Essential Guide to CMMC & NIST SP 800-171 Compliance
This episode of “Coffee Thoughts With Tom” ponders the question “CMMC was never a “real maturity model” so what does a NIST 800-171 Capability Maturity Model (CMMC) look like?” and builds off a previous article about how the Cybersecurity Maturity Model Certification (CMMC) was really never a Capability Maturity Model (CMM), beyond having “maturity model” embedded within its name [note – that article is well worth the read if you have time to get good background information on maturity models].
Why Should You Care About Maturity?
The simple answer is to help eliminate, or at least minimize, the Fear, Uncertainty & Doubt (FUD) in your organization’s cybersecurity program. Maturity targets and current state assessments can be used to:
- Justify budgetary resources for people, processes and technologies; and
- Evaluate controls by injecting objectivity into the assessment process.
When you start working through maturity considerations, please keep in mind with CMMC that the DoD prescribes the baseline controls as a means to manage the DoD’s risks, not necessarily your business’ risks! No OSC should seriously consider itself “secure” by meeting just Level 1 or Level 2 CMMC controls. One reason is simply that CMMC only focuses on the DoD’s risk management for Confidentiality and Integrity of regulated data (FCI/CUI), while for the most part ignoring Availability (your ability to stay in business). The other reason is most OSCs also have other requirements that range from ITAR to PCI DSS to state/international data protection laws that they also have to contend with.
CMMC / NIST SP 800-171 should be viewed as a threshold for establishing the “must have” security practices that a modern business should align with, since it is on its way to being a global “gold standard” for identifying the threshold for what would be considered negligent business practices.
Leverage An Existing Maturity Model
The concept of managing cybersecurity and data protection controls based on maturity expectations is a worthwhile topic, so I decided to demonstrate how a “NIST SP 800-171 Maturity Model” could look that leverages existing maturity model constructs. In general, a maturity model is meant to accomplish a few things, beyond just sounding cool:
- Implement a mindset focused on continuous improvement (e.g., strive to make things more secure);
- Align process improvement goals with an organization’s business objectives; and
- Provide an evolutionary path to performance improvement.
Since NIST SP 800-171/CMMC are not focused on evolving capabilities, there is no defined “sweet spot” for Organizations Seeking Certification (OSC) to work towards for its level of process maturity. The reason for this is CMMC levels are dictated to the OSC according to:
- The type of regulated data (FCI or CUI); and
- If the OSC is required to address additional controls for mitigating risks relative to Advanced Persistent Threats (APTs).
For this example, I am going to use the Cybersecurity & Data Privacy Capability Maturity Model (C|P-CMM) that is a free resource of the Secure Controls Framework (SCF). The SP-CMM is meant to solve the problem of objectivity in both establishing and evaluating cybersecurity and privacy controls. There are three main objectives for the SP-CMM and this supports using it for NIST SP 800-171/CMMC:
- 1.Provide CISOs/CPOs/CIOs with objective criteria that can be used to establish expectations for a cybersecurity & privacy program;
- 2.Provide objective criteria for project teams so that secure practices are appropriately planned and budgeted for; and
- 3.Provide minimum criteria that can be used to evaluate third-party service provider controls.
The SP-CMM leverages the framework established by the Systems Security Engineering Capability Maturity Model (SSE-CMM) and it a SP-CMM as “a framework for evolving an engineering organization from an ad hoc, less organized, less effective state to a highly structured and highly effective state. Use of such a model is a means for organizations to bring their practices under statistical process control in order to increase their process capability.” These 5 levels of maturity from SSE-CMM that the SP-CMM uses should not be construed as having anything to do with the five CMMC v1.0 “maturity levels” since they are entirely different animals.
