# https://complianceforge.com llms-full.txt
## Cybersecurity Compliance Templates
[Skip to main content](https://complianceforge.com/#main-content)

## Purchase Editable Cybersecurity Documentation Templates Online
## Why Choose ComplianceForge Cybersecurity Documentation Templates?
ComplianceForge specializes in editable cybersecurity documentation templates that save our clients considerable time and money. As an industry leader in providing affordable, editable and scalable documentation solutions to support cybersecurity and data privacy compliance efforts, ComplianceForge products follow recognized secure practices for scalable, hierarchical documentation solutions. ComplianceForge products serve as a business accelerator, where we do the heavy lifting for our clients so their cybersecurity and IT staff can focus on the roles they were hired to do. Essentially, we help our clients stay in business by providing the necessary policies, standards, procedures and other documentation they need to address their cybersecurity and data privacy compliance obligations in the most efficient manner possible. We leverage industry-recognized secure practices so our solutions can scale from Fortune 100 multinationals with complex compliance requirements, all the way down to small companies (1-2 person endeavors) that just need single solutions, such as NY DFS 23 NYCRR 500, PCI DSS or CMMC compliance.
At ComplianceForge, we have been writing cybersecurity documentation since 2005. Our documentation can help organizations meet common cybersecurity and data privacy compliance obligations, including CMMC, NIST SP 800-171, ISO 27001, NY DFS 23 NYCRR 500, EU GDPR, RMF, FedRAMP, PCI DSS, HIPAA, FACTA, GLBA and others. ComplianceForge has options for organizations of any size or industry. We offer multiple solutions to help organizations meet their statutory, regulatory and contractual obligations for cybersecurity and data protection:
- [Policies, Standards & Controls](https://complianceforge.com/cybersecurity-policies-standards-controls)
- [Procedures](https://complianceforge.com/standardized-operating-procedures/)
- [Supply Chain Risk Management](https://complianceforge.com/supply-chain-risk-management/)
- [NIST 800-171 Compliance](https://complianceforge.com/nist-800-171-cmmc-policy-templates/)
- [Risk Management](https://complianceforge.com/digital-cybersecurity-risk-management/)
- [Data Protection (Privacy) & Secure Engineering](https://complianceforge.com/data-protection-privacy-secure-engineering)
- [Vulnerability & Patch Management](https://complianceforge.com/digital-cybersecurity-vulnerability-patch-management/)
- [Incident Response](https://complianceforge.com/digital-cybersecurity-incident-response-program-documentation/)
- [PCI DSS Compliance](https://complianceforge.com/pci-dss-cybersecurity-compliance-policies-standards)
ComplianceForge products are editable templates that are designed to address industry-recognized security requirements. These documentation templates are written to address leading security practices, so while there are no "fill in the blanks" sections, the expectation is that you do have to tailor these documents for your specific needs, since only you know the technologies and resources available in your environment. In designing and building our documentation, we have done the heavy lifting for you and provide a solution that is efficient for our clients to finalize and adopt.
Under each product page, you will find product examples and cost savings estimates. The PDF product examples allow you to see the professionalism and level of detail that we provide when creating our products. The cost savings estimates are insightful for the potential time and money savings by purchasing ComplianceForge documentation instead of hiring a consultant to write the documentation or writing the documentation yourself.
In addition to the individual products, ComplianceForge also provides bundled compliance solutions to help provide a robust, yet efficient and scalable solution:
- [NIST 800-171 & CMMC Compliance](https://complianceforge.com/cmmc-nist-800-171-templates/)
- [Premium GRC Content (Secure Controls Framework)](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/)
- [Cybersecurity Policies, Standards & Procedures](https://complianceforge.com/cybersecurity-policies-standards-procedures-bundles/)
- [Cybersecurity Supply Chain Risk Management](https://complianceforge.com/cybersecurity-supply-chain-risk-management/)
- [Data Privacy & Data Protection (GDPR, CCPA & more)](https://complianceforge.com/privacy-data-protection-gdpr-eprivacy-bundles/)
- [Risk Management Bundles](https://complianceforge.com/risk-management-bundles/)
ComplianceForge sells more than just policies, standards and procedures. Our solutions can help provide additional detail on how a company implements their policies, standards and procedures. Essentially, this can be considered a playbook of how a company operationalizes these compliance concepts (e.g., risk management, vulnerability management, etc.).
## ComplianceForge Is A Secure Controls Framework Licensed Content Provider (SCF LCP)
ComplianceForge is a [SCF Licensed Content Provider](https://complianceforge.com/scf/scf-cap-editable-scf-based-documentation/). This means ComplianceForge is able to sell cybersecurity and data protection policies, standards and procedures based on [Secure Controls Framework (SCF)](https://securecontrolsframework.com/) controls:
- [Digital Security Program (DSP) - SCF-based policies, standards and metrics](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [Cybersecurity Standardized Operating Procedures (CSOP) - SCF-based procedures](https://complianceforge.com/product/scf-dsp-procedures-csop/)
- [Digital Privacy Program (DPP) - SCF-based data privacy program](https://complianceforge.com/product/data-privacy-program-dpp/)
For the [SCF Conformity Assessment Program (SCF CAP)](https://securecontrolsframework.com/scf-conformity-assessment-program-cap/), ComplianceForge has documentation solutions that can save an Organization Seeking Assessment (OSA) hundreds of hours. These editable templates can help an organization quickly prepare for a third-party SCF CAP assessment:
- [SCF-based NIST CSF 2.0 policies, standards and procedures](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
- [SCF-based policies, standards and procedures that address all SCF controls](https://complianceforge.com/bundle/dsp-bundle-1)
[](https://securecontrolsframework.com/scf-licensed-content-provider/)
## Editable Policy & Procedures Templates For NIST 800-171 & CMMC Compliance
In cybersecurity compliance matters, it doesn't exist unless it is documented. Meticulous documentation is the unsung hero in ensuring your organization's compliance with NIST 800-171 and readiness for a CMMC assessment. ComplianceForge is an industry-leader in NIST 800-171 & CMMC compliance. We specialize in cybersecurity compliance documentation and our products include the NIST 800-171 and CMMC policies, standards, procedures and POA&M/SSP templates that companies (small, medium and large) need to comply with NIST 800-171 / CMMC. We've been writing NIST 800-171 cybersecurity documentation since 2016 and continue to improve our solitions to help make NIST 800-171 & CMMC compliance as easy and as affordable as possible.
Our NIST 800-171 & CMMC compliance policies, standards and procedures are designed to scale for organizations of any size or level of complexity, so we serve businesses of all sizes, from the Fortune 500 all the way to small and medium businesses. The focus of NIST 800-171 and CMMC is to protect Controlled Unclassified Information (CUI) anywhere it is stored, transmitted and processed. NIST 800-171 & CMMC compliance starts with documentation for the very simple fact that when it comes to cybersecurity compliance, if it is not documented then it does not exist. Given that reality, you need to ensure your company has the proper cybersecurity documentation in place:
- [NIST 800-171 & CMMC policies, standards & procedures (specific to NIST SP 800-171 and CMMC 2.0 L2)](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-policies-standards-procedures)
- [Supply Chain Risk Management (SCRM) Plan](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-scrm-plans)
- [Risk Assessment Worksheet & Report Template](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-risk-assessment)
- [System Security Plan (SSP) Template](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-ssp)
- [Plan of Action (POA) / Plan of Action & Milestones (POA&M) Templates](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-poam)
- [A Considerable Number of Reference Documents and other templates](https://complianceforge.com/product/nist-800-171-compliance-program#ncp-templates)
ComplianceForge sells more than just CMMC policy templates policies, standards and procedures. Our solutions can save hundreds to thousands of hours, as compared to writing comparable documentation yourself or hiring a consultant to write it for you.
## What Is Your Upgrade Path For NIST 800-171 R3?
Sooner, rather than later, the US Government's global supply chain will have to transition to NIST 800-171 R3. ComplianceForge provides a free resource for organizations migrating from NIST 800-171 R2 to R3. This guide provides an Assessment Objective (AO)-level analysis to address differences:
- Over 1/3 are minimal effort (clear, direct mapping)
- Approximately 1/5 are moderate effort (indirect mapping)
- Approximately 1/2 are significant effort (no clear mapping or new AOs)
This guide also addresses the logical dependencies that exist from "orphaned AOs" that are not in NIST 800-171A R3, but a requirement to demonstrate evidence of due diligence and due care still exists for specific functions (e.g., maintenance operations, roles & responsibilities, inventories, physical security, etc.).
[](https://complianceforge.com/content/pdf/guide-nist-800-171-r3-transition.pdf)
## Editable & Affordable Cybersecurity Compliance Documentation Templates
[**NIST 800-171 & CMMC Compliance**](https://complianceforge.com/cmmc-nist-800-171-templates/ "")
Our NIST 800-171 & CMMC documentation is "DIBCAC battle tested" where it has been
successfully used in DIBCAC audits. That says a great deal about the quality of our content!
ComplianceForge is an industry leader in [**NIST 800-171**](https://complianceforge.com/compliance/nist-800-171 "understanding NIST 800-171 compliance requirements") & **[Cybersecurity\**\
**Maturity Model Certification (CMMC)](https://complianceforge.com/cybersecurity-maturity-model-certification-cmmc/ "CMMC compliance")** compliance documentation solutions. Our documentation templates
have helped customers that range from the Fortune 500 down to small and medium-sized businesses comply with **[DFARS](https://complianceforge.com/compliance/nist-800-171 "dfars cybersecurity requirement")** requirements
for NIST 800-171. Our products are scalable, professionally-written and affordable. The focus of NIST 800-171
& CMMC is to protect [**Controlled**\\
**Unclassified Information (CUI)**](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret "Controlled Unclassified Information CUI definition") anywhere it is stored, transmitted and processed. Our solutions
range from small businesses through to enterprise-class environments.
Our NIST 800-171 /
CMMC documentation is updated to address CMMC 2.0 that addresses all Controlled Unclassified Information (CUI) and
Non-Federal Organization (NFO) controls from NIST SP 800-171 R2.
[](https://complianceforge.com/cmmc-nist-800-171-templates/#nist-800-171-policies-standards-procedures "NIST 800-171 CMMC policies standards procedures template")
[Browse This Collection of Bundles](https://complianceforge.com/cmmc-nist-800-171-templates/ "")
[**Premium GRC Content (Secure Controls Framework)**](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/ "")
If you use the [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework (SCF)"), then you
will want to buy one of these bundles, since the [**Digital**\\
**Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)") has 1-1 mapping between the SCF and the DSP.
We sell the **policies, standards, procedures & more** that will compliment the SCF controls that you use! The DSP provides you with SCF-aligned policies, standards, guidelines, metrics, controls and capability maturity criteria. The **[Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)** provides you with SCF-aligned procedures/control activities. These two products alone can save you hundreds of hours of document writing and can help your organization hit the ground running with the SCF.
[](https://securecontrolsframework.com/ "Secure Controls Framework - premium grc content")
The **Digital Security Program (DSP)** is a product we developed for companies that need to comply with multiple requirements, but do not want to be locked into documentation that is formatted to conform with the taxonomy ISO 27002 or NIST 800-53. Essentially, the DSP is a "best in class" approach to security documentation. The DSP metrics come mapped to the **NIST Cybersecurity Framework (CSF).**
[Browse This Collection of Bundles](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/ "")
[**Cybersecurity Supply Chain Risk Management**](https://complianceforge.com/cybersecurity-supply-chain-risk-management/ "")
ComplianceForge developed an editable template for a C-SCRM strategy and implementation plan
that is based on NIST SP 800-161 Rev 1, which is the current "gold standard" for authoritative C-SCRM guidance. This
is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the
ground running" with C-SCRM operations.

[Browse This Collection of Bundles](https://complianceforge.com/cybersecurity-supply-chain-risk-management/ "")
[**Privacy & Data Protection (GDPR, CCPA & more)**](https://complianceforge.com/privacy-data-protection-gdpr-eprivacy-bundles/ "")
NIST SP 800-160 is the "gold standard" for security by design, which is important since: (1) you
can have security without privacy, but (2) you cannot have privacy without security. Therefore, secure practices are
fundamental to any cybersecurity and privacy program.
Our documentation is designed to
address common cybersecurity and privacy needs, so that you can demonstrate compliance with your specific
requirements. This may be European Union General Data Protection Regulation (EU GDPR), California Consumer
Protection Act (CCPA) / California Privacy Rights Act (CPRA), NIST Privacy Framework, or SOC 2 Privacy Principles.
Regardless of the framework, you need to have evidence of how both cybersecurity and privacy principles are designed
and implemented. Our privacy bundles are uniquely designed to help you comply with leading privacy practices!

[Browse This Collection of Bundles](https://complianceforge.com/privacy-data-protection-gdpr-eprivacy-bundles/ "")
[**Risk Management Bundles**](https://complianceforge.com/risk-management-bundles/ "")
Identifying and managing risk is a part of business. We work hard to develop products that
assist clients with removing the Fear, Uncertainty & Doubt (FUD) factor that clouds many cybersecurity risk
management decisions. These products are editable Microsoft Word & Excel templates, so if you can use Microsoft
Office products, then you can use these risk management solutions!
When you "peel
back the onion" and prepare for an audit/assessment, there is a need to address "the how" for certain topics, such
as risk management. While policies and standards are designed to describe WHY something is required and WHAT needs
to be done, many companies fail to create documentation to address HOW the policies and standards are actually
implemented. We did the heavy lifting and created several program-level documents to address this need and the Risk
Management Program (RMP) is one of those products that can help demonstrate HOW risk management is structured at
your organization.

[Browse This Collection of Bundles](https://complianceforge.com/risk-management-bundles/ "")
## Editable Cybersecurity Policies, Standards & Procedures Templates
[**Policies, Standards & Controls**](https://complianceforge.com/cybersecurity-policies-standards-controls "")
- [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [NIST CSF - Policies & Standards (CDPP)](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
- [ISO 27001 / 27002 - Policies & Standards (CDPP)](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [NIST 800-53 R5 (moderate) - Policies & Standards (CDPP)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [NIST 800-53 R5 (high) - Policies & Standards (CDPP)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
[Browse This Category of Products](https://complianceforge.com/cybersecurity-policies-standards-controls "")
[**Procedures**](https://complianceforge.com/standardized-operating-procedures/ "")
- [NIST CSF Procedures (CSOP)](https://complianceforge.com/product/nist-csf-procedures-csop/)
- [ISO 27002 Procedures (CSOP)](https://complianceforge.com/product/iso-27002-procedures-csop/)
- [NIST 800-53 R5 (moderate) Procedures (CSOP)](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
- [NIST 800-53 R5 (high) Procedures (CSOP)](https://complianceforge.com/procedures-nist-800-53-fedramp-high/)
- [DSP & SCF Version Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
[Browse This Category of Products](https://complianceforge.com/standardized-operating-procedures/ "")
[**Supply Chain Risk Management**](https://complianceforge.com/supply-chain-risk-management/ "")
- [C-SCRM Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
[Browse This Category of Products](https://complianceforge.com/supply-chain-risk-management/ "")
[**NIST 800-171 Compliance**](https://complianceforge.com/nist-800-171-cmmc-policy-templates/ "")
- [NIST 800-171 Compliance Program (NCP): CMMC Level 2](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [NIST 800-171 System Security Plan (SSP) Template](https://complianceforge.com/product/nist-800-171-system-security-plan-ssp-poam-template/)
[Browse This Category of Products](https://complianceforge.com/nist-800-171-cmmc-policy-templates/ "")
[**Risk Management**](https://complianceforge.com/digital-cybersecurity-risk-management/ "")
- [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
- [Cybersecurity Risk Assessment (CRA) Template](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
- [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
[Browse This Category of Products](https://complianceforge.com/digital-cybersecurity-risk-management/ "")
[**Data Protection (Privacy) & Secure Engineering**](https://complianceforge.com/data-protection-privacy-secure-engineering "")
- [Data Privacy Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/)
- [Secure Engineering & Data Privacy (SEDP) Program](https://complianceforge.com/product/security-by-design-privacy-by-design/)
- [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
[Browse This Category of Products](https://complianceforge.com/data-protection-privacy-secure-engineering "")
[**Vulnerability & Patch Management**](https://complianceforge.com/digital-cybersecurity-vulnerability-patch-management/ "")
- [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
[Browse This Category of Products](https://complianceforge.com/digital-cybersecurity-vulnerability-patch-management/ "")
[**Incident Response**](https://complianceforge.com/digital-cybersecurity-incident-response-program-documentation/ "")
- [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
- [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
[Browse This Category of Products](https://complianceforge.com/digital-cybersecurity-incident-response-program-documentation/ "")
[**PCI DSS Compliance**](https://complianceforge.com/pci-dss-cybersecurity-compliance-policies-standards "")
- [SAQ A - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/pci-dss-v4-saq-a)
- [SAQ A-EP - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
- [SAQ B - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
- [SAQ B-IP - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
- [SAQ C - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
- [SAQ C-VT - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
- [SAQ D-Merchant - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
- [SAQ D-Service Provider - PCI DSS v4.0 - Policies & Standards](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
[Browse This Category of Products](https://complianceforge.com/pci-dss-cybersecurity-compliance-policies-standards "")
## ComplianceForge Serves Worldwide Clients Across Nearly Every Industry
#### Financial
- Certified Public Accountants (CPAs)
- Financial Planners &
Wealth Managers
- Banks & Credit Unions
- Bookkeepers
#### Technology Companies
- Hardware Manufacturers
- Consultants
- Software Companies
- Website Developers
- Managed Service Providers
- Auditors
- Cybersecurity
#### Medical
- Hospitals
- Doctors
- Dentists
- Physical Therapists
- Chiropractors
- Medical Billing
- Elder Care Facilities
#### Consultants
- Business Analysts
- Management Consultants
#### Government
- Defense Contractors (DoD)
- Federal Government Contractors
- Federal Government Agencies
- Local Municipalities
- Regional Airports
- Law Enforcement
#### Legal
- Lawyers
- Court Reporters
- Privacy Professionals
#### Real State
- Brokers
- Real Estate Offices
- Title Companies
- Developers
- Property Management
#### Utilities
- Oil & Natural Gas
- Coal
- Electric
- Nuclear
#### Construction & Manufacturing
- Commercial
- Architects
- Retail Products
- Fabrication
- Firearms Industry
#### Hospitality & Food Services
- Hotels / Resorts
- Restaurants
- Casinos / Gaming
- Coffee Shops
#### Retail (B&M) & Services
- Health Clubs / Gyms
- Credit Monitoring / ID Theft
- Janitorial
- Human Resources / Recruiting
#### Non-Profits & Associations
- Chambers of Commerce
- Clubs
- Non-Profits
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
compliance forge, compliance documents, complianceforge
## Cybersecurity Partner Solutions
[Skip to main content](https://complianceforge.com/partners/#main-content)
# Strategic Partners
At ComplianceForge, we are often asked for referrals for subject matter experts who can help with their unique needs. We've put together a list of strategic partners who can help you with your cybersecurity, privacy and other security needs.
## **Cybersecurity Consulting Services**
| | |
| --- | --- |
| [](https://www.howtogrc.com/scf "How To GRC")
**How To GRC**
+1-907-299-7775
[https://howtogrc.com](https://howtogrc.com/)
learn@howtogrc.com | **HowToGRC** has extensive experience implementing and tailoring ComplianceForge products. HowToGRC is a cybersecurity firm focused on designing and implementing cost-effective and scalable Secure Control Framework (SCF) based security programs.
**HowToGRC offers the following services:**
- Tailoring & implementation consulting services for ComplianceForge products (e.g., DSP, CDPP, CSOP, etc.).
- Governance, Risk & Compliance (GRC) platform integration.
- Developing a tailored cybersecurity program.
- Secure Controls Framework (SCF) consulting.
- Capability maturity assessments. |
| [****](https://securitywaypoint.com/ "SecurityWaypoint")
**SecurityWaypoint**
+1-800-289-3740
[https://securitywaypoint.com](https://securitywaypoint.com/ "SecurityWaypoint")
connect@securitywaypoint.com | **SecurityWaypoint** has extensive experience implementing and tailoring ComplianceForge products. SecurityWaypoint is a specialized cybersecurity consulting company that focuses on the compliance and governance aspects of your cybersecurity needs. SecurityWaypoint provides vCISO services and can help organizations implement NIST 800-171 & CMMC 2.0 requirements. Security doesn't have to be hard, let SecurityWaypoint do the work for you.
**SecurityWaypoint offers the following services:**
- Tailoring & implementation consulting services for ComplianceForge products (e.g., DSP, CDPP, CSOP, etc.).
- NIST 800-171 / CMMC 2.0 gap assessments utilizing the Secure Controls Framework (SCF).
- CMMC 2.0 Level 1 & Level 2 program and process implementation packages.
- Cybersecurity business planning services (CISO-level business plan).
- Risk assessments.
- System Security Plan (SSP) & Plan of Action & Milestones (POA&M) development.
- Secure Controls Framework (SCF) consulting. |
| [](https://www.steelroot.us/ "Steel Root")
**Steel Root**
+1-978-312-7668
[https://www.steelroot.us](https://www.steelroot.us/ "Steel Root")
info@steelroot.us | **Steel Root** is an IT Managed Services Provider (MSP) that specializes in helping companies in the U.S. Defense Industrial Base (DIB) implement and manage security requirements under DFARS, CMMC, and other federal standards.
Key elements of the Steel Root approach:
- Steel Root offers a reference architecture for CMMC that allows companies to effectively scope out technical debt and accelerate compliance timelines. The system design can be deployed as an enclave or across the entire organization.
- The Steel Root reference architecture is a set of systems, configuration baselines, and tools — built on the Microsoft Government cloud and using zero trust architecture principles — that is purpose built for meeting the CUI safeguarding requirements in DFARS 252.204-7012 and preparing for CMMC Maturity Level 3.
- Steel Root provides managed cybersecurity and IT services post-implementation, as well as program management coaching and virtual ISSO services to help organizations meet their ongoing responsibilities. |
For CMMC-specific consulting services, the [**CMMC Center of Awesomeness (CMMC-COA)**](https://www.cmmc-coa.com/ "CMMC Center of Awesomeness (CMMC-COA)") has a list of "CMMC Practitioners" that is a good place to start - [https://www.cmmc-coa.com/cmmc-practitioners](https://www.cmmc-coa.com/cmmc-practitioners "CMMC Practitioners")
## Governance, Risk & Compliance (GRC) & Integrated Risk Management (IRM) Platforms
| | |
| --- | --- |
| [](https://scfconnect.com/ "https://scfconnect.com/")
**SCF Connect**
[https://www.scfconnect.com](https://scfconnect.com/ "https://scfconnect.com/")
info@scfconnect.com | **SCF Connect** is a GRC platform that takes the guesswork out of operationalizing the Secure Controls Framework (SCF). SCF Connect was built to natively support the SCF and is designed to integrate with ComplianceForge's Digital Security Program (DSP) and Cybersecurity Operating Procedures (CSOP).
- SCF Connect is affordable, starting at $200 / month.
- Designed to perform SCF Conformity Assessment Program (CAP) assessments.
- Consultant and auditor / assessor portals. |
| | |
| --- | --- |
| [](https://ignyteplatform.com/)
**Ignyte Assurance Platform**
+1-833-446-9831
[https://www.ignyteplatform.com](https://www.ignyteplatform.com/ "Ignyte Assurance Platform")
info@ignyteplatform.com | **Ignyte Assurance Platform** is a leader in collaborative security and integrated GRC solutions for global corporations. For corporate risk and compliance officers who depend heavily on the protection of their resources, Ignyte is the ultimate translation engine for simplifying compliance across regulations, standards and guidelines.
- The Ignyte platform is used by leading corporations in diverse industries, such as Healthcare, Defense, and Technology.
- Ignyte operationalizes compliance for many organizations through the use of the SCF controls and can be used to facilitate a SCF Certification, based on the [SCF Information Assurance Program (IAP):](https://www.securecontrolsframework.com/scf-iap "SCF Information Assurance Program (IAP)")
- The IAP program leverages the SCF controls and is designed to help organizations quickly get up to speed on completing information assurance tasks; and
- Ignyte helps organizations scale these tasks to make audit-preparation and audits much more efficient. |
| | |
| --- | --- |
| 
**LogicGate**
+1-312-279-2775
[https://www.logicgate.com](https://www.logicgate.com/ "LogicGate")
sales@logicgate.com | **LogicGate** utilizes the SCF to define how we map controls between the standards and regulations which are included as part of our core content repository.
- LogicGate's flexible data mapping capabilities allow users to easily view relationships between these controls, as well as between other critical data objects, such as risks, assessments, evidence, policies, and assets. Through these relationships, risk teams can perform an assessment on one control framework and then easily determine the compliance status of a mapped control framework, helping to reduce the amount of time and effort spent by teams needing to ask for the same evidence or attestations over time.
- The database technology that LogicGate is built on also enables organizations to easily adjust relationships between controls and other items as regulatory requirements and standards change. |
| | |
| --- | --- |
| [](https://www.ostendio.com/)
**Ostendio**
+1-877-668-5658
[https://www.ostendio.com](https://www.ostendio.com/ "Ostendio")
info@ostendio.com | **Ostendio** My Virtual Compliance Manager (MyVCM) is a cloud-based GRC/IRM platform that:
- Helps organizations understand what they need to do to build their security and risk management program;
- Operates the program across the entire organization on a day by day basis; and
- Makes it simple to demonstrate compliance across over 100 laws, regulations and industry standards, ensuring the organization is always audit ready.
- Fully integrates the SCF's controls and allows organizations to easily compare their security program against over 100 security and privacy frameworks by simply mapping the controls necessary for any additional standard or regulation:
- Everyone in the company can log in and use the platform, which makes MyVCM's licensing model the most cost-effective GRC/IRM solution for multiple-user involvement.
- It offers a "single-pane-of-glass" reporting, automated workflow management, and integration with some of the world’s leading platforms including OneLogin, Microsoft and Google. |
| | |
| --- | --- |
| 
**Reciprocity (ZenGRC)**
+1-877-440-7971
[https://www.reciprocitylabs.com](https://www.reciprocitylabs.com/ "Reciprocity (ZenGRC)")
engage@reciprocitylabs.com | **Reciprocity** ZenGRC is a cloud-based GRC/IRM platform that utilizes the SCF as an available set of cybersecurity and privacy controls.
- ZenGRC is an easy-to-use, enterprise-grade GRC/IRM solution for compliance and risk management that offers businesses efficient control tracking, testing, and enforcement.
- ZenGRC streamlines control management to provide tangible value because it speeds up audit and vendor management tracking and consolidates risk mitigation tasks.
- Clients can be up and running in as little as 6-8 weeks, saving time for compliance teams to focus on security work while saving time on mundane implementation tasks. |
## Risk Management Solutions
| | |
| --- | --- |
| [](https://www.simplerisk.com/)
**SimpleRisk**
+1-650-619-8669
[https://www.simplerisk.com](https://www.simplerisk.com/ "SimpleRisk")
sales@simplerisk.com | **SimpleRisk** is a free and open source GRC tool that leverages the SCF, giving our customers what they've been asking for - an easy way to load up and utilize controls for various compliance frameworks.
- The SCF is a free downloadable "extra" within SimpleRisk. Customers can go to the Configure > Register & Upgrade menu in any registered SimpleRisk instance and click "Download" to download and then install the SCF in that instance.
- Within SimpleRisk, clients are presented with a list of the frameworks represented with the SCF and the option to select which ones apply to their organization. Applicable controls are automatically imported into the Governance functionality of SimpleRisk with mappings to their associated frameworks. From there, customers can document exceptions, perform testing, and use the controls to plan mitigations for their risks. |
## Technology Solutions
| | |
| --- | --- |
| [](https://www.cimcor.com/ "https://www.cimcor.com/")
**CIMCOR**
+1-219-736-4400
[https://www.cimcor.com](https://www.cimcor.com/ "Cimcor")
info@cimcor.com | The CimTrak Integrity Suite, developed by **Cimcor**, is a robust security, compliance, and integrity management tool that offers real-time integrity monitoring, assessment, and remediation of critical IT assets. Those capabilities include system hardening, configuration management, change management, change prevention, roll-back and remediation, allow-listing, file reputation, STIX/TAXII feeds, and a built-in ticketing system.
Examples of crosswalk functionality of CimTrak to security/compliance frameworks:
- NIST 800-53: 276 of the 1,189 controls;
- 800-171 R2: 33 of the 110 controls;
- 800-171 R3: 40 of the 95 controls;
- PCI DSS v4: 141 of the 280 controls (including Appendix A1, A3, and A3);
- CIS v8: 43 of the 153 controls;
- SWIFT: 19 of the 31 controls;
- FFIEC: 124 of the 494 controls;
- TSC (SOC2): 81 of the 319 controls;
- And more… |
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[compliance solutions risk management bundles](https://complianceforge.com/compliance-solutions/risk-management-bundles/) [scf risk management model. free guide to risk management](https://complianceforge.com/scf/cybersecurity-data-privacy-risk-management-model/)
## Documentation Errata Updates
[Skip to main content](https://complianceforge.com/errata/#main-content)
# Errata
Documentation version changes (e.g. erratas) are published with their applicable products. This enables you to update your documentation to their latest versions according to your company's internal change control processes in an organized and efficient manner.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Privacy Practices Overview
[Skip to main content](https://complianceforge.com/privacy/#main-content)
# Privacy
## Privacy Notice
**Last Updated: 2023-07-24**
Compliance Forge, LLC (us/we) is committed to transparency for how we collect, use, share and protect the Personal Data ( **PD**) and/or Sensitive Personal Data ( **sPD**) under our control. We strive to honor the confidentiality of our customers. We want customers to have confidence in their use of our products and services that their PD / sPD is adequately protected.
This Privacy Notice is subject to change. We update this notice periodically to comply with evolving statutory and regulatory requirements. When we make changes to the Privacy Notice, we revise the Last Updated date on the upper left corner of this page.
Please read this notice carefully to understand what we do with PD / sPD, since it is the consumer’s (you/your) due diligence obligation to review this Privacy Notice and contact us if you have questions on this topic. If you have any questions concerning our Privacy Notice, please contact us by email at [support@complianceforge.com](mailto:support@complianceforge.com "ComplianceForge Privacy Notice Contact Form") and include your name, telephone number and email address so that we can contact you; or phone us at 1-855-205-8437.
### Who We Are
Compliance Forge, LLC (ComplianceForge) is a US-based Limited Liability Company (LLC) that is headquartered in Sheridan, Wyoming.
### Protecting Your Data (Data Security)
We are committed to ensuring that your PD / sPD is adequately protected. In order to prevent unauthorized access or disclosure, we put in place suitable administrative, physical and technical controls to safeguard the PD / sPD under our control. To protect the confidentiality and integrity of your PD / sPD, we use physical and cybersecurity measures that comply with applicable statutory, regulatory and contractual obligations.
### Transparent Privacy Practices
We are committed to transparency about how your PD / sPD is captured, processed, stored, transmitted and/or shared. The types of PD / sPD collected and shared depends on the interaction you have with us. Any PD / sPD is what you voluntarily provided to ComplianceForge, directly by you or through cookies on your system(s).
ComplianceForge collects relevant PD / sPD when a data subject:
- Visits ComplianceForge website (e.g., cookies);
- Contacts ComplianceForge to ask questions about products/services;
- Creates an account on ComplianceForge website;
- Requests information about a product or service;
- Purchases a product or service;
- Registers as a participant in one of our events (online or in-person); and/or
- Completes a survey, contest or sweepstakes or other promotion.
PD may include the data subject’s:
- Name;
- Billing address;
- Shipping /or mailing address;
- Telephone number;
- Email address;
- Order comments (e.g., notes and/or preferences);
- Purchase history; and
- Other information relevant to order fulfilment, customer surveys and/or offers.
If payment is made with a payment card (e.g., credit card or debit card), sPD includes the data subject’s:
- Payment card account number;
- Payment card expiration date; and
- Payment card Card Verification Value (CVV).
If payment is made with check, ACH or wire transfer, sPD may include the data subject’s:
- Bank name;
- Bank account name;
- Bank account number; and
- Bank routing number.
ComplianceForge’s products and services are not marketed to minors. We do not knowingly collect PD / sPD from children under 13.
### How We Use Cookies & Analytics
A cookie is a small file which asks permission to be placed on your computer's hard drive. Once you agree, the file is added and the cookie helps analyze web traffic or lets you know when you visit a particular site. Cookies allow web applications to respond to you as an individual. The web application can tailor its operations to your needs, likes and dislikes by gathering and remembering information about your preferences.
Cookies also allow us to personalize your experience, advertise to you on other websites and speed the check-out process. ComplianceForge may collect the following analytics-related information from your computer and mobile devices where allowed by individual browsers and/or operating systems, that includes, but is not limited to:
- Unique device identifiers (e.g., MAC and IP addresses);
- Browser type, version, language and display/screen settings;
- Information about how you use and interact with ComplianceForge's website(s) (e.g., activities on pages visited, links clicked or unique and measurable patterns such as keystrokes, mouse clicks and movements, swipes and gestures);
- Responses to advertisements on websites where ComplianceForge advertises; and/or
- Search engine referrals.
### Data Sharing
If you limit sharing PD / sPD with ComplianceForge, it may affect our ability to transact business processes (e.g., create an account, communicate with ComplianceForge and/or purchase products and/or services).
ComplianceForge may share relevant PD / sPD with third-parties in these cases:
- The ComplianceForge website is hosted on BigCommerce, which is an ecommerce platform, so relevant PD may be visible to BigCommerce technical support personnel.
- Customer contact information and order history-related PD are shared with a third-party Customer Resource Management (CRM) solution for customer service functions (e.g., newsletters, email marketing, product renewal notifications, etc.).
- Payment card-related sPD is collected, stored, processed and transmitted in accordance with the Payment Card Industry Data Security Standard (PCI DSS) for how payment card data is captured via the ComplianceForge website (BigCommerce hosted store) and securely transmitted to the selected Merchant Services Provider (MSP) (e.g., Authorize.net or Stripe). ComplianceForge does not store any payment card data and is only retained by the MSP for payment processing purposes.
- Business support activities (e.g., accounts receivable, internal financial record keeping (e.g., bookkeeping), website maintenance and improvements, etc.).
- Government Agencies as required by laws and regulations (e.g., court order).
**Links To Other Websites**
Our website contains links to other websites of interest. However, once you follow any links to leave our site, we do not have any control over that other website. Therefore, we are not responsible for the protection mechanisms and privacy of any PD / sPD which you provide while visiting such sites and such sites are not governed by this Privacy Notice . You should exercise caution and look at the Privacy Notice applicable any third-party websites.
### Controlling The Use of Your Personal Data
If you created an account, you can login and update your relevant PD. You can also contact ComplianceForge to have your email address removed from our mailing list. If you previously agreed to us using your PD for direct marketing purposes, you may change your mind at any time by writing to or emailing us at [support@complianceforge.com](mailto:support@complianceforge.com "ComplianceForge Privacy Notice Contact Form") to manage your preferences. Our marketing emails also contain unsubscribe links for self-service unsubscribing actions.
You may request details of PD / sPD which we hold about you. A small fee may be payable to cover administrative costs associated with processing the request. If you would like a copy of the information held on you please write to 30 N Gould St, Suite 9141, Sheridan, Wyoming, 82801 and state your request.
If you believe that any information we are holding on you is incorrect or incomplete, please contact us as soon as possible. We will promptly correct any information found to be incorrect.
There are known methods that spammers can use to hide their identity by using other people's email address to send out emails. If you have any question about the genuineness of an email you receive that appears to be from ComplianceForge, contact us to verify the legitimacy of the email and do not furnish PD / sPD in response to the email in question.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Value Added Reseller Program
[Skip to main content](https://complianceforge.com/var#main-content)
# Resellers
**Value Added Reseller (VAR) Program**
As a VAR, you can receive a discounted purchase price on ComplianceForge products that you then resell to your clients. Our VARs tend to focus on the consulting side of assisting their clients with the implement the security policies, standards, procedures, etc. so it is a very beneficial arrangement between ComplianceForge and VARs. We currently partner with select IT service providers across the US for our VAR program. If this sounds interesting to you, please email [support@complianceforge.com](mailto:support@complianceforge.com) and we can send you a VAR application and pricing information.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## ComplianceForge FAQ
[Skip to main content](https://complianceforge.com/faq/#main-content)
# Frequently Asked Questions (FAQ)
If you are unable to find an answer to your question in the following FAQs, please [contact us](https://complianceforge.com/contact-us/ "Contact Us") and we will respond as soon as we can.
## What is the order process?
## How will I receive my order?
We manually process our orders to customize the documentation and email you the finished documentation either as a secure download link or as an attachment (depends on the size of the order). The exception is with the SSP product, since there is no additional customization needed and that is available as an electronic download. Generally, we process the orders the same day they are received. However, depending on the volume of orders, it may be processed the following business day.
## How can I get a quote?
If you need a formal quote, please use the “Add To Quote” feature on the product page. This will allow us to generate a formal quote for you.
## Can I pay with a Purchase Order (PO) or an offline invoice?
Yes. In addition to accepting all major credit cards, ComplianceForge can process orders through offline invoicing. It is a simple process where you place the order online and we email you the invoice. However, due to the unfortunate tendency of many companies to process payments slowly (even backed up by a Purchase Order (PO)), we instituted the practice of waiting for payment before orders are processed.
- To place an order, select the Invoice / Purchase Order (PO) payment option during the checkout process, since that ensures the order is in the system and that we can generate an invoice for you.
- You can reference the PO# in the comments section of the order checkout processes, which will ensure the PO# is included on the invoice.
- You will receive a separate email with the invoice that contains check or ACH payment instructions
If you need a formal quote, please use the “Add To Quote” feature on the product page. This will allow us to generate a formal quote for you.
## Are the products editable?
Yes. Our products are delivered in editable Microsoft Office formats (e.g., Word, Excel, PowerPoint, Visio, etc.). These are editable documents that you are able to modify for your organization's unique needs. There is no software to install - it is just templatized documentation that you can edit for your needs.
## How are product updates handled?
We put together an entire page to help discuss how products are updated and how customers can be notified of changes - [FAQ - Product Updates](https://complianceforge.com/faq/product-updates "FAQ - Product Updates")
## Is this software or a subscription service?
Neither. Our products are a one-time purchase and no software needs to be installed. However, the Digital Security Program (DSP) and NIST 800-171 Compliance Program (NCP) products do include one year of updates. Our product update process is covered here - [FAQ - Product Updates](https://complianceforge.com/faq/product-updates "FAQ - Product Updates")
## How quickly can I receive my order?
Turn around time is generally the same business day for orders placed by credit card, but we give a buffer of 1-2 business days. Upon completing the online transaction, you will receive a confirmation e-mail. The completed product will be delivered to the e-mail address used to register at the time of purchase. If you pay by PO/Invoice, we do not process the order until payment is received.
## What is the refund policy?
Due to the Intellectual Property (IP) nature of the products offered by ComplianceForge, we do not offer refunds once the product has been delivered to a client. ComplianceForge stands behind its products and services. The quality of the work is equivalent to what is found in a Fortune 500 (enterprise-class) environment and the solutions provided by ComplianceForge are based on industry-recognized leading practices - with many satisfied clients.
## Can I get a discount?
Our discounts are built into our bundles, where we offer discounts up to 45% for certain bundles. We do not "grandfather" discounts on products that are purchased outside of a bundle (e.g., you buy one product this week and come back next week to buy other products). Discounts are only available at the time of purchase with two or more products as part of that purchase.
## What is the difference between the DSP & CDPP products?
We put together an entire page to help discuss the differences between the Digital Security Program (DSP) and the Cybersecurity & Data Protection Program (CDPP) - [DSP vs CDPP.](https://complianceforge.com/faq/dsp-vs-wisp "DSP vs CDPP")
\+ How are the Digital Security Program (DSP) and Cybersecurity & Data Protection Program (CDPP) a "customized" set of policies?
Based on our extensive experience consulting with businesses on Information Security projects and documentation, we developed a very robust template of policies, procedures, standards, and guidelines that businesses require to meet compliance requirements. Since most compliance requirements are based on industry-recognized “best practices” and that standards are openly published, we were able to develop a modular approach to policies and create a customized template framework. This allows us to efficiently customize the policies for our clients.
Our solution is approximately 1/10th the cost of hiring a dedicated cybersecurity consultant to write policies for your company. The irony is that those cybersecurity consultants use the same basis of working off templates for their clients. The end result is the same that you get customized Information Security policies for an extremely affordable cost.
## How is this different from the free templates on the Internet?
You get what you pay for. Free templates are generally of little value, whereas ComplianceForge products are high-quality, professionally-written solutions for your compliance needs. With a lot of template sites, options are given to pick and choose policies. Realistically, unless you are trained in cybersecurity and legitimately know what components are required to meet compliance minimums with a law or regulation, you are assuming a significant liability. Without expertise, it is a situation of “the blind leading the blind” in selecting and implementing policies.
This is where our guide on [NIST CSF vs ISO 27001/2 vs NIST 800-53 vs SCF](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf "NIST CSF vs ISO 27001/2 vs NIST 800-53 vs SCF") is a very useful tool to help identify the most appropriate solution for your specific needs.
## Why don't I save money and create my own documentation?
How much is your time worth and how long would it take you to actually research and write comparable documentation? We invested thousands of hours in the creation of our documentation, so that you can focus on what you do best, which is running your company. For what we charge for our products, it is a fantastic deal - it is as simple as that. The product pages contain cost savings estimates so that you can see for yourself what a reasonable cost would be to write it yourself or hire someone to write it for you.
The expertise that has been drawn upon to develop ComplianceForge documentation covers over three decades of experience in mitigating risk for technical, operational, and physical threats. You are buying expertise. With a lot of lesser options on the Internet, you get what you pay for and that is not much. When it comes to the liability facing your company, it would be careless to rely on amateur solutions. You use a CPA for your finances. You see a doctor for your medical care. Why would you rely on an amateur solution for your cybersecurity documentation needs?
## Will the documentation have your logo or mine?
If you have a logo, have it ready at the time of purchase since you will be prompted to upload it. The cover page of the documentation will have your company's logo prominently displayed. The rest of the document will have your company name throughout, so anyone reading the document will get the feel it was was custom created and tailored to your company.
If you do not have a logo, that is no problem. We just leave the logo off. The documentation will still look very professional, even without your logo on the front page.
## What do I need to provide as part of the order process?
We would like to have a high-resolution company logo file (JPG, PNG, GIF or BMP), but we do need your company’s official name and your company’s common name. You will be prompted to upload this information prior to payment.
Examples of "official" and "common" names for businesses: Official Name (Common Name)
- Beaverton Metropolitan Chamber of Commerce (Beaverton Chamber)
- City of Beaver Springs (COBS)
- Sonoma Technology Consulting, LLC (SonomaTech)
- BlackHat Consultants, LLC (BlackHat)
## Can I get additional customization?
Yes. ComplianceForge, or its partners, can offer professional services to provide additional customization. However, it is added cost involved due to labor incurred. Please review the [Partners](https://complianceforge.com/partners/ "https://complianceforge.com/partners/") page for consultants who you want want to work with for any professional services.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Compliance Blog
[Skip to main content](https://complianceforge.com/blog/#main-content)
# Blog
[](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Maturity Model Certification (CMMC), the area of supply chain security practices is unfamiliar territory,
… [read more](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
[](https://complianceforge.com/blog/secure-software-development-attestation/)
Can you tell the difference in these secure software development attestation forms? There isn't one - they all require attestation against Executive Order 14028 (EO 14028) requirements.
The CISA Secu
… [read more](https://complianceforge.com/blog/secure-software-development-attestation/)
[](https://complianceforge.com/blog/nist-800171-r3-odps/)
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-Defined Parameters (ODP)! The NIST 800-171 Compliance Program (NCP) has been updated to include the
… [read more](https://complianceforge.com/blog/nist-800171-r3-odps/)
[](https://complianceforge.com/blog/scf-training-certifications/)
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SCF) and it is exciting to see SCF-based training options and certifications are now live. This h
… [read more](https://complianceforge.com/blog/scf-training-certifications/)
[](https://complianceforge.com/blog/gsa-oasis-j3-cscrm-deliverables/)
Need GSA OASIS+ J-3 C-SCRM Deliverables?
The US Government's General Services Administration (GSA) has the One Acquisition Solution for Integrated Services (OASIS+) that is a new Indefinite Delivery,
… [read more](https://complianceforge.com/blog/gsa-oasis-j3-cscrm-deliverables/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[gsa oasis+ j](https://complianceforge.com/blog/gsa-oasis-j3-cscrm-deliverables/) [your cmmc requirements guide](https://complianceforge.com/blog/your-cmmc-requirements-guide/)
## Verutus Brand Products
[Skip to main content](https://complianceforge.com/verutus/#main-content)

