements to manage cybersecurity risk and failing to manage risk could leave your company liable from non-compliance from these requirements:
- NIST 800-171 - Protecting CUI in Nonfederal Information Systems and Organizations - Section 3.11 requires risks to be periodically assessed!
- Federal Trade Commission (FTC) Act - 15 U.S. Code § 45 deems unfair or deceptive acts or practices in or affecting commerce to be unlawful - poor security practices are covered under this requirement and not managing cybersecurity risk is an indication of poor security practices!
- Payment Card Industry Data Security Standard (PCI DSS) - Section#12.2 requires companies to perform a formal risk assessment!
- Massachusetts MA 201 CMR 17.00 - Section# 17.03(2)(b) requires companies to "identify & assess" reasonably-foreseeable internal and external risks!
- Oregon Identity Theft Protection Act - Section 646A.622(2)(d)(B)(ii) requires companies to assess risks in information processing, transmission & storage!
- Health Insurance Portability and Accountability Act (HIPAA) - Security Rule (Section 45 C.F.R. §§ 164.302 – 318) requires companies to conduct an accurate & thorough assessment of potential risks!
- Gramm-Leach-Bliley Act - Safeguard Rule requires company to identify and assess risks to customer information!
- Vendor Contracts - It is increasingly common for vendors, partners and subcontractors to be contractually-bound to perform recurring risk assessments. Not having a cybersecurity risk management program could lead to breach of contract or losing a bid!
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The RMP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The RMP is an efficient method to obtain comprehensive risk management documentation for your organization!
- Compliance Requirements - Requirements such as PCI DSS, HIPAA, MA 201 CMR 17.00 and NIST 800-171 establish a mandate to formally manage risk. The RMP addresses these compliance requirements!
- Audit Failures - Similar to vulnerability management, most organizations run into trouble in audits when asked HOW risk is managed, since they cannot provide documentation beyond policies and standards. The RMP addresses the HOW for you!
- Vendor Requirements - It is very common for clients and partners to request evidence of a risk management program during their due diligence. The RMP provides this evidence!
How Does The RMP Solve These Problems?
- Clear Documentation - The RMP provides the comprehensive documentation to prove that your risk program exists.
- Time Savings - The RMP provides actionable guidance on what steps can be taken to categorize, calculate and manage risk in a sustainable manner.
- Alignment With Leading Practices - The RMP is written to support COSO, COBIT, NIST and ISO frameworks that provide you with significant flexibilit
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The RMP is an editable Microsoft Word document that providers program-level guidance to directly supports your organization's policies and standards for managing cybersecurity risk. Unfortunately, most companies lack a coherent approach to managing risks across the enterprise:
- When you look at getting audit ready, your policies and standards only cover the "why?" and "what?" questions of an audit. This product addresses the “how?” questions for how your company manages risk.
- The RMP provides clear, concise documentation that provides a "paint by numbers" approach to how risk is managed.
- The RMP addresses fundamental needs when it comes to what is expected in cybersecurity risk management:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential the impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as NIST Risk Management Framework (NIST 800-37 rev2), NIST 800-39, ISO 31010 and COSO 2013.
- Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the RMP does this from a cybersecurity risk management perspective.
The new version of the RMP for 2023 is aligned with the Secure Controls Framework (SCF) Risk Management Model (C|P-RMM) that provides a very flexible approach to risk management. This ties in with the Cybersecurity Risk Assessment (CRA) template product that is also aligned with the SP-RMM, so it compliments the RMP by having a repeatable, professional template for performing controls-based risk assessments.
Product Example - Risk Management Program (RMP)
Regardless if your cybersecurity program aligns with NIST, ISO, COBIT, ENISA or another framework, the RMP is designed to address the strategic, operational and tactical components of risk management to provide cybersecurity risk management governance. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW risk is actually managed. The RMP provides this middle ground between high-level policies and the actual procedures of how risk is managed on a day-to-day basis by those individual contributors who execute risk-based controls.