The six SP-CMM levels are:
- SP-CMM 0 – Not Performed
- SP-CMM 1 – Performed Informally
- SP-CMM 2 – Planned & Tracked
- SP-CMM 3 – Well-Defined
- SP-CMM 4 – Quantitatively Controlled
- SP-CMM 5 – Continuously Improving
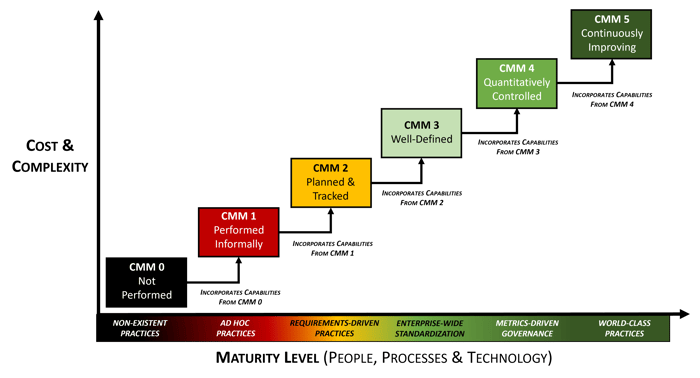
Note: If this concept of using the SP-CMM interests you, please make a cup of coffee and read the C|P-CMM overview document, since that will provide a lot of background information on how to use it efficiently and keeps me from having to retype a lot of words that already exist in that document.
Getting Started: Identify Your Organization’s “Sweet Spot” For CMMC/NIST SP 800-171?
When you look at the various maturity models used across industries, it is possible to identify a “sweet spot” that is unique to each organization’s risk appetite and budget. That sweet spot is made up of four different considerations:
- 1.RISK. Risk decreases with maturity, but noticeable risk reductions are harder to attain as maturity increases.
- 2.PROCESS REVIEW LAG. Process improvements increase with maturity, based on shorter review cycles and increased process oversight. Artificial Intelligence (AI) and Machine Learning (ML) can make process improvements near real-time in a world-class environment.
- 3.STAKEHOLDER VALUE. The perceived value of security controls increases with maturity, but tends to decrease once the value of the additional cost and complexity becomes harder to justify to business stakeholders or where cost and complexity outweigh the risk reduction benefits.
- 4.NEGLIGENCE THRESHOLD. Without the ability to demonstrate evidence of both due care and due diligence, an organization may be found negligent. In practical terms, the “negligence threshold” is when maturity is progressing out of ad hoc practices and are formalized to the point that documented evidence exists to demonstrate reasonable steps were taken to operate a control.
For most organizations, the “sweet spot” for maturity targets is between SP-CMM 2 and 4 levels. What defines the ideal target within this zone is generally based on resource limitations and other business constraints, so it goes beyond just the cybersecurity and privacy teams dictating targets. Identifying maturity targets is meant to be a team effort between both technologists and business stakeholders. From a business consideration, the increase in cost and complexity will always require cybersecurity and privacy leadership to provide a compelling business case to support any maturity planning needs. Speaking in terms the business can understand is vitally important.
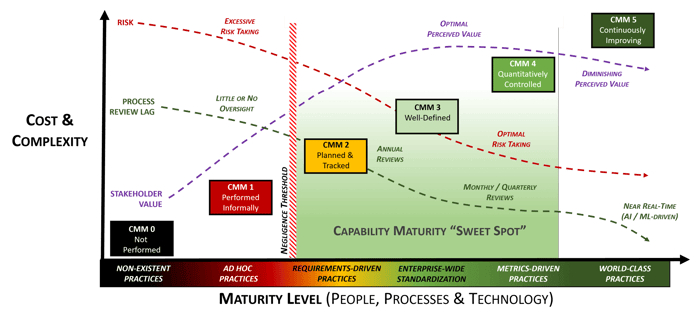
Fun Fact: During the development of the SP-CMM, a contributor identified an interesting insight that SP-CMM 0-3 are “internal” maturity levels for cybersecurity and privacy teams, whereas SP-CMM 4-5 are “external” maturity levels that expand beyond those teams. When you look at the stakeholders involved in SP-CMM 0-3, it is almost entirely IT, cybersecurity and privacy. It isn’t until SP-CMM 4-5 where there is true business stakeholder involvement in oversight and process improvement. This creates an internal to external shift in owning the cybersecurity & privacy program.
