Secure Controls Framework (SCF) CORE Fundamentals - Procedures
The Secure Controls Framework Council (SCF Council) created the Cybersecurity Oversight, Resilience and Enablement (CORE) initiative as a means to help an organization tailor cybersecurity and data protection controls for its specific needs. The concept for SCF CORE Fundamentals came from Texas SB 2610 that named the SCF as one of a select few cybersecurity frameworks with adequacy to provide necessary security coverage. The law is the newest in a line of US State-level “cybersecurity safe harbor” laws that provide legal protection for businesses if at the time of the incident the business can prove it implemented reasonable cybersecurity practices. This type of legislation is meant to encourage Small and Medium Businesses (SMBs) to invest in cybersecurity to reduce legal exposure. This incentivization can enhance business resilience and that benefits the everyone involved.
The controls in the SCF CORE Fundamentals are scoped for SMBs and are designed to meet the requirements in Texas SB 2610:
- Contain administrative, technical, and physical safeguards for the protection of personal identifying information and sensitive personal information (Section 542.004(1));
- Protect the security of personal identifying information and sensitive personal information (Section 542.004(3)(a));
- Protect against any threat or hazard to the integrity of personal identifying information and sensitive personal information (Section 542.003(4)(b)); and
- Protect against unauthorized access to or acquisition of personal identifying information and sensitive personal information that would result in a material risk of identity theft or other fraud to the individual to whom the information relates (Section 542.004(3)(c)).
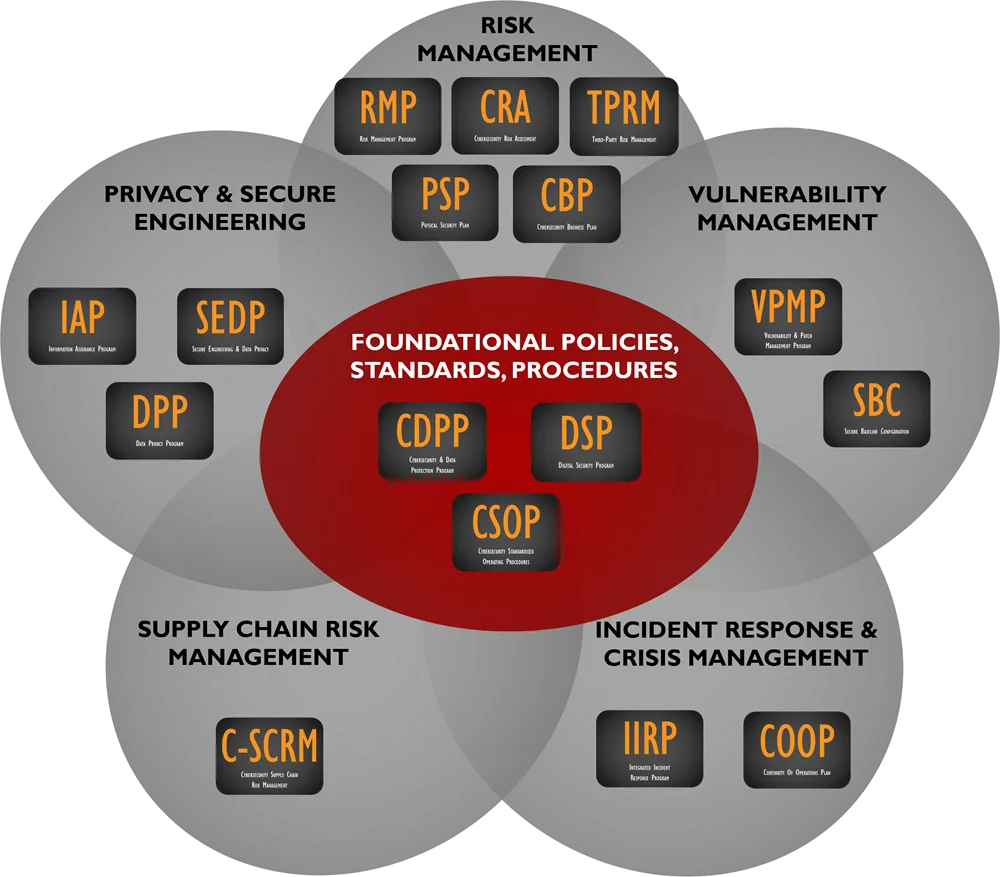
What Is The Cybersecurity Standardized Operating Procedures (CSOP)?