View Product Example
If you would like to view an example of ComplianceForge's Risk Management Plan (RMP), please click the image below:
 Policies & Standards |
Cost Savings Estimate - Risk Management Program (RMP)
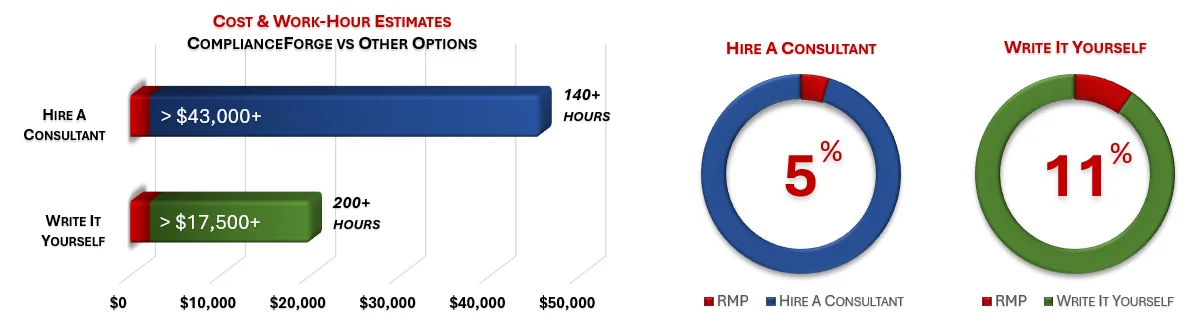
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the RMP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 220 internal staff work hours, which equates to a cost of approximately $20,000 in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 140 consultant work hours, which equates to a cost of approximately $45,500. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The RMP is approximately 5% of the cost for a consultant or 11% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the RMP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the C-SCRM! |
|
|
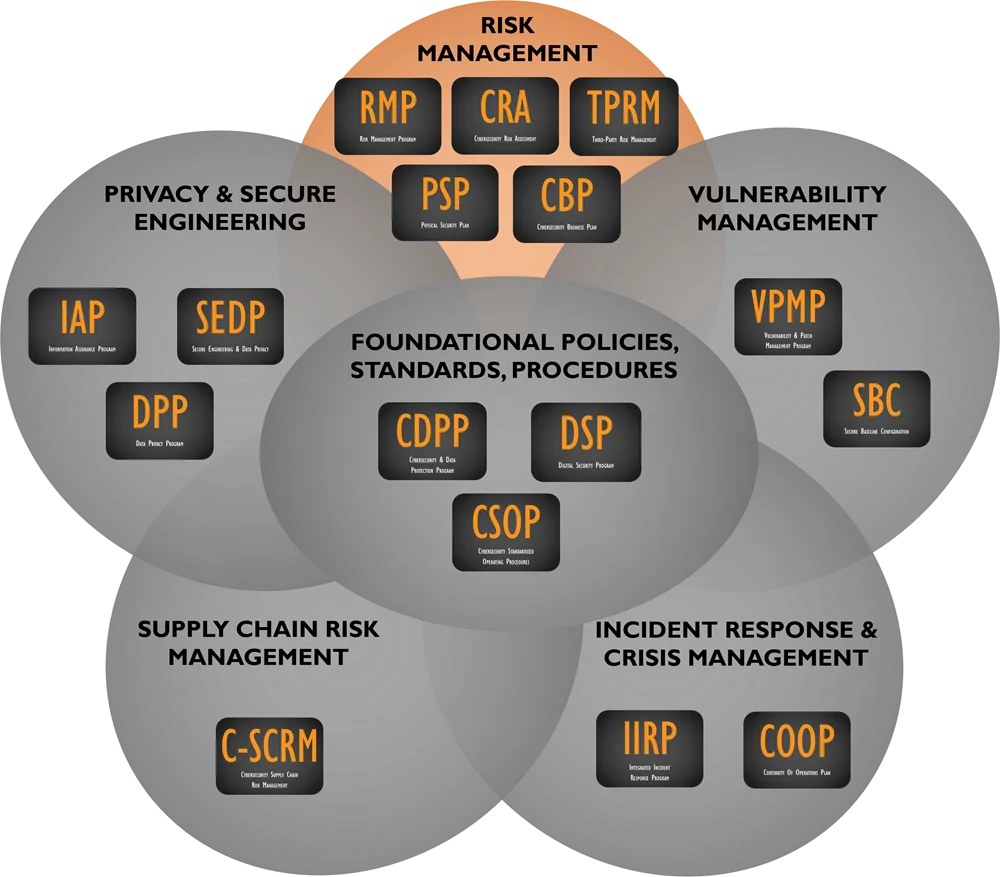
Cybersecurity Risk Management Program Documentation
The RMP serves as a foundational element in your organization's cybersecurity risk program. It can stand alone or be paired with other specialized products we offer.