# Verutus
There are no products listed under this brand.
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Contact ComplianceForge
[Skip to main content](https://complianceforge.com/contact-us/#main-content)
# Contact ComplianceForge
How can we help? We're happy to answer questions you have about our products or services, since we know cybersecurity & privacy compliance can be overwhelming. We want to make sure our clients pick the right solution for their specific needs, so we understand this sometimes necessitates a brief call to help answer any questions you may have.
We generally respond to emails within a few hours, since we strive to provide the best customer service we can. If you need a quick answer to your questions, you can also give us a call at **+1-855-205-8437** between 7am-5pm PST.
Full Name
Phone Number
Email Address
Required
Company Name
Details
Required
Please answer the question below for additional verification.
Required
What is 1 + 16?
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[complianceforge](https://complianceforge.com/cart.php) [complianceforge](https://complianceforge.com/login.php)
reCAPTCHA
## Digital Security Program Subscription
[Skip to main content](https://complianceforge.com/subscription/dsp#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/221/1506/complianceforge-subscription-digital-security-program-dsp__73790.1740599307.jpg?c=2)
No reviews yet
$1,700.00
(You save)
# Subscription - Digital Security Program (DSP)
SKU:P51-S-DSPUPC:692878857222Availability:Email Delivery Within 1-2 Business Days
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Subscribe%20Now%3A%20Digital%20Security%20Program%20by%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp&title=Subscribe%20Now%3A%20Digital%20Security%20Program%20by%20ComplianceForge&summary=Subscribe%20Now%3A%20Digital%20Security%20Program%20by%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp "Linkedin")
## Digital Security Program (DSP) - Annual Subscription for Product Updates
This is a subscription service for existing [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/) clients to obtain product updates. Due to the dynamic nature of the DSP and the Secure Controls Framework (SCF), the DSP continues to be updated (nearly a quarterly basis) as new laws, regulations and other frameworks are added. This is a cost-effective method for existing DSP clients to obtain the most current version of the DSP and SCF.
- The DSP subscription service entitles the purchaser to 12-months of updates to the DSP, including both the Word and Excel (mappings) documents.
- The method of delivery of the DSP is email delivery. It includes an errata that describes the additions/changes in the latest version of the documentation.
- This does not include updates to other ComplianceForge products, as those are governed by the [traditional product update process](https://complianceforge.com/faq/product-updates).
Upon payment, you will receive an email containing a ShareFile link with the latest version of the DSP.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[renew your dsp & csop subscription for cybersecurity success](https://complianceforge.com/subscription/dsp-csop) [dsp bundle 2: enhanced digital security documentation](https://complianceforge.com/bundle/dsp-bundle-2) [dsp bundle 3: robust digital security documentation](https://complianceforge.com/bundle/dsp-bundle-3) [renew your csop (dsp version) subscription \| complianceforge](https://complianceforge.com/subscription/csop) [product comprehensive digital security program](https://complianceforge.com/product/comprehensive-digital-security-program/) [renew your nist 800](https://complianceforge.com/subscription/ncp) [blog tag digital security program](https://complianceforge.com/blog/tag/Digital+Security+Program) [compare dsp vs cdpp: find your ideal cybersecurity program](https://complianceforge.com/faq/dsp-vs-cdpp) [dsp version 2022.3 release](https://complianceforge.com/blog/dsp-version-20223-release/)
reCAPTCHA
## Cybersecurity Compliance Guidance
[Skip to main content](https://complianceforge.com/start-here/#main-content)

# ComplianceForge Documentation - Where Do I Start?
There is a lot of information on the ComplianceForge website. We publish a considerable amount of guidance documents to help our clients identify what is most appropriate for them.
From a "start here" perspective, baselining your level of understanding is critical so that you can make "apples to apples" comparisons from an objective perspective:
- [**NIST CSF vs ISO 27001 / 27002 vs NIST 800-53 vs NIST 800-171 vs SCF**](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf "NIST CSF vs ISO 27001 / 27002 vs NIST 800-53 vs NIST 800-171 vs SCF"). Understand the differences between NIST CSF, ISO 27001/27002, NIST 800-53, NIST 800-171 and the Secure Controls Framework. We put together a useful guide on that topic.
- **[Policies vs Standards vs Procedures](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure "Policies vs Standards vs Procedures")**. Gain an insight into the differences between policies, standards, controls, procedures and other documentation components. The Hierarchical Cybersecurity Governance Framework (HCGF) puts those concepts into a "swim lane" diagram to make it easy to understand the relationships and the authoritative definitions from sources like ISO, NIST, ISACA and AICPA.
- [**Statutory vs Regulatory vs Contractual Obligations**](https://complianceforge.com/free-guides/statutory-vs-regulatory-vs-contractual-compliance "Statutory vs Regulatory vs Contractual Cybersecurity Compliance Obligations"). Prioritize your "must have" vs "nice to have" requirements by understanding statutory, regulatory and contractual compliance.
- [**Strategic vs Operational vs Tactical**](https://complianceforge.com/free-guides/strategy-vs-operations-vs-tactics "Strategic vs Operational vs Tactical"). From a scoping perspective, understand strategic vs operational vs tactical considerations.
- [**Threats vs Vulnerabilities vs Risks**](https://complianceforge.com/free-guides/threat-vs-vulnerability-vs-risk "Threats vs Vulnerabilities vs Risks"). Understand the differences between threats, vulnerabilities and risks to appreciate how controls are central to your cybersecurity program.
## Defense Contractor-Specific Guidance
We recognize that the US Defense Industrial Base (DIB) has a lot of unique cybersecurity challenges. Therefore, we put together some helpful information that is specific to the DIB:
- [**NIST 800-171 Compliance - Where Do I Start?**](https://complianceforge.com/nist-800-171/nist-800-171-cmmc "NIST 800-171 Compliance - Where Do I Start?")
- [**What Is Controlled Unclassified Information (CUI)?**](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret "What Is Controlled Unclassified Information (CUI)?")
- [**ITAR vs EAR vs FAR vs DFARS (CUI & CMMC)**](https://complianceforge.com/nist-800-171/itar-vs-ear-vs-far-vs-dfars-cui-cmmc/ "ITAR vs EAR vs FAR vs DFARS (CUI & CMMC)")
## Product-Related Questions
- [What are the differences between the Digital Security Program (DSP) and Cybersecurity & Data Protection Program (CDPP)?](https://complianceforge.com/faq/dsp-vs-wisp)
- [Do you offer multiple company discounts?](https://complianceforge.com/faq/multiple-company-discount)(e.g., subsidiaries or franchises)
- [What industries do you serve? What client references do you have?](https://complianceforge.com/faq/industries-served)
- [How are product updates handled?](https://complianceforge.com/faq/product-updates)
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Product Updates Overview
[Skip to main content](https://complianceforge.com/product-updates/#main-content)
# ComplianceForge Product Updates
We do offer product updates. However, we do charge for updates/upgrades since it takes our staff time to keep current on evolving requirements and maintain the documentation, so we need to cover our costs so that we can continue to offer these quality products. For minor updates to mapping spreadsheets, we do not charge for those.
## **Cybersecurity Documentation Generally Has A 3-5 Year Shelf Life**
Cybersecurity and data protection practices are a constantly-evolving and this means your documentation needs to be kept current to reflect changes. These changes tend to come from evolving statutory, regulatory or contractual requirements, but documentation changes also come from evolving technologies (e.g., Artificial Intelligence, Zero Trust Architecture, etc.). However, ComplianceForge designed its documentation to help with managing the life cycle of your organization's documentation through a hierarchical model that is easy to update and maintain.
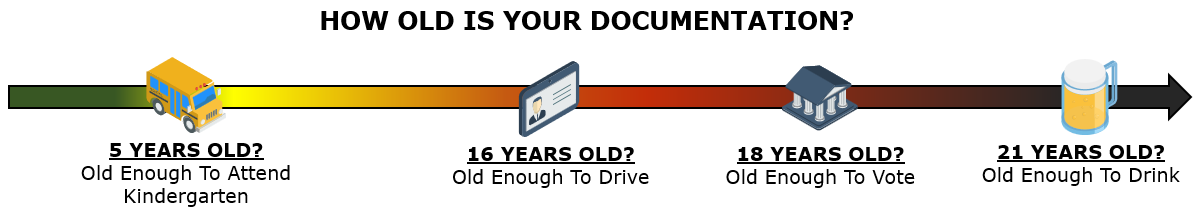
Our documentation is targeted for a 3-5 year life cycle before a major upgrade is needed. A common rule of thumb is that if your documentation is old enough to attend kindergarten, then it is time to do a thorough review and update to ensure it is applicable for your current needs. We have actually helped companies replace documentation that was old enough to drive, old enough to vote and even old enough to drink! Documentation has a shelf life and your Governance, Risk & Compliance (GRC) team is responsible for ensuring your documentation is sufficient for your current and future needs:
- **Policy Lifecycle** \- Policy statements are the most static components of the documentation hierarchy, since policies focus on high-level statements of management intent. Policies should be good for 3-5 years without making changes.
- **Standards Lifecycle** \- Standards are generally static, but change when influenced by a statutory, regulatory or contractual obligation or technology change. Standards can also change when new technologies are introduced. Annual reviews of standards are needed to ensure those are still accurate for your environment, but similar to policies, your standards should be good for a 3-5 year life cycle without making many significant changes.
- **Procedures Lifecycle** \- Procedures are the most dynamic component of your security documentation. Procedures are influenced by your available people, service providers, processes and technologies, so you have to expect procedure documentation to be a "living document" where it requires ongoing attention to keep it current.
Please note that when ComplianceForge product upgrades are sent out, they are not customized to your organization (e.g., logo & company name). The updates come with errata that shows what has changed in the documentation, where you can make the decision if you want to adopt the changes in your existing documentation, since it is expected that your organization has already tailored the original documentation for its specific purposes. It is expected that you would follow your organization's existing documentation change control processes to review and approve changes.
## Upgrade Non-Subscription Products To The Latest Version
Most ComplianceForge products are one-time purchase that do not include updates or free upgrades. The reason for this is that the non-subscription products are designed to be relatively static, since the underlying framework (e.g., best practice) is static, where it may change once every 3-7 years. When new versions are released, we let customers know that they can obtain updated versions at significant discounts.
In an effort to reward existing customers, we have three different tiers of pricing for upgrades for products without subscriptions:
- Within 90 days of purchase - No charge
- Within 365 days of purchase - 25% of current product price
- Beyond 365 days of purchase - 50% of current product price

