Cybersecurity Risk Assessment Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CRA is to help answer common questions we receive.
What Is The Cybersecurity Risk Assessment (CRA) Template?
The CRA serves as a key element in your organization's cybersecurity risk program. It can stand alone or be paired with other specialized products we offer.
Most companies have requirements to perform risk assessments, but they lack the knowledge and experience to undertake such assessments. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with a compliance requirement. In either situation, it is not a good place to be. The good news is that we created an affordable solution for businesses to conduct their own information security risk assessments.
If you can use Microsoft Word and Excel, then you can perform a risk assessment by simply following the instructions and editing the template to suit your specific requirements. While this is a template, we did the hard work of creating the formatting, bringing together the correct scope of information that needs to be assessed, and we built the calculations to make your work as simple as selecting from a few drop-down answers!
The technical controls selected for the CRA are the cybersecurity controls from the Secure Controls Framework (SCF), so the requirements are based on leading practices for risk management.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The RMP is an editable Microsoft Word document that providers program-level guidance to directly supports your organization's policies and standards for managing cybersecurity risk. Unfortunately, most companies lack a coherent approach to managing risks across the enterprise:
- The CRA is an editable risk assessment template that you use to create risk assessments.
- It contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- Included is an example risk assessment that can be used as a guide.
- The CRA supports the Risk Management Program (RMP) product in answering the “how?” questions for how your company manages risk.
- You do not need the RMP to generate risk assessments with the CRA.
- The RMP just tells the rest of the story for how risk is managed at your organization.
- Where the RMP lays the groundwork for how risk is to be managed, the CRA is a template that allows you to product the end product of risk management, which is a professional-quality risk assessment report.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.

What Problems Does The CRA Solve?
- Lack of In House Security Experience - Many organizations lack internal staff who can come up with quality risk assessments. The CRA is an affordable solution for managers or IT staff to conduct quality risk assessments.
- Compliance Requirements - Most organizations run into trouble in audits when asked to provide evidence of risk assessments being performed. The CRA provides a template to conduct repeatable risk assessments in a very professional format. The CRA provides this evidence!
- Audit Failures - It is very common for clients and partners to request evidence of a risk assessments. Clients and partners often ask to see evidence of risk assessments so they can also understand your risks. The CRA provides this evidence!
- Vendor Requirements - Requirements such as PCI DSS, HIPAA, MA 201 CMR 17.00 and NIST 800-171 establish a mandate to conduct risk assessments. The CRA addresses these compliance requirements!
How Does The CRA Solve These Problems?
- Clear Documentation - The CRA provides the comprehensive documentation to prove that your risk program exists.
- Time Savings - You can start assessing risk as soon as you receive the CRA. Orders are generally delivered the same business day!
- Alignment With Leading Practices - The CRA covers natural and man-made risks, as well as risk associated with the absence or state of cybersecurity controls (as defined by NIST 800-171). This creates a quality scope for a cybersecurity risk assessment.
Need to perform an information security risk assessment? This is a pretty common requirement that can seem like an insurmountable obstacle, since most people are not trained on how to perform a risk assessment or they lack a simple tool that is comprehensive enough to meet their needs. This is where our Cybersecurity Risk Assessment Template comes into play - we developed a simple Microsoft Excel template to walk you through calculating risk and a corresponding Word template to report on that risk. If you can use Word and Excel, you can successfully use our templates to perform a risk assessment. We even give you a completely filled-out example risk assessment, so that you can use that as a reference.
Product Example - Cybersecurity Risk Assessment (CRA) Template
The CRA provides you a format to produce high-quality risk assessment reports, based on the Risk Management Program's (RMP) structure of managing risk. The CRA provides a high-quality template to actually perform the risk assessments that are called for by policies, standards and procedures. This allows your organization to have a risk assessment template that is repeatable and looks professional.