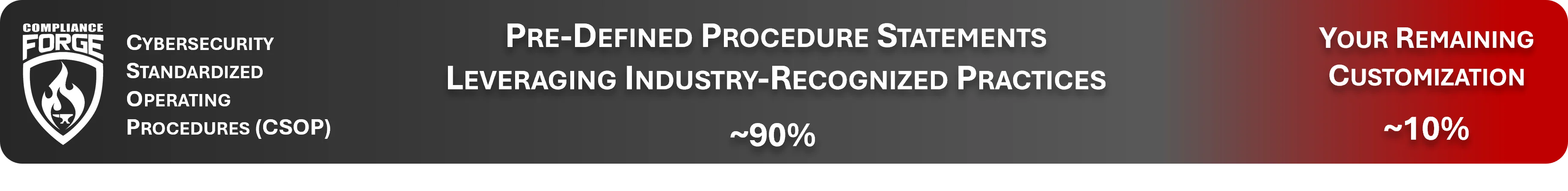
The CORE Fundamentals version of the CSOP contains a catalog of procedure statements applicable to sixty-eight (68) SCF controls! While the control catalog of the SCF contains 1,342 unique controls, the 68 controls of the SCF CORE Fundamentals represents a mere 5% of the SCF and that is by design. Ever since the SCF was first released in 2018, there has never been an expectation for any organization, regardless of its size or industry, to implement every SCF control. The reason is simple - the SCF was designed to be tailored to an organization’s specific needs, based on “must have” versus “nice to have” requirements:
- Minimum Compliance Requirements (MCR) are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- Discretionary Security Requirements (DSR) are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.
The CSOP contains editable procedure statements in an editable Microsoft Word format:
- The CSOP addresses the “how?” questions in an audit, since procedures provide the means for how your organization's policies and standards are actually implemented.
- The CSOP provides the underlying cybersecurity procedures that must be documented, as may be stipulated by statutory, regulatory and contractual requirements.
- The procedure statements in the CSOP can be cut & pasted into other tools (e.g., wiki page) or left in a single document. There is no wrong answer for how procedures are maintained, since every organization is unique in the tools used and the location of users.
How Much Customization Is Remaining?
Given the difficult nature of writing templated policy and standards, we aimed for approximately a "90% solution" since it is impossible to write a 100% complete cookie cutter document that can be equally applied across multiple organizations. This means ComplianceForge did the heavy lifting for you, and all you have to do is fine-tune the policies and standards with the specific information that only you know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product!
What Problems Does The CSOP Solve?
- Lack of In House Security Experience - Writing cybersecurity procedures is a skill that most cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive procedure documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The CSOP is an efficient method to obtain comprehensive IT security procedures for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security procedures. Requirements range from PCI DSS to HIPAA to NIST 800-171. The CSOP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The CSOP's procedures provide mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies, standards and procedures.
Our customers choose the Cybersecurity Standardized Operating Procedures (CSOP) because they:
- Have a need for comprehensive cybersecurity procedures to address their compliance needs.
- Need to be able to edit the document to their specific technology, staffing and other considerations.
- Do not have to comply with most of the controls linked to leading frameworks (e.g., NIST 800-53, NIST 800-171, ISO 27002, HIPAA and others).
- Need an affordable and timely solution to address not having procedures.
How Does The CSOP Solve These Problems?
- Clear Documentation - The CSOP provides a comprehensive template for your procedures to help prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The CSOP can provide your organization with a templated solution that requires minimal resources to fine tune for your organization's specific procedural needs.
- Alignment With Leading Practices - The CSOP is written to support over two dozen leading frameworks!
Until now, developing a template to provide worthwhile cybersecurity procedures is somewhat of a "missing link" within the cybersecurity documentation industry. The good news is that ComplianceForge solved this issue with the Cybersecurity Standardized Operating Procedures (CSOP) product. We are the only provider to have an affordable and comprehensive procedures template! Our CSOP can save a business several hundred hours of work in developing control activities / procedure statements, so the CSOP is worth checking out!