|
Even with larger organizations that have Enterprise Risk Management (ERM) departments, the RMP can tie into the broader risk management framework for any organization. What ComplianceForge.com did was simply reduce the complexity by creating a usable risk management framework that any company can implement to manage risks:
|
|
|
Cybersecurity Risk Management Program (RMP) Framework - Based on NIST 800-37 Rev2, COSO 2013, COBIT 5 & ISO 31010 Best Practices!
The RMP is an editable Microsoft Word document that contains the requirements needed to establish a risk management program. Quite simply, the Cybersecurity Risk Management Program (RMP) provides your company with evidence that a documented risk management program exists to address operational risks associated with information and technology. From a Capability Maturity Model (CMM) perspective, if a risk program is not documented, incomplete or ad-hoc, it could be a liability for a company, since it indicates negligence with a statutory, regulatory or contractual requirement to manage risk. The RMP addresses the due care component of getting an organization to a mature level for managing risk.
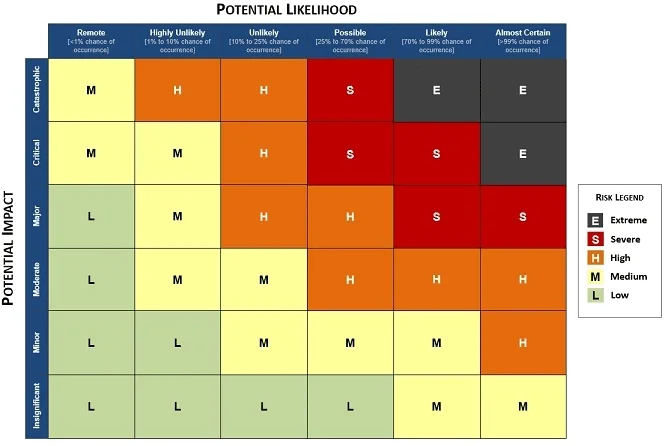
Determine the Potential Likelihood of Threat Occurrence
Organizations must take into account the probability of potential risks, since that identifies the legitimate threat landscape. The results of this assessment, combined with the initial list of threats, will influence the determination of which threats require protection against because those are “reasonably anticipated” based on your unique situation.
Determine the Potential Impact of Threat Occurrence
Organizations must consider the “criticality,” or impact, of potential risks to confidentiality, integrity, and availability of their data and information systems. Not all systems are equal – some systems could go down and no one would be impacted, but some systems could bring your business operations to an immediate halt.
The RMP helps assess the magnitude of the potential impact resulting from a threat triggering or exploiting a specific vulnerability. This can be qualitative, quantitative or a combination of the two methods to measure the impact on your organization.
Determine the Level of Risk
From likelihood and potential impact, organizations can assign risk levels for all threat and vulnerability combinations identified during the risk analysis. The RMP allows you to assign a level of risk by analyzing the values assigned to the likelihood of threat occurrence and resulting impact of threat occurrence.
