C-SCRM & NIST 800-161 R1
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Maturity Model Certification (CMMC), the area of supply chain security practices is unfamiliar territory, beyond responding to Third-Party Risk Management (TRPM) questionnaires. This guidance is to help paint the picture of how to view supply chain security.
NIST 800-171 (protecting CUI) vs NIST 800-171 (supply chain security)
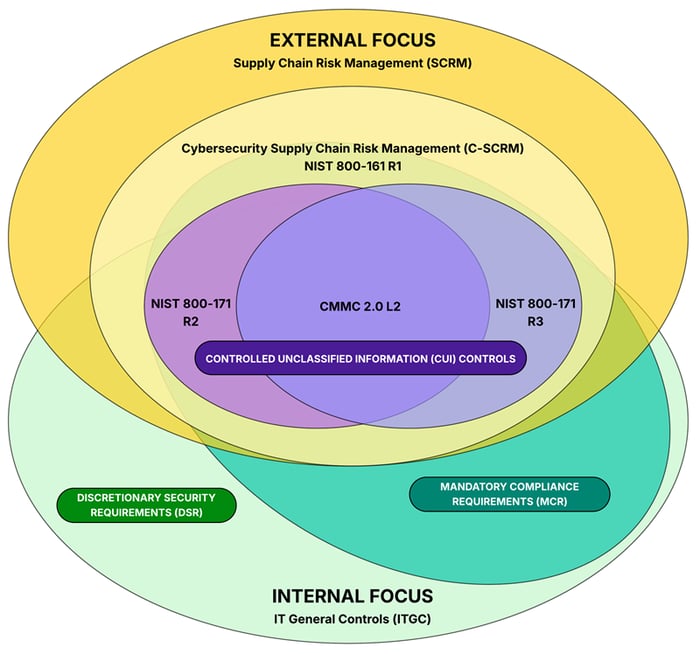
What is important to understand is there are hierarchical layers associated with NIST 800-171 / CMMC and NIST 800-161:
- NIST 800-171 exists to protect Controlled Unclassified Information (CUI) and is focused on confidentiality and integrity. There is no consideration for availability or resiliency, due to the very narrow focus of NIST 800-171 to protect only CUI, nothing more. CMMC is a third-party assessment mechanism to ensure NIST 800-171 controls are in place and operational.
- NIST 800-161 encompasses the concepts covered within NIST 800-171, where the broader focus is to help organizations be both secure and resilient (e.g., addresses all confidentiality, integrity & availability components). Cybersecurity Supply Chain Risk Management (C-SCRM) is meant to holistically address the broader threats and risks to an organization's ability to operate.
- While NIST 800-161 addresses C-SCRM, it is important to note that C-SCRM is just a subset of the organization's broader Supply Chain Risk Management (SCRM) practices, since there is more to supply chain risk management than just cybersecurity and data protection practices.
Deliverables: SSP (NIST 800-171) & SCRM Plan (NIST 800-161)
Where there is added confusion is the aspect of generating a "Supply Chain Risk Management (SCRM) Plan" in both GSA requirements and NIST 800-171 R3. The SCRM Plan is an output (e.g., deliverable) that is the end product of establishing an organization's SCRM/C-SCRM strategy and implementation plan. Similar in concept to how a System Security Plan (SSP) is a deliverable for NIST 800-171 / CMMC, the SCRM plan is a deliverable for NIST 800-161.
From a NIST 800-171 perspective, the SSP is a "living document" that reflects what the organization does to apply and maintain security controls for the CUI environment. As thing change in the CUI environment, the SSP is updated to reflect the reality of the security controls in place. The same concept applies to a SCRM Plan, where it is also a "living document" that is expected to be updated as there are changes that directly or indirectly affect the supply chain. The similarity between the two documents is that these deliverables provide summarizations and are not the actual source documents (e.g., policies, standards, procedures, risk assessment processes, inventories, etc.). You still need underlying artifacts and processes to populate a SSP or SCRM Plan document.
Similar in concept to there being no US Government-sanctioned "gold standard" for a SSP template, the same issue exists for a SCRM Plan template. Generally, for a SCRM Plan template, there are two (2) basic starting points that provide examples for what a SCRM Plan should contain:
- NIST 800-161 R1; and
- DI-MGMT-82256A
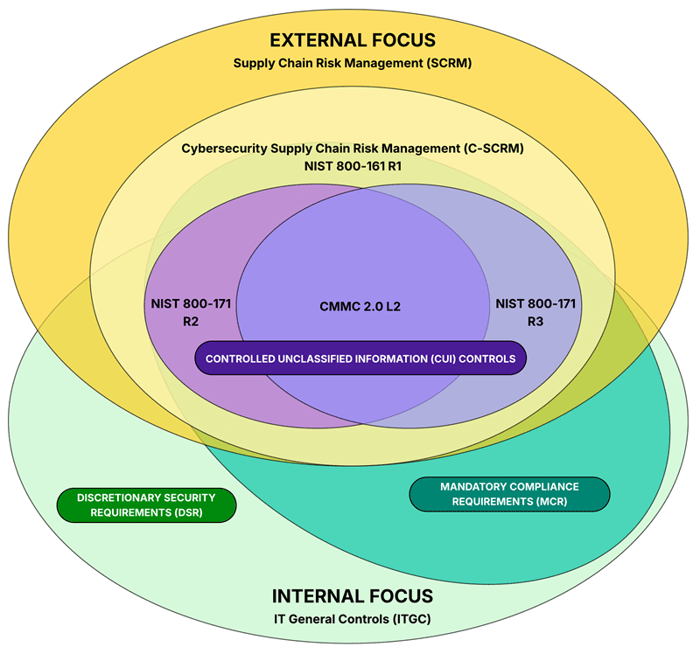
At the root of the concept, there are two (2) sides to consider: (1) internal and (2) external. From an internal perspective for cybersecurity and data protection operations, it generally comes down to addressing both Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR):
- Minimum Compliance Requirements (MCR) are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- Discretionary Security Requirements (DSR) are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.
For many companies, compliance with NIST 800-171 R2 & CMMC are mandatory requirements (e.g., MCR). With new contracts from the GSA, there are also mandatory requirements for NIST 800-161 R1 that focus on C-SCRM. NIST 800-161 R1 is the “gold standard” for C-SCRM practices. When NIST 800-171 R3 is applicable to the Defense Industrial Base (DIB), that will bring C-SCRM into scope for NIST 800-171/CMMC since it has a C-SCRM component.
Note: If you want to read more about MCR vs DSR, the Integrated Controls Management (ICM) model is a free reference that is worth reading.