The method to obtain a product upgrade is very straightforward. Go to the product page and select "add to quote" at the top of the page. In the comments section for the quote, mention that you are requesting a product upgrade. We will then validate your request against your company's orders and apply the appropriate discount for the upgrade.
## Annual Product Update Subscriptions
Only the following four (4) ComplianceForge products have annual product update subscriptions:
| | | | |
| --- | --- | --- | --- |
| [](https://complianceforge.com/subscription/dsp "DSP updates") | [](https://complianceforge.com/subscription/csop "CSOP updates") | [](https://complianceforge.com/subscription/dsp-csop "DSP & CSOP updates") | [](https://complianceforge.com/subscription/ncp "NCP updates") |
## Subscription Eligibility
When a customer purchases any of the products listed above, the first year of product of updates are included from the time of purchase.
Annual subscription updates are available only to clients who purchased a product that offers a subscription.
If a client skips one, or more, years of an annual update subscription, the cost to restart the subscription for one year is 50% of the published price of the product.
## Pricing
### Subscription Pricing: [Digital Security Program](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP) - Upgrade") & [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Procedures (CSOP) - DSP & SCF Version")
Clients who purchase the Digital Security Program (DSP) or DSP version of the Cybersecurity Standardized Operating Procedures (CSOP) can subscribe to product updates. The first year of DSP and CSOP product updates will be included in the purchase of the DSP or CSOP. For subscription renewals for the DSP and the CSOP (DSP version), these are the links to renew:
- [DSP only subscription ($1,700/yr)](https://complianceforge.com/subscription/dsp "Subscription - Digital Security Program (DSP)")
- [CSOP only subscription ($900/yr)](https://complianceforge.com/subscription/csop "Subscription - CSOP (DSP Version)")[DSP Subscription](https://complianceforge.com/subscription/dsp "DSP Subscription")
- [DSP & CSOP subscription ($2,600/yr)](https://complianceforge.com/subscription/dsp-csop "Subscription - DSP & CSOP")
### Subscription Pricing: [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/ "NIST 800-171 R3 Policies, Standards & Procedures")
Clients who purchase the NIST 800-171 Compliance Program (NCP) can subscribe to NCP updates ($950/yr) when the first year of updates expires. The first year of NCP product updates is included in the purchase of the NCP. For subscription renewals for the NCP, here is the link to renew:
- [NCP subscription ($950/yr)](https://complianceforge.com/subscription/ncp "NCP Subscription")
## Browse Our Products
- [](https://complianceforge.com/subscription/dsp-csop)
#### [Subscription - DSP & CSOP](https://complianceforge.com/subscription/dsp-csop)
ComplianceForge
DSP & CSOP - Annual Subscription for Product Updates
This is a subscription service for existing DSP & CSOP clients to obtain product updates. Due to the dynamic nature of the DSP and the Secure Controls Framework (SCF), the DSP...
$2,600.00
[Choose Options](https://complianceforge.com/subscription/dsp-csop)
- [](https://complianceforge.com/subscription/dsp)
#### [Subscription - Digital Security Program (DSP)](https://complianceforge.com/subscription/dsp)
ComplianceForge
Digital Security Program (DSP) - Annual Subscription for Product Updates
This is a subscription service for existing Digital Security Program (DSP) clients to obtain product updates. Due to the dynamic nature of the DSP and the Secure Controls...
$1,700.00
[Choose Options](https://complianceforge.com/subscription/dsp)
- [](https://complianceforge.com/subscription/csop)
#### [Subscription - CSOP (DSP version)](https://complianceforge.com/subscription/csop)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) - Annual Subscription for Product Updates
This is a subscription service for existing clients of the DSP/SCF version of the CSOP to obtain product updates. Due to the dynamic nature of the...
$900.00
[Choose Options](https://complianceforge.com/subscription/csop)
- [](https://complianceforge.com/subscription/ncp)
#### [Subscription - NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/subscription/ncp)
ComplianceForge
NIST 800-171 Compliance Program (NCP) - Annual Subscription for Product Updates
This is a subscription service for existing NIST 800-171 Compliance Program (NCP) clients, who have not skipped one or more years of a subscription, to obtain...
$950.00
[Choose Options](https://complianceforge.com/subscription/ncp)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cost Savings in Security
[Skip to main content](https://complianceforge.com/cost-savings#main-content)
# Security Return on Investment (SROI)
Good Information Security practices are one of the few improvements a company can make that will actually provide a positive Security Return on Investment (SROI). The costs that a business spends on preventative Information Security practices can dramatically reduce expenses throughout the company.
## Cost Savings Benefits
The benefits of Information Security for Small and Medium Businesses (SMBs) are many:
- Decreased IT support costs;
- Less virus outbreaks;
- Less wasted time from opening spam e-mail;
- Reduced downtime from data lost;
- You will be able to prove documented due care and due diligence;
- Documentation can be the difference between being compliant or negligent;
- Insurance will cover data breach costs if you are able to prove you were compliant at the time of the breach;
- Insurance will not cover data breach costs if you were non-compliant at the time of the breach;
- Improved productivity with decreased distractions; and
- Good Information Security policies reduces distractions from common issues:
- Block inappropriate web sites;
- Reduce or limit personal use (wasted time);
- Operations are more efficient with better performing network & computers;
- You can hold employees liable for what they do and fail to do on your network at with company assets;
- Better accountability of assets & resources; and
- Better educated & trained employees.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Documentation Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/#main-content)
# Cybersecurity Best Practices Documentation Templates
The development of cybersecurity and privacy documentation provides evidence of due diligence and due care through defining administrative, technical and physical requirements. Implementing consistent cybersecurity & data protection documentation helps your organization comply with current and evolving statutory, regulatory and contractual obligations associated with protecting the confidentiality, integrity, availability and safety of data and technology assets.
We offer a wide-assortment of cybersecurity policies, standards, procedures and more, since we understand that businesses have unique needs that cannot be met by just one product. While companies want to align with a single cybersecurity framework such as NIST 800-53, ISO 27002 or NIST Cybersecurity Framework, it is getting much more common for companies to have to juggle multiple frameworks and that requires scalable documentation.
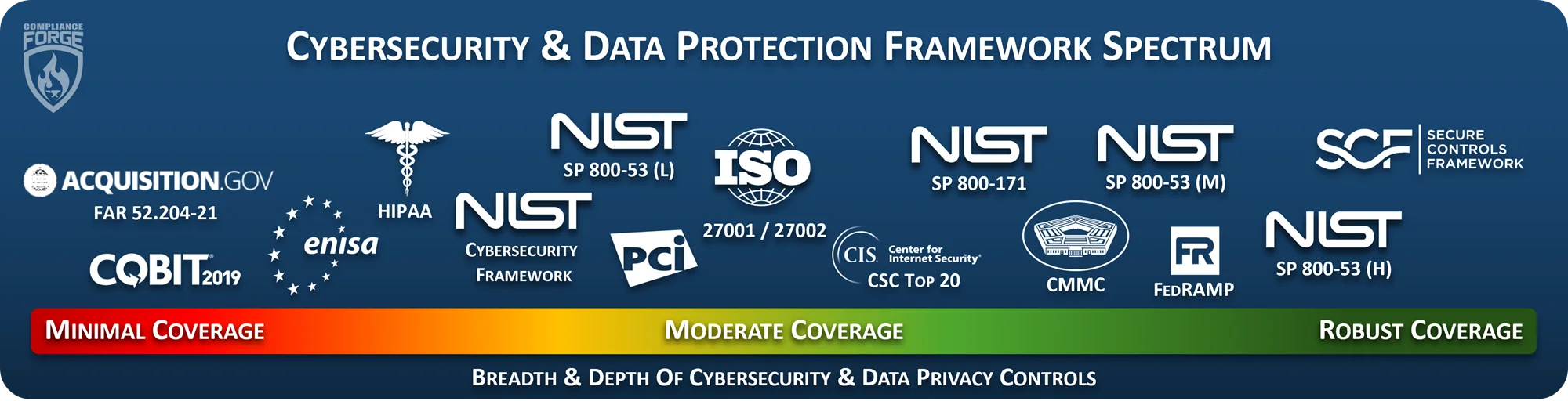
## Concise & Clear Cybersecurity & Privacy Documentation
Effective cybersecurity and data protection is a team effort involving the participation and support of every user that interacts with your company’s data and/or systems, it is a necessity for your company’s cybersecurity & data protection requirements to be made available to all users in a format that they can understand. That means your company must publish those requirements in some manner, generally in either PDF format or published to an internal document management tool (e.g., GRC/IRM, SharePoint, wiki, etc.). Regardless of the format in which you deliver your documentation to end users, our goal is to make that process as efficient, cost-effective and scalable, as possible.
## We Know How To Write Cybersecurity & Privacy Documentation - Scalable, Comprehensive & Efficient
We leverage the **[Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")** to take a comprehensive view towards the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care. This framework addresses the interconnectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. This approach works well with any cybersecurity framework to help any organization, regardless of industry, to get and stay both secure and compliant.
ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following downloadable diagram that demonstrates the unique nature of each documentation component that is expected to exist as part of a cybersecurity and privacy program. You can click on the image below to better understand how we write our documentation to link from policies all the way down to metrics.
[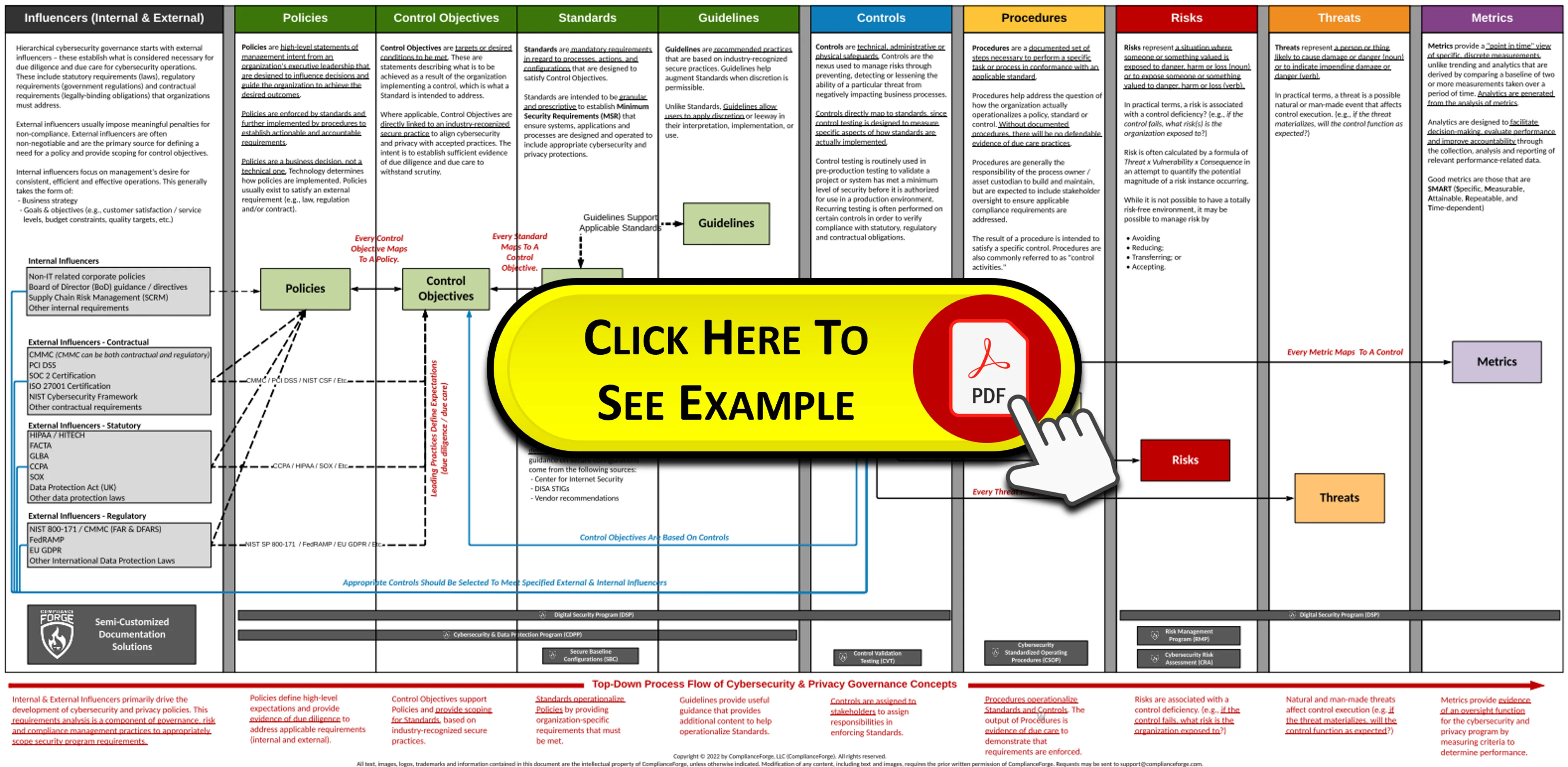](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "complianceforge reference model - hierarchical cybersecurity governance framework")
## Establishing Context For Cybersecurity & Privacy Documentation
Your cybersecurity & data protection documentation is meant to address the “who, what, when, how & why” across the strategic, operational and tactical needs of your organization:
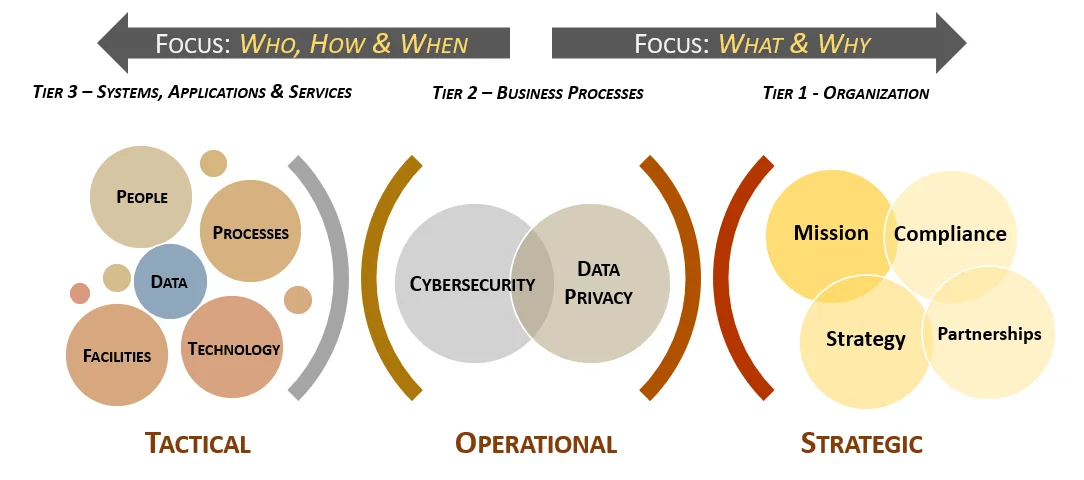
In a business context, cybersecurity and privacy documentation (e.g., policies, standards, procedures, etc.) provide direction to all employees and contractors within an organization to address needs for secure practices. This guidance for cybersecurity and data protection is intended to be in accordance with the organization's overall business objectives (e.g., strategic business plan), as well as relevant laws, regulations and other legal obligations for cybersecurity and privacy.
The development and implementation of the policies and standards is evidence of due diligence that the organization's compliance obligations are designed to address applicable administrative, technical and physical security controls. It is important to ensure that policies and standards document what the organization is doing, as the policies and standards are often the mechanisms by which outside regulators measure implementation and maturity of the control.
The purpose of a organization's cybersecurity & privacy documentation is to prescribe a comprehensive framework for:
- Creating a clearly articulated approach to how your company handles cybersecurity – in terms of ISO 27001, this concept would be considered an Information Security Management System (ISMS).
- Protecting the confidentiality, integrity, availability and safety of data and systems on your network.
- Providing guidance to help ensure the effectiveness of cybersecurity and data protection controls that are put in place to support your company’s operations.
- Helping your users to recognize the highly-networked nature of the current computing environment to provide effective company-wide management and oversight of those related cybersecurity risks.
The objective is to provide management direction and implement necessary cybersecurity and data protections in accordance with business requirements and relevant laws and regulations.
## Cybersecurity & Privacy Documentation - Editable, Scalable & Affordable
While policies and standards are designed to describe **WHY** something is required and **WHAT** needs to be done, many companies fail to create documentation to address **HOW** the policies and standards are actually implemented. When you "peel back the onion" and want to build an audit-ready cybersecurity and privacy program, there is a need to address "the how" for certain topics, such as vulnerability management, risk management, vendor management and incident response. We did the heavy lifting and created several program-level documents to address this need!
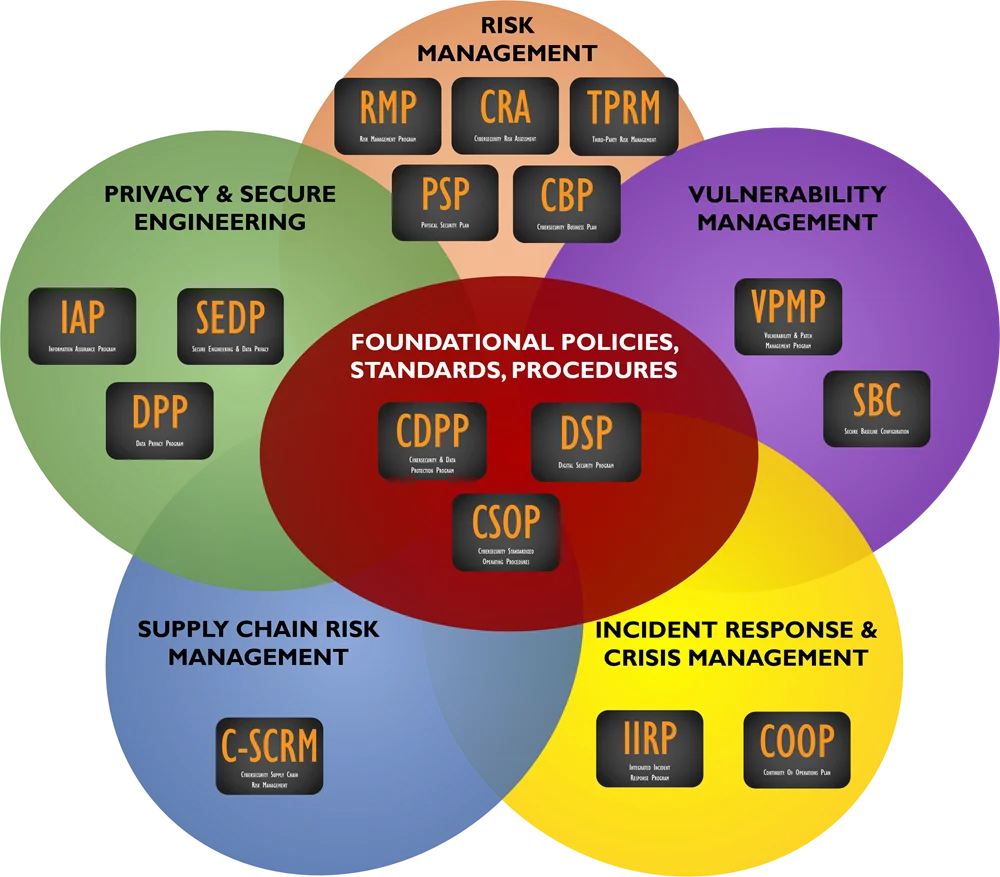
## Written Information Security Documentation Starts with Policies & Standards Based on Industry-Recognized Best Practices
A single negligent breach can close your business forever, because your liability insurance may not cover professional negligence if you are unable to provide evidence that you took reasonable steps to prevent a breach or other cybersecurity-related incident. Without the ability to prove steps were taken to ensure due care and due diligence were applied to your business operations, you may be considered negligent in a lawsuit and be fully exposed to fines, penalties and damages.
This is where ComplianceForge can help, since we have the information security solutions that your company needs to be able to prove evidence of due care and due diligence with industry-accepted best practices for IT security. From IT security policies, to risk assessments, to vendor management solutions, we can help you keep your company secure! Documentation serves as the foundational building blocks for your cybersecurity and privacy program. Without properly-scoped policies to address your applicable statutory, regulatory and contractual obligations, your associated standards and procedures will likely be inadequate to meet your compliance needs. The requires a holistic approach to right-sizing your cybersecurity program to meet your organization's specific compliance and security requirements.
## Concept of Operations (CONOPS) Provides Program-Level Guidance
A Concept of Operations (CONOPS) is a user-oriented guidance document that describes the mission, operational objectives and overall expectations from an integrated systems point of view, without being overly technical or formal. A CONOPS is meant to:
- Benefit stakeholders by establishing a baseline “operational concept” to establish a conceptual, clearly-understood view for everyone involved in the scope of operations described by the CONOPS.
- Record design constraints, the rationale for those constraints and to indicate the range of acceptable solution strategies to accomplish the mission and any stated objectives.
- Contain a conceptual view that illustrates the top-level functionality in the proposed process or system.
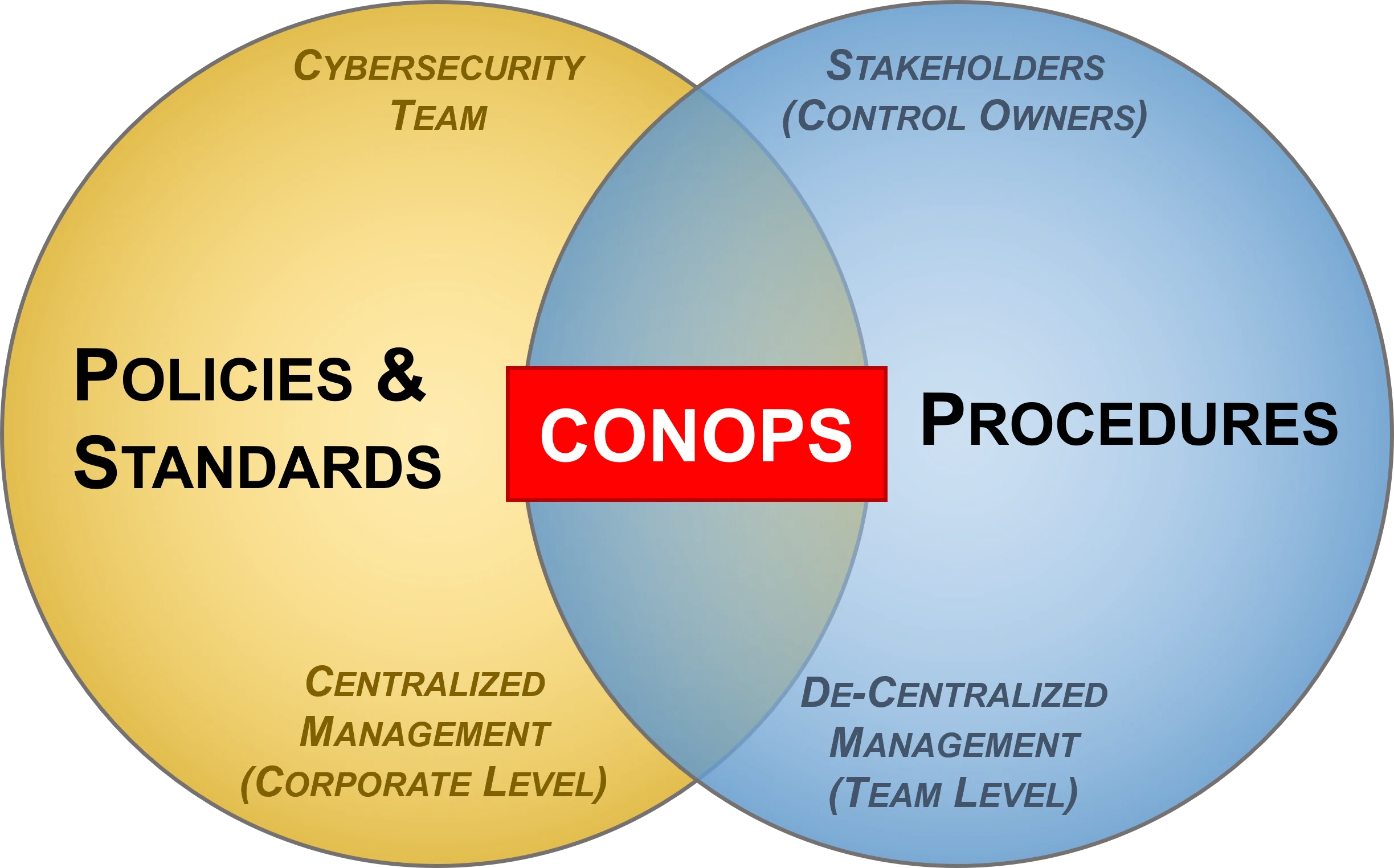
Several ComplianceForge documents are essentially CONOPS documents, where CONOPS are more conceptual than procedures and are focused on providing program-level guidance. A _**CONOPS straddles the territory between an organization's centrally-managed policies/standards and its decentralized, stakeholder-executed procedures**_, where CONOPS serves as expert-level guidance that is meant to run a specific function. Examples of where a CONOPS is useful for providing program-level guidance:
- Risk management (e.g., [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/))
- Vulnerability management (e.g., [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/))
- Incident response (e.g., [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/))
- Business Continuity / Disaster Recovery (e.g., [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/))
- Secure Engineering (e.g., [Security & Privacy By Design (SPBD)](https://complianceforge.com/product/security-by-design-privacy-by-design/))
- Pre-production testing (e.g., [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template))
- Supply Chain Risk Management (SCRM) (e.g., [Cybersecurity Supply Chain Risk Management Program Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan "Cybersecurity Supply Chain Risk Management Program Strategy & Implementation Plan (C-SCRM SIP)"))
Your organization’s Subject Matter Experts (SMEs) are expected to use a CONOPS as a tool to communicate user needs and system characteristics to developers, integrators, sponsors, funding decision makers and other stakeholders.
## Procedures Operationalize Policies & Standards - This Is A Key Concept To Being Both Secure & Compliant
We leverage the [Operationalizing Cybersecurity Planning Model](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model") in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
[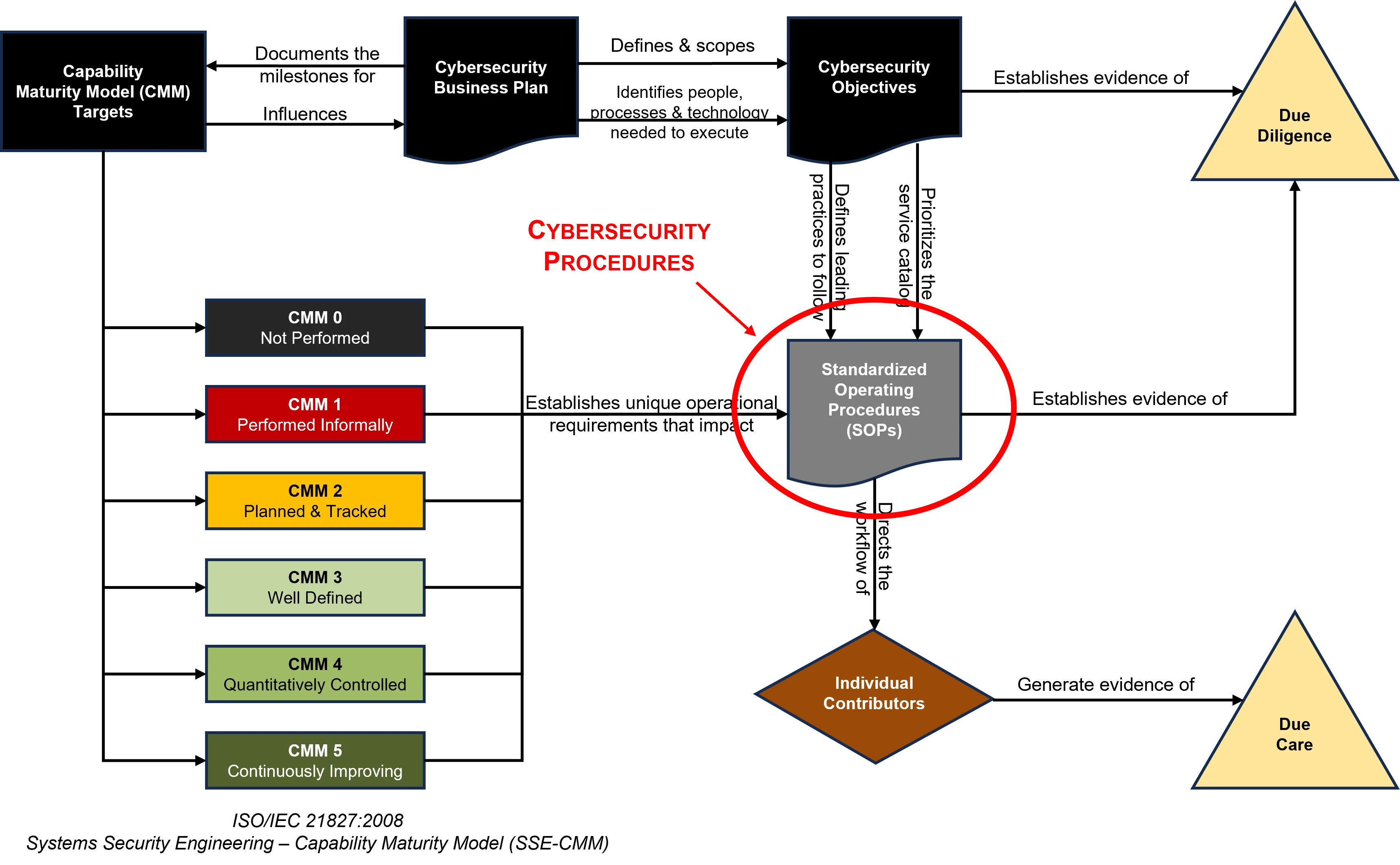](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")
## Policies, Standards, Function-Specific Guidance & Procedures - How Our Products Support Each Other
The following diagram helps demonstrate the layered nature of cybersecurity documentation. Policies & standards set the stage for teams/departments to create and implement programs that are function-specific.
For example:
- A policy on risk will define management's intent to manage risk ( **RA section of NIST 800-53**);
- One of the standards supporting the risk policy might require an annual risk assessment ( **RA-3**);
- Products such as the **Risk Management Program (RMP)** provide the middle-ground between the policy/standard and the actual deliverable risk assessment to provide risk-specific guidance on concepts such as acceptable risk, the methodology of risk management the organization aligns to, who within the organization can sign off on various levels of risk, etc.
If you would like to know more about how this works, please [contact us](https://complianceforge.com/contact-us/) and we'd be happy to further explain how our documentation links together to create comprehensive, linked cybersecurity and privacy documentation.
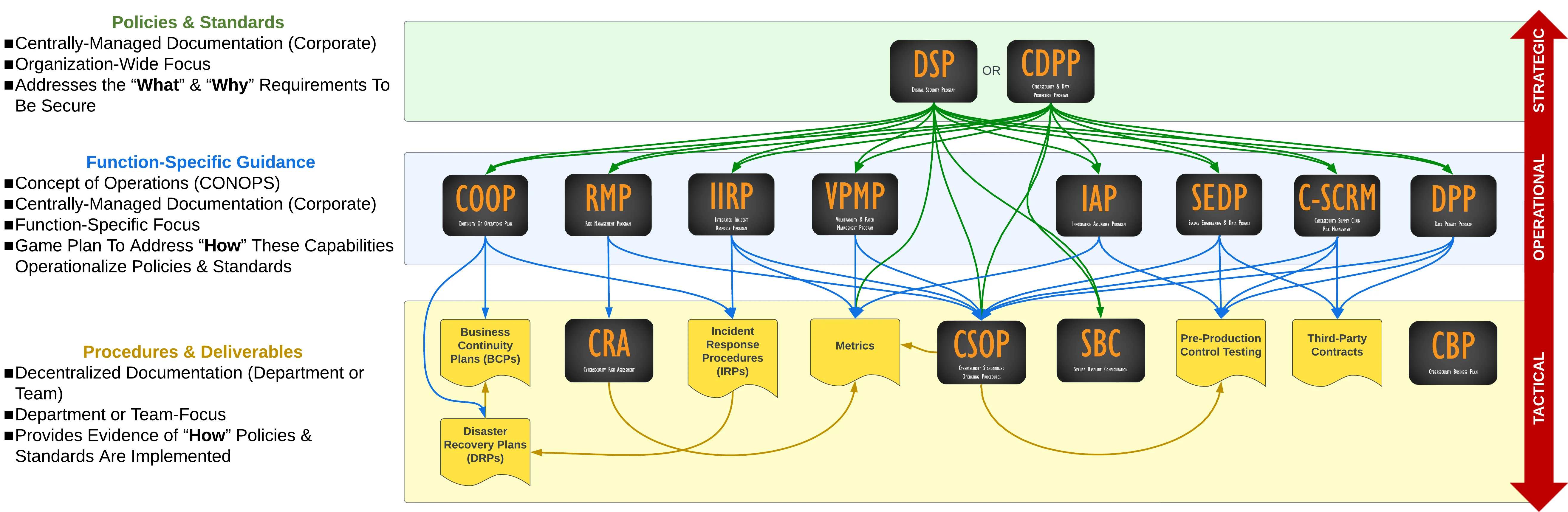
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) Policy Template - Editable Policies & Standards
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
#### [C-SCRM Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
ComplianceForge
NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
#### [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
ComplianceForge
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
#### [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
ComplianceForge
Cybersecurity Risk Management Program (RMP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
#### [Cybersecurity Risk Assessment (CRA) Template](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
ComplianceForge
Cybersecurity Risk Assessment Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$1,925.00 - $6,725.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
- [](https://complianceforge.com/product/integrated-incident-response-program/)
#### [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/integrated-incident-response-program/)
ComplianceForge
Integrated Incident Response Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/integrated-incident-response-program/)
- [](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
#### [NIST 800-171 System Security Plan (SSP) Template](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
ComplianceForge
NIST 800-171 System Security Plan (SSP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$950.00 - $5,750.00
[Choose Options](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
- [](https://complianceforge.com/product/pci-dss-v4-saq-a)
#### [Policies & Standards - PCI DSS v4 SAQ A](https://complianceforge.com/product/pci-dss-v4-saq-a)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) A for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,155.00
[Choose Options](https://complianceforge.com/product/pci-dss-v4-saq-a)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Compliance Forge Terms
[Skip to main content](https://complianceforge.com/terms-conditions/#main-content)
# Terms & Conditions
Terms & Conditions Last Updated Date: 2024-08-21
**COMPLIANCEFORGE.COM** **TERMS & CONDITIONS**
Purchasing product(s) from Compliance Forge, LLC (“ComplianceForge”, “the Company”, “us”, “we” or “ours”) and the complianceforge.com website (the “Website” or “Site”) signifies and confirms the Purchaser’s (“you” or “your”) acceptance of these terms and conditions of use (“Terms & Conditions”, "Terms"). We may revise and update these Terms & Conditions from time to time in our sole discretion. All changes are effective immediately when we post them and apply to all access to and use of the Compliance Forge website thereafter. Your continued use of the Website following the posting of revised Terms & Conditions means that you accept and agree to the changes, as they are binding on you.
**THIS DOCUMENT CONTAINS VERY IMPORTANT INFORMATION REGARDING YOUR RIGHTS AND OBLIGATIONS, AS WELL AS CONDITIONS, LIMITATIONS AND EXCLUSIONS THAT MIGHT APPLY TO YOU. PLEASE READ IT CAREFULLY.**
**THESE TERMS & CONDITIONS MAY REQUIRE THE USE OF ARBITRATION TO RESOLVE A PARTICULAR DISPUTE, RATHER THAN A JUDGE OR JURY TRIAL.**
**BY PLACING AN ORDER FOR PRODUCT(S) FROM THIS WEBSITE, YOU AFFIRM THAT YOU ARE OF LEGAL AGE TO ENTER INTO THIS AGREEMENT, AND YOU ACCEPT AND ARE BOUND BY THESE TERMS AND CONDITIONS. YOU AFFIRM THAT IF YOU PLACE AN ORDER ON BEHALF OF AN ORGANIZATION OR COMPANY, YOU HAVE THE LEGAL AUTHORITY TO BIND ANY SUCH ORGANIZATION OR COMPANY TO THESE TERMS. IF YOU ARE A THIRD-PARTY RESELLER, PURCHASING ON BEHALF OF AN ORGANIZATION OR COMPANY, YOU AFFIRM THAT SUCH ORGANIZATION OR COMPANY IS AWARE OF AND AGREES TO COMPLY WITH THESE TERMS.**
**A VIOLATION OF THESE TERMS MAY RESULT IN CLAIMS BY THE COMPANY AGAINST YOU FOR COPYRIGHT INFRINGEMENT, BREACH OF CONTRACT OR OTHER LEGAL CLAIMS NECESSARY FOR THE COMPANY TO ENFORCE ITS RIGHTS.**
**YOU MAY NOT ORDER OR OBTAIN PRODUCTS(S) or SERVICES FROM THIS WEBSITE IF YOU:**
a. DO NOT AGREE TO THESE TERMS;
b. ARE NOT THE OLDER OF:
i. AT LEAST 18 YEARS OF AGE; OR
ii. LEGAL AGE TO FORM A BINDING CONTRACT WITH THE COMPANY; OR
c. ARE PROHIBITED FROM ACCESSING OR USING THIS WEBSITE OR ANY OF THIS WEBSITE’S CONTENTS, PRODUCTS OR SERVICES BY APPLICABLE LAW.
These Terms & Conditions are subject to change by the Company without prior written notice at any time, in our sole discretion. Any changes to these Terms will be in effect as of the "Last Updated Date" referenced on the Site. You should review these Terms prior to purchasing any product or services that are available through this Site. Your continued use of this Site after the "Last Updated Date" will constitute your acceptance of and agreement to such changes. These Terms are an integral part of the Website Terms of Use that apply generally to the use of our Site. You should also carefully review our Privacy Policy before placing an order for products or services through this Site.
**TERMS OF USE**
All uses of our Website resulting from visits made by you to our Website, are governed by our Terms of Use set forth below, which are hereby incorporated into these Terms & Conditions.
**1\. Accessing the Website and Account Security**
We reserve the right to withdraw or amend this Website, and any service or material we provide on the Website, in our sole discretion without notice. We will not be liable if for any reason all or any part of the Website is unavailable at any time or for any period. From time to time, we may restrict access to some parts of the Website, or the entire Website, to users, including registered users. You agree that all information you provide to register with this Website or otherwise, including, but not limited to, through the use of any interactive features on the Website, is governed by our Privacy Notice \[[https://complianceforge.com/privacy/](https://complianceforge.com/privacy/)\], and you consent to all actions we take with respect to your information consistent with our Privacy Notice. You acknowledge that your account is personal to you and agree not to provide any other person with access to this Website or portions of it using your username, password, or other security information. You agree to notify us immediately of any unauthorized access to or use of your username or password or any other breach of security. You should use particular caution when accessing your account from a public or shared computer so that others are not able to view or record your password or other personal information. We have the right to disable any username, password, or other identifier, whether chosen by you or provided by us, at any time in our sole discretion, for any or no reason, including if, in our opinion, you have violated any provision of these Terms of Use. You are responsible for making all arrangements necessary for you to have access to the Website and for ensuring that all persons who access the Website through your internet connection are aware of these Terms of Use and comply with them.
**2\. Intellectual Property Rights in the Website**
The Website and its entire contents, features, and functionality (including but not limited to all information, software, text, displays, images, video, and audio, and the design, selection, and arrangement thereof) are owned by the Company, its licensors, or other providers of such material and are protected by United States and international copyright, trademark, patent, trade secret, and other intellectual property or proprietary rights laws. No right, title, or interest in or to the Website or any content on the Website is transferred to you, and all rights not expressly granted are reserved by the Company. Any use of the Website not expressly permitted by these Terms of Use is a breach of these Terms of Use and may violate copyright, trademark, and other laws. You must not reproduce, distribute, modify, create derivative works of, publicly display, publicly perform, republish, download, store, or transmit any of the material on our Website, except as follows:
a. Your computer may temporarily store copies of such materials in RAM incidental to your accessing and viewing those materials.
b. You may store files that are automatically cached by your Web browser for display enhancement purposes.
**TERMS OF SALE**
All purchases of products through our Website or resulting from visits made by you to our Website, are governed by our Terms of Sale set forth below, which are hereby incorporated into these Terms & Conditions.
**3\. Purchaser Responsibility to Evaluate Risks**
Purchaser acknowledges and agrees that:
a. No network, system, device, hardware, software, or component can be made fully secure;
b. Purchaser has the sole responsibility to evaluate the risks and benefits of the ComplianceForge products to Purchaser’s particular circumstances and requirements; and
c. ComplianceForge is not assuming any of the liabilities associated with Purchaser’s use of any ComplianceForge product.
**4\. Order Acceptance and Cancellation**
You agree that your order is an offer to buy, under these Terms of Sale, all products listed in your order. All orders must be accepted by us or we will not be obligated to sell the products to you. We may choose not to accept orders at our sole discretion, even after we send you an automated confirmation email with your order number and details of the items you have ordered.
**5\. No Refunds, Cancellations & Exchanges**
a. You acknowledge your obligation to pay for the product(s) ordered by placing an order;
b. Purchaser may cancel an order up to the point when the order is shipped (e.g., emailed or made available for download) to fulfill the order. Once the order is fulfilled, no cancellations will be honored; and
c. ComplianceForge does not offer refunds, cancellations or exchanges. Due to the nature of intellectual property, it is not possible to confirm that Purchaser deleted the ordered material, and that fact dictates the reason ComplianceForge does not offer refunds, cancellations or exchanges.
**6\. Prices and Payment Terms**
a. All prices, discounts, and promotions posted on this Site are subject to change without notice. The price charged for any product will be the price advertised on this Site at the time the order is placed, subject to the terms of any promotions or discounts that may be applicable. The price charged will be clearly stated in your order confirmation email. Price increases will only apply to orders placed after the time of the increase. We strive to display accurate price information, however we may, on occasion, make inadvertent typographical errors, inaccuracies or omissions related to pricing and availability. We reserve the right to correct any errors, inaccuracies, or omissions at any time and to cancel any orders arising from such occurrences; and
b. Terms of payment are within our sole discretion and, unless otherwise agreed by us in writing, payment must be received by us before our acceptance of an order. We accept approved credit cards and other payment methods for all purchases. For credit card purchases, you represent and warrant that:
i. The credit card information you supply to us is true, correct and complete;
ii. You are duly authorized to use such credit card for the purchase; and
iii. Charges incurred by you will be honored by your credit card company.
**7\. Restrictions on Use of the Products**
Purchaser acknowledges and agrees that Purchaser may not:
a. Sell, rent, lease, sublicense or otherwise transfer or exploit any rights to any ComplianceForge product in any way or for any purpose;
b. Post any ComplianceForge product on any publicly-available website, bulletin board, newsgroup, or other similar mechanism or device;
c. Facilitate or otherwise aid other individuals or entities in violating these Terms & Conditions;
d. Disclose any ComplianceForge product to a third-party without first obtaining a fully-executed Non-Disclosure Agreement (NDA) between you and the third-party that restricts the use, distribution or release of the disclosed material (e.g., sharing documentation with auditors or an evidence request as part of a third-party risk assessment);
e. Utilize ComplianceForge products and/or content to create derivative works to sell and/or share with third-parties; and/or
f. Upload ComplianceForge products and/or content to a Large Language Model (LLM), or similar Artificial Intelligence (AI) technology, where ComplianceForge products and/or content could be used to train the LLM.
**8\. Single Entity License and Intellectual Property Rights in the Products**
Purchaser acknowledges and agrees that:
a. All uses on this Site of the terms “sell,” “sale,” “resell,” “resale,” “purchase,” “price,” and the like mean the purchase or sale of a license. Each product marketed on this Website (“the Licensed Product”) is made available solely for license, not sale, to you and other prospective customers under these Terms & Conditions;
b. Upon purchase of any Licensed Product on the Website, Purchaser receives a non-exclusive, perpetual, worldwide, non-transferable, non-sublicensable license for use of the product by a single legal entity (e.g., corporation, LLC, non-profit, partnership, sole proprietorship, government agency, major military command, etc.)(“License”); such License does not transfer any title or ownership rights for Intellectual Property in any ComplianceForge product. However, you may edit purchased products, as necessary, to meet your internal business requirements only so long as you are in compliance with the License. The Company may terminate the License without notice upon your breach of these Terms & Conditions, including any breach of the License. Upon termination of the License by the Company, all rights licensed under the License will revert immediately to the Company and/or its Licensor and within seven (7) days you shall inactivate and erase all digital copies of the Work and, at Licensor’s written request, you shall also return or destroy, any tangible copies of the Work;
c. The Company and/or its Licensor are and will remain the sole and exclusive owner and/or Licensee of all intellectual property rights in and to each product made available on this Site and any related specifications, instructions, documentation or other materials, including, but not limited to, all related copyrights, patents, trademarks and other intellectual property rights, subject only to the limited license granted under the product’s License. You do not and will not have or acquire any ownership of these intellectual property rights in or to the products made available through this Site, or of any intellectual property rights relating to those products or services;
d. Purchaser will comply with all Terms & Conditions for any Product obtained through this Site, including, but not limited to, all confidentiality obligations and restrictions on resale, use, reverse engineering, copying, making, modifying, improving, sublicensing, and transfer of those licensed products and services;
e. Purchaser will not cause, induce or permit others’ noncompliance with these Terms and Conditions or the License granted thereunder; and
f. ComplianceForge products are considered Commercial Off The Shelf (COTS) products regarding Federal Acquisition Regulation (FAR) and Defense Federal Acquisition Regulation Supplement (DFARS). There is no storage, transmission and/or processing of Federal Contract Information (FCI) and/or Controlled Unclassified Information (CUI) in the purchase of ComplianceForge Products.
**9\. Disclaimer of Warranties**
**WE MAKE NO WARRANTY WHATSOEVER WITH RESPECT TO THE PRODUCTS PURCHASED THROUGH THE SITE, INCLUDING ANY:**
a. WARRANTY OF MERCHANTABILITY;
b. WARRANTY OF FITNESS FOR A PARTICULAR PURPOSE;
c. WARRANTY OF TITLE; OR
d. WARRANTY AGAINST INFRINGEMENT OF INTELLECTUAL PROPERTY RIGHTS OF A THIRD PARTY; WHETHER EXPRESS OR IMPLIED BY LAW, COURSE OF DEALING, COURSE OF PERFORMANCE, USAGE OF TRADE, OR OTHERWISE.
e. ComplianceForge is providing products "as is" and "as available" without any representations, warranties, or covenants of any kind whatsoever regarding:
i. The effect or lack of effect of any ComplianceForge product on the operation or the security of any network, system, software, hardware, or any component of any of them, and
ii. The accuracy, utility, reliability, timeliness, or completeness of the product; or
iii. The responsibility to make or notify Purchaser of any corrections, updates, upgrades, or fixes.
**10\. Limitation of Liability**
a. IN NO EVENT SHALL COMPLIANCEFORGE OR ANY OF ITS EMPLOYEES, OFFICERS, DIRECTORS, AGENTS OR OTHER SERVICE PROVIDERS BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OF USE, REVENUE, PROFIT, LOSS OF DATA OR DIMINUTION IN VALUE, OR FOR ANY CONSEQUENTIAL, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR PUNITIVE DAMAGES WHETHER ARISING OUT OF BREACH OF CONTRACT, TORT (INCLUDING NEGLIGENCE) OR OTHERWISE, REGARDLESS OF WHETHER SUCH DAMAGES WERE FORESEEABLE AND WHETHER OR NOT WE HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES, AND NOTWITHSTANDING THE FAILURE OF ANY AGREED OR OTHER REMEDY OF ITS ESSENTIAL PURPOSE.
b. IN NO EVENT SHALL OUR AGGREGATE LIABILITY ARISING OUT OF OR RELATED TO THIS AGREEMENT, WHETHER ARISING OUT OF OR RELATED TO BREACH OF CONTRACT, TORT (INCLUDING NEGLIGENCE) OR OTHERWISE, EXCEED THE AMOUNTS PAID BY YOU FOR THE PRODUCTS AND SERVICES SOLD THROUGH THE SITE.
**GENERAL PROVISIONS APPLICABLE TO THESE TERMS & CONDITIONS**
**11\. Trademarks**
The Company tradename ComplianceForge, the word marks COMPLIANCE FORGE and COMPLIANCEFORGE, and the design mark \[ComplianceForge logo,\] and all related or confusingly similar names, logos, product and service names, designs, and slogans are trademarks of the Company or its affiliates or licensors. You must not use such marks without the prior written permission of the Company. All other names, logos, product and service names, designs, and slogans on this Website are the trademarks of their respective owners.
**12\. Indemnification**
You agree to hold harmless the Company, its parent(s), subsidiary(ies), affiliates, partners, officers, directors, agents, contractors, licensors, service providers, subcontractors, suppliers, interns and employees, successors, and assigns from and against any claims, liabilities, damages, judgments, awards, losses, costs, expenses, or fees (including reasonable attorneys’ fees) arising out of or relating to your use of the Website, including, but not limited to any use of the Website’s information, content, services, and products other than as expressly authorized in these Terms & Conditions. Any use of the Website’s content, information, services, and products by you is entirely at your own risk and discretion.
**13\. Governing Law and Jurisdiction**
All matters relating to the Website and these Terms & Conditions, and any dispute or claim arising therefrom or related thereto (in each case, including non-contractual disputes or claims), shall be governed by and construed in accordance with the internal laws of the State of Wyoming without giving effect to any choice or conflict of law provision or rule.
Any legal suit, action, or proceeding arising out of, or related to, these Terms & Conditions or the Website shall be instituted exclusively in the United States federal and state courts of the State of Wyoming, in each case located in the County of Sheridan, although we retain the right to bring any suit, action, or proceeding against you for breach of these Terms & Conditions in your country of residence or any other relevant country. You waive any and all objections to the exercise of jurisdiction over you by such courts and to venue in such courts.
**14\. Arbitration**
At Company’s sole discretion, it may require You to submit any disputes arising from these Terms & Conditions or use of the Website, including disputes arising from or concerning their interpretation, violation, invalidity, non-performance, or termination, to final and binding arbitration in Wyoming applying Wyoming law. In such event, the arbitration will be administered by the American Arbitration Association ("AAA") under its Commercial Arbitration Rules and Mediation Procedures ("Commercial Rules"). The arbitrator(s) will have exclusive authority to resolve any dispute relating to arbitrability and/or enforceability of this arbitration provision, including any unconscionability challenge or any other challenge that the arbitration provision or the agreement is void, voidable or otherwise invalid. The arbitrator will be empowered to grant whatever relief would be available in court under law or in equity. Any award of the arbitrator(s) will be final and binding on each of the parties, and may be entered as a judgment in any court of competent jurisdiction. If any provision of this arbitration agreement is found unenforceable, the unenforceable provision will be severed, and the remaining arbitration terms will be enforced.
**15**. **Assignment**
You will not assign any of your rights or delegate any of your obligations under these Terms without our prior written consent. Any purported assignment or delegation in violation of this Section 15 is null and void. No assignment or delegation relieves you of any of your obligations under these Terms.
**16\. Waiver and Severability**
No waiver by the Company of any term or condition set out in these Terms & Conditions shall be deemed a further or continuing waiver of such term or condition or a waiver of any other term or condition, and any failure of the Company to assert a right or provision under these Terms & Conditions shall not constitute a waiver of such right or provision.
If any provision of these Terms & Conditions is held by a court or other tribunal of competent jurisdiction to be invalid, illegal, or unenforceable for any reason, such provision shall be eliminated or limited to the minimum extent such that the remaining provisions of the Terms & Conditions will continue in full force and effect.
**17\. Force Majeure**
The Company shall not be liable or responsible to You, nor be deemed to have defaulted under or breached this Agreement, for any failure or delay in fulfilling or performing any term of this Agreement, when and to the extent such failure or delay is caused by or results from the following force majeure events ("Force Majeure Event(s)"): (a) acts of God; (b) flood, fire, earthquake, pandemics, epidemics; (c) war, invasion, hostilities (whether war is declared or not), terrorist threats or acts, riot or other civil unrest; (d) government order, law, or action; (e) embargoes or blockades in effect on or after the date of this Agreement; (f) national or regional emergency; (g) strikes, labor stoppages or slowdowns or other industrial disturbances; and (h) shortage of adequate power or transportation facilities.
**18\. Entire Agreement**
The Company’s Terms & Conditions, License, and Privacy Notice constitute the sole and entire agreement between you and the Company regarding the Website and the Products sold on the Website and supersede all prior and contemporaneous understandings, agreements, representations, and warranties, both written and oral, regarding the Website or the Products sold on the Website.
**19\. No Reliance on Other Representations.**
You acknowledge and agree that no consideration, other than as provided for by these Terms, has been or will be paid or furnished and that You have freely and voluntarily purchased product without reliance on any representation of any third party.
**20\. Agreement Binding.**
This Agreement shall be binding upon and inure to the benefit of the Company and its respective owners, shareholders, successors, affiliates, subsidiaries, officers, managers, members, directors, agents, heirs, successors, and assigns.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Compliance Solutions
[Skip to main content](https://complianceforge.com/brands/ComplianceForge#main-content)

