Strategy vs Operations vs Tactics
Strategy vs Operations vs Tactics
The purpose of this article is to help cybersecurity leaders up their game by gaining a baseline understanding of strategy vs operations vs tactics.
All too often, unprincipled cybersecurity leaders manipulate the business through Fear, Uncertainty and Doubt (FUD) to scare other technology and business leaders into supporting cybersecurity initiatives. These bad actors maintain the illusion of a strong cybersecurity program, when in reality the cybersecurity department is an array of disjointed capabilities that lacks a unifying plan. These individuals stay in the job long enough to claim small victories, implement some cool technology, and then jump ship for larger roles in other organizations to extend their path of disorder. In these cases, a common theme is the lack of viable business planning beyond a shopping list of technologies and headcount targets to further their career goals.
Understand Your Audience - Business Planning Terminology Matters
Cybersecurity is a cost center, not a revenue-generating business function. That means cybersecurity competes with all other departments for budget, and it necessitates a compelling business case to justify needed technology and staffing. Business leaders are getting smarter on the topic of cybersecurity, so cybersecurity leadership needs to rise above the FUD mentality and deliver value that is commensurate with the needs of the business.
With compliance such as EU GDPR and NIST 800-171/CMMC, there is a strong need for cybersecurity leaders who can develop and implement strategic plans to protect systems and data in order to keep their company both secure and compliant. The act of implementing cybersecurity strategic plans does not happen overnight since it requires funding for proper staffing and resources. All of this requires a plan.
Having a hierarchical business plan is a logical step to operationalize the business’ requirements. Understanding the hierarchy of business planning documentation can lead to well-informed risk decisions, which influences technology purchases, staffing resources, and management involvement. This is your opportunity to step up by designing and implementing a cohesive cybersecurity strategy that will be an asset to your company and enable you to be the cybersecurity leader that your organization needs you to be.
- Would you like to reward exceptional behavior and at the same time hold people accountable for substandard performance? Business planning goals provide quantifiable targets for both individual contributors and management to objectively gauge performance.
- Would you like to know what your priorities are for day-to-day work or initiatives? Business planning goals prioritize efforts that can help reduce confusion and focus efforts.
Why Should You Conduct Cybersecurity Business Planning As A CISO? If You Fail To Plan, You Plan To Fail
Some of the most-abused business planning statements are strategy, operations, and tactics. While these terms are used by organizations across the globe, the terms have their origins in military planning where the terms have very unique scopes that are important to understand. Hierarchically, tactics support operations and operations support strategy.
STRATEGY > OPERATIONS > TACTICS
The discussion of “strategy vs operations vs tactics” primarily comes down to the concept of defining doctrine. The concepts of strategy, operations and tactics are directly rooted in military planning. The US Army’s formalization of this doctrine occurred in 1982 release of Field Manual (FM) 100-5 as a way to formalize a logical approach to describe the “levels of war” that span from the generals in charge, all the way to the lowly private in the trenches.
There is overlap between strategic, operational and tactical levels, so there is no clear demarcation that can be uniformly applied to all organizations. The actions of individual contributors at the tactical level stack up to support broader operational goals, which in turn are designed to support a strategy that is aligned with the company’s success.
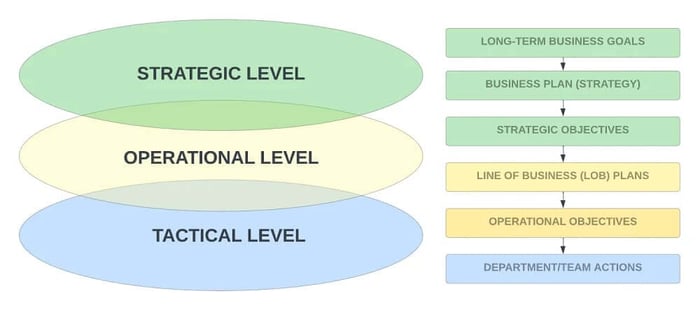
As it applies to the private sector:
- Strategic - At the strategic level, an organization employs available resources to secure its business objectives (e.g., corporate business plan).
- Operational - At the operational level, an organization uses available resources to attain strategic goals within a specific Line of Business (LOB).