SCF CORE Fundamentals Policies & Standards
The CORE Fundamentals provides the following editable policies & standards:
- Cybersecurity & Data Protection Governance Policy (GOV)
- GOV-02. Publishing Cybersecurity & Data Protection Documentation
- GOV-04. Assigned Cybersecurity & Data Protection Responsibilities
- GOV-15. Operationalizing Cybersecurity & Data Protection Practices
- Asset Management Policy (AST)
- AST-02. Asset Inventories
- AST-02.8. Data Action Mapping
- AST-04. Network Diagrams & Data Flow Diagrams (DFDs)
- AST-09. Secure Disposal, Destruction or Re-Use of Equipment
- AST-16. Bring Your Own Device (BYOD) Usage
- Business Continuity & Disaster Recovery Policy (BCD)
- BCD-04. Contingency Plan Testing & Exercises
- BCD-11. Data Backups
- Change Management Policy (CHG)
- CHG-02. Configuration Change Control
- CHG-03. Security Impact Analysis for Changes
- Cloud Security Policy (CLD)
- CLD-01. Cloud Services
- CLD-10. Sensitive Data In Public Cloud Providers
- Compliance Policy (CPL)
- CPL-01. Statutory, Regulatory & Contractual Compliance
- Configuration Management Policy (CPL)
- CFG-02. System Hardening Through Baseline Configurations
- CFG-03. Least Functionality
- Continuous Monitoring Policy (MON)
- MON-01.8. Security Event Monitoring
- MON-03. Content of Event Logs
- MON-16. Anomalous Behavior
- Cryptographic Protections Policy (CRY)
- CRY-03. Transmission Confidentiality
- CRY-05. Encrypting Data At Rest
- CRY-09. Cryptographic Key Management
- Data Classification & Handling Policy (DCH)
- DCH-01.2. Sensitive / Regulated Data Protection
- DCH-01.4. Defining Access Authorizations for Sensitive/Regulated Data