# ComplianceForge
Sort By:Featured ItemsNewest ItemsBest SellingA to ZZ to ABy ReviewPrice: AscendingPrice: Descending
- [](https://complianceforge.com/subscription/dsp-csop)
#### [Subscription - DSP & CSOP](https://complianceforge.com/subscription/dsp-csop)
ComplianceForge
DSP & CSOP - Annual Subscription for Product Updates
This is a subscription service for existing DSP & CSOP clients to obtain product updates. Due to the dynamic nature of the DSP...
$2,600.00
[Choose Options](https://complianceforge.com/subscription/dsp-csop)
- [](https://complianceforge.com/subscription/dsp)
#### [Subscription - Digital Security Program (DSP)](https://complianceforge.com/subscription/dsp)
ComplianceForge
Digital Security Program (DSP) - Annual Subscription for Product Updates
This is a subscription service for existing Digital Security Program (DSP) clients to obtain product updates. Due to the...
$1,700.00
[Choose Options](https://complianceforge.com/subscription/dsp)
- [](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
#### [C-SCRM Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
ComplianceForge
NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
Product Walkthrough Video
When you click the image or the link below,...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
- [](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
#### [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
ComplianceForge
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
#### [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
ComplianceForge
Cybersecurity Risk Management Program (RMP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
#### [Cybersecurity Risk Assessment (CRA) Template](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
ComplianceForge
Cybersecurity Risk Assessment Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product...
$1,925.00 - $6,725.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
- [](https://complianceforge.com/subscription/csop)
#### [Subscription - CSOP (DSP version)](https://complianceforge.com/subscription/csop)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) - Annual Subscription for Product Updates
This is a subscription service for existing clients of the DSP/SCF version of the CSOP to...
$900.00
[Choose Options](https://complianceforge.com/subscription/csop)
- [](https://complianceforge.com/product/integrated-incident-response-program/)
#### [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/integrated-incident-response-program/)
ComplianceForge
Integrated Incident Response Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/integrated-incident-response-program/)
- [](https://complianceforge.com/product/data-privacy-program-dpp/)
#### [Data Privacy Program (DPP)](https://complianceforge.com/product/data-privacy-program-dpp/)
ComplianceForge
Data Privacy Program (DPP) - Editable Privacy Program Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that...
$3,300.00 - $8,100.00
[Choose Options](https://complianceforge.com/product/data-privacy-program-dpp/)
- [](https://complianceforge.com/product/nist-csf-procedures-csop/)
#### [Procedures Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST Cybersecurity Framework 2.0
Product Walkthrough Video
When you click the image or the link below, it will direct you to...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/nist-csf-procedures-csop/)
- [](https://complianceforge.com/product/security-by-design-privacy-by-design/)
#### [Secure Engineering & Data Privacy (SEDP) Program](https://complianceforge.com/product/security-by-design-privacy-by-design/)
ComplianceForge
Secure Engineering & Data Privacy
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/security-by-design-privacy-by-design/)
- [](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
#### [Procedures Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) ISO 27001 / ISO 27002
Product Walkthrough Video
When you click the image or the link below, it will direct you to a...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Documentation Solutions
[Skip to main content](https://complianceforge.com/about-us/#main-content)
# About Us

**ComplianceForge specializes in cybersecurity & data protection documentation**. We are an industry leader in providing affordable, editable and scalable documentation solutions to support cybersecurity and data privacy compliance efforts. Our products serve as a business accelerator, where we do the heavy lifting for our clients so their cybersecurity and IT staff can focus on the roles they were hired to do. Essentially, we help our clients stay in business by providing the necessary policies, standards, procedures and other documentation they need to address their cybersecurity and data privacy compliance obligations in the most efficient manner possible. We leverage industry-recognized secure practices so our solutions can scale from Fortune 100 multinationals with complex compliance requirements, all the way down to micro-small companies that just need single solutions, such as PCI DSS or CMMC compliance.
ComplianceForge's mission is to serve as a business accelerator \- we provide affordable cybersecurity and data privacy solutions of the highest quality to save our clients both time and money in meeting their specific statutory, regulatory and contractual compliance needs. Our business model allows us to sell our documentation solutions at a small fraction of the cost when compared to hiring a consultant to custom-develop documentation or writing it in-house with your existing staff. Additionally, our products are usually delivered via email the same business day. Our focus is on Governance, Risk and Compliance (GRC) and we fully-understand cybersecurity and privacy are necessary for organizations to protect not only their clients, but their employees and partners. With our comprehensive documentation, we enable companies to efficiently become and stay compliant with common cybersecurity and privacy requirements.
Since 2005, ComplianceForge has been selling solutions to a [worldwide list of clients](https://complianceforge.com/faq/industries-served) that range from the Fortune 100, to government agencies to small and medium businesses. The reason we have such a broad reach across both industries and organization sizes is that our documentation is designed to be scalable and align an organization with an applicable framework. We understand that _"a standard is a standard for a reason"_ and that is a fundamental concept in how we develop our solutions so requirements can be clearly addressed.
We continuously innovate and share those ideas to better the industry. In additional to helping launch the [Secure Controls Framework (SCF)](https://complianceforge.com/GRC%20Is%20a%20Plan,%20Do,%20Check%20&%20Act%20(PDCA)%20Adventure%20%E2%80%93%20That%20Is%20A%20Concept%20That%20Should%20Be%20Embraced,%20Not%20Fought%20Against%20GRC%20most%20often%20deals%20with%20legally-binding%20requirements,%20so%20it%20is%20important%20to%20understand%20that%20negligence%20is%20situationally-dependent.%20For%20example,%20an%20intoxicated%20driver%20who%20gets%20behind%20the%20wheel%20acting%20negligently.%20However,%20when%20sober,%20that%20same%20individual%20is%20a%20champion%20race%20car%20driver%20who%20is%20highly-skilled%20and%20would%20not%20be%20considered%20incompetent%20in%20any%20regard.%20In%20this%20example,%20driving%20intoxicated%20constitutes%20a%20negligent%20act%20and%20shows%20that%20negligence%20has%20nothing%20to%20do%20with%20being%20incompetent.%20The%20point%20is%20to%20demonstrate%20that%20an%20organization%20can%20employ%20many%20highly-competent%20personnel,%20but%20even%20competent%20people%20can%20behave%20in%20a%20negligent%20manner.%20GRC%20fundamentally%20exists%20to%20help%20an%20organization%20avoid%20circumstances%20that%20could%20be%20construed%20as%20negligent%20acts.%20%20%20Considering%20how%20business%20practices%20continuously%20evolve,%20so%20must%20cybersecurity%20practices.%20The%20Plan,%20Do,%20Check%20&%20Act%20(PDCA)%20process%20enables%20the%20GRC%20function%20to%20continuously%20evaluate%20risks,%20threats%20and%20performance%20trends,%20so%20that%20the%20organization's%20leadership%20can%20take%20the%20necessary%20steps%20to%20minimize%20risk%20by%20modifying%20how%20people,%20processes%20and%20technology%20work%20together%20to%20keep%20everything%20both%20secure%20and%20operational.%20The%20PDCA%20approach%20(also%20referred%20to%20as%20the%20Deming%20Cycle)%20is%20a%20logical%20way%20to%20conceptualize%20how%20GRC%20works:%20%20Plan.%20The%20overall%20GRC%20process%20beings%20with%20planning.%20This%20planning%20will%20define%20the%20policies,%20standards%20and%20controls%20for%20the%20organization.%20It%20will%20also%20directly%20influence%20the%20tools%20and%20services%20that%20an%20organization%20purchases,%20since%20technology%20purchases%20should%20address%20needs%20that%20are%20defined%20by%20policies%20and%20standards.%20Do.%20Arguably,%20this%20is%20the%20most%20important%20section%20for%20cybersecurity%20and%20privacy%20practitioners.%20Controls%20are%20the%20%E2%80%9Csecurity%20glue%E2%80%9D%20that%20make%20processes,%20applications,%20systems%20and%20services%20secure.%20Procedures%20(also%20referred%20to%20as%20control%20activities)%20are%20the%20processes%20how%20the%20controls%20are%20actually%20implemented%20and%20performed.%20The%20Secure%20Controls%20Framework%20(SCF)%20can%20be%20an%20excellent%20starting%20point%20for%20a%20control%20set%20if%20your%20organization%20lacks%20a%20comprehensive%20set%20of%20cybersecurity%20and%20privacy%20controls.%20Check.%20In%20simple%20terms,%20this%20is%20situational%20awareness.%20Situational%20awareness%20is%20only%20achieved%20through%20reporting%20through%20metrics%20and%20reviewing%20the%20results%20of%20audits/assessment.%20Act.%20This%20is%20essentially%20risk%20management,%20which%20is%20an%20encompassing%20area%20that%20deals%20with%20addressing%20two%20main%20concepts%20(1)%20real%20deficiencies%20that%20currently%20exist%20and%20(2)%20possible%20threats%20to%20the%20organization. "Secure Controls Framework (SCF)") as an independent company, ComplianceForge is notable for:
- [Integrated Controls Management (ICM)](https://complianceforge.com/grc/integrated-controls-management/ "Integrated Controls Management (ICM)")
- [Hierarchical Cybersecurity Governance Framework (HCGF)](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/ "Hierarchical Cybersecurity Governance Framework (HCGF)")
- [Cybersecurity Metrics Reporting Model (CMRM)](https://complianceforge.com/free-guides/cybersecurity-metrics-reporting-model/ "Cybersecurity Metrics Reporting Model (CMRM)")
- [Cybersecurity Supply Chain Risk Management (C-SCRM)](https://complianceforge.com/free-guides/cybersecurity-metrics-reporting-model/ "Cybersecurity Metrics Reporting Model (CMRM)")
## Cybersecurity Documentation Done Right - A Standard Is A Standard For A Reason
In our ongoing commitment to provide excellent customer service, we feel compelled to make sure businesses have the support they need for their cybersecurity and privacy needs. This is where we make a difference and decrease the liabilities associated with running a business, since businesses rely too much on their IT resources to let amateurs provide guidance. The liabilities are too great to take chances. We fill the niche skillset of writing quality cybersecurity and privacy documentation that is comprehensive, scalable and affordable.
## What Makes Us Special
We are specialists within the cybersecurity and privacy professions, where our focus is on [Governance, Risk and Compliance (GRC)](https://complianceforge.com/governance-risk-compliance-grc-content/ "Governance, Risk and Compliance (GRC)"). Our comprehensive documentation helps companies become and stay compliant with cybersecurity and privacy requirements.
| | | |
| --- | --- | --- |
|  |  |  |
| **Compliance Forge, LLC (ComplianceForge)** | **Compliance-Focused Documentation** | **Veteran-Owned & Made In The USA** |
| _We focus on writing cybersecurity and privacy documentation so that you can focus on what you do best - growing your business! [Our customers](https://complianceforge.com/faq/industries-served) are in good company, since our products are used by many of the most well-known companies in the country, as well as many international companies._ | _There are no such things as "Bronze, Silver or Gold" levels of compliance - a standard is a standard for a reason and we understand that when we develop our documentation products to help our customers have evidence of due care and due diligence for their compliance needs._ | _We are proud to be a Veteran-Owned Small Business (VOSB). ComplianceForge was formed by two former military officers with extensive backgrounds in cybersecurity and Counter Terrorism / Force Protection (CT/FP)._ |
## Our Beliefs
We are here to help businesses that lack this special knowledge & experience. Simple truths that we believe in include:
- Cybersecurity & privacy documentation is too important to be left to amateurs;
- Every business needs appropriate policies, standards and procedures to be able to demonstrate due diligence and due care efforts;
- Our solution should be affordable and scalable to encourage growth; and
- Documentation should be written in business-friendly language that is both scalable and concise, yet comprehensive.
Our vision at ComplianceForge is based on the core understanding of the necessity for businesses of all sizes and industries to adopt security practices to protect their interests, including their customers, their employees, and their partners.
## Which Industries Have We Served?
**Our Products Are Used By Some Of the Biggest Names In The Industry**
We've been writing quality security documentation since 2005. In that time, we've served clients across nearly every industry and size, both domestically and internationally. Our clients range from well-known Fortune 100 corporations to small businesses, both within the US and abroad. We've proved time and again that our cybersecurity documentation is flexible enough to work in any organization and can scale accordingly.
Since we respect the privacy of our clients, we do not provide the names of the companies we serve. Many of the well-known and trusted brands that you use on a daily basis are our clients and we are very proud of that fact. In many ways, we are corporate America's "dirty little secret" since we are a leading source for professionally-written cybersecurity documentation, yet we stay in the shadows as quiet professionals. Below is a list of industries where our products have been successfully implemented, so you will be in good company as a client of ours:
| | | |
| --- | --- | --- |
| **Financial**
\- Certified Public Accountants (CPAs)
\- Financial Planners & Wealth Managers
\- Banks & Credit Unions
\- Bookkeepers
**Technology Companies**
\- Hardware Manufacturers
\- Consultants
\- Software Companies
\- Website Developers
\- Managed Service Providers
\- Auditors
\- Cybersecurity
**Medical**
\- Hospitals
\- Doctors
\- Dentists
\- Physical Therapists
\- Chiropractors
\- Medical Billing
\- Elder Care Facilities
**Consultants**
\- Business Analysts
\- Management Consultants | **Government**
\- Defense Contractors (DoD)
\- Federal Government Contractors
\- Federal Government Agencies
\- State Government Agencies
\- Local Municipalities
\- Regional Airports
\- Law Enforcement
**Legal**
\- Lawyers
\- Court Reporters
\- Privacy Professionals
**Real Estate**
\- Brokers
\- Real Estate Offices
\- Title Companies
\- Developers
\- Property Management
**Utilities**
\- Oil & Natural Gas
\- Coal
\- Electric
\- Nuclear | **Construction & Manufacturing**
\- Commercial
\- Residential
\- Architects
\- Retail Products
\- Fabrication
\- Firearms Industry
**Hospitality & Food Services**
\- Hotels / Resorts
\- Restaurants
\- Casinos / Gaming
\- Coffee Shops
**Retail (B&M) & Services**
\- Health Clubs / Gyms
\- Credit Monitoring / ID Theft
\- Janitorial
\- Human Resources / Recruiting
**Non-Profits & Associations**
\- Chambers of Commerce
\- Clubs
\- Non-Profits |
## Cybersecurity & Privacy Documentation as a Service (DaaS)
Information security breaches and non-compliance fines have the ability to close a business for good. When it comes to NIST 800-171, FAR and NISPOM, companies can lose contracts or be prevented from being eligible to bid. We are experts in our field and have done the heavy lifting for you, so that you can focus on what you do best, which is growing your business and not having to worry about creating documentation for requirements that you are not experienced with:
- NIST 800-171 / CMMC
- DFARS
- EU General Data Protection Regulation (EU GDPR)
- California Consumer Privacy Act (CCPA)
- FAR
- NISPOM
- Payment Card Industry Data Security Standard (PCI DSS)
- State laws such as MA 201 CMR 17.00
- Fair & Accurate Credit Transactions Act (FACTA) "red flags" rule
- Gramm-Leach Bliley Act (GLBA) "safeguards" rule
- FTC "unfair business practices" - poor internal security programs
## Background on Documentation Developers
When it comes to cybersecurity, we take the topic seriously since this is our profession. We hire only certified cybersecurity professionals. As you can see below, our developers' qualifications are impressive:
- Certified Information Systems Security Professional ( **CISSP**)
- Payment Card Industry Professional ( **PCIP**)
- Certified in Risk and Information Systems Control ( **CRISC**)
- Certified Information Privacy Professional ( **CIPP/US**)
- Microsoft Certified Systems Engineer ( **MCSE**)
- Microsoft Certified Information Technology Professional ( **MCITP**)
- Federal IT Security Professional - Manager ( **FITSP-M**)
- Certified Computer Forensics Examiner ( **CCFE**)
- Certified Hacking Forensic Investigator ( **CHFI**)
- Security+ ( **CompTIA**)
- Network+ ( **CompTIA**)
- Master of Business Administration ( **MBA**)
- Master of Science, Management Information Systems ( **MIS**)
- Former military officers and a Department of Defense ( **DoD**) Information Security consultant
- Member of **MENSA**
Since 2005, we have been selling on-demand cybersecurity policies and we are proud to be the first company to offer such a service on the Internet.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
compliance forge, it compliance templates, complianceforge, it compliance templates for policy creation, compliance templates
## Cybersecurity Compliance Solutions
[Skip to main content](https://complianceforge.com/compliance-solutions/#main-content)
# Cybersecurity Policies, Standards & Procedures Templates

## Our Cybersecurity & Privacy Documentation Is Designed To Be Scalable, Comprehensive & Efficient
| | |
| --- | --- |
| We leverage the **[Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")** to develop the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care for our clients. This methodology towards documentation addresses the interconnectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. The **[Secure Controls Framework (SCF)](https://www.securecontrolsframework.com/ "Secure Controls Framework")** fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant. In addition to the SCF, this model works with ISO 27002, NIST CSF, NIST 800-171, CIS 20, PCI DSS, NIST 800-53 and other control frameworks.
ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist. You can click on the image below to better understand how we write our documentation that links policies all the way down to metrics. This is a great solution for any organization currently using or migrating to a **Governance, Risk & Compliance (GRC)** or **Integrated Risk Management (IRM)** platform to help automate their governance practices.
Documentation serves as the foundational building blocks for your cybersecurity and privacy program. Without properly-scoped policies to address your applicable statutory, regulatory and contractual obligations, your associated standards and procedures will likely be inadequate to meet your compliance needs. The requires a holistic approach to right-sizing your cybersecurity program to meet your organization's specific compliance and security requirements. |  |
[](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "complianceforge reference model - hierarchical cybersecurity governance framework")
## We Offer Huge Discounts Through Bundling Our Documentation
As visualized in the graphic below, the core of our solutions are based on policies, standards and procedures. From there, we have program-level solutions to address (1) risk management, (2) vulnerability management, (3) incident response & crisis management, (4) supply chain risk management and (5) privacy & secure engineering. Our bundles offer **saving up to 45%** and can provide near-turnkey documenation solutions for your organization. If you have a unique need, please [contact us](https://complianceforge.com/contact-us/ "Information security documentation template savings") since we might be able to work with you on your request.