- Tactical - At a tactical level, departments/teams employ techniques/procedures to support operational objectives, as defined by the LOB.
In the context of cybersecurity & data privacy considerations, it is possible to overlay the “who, what, when, how & why” across the strategic, operational and tactical needs of your organization:
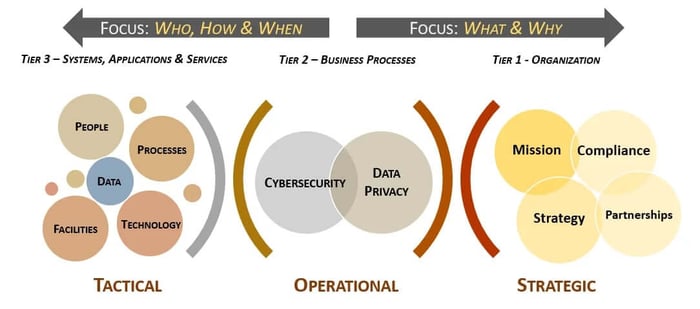
Real Word Scenario Where Tactics Support Operations & Operations Support The Strategy.
In a real-world scenario, look at the historical event of the Allied invasion of Normandy during the Second World War:
- Strategy. The Allies’ high-level plan in Europe was to wage a multi-pronged effort to pressure the Axis powers into an unconditional surrender. This involved the coordination of several heads of state to agree upon a combined goal.
- Operations. One of these multi-pronged efforts of the Allied strategy involved opening a new front in western Europe by landing Allied forces in France. Operation Overlord was the effort to invade France via multiple beach landings throughout Normandy in June 1944. This involved the coordination of multiple divisions and military services to deliver the appropriate personnel, equipment, and supplies at the right time and locations.
- Tactics. The actions taken by individual soldiers and small units were designed to support the larger effort of Operation Overlord. Each soldier had a role in his unit, and each unit had a role in the beach landings.

The same concept applies to businesses in every industry. The actions of individual contributors at the tactical level stack up to support broader operational goals, which in turn are designed to support a strategy that is aligned with the company’s success.
What Right Looks Like
An indicator of a well-run cybersecurity program is where staff at all levels clearly know their role in making the organization successful because the leadership implemented a mission, vision, and strategy to drive its operations. This is leadership in its purest form, since it involves providing appropriate direction and then empowering staff to make the right things happen.
A picture is sometimes worth 1,000 words. This diagram helps visualize the hierarchical nature of these business planning components.
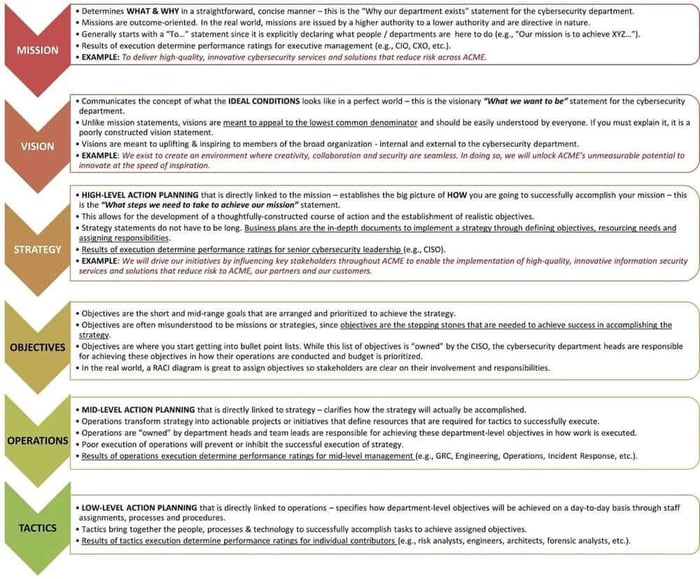
Mission
Mission statements are similar to vision statements, in that they, too, look at the big picture. However, they're more concrete, and they are definitely more "action-oriented" than vision statements. Your vision statement should inspire people to dream; your mission statement should inspire them to action. Mission statements answer the question of why your business/department exists.
- Mission statements are outcome-oriented and determine the what and why in a straightforward, concise manner.