View Product Examples
If you would like to view examples of ComplianceForge's Cybersecurity Risk Assessment (CRA) template, please click any of the images below:
Cost Savings Estimate - Cybersecurity Risk Assessment (CRA) Template
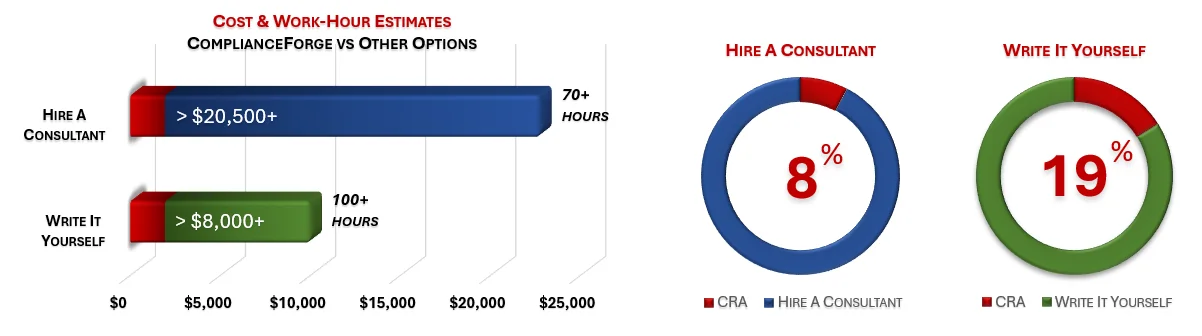
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CRA from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 100 internal staff work hours, which equates to a cost of approximately $10,000 in staff-related expenses. This is about 2-3 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 70 consultant work hours, which equates to a cost of approximately $22,750. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- The CRA is approximately 8% of the cost for a consultant or 19% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CRA the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CRA! |
|
|
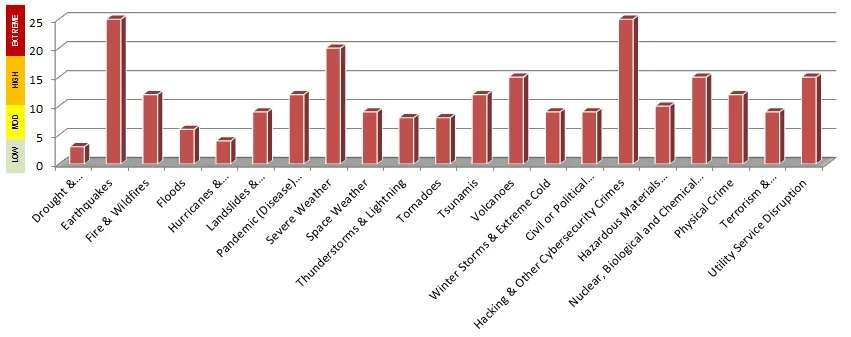
Common Scenarios That Require Information Security Risk Assessments
If you fall in scope for any of these compliance requirements, you have to perform risk assessments and you need this template:
|
|
|
Given that we designed this risk assessment template based on industry-recognized best practices, you can use our template to address those information security risk assessment requirements. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks - NIST 800‐30 (Risk Management Guide for Information Technology Systems), NIST 800‐37 (Guide for Applying the Risk Management Framework to Federal Information Systems) & NIST 800‐39 (Managing Information Security Risk).
Risk Assessment Template Contents
Our latest version of the Cybersecurity Risk Assessment Template includes:
- Section for assessing both natural & man-made risks.
- Section for assessing reasonably-expected cybersecurity controls. The CRA uses the Secure Controls Framework (SCF) control set, so as a metaframework it is applicable to over 100 cybersecurity laws, regulations and frameworks, including NIST 800-53, NIST 800-171 and ISO 27001/27002!
- Section for assessing Capability Maturity Model (CMM) - built into cybersecurity control assessment portion of the risk assessment.
- Blank templates in Microsoft Word & Excel formats.
- Fully filled-out example of the templates that you can edit in Microsoft Word & Excel
Graph Depicting Natural & Man-Made Risks
The Excel-based worksheet comes with graphs showing before & after risk levels. These are just embedded into the report to provide a good visual. The calculations from the worksheets make it easy to show raw risk scores and also weighted scores, which take into consideration the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk.
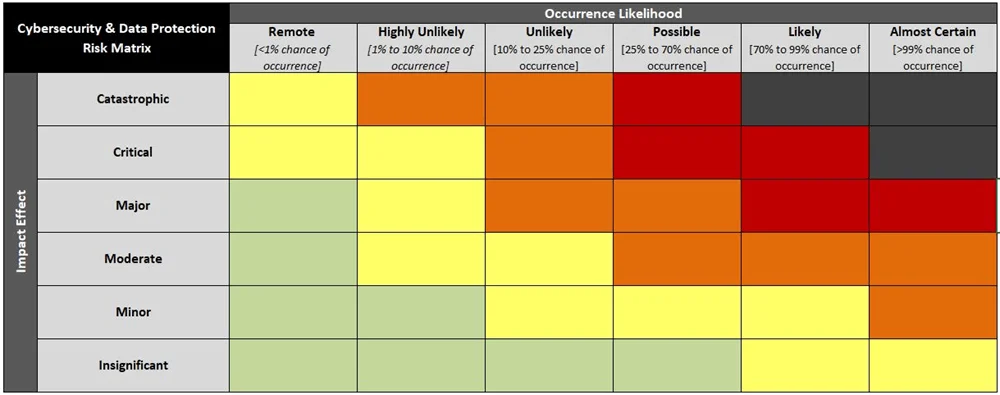
Risk Assessment Matrix
The calculations show raw risk scores and also take into account weighting factors, such as the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk. The CRA utilizes a 6x6 risk assessment matrix. The CRA is able to show both the raw risk score, as well as the final score when compensating controls are taken into consideration.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.