Cybersecurity Control Applicability
The Secure Controls Framework (SCF) approaches the concept of control applicability in a rational manner where cybersecurity and data protection controls primarily apply to one (1) of the following five (5) functions:
People, Processes, Technologies, Data & Facilities (PPTDF)
- People - The control directly applies to humans (e.g., training, background checks, non-disclosure agreements, etc.).
- Processes - The control directly applies to administrative work performed (e.g., processes, procedures, administrative documentation, etc.).
- Technologies - The control directly applies to systems, applications and services (e.g., secure baseline configurations, patching, etc.).
- Data - The control directly applies to data protection (e.g., encrypting sensitive and/or regulated data, applying metatags, etc.).
- Facilities - The control directly applies to infrastructure assets (e.g., physical access, HVAC systems, visitor control, etc.).
While the importance of robust cybersecurity controls cannot be overstated, the applicability of those controls is sometimes in question. These examples help demonstrate the applicable nature of controls:
- An employee (people) cannot have a secure baseline configuration applied.
- An Incident Response Plan (IRP) (process) cannot sign a NDA, use MFA or be patched.
- You cannot apply end user training to a firewall (technology).
- Controlled Unclassified Information (CUI) (data) cannot be assigned roles and responsibilities.
- Your data center (facility) cannot undergo employee background screening.
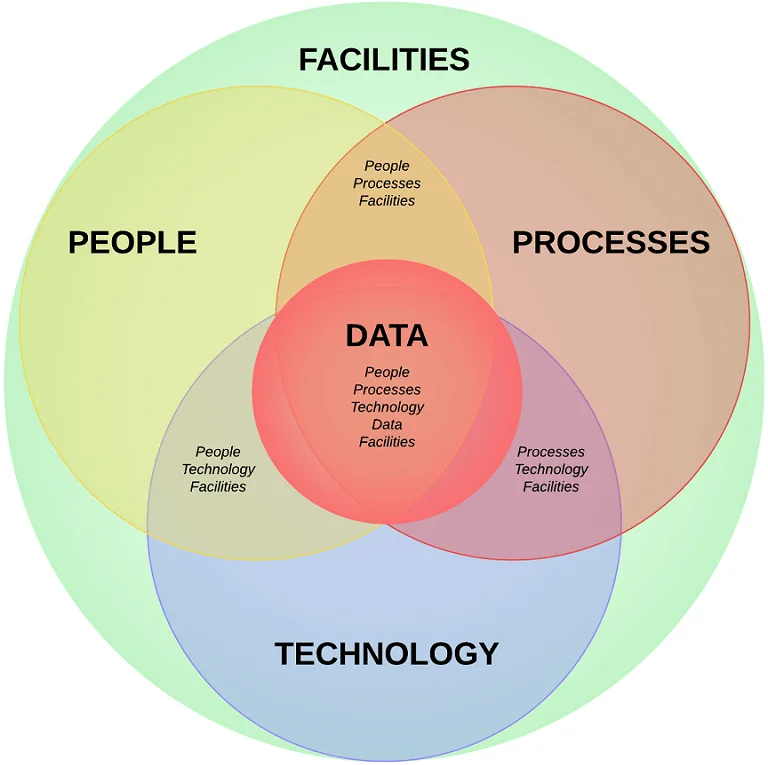
The PPTDF model, encompassing People, Processes, Technology, Data, and Facilities, provides a comprehensive approach to cybersecurity control applicability, as described below:
Control Applicability - People
People are often considered the weakest link in cybersecurity. Human error, negligence, or malicious intent can lead to significant vulnerabilities. To mitigate these risks, organizations implement human-specific controls such as:
- Security Awareness Training: Educating employees about cybersecurity best practices and potential threats.
- Access Controls: Enforcing the principle of least privilege to restrict access based on job roles.
- User Authentication and Authorization: Implementing strong authentication mechanisms and carefully managing user permissions.
Control Applicability - Processes
Effective cybersecurity processes are essential for identifying, responding to, and mitigating threats. Common processes that exist as controls include:
- Incident Response Plans: Establishing well-defined processes to respond promptly and effectively to security incidents.
- Regular Audits and Assessments: Conducting periodic assessments to identify vulnerabilities and measure compliance with security policies.
- Change Management: Implementing controls to manage changes in technology and processes to avoid unintended security consequences.
Control Applicability - Technologies
The technological aspect of cybersecurity involves deploying and configuring tools to protect against threats. Common technologies that exist as controls include:
- Network Defenses: Filtering and monitoring network traffic to prevent unauthorized access (e.g., firewalls, Intrusion Protection Systems (IPS), Data Loss Prevention (DLP), etc.).
- Endpoint Protection: Installing antimalware software, Endpoint Detection and Response (EDR) tools to secure individual devices, etc.
- Encryption: Safeguarding data in transit and at rest through robust encryption mechanisms.
Control Applicability - Data
Data is at the heart of the PPTDF model, making data protection truly the central focus of cybersecurity controls. There are many types of data that are considered sensitive/regulated that include, but are not limited to:
- Controlled Unclassified Information (CUI),
- Federal Contract Information (FCI),
- Personally Identifiable Information (PII),
- Cardholder Data (CHD),
- Export-Controlled Data (ITAR / EAR),
- Electronic Protected Health Information (ePHI),
- Intellectual Property (IP),
- Critical Infrastructure Information (CII),
- Attorney-Client Privilege Information (ACPI) and
- Student Educational Records (FERPA).
These data types have specific controls that are dictated by applicable laws, regulations or contractual obligations and include:
- Data Classification: Data must be categorized to apply the appropriate security measures.
- Limited Access: Data must be protected by limiting logical and physical access to data to individuals and systems that have a legitimate business need.
- Redundant, Obsolete/Outdated, Toxic or Trivial (ROTT) Data: Data must be trustworthy, based on the data's currency, accuracy, integrity and/or applicability.
- Availability: Data must be available, which involves regularly backing up data and establishing effective data recovery mechanisms that protects the integrity and confidentiality of the data being backed up and recovered.
Control Applicability - Facilities
Physical security is often overlooked but plays a crucial role in overall cybersecurity and data protection. Common physical controls include:
- Physical Access Control (PAC): Restricting physical access to any facility where systems or data exist. PAC exists in more than datacenters and corporate offices. The concept of PAC extends to home offices and Work From Anywhere (WFA) workers who still have an obligation to apply physical security protections to their systems and data.
- Surveillance Systems: Monitoring and recording activities within facilities to detect and deter unauthorized access.
- Environmental Controls: Maintaining optimal conditions for hardware to prevent damage or disruptions.
The PPTDF model shows that a multi-faceted approach to control applicability is indispensable, where it can create a resilient defense against a myriad of physical and cyber threats. A proactive stance in implementing and refining these controls will be crucial in securing the ever-expanding digital frontier.
There are no products listed under this category.
-
C-SCRM & NIST 800-161 R1
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...
-
Your CMMC Requirements Guide
A common issue facing many front-line IT / cybersecurity practitioners is that they do not know wher...
-
SCF Cybersecurity Documentation Experts
ComplianceForge is very pleased to announce it is now a Secure Controls Framework Licensed Cont...
-
Affordable Cybersecurity Policy Templates
ComplianceForge specializes in cybersecurity documentation. We are an industry leader in providing a...