## Concept of Operations (CONOPS) - Program-Level Guidance
A Concept of Operations (CONOPS) is a user-oriented guidance document that describes the mission, operational objectives and overall expectations from an integrated systems point of view, without being overly technical or formal. A CONOPS is meant to:
- Benefit stakeholders by establishing a baseline “operational concept” to establish a conceptual, clearly-understood view for everyone involved in the scope of operations described by the CONOPS.
- Record design constraints, the rationale for those constraints and to indicate the range of acceptable solution strategies to accomplish the mission and any stated objectives.
- Contain a conceptual view that illustrates the top-level functionality in the proposed process or system.
Several ComplianceForge documents are essentially CONOPS documents, where CONOPS are more conceptual than procedures and are focused on providing program-level guidance. A _**CONOPS straddles the territory between an organization's centrally-managed policies/standards and its decentralized, stakeholder-executed procedures**_, where CONOPS serves as expert-level guidance that is meant to run a specific function. Examples of where a CONOPS is useful for providing program-level guidance:
- Risk management (e.g., [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/))
- Vulnerability management (e.g., [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/))
- Incident response (e.g., [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/))
- Business Continuity / Disaster Recovery (e.g., [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/))
- Secure Engineering (e.g., [Security & Privacy By Design (SPBD)](https://complianceforge.com/product/security-by-design-privacy-by-design/))
- Pre-production testing (e.g., [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template))
- Supply Chain Risk Management (SCRM) (e.g., [NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan "NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)"))
Your organization’s Subject Matter Experts (SMEs) are expected to use a CONOPS as a tool to communicate user needs and system characteristics to developers, integrators, sponsors, funding decision makers and other stakeholders.
## Procedures Operationalize Policies & Standards - This Is A Key Concept To Being Both Secure & Compliant
We leverage the **[Operationalizing Cybersecurity Planning Model](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")** in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.).
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations.
- Procedures are by their very nature de-centralized, where control implementation at the team-level is defined to explain how the control is addressed (e.g., network team, desktop support, HR, procurement, etc.).
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.
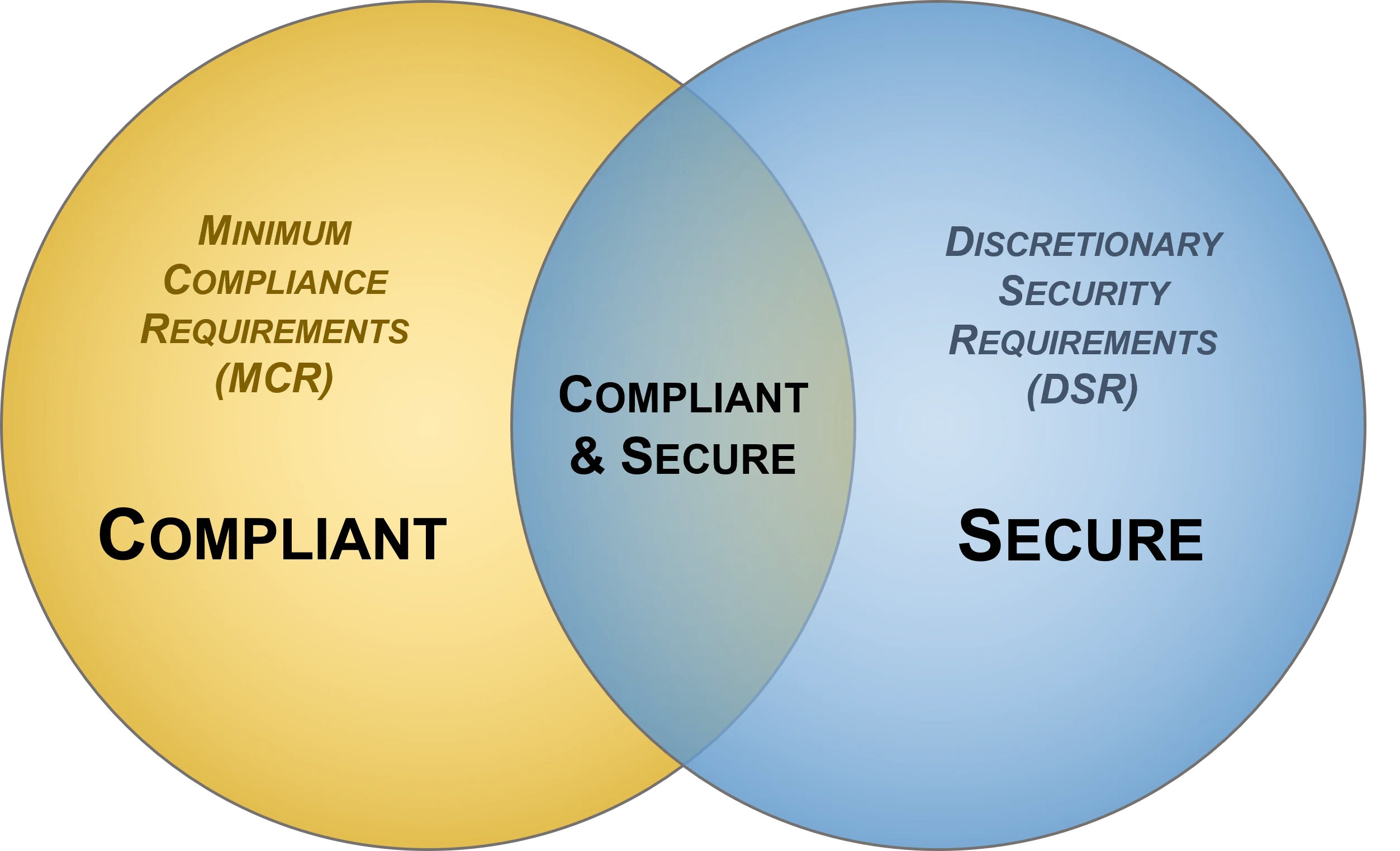
The central focus of any procedures should be a **Capability Maturity Model (CMM)** target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
[](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")
## Policies, Standards, Function-Specific Guidance & Procedures - Our Product Lineup
The following diagram helps demonstrate the layered nature of cybersecurity documentation. Policies & standards set the stage for teams/departments to create and implement programs that are function-specific.
For example:
- A policy on risk will define management's intent to manage risk ( **RA section of NIST 800-53**);
- One of the standards supporting the risk policy might require an annual risk assessment ( **RA-3**);
- Products such as the **Risk Management Program (RMP)** provide the middle-ground between the policy/standard and the actual deliverable risk assessment to provide risk-specific guidance on concepts such as acceptable risk, the methodology of risk management the organization aligns to, who within the organization can sign off on various levels of risk, etc.
If you would like to know more about how this works, please [contact us](https://complianceforge.com/contact-us/) and we'd be happy to further explain how our documentation links together to create comprehensive, linked cybersecurity and privacy documentation.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
#### [Policies & Procedures Bundle - NIST CSF 2.0](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1A - NIST CSF 2.0 (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing the NIST Cybersecurity...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
#### [Policies & Procedures Bundle - ISO 27001/27002](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1B - ISO 27002:2022 (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing NIST SP 800-53 R5...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
#### [Policies & Procedures Bundle - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1C - NIST SP 800-53 R5 Low & Moderate Baselines (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
#### [Policies & Procedures Bundle - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1D - NIST SP 800-53 R5 Low, Moderate & High Baselines (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on...
$8,965.00
$7,172.00 - $11,972.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
- [](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
#### [Compliance Templates - NIST CSF 2.0](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #2 (30% discount)
Is your organization looking for enterprise-class NIST Cybersecurity Framework policy, standard & procedure documentation? This is a bundle that includes the following ten...
$29,075.00
$20,353.00 - $25,153.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
- [](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
#### [Compliance Templates - ISO 27001/27002](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #3 ISO 27002:2022 (35% discount)
Is your organization looking for ISO cybersecurity documentation? This is a bundle that includes the following eleven (11) ComplianceForge...
$33,310.00
$21,652.00 - $26,452.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [](https://complianceforge.com/bundle/risk-bundle-1)
#### [Risk Bundle 1: Assessing & Managing Risk](https://complianceforge.com/bundle/risk-bundle-1)
ComplianceForge
Cybersecurity Risk Bundle #1 (10% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk Management Program (RMP)
Cybersecurity Risk Assessment...
$4,100.00
$3,690.00 - $5,040.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-1)
- [](https://complianceforge.com/bundle/risk-bundle-2)
#### [Risk Bundle 2: Risk, Vulnerability & IR Management](https://complianceforge.com/bundle/risk-bundle-2)
ComplianceForge
Cybersecurity Risk Bundle #2 (25% discount)
This is a bundle that includes the following four (4) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk Management Program (RMP)
Cybersecurity Risk Assessment...
$8,450.00
$6,338.00 - $7,688.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-2)
- [](https://complianceforge.com/bundle/c-scrm-bundle-1/)
#### [C-SCRM Bundle 1: CDPP version (ISO or NIST alignment)](https://complianceforge.com/bundle/c-scrm-bundle-1/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk...
$39,720.00
$39,720.00
$23,832.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-1/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Free Cybersecurity Guides
[Skip to main content](https://complianceforge.com/free-guides/#main-content)
# Free Education Resources - Cybersecurity & Privacy
At ComplianceForge, we pride ourselves on the level of educational material we provide to clients, so that they have a firm understanding of their requirements. We provide these resources at no-cost, so you are free to download them. If you have any questions, please [contact us](https://complianceforge.com/contact-us/).
## [NIST Cybersecurity Framework vs ISO 27002 vs NIST 800-55 vs Secure Controls Framework (SCF)](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf "nist csf vs iso 27001 vs nist 800-53")
Helpful information pertaining to selecting the appropriate cybersecurity framework for your needs, specifically NIST Cybersecurity Framework, ISO 27002, NIST 800-53 and the Secure Controls Framework (SCF).
## [Understanding Cybersecurity & Privacy Requirements: Statutory vs Regulatory vs Contractual Obligations](https://complianceforge.com/free-guides/statutory-vs-regulatory-vs-contractual-compliance "statutory vs regulatory vs contractual compliance")
Free guide to understanding the difference between cybersecurity & privacy compliance requirements, specifically statutory, regulatory and contractual obligations.
## [Understanding Cybersecurity & Privacy Documentation: Policies vs Standards vs Procedures](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure "policy vs standard")
Free guide to understanding the terminology of cybersecurity and privacy documentation, specifically, policies, standards, controls and procedures.
## [Free NIST 800-171 / Cybersecurity Maturity Model Certification (CMMC) Compliance Scoping Guide](https://complianceforge.com/nist-800-171/nist-800-171-cmmc)
We put together several videos and a scoping guide to help businesses understand their needs for complying with NIST 800-171. Those free resources can be found **[here](https://complianceforge.com/nist-800-171/nist-800-171-cmmc)**.
## [EU GDPR Compliance Criteria (EGCC)](https://complianceforge.com/international-data-security-laws/eu-gdpr-compliance)
The European Union General Data Protection Regulation (EU GDPR) is a hot topic and we worked with the Secure Controls Framework (SCF) to develop the EU GDPR Compliance Criteria (EGCC), which is a free tool for businesses to understand their compliance needs and map those requirements to their existing cybersecurity and privacy principles. You can access the EGCC **[here](https://complianceforge.com/international-data-security-laws/eu-gdpr-compliance)**.
## **[Free Guide To Cybersecurity Policies & Standards](https://complianceforge.com/free-guides/free-guide-cybersecurity-policy-standard)**
We wrote a primer on cybersecurity documentation to help explain the components that go into making hierarchical, scalable cybersecurity documentation. That can be found **[here](https://complianceforge.com/free-guides/free-guide-cybersecurity-policy-standard)**.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[free guides statutory vs regulatory vs contractual](https://complianceforge.com/free-guides/statutory-vs-regulatory-vs-contractual/) [complianceforge: compare nist 800](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf) [complianceforge: grc](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure) [begin your compliance journey: nist 800](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-compliance) [cybersecurity documentation guide from complianceforge](https://complianceforge.com/grc/free-guide-cybersecurity-policy-standard) [example cmmc & nist cybersecurity documentation templates](https://complianceforge.com/example-cybersecurity-documentation/) [easy nist 800](https://complianceforge.com/compliance/nist-800-171)
compliance forge, it compliance templates, complianceforge, it compliance templates for policy creation, compliance templates
## NIST 800-171 Compliance Subscription
[Skip to main content](https://complianceforge.com/subscription/ncp#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/257/1501/complianceforge-subscription-nist-800-171-compliance-program-ncp__09509.1740599302.jpg?c=2)
[2 reviews](https://complianceforge.com/subscription/ncp#product-reviews)
$950.00
(You save)
# Subscription - NIST 800-171 Compliance Program (NCP)
SKU:P55-S-NCPUPC:692878857253Availability:Email Delivery Within 1-2 Business Days
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Renew%20Your%20NIST%20800-171%20Compliance%20Subscription%20Today&body=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fncp "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fncp&title=Renew%20Your%20NIST%20800-171%20Compliance%20Subscription%20Today&summary=Renew%20Your%20NIST%20800-171%20Compliance%20Subscription%20Today&source=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fncp "Linkedin")
## NIST 800-171 Compliance Program (NCP) - Annual Subscription for Product Updates
This is a subscription service for existing [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/ "NIST 800-171 Compliance Program (NCP)") clients, who have not skipped one or more years of a subscription, to obtain product updates. Throughout the period of the subscription, you will receive the most current version of the NCP, as it is released to address changes to NIST SP 800-171 and CMMC. The errata will indicate the changes from the previous version. This is a cost-effective method for existing NCP clients to obtain the most current version of the NCP.
- The NCP subscription service entitles the purchaser to 12-months of updates to the NCP.
- The method of delivery of the NCP is email delivery. It includes an errata that describes the additions/changes in the latest version of the documentation.
- This does not include updates to other ComplianceForge products, as those are governed by the [traditional product update process](https://complianceforge.com/faq/product-updates).
Upon payment, you will receive an email containing a ShareFile link with the latest version of the NCP.
## Includes NIST 800-171 Rev 3 Changes
NIST 800 171 Rev 3 was released on 14 May 2024 and it contains significant changes from the NIST 800-171 Rev 2. As stated by [Ron Ross](https://www.linkedin.com/posts/ronrossecure_nist800171-securityrequirements-nist800171a-activity-7192246756338774016-vpjN/?utm_source=share&utm_medium=member_desktop) from NIST, the official government requirements from the Office of Management and Budget (OMB) requires organizations to adopt the most current version of NIST one year after its release. From a NIST 800-171 perspective, this means NIST 800-171 Rev3 will be expected to be used for contracts going forward and at that time NIST 800-171 Rev 2 will be deprecated (outdated). Therefore, it is essential for businesses to start now to implement required controls to comply with NIST 800-171 Rev 3.
Seeing is believing when you look at the differences between NIST 800-171 R2 and R3. The new content in R3 is expected to be a heavy lift by many in the Defense Industrial Base (DIB), but ComplianceForge's NIST 800-171 Compliance Program (NCP) is an affordable and editable collection documentation templates that can help ease the transition to R3.
The following graphic is a summarized version of the differences between NIST 800-171 Rev 2, NIST 800-171A, NIST 800-171 Rev 3 and CMMC 2.0. Please click the graphic to view an extended version of all the differences that the NCP covers:
[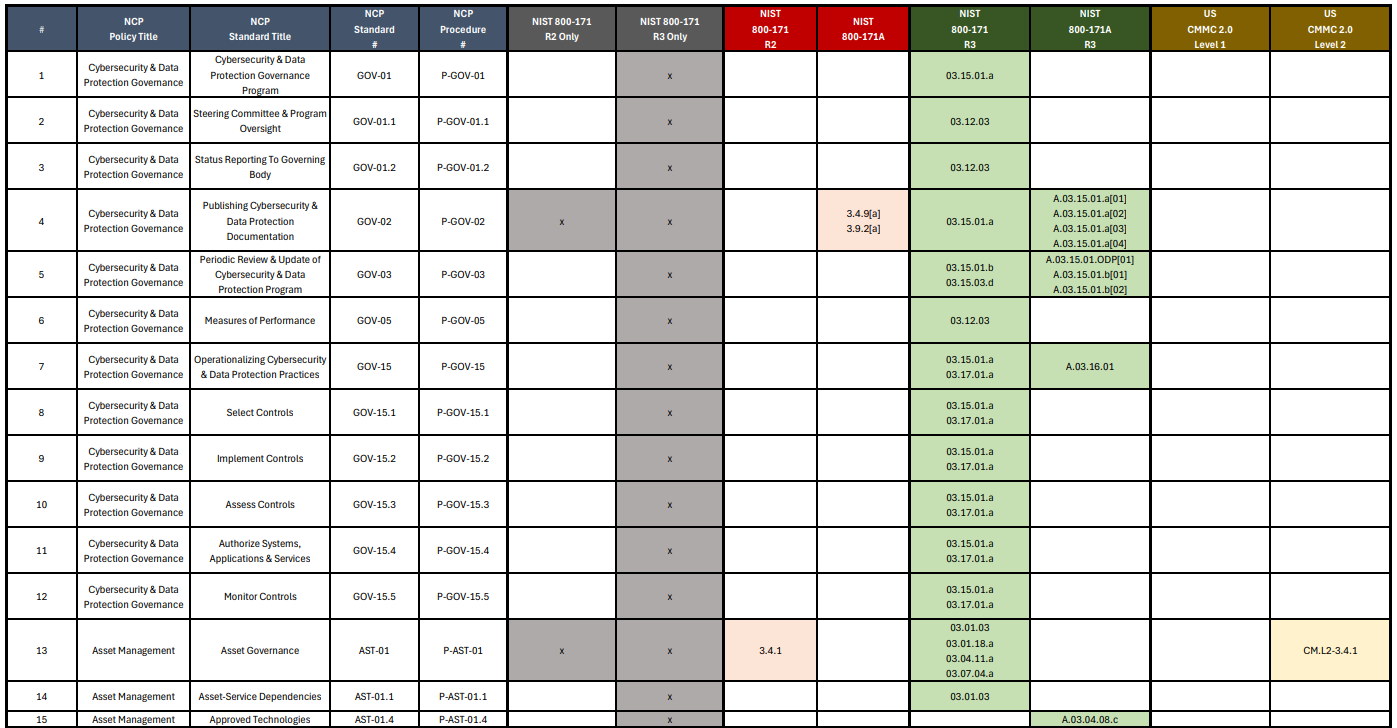](https://complianceforge.com/content/pdf/example-ncp-nist-800-171-r3-crosswalk.pdf "NIST 800-171 R3 changes")
NIST provided the following information on what changed between NIST 800-171 R2 and R3:
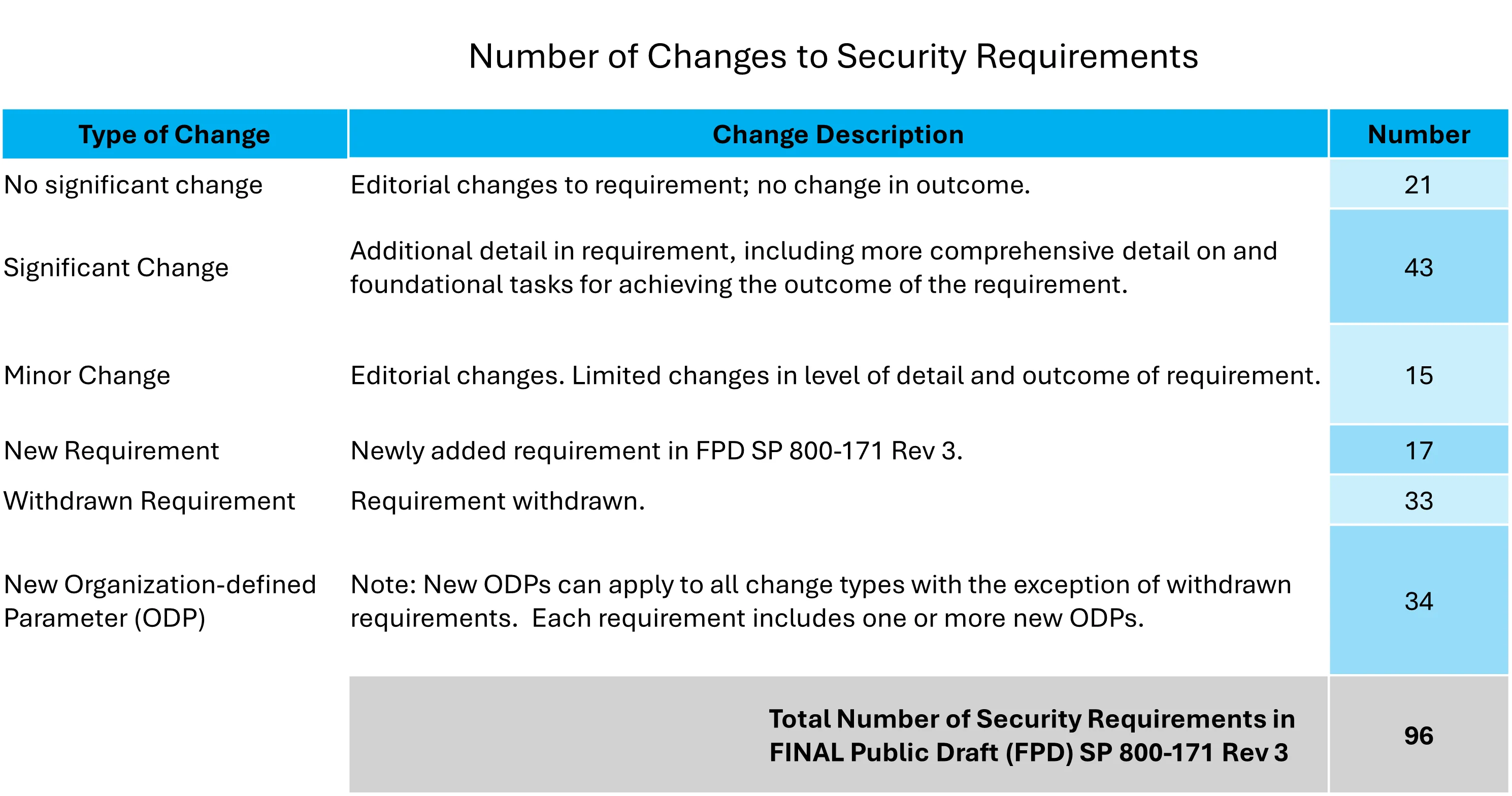
What makes the NCP great is that it saves you time and money! The NCP was designed to make it less painful to upgrade to the latest version of NIST 800-171. One of its key features of the NCP is that it is backwards compatible with NIST 800-171 Rev 2, in addition to providing coverage for NIST 800-171 Rev 3. This is beneficial, since you can demonstrate coverage for the current version of NIST 800-171 (Rev 2), while you implement the new controls from NIST 800-171 Rev 3.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
#### 2 Reviews [Hide Reviews\ \ Show Reviews](https://complianceforge.com/subscription/ncp\#productReviews-content)
- These products have given my team back valuable time to allow them to focus on other activities. Well worth the money spent.
- ComplianceForge has always been fair and generous in providing updates to purchased products. We appreciate their diligence in staying current with this ever-changing field!
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
nist compliance services, it compliance reviews for nist, nist 800 171 compliance services, nist 800 171 email, nist compliance service
## Customer Service Support
[Skip to main content](https://complianceforge.com/customer-service/#main-content)
# Customer Service
## We Strive For Customer Satisfaction!
### CUSTOMER SUPPORT - CONTACT INFORMATION
You can reach us at +1-855-205-8437 or you can [submit a message](https://complianceforge.com/contact-us/ "Contact ComplianceForge") for our support staff. We try to respond back to inquiries the same business day.
### SHIPPING & DELIVERY
All orders are digital in nature, so orders are delivered via email or secure file transfer. There is nothing hard copy for us to send you.
### PRIVACY PRACTICES
Please read through our [PRIVACY PRACTICES](https://complianceforge.com/privacy/) for more information on that subject.
### TERMS & CONDITIONS
Please read through our [TERMS & CONDITIONS](https://complianceforge.com/terms-conditions/ "ComplianceForge Terms & Conditions") for our products.
### REFUNDS, CANCELLATIONS & EXCHANGES
While we have a long history of satisfied and repeat customers, we do not offer refunds, cancellations or exchanges. Since we deal in intellectual property, we have no way of confirming that a customer may have deleted the material we provided and that dictates that we do not offer refunds, cancellations or exchanges.
An order may be cancelled up to the point when the order is shipped (e.g., emailed or made available for download) to fulfill the order. Once the order is fulfilled, no cancellations will be honored.
### ORDERING
Our preferred method or ordering is online via a credit card. If you need to be invoiced through an offline method of payment, we can arrange that. Just select the invoice option at checkout or contact us. Please note that orders made via invoice may not ship until payment is made.
### PAYMENT, PRICING & PROMOTIONS
Prices are subject to change without notice and changes are effective at the time of the change.
### VIEWING ORDERS
Our normal turn-around time for orders is within 1-2 business days for orders. You will receive a confirmation email once the order is completed.
### UPDATING ACCOUNT INFORMATION
Please be sure your contact address is correct so that the files are delivered to the correct recipient. This will also allow you to have access to your account to correct any information in your user profile.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## CSOP Subscription Service
[Skip to main content](https://complianceforge.com/subscription/csop#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/263/1547/complianceforge-subscription-csop-dsp-version__50392.1740599345.jpg?c=2)
No reviews yet
$900.00
(You save)
# Subscription - CSOP (DSP version)
SKU:P52-S-CSOPUPC:692878857239Availability:Email Delivery Within 1-2 Business Days
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Renew%20Your%20CSOP%20(DSP%20Version)%20Subscription%20%7C%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fcsop "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fcsop&title=Renew%20Your%20CSOP%20(DSP%20Version)%20Subscription%20%7C%20ComplianceForge&summary=Renew%20Your%20CSOP%20(DSP%20Version)%20Subscription%20%7C%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fcsop "Linkedin")
## Cybersecurity Standardized Operating Procedures (CSOP) - Annual Subscription for Product Updates
This is a subscription service for existing clients of the [DSP/SCF version of the CSOP](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "DSP/SCF version of the CSOP") to obtain product updates. Due to the dynamic nature of the DSP and the Secure Controls Framework (SCF), the DSP continues to be updated (on nearly a quarterly basis) as new laws, regulations and other frameworks are added. This is a cost-effective method for existing clients of the DSP/SCF version of the CSOP to obtain the most current version of their documentation.
- The subscription service entitles the purchaser to 12-months of updates to the DSP/SCF version of the CSOP, including both the Word and Excel (mappings) documents.
- The method of delivery of the DSP/SCF version of the CSOP is email delivery. It includes an errata that describes the additions/changes in the latest version of the documentation.
- This does not include updates to other ComplianceForge products, as those are governed by the [traditional product update process](https://complianceforge.com/faq/product-updates).
Upon payment, you will receive an email containing a ShareFile link with the latest version of the DSP/SCF version of the CSOP.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Testing Resources
[Skip to main content](https://complianceforge.com/testing/#main-content)
# Testing
Testing 4/16
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Compliance Documentation Templates
[Skip to main content](https://complianceforge.com/brands#main-content)
# Brands
- [](https://complianceforge.com/brands/ComplianceForge)
### [ComplianceForge](https://complianceforge.com/brands/ComplianceForge)
- [](https://complianceforge.com/complianceforge-nist-800-171-cmmc/)
### [ComplianceForge - NIST 800-171 & CMMC](https://complianceforge.com/complianceforge-nist-800-171-cmmc/)
- [](https://complianceforge.com/complianceforge-iso-27001-27002-compliance-documentation-templates/)
### [ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates](https://complianceforge.com/complianceforge-iso-27001-27002-compliance-documentation-templates/)
- [](https://complianceforge.com/complianceforge-nist-800-53-compliance-documentation-templates/)
### [ComplianceForge NIST 800-53 Compliance Documentation Templates](https://complianceforge.com/complianceforge-nist-800-53-compliance-documentation-templates/)
- [](https://complianceforge.com/complianceforge-nist-cybersecurity-framework-compliance-documentation-templates/)
### [ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates](https://complianceforge.com/complianceforge-nist-cybersecurity-framework-compliance-documentation-templates/)
- [](https://complianceforge.com/secure-controls-framework-scf/)
### [Secure Controls Framework (SCF)](https://complianceforge.com/secure-controls-framework-scf/)
- [](https://complianceforge.com/verutus/)
### [Verutus](https://complianceforge.com/verutus/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Cybersecurity Compliance Solutions
[Skip to main content](https://complianceforge.com/compliance-solutions/#main-content)
# Cybersecurity Policies, Standards & Procedures Templates

## Our Cybersecurity & Privacy Documentation Is Designed To Be Scalable, Comprehensive & Efficient
| | |
| --- | --- |
| We leverage the **[Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")** to develop the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care for our clients. This methodology towards documentation addresses the interconnectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. The **[Secure Controls Framework (SCF)](https://www.securecontrolsframework.com/ "Secure Controls Framework")** fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant. In addition to the SCF, this model works with ISO 27002, NIST CSF, NIST 800-171, CIS 20, PCI DSS, NIST 800-53 and other control frameworks.
ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist. You can click on the image below to better understand how we write our documentation that links policies all the way down to metrics. This is a great solution for any organization currently using or migrating to a **Governance, Risk & Compliance (GRC)** or **Integrated Risk Management (IRM)** platform to help automate their governance practices.
Documentation serves as the foundational building blocks for your cybersecurity and privacy program. Without properly-scoped policies to address your applicable statutory, regulatory and contractual obligations, your associated standards and procedures will likely be inadequate to meet your compliance needs. The requires a holistic approach to right-sizing your cybersecurity program to meet your organization's specific compliance and security requirements. |  |
[](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "complianceforge reference model - hierarchical cybersecurity governance framework")
## We Offer Huge Discounts Through Bundling Our Documentation
As visualized in the graphic below, the core of our solutions are based on policies, standards and procedures. From there, we have program-level solutions to address (1) risk management, (2) vulnerability management, (3) incident response & crisis management, (4) supply chain risk management and (5) privacy & secure engineering. Our bundles offer **saving up to 45%** and can provide near-turnkey documenation solutions for your organization. If you have a unique need, please [contact us](https://complianceforge.com/contact-us/ "Information security documentation template savings") since we might be able to work with you on your request.

## Concept of Operations (CONOPS) - Program-Level Guidance
A Concept of Operations (CONOPS) is a user-oriented guidance document that describes the mission, operational objectives and overall expectations from an integrated systems point of view, without being overly technical or formal. A CONOPS is meant to:
- Benefit stakeholders by establishing a baseline “operational concept” to establish a conceptual, clearly-understood view for everyone involved in the scope of operations described by the CONOPS.
- Record design constraints, the rationale for those constraints and to indicate the range of acceptable solution strategies to accomplish the mission and any stated objectives.
- Contain a conceptual view that illustrates the top-level functionality in the proposed process or system.
Several ComplianceForge documents are essentially CONOPS documents, where CONOPS are more conceptual than procedures and are focused on providing program-level guidance. A _**CONOPS straddles the territory between an organization's centrally-managed policies/standards and its decentralized, stakeholder-executed procedures**_, where CONOPS serves as expert-level guidance that is meant to run a specific function. Examples of where a CONOPS is useful for providing program-level guidance:
- Risk management (e.g., [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/))
- Vulnerability management (e.g., [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/))
- Incident response (e.g., [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/))
- Business Continuity / Disaster Recovery (e.g., [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/))
- Secure Engineering (e.g., [Security & Privacy By Design (SPBD)](https://complianceforge.com/product/security-by-design-privacy-by-design/))
- Pre-production testing (e.g., [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template))
- Supply Chain Risk Management (SCRM) (e.g., [NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan "NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)"))
Your organization’s Subject Matter Experts (SMEs) are expected to use a CONOPS as a tool to communicate user needs and system characteristics to developers, integrators, sponsors, funding decision makers and other stakeholders.
## Procedures Operationalize Policies & Standards - This Is A Key Concept To Being Both Secure & Compliant
We leverage the **[Operationalizing Cybersecurity Planning Model](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")** in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.).
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations.
- Procedures are by their very nature de-centralized, where control implementation at the team-level is defined to explain how the control is addressed (e.g., network team, desktop support, HR, procurement, etc.).
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.