- DCH-02. Data & Asset Classification
- DCH-13. Use of External Information Systems
- DCH-17. Ad-Hoc Transfers
- Endpoint Security Policy (END)
- END-04. Malicious Code Protection (Anti-Malware)
- END-08. Phishing & Spam Protection
- Human Resources Security Policy (HRS)
- HRS-04. Personnel Screening
- HRS-05. Terms of Employment
- Identification & Authentication Policy (IAC)
- IAC-01.3. User & Service Account Inventories
- IAC-06. Multi-Factor Authentication (MFA)
- IAC-07. User Provisioning & De-Provisioning
- IAC-08. Role-Based Access Control (RBAC)
- IAC-10. Authenticator Management
- IAC-10.8. Default Authenticators
- IAC-15. Account Management
- IAC-16. Privileged Account Management (PAM)
- IAC-17. Periodic Review of Account Privileges
- IAC-21. Least Privilege
- Incident Response Policy (IRO)
- IRO-02. Incident Handling
- IRO-04. Incident Response Plan (IRP)
- Network Security Policy (NET)
- NET-02. Layered Network Defenses
- NET-02.2. Guest Networks
- NET-03. Boundary Protection
- NET-04. Data Flow Enforcement – Access Control Lists (ACLs)
- NET-14. Remote Access
- NET-14.5. Work From Anywhere (WFA) - Telecommuting Security
- NET-15. Wireless Networking
- NET-18. DNS & Content Filtering
- Physical & Environmental Security Policy (PES)
- PES-02. Physical Access Authorizations
- PES-03. Physical Access Control
- PES-06. Visitor Control
- Risk Management Policy (RSK)
- RSK-03. Risk Identification
- RSK-04. Risk Assessment
- RSK-04.1. Risk Register
- RSK-06. Risk Remediation
- Security Awareness & Training Policy (SAT)
- SAT-02. Cybersecurity & Data Privacy Awareness Training
- Third-Party Management Policy (TPM)