The Cybersecurity Risk Management Program (RMP) provides best-practices guidance on risk management at the strategic, operational and tactical levels! This is important, since this hybrid or "best of breed" approach to risk management takes advantage of the strengths of each best practice model (e.g., COSO, COBIT, ISO & NIST). This allows you to have a considerable amount of flexibility to conduct risk management operations.
Due Care Considerations - Reasonable Expectations For Managing Risk
|
Are you prepared to answer the "why" or "how" questions for your risk assessments? It is a pretty scary question for many people, since their risk assessments are not based on anything beyond “gut feelings” and are overly subjective. When an auditor comes knocking, it is critically important to be able to point to program documentation that justifies your decisions. The Cybersecurity Risk Assessment Framework is intended to be the foundational documentation that you implement to define and manage risk at your company. The Cybersecurity Risk Management Program clearly lays out and defines cybersecurity risk for your organization - how you plan to address risk management at the strategic, operational, and tactical levels! This is based on industry-recognized best practices for risk management from COSO, ISO and NIST, so the framework is based on what reasonable expectations are for managing cybersecurity risk. For simple risk assessments, the 6x6 risk matrix can be used to quickly identify the appropriate level of risk the scenario represents. With that knowledge, it is easy to then escalate the risk to the appropriate level of management for resolution (e.g., accept, transfer, mitigate or avoid the risk). |
|
|
Make Assessing Risk More Efficient- Understanding Layers of Risk
Dependencies are of critical importance when assessing risk, since risk can have a cascading effect. Ideally, a risk assessment at a tactical level (e.g., assessment of a specific application or host) should leverage existing risk assessments that address “upstream” risks. For example, a well-designed and securely-coded application could be compromised if the host system it is running on is insecure. Similarly, the application could be made unavailable if the datacenter lacks measures to ensure uptime against natural or man-made threats.
As part of overall risk management, your company should perform several formal risk assessments, which are meant to be used as references for more detailed project-specific risk assessments. At a minimum, risk assessments should exist for commonly-leveraged aspects of your company's IT environment:
- Datacenters (including infrastructure risks)
- Secure configurations for hosts and major applications (e.g., databases, email, Intranet)
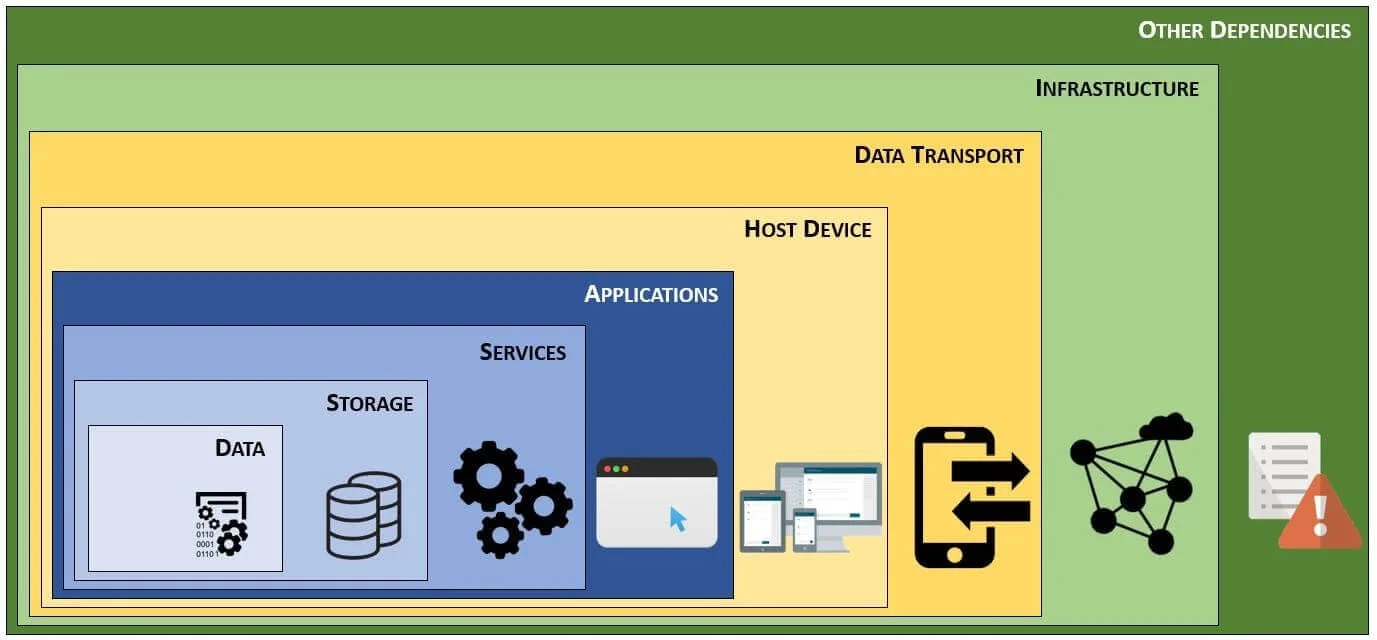
By being able to leverage those existing risk assessments, it will allow for more efficient assessments of applications. The RMP helps build this foundation for efficient risk management by framing risk according to the following concepts:
Application-Specific Risk
Risks associated with applications include, but are not limited to:
- Insecure code (developers did not follow secure coding practices)
- Default/weak credentials
- Weak encryption
- Passwords/sensitive data stored in clear text
- Permissions management
- Missing software patches
- Logging/monitoring not being performed
Host-Specific Risk
Risks associated with hosts include, but are not limited to:
- Lack of system hardening
- Default/weak credentials
- Lack of encryption at rest
- Role-Based Access Control (RBAC)
- Missing software patches
- Logging/monitoring not being performed
- Backups not being performed
Infrastructure-Specific Risk
Risks associated with infrastructure include, but are not limited to:
- Improper equipment (e.g., consumer-grade networking hardware vs business/enterprise-grade)
- Lack of system hardening
- Default/weak credentials
- Lack of encryption in transit
- Role-Based Access Control (RBAC)
- Missing software patches
- Logging/monitoring not being performed
Facility-Specific Risk
Risks associated with facilities include, but are not limited to:
- Physical access controls
- Environmental controls
- Redundant utilities
- Trained response personnel (disaster recovery plan)
Risk Associated With Other Dependencies
Risks associated with other dependencies include, but are not limited to:
- Software escrow agreements
- Developer/vendor management
- Trans-border data transfers (international law ramifications)
- Business limitations (e.g., timelines, funding, regulations, politics, etc.)
Professionally-Written, Editable & Easily-Implemented Cybersecurity Risk Management Framework
Our latest version of the Cybersecurity Risk Management Program (RMP) is a Microsoft Word document that is fully editable, so that you can customize it for your own unique needs.
The Cybersecurity Risk Management Program (RMP) includes the following content to establish a comprehensive basis for defining and documenting how your company manages cybersecurity risk:
- Risk Taxonomy
- What Is Risk?
- Risk Management Activities
- Risk Management Benefits
- Who Has The Authority To Manage Risk
- Risk Management Decisions
- How Risk Is Categorized
- Low Risk
- Medium Risk
- High Risk
- Severe Risk
- Extreme Risk
- Risk Management Fundamentals
- Risk Management Principles
- Risk Management Maturity Levels
- Defining The Risk Appetite
- Situation Awareness
- Analyzing Risks
- Evaluating & Prioritizing Risks
- Risk Treatment
- Monitoring Risk
- Documenting Risk & Reporting Findings
- Cybersecurity Risk Management Methodology
- COSO – Strategic (Enterprise-Level Approach to Risk Management)
- ISO – Operational (Initiative / Program-Level Approach to Risk Management)
- NIST – Tactical (Asset / Project-Level Approach to Risk Management)
- Appendices
- Sources of Risk
- Risk Roles & Responsibilities
- Risk Assessment Techniques
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.