The central focus of any procedures should be a **Capability Maturity Model (CMM)** target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
[](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")
## Policies, Standards, Function-Specific Guidance & Procedures - Our Product Lineup
The following diagram helps demonstrate the layered nature of cybersecurity documentation. Policies & standards set the stage for teams/departments to create and implement programs that are function-specific.
For example:
- A policy on risk will define management's intent to manage risk ( **RA section of NIST 800-53**);
- One of the standards supporting the risk policy might require an annual risk assessment ( **RA-3**);
- Products such as the **Risk Management Program (RMP)** provide the middle-ground between the policy/standard and the actual deliverable risk assessment to provide risk-specific guidance on concepts such as acceptable risk, the methodology of risk management the organization aligns to, who within the organization can sign off on various levels of risk, etc.
If you would like to know more about how this works, please [contact us](https://complianceforge.com/contact-us/) and we'd be happy to further explain how our documentation links together to create comprehensive, linked cybersecurity and privacy documentation.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
#### [Policies & Procedures Bundle - NIST CSF 2.0](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1A - NIST CSF 2.0 (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing the NIST Cybersecurity...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
#### [Policies & Procedures Bundle - ISO 27001/27002](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1B - ISO 27002:2022 (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing NIST SP 800-53 R5...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
#### [Policies & Procedures Bundle - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1C - NIST SP 800-53 R5 Low & Moderate Baselines (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-moderate)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
#### [Policies & Procedures Bundle - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1D - NIST SP 800-53 R5 Low, Moderate & High Baselines (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on...
$8,965.00
$7,172.00 - $11,972.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-800-53-r5-high)
- [](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
#### [Compliance Templates - NIST CSF 2.0](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #2 (30% discount)
Is your organization looking for enterprise-class NIST Cybersecurity Framework policy, standard & procedure documentation? This is a bundle that includes the following ten...
$29,075.00
$20,353.00 - $25,153.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf)
- [](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
#### [Compliance Templates - ISO 27001/27002](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #3 ISO 27002:2022 (35% discount)
Is your organization looking for ISO cybersecurity documentation? This is a bundle that includes the following eleven (11) ComplianceForge...
$33,310.00
$21,652.00 - $26,452.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-3-iso-27001-27002)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [](https://complianceforge.com/bundle/risk-bundle-1)
#### [Risk Bundle 1: Assessing & Managing Risk](https://complianceforge.com/bundle/risk-bundle-1)
ComplianceForge
Cybersecurity Risk Bundle #1 (10% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk Management Program (RMP)
Cybersecurity Risk Assessment...
$4,100.00
$3,690.00 - $5,040.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-1)
- [](https://complianceforge.com/bundle/risk-bundle-2)
#### [Risk Bundle 2: Risk, Vulnerability & IR Management](https://complianceforge.com/bundle/risk-bundle-2)
ComplianceForge
Cybersecurity Risk Bundle #2 (25% discount)
This is a bundle that includes the following four (4) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk Management Program (RMP)
Cybersecurity Risk Assessment...
$8,450.00
$6,338.00 - $7,688.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-2)
- [](https://complianceforge.com/bundle/c-scrm-bundle-1/)
#### [C-SCRM Bundle 1: CDPP version (ISO or NIST alignment)](https://complianceforge.com/bundle/c-scrm-bundle-1/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk...
$39,720.00
$39,720.00
$23,832.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-1/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Standards Overview
[Skip to main content](https://complianceforge.com/blog/tag/Standards#main-content)
# Blog
[](https://complianceforge.com/blog/cybersecurity-policies-standards/)
Policies and standards are the foundation for an organization's cybersecurity and privacy program. These components form the alignment with leading practices to help ensure applicable statutory, regul
… [read more](https://complianceforge.com/blog/cybersecurity-policies-standards/)
[](https://complianceforge.com/blog/nist-800171-r3/)
NIST 800-171 Rev 3 was released on 14 May of this year, and it contains significant changes from the NIST 800-171 Rev 2.ComplianceForge has gone ahead updated its NIST Compliance Program (NCP) to incl
… [read more](https://complianceforge.com/blog/nist-800171-r3/)
[](https://complianceforge.com/blog/simplified-cmmc-compliance-policies/)
In the ever-evolving landscape of cybersecurity and data protection, organizations face the formidable challenge of adhering to regulatory frameworks such as NIST 800-171 and CMMC (Cybersecurity Matur
… [read more](https://complianceforge.com/blog/simplified-cmmc-compliance-policies/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## DSP & CSOP Subscription
[Skip to main content](https://complianceforge.com/subscription/dsp-csop#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/291/1504/complianceforge-subscription-dsp-and-csop__18971.1740599305.jpg?c=2)
No reviews yet
$2,600.00
(You save)
# Subscription - DSP & CSOP
SKU:P53-S-DSP-CSOPUPC:692878857246Availability:Email Delivery Within 1-2 Business Days
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Renew%20Your%20DSP%20%26%20CSOP%20Subscription%20for%20Cybersecurity%20Success&body=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp-csop "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp-csop&title=Renew%20Your%20DSP%20%26%20CSOP%20Subscription%20for%20Cybersecurity%20Success&summary=Renew%20Your%20DSP%20%26%20CSOP%20Subscription%20for%20Cybersecurity%20Success&source=https%3A%2F%2Fcomplianceforge.com%2Fsubscription%2Fdsp-csop "Linkedin")
## DSP & CSOP - Annual Subscription for Product Updates
This is a subscription service for existing [DSP & CSOP](https://complianceforge.com/bundle/dsp-bundle-1 "DSP & CSOP (DSP Bundle 1)") clients to obtain product updates. Due to the dynamic nature of the DSP and the Secure Controls Framework (SCF), the DSP continues to be updated (nearly a quarterly basis) as new laws, regulations and other frameworks are added. This is a cost-effective method for existing DSP & CSOP clients to obtain the most current version of the DSP and SCF.
- The subscription service entitles the purchaser to 12-months of updates to the DSP & CSOP, including both the Word and Excel (mappings) documents.
- The method of delivery of the DSP & CSOP is email delivery. It includes an errata that describes the additions/changes in the latest version of the documentation.
- This does not include updates to other ComplianceForge products, as those are governed by the [traditional product update process](https://complianceforge.com/faq/product-updates).
Upon payment, you will receive an email containing a ShareFile link with the latest version of the DSP & CSOP.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## C3PAO Compliance Insights
[Skip to main content](https://complianceforge.com/blog/tag/C3PAO#main-content)
# Blog
[](https://complianceforge.com/blog/ncp-client-success-peerless-electronics/)
ComplianceForge celebrates another client win with Peerless Electronics, Inc. passing a DIBCAC Joint Surveillance Voluntary Assessment (JSVA).From the following LinkedIn article that highlights the su
… [read more](https://complianceforge.com/blog/ncp-client-success-peerless-electronics/)
[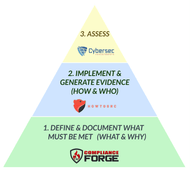](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Bottom Line Up Front (BLUF): Time is money when it comes to CMMC compliance efforts:
If you have poorly-crafted documentation, it will cost you more time & money in implementation and assessment.
… [read more](https://complianceforge.com/blog/cmmc-document-implement-assess/)
[](https://complianceforge.com/blog/nist-800171-cmmc-terms-guide/)
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hie
… [read more](https://complianceforge.com/blog/nist-800171-cmmc-terms-guide/)
Congratulations to Cybersec Investments for passing its DIBCAC audit to become a CMMC Third-Party Assessment
Organization (C3PAO)! This is no small feat of achievement! This success was due in l
… [read more](https://complianceforge.com/blog/dibcac-battled-tested-cmmc-policies/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## CDPAS Overview
[Skip to main content](https://complianceforge.com/blog/tag/cdpas#main-content)
# Blog
[](https://complianceforge.com/blog/thirdparty-cybersecurity-assessment-standards/)
The release of the Cybersecurity & Data Protection Assessment Standards (CDPAS) is important to the cybersecurity industry.
The CDPAS is a cohesive, consistent set of standards to govern cybersec
… [read more](https://complianceforge.com/blog/thirdparty-cybersecurity-assessment-standards/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Industries Served by ComplianceForge
[Skip to main content](https://complianceforge.com/faq/industries-served#main-content)
# ComplianceForge References & Industries Served
## **We stand behind the quality of our work as security professionals**
We've been writing quality security documentation since 2005. In that time, we've served clients across nearly every industry and size. Our clients range from well-known Fortune 500 corporations to small businesses, both within the US and internationally. We've proved time and again that our cybersecurity documentation is flexible enough to work in any organization and can scale accordingly.
## **Industries We Serve - Our Clients Range From the Fortune 500 down to Small & Medium Businesses (SMBs)**
ComplianceForge is "corporate America's dirty little secret" where our documentation solutions are used extensively by some of the most well-known US and international brands. Our clients appreciate ComplianceForge's ability to deliver high-quality, editable documentation the same business day, since it can save thousands of hours of labor and that equates to immediate and significant savings.
Below is a non-exhaustive list of industries where our products have been successfully implemented:
| | | |
| --- | --- | --- |
| **Financial**
\- Certified Public Accountants (CPAs)
\- Financial Planners & Wealth Managers
\- Banks & Credit Unions
\- Bookkeepers
**Technology Companies**
\- Hardware Manufacturers
\- IT Consultants
\- Software Companies
\- Website Developers
\- Managed Service Providers (MSPs)
\- Auditors
\- Cybersecurity Consultants
**Medical**
\- Hospitals
\- Doctors
\- Dentists
\- Physical Therapists
\- Chiropractors
\- Medical Billing
\- Elder Care Facilities
**Consultants**
\- Business Analysts
\- Management Consultants | **Government**
\- Defense Contractors (DoD)
\- Federal Government Contractors
\- Federal Government Agencies
\- State Government Agencies
\- Local Municipalities
\- Regional Airports
\- Law Enforcement
**Legal**
\- Lawyers
\- Court Reporters
\- Privacy Professionals
**Real Estate**
\- Brokers
\- Real Estate Offices
\- Title Companies
\- Developers
\- Property Management
**Utilities**
\- Oil & Natural Gas
\- Coal
\- Electric
\- Nuclear | **Construction & Manufacturing**
\- Commercial
\- Residential
\- Architects
\- Retail Products
\- Fabrication
\- Firearms Industry
**Hospitality & Food Services**
\- Hotels / Resorts
\- Restaurants
\- Casinos / Gaming
\- Coffee Shops
**Retail (B&M) & Services**
\- Health Clubs / Gyms
\- Credit Monitoring / ID Theft
\- Janitorial
\- Human Resources / Recruiting
**Non-Profits & Associations**
\- Chambers of Commerce
\- Clubs
\- Non-Profits
**Education**
\- Universities & Colleges
\- School Districts |
We understand that no one wants to "fly blind" in their purchasing decisions and that is why we offer so many [examples](https://complianceforge.com/example-cybersecurity-documentation "Example Cybersecurity & Privacy Documentation")for your review. In addition to the product examples and videos, we are more than happy to setup a video teleconference session to do a more detailed walkthrough of our documentation to help answer your product-related questions, ensuring you find the right fit for your specific needs.
## Client References
When it comes to providing client names for references, we respect the privacy of our clients and refrain from providing the names of the companies we serve, even if that means losing a sale due to your organization's internal review process that might require client references. Here are our reasons for this business practice:
- **Reason #1**: Many of the well-known and trusted companies that you see and/or use on a daily basis are our clients and we are very proud of that fact. In many ways, we are " _corporate America's dirty little secret_" since we are a leading source for professionally-written cybersecurity and privacy documentation, yet we stay in the shadows as quiet professionals.
- Feedback from our clients is that they appreciate the discretion we provide, since they do not want it public that they outsourced the document writing component of their cybersecurity program.
- We feel it is important to protect the privacy of our clients, since we understand the sensitive nature of a company trusting a third-party to write their core cybersecurity and privacy documentation.
- **Reason #2**: The common **"How easy is it to implement?"** question offers no value to another organization based on the unique nature of how organizations are governed. Governance is as unique as a fingerprint and the number one factor in implementing any documentation we sell is management support:
- If your organization's leadership team takes cybersecurity/privacy governance seriously and is able to assign accountability to getting documentation reviewed, tailored and approved, it is a straightforward process to review and implement the ComplianceForge-written documentation.
- If your organization's leadership team is resistant to change, incompetent and/or suffers from "analysis paralysis" then it will be a slower process, based entirely on the dysfunction inherent to your organization. Keep in mind that if your organization suffers from that type of management dysfunction, the same issues associated with rolling out new documentation apply equally to trying to write the documentation yourself or implementing purchased templates from one of our competitors.
- **Reason #3**: The also common **"Does it meet all of your needs?**" question is a pointless question to ask another organization, since every organization has a different set of needs that are defined by its uniquely-applicable laws, regulations and contractual agreements that it is legally-obligated to comply with. That mix defines a set of **Minimum Security Requirements (MSR)** that are unique to each organization, so one company's requirements will be different from another, even if they are in the same industry, since geographic location and unique business operations impact what is applicable.
- Situational awareness for all applicable statutory, regulatory and contractual obligations can't be avoided. This is crucial to a successful implementation, since your organization needs to be able to address all applicable cybersecurity and privacy needs that are unique to your organization. This also ties directly back to Reason #2 (management support) about doing the right thing from a corporate governance perspective to ensure that all applicable requirements are properly addressed, not just a subset what is required. If you want to learn more about how to address that issue, we have a great reference for you that you can see [**here**](https://complianceforge.com/grc/integrated-controls-management/ "Integrated Controls Management (ICM)").
- For each organization, there is set number of statutory, regulatory and contractual obligations. These objective requirements are unique to each company and can be clearly identified by distilling the requirements from those applicable laws, regulations and reasonable practices. These requirements must be followed by your organization in order to demonstrate "reasonable" practices are in place, so asking another company if a product meets all their specific needs has little applicability to your specific needs. Our mapping documents can significantly help you in this step.
Look at it from the perspective that ComplianceForge is a "toolmaker" that sells specialized tools, no different than a quality hammer or screwdriver. In this context as a toolmaker, we provide basic instructions on how to use these tools, but how you actually use it is outside of our control and completely up to you for how it is implemented. For example, it is no different than how Craftsman or SnapOn can’t prevent someone from using one of their screwdrivers as a pry bar, where the tool is used incorrectly or for purposes it wasn't designed. **Just like any tool, in the right hands and with proper usage you can build anything!**
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## DFARS Compliance Blog
[Skip to main content](https://complianceforge.com/blog/tag/DFARS#main-content)
# Blog
[](https://complianceforge.com/blog/nist-800171-r2-cmmc-kill-chain/)
The CMMC 2.0 & NIST 800-171 R2 version of the CMMC Kill Chain introduces the theory of constraints as it applies to your technical and business limitations.
You can download the NIST 800-171 R3 Ki
… [read more](https://complianceforge.com/blog/nist-800171-r2-cmmc-kill-chain/)
[](https://complianceforge.com/blog/nist-800171-r3/)
NIST 800-171 Rev 3 was released on 14 May of this year, and it contains significant changes from the NIST 800-171 Rev 2.ComplianceForge has gone ahead updated its NIST Compliance Program (NCP) to incl
… [read more](https://complianceforge.com/blog/nist-800171-r3/)
[](https://complianceforge.com/blog/nist-800171-r3-easy-button/)
Professionally-written and editable NIST 800-171 Rev 3 policies, standards, procedures and SCRM Plan template. Work smarter, not harder!Learn more at: https://complianceforge.com/product/nist-800
… [read more](https://complianceforge.com/blog/nist-800171-r3-easy-button/)
[](https://complianceforge.com/blog/nist-sp-800171-r3-requirements/)
ComplianceForge is focused on making the documentation side
of the NIST SP 800-171 R3 upgrade as painless, as possible.
We already have
policies, standards and procedures to address all of the
… [read more](https://complianceforge.com/blog/nist-sp-800171-r3-requirements/)
What is the single greatest threat that your organization faces? SolarWinds-style attacks? APTs? The answer is not what many initially think and the reason is primarily based on the sensitive natur
… [read more](https://complianceforge.com/blog/cybersecurity-management-threat/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Avoid Cybersecurity Negligence
[Skip to main content](https://complianceforge.com/solutions/avoid-negligence#main-content)
# Understanding Cybersecurity Negligence
Negligent behavior will most likely NOT be covered by your insurer in the event you are taken to court. Every insurer uses its own description for negligent behavior. However, in terms of IT security, negligent behavior can be defined as not following industry-recognized best practices or failing to meet ALL compliance requirements. A single negligent breach can close your business forever, because liability insurance may not cover IT security-related negligence. The devastating effects of non-compliance with statutory, regulatory and contractual requirements have the ability to bankrupt a company.
## **DECREASE LIABILITIES & IMPROVE EFFICIENCIES!**
Avoiding Professional Negligence Is Good For Business! The goal of IT security documentation is to build an IT security program for your company that decreases liabilities, while at the same time improves operational efficiencies – this equates to bottom-line savings for your company!
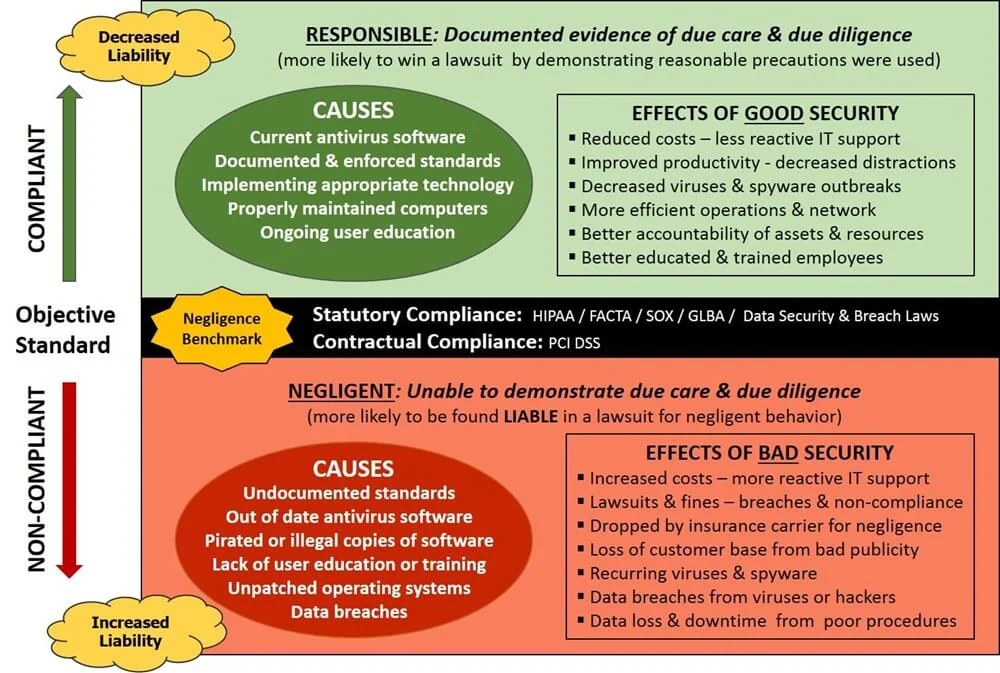
#1 - If your company accepts credit cards, advises on financial matters, provides healthcare services, or maintains any sensitive Personally Identifiable Information (sPII) on clients or employees, then you are responsible for certain compliance requirements. These standards, dictated by the regulation or requirement, establish the objective benchmark for what “reasonably expected” IT security protections should be in place.
#2 - If your company does not meet the minimum standards of a compliance requirement, that deficiency is evidence of negligence. Negligence can be as simple as outdated antivirus software, weak passwords, unencrypted wireless, unpatched operating systems, or inadequate IT security documentation. Ignorance is not an excuse!
#3 - Negligence is demonstrated by a lack of documented due care and due diligence. If you are taken to court, a prosecuting attorney’s aim likely will be to prove negligence. Without documented due care and due diligence, the task is made easier to prove negligence and allow damages to be awarded to the plaintiff.
#4 - The ramifications of being “negligent” can be devastating for a company, since most insurance policies have a “negligence loophole” built in that precludes insurers from having to pay out. The bottom line is your company may have to pay all fines, damages, and legal fees on its own, without any insurance reimbursement.
A single negligent event can cause a business to go out of business forever, since liability insurance may not cover professional negligence for IT security-related incidents. The simple rule of thumb is if you are not in compliance with what you are legally obligated to do, then you are professionally negligent.
## Procedures Operationalize Policies & Standards - This Is A Key Concept To Avoiding Negligence
We leverage the [Operationalizing Cybersecurity Planning Model](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model") in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
[](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## ComplianceForge Blog
[Skip to main content](https://complianceforge.com/blog/tag/ComplianceForge#main-content)
# Blog
[](https://complianceforge.com/blog/scf-training-certifications/)
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SCF) and it is exciting to see SCF-based training options and certifications are now live. This h
… [read more](https://complianceforge.com/blog/scf-training-certifications/)
[](https://complianceforge.com/blog/what-is-complianceforge/)
ComplianceForge specializes in cybersecurity & data protection documentation. We are an industry leader in providing affordable, editable and scalable documentation solutions to support cybersecur
… [read more](https://complianceforge.com/blog/what-is-complianceforge/)
[](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Bottom Line Up Front (BLUF): Time is money when it comes to CMMC compliance efforts:
If you have poorly-crafted documentation, it will cost you more time & money in implementation and assessment.
… [read more](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Solutions Overview
[Skip to main content](https://complianceforge.com/reasons-to-buy#main-content)
# Reasons To Buy ComplianceForge Products
We offer a wide-assortment of cybersecurity policies, standards, procedures and more, since we understand that businesses have unique needs that cannot be met by just one product. While companies want to align with a single cybersecurity framework such as NIST 800-53, ISO 27002 or NIST Cybersecurity Framework, it is getting much more common for companies to have to juggle multiple frameworks and that requires scalable documentation.

## ComplianceForge Continues To Contribute To The Profession!
ComplianceForge is a business accelerator - we strive to provide cybersecurity and privacy solutions to save our clients both time and money to meet their specific cybersecurity and privacy documentation needs. We continuously innovate and share those ideas to better the industry. In additional to helping launch the [Secure Controls Framework (SCF)](https://complianceforge.com/GRC%20Is%20a%20Plan,%20Do,%20Check%20&%20Act%20(PDCA)%20Adventure%20%E2%80%93%20That%20Is%20A%20Concept%20That%20Should%20Be%20Embraced,%20Not%20Fought%20Against%20GRC%20most%20often%20deals%20with%20legally-binding%20requirements,%20so%20it%20is%20important%20to%20understand%20that%20negligence%20is%20situationally-dependent.%20For%20example,%20an%20intoxicated%20driver%20who%20gets%20behind%20the%20wheel%20acting%20negligently.%20However,%20when%20sober,%20that%20same%20individual%20is%20a%20champion%20race%20car%20driver%20who%20is%20highly-skilled%20and%20would%20not%20be%20considered%20incompetent%20in%20any%20regard.%20In%20this%20example,%20driving%20intoxicated%20constitutes%20a%20negligent%20act%20and%20shows%20that%20negligence%20has%20nothing%20to%20do%20with%20being%20incompetent.%20The%20point%20is%20to%20demonstrate%20that%20an%20organization%20can%20employ%20many%20highly-competent%20personnel,%20but%20even%20competent%20people%20can%20behave%20in%20a%20negligent%20manner.%20GRC%20fundamentally%20exists%20to%20help%20an%20organization%20avoid%20circumstances%20that%20could%20be%20construed%20as%20negligent%20acts.%20%20%20Considering%20how%20business%20practices%20continuously%20evolve,%20so%20must%20cybersecurity%20practices.%20The%20Plan,%20Do,%20Check%20&%20Act%20(PDCA)%20process%20enables%20the%20GRC%20function%20to%20continuously%20evaluate%20risks,%20threats%20and%20performance%20trends,%20so%20that%20the%20organization's%20leadership%20can%20take%20the%20necessary%20steps%20to%20minimize%20risk%20by%20modifying%20how%20people,%20processes%20and%20technology%20work%20together%20to%20keep%20everything%20both%20secure%20and%20operational.%20The%20PDCA%20approach%20(also%20referred%20to%20as%20the%20Deming%20Cycle)%20is%20a%20logical%20way%20to%20conceptualize%20how%20GRC%20works:%20%20Plan.%20The%20overall%20GRC%20process%20beings%20with%20planning.%20This%20planning%20will%20define%20the%20policies,%20standards%20and%20controls%20for%20the%20organization.%20It%20will%20also%20directly%20influence%20the%20tools%20and%20services%20that%20an%20organization%20purchases,%20since%20technology%20purchases%20should%20address%20needs%20that%20are%20defined%20by%20policies%20and%20standards.%20Do.%20Arguably,%20this%20is%20the%20most%20important%20section%20for%20cybersecurity%20and%20privacy%20practitioners.%20Controls%20are%20the%20%E2%80%9Csecurity%20glue%E2%80%9D%20that%20make%20processes,%20applications,%20systems%20and%20services%20secure.%20Procedures%20(also%20referred%20to%20as%20control%20activities)%20are%20the%20processes%20how%20the%20controls%20are%20actually%20implemented%20and%20performed.%20The%20Secure%20Controls%20Framework%20(SCF)%20can%20be%20an%20excellent%20starting%20point%20for%20a%20control%20set%20if%20your%20organization%20lacks%20a%20comprehensive%20set%20of%20cybersecurity%20and%20privacy%20controls.%20Check.%20In%20simple%20terms,%20this%20is%20situational%20awareness.%20Situational%20awareness%20is%20only%20achieved%20through%20reporting%20through%20metrics%20and%20reviewing%20the%20results%20of%20audits/assessment.%20Act.%20This%20is%20essentially%20risk%20management,%20which%20is%20an%20encompassing%20area%20that%20deals%20with%20addressing%20two%20main%20concepts%20(1)%20real%20deficiencies%20that%20currently%20exist%20and%20(2)%20possible%20threats%20to%20the%20organization. "Secure Controls Framework (SCF)") as an independent company, ComplianceForge is notable for:
- [Integrated Controls Management (ICM)](https://complianceforge.com/grc/integrated-controls-management/ "Integrated Controls Management (ICM)")
- [Hierarchical Cybersecurity Governance Framework (ICM)](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/)
- [Security Metrics Reporting Model (SMRM)](https://complianceforge.com/free-guides/security-metrics-reporting-model/)
- [Change Kill Chain](https://complianceforge.com/free-guides/cybersecurity-supply-chain-risk-management-scrm)
The most compelling reason to buy from Compliance Forge is that we have invested thousands of hours into our cybersecurity and privacy solutions with one goal in mind - to help our clients get a handle on their Information Security needs.
As cybersecurity professionals, we live and breathe security on a daily basis! Our driving ideal has been to remove the complexity of information security policies, enabling you to implement our solutions as easily as possible. If you look at the examples, you will notice the level of thought and detail that goes into our offerings. We offer solutions that are tailored to your business.
For the prices we charge, you simply will not find comparable, comprehensive IT security policies. Granted, there are websites with lower cost security policies, but they are incomplete when compared to our Cybersecurity & Data Protection Program (CDPP) or PCI DSS Policy. When we see competing solutions offering "Bronze, Silver & Gold" package levels, we know we are doing the right thing by providing solutions that are rooted in the actual requirements and best practices - we know that "a standard is a standard for a reason" and anything less could leave you exposed. We fundamentally disagree with models that offer varying levels of compliance coverage, since the lesser versions offer only partial coverage to businesses that buy them. Partial solutions are less than what would be considered "industry-recognized best practices" and are simply a waste of your money. Additionally, they should be avoided since they fail to comprehensively offer protection from both a compliance and holistic security program perspective.

A central theme across nearly all cybersecurity-related statutory, regulatory and contractual requirements is a need to focus on secure engineering. This expectation for operationalizing security and privacy principles is found in the following requirements:
- NIST 800-53 - SA-8
- NIST Cybersecurity Framework - PR.IP-2
- ISO 27002 - 14.2.5 & 18.1.4
- Defense Federal Acquisition Regulations Supplement (DFARS) 252.204-7012 (NIST 800-171) - 3.13.1 & 3.13.2
- Federal Acquisition Regulations (FAR) 52.204-21 - 4
- National Industrial Security Program Operating Manual (NISPOM) - 8-302 & 8-311
- SOC2 - CC3.2
- Generally Accepted Privacy Principles (GAPP) - 4.2.3, 6.2.2, 7.2.2 & 7.2.3
- New York State Department of Financial Service (DFS) - 23 NYCRR 500.08
- Payment Card Industry Data Protection Standard (PCI DSS) - 2.2
- Center for Internet Security Critical Security Controls (CIS CSC) - 1.2, 5.9, 6.2, 6.3, 6.4, 6.5, 7.1, 7.2, 7.3, 7.4, 7.5, 7.6, 7.7, 7.8, 8.6, 9.1, 9.2, 9.3, 9.4, 9.5, 9.6, 11.4, 11.5, 11.6, 11.7, 13.4, 13.5 & 16.5
- European Union General Data Protection Regulation (EU GDPR) - 5 & 25
## **Best Practices & Common Compliance Frameworks**
Our Cybersecurity & Data Protection Program (CDPP) and Digital Security Program (DSP) offerings are a professionally-written and cohesive compilation of Information Security policies, standards, procedures and guidelines designed with one purpose in mind - to secure your business with written information security policies that will meet your specific legal requirements. The CDPP and DSP are founded on industry recognized best practices. Each control objective has a documented reference to its specific source of best practice so you have the ability to prove your policies are supported by industry standards.
We know the policies you need to have in place to meet the requirements for compliance. We follow proven, internationally-recognized standards for what Information Security policies should consist of. Many competitor sites unfortunately offer solutions that will leave you exposed and unprepared - when keeping your company in business and protected is the priority, there is no room for amateur solutions. The Cybersecurity & Data Protection Program (CDPP) and Digital Security Program (DSP) stand out from the competition in their coverage, depth, and price.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Cybersecurity Compliance Insights
[Skip to main content](https://complianceforge.com/blog/tag/SCF#main-content)
# Blog
[](https://complianceforge.com/blog/thirdparty-cybersecurity-assessment-standards/)
The release of the Cybersecurity & Data Protection Assessment Standards (CDPAS) is important to the cybersecurity industry.
The CDPAS is a cohesive, consistent set of standards to govern cybersec
… [read more](https://complianceforge.com/blog/thirdparty-cybersecurity-assessment-standards/)
[](https://complianceforge.com/blog/dsp-version-20223-release/)
ComplianceForge is pleased to announce the release of version 2022.3 of the Digital Security Program (DSP). There is some new content and minor refinement of the risk catalog to standardize wording
… [read more](https://complianceforge.com/blog/dsp-version-20223-release/)
This episode of “Coffee Thoughts With Tom” ponders the question “CMMC was never a “real maturity model” so what does a NIST 800-171 Capability Maturity Model (CMMC) look
… [read more](https://complianceforge.com/blog/essential-guide-to-cmmc-nist-sp-800171-compliance/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Documentation Examples
[Skip to main content](https://complianceforge.com/example-cybersecurity-documentation/#main-content)

# Example Cybersecurity & Privacy Policies, Standards, & Procedures
We are proud of the documentation that we produce for our clients and we encourage you to take a look at our example cybersecurity documentation. **Each product page has at least one PDF example** so that you can view the quality of ComplianceForge products for yourself - if you scroll down on the product pages you will find an "examples" section (generally located about 1/4 of the way down each product page).
Let us help you be successful! For many IT / cybersecurity / privacy professionals, when they refer to a “policy” they are really meaning a “standard” and that creates a great deal of confusion when discussing cybersecurity documentation, since those are not interchangeable terms. The most common questions we get pertain to " [word crimes](https://complianceforge.com/example-cybersecurity-documentation/#word_crimes "cybersecurity word crimes")" that revolve around the misunderstanding what a policy, standard or procedure is meant to be, based on industry-recognized definitions. There are a lot of bad practices and we demonstrate what the words actually mean, so that everyone can operate from the same baseline understanding of the terminology, since in compliance, words have meanings and terminology matters.
Cybersecurity & data protection documentation needs to usable. This means the documentation needs to be written clearly, concisely and in a business-context language that users can understand. By doing so, users will be able to find the information they are looking for and that will lead to IT security best practices being implemented throughout your company. Additionally, having good cybersecurity documentation can be “half the battle” when preparing for an audit, since it shows that effort went into the program and key requirements can be easily found. The PDF document shown below provides two, side-by-side examples from policies all the way through metrics, so you can see what the actual content looks like.
[](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-documentation-template-examples.pdf "example cybersecurity policies standards procedures controls metrics")
## Word Crimes: Start From A Solid Understanding Of What Right Looks Like For Cybersecurity Documentation
The [Hierarchical Cybersecurity Governance Framework ( **HCGF**)](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "ComplianceForge Reference Model") is the "ComplianceForge Reference Model" of cybersecurity and privacy documentation. The HCGF is a documentation model that leverages industry-recognized terminology to logically arrange these documentation components into their rightful order. This model creates an approach to architecting documentation that is concise, scalable and comprehensive. When that is all laid out properly, an organization's cybersecurity and data protection documentation should be hierarchical and linked from policies all the way through metrics. The swimlane diagram shown below (click for a larger PDF) defines the terminology and demonstrates the linkages between these various documentation components.
It all starts with influencers – these influencers set the tone and establish what is considered to be due care for cybersecurity & data protection operations. For external influencers, this includes statutory requirements (laws), regulatory requirements (government regulations) and contractual requirements (legally-binding agreements) that companies must address. For internal influencers, these are business-driven and the focus is more on management’s desire for consistent, efficient and effective operations:
- Alignment with business strategy; and
- Meeting business goals & objectives.
[](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")
## Not Sure Which Framework Is The "Best" Cybersecurity Framework For Your Needs?
The concept of a "best" cybersecurity framework is misguided, since the most appropriate framework to align with is entirely dependent upon your business model. The applicable laws, regulations and contractual obligations that your organiation must comply with will most often point you to one of these cybersecurity frameworks to kick off the discussion about " **_Which framework is most appropriate for our needs?_**":
- [**NIST Cybersecurity Framework (NIST CSF)**](https://complianceforge.com/solutions/nist-csf "NIST Cybersecurity Framework (NIST CSF) policies standards procedures")
- [**ISO 27001/27002**](https://complianceforge.com/solutions/iso-27001-27002 "ISO 27001/27002 policies standards procedures")
- [**NIST SP 800-171**](https://complianceforge.com/cmmc-nist-800-171-templates/ "NIST 800-171 CMMC policies standards procedures") (e.g., CMMC compliance)
- [**NIST SP 800-53**](https://complianceforge.com/solutions/nist-sp-800-53-r5-moderate "NIST SP 800-53 policies standards procedures") (moderate or high baselines); or
- **[Secure Controls Framework (SCF)](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/ "Secure Controls Framework (SCF) policies standards procedures")**(cybersecurity & privacy metaframework / common controls framework)
[](https://complianceforge.com/content/pdf/start-here-cybersecurity-framework-selection.pdf "Cybersecurity Frameworks NIST CSF vs ISO 27001 27001 vs NIST 800171 vs NIST 800-53 vs SCF")
In the context of good cybersecurity documentation, components are hierarchical and build on each other to build a strong governance structure that utilizes an integrated approach to managing requirements. Well-designed documentation is generally comprised of six (6) main parts:
1. Policies establish management’s intent;
2. Control Objectives identify leading practices (mapped to requirements from laws, regulations and frameworks);
3. Standardsprovide quantifiable requirements;
4. Controls identify desired conditions that are expected to be met (requirements from laws, regulations and frameworks);
5. Procedures / Control Activities establish how tasks are performed to meet the requirements established in standards and to meet controls; and
6. Guidelines are recommended, but not mandatory.
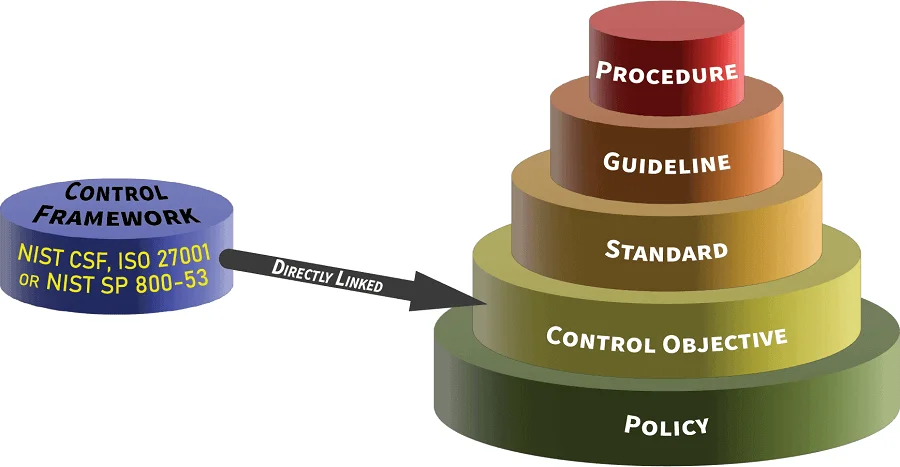
**The " [ComplianceForge Reference Model](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "ComplianceForge Method")" for writing documentation is entirely based on industry-recognized "best practices" according to terminology definitions from [NIST, ISO, ISACA and AICPA](https://complianceforge.com/content/pdf/start-here-cybersecurity-documentation-overview.pdf#page=6 "cybersecurity documentation definitions").** This approach is designed to encourage clear communication by clearly defining cybersecurity and privacy documentation components and how those are linked. This comprehensive view identifies the primary documentation components that are necessary to demonstrate evidence of due diligence and due care. It addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. The Secure Controls Framework ( **SCF**) fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant. ComplianceForge simplified the concept of the hierarchical nature of cybersecurity and privacy documentation that visualizes the unique nature of these components, as well as the dependencies that exist.
To demonstrate that bold claim, we wrote the " [START HERE: A guide to understanding cybersecurity and data protection documentation](https://complianceforge.com/content/pdf/start-here-cybersecurity-documentation-overview.pdf "understanding cybersecurity documentation word crimes")". This follows the schema shown above (the [Hierarchical Cybersecurity Governance Framework (HCGF)](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/ "Hierarchical Cybersecurity Governance Framework")) that demonstrates the linkages from policies all the way through metrics. The following guide is designed to demonstrate "what right looks like" for cybersecurity and privacy documentation, so that it is at the same time scalable, concise and provides comprehensive coverage. You can [jump straight to the definitions on page 6](https://complianceforge.com/content/pdf/start-here-cybersecurity-documentation-overview.pdf#page=6 "NIST ISO ISACA AICPA cybersecurity glossary") if you are curious.
[](https://complianceforge.com/content/pdf/start-here-cybersecurity-documentation-overview.pdf "Guide To Understanding Cybersecurity & Data Protection Documentation")
Cybersecurity & data protection documentation needs to usable – it cannot just exist in isolation. This means the documentation needs to be written clearly, concisely and in a business-context language that users can understand. By doing so, users will be able to find the information they are looking for and that will lead to IT security best practices being implemented throughout your company. Additionally, having good cybersecurity documentation can be “half the battle” when preparing for an audit, since it shows that effort went into the program and key requirements can be easily found.