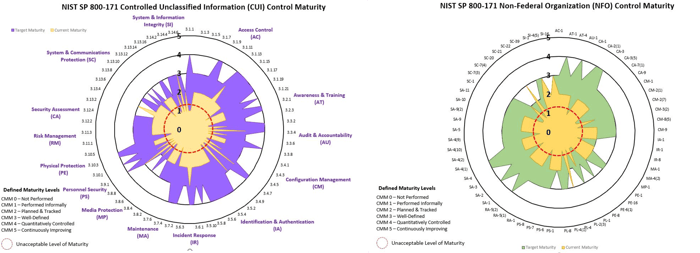
There are two ways to approach assigning maturity levels by assigning a maturity target at the:
- Domain level (14 domains); or
- Control level (110 CUI controls and 61 NFO controls);
Both NIST SP 800-171 and CMMC 2.0 break its controls down into 14 different domains/families, so the easiest way to start off is to identify what level of maturity is appropriate at a domain level:
- Access Control (AC)
- Audit & Accountability (AU)
- Awareness & Training (AT)
- Configuration Management (CM)
- Identification & Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Risk Management (RM)
- Security Assessment (CA)
- System & Communications Protection (SC)
- System & Information Integrity (SI)
What About Non-Federal Organization (NFO) Control?
You should also evaluate the maturity of your NFO controls. If you are not sure what NFO controls are, please make another pot of coffee and read all about them this website that is dedicated to demystifying NFO Controls.
SP-CMM Levels
Here is an overview of what defines the criteria associated with the SP-CMM levels:
SP-CMM 0 – Not Performed
This level of maturity is defined as “non-existence practices,” where the control is not being performed.
- There are no identifiable work products of the process.
SP-CMM 0 practices, or a lack thereof, are generally considered to be negligent. The reason for this is if a control is reasonably-expected to exist, by not performing the control that would be negligent behavior. The need for the control could be due to a law, regulation or contractual obligation (e.g., client contract or industry association requirement).
SP-CMM 1 – Performed Informally
This level of maturity is defined as “ad hoc practices,” where the control is being performed, but lacks completeness & consistency.
- Base practices of the process area are generally performed.
- The performance of these base practices may not be rigorously planned and tracked.
- Performance depends on individual knowledge and effort.
- There are identifiable work products for the process.
SP-CMM 1 practices are generally considered to be negligent. The reason for this is if a control is reasonably-expected to exist, by only implementing ad-hoc practices in performing the control that could be considered negligent behavior. The need for the control could be due to a law, regulation or contractual obligation (e.g., client contract or industry association requirement).
Note – The reality with a SP-CMM 1 level of maturity is often:
- For smaller organizations, the IT support role only focuses on “break / fix” work or the outsourced IT provider has a limited scope in its support contract.
- For medium / large organizations, there is IT staff but there is no management focus to spend time on the control.
SP-CMM 2 – Planned & Tracked
This level of maturity is defined as “requirements-driven practices,” where the expectations for controls are known (e.g., statutory, regulatory or contractual compliance obligations) and practices are tailored to meet those specific requirements.
- Performance of the base practices in the process area is planned and tracked.
- Performance according to specified procedures is verified.
- Work products conform to specified standards and requirements.
SP-CMM 2 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control. SP-CMM 2 practices are generally targeted on specific systems, networks, applications or processes that require the control to be performed for a compliance need (e.g., PCI DSS, HIPAA, NIST 800-171, etc.).
It can be argued that SP-CMM 2 practices focus more on compliance over security. The reason for this is the scoping of SP-CMM 2 practices are narrowly-focused and are not organization-wide.
Note – The reality with a SP-CMM 2 level of maturity is often:
- For smaller organizations:
- IT staff have clear requirements to meet applicable compliance obligations or the outsourced IT provider is properly scoped in its support contract to address applicable compliance obligations.