- TPM-01.1. Third-Party Inventories
- TPM-03. Supply Chain Risk Management (SCRM)
- TPM-05. Third-Party Contract Requirements
- TPM-05.4. Responsible, Accountable, Supportive, Consulted & Informed (RASCI) Matrix
- TPM-08. Review of Third-Party Services
- Vulnerability & Patch Management Policy (VPM)
- VPM-02. Vulnerability Remediation Process
- VPM-05. Software & Firmware Patching
- VPM-06. Vulnerability Scanning
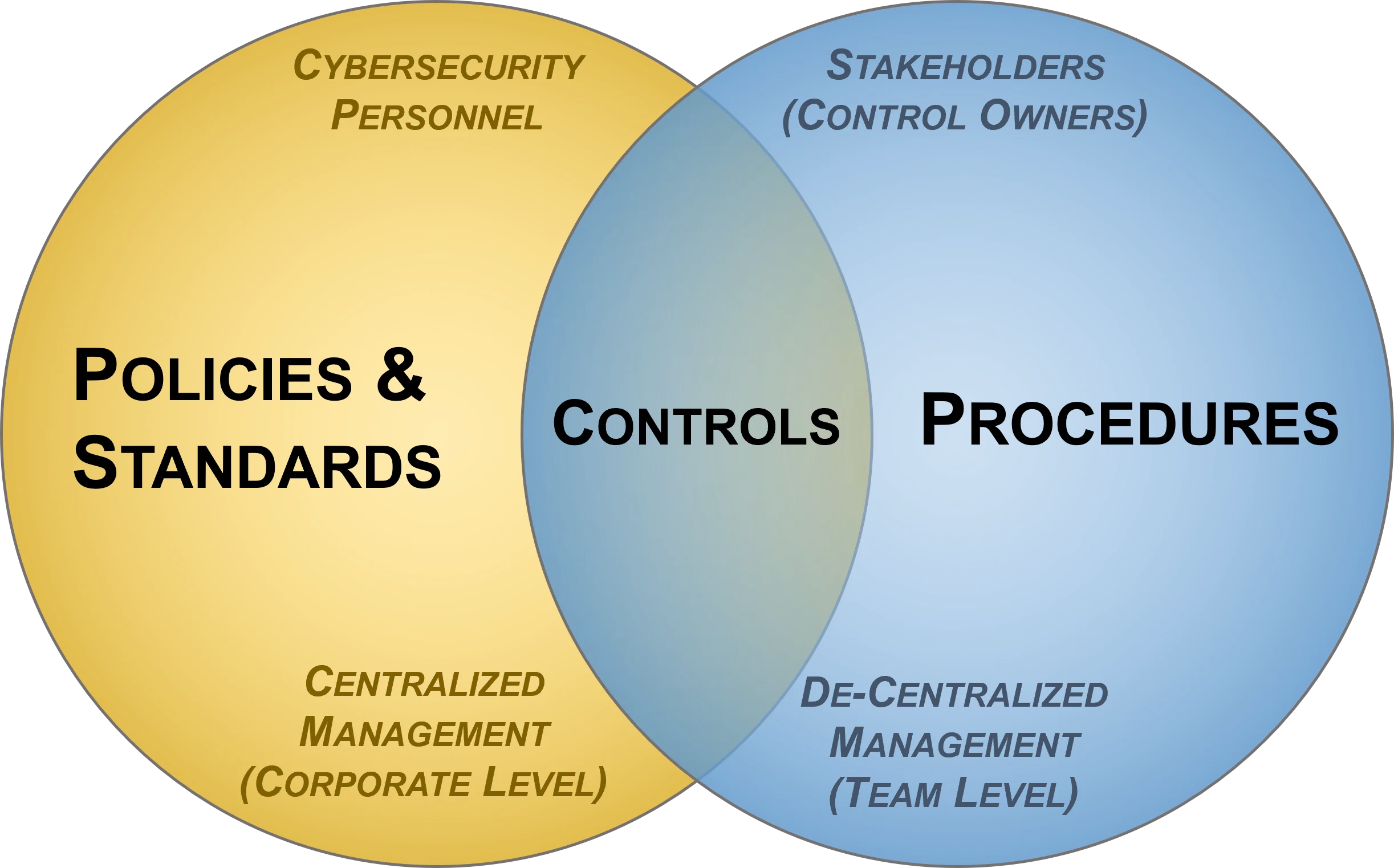
Procedures Operationalize Policies & Standards - This Is A Key Concept To Being Both Secure & Compliant
We leverage the Operationalizing Cybersecurity Planning Model in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
|
One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
|
|
|
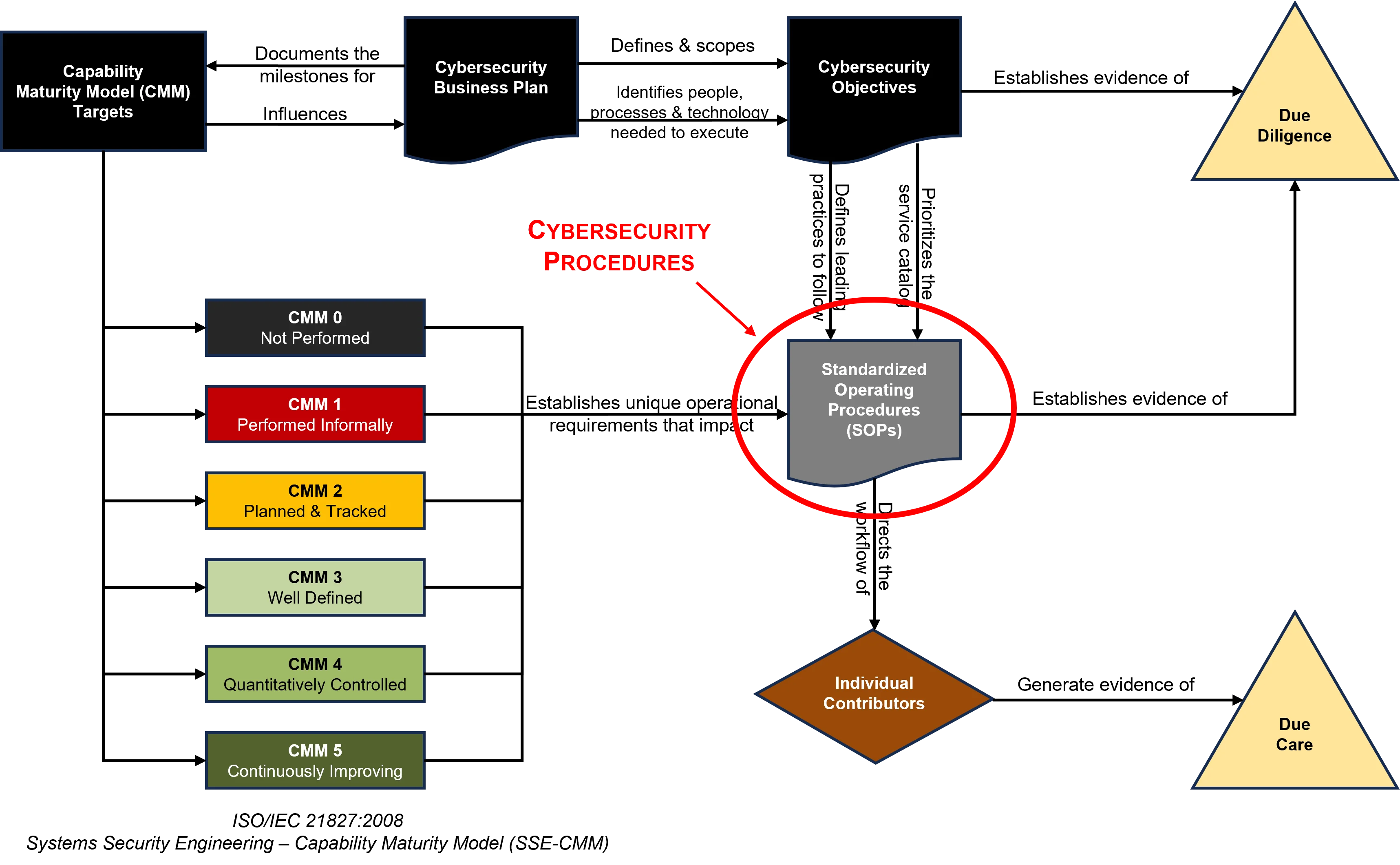
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
Product Example - CORE Fundamentals Template
The Cybersecurity Standardized Operating Procedures (CSOP) comes in two main versions (1) Digital Security Program (DSP) and (2) Cybersecurity & Data Protection Program (CDPP). These versions contain different levels of coverage, so you want to buy the correct CSOP for your needs. The CSOP is essentially a templatized catalog of procedures that you can edit for your needs. We did the heavy lifting in writing the procedures to get to approximately an "90% solution" so you just need to do the final customization of the procedure that only you will know since that is going to be very specific to your organization and business processes. This can jump start your procedures effort and save you several hundred hours of development time.