## Understanding Basic Cybersecurity & Data Protection Documentation Components
It is imperative that cybersecurity and privacy documentation be scalable and flexible, so it can adjust to changes in technology, evolving risk and changes within an organization. The modern approach to cybersecurity and privacy documentation is being modular, where it is best to link to or reference other documentation, rather than replicated content throughout multiple policy or standard documents. Not only is "traditional model of cybersecurity documentation" inefficient, but it can also be confusing and lead to errors. Additionally, when it comes to audits/assessments, it is true that "time is money" where inefficient, cumbersome documentation has a very real financial cost associated with the amount of time it takes an auditor/assessor to parse through the documentation. Concise, efficient documentation can pay for itself in the cost-savings from a single audit/assessment. Additionally, having good cybersecurity documentation can be “half the battle” when preparing for an audit, since it shows that effort went into the program and key requirements can be easily found.
A good example of documentation that is scalable, modular and hierarchical is in the diagram below:
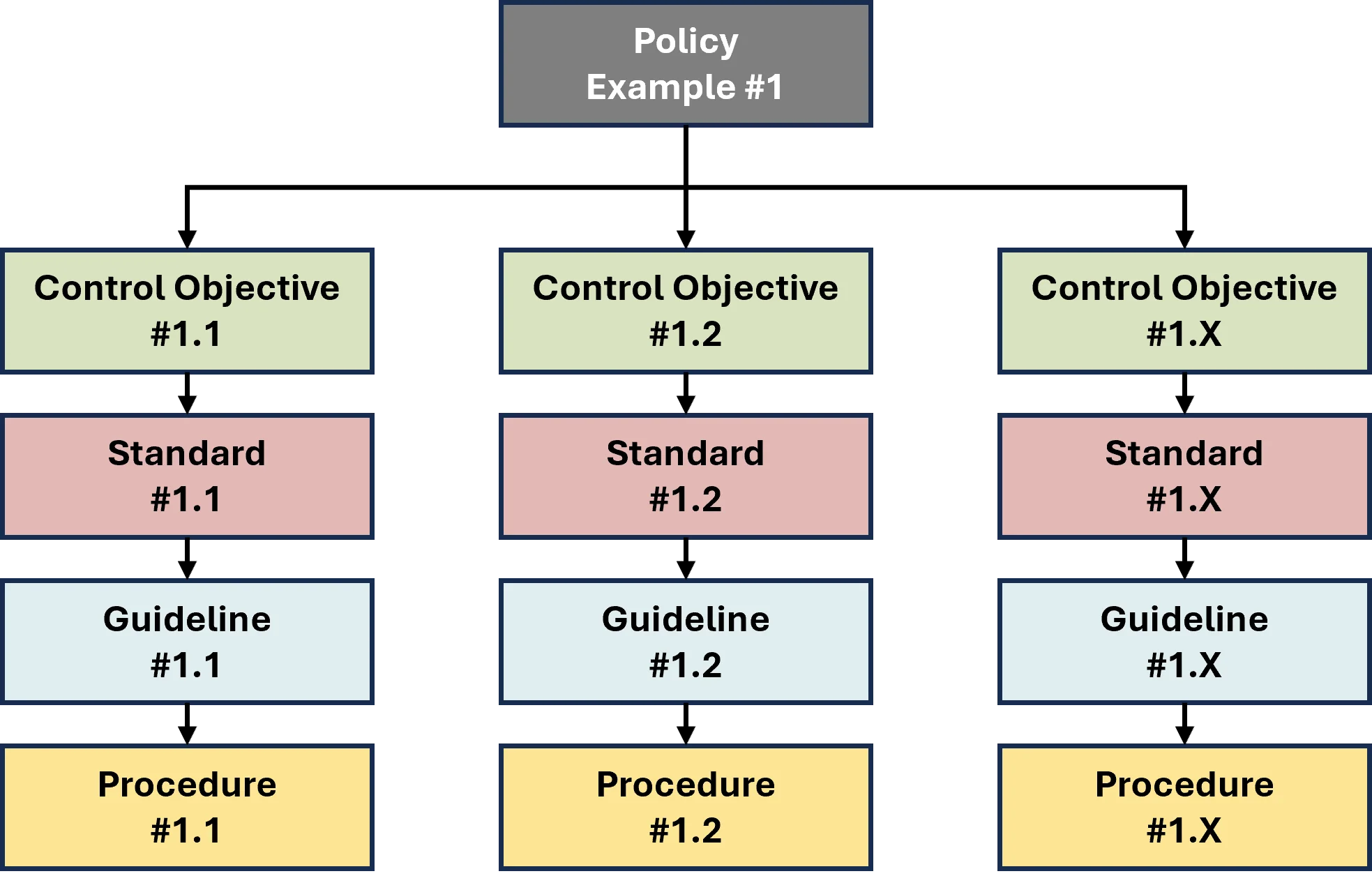
## External vs Internal Documentation
**External Frameworks**
Industry frameworks are often referred to as a standard. In reality, most frameworks are merely a repository of specific controls that are organized by control families (e.g., NIST CSF, ISO 27002, NIST SP 800-171, NIST SP 800-53, etc.). For example, while **NIST SP 800-53 R5** is called a "standard" it is made up of 1,189 controls that are organized into 20 control families (e.g., Access Control (AC), Program Management (PM), etc.). These controls are what make up NIST SP 800-53 as a "framework" that an organization can use as a guide to develop its internal policies and standards that allow it to align with those expected practices.
**Internal Cybersecurity & Privacy Documentation**
An organization is expected to identify cybersecurity and privacy principles (e.g., industry framework) that it wants to align its cybersecurity and privacy program with, so that its practices follow reasonably-expected controls. For example, to help make an organization's alignment with its NIST SP 800-53 R5 more straightforward and efficient:
- A policy that corresponds to each of the control families that defines executive leadership's statement of management intent for that specific area of focus (e.g., access control, compliance, physical security, etc.).
- Control objectives provide a 1-1 mapping to address a specific control (e.g., AC-3, AC-7, etc.). For each control, there should be a control objective.
- Granular standards addresses the particulars necessary to accomplish the objective of the control (hence the name "control objective").
- Guidelines may or may not be needed to provided additional details about the standard.
- Procedures (e.g., Standardized Operating Procedures ( **SOP**)) describes how the standard is operationalized to meet the intent of the control.
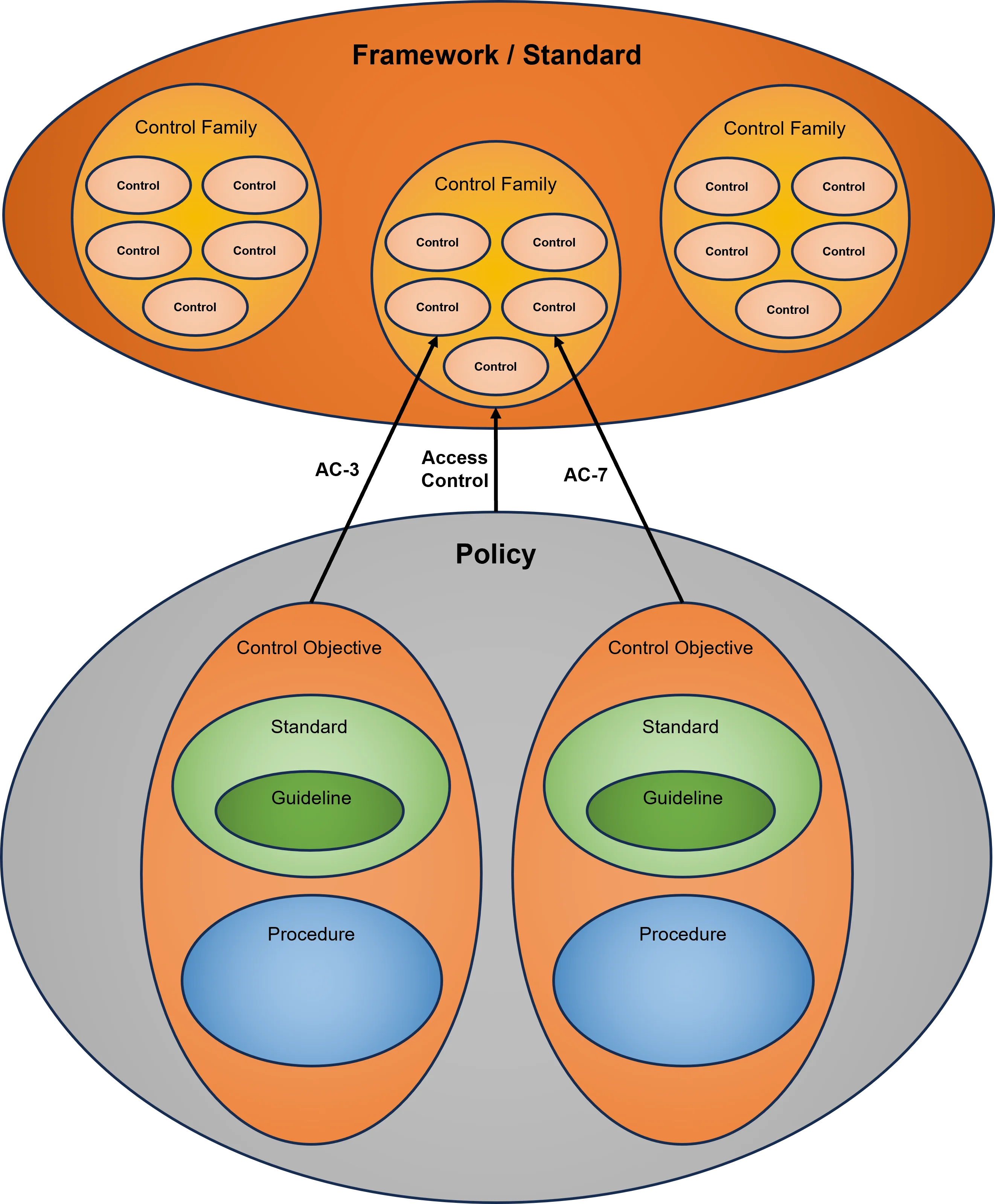
## ComplianceForge Sells Far More Than Just Cybersecurity Policies & Standards!
ComplianceForge sells a wide range of documentation from core policies and standards, to function-specific "program level" documentation to procedures. We encourage you to read through the product pages to learn more.

If you have any product-related questions, please let us know. We are happy to help answer your questions!
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) Policy Template - Editable Policies & Standards
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
#### [C-SCRM Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
ComplianceForge
NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
#### [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
ComplianceForge
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
#### [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
ComplianceForge
Cybersecurity Risk Management Program (RMP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
#### [Cybersecurity Risk Assessment (CRA) Template](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
ComplianceForge
Cybersecurity Risk Assessment Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$1,925.00 - $6,725.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
- [](https://complianceforge.com/product/integrated-incident-response-program/)
#### [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/integrated-incident-response-program/)
ComplianceForge
Integrated Incident Response Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/integrated-incident-response-program/)
- [](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
#### [Procedures Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST 800-53 R5 HIGH & FedRAMP LOW/MODERATE/HIGH Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website...
$5,995.00 - $10,795.00
[Choose Options](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[cybersecurity documentation guide from complianceforge](https://complianceforge.com/grc/free-guide-cybersecurity-policy-standard) [affordable cybersecurity templates for compliance standards](https://complianceforge.com/cybersecurity-templates/policies-standards-controls/) [complianceforge: grc](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure) [affordable nist cybersecurity solutions by complianceforge](https://complianceforge.com/solutions/nist-csf-policies-standards-procedures/) [cybersecurity best practices documentation templates](https://complianceforge.com/cybersecurity-templates/) [free guides](https://complianceforge.com/free-guides/)
security documentation, cyber security documentation, cyber security document
## CMMC Compliance Blog
[Skip to main content](https://complianceforge.com/blog/tag/CCA#main-content)
# Blog
[](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Bottom Line Up Front (BLUF): Time is money when it comes to CMMC compliance efforts:
If you have poorly-crafted documentation, it will cost you more time & money in implementation and assessment.
… [read more](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Enhanced Digital Security
[Skip to main content](https://complianceforge.com/bundle/dsp-bundle-2#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/200/1523/secure-controls-framework-scf-dsp-bundle-2-enhanced-digital-security-documentation__19830.1740599323.jpg?c=2)
No reviews yet
$29,485.00
$19,165.00
(You save
$10,320.00
)
# DSP Bundle 2: Enhanced Digital Security Documentation
SKU:DSP-B2-NOUPC:692878857161Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=DSP%20Bundle%202%3A%20Enhanced%20Digital%20Security%20Documentation&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-2 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-2&title=DSP%20Bundle%202%3A%20Enhanced%20Digital%20Security%20Documentation&summary=DSP%20Bundle%202%3A%20Enhanced%20Digital%20Security%20Documentation&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-2 "Linkedin")

## Digital Security Plan (DSP) Bundle \#2 - ENHANCED DIGITAL SECURITY(35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are focused on operationalizing the Secure Controls Framework (SCF):
1. [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
2. [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
3. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)
4. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
5. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
6. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
7. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
The DSP and its corresponding [Cybersecurity Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity Operating Procedures (CSOP)"), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices by providing GRC policies and GRC procedures. This bundle builds on the core documentation that comes in [DSP bundle #1](https://complianceforge.com/bundle/dsp-bundle-1 "Secure Controls Framework Policy") and adds much-needed operational guidance on risk management, vulnerability management and incident response. Not only do you get the policies, standards, controls, procedures and metrics that form the basis of security and privacy operations, but you get program-level guidance that addresses common areas of compliance with risk, vulnerability and incident management. The end result with this DSP bundle is a comprehensive, customizable, easily-implemented set of documentation that your company needs to establish a scalable, "best in class" cybersecurity and privacy program. Being Microsoft Word documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you - just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")

## Cost Savings Estimate - DSP Bundle \#2
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 2,900 internal staff work hours, which equates to a cost of approximately **$295,000** staff-related expenses. This is about 24-40 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 2,200 contractor work hours, which equates to a cost of approximately **$734,500**. This is about 15-30 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 6% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
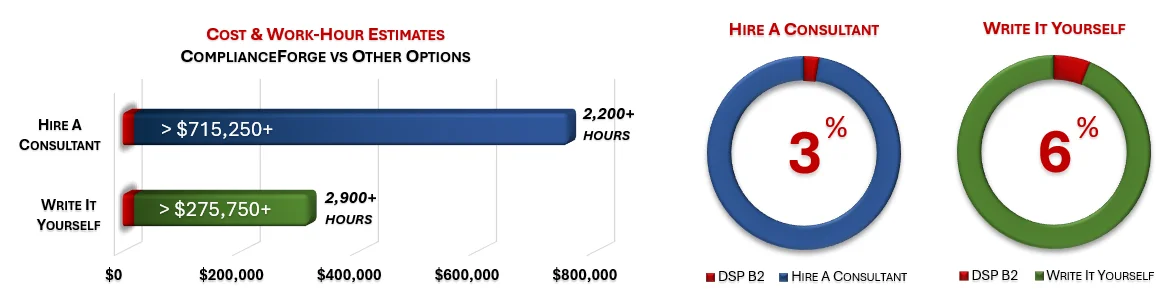
## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.
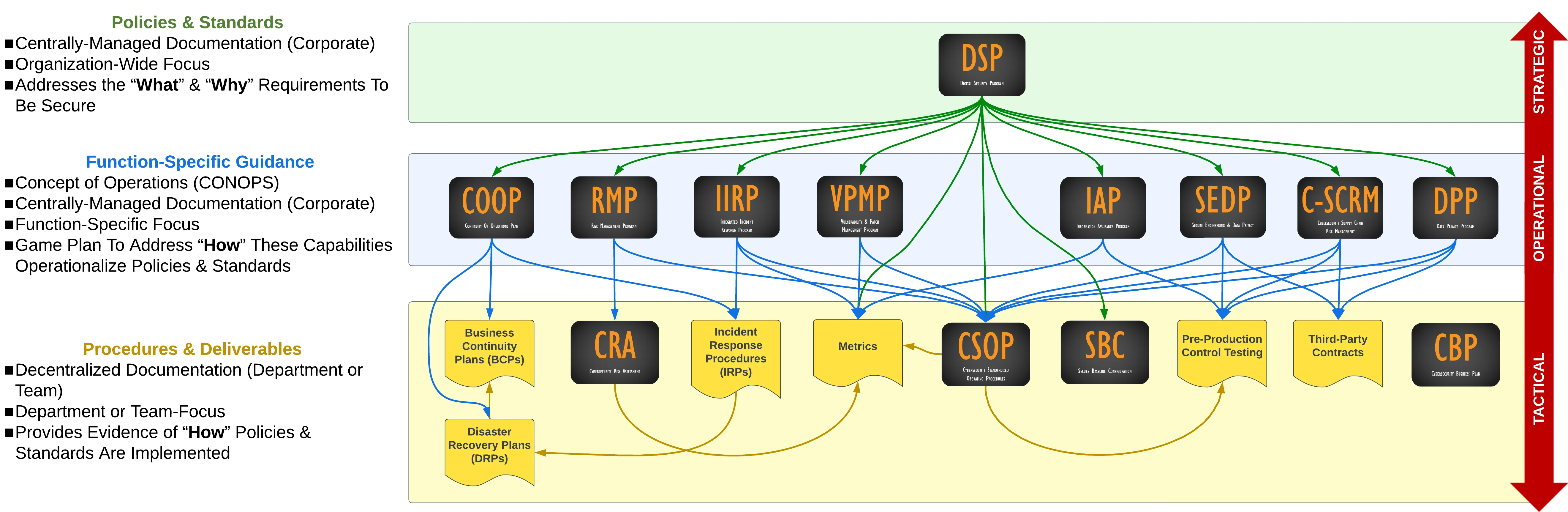
## Products Included in DSP Bundle \#2
| | |
| --- | --- |
|  | [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the [**Secure Controls Framework (SCF)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework Policy"), so you can easily align your **policies**, **standards** and **metrics** with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template")
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=ae4zy9gddvcr)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Control Applicability
[Skip to main content](https://complianceforge.com/grc/cybersecurity-control-applicability/#main-content)
# Cybersecurity Control Applicability
The Secure Controls Framework (SCF) approaches the concept of control applicability in a rational manner where cybersecurity and data protection controls primarily apply to one (1) of the following five (5) functions:
## People, Processes, Technologies, Data & Facilities (PPTDF)
1. **People** \- The control directly applies to humans (e.g., training, background checks, non-disclosure agreements, etc.).
2. **Processes** \- The control directly applies to administrative work performed (e.g., processes, procedures, administrative documentation, etc.).
3. **Technologies** \- The control directly applies to systems, applications and services (e.g., secure baseline configurations, patching, etc.).
4. **Data** \- The control directly applies to data protection (e.g., encrypting sensitive and/or regulated data, applying metatags, etc.).
5. **Facilities** \- The control directly applies to infrastructure assets (e.g., physical access, HVAC systems, visitor control, etc.).
While the importance of robust cybersecurity controls cannot be overstated, the applicability of those controls is sometimes in question. These examples help demonstrate the applicable nature of controls:
- An employee (people) cannot have a secure baseline configuration applied.
- An Incident Response Plan (IRP) (process) cannot sign a NDA, use MFA or be patched.
- You cannot apply end user training to a firewall (technology).
- Controlled Unclassified Information (CUI) (data) cannot be assigned roles and responsibilities.
- Your data center (facility) cannot undergo employee background screening.
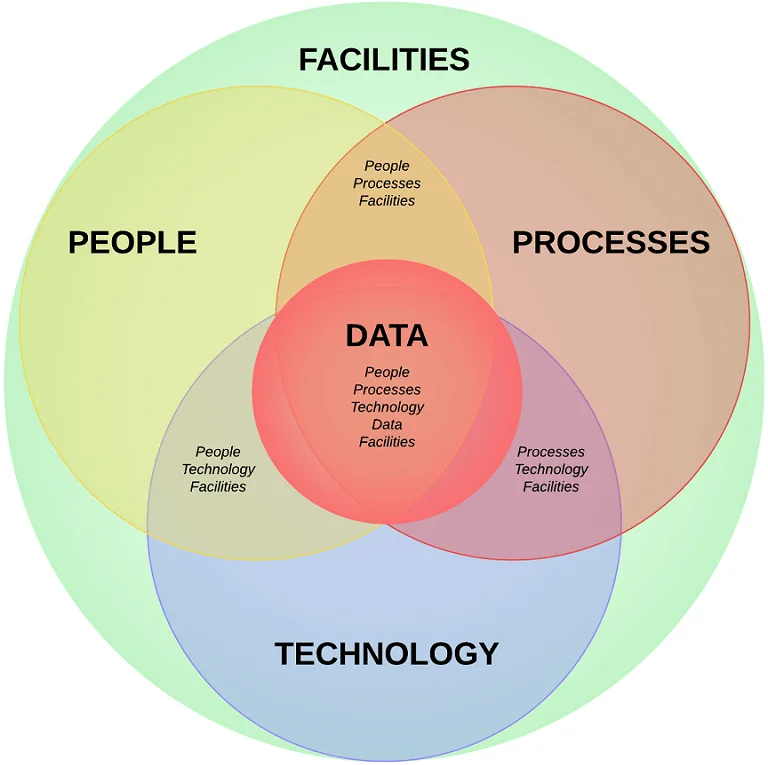
The PPTDF model, encompassing People, Processes, Technology, Data, and Facilities, provides a comprehensive approach to cybersecurity control applicability, as described below:
## People
People are often considered the weakest link in cybersecurity. Human error, negligence, or malicious intent can lead to significant vulnerabilities. To mitigate these risks, organizations implement human-specific controls such as:
- Security Awareness Training: Educating employees about cybersecurity best practices and potential threats.
- Access Controls: Enforcing the principle of least privilege to restrict access based on job roles.
- User Authentication and Authorization: Implementing strong authentication mechanisms and carefully managing user permissions.
## Processes
Effective cybersecurity processes are essential for identifying, responding to, and mitigating threats. Common processes that exist as controls include:
- Incident Response Plans: Establishing well-defined processes to respond promptly and effectively to security incidents.
- Regular Audits and Assessments: Conducting periodic assessments to identify vulnerabilities and measure compliance with security policies.
- Change Management: Implementing controls to manage changes in technology and processes to avoid unintended security consequences.
## Technologies
The technological aspect of cybersecurity involves deploying and configuring tools to protect against threats. Common technologies that exist as controls include:
- Network Defenses: Filtering and monitoring network traffic to prevent unauthorized access (e.g., firewalls, Intrusion Protection Systems (IPS), Data Loss Prevention (DLP), etc.).
- Endpoint Protection: Installing antimalware software, Endpoint Detection and Response (EDR) tools to secure individual devices, etc.
- Encryption: Safeguarding data in transit and at rest through robust encryption mechanisms.
## Data
Data is at the heart of the PPTDF model, making data protection truly the central focus of cybersecurity controls. There are many types of data that are considered sensitive/regulated that include, but are not limited to:
- Controlled Unclassified Information (CUI),
- Federal Contract Information (FCI),
- Personally Identifiable Information (PII),
- Cardholder Data (CHD),
- Export-Controlled Data (ITAR / EAR),
- Electronic Protected Health Information (ePHI),
- Intellectual Property (IP),
- Critical Infrastructure Information (CII),
- Attorney-Client Privilege Information (ACPI) and
- Student Educational Records (FERPA).
These data types have specific controls that are dictated by applicable laws, regulations or contractual obligations and include:
- Data Classification: Data must be categorized to apply the appropriate security measures.
- Limited Access: Data must be protected by limiting logical and physical access to data to individuals and systems that have a legitimate business need.
- Redundant, Obsolete/Outdated, Toxic or Trivial (ROTT) Data: Data must be trustworthy, based on the data's currency, accuracy, integrity and/or applicability.
- Availability: Data must be available, which involves regularly backing up data and establishing effective data recovery mechanisms that protects the integrity and confidentiality of the data being backed up and recovered.
## Facilities
Physical security is often overlooked but plays a crucial role in overall cybersecurity and data protection. Common physical controls include:
- Physical Access Control (PAC): Restricting physical access to any facility where systems or data exist. PAC exists in more than datacenters and corporate offices. The concept of PAC extends to home offices and Work From Anywhere (WFA) workers who still have an obligation to apply physical security protections to their systems and data.
- Surveillance Systems: Monitoring and recording activities within facilities to detect and deter unauthorized access.
- Environmental Controls: Maintaining optimal conditions for hardware to prevent damage or disruptions.
The PPTDF model shows that a multi-faceted approach to control applicability is indispensable, where it can create a resilient defense against a myriad of physical and cyber threats. A proactive stance in implementing and refining these controls will be crucial in securing the ever-expanding digital frontier.
There are no products listed under this category.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Compliance Resources
[Skip to main content](https://complianceforge.com/testing-april/#main-content)
# testing april
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Secure Controls Framework Overview
[Skip to main content](https://complianceforge.com/secure-controls-framework-scf/#main-content)