- Missions are directive in nature by a higher authority to a lower authority (e.g., CIO or board of directors issues a mission to the CISO).
- The results of mission execution determine performance ratings for executive management.
Quite simply, a mission statement is a concise statement that describes why an organization is operating and thus provides a framework within which strategies are formulated. It describes:
- What the organization does (i.e., present capabilities);
- Who all it serves (i.e., stakeholders); and
- What makes an organization unique (i.e., reason for existence).
A mission statement differentiates an organization from others by explaining its broad scope of activities, its products, and technologies it uses to achieve its goals and objectives. Features of a mission statement:
- It must be feasible and attainable.
- It must be credible so all stakeholders will be able to believe it.
- It must be clear enough so that any action can be taken.
- It should be unique and distinctive to leave an impact in everyone’s mind.
- It should be inspiring for all employees (both management and staff).
After having developed possible statements, you will want to ask of each one:
- Does it describe what your organization will do and why it will do it?
- Is it concise (1-3 sentences)?
- Is it outcome oriented?
- Is it inclusive of the goals and people who may become involved in the organization?
Example mission statements:
- “To deliver high-quality, innovative cybersecurity services and solutions that reduce risk across ACME.“
- “To bring inspiration and innovation to every athlete in the world.”
- ”To provide customers with superb value; high-quality, relevant technology; customized systems; superior service and support; and products and services that are easy to buy and use.”
- “To dedicate ourselves to humanity's quest for longer, healthier, happier lives through innovation in pharmaceutical, consumer and animal health products.”
- “To provide fast food customer food prepared in the same high-quality manner world-wide that is tasty, reasonably-priced & delivered consistently in a low-key decor and friendly atmosphere.”
- “To develop & deliver the most innovative products, manage customer experience, deliver quality services that contribute to brand strength, establishes a competitive advantage and enhances profitability, thus providing value to the stakeholders of the bank.”
- “To be the company that best understands and satisfies the product, service and self-fulfillment needs of women—globally.”
Vision
A vision answers the “where we want to be” question. It gives us a reminder about what an organization is attempting to develop. It incorporates a shared understanding about the nature and aim of the organization and utilizes this understanding to direct and guide the organization towards a better purpose. Vision statements communicate the concept of what ideal conditions look like in a perfect world for the execution of the mission.
- Vision statements are meant to appeal to every staff member and should be easily understood by everyone. Quite simply, if you must explain it, it is a poorly constructed vision statement!
- This is an executive function performed by the CISO to uplift & inspire across the broader organization - internal and external to the cybersecurity department.
The best visions are inspirational, clear, memorable, and concise. An effective vision statement must have following features:
- It must be concise.
- It must be unambiguous.
- It must be clear.
- It must harmonize with organization’s culture and values.
- The dreams and aspirations must be rational & realistic.
In order to realize the vision, it must be deeply instilled in the organization, being owned and shared by everyone involved in the organization. For vision statements, we have to make sure it passes the "sniff test":
- Will it draw people to common work?
- Does it give hope for a better future?
- Will it inspire employees to realize their dreams through positive, effective action?
- Does it provide a basis for developing the other aspects of your action planning process?
Example vision statements:
- “We exist to create an environment where security, collaboration and creativity are seamless. In doing so, we will unlock ACME’s unmeasurable potential to innovate at the speed of inspiration.”
- “Our vision is to be earth's most customer centric company; to build a place where people can come to find and discover anything they might want to buy online.”
- “We intend to provide our customers with the best online shopping experience from beginning to end, with a smart, searchable website, easy-to-follow instructions, clear and secure payment methods, and fast, quality delivery.”
- “The ACME Company will inspire its employees to be the best they can be. We will engage in sustainable practices and anticipate the needs of our customers. We will maximize return to the stockholders while still maintaining quality in our products. “
- “Our vision is to bring our students into the 21st century through innovation and modern technology. Learning will be enhanced with computer software and educational games that will allow students to proceed at their own rate according to their ability.”
- “We will be the premier organization operating locally and internationally that provides the complete range of financial services to all segments under one roof.”