At ComplianceForge, we are sometimes asked by customers about whether we have example cybersecurity procedures, and you can view the examples below!
View Product Example
If you would like to view an example of ComplianceForge's CORE Fundamentals Cybersecurity Standardized Operating Procedures (CSOP) documentation, please click on the image below:
 SCF CORE Fundamentals Procedures |
The PDF document shown below provides two, side-by-side examples from policies all the way through metrics, so you can see what the actual content looks like.
Cost Savings Estimate - Cybersecurity Standardized Operating Procedures (CSOP)
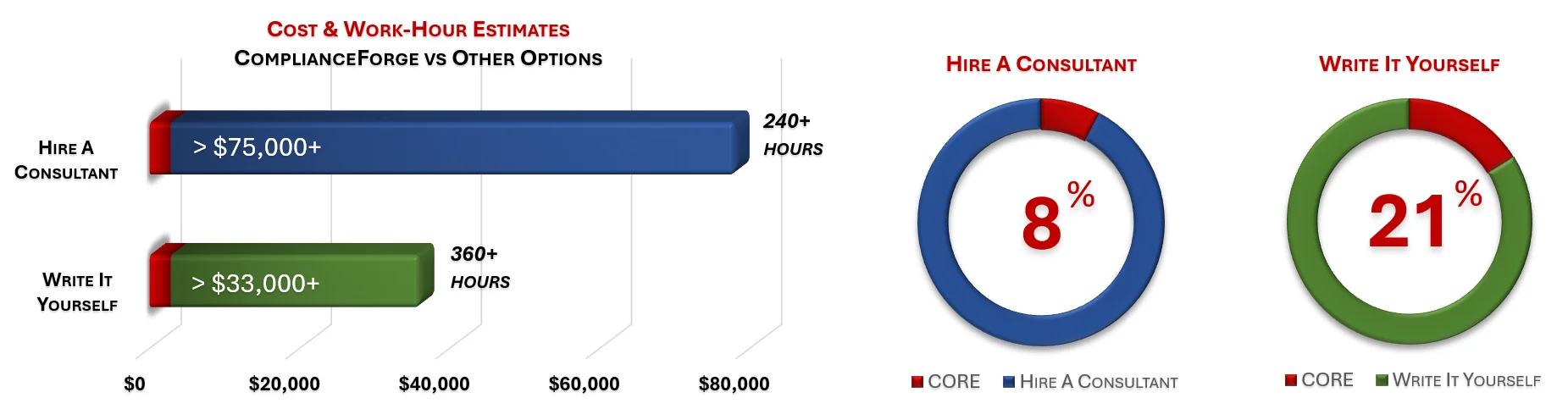
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CORE Fundamentals CSOP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 360 internal staff work hours, which equates to a cost of approximately $36,000 in staff-related expenses. This is about 4-8 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 240 consultant work hours, which equates to a cost of approximately $78,000. This is about 3-4 months of development time for a contractor to provide you with the deliverable.
- The CORE Fundamentals CSOP is approximately 8% of the cost for a consultant or 21% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CORE Fundamentals CSOP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
No Software To Install
|
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CSOP! |
|
|
Alignment With The NIST NICE Framework
One very special aspect of the CDPP and CORE Fundamentals versions of the CSOP is that it leverages the NIST NICE Cybersecurity Workforce Framework. NIST released the NICE framework in 2017 with purpose of streamlining cybersecurity roles and responsibilities. We adopted this in the CSOP framework since work roles have a direct impact procedures. By assigning work roles, the CSOP helps direct the work of employees and contractors to minimize assumptions about who is responsible for certain cybersecurity and privacy tasks.

