Integrated Incident Response Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the IIRP is to help answer common questions we receive.
What Is The Integrated Incident Response Program (IIRP)?
The Integrated Incident Response Program (IIRP) can serve as the cornerstone element in your organization's incident response capability. The reality is that incidents do not care if your responders are or are not prepared and generally with incident response operations if you fail to plan you plan to fail. What matters most is appropriate leadership that is capable of directing response operations in an efficient and effective manner. This is where the IIRP is an invaluable resource for cybersecurity and privacy leaders to have a viable plan to respond to cybersecurity and privacy-related incidents.
The IIRP is an editable Microsoft Word document, but it also comes with Microsoft Excel, PowerPoint and Visio templates that contain the program-level documentation and process flows to establish a mature Integrated Incident Response Program.
- This product addresses the “how?” questions for how your company manages cybersecurity incident response.
- This product helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents, so that your company can train on likely scenarios and tailor plans specific to your needs.
- The IIRP helps address the fundamental expectations when it comes to incident response requirements:
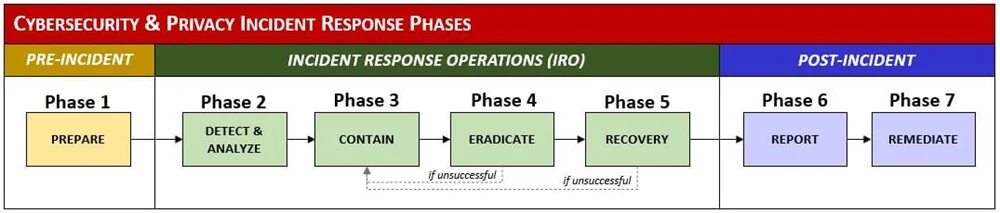
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team (ISIRT) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise (IoC).
- Identifies and defines sources of evidence.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "80% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
What Problems Does The IIRP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation (e.g., Integrated Incident Response Program documentation) means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The NIST 800-61-based IIRP is an efficient method to obtain a comprehensive incident response program for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented incident response program. Requirements range from PCI DSS to NIST 800-171 to EU GDPR. The IIRP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected incident response activities.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The IIRP is easy to maintain and customize for your organization, since it is Microsoft Office-based documentation that you can edit for your needs and keep current as things change in your environment.
- Vendor Requirements - It is very common for clients and partners to request evidence of an incident response program. The IIRP provides this evidence!
Can you honestly answer how incident response is documented at your organization? When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as incident response. While policies and standards are designed to describe why something is required and what needs to be done, many companies fail to create documentation to address how the policies and standards are actually implemented.
We did the heavy lifting and created several program-level documents to address this need and the Integrated Incident Response Program (IIRP) is one of those products. This is specifically designed to provide you with the ability to hit the ground running with incident response. From laying the foundation of how to classify incidents, to responding to events, and providing tabletop exercise material, the IIRP can quickly mature your incident response capabilities.
Most companies have requirements to document its incident response processes, but they lack the knowledge and experience to undertake such documentation efforts. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with a compliance requirement. In either situation, it is not a good place to be. The good news is that ComplianceForge developed a viable incident response program that is based on NIST 800-61 guidance, which is the "gold standard" for incident response frameworks. This document is capable of scaling for any sized company.
How Does The IIRP Solve These Problems?
- Clear Documentation - The IIRP provides comprehensive documentation to prove that your incident response program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The IIRP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The NIST-based IIRP is written to align your organization with leading practices for incident response.
Product Example - Integrated Incident Response Program (IIRP)
The IIRP addresses program-level guidance on HOW to actually manage incident response operations, including forensics and reporting. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW incident response is actually managed. The IIRP provides this middle ground between high-level policies and the actual procedures of how Incident Response Plans (IRPs) are executed by those individual contributors task with incident response duties. The IIRP comes with a wealth of guidance, including scenario-based guidance, example IRPs, how to identify both Indicators of Exposure (IoE) and Indicators of Compromise (IoC) and more!
View Product Example
If you would like to view an example of ComplianceForge's Integrated Incident Response Program (IIRP), please click the image below:
 Policies & Standards |
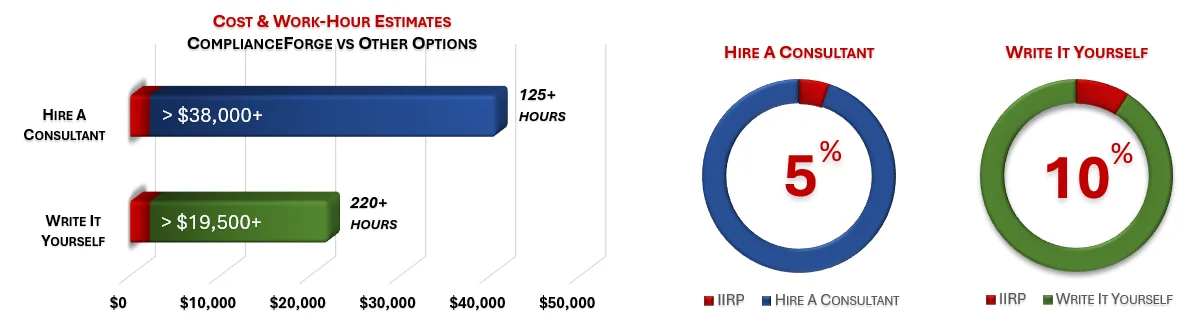
Cost Savings Estimate - Integrated Incident Response Program (IIRP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the VPMP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 240 internal staff work hours, which equates to a cost of approximately $22,000 in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 125 consultant work hours, which equates to a cost of approximately $40,625. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The VPMP is approximately 5% of the cost for a consultant or 10% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the VPMP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the IIRP! |
|
|
Cybersecurity Incident Response Documentation
Professionally-Written, Editable & Easily-Implemented NIST 800-61 Based Incident Response Program
The IIRP operates at the strategic level to provide guidance to your organization's incident responders. It provides the overall framework that governs incident response across the enterprise with a focus on repeatable processes and sustainable operations. The IIRP breaks down the management of incident response into phases:
|
|
|
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.