# Secure Controls Framework (SCF)
Sort By:Featured ItemsNewest ItemsBest SellingA to ZZ to ABy ReviewPrice: AscendingPrice: Descending
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/scf-dsp-procedures-csop/)
#### [Procedures Template - DSP / SCF](https://complianceforge.com/product/scf-dsp-procedures-csop/)
Secure Controls Framework (SCF)
Cybersecurity Standardized Operating Procedures (CSOP) DSP \| SCF Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on...
$6,400.00 - $11,200.00
[Choose Options](https://complianceforge.com/product/scf-dsp-procedures-csop/)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
#### [CMMC Bundle 4: Levels 1-3 (DSP & SCF)](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
Secure Controls Framework (SCF)
NIST 800-171 & CMMC 2.0 Compliance Bundle #4 - EXPERT CMMC 2.0 Levels 1-3 (45% discount)
Is your organization looking to achieve CMMC compliance? This is a bundle that...
$47,490.00
$26,120.00 - $30,920.00
[Choose Options](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## CMMC Bundle 1
[Skip to main content](https://complianceforge.com/bundle/cmmc-bundle-1#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/266/1514/complianceforge-nist-800-171-and-cmmc-cmmc-bundle-1-level-1-cmmc-2.0-l1-and-far-52.204-21__20465.1740599314.jpg?c=2)
No reviews yet
$6,680.00
$5,344.00
(You save
$1,336.00
)
# CMMC Bundle 1: Level 1 (CMMC 2.0 L1 & FAR 52.204-21)
SKU:CMMC-B1-L1-NOUPC:692878857116Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=CMMC%20Bundle%201%3A%20Level%201%20(CMMC%202.0%20L1%20%26%20FAR%2052.204-21)&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fcmmc-bundle-1 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fcmmc-bundle-1&title=CMMC%20Bundle%201%3A%20Level%201%20(CMMC%202.0%20L1%20%26%20FAR%2052.204-21)&summary=CMMC%20Bundle%201%3A%20Level%201%20(CMMC%202.0%20L1%20%26%20FAR%2052.204-21)&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fcmmc-bundle-1 "Linkedin")
## **CMMC 2.0 Level 1 - CMMC 2.0 L1 & FAR 52.204-21 Policies, Standards & Procedures - CMMC Level 1 (20% discount)**
This bundle is as streamlined as we've been able to make it for those needing to demonstrate compliance with Cybersecurity Maturity Model Certification (CMMC) Level 1. If you need to address CUI requirements, then the [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/) is the most appropriate solution for your needs.
The CMMC Level 1 Bundle includes two (2) ComplianceForge products:
1. CMMC Level 1 Policies & Standards
2. CMMC Level 1 Procedures
The CMMC 2.0 Level 1 & FAR 52.204-21 Policies, Standards & Procedures bundle is narrowly tailored for CMMC Level 1 organizations.
## FAR 52.204-21 + CMMC Level 1
FAR 52.204-21 cybersecurity requirements form the basis for what CMMC Level 1 practices. While FAR 52.204-21 has 15 requirements, CMMC Level 1 adds 2 additional requirements. The CMMC Bundle #1 contains coverage for both FAR 52.204-21 and CMMC 2.0 Level 1 requirements.
## **Why Are These Products Part of The Bundle?**
At ComplianceForge, we sometimes receive questions from customers, asking "Does ComplianceForge provide CMMC policy documentation?" or "Does ComplianceForge provide FAR cybersecurity policy documentation?" The short answer is, yes, we do procide this documentation, but before we can point them where to find the documentation, we must first know what requirements the customers has, as there are difference CMMC levels. This bundle is designed for organizations that need a cost-effective and timely solution to demonstrate compliance with CMMC Level 1. Our solutions is a customizable, easily-implemented set of documentation that your company needs to demonstrate compliance with CMMC 2.0 L1 & FAR 52.204-21 requirements. Being Microsoft Word documents, you have the ability to make edits, as needed.
Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Products Included in CMMC Bundle \#1:
| | |
| --- | --- |
|  | **CMMC 2.0 L1 & FAR 52.204-21 Policies & Standards**
- These policies & standards are in an editable Microsoft Word format.
- Content is specific to CMMC 2.0 L1 & FAR 52.204-21 requirements.
- Under each of the policies are standards that support those policy statements.
- Includes many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- Bring Your Own Device ( **BYOD**) usage guidelines
- and more templates |
|  | **CMMC 2.0 L1 & FAR 52.204-21 Procedures**
- These procedures are in an editable Microsoft Word document.
- The structure of the procedures make it easy to map to the corresponding policies and standards. This is an expectation that companies have to demonstrate how cybersecurity controls are actually implemented.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## DSP vs CDPP Overview
[Skip to main content](https://complianceforge.com/faq/dsp-vs-cdpp#main-content)
# DSP vs CDPP
## **A common question is “What is the difference between the [CDPP](https://complianceforge.com/cybersecurity-policies-standards-controls "Cybersecurity & Data Protection Program (CDPP)")and the [DSP](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")?”**
ANSWER: In simple terms, the **[Cybersecurity & Data Protection Program (CDPP)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "Cybersecurity & Data Protection Program (CDPP)")**is designed to address a single, specific framework (e.g., [ISO 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/ "ISO 27001 / 27002 - Policies & Standards (CDPP)"), [NIST 800-53](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-53 R5 (high) - Policies & Standards (CDPP)") or the [NIST Cybersecurity Framework](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/ "NIST CSF - Policies & Standards (CDPP)")), whereas the **[Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")**is designed to address multiple frameworks as a hybrid, "best-in-class" metaframework.
- The CDPP is designed to help a company _align with a single cybersecurity framework_(e.g., NIST CSF, ISO 27002 or NIST 800-53).
- The DSP is designed for companies that need to _align with multiple cybersecurity and privacy frameworks_ and cannot be constrained by aligning with just ISO or NIST. This is also applicable to companies that need to efficiently manage both cybersecurity and privacy principles.
### Privacy Considerations
If your organization needs to address **EU GDPR**, **CCPA**, or any other privacy requirement, you should seriously consider the DSP instead of the CDPP, since the DSP contains a robust privacy section, in addition to its cybersecurity sections. When considering any of the newer laws, regulations and industry frameworks, they can be considered _"two-sided coins"_ in regards to the interconnected nature of privacy and cybersecurity where there is a clear expectation that in addition to a formal cybersecurity program, that your organization also maintains a privacy program to maintain "secure practices" for both privacy and security:
- The determination of "secure practices" is left to the organization to define. In most cases, this means alignment with ISO 27001/27002, NIST Cybersecurity Framework, or NIST 800-53 as the framework used to define what "right" looks like from a cybersecurity perspective. The SCF also is applicable, since you can align with multiple frameworks.
- The determination of "privacy practices" are also left to the organization to define. Just like with cybersecurity frameworks, there are numerous privacy frameworks an organization can choose from. The DSP contains mappings to multiple privacy frameworks and even leverages the SCF's **[Data Privacy Management Principles](https://securecontrolsframework.com/data-privacy-management-principles/ "SCF - Data Privacy Management Principles")**.
- The selection of security and privacy frameworks for an organization to align with is a business decision and is not dictated by technology. Those frameworks are meant to support the organization's overall business operations and strategic goals. The selection of frameworks is foremost a business decision.
- These expectations for both privacy and cybersecurity apply not only to processors and controllers of data, but supply chains as well. An organization's internal "secure practices" are meaningless if there are unmanaged third-party service providers that have unfettered access to sensitive data or the systems / applications / services that store, transmit and process personal data. The DSP maps to over 100 laws, regulations and frameworks, so its flexibility is unmatched.
When you lay out the various frameworks in a spectrum from "weaker" to "robust" the DSP provides the most comprehensive coverage. However, some companies only need/want to align with a single framework.
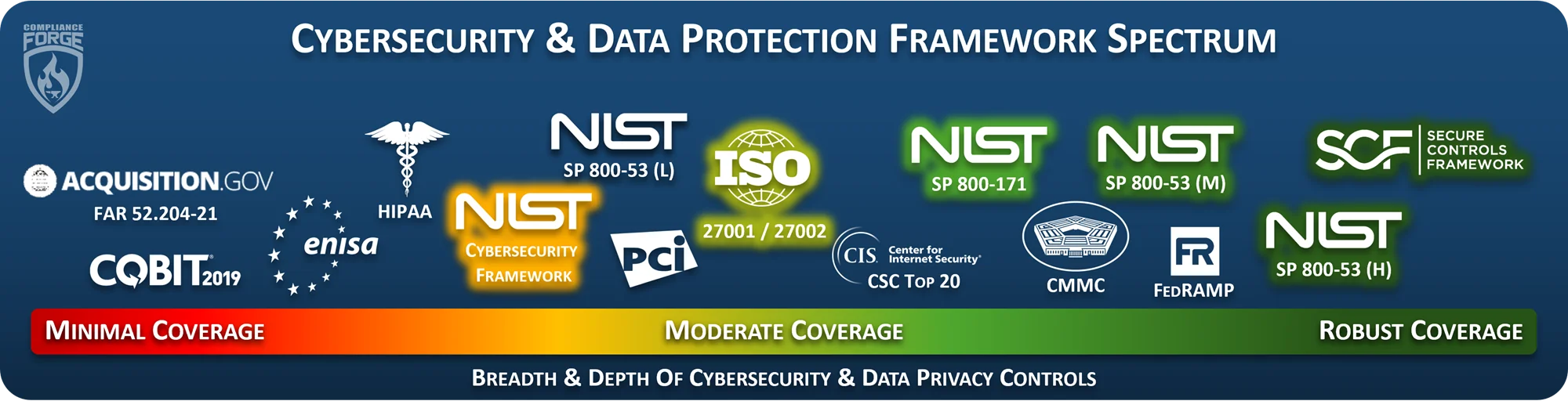
There are two main factors that will assist you in determining which product is best suited to your business: (1) content and (2) functionality. However, while both cover common requirements, only your organization's needs (current AND future needs in terms of meeting specific statutory, regulatory and contractual requirements) will ultimately determine which is the best fit for you.
| | | |
| --- | --- | --- |
| **DSP vs CDPP Comparison** | **** |  |
| **Editable documentation** | **** | **** |
| **Policies** | **** | **** |
| **Control Objectives** | **** | **** |
| **Standards** | **** | **** |
| **Guidelines** | **** | **** |
| **Procedures**(separate product is available - CDPP or DSP Cybersecurity Standardized Operating Procedures (CSOP)) | [****](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "DSP SCF procedures") | [****](https://complianceforge.com/standardized-operating-procedures/ "NIST 800-53 ISO 27002 NIST CSF CMMC procedures") |
| **Controls** | **** | **** |
| **Metaframework**(multiple cybersecurity & privacy framework alignment) | **** | **** |
| **Single cybersecurity framework**(e.g., NIST CSF 2.0, ISO 27001/27002, NIST 800-53 or NIST 800-171) | **** | **** |
| **Privacy coverage**(e.g., GDPR, CCPA, etc.) | **** | **** |
| **Metrics**(including KPIs & KRIs) | **** | **** |
| **Capability Maturity Model** | **** | **** |
| **Reference Mapping**(Excel spreadsheet) | **** | **limited to CDPP framework selected** |
| **GRC-Importable**(Microsoft Word & Excel formats) | **** | **** |
### CONTENT
In terms of content, the scope of the DSP surpasses both versions of the CDPP, due to its structure and additional materials.
- **“Best-In-Class” Structure** – The CDPP versions are designed to stay true to NIST CSF, ISO 27002 or NIST 800-53, so their scopes are constrained by those specific frameworks.
- We designed the DSP to avoid similar constraints by creating a hybrid framework that takes of best components of leading frameworks, while avoiding their weaknesses.
- The DSP currently covers over 100 laws, regulations and industry frameworks to allow alignment with multiple requirements with one document!
- The DSP is directly mapped to the [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework (SCF)"), which is a free resource for companies that need cybersecurity and privacy controls.
- **Controls & Metrics** \- While both the CDPP and DSP contain policies, control objectives, standards and guidelines, the DSP in unique in that it contains controls and metrics (including KPIs and KRIs).
- This added content can save a company several months’ work from developing their own control wording and associated metrics!
- This allows organizations to rapidly advance their cybersecurity program’s maturity by being able to PROVE that security is in place through metrics reporting!
Graphically, the difference in content can be seen in the comparison below (note – this just shows a fraction of what the DSP is mapped to, due to space limitations).
### FUNCTIONALITY
In terms of functionality, the CDPP and DSP both come in Microsoft Word formats, so that it is easy to edit for your needs and gives our clients a wide range of methods to share the content. The difference is in added functionality that can save hundreds of hours in staff and consultant time!
- With the DSP, we did something different where we also put the DSP’s content into a Microsoft Excel format, so that it is importable into other tools or databases.
- Specifically, this Excel formatting makes it a breeze to import it into a Governance, Risk & Compliance (GRC) tool, such as Archer, RSAM, MetricStream, MyVCM, ZenGRC, ServiceNow, etc.
- If you are currently using a GRC tool or are planning one within the next few years, the DSP is the product you will want to buy, since it can save you hundreds of hours in formatting and preparation time.
One of the biggest differences in functionality is in the controls used by the CDPP vs the DSP. The CDPP does its best to stay true to the aligned framework (e.g., NIST CSF, ISO 27002 or NIST 800-53). However, the DSP leverages the Secure Controls Framework (SCF) to map to over 100 different laws, regulations and industry frameworks.
## US GOVERNMENT & DOD CONTRACTORS
On a daily basis, we receive questions from government / DoD contractors about both NISPOM and NIST 800-171 (DFARS). Both the NIST 800-53 version of the CDPP and the DSP will allow an organization to comply with both NISPOM and NIST 800-171. Just as explained above, the DSP will just give you far more usefulness if you want to mature your security program beyond policies and standards.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## ComplianceForge Sitemap
[Skip to main content](https://complianceforge.com/sitemap.php#main-content)
# Sitemap
- ## Pages
- [Customer Service](https://complianceforge.com/customer-service/)
- [Blog](https://complianceforge.com/blog/)
- [Contact ComplianceForge](https://complianceforge.com/contact-us/)
- [About Us](https://complianceforge.com/about-us/)
- [Privacy](https://complianceforge.com/privacy/)
- [Terms & Conditions](https://complianceforge.com/terms-conditions/)
- [ComplianceForge - View All Pages](https://complianceforge.com/sitemap.php)
- [Errata](https://complianceforge.com/errata/)
- [What Is The NIST 800-53 R5 Low & Moderate Baseline Version Of The CDPP?](https://complianceforge.com/what-is-the-nist-800-53-r5-low-moderate-baseline-version-of-the-cdpp/)
- [What Is The Data Privacy Program (DPP)?](https://complianceforge.com/data-privacy-program-video/)
- [NIST CSF vs ISO 27002 vs NIST 800-171 vs NIST 800-53 vs Secure Controls Framework Video](https://complianceforge.com/nist-csf-vs-iso-27002-vs-nist-800-171-vs-nist-800-53-vs-secure-controls-framework-video/)
- [Bundle Policies Procedures Video](https://complianceforge.com/bundle-policies-procedures-video/)
- [What Is The PCI DSS Policies & Standards?](https://complianceforge.com/what-is-the-pci-dss-policies-standards/)
- [What Is The NIST 800-53 R5 Low, Moderate & High Baseline Version Of The CDPP?](https://complianceforge.com/what-is-the-nist-800-53-r5-low-moderate-high-baseline-version-of-the-cdpp/)
- [What Is The Cybersecurity Business Plan (CBP)?](https://complianceforge.com/what-is-the-cybersecurity-business-plan-cbp/)
- [Policies & Procedures Bundle Video](https://complianceforge.com/policies-procedures-bundle-video/)
- [What Is The NIST CSF Version Of The CDPP?](https://complianceforge.com/what-is-the-nist-csf-version-of-the-cdpp/)
- [What Is The Risk Management Program (RMP)?](https://complianceforge.com/what-is-the-risk-management-program-rmp/)
- [What Is The ISO 27001 / 27002 Version Of The CSOP?](https://complianceforge.com/what-is-the-iso-27001-27002-version-of-the-csop/)
- [What Is The NIST 800 171 Compliance Program (NCP)?](https://complianceforge.com/what-is-the-nist-800-171-compliance-program-ncp/)
- [Home](https://complianceforge.com/)
- [Show All](https://complianceforge.com/sitemap/pages/)
- ## Categories
- [Start Here](https://complianceforge.com/start-here/) - [Governance Risk & Compliance (GRC) Content](https://complianceforge.com/governance-risk-compliance-grc-content/) - [Cybersecurity Documentation Fundamentals](https://complianceforge.com/grc/free-guide-cybersecurity-policy-standard)
- [NIST 800-53 vs ISO 27002 vs NIST CSF vs SCF](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf)
- [Policies vs Standards vs Controls vs Procedures](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure)
- [Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/)
- [Cybersecurity Risk Management & Materiality](https://complianceforge.com/grc/cybersecurity-risk-management-materiality/)
- [Cybersecurity Control Applicability](https://complianceforge.com/grc/cybersecurity-control-applicability/)
- [Secure Controls Framework (SCF)](https://complianceforge.com/scf/secure-controls-framework-scf-download/) - [SCF CAP - Editable SCF-Based Documentation](https://complianceforge.com/scf/scf-cap-editable-scf-based-documentation/)
- [Integrated Controls Management (ICM) Model](https://complianceforge.com/scf/integrated-controls-management/)
- [Cybersecurity & Data Privacy by Design (C\|P)](https://complianceforge.com/scf/cybersecurity-data-privacy-by-design-principles/)
- [Risk Management Model (C\|P-RMM)](https://complianceforge.com/scf/cybersecurity-data-privacy-risk-management-model/)
- [Capability Maturity Model (C\|P-CMM)](https://complianceforge.com/scf/capability-maturity-model/)
- [NIST 800-171 & CMMC - Where Do I Start?](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-compliance) - [Understanding ITAR vs EAR vs FAR vs DFARS](https://complianceforge.com/nist-800-171/itar-vs-ear-vs-far-vs-dfars-cui-cmmc/)
- [Understanding Unclassified vs Classified Data](https://complianceforge.com/nist-800-171/unclassified-vs-classified-data-types/)
- [CMMC Kill Chain - A Prioritized Approach](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-kill-chain/)
- [NIST 800-171 R3 Transition Guide](https://complianceforge.com/nist-800-171/nist-800-171-r3-transition-guide/)
- [Non-Federal Organization (NFO) Controls](https://complianceforge.com/nist-800-171/nfo-controls)
- [Show All](https://complianceforge.com/sitemap/categories)
- ## Brands
- [ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates](https://complianceforge.com/complianceforge-nist-cybersecurity-framework-compliance-documentation-templates/)
- [ComplianceForge NIST 800-53 Compliance Documentation Templates](https://complianceforge.com/complianceforge-nist-800-53-compliance-documentation-templates/)
- [ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates](https://complianceforge.com/complianceforge-iso-27001-27002-compliance-documentation-templates/)
- [ComplianceForge](https://complianceforge.com/brands/ComplianceForge)
- [Secure Controls Framework (SCF)](https://complianceforge.com/secure-controls-framework-scf/)
- [ComplianceForge - NIST 800-171 & CMMC](https://complianceforge.com/complianceforge-nist-800-171-cmmc/)
- [Verutus](https://complianceforge.com/verutus/)
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## International Data Security Laws
[Skip to main content](https://complianceforge.com/international-data-security-laws#main-content)
# International Data Protection / Cybersecurity Laws
Our experience has proven that when it comes to information security policies, a standard is a standard for a reason. With that in mind, our Cybersecurity & Data Protection Program (CDPP) is based on industry-recognized best practices and information security standards so that you can meet your legal requirements. Unlike some competitor sites that offer “Bronze, Silver or Gold” packages that may leave you critically exposed, we offer a comprehensive information security solution to meet your specific compliance requirements. Why is this? It is simple - in the real world, compliance is penalty-centric. The court systems have established a track record of punishing businesses for failing to perform “reasonably expected” steps to meet compliance with known standards. In addition to the courts, insurance companies penalize companies for non-compliance by refusing policy coverage due to professional negligence exclusions. In terms of Information Security compliance, what you do not know has the proven ability to hurt you!
Our ISO 27002-based Cybersecurity & Data Protection Program (CDPP) is a professionally written compilation of information security policies, procedures, standards and guidelines that are designed with one purpose in mind - to provide you with the written security policies necessary to secure your business and meet your specific regulatory requirements.
We take the hassle of the guesswork away so you can focus on what you do best - growing your business. As information security professionals we know the policies you need to have in place to meet the requirements for compliance. The likelihood that your local “IT guy” knows your compliance requirements is slim to none, since information security is a very specific skill set. We follow proven, internationally recognized standards for what security policies should consist of. Many competitor sites unfortunately offer solutions that will leave you exposed and unprepared - when keeping your company in business and protected is the priority, there is no room for amateur solutions. The Cybersecurity & Data Protection Program (CDPP) stands out from the competition in its coverage, depth, and price. Additionally, the turnaround for a CDPP is generally 1-2 business days.
## **Why Does Your Business Need A Cybersecurity & Data Protection Program?**
The reason is simple - information security policies and standards are entirely focused on protecting your business! Professionally written cybersecurity policies provide the necessary steps to document the due care and due diligence your business needs to prove compliance with information security laws and industry regulations. While you spend thousands of dollars a year on business liability insurance, purchasing an ISO 27002-based Cybersecurity & Data Protection Program (CDPP) from ComplianceForge.com might be the most cost-effective protection you can provide for your company.
## **Our ISO 27002:2022 Cybersecurity & Data Protection Program (CDPP) Is Ideal for International Companies!**
The ISO 27002-based Cybersecurity & Data Protection Program (CDPP) provides a comprehensive framework to manage your company’s information security program. The ISO 27002-based Cybersecurity & Data Protection Program (CDPP) allows you to implement and document the steps to be compliant with Federal, state and industry laws and regulations.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## SCF Training Certifications
[Skip to main content](https://complianceforge.com/blog/scf-training-certifications/#main-content)
[](https://complianceforge.com/blog/scf-training-certifications/)
[ComplianceForge](https://complianceforge.com/ "ComplianceForge") is a [Licensed Content Provider (LCP)](https://securecontrolsframework.com/scf-licensed-content-provider/ "SCF LCP") for the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)")and it is exciting to see SCF-based training options and certifications are now live. This helps bring a new level of professional acknowledgement for those cybersecurity and data privacy professionals who have designed, built and implemented their organization's GRC program using SCF principles and controls.
SCF training and certifications are discounted 50% through the end of May with coupon code **LAUNCH**. You can learn more at: [https://training.securecontrolsframework.com](https://training.securecontrolsframework.com/ "SCF Training & Certification").
- [#ComplianceForge](https://complianceforge.com/blog/tag/ComplianceForge)
- [#Licensed Content Provider (LCP)](https://complianceforge.com/blog/tag/Licensed+Content+Provider+%28LCP%29)
- [#Secure Controls Framework](https://complianceforge.com/blog/tag/Secure+Controls+Framework)
- [Email](mailto:?subject=SCF%20Training%20%26%20Certifications%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fscf-training-certifications%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fscf-training-certifications%2F&title=SCF%20Training%20%26%20Certifications%20-%20ComplianceForge&summary=SCF%20Training%20%26%20Certifications%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fscf-training-certifications%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Cybersecurity Maturity Model
[Skip to main content](https://complianceforge.com/scf/capability-maturity-model/#main-content)
# Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)
The [Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/ "https://securecontrolsframework.com/capability-maturity-model/") is built directly into the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "https://securecontrolsframework.com/"). The C\|P-CMM is meant to solve the problem of objectivity in both establishing and evaluating cybersecurity and privacy controls. There are four (4) main objectives for the C\|P-CMM:
1. Provide CISO/CPOs/CIOs with objective criteria that can be used to establish expectations for a cybersecurity & privacy program;
2. Provide objective criteria for project teams so that secure practices are appropriately planned and budgeted for;
3. Provide minimum criteria that can be used to evaluate third-party service provider controls; and
4. Provide a means to perform due diligence of cybersecurity and privacy practices as part of Mergers & Acquisitions (M&A).
There are likely many other use cases that the C\|P-CMM can be used, but those objectives listed above drove the development of this project. The reason for this simply comes down to a need by businesses, regardless of size or industry, for a solution that can help fix those common frustrations that exist in most cybersecurity and privacy programs.
[](https://securecontrolsframework.com/content/projects/SCF-Capability-Maturity-Model.pdf "SCF Capability Maturity Model")
## Nested Approach To Cybersecurity Maturity
The term “nested” regarding maturity, refers to how the C\|P-CMM’s control criteria were written to acknowledge that each succeeding level of maturity is built upon its predecessor. Essentially, you cannot run without first learning how to walk. Likewise, you cannot walk without first learning how to crawl. This approach to defining cybersecurity & privacy control maturity is how the C\|P-CMM is structured.
The C\|P-CMM draws upon the high-level structure of the **Systems Security Engineering Capability Maturity Model v2.0 (SSE-CMM)**, since we felt it was the best model to demonstrate varying levels of maturity for people, processes and technology at a control level. If you are unfamiliar with the SSE-CMM, it is well-worth your time to read through the SSE-CMM Model Description Document that is hosted by the US Defense Technical Information Center (DTIC).
## C\|P-CMM Levels
The C\|P-CMM draws upon the high-level structure of the Systems Security Engineering Capability Maturity Model v2.0 (SSE-CMM), since we felt it was the best model to demonstrate varying levels of maturity for people, processes and technology at a control level. If you are unfamiliar with the SSE-CMM, it is well-worth your time to read through the SSE-CMM Overview Document that is hosted by the US Defense Technical Information Center (DTIC).
The six (6) C\|P-CMM levels are:
1. CMM 0 – Not Performed;
2. CMM 1 – Performed Informally;
3. CMM 2 – Planned & Tracked;
4. CMM 3 – Well-Defined;
5. CMM 4 – Quantitatively Controlled; and
6. CMM 5 – Continuously Improving.
[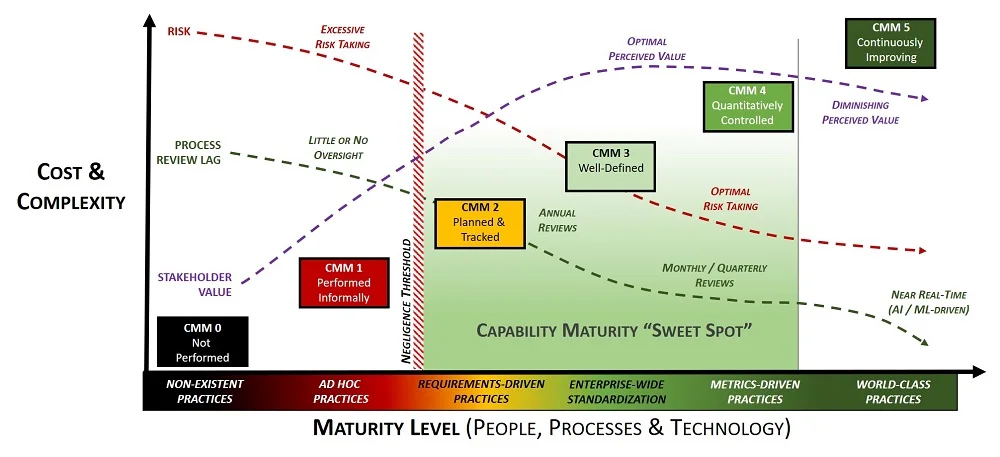](https://securecontrolsframework.com/capability-maturity-model/ "SCF maturity model")
### C\|P-CMM Level 0 (L0) – Not Performed
This level of maturity is defined as “non-existence practices,” where the control is not being performed:
- Practices are non-existent, where a reasonable person would conclude the control is not being performed.
- Evidence of due care and due diligence do not exist to demonstrate compliance with applicable statutory, regulatory and/or contractual obligations.
L0 practices, or a lack thereof, are generally considered to be negligent. The reason for this is if a control is reasonably-expected to exist, by not performing the control that is negligent behavior. The need for the control could be due to a law, regulation or contractual obligation (e.g., client contract or industry association requirement).
_Note – The reality with a L0 level of maturity is often:_
- _For smaller organizations, the IT support role only focuses on “break / fix” work or the outsourced IT provider has a scope in its support contract that excludes the control through either oversight or ignorance of the client’s requirements._
- _For medium / large organizations, there is IT and/or cybersecurity staff, but governance is functionally non-existent and the control is not performed through either oversight, ignorance or incompetence._
### C\|P-CMM Level 1 (L1) – Performed Informally
This level of maturity is defined as “ad hoc practices,” where the control is being performed, but lacks completeness & consistency:
- Practices are “ad hoc” where the intent of a control is not met due to a lack consistency and formality.
- When the control is met, it lacks consistency and formality (e.g., rudimentary practices are performed informally).
- A reasonable person would conclude the control is not consistently performed in a structured manner.
- Performance depends on specific knowledge and effort of the individual performing the task(s), where the performance of these practices is not proactively governed.
- Limited evidence of due care and due diligence exists, where it would be difficult to legitimately disprove a claim of negligence for how cybersecurity/privacy controls are implemented and maintained.
L1 practices are generally considered to be negligent. The reason for this is if a control is reasonably-expected to exist, by only implementing ad-hoc practices in performing the control that could be considered negligent behavior. The need for the control could be due to a law, regulation or contractual obligation (e.g., client contract or industry association requirement).
_Note – The reality with a L1 level of maturity is often:_
- _For smaller organizations, the IT support role only focuses on “break / fix” work or the outsourced IT provider has a limited scope in its support contract._
- _For medium / large organizations, there is IT and/or cybersecurity staff but there is no management focus to spend time or resources on the control._
### C\|P-CMM Level 2 (L2) – Planned & Tracked
Practices are “requirements-driven” where the intent of control is met in some circumstances, but not standardized across the entire organization:
- Practices are “requirements-driven” (e.g., specified by a law, regulation or contractual obligation) and are tailored to meet those specific compliance obligations (e.g., evidence of due diligence).
- Performance of a control is planned and tracked according to specified procedures and work products conform to specified standards (e.g., evidence of due care).
- Controls are implemented in some, but not all applicable circumstances/environments (e.g., specific enclaves, facilities or locations).
- A reasonable person would conclude controls are “compliance-focused” to meet a specific obligation, since the practices are applied at a local/regional level and are not standardized practices across the enterprise.
- Sufficient evidence of due care and due diligence exists to demonstrate compliance with specific statutory, regulatory and/or contractual obligations.
L2 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control. L2 practices are generally targeted on specific systems, networks, applications or processes that require the control to be performed for a compliance need (e.g., PCI DSS, HIPAA, CMMC, NIST 800-171, etc.).
It can be argued that L2 practices focus more on compliance over security. The reason for this is the scoping of L2 practices are narrowly-focused and are not enterprise-wide.
_Note – The reality with a L2 level of maturity is often:_
- _For smaller organizations:_
- _IT staff have clear requirements to meet applicable compliance obligations or the outsourced IT provider is properly scoped in its support contract to address applicable compliance obligations._
- _It is unlikely that there is a dedicated cybersecurity role and at best it is an additional duty for existing personnel._
- _For medium / large organizations:_
- _IT staff have clear requirements to meet applicable compliance obligations._
- _There is most likely a dedicated cybersecurity role or a small cybersecurity team._
### C\|P-CMM Level 3 (L3) – Well-Defined
This level of maturity is defined as “enterprise-wide standardization,” where the practices are well-defined and standardized across the organization:
- Practices are standardized “enterprise-wide” where the control is well-defined and standardized across the entire enterprise.
- Controls are implemented in all applicable circumstances/environments (deviations are documented and justified).
- Practices are performed according to a well-defined process using approved, tailored versions of standardized processes.
- Performance of a control is according to specified well-defined and standardized procedures.
- Control execution is planned and managed using an enterprise-wide, standardized methodology.
- A reasonable person would conclude controls are “security-focused” that address both mandatory and discretionary requirements. Compliance could reasonably be viewed as a “natural byproduct” of secure practices.
- Sufficient evidence of due care and due diligence exists to demonstrate compliance with specific statutory, regulatory and/or contractual obligations.
- The Chief Information Security Officer (CISO) , or similar function, develops a security-focused [Concept of Operations (CONOPS)](https://complianceforge.com/free-guides/cybersecurity-conops "Concept of Operations (CONOPS)") that documents organization-wide management, operational and technical measures to apply defense-in-depth techniques (note - in this context, a CONOPS is a verbal or graphic statement of intent and assumptions regarding operationalizing the identified tasks to achieve the CISO’s stated objectives. The result of the CONOPS is operating the organization’s cybersecurity and data protection program so that it meets business objectives). Control or domain-specific CONOPS may be incorporated as part of a broader operational plan for the cybersecurity and privacy program (e.g., cybersecurity-specific business plan)
L3 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control. Unlike L2 practices that are narrowly focused, L3 practices are standardized across the organization. It can be argued that L3 practices focus on security over compliance, where compliance is a natural byproduct of those secure practices. These are well-defined and properly-scoped practices that span the organization, regardless of the department or geographic considerations.
_Note – The reality with a L3 level of maturity is often:_
- _For smaller organizations:_
- _There is a small IT staff that has clear requirements to meet applicable compliance obligations._
- _There is a very competent leader (e.g., security manager / director) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization._
- _For medium / large organizations:_
- _IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise._
- _In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)_
- _There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization._
### C\|P-CMM Level 4 (L4) – Quantitatively Controlled
This level of maturity is defined as “metrics-driven practices,” where in addition to being well-defined and standardized practices across the organization, there are detailed metrics to enable governance oversight:
- Practices are “metrics-driven” and provide sufficient management insight (based on a quantitative understanding of process capabilities) to predict optimal performance, ensure continued operations, and identify areas for improvement.
- Practices build upon established L3 maturity criteria and have detailed metrics to enable governance oversight.
- Detailed measures of performance are collected and analyzed. This leads to a quantitative understanding of process capability and an improved ability to predict performance.
- Performance is objectively managed, and the quality of work products is quantitatively known.
L4 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control, as well as detailed metrics enable an objective oversight function. Metrics may be daily, weekly, monthly, quarterly, etc.
_Note – The reality with a L4 level of maturity is often:_
- _For smaller organizations, it is unrealistic to attain this level of maturity._
- _For medium / large organizations:_
- _IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise._
- _In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)_
- _There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization._
- _Business stakeholders are made aware of the status of the cybersecurity and privacy program (e.g., quarterly business reviews to the CIO/CEO/board of directors). This situational awareness is made possible through detailed metrics._
### C\|P-CMM Level 5 (L5) – Continuously Improving
This level of maturity is defined as “world-class practices,” where the practices are not only well-defined and standardized across the organization, as well as having detailed metrics, but the process is continuously improving:
- Practices are “world-class” capabilities that leverage predictive analysis.
- Practices build upon established L4 maturity criteria and are time-sensitive to support operational efficiency, which likely includes automated actions through machine learning or Artificial Intelligence (AI).
- Quantitative performance goals (targets) for process effectiveness and efficiency are established, based on the business goals of the organization.
- Process improvements are implemented according to “continuous improvement” practices to affect process changes.
L5 practices are generally considered to be “audit ready” with an acceptable level of evidence to demonstrate due diligence and due care in the execution of the control and incorporates a capability to continuously improve the process. Interestingly, this is where Artificial Intelligence (AI) and Machine Learning (ML) would exist, since AI/ML would focus on evaluating performance and making continuous adjustments to improve the process. However, AI/ML are not required to be L5.
_Note – The reality with a L5 level of maturity is often:_
- _For small and medium-sized organizations, it is unrealistic to attain this level of maturity._
- _For large organizations:_
- _IT staff have clear requirements to implement standardized cybersecurity & privacy principles across the enterprise._
- _In addition to the existence of a dedicated cybersecurity team, there are specialists (e.g., engineers, SOC analysts, GRC, privacy, etc.)_
- _There is a very competent leader (e.g., CISO) with solid cybersecurity experience who has the authority to direct resources to enact secure practices across the organization._
- _Business stakeholders are made aware of the status of the cybersecurity and privacy program (e.g., quarterly business reviews to the CIO/CEO/board of directors). This situational awareness is made possible through detailed metrics._
- _The organization has a very aggressive business model that requires not only IT, but its cybersecurity and privacy practices, to be innovative to the point of leading the industry in how its products and services are designed, built or delivered._
- _The organization invests heavily into developing AI/ML technologies to make near real-time process improvements to support the goal of being an industry leader._
There are no products listed under this category.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
security capability maturity model, cmm compliance, vulnerability management capability maturity model, information security assessment capability maturity model, masters and standards cmm, csf maturity model, understanding information security maturity levels
## Digital Security Program Overview
[Skip to main content](https://complianceforge.com/digital-security-program-dsp-product-video/#main-content)
# What Is The Digital Security Program (DSP)?
Product Walkthrough Video
This short product walkthrough video is designed to give a brief overview about what the PCI DSS policy and standard compliance documentation is to help answer common questions we receive.
Digital Security Program (DSP) Product Walkthrough - YouTube
[Photo image of ComplianceForge](https://www.youtube.com/channel/UCRGQPnfaReUhqwkaiw9rgBg?embeds_referring_euri=https%3A%2F%2Fcomplianceforge.com%2F)
ComplianceForge
936 subscribers
[Digital Security Program (DSP) Product Walkthrough](https://www.youtube.com/watch?v=5O0driBCRKs)
ComplianceForge
Search
Watch later
Share
Copy link
Info
Shopping
Tap to unmute
If playback doesn't begin shortly, try restarting your device.
More videos
## More videos
You're signed out
Videos you watch may be added to the TV's watch history and influence TV recommendations. To avoid this, cancel and sign in to YouTube on your computer.
CancelConfirm
Share
Include playlist
An error occurred while retrieving sharing information. Please try again later.
[Watch on](https://www.youtube.com/watch?v=5O0driBCRKs&embeds_referring_euri=https%3A%2F%2Fcomplianceforge.com%2F)
0:00
0:00 / 7:46
•Live
•
[Watch on YouTube](https://www.youtube.com/watch?v=5O0driBCRKs "Watch on YouTube")
The Digital Security Program (DSP) from ComplianceForge is a comprehensive, editable cybersecurity and data privacy documentation solution, covering 33 domains with policies, control objectives, standards, guidelines, and metrics. It is designed to be easily customizable using Microsoft Word and Excel, providing a cost-effective and time-saving alternative to hiring consultants or creating documentation from scratch.
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## ComplianceForge Cybersecurity Solutions
[Skip to main content](https://complianceforge.com/brands/ComplianceForge?page=3#main-content)

# ComplianceForge
Sort By:Featured ItemsNewest ItemsBest SellingA to ZZ to ABy ReviewPrice: AscendingPrice: Descending
- [](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ C](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) C for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council...
$1,625.00
[Choose Options](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ C-VT](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) C-VT for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council...
$1,625.00
[Choose Options](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ D (Merchant)](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) D-Merchant for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI...
$1,870.00
[Choose Options](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ D (Service Provider)](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) D-Service Provider for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI...
$1,870.00
[Choose Options](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/bundle/risk-bundle-1)
#### [Risk Bundle 1: Assessing & Managing Risk](https://complianceforge.com/bundle/risk-bundle-1)
ComplianceForge
Cybersecurity Risk Bundle #1 (10% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk...
$4,100.00
$3,690.00 - $5,040.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-1)
- [](https://complianceforge.com/bundle/risk-bundle-2)
#### [Risk Bundle 2: Risk, Vulnerability & IR Management](https://complianceforge.com/bundle/risk-bundle-2)
ComplianceForge
Cybersecurity Risk Bundle #2 (25% discount)
This is a bundle that includes the following four (4) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
Risk...
$8,450.00
$6,338.00 - $7,688.00
[Choose Options](https://complianceforge.com/bundle/risk-bundle-2)
- [](https://complianceforge.com/bundle/c-scrm-bundle-1/)
#### [C-SCRM Bundle 1: CDPP version (ISO or NIST alignment)](https://complianceforge.com/bundle/c-scrm-bundle-1/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused...
$39,720.00
$39,720.00
$23,832.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-1/)
- [](https://complianceforge.com/bundle/c-scrm-bundle-2/)
#### [C-SCRM Bundle 2: DSP version (SCF alignment)](https://complianceforge.com/bundle/c-scrm-bundle-2/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #2 - DSP Version (45% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-2/)
- [](https://complianceforge.com/bundle/privacy-bundle-1)
#### [Privacy Bundle 1: CDPP version (ISO or NIST alignment)](https://complianceforge.com/bundle/privacy-bundle-1)
ComplianceForge
Privacy Bundle #1 - CDPP Version (35% discount)
This is a bundle that includes the following twelve (12) ComplianceForge products that are focused on operationalizing the cybersecurity and privacy...
$35,485.00
$35,485.00
$23,065.00
[Choose Options](https://complianceforge.com/bundle/privacy-bundle-1)
- [](https://complianceforge.com/updated-crosswalk-mapping/)
#### [Updated Crosswalk Mapping](https://complianceforge.com/updated-crosswalk-mapping/)
ComplianceForge
CDPP / CSOP Crosswalk Mapping Update
For customers who previously purchased a Cybersecurity & Data Protection Program (CDPP) and/or Cybersecurity Standardized Operating Procedures (CSOP) product,...
$250.00
[Choose Options](https://complianceforge.com/updated-crosswalk-mapping/)
- [](https://complianceforge.com/bundle/privacy-bundle-2)
#### [Privacy Bundle 2: DSP version (SCF alignment)](https://complianceforge.com/bundle/privacy-bundle-2)
ComplianceForge
Privacy Bundle #2 - DSP Version (45% discount)
This is a bundle that includes the following twelve (12) ComplianceForge products that are focused on operationalizing the cybersecurity and privacy...
$45,605.00
$25,083.00 - $26,433.00
[Choose Options](https://complianceforge.com/bundle/privacy-bundle-2)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Compliance Insights
[Skip to main content](https://complianceforge.com/blog/?page=4#main-content)
# Blog
[](https://complianceforge.com/blog/supply-chain-risk-management/)
Cybersecurity Supply Chain Risk Management (C-SCRM)
is the process of identifying, assessing and mitigating risks in an
organization's supply chain that could impact the security and integrity of an
o
… [read more](https://complianceforge.com/blog/supply-chain-risk-management/)
[](https://complianceforge.com/blog/cybersecurity-policies-standards/)
Policies and standards are the foundation for an organization's cybersecurity and privacy program. These components form the alignment with leading practices to help ensure applicable statutory, regul
… [read more](https://complianceforge.com/blog/cybersecurity-policies-standards/)
[](https://complianceforge.com/blog/what-is-complianceforge/)
ComplianceForge specializes in cybersecurity & data protection documentation. We are an industry leader in providing affordable, editable and scalable documentation solutions to support cybersecur
… [read more](https://complianceforge.com/blog/what-is-complianceforge/)
[](https://complianceforge.com/blog/cybersecurity-materiality-key-controls/)
There is a "materiality ecosystem" that exists within modern cybersecurity risk management discussions. The process begins with determining what constitutes materiality for an organization. This is or
… [read more](https://complianceforge.com/blog/cybersecurity-materiality-key-controls/)
[](https://complianceforge.com/blog/ncp-client-success-peerless-electronics/)
ComplianceForge celebrates another client win with Peerless Electronics, Inc. passing a DIBCAC Joint Surveillance Voluntary Assessment (JSVA).From the following LinkedIn article that highlights the su
… [read more](https://complianceforge.com/blog/ncp-client-success-peerless-electronics/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[gsa oasis+ j](https://complianceforge.com/blog/gsa-oasis-j3-cscrm-deliverables/) [your cmmc requirements guide](https://complianceforge.com/blog/your-cmmc-requirements-guide/)
## Cybersecurity Management Threats
[Skip to main content](https://complianceforge.com/blog/cybersecurity-management-threat/#main-content)
What is the single greatest threat that your organization faces? SolarWinds-style attacks? APTs? The answer is not what many initially think and the reason is primarily based on the sensitive nature of the answer. Based on years of observations that span multiple industries, it is clear the single greatest threat that many organizations face is the dysfunction of its own management team. This is not meant to be cynical or comical, but point out the nature of a legitimate cybersecurity and data protection threat that is often manifested by the inability of weak, ineffective and/or incompetent management to (1) make a risk-based decision and (2) support that decision. I am joined by Ryan Bonner from DefCERT to shed light on this understanding of threats, how that impacts an organization’s security/compliance efforts and what can be done to remedy the situation.
This bold statement about an organization’s management team being its greatest threat may sound harsh, but it is a defendable position when you assess what natural and manmade threats are and how that relates to risks:

In practical terms, weak, ineffective and/or incompetent management practices are a manmade threat that exposes an organization to significant risk (see further down this article for a listing of these risks). The reason for this is risks and threats are directly tied to controls, so if management inaction or interference leads to (1) an absence of a required control or (2) a control deficiency, this means that the control execution has been negatively affected and this exposes the organization to those risks associated with the specific control deficiency.

Unlike an Advanced Persistent Threat (APT) from China, Russia or Iran, an organization’s internal management dysfunction is a “persistent threat” that should not be overlooked as part of a threat assessment process.
### What Is Driving The Need For Risk Management?
Recent, high-profile hacking incidents have led to more regulatory pressure at the state, federal and international level for maintaining secure practices from both a cybersecurity and data protection (privacy) perspective. This has directly led to greater scrutiny of organizational practices from partners and clients. No one can manage risk if the concept of risk management is ethereal and ever-changing, so it is the role of the leadership team to:
- Formalize a viable risk management program;
- Clearly define risk that is specific to the organization;
- Identify the risk management roles and assign individuals with responsibilities for their role in managing risk; and
- Apply those accepted risk management principles uniformly across the organization and its supply chain.
When you look at the fundamental role of a “leader” it is to establish context and drive operations to meet the organization’s business plan. It is beyond managing resources and is more a question of character where the leader establishes a positive environment in which everyone thrives, while achieving targeted results.
This concept of “management threat” has evolved from affecting individual organizations to an entire industry. Starting 1 January 2018, the Defense Industrial Base (DIB) was obligated to protect Controlled Unclassified Information (CUI) according to National Institute for Standards and Technology (NIST) SP 800-171. Due to the abysmal adoption of secure practices by the DIB to protect CUI, the US Department of Defense (DoD) was obligated to invent the Cybersecurity Maturity Model Certification (CMMC) to implement an independent, third-party assessment program. Fundamentally, CMMC is directly the result of management failure within the DIB to adopt secure practices and implement contractual obligations to protect its client’s data.
### Risk Blindness & Personal Bias
In the government contracting space, management often suffers from a kind of “risk blindness” stemming from the way risk is communicated in the supply chain. For decades, unclassified information was poorly categorized, marked and managed, while classified information was treated with reverence and highly-structured processes. With the US government’s focus on protecting regulated data (e.g., CUI) without clear definitions, this has created creates a scenario where contractors often lack the