The CSOP uses the work roles identified in the NIST NICE Cybersecurity Workforce Framework to help make assigning the tasks associated with procedures/control activities more efficient and manageable. Keep in mind these are merely recommendations and are fully editable for every organization – this is just a helpful point in the right direction!
 |
|
The CSOP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer. At the heart of it, the CSOP provides an organization with clear cybersecurity procedures that can scale to meet the needs and complexity of any team. The procedures are mapped to leading frameworks, so it is straightforward to have procedures that directly link to requirements from NIST 800-171, ISO 27002, NIST 800-53 and many other common cybersecurity and privacy-related statutory, regulatory and contractual frameworks! The value of the CSOP comes from having well-constructed procedure statements that can help you become audit ready in a fraction of the time and cost to do it yourself or hire a consultant to come on-site and write it for you. The entire concept of this cybersecurity procedures template is focused on two things:
|
What Is The Cybersecurity Standardized Operating Procedures (CSOP)?
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The NIST 800-171 version of the CSOP contains procedure statements in an editable Microsoft Word format:
- For each standard within the CORE Fundamentals (equates to each control from the SCF), the CSOP has a procedure associated with it.
- The CSOP addresses the “how?” questions in an audit, since procedures provide the means for how your organization's policies and standards are actually implemented.
- The CSOP provides the underlying cybersecurity procedures that must be documented, as many stipulated by statutory, regulatory and contractual requirements.
- The procedure statements in the CSOP can be cut & pasted into other tools (e.g., wiki page) or left in a single document. There is no wrong answer for how procedures are maintained, since every organization is unique in the tools used and the location of users.
Standardized Process Criteria - Helps Identify The Who/What/Where/When/How For Procedures
Your customization will be to help "fill in the blanks" with specific process owners, process operators, where additional documentation can be found, applicable service obligations (e.g., SLAs), and what technology/tools your team has available. We've done the heavy lifting and you just need to fill in the blanks.
- Process Owner:
- This is name of the individual or team accountable for the procedure being performed.
- Example: Chief Information Security Officer (CISO) / Cybersecurity Director.
- Process Operator:
- This is the name of the individual or team responsible to perform the actual task.
- Example: SOC Analyst / Risk Analyst / Network Admin.
- Occurrence:
- This is the annual, semi-annual, quarterly, monthly, bi-weekly, weekly, daily, continuous or as needed cadence for how often the procedure needs to be performed.
- Example: Quarterly vulnerability scans / Monthly software patches / Annual risk assessments.
- Scope of Impact:
- Purely internal processes;
- Purely external processes (e.g., outsourced vendor processes); or
- Scope covers both internal processes and external ones.
- System;
- Application;
- Process
- Team;
- Department;
- User;
- Client;
- Vendor;
- Geographic region; or
- The entire company
- This is the scope of the procedure:
- It also that affects the potential impact from the process, which can be one or more of the following:
- Location of Additional Documentation:
- This is where additional documentation is stored or can be found. You might want to reference a Wiki, SharePoint site, or other documentation repository.
- Performance Target:
- This addresses targeted timelines for the process to be completed (e.g., Service Level Agreements).
- Not all processes have SLAs or targeted timelines
- Technology in Use:
- Splunk for a Security Incident Event Manager (SIEM) solution to collect logs;
- McAfee ePO for centralized antimalware management; or
- Tripwire Enterprise for File Integrity Monitoring (FIM).
- This addresses the applications/systems/services that are available to perform the procedure.
- Examples:

Clear Use Case For Third-Party Risk Management (TPRM)
The SCF CORE Fundamentals can serve as a baseline for Third-Party Risk Management (TPRM) to evaluate an organization’s supply chain. Businesses struggle with trying to find the right questions to leverage for risk analysis purposes. The SCF has control questions written for all of its controls, so the SCF CORE Fundamentals is already available in question format. There are also:
- Control weighting to determine how important each control is;
- An Evidence Request List (ERL) that identifies reasonable evidence to ask for to evaluate a control;
- Assessment Objectives (AOs) that can be used to objectively evaluate each control; and
- A risk and threat catalog to understand the risks and threats associated with each control.
Third-Party Assessable
The SCF Conformity Assessment Program (SCF CAP) published an assessment guide for the SCF CORE Fundamentals, so a business can obtain a third-party certification to demonstrate conformity with those controls. This is a great feature for businesses that want assurance that the controls are implemented and operating as expected, so a SCF Certified – CORE Fundamentals certification carries far more validity than a self-assessment. For laws such as the Texas SB 2610, having third-party validated conformity can be valuable in case there is an incident and it is necessary for the business to prove it was compliant with expected security practices at the time of the incident.
Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: www.complianceforge.com/contact-us/.
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.