- It is unlikely that there is a dedicated cybersecurity role and at best it is an additional duty for existing personnel.
- For medium / large organizations:
- IT staff have clear requirements to meet applicable compliance obligations.
- There is most likely a dedicated cybersecurity role or a small cybersecurity team.
SP-CMM 3 – Well-Defined
This level of maturity is defined as “enterprise-wide standardization,” where the practices are well-defined and standardized across the organization.
- Base practices are performed according to a well-defined process using approved, tailored versions of standard, documented processes.
- Process is planned and managed using an organization-wide, standardized process.
SP-CMM 3 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control. Unlike SP-CMM 2 practices that are narrowly focused, SP-CMM 3 practices are standardized across the organization.
It can be argued that SP-CMM 3 practices focus on security over compliance, where compliance is a natural byproduct of those secure practices. These are well-defined and properly-scoped practices that span the organization, regardless of the department or geographic considerations.
Note – The reality with a SP-CMM 3 level of maturity is often:
- For smaller organizations:
- There is a small IT staff that has clear requirements to meet applicable compliance obligations.
- There is a very competent leader (e.g., security manager / director) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization.
- For medium / large organizations:
- IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise.
- In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)
- There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization.
SP-CMM 4 – Quantitatively Controlled
This level of maturity is defined as “metrics-driven practices,” where in addition to being well-defined and standardized practices across the organization, there are detailed metrics to enable governance oversight.
- Detailed measures of performance are collected and analyzed. This leads to a quantitative understanding of process capability and an improved ability to predict performance.
- Performance is objectively managed, and the quality of work products is quantitatively known.
SP-CMM 4 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control, as well as detailed metrics enable an objective oversight function. Metrics may be daily, weekly, monthly, quarterly, etc.
Note – The reality with a SP-CMM 4 level of maturity is often:
- For smaller organizations, it is unrealistic to attain this level of maturity.
- For medium / large organizations:
- IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise.
- In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)
- There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization.
- Business stakeholders are made aware of the status of the cybersecurity and privacy program (e.g., quarterly business reviews to the CIO/CEO/board of directors). This situational awareness is made possible through detailed metrics.
SP-CMM 5 – Continuously Improving
This level of maturity is defined as “world-class practices,” where the practices are not only well-defined and standardized across the organization, as well as having detailed metrics, but the process is continuously improving.
- Quantitative performance goals (targets) for process effectiveness and efficiency are established, based on the business goals of the organization.
- Continuous process improvement against these goals is enabled by quantitative feedback from performing the defined processes and from piloting innovative ideas and technologies.
SP-CMM 5 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control and incorporates a capability to continuously improve the process. Interestingly, this is where Artificial Intelligence (AI) and Machine Learning (ML) would exist, since AI/ML would focus on evaluating performance and making continuous adjustments to improve the process. However, AI/ML are not requirements to be SP-CMM 5.
Note – The reality with a SP-CMM 5 level of maturity is often:
- For smaller organizations, it is unrealistic to attain this level of maturity.
- For medium-sized organizations, it is unrealistic to attain this level of maturity.
- For large organizations:
- IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise.
- In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)
- There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization.
- Business stakeholders are made aware of the status of the cybersecurity and privacy program (e.g., quarterly business reviews to the CIO/CEO/board of directors). This situational awareness is made possible through detailed metrics.
- The organization has a very aggressive business model that requires not only IT, but its cybersecurity and privacy practices, to be innovative to the point of leading the industry in how its products and services are designed, built or delivered.
- The organization invests heavily into developing AI/ML technologies to made near real-time process improvements to support the goal of being an industry leader.
In Summary
You can create your own useful spider charts for current vs targeted maturity by modifying cells D & E on the "Control Maturity Worksheet" that is provided as a free resource (hosted for download by the CMMC Center of Awesomeness).