Strategy
Strategy statements are high-level actions that are coherently arranged to achieve your mission. Defining the objective, scope and competitive advantage requires trade-offs, which are fundamental considerations to building a strategy. For example, if a company decides to pursue growth, it must accept that profitability will not be a priority. If it decides to serve institutional clients, it may ignore retail customers.
- The CISO establishes the big picture of how the department will accomplish its mission.
- Strategies allow for the development of a thoughtfully-constructed course of action and the establishment of realistic objectives.
- Business plans are the in-depth documents to implement a strategy through the detailed definition of objectives, resourcing needs and assigning responsibilities.
- The results of strategy execution determine performance ratings for senior cybersecurity leadership (e.g., CISO).
Now that we’ve got the “what” and “why” answered for your organization, it’s time to jump into the “how.” It’s time to lay down how we’re going to execute and bring the vision and mission statements to reality. That’s where setting goals and objectives come into play. We’ll start with a friendly reminder of the importance of making them SMART:
- S – Specific (target a specific area for improvement)
- M – Measurable (quantify or at least suggest an indicator of progress)
- A – Actionable (specifically who will do it)
- R – Realistic (state what results can realistically be achieved, based on available resources)
- T – Time-Bound (specify when the results can be achieved)
Strategic intent:
- Gives a picture about what an organization must get into immediately in order to achieve the company’s vision.
- Motivates the people. It clarifies the vision of the company.
- Helps management to emphasize and concentrate on the priorities.
- Influences people to achieve what at first may seem to be unachievable goals.
There are three basic elements of a strategy statement:
- The objective defines the ends that the strategy is designed to achieve within a specific time frame.
- The scope is the domain of the business—the part of the business landscape in which your company will operate.
- The competitive advantage is the essence of your strategy. It determines what you will do differently or better than the competition to achieve your objective.
Example strategy statements:
- “We will influence key stakeholders to raise the level of technology and security maturity in ACME so that compliance requirements are proactively addressed in a ‘business as usual’ manner. The role of IT security will evolve from actively managing control execution to a validation and reporting role.”
- “ACME will grow from 10,000 to 17,000 financial advisers by 2022 by offering trusted and convenient face-to-face financial advice to conservative individual investors who delegate their financial decisions, through a national network of one-financial- adviser offices.”
- “ACME will increase market penetration in the North America SOHO segment by 20% through improvements in product usability, partner marketing, and customer relationship management leveraging our long-term relationships with customers and deep awareness of their business needs.”
Objectives
Objectives are the short and mid-range goals that are arranged and prioritized to achieve the strategy.
- Objectives are merely the stepping stones that are needed to achieve success in accomplishing the strategy.
- Objectives can be as simple as a bullet point list that documents components necessary to achieve the strategy.
- While this list of objectives is “owned” by the CISO, the cybersecurity department heads are responsible for achieving these objectives through formulating and executing the plans for how their unique operations are conducted and resources are prioritized.
- A responsibility assignment matrix (also known as RASCI diagram) is a great tool to assign stakeholder roles and responsibilities to ensure objectives are proactively managed.
Example objectives:
- “Develop, implement and manage Continuous Monitoring (CM) capabilities to enable the timely identification and response to potential cybersecurity events.”
- “Achieve an ISMS maturity level of CMM 3 by 2023 and CMM 4 by 2025.”
Operations
Operations are mid-level actions that directly link to strategy and objectives – it clarifies how both will actually be accomplished. Operations transform strategy and objectives into actionable projects or initiatives that define the required resources for tactics to successfully execute.
- Operations are “owned” by department heads and team leads are responsible for achieving these department-level objectives in how work is prioritized, resourced and managed.
- Poor execution of operations will prevent or inhibit the successful execution of a strategy.
- The results of operations execution determine performance ratings for mid-level management (e.g., GRC, Engineering, SOC, Incident Response, etc.).
Tactics
Tactics are low-level actions that directly link to operations – it specifies how department-level objectives will be achieved on a day-to-day basis through staff assignments, processes and procedures.
- Tactics bring together the people, processes & technology to successfully accomplish tasks to achieve assigned objectives.
- Poor execution of tactics will prevent or inhibit the successful execution of operations.
- The results of tactics execution determine performance ratings for individual contributors (e.g., risk analysts, engineers, architects, forensic analysts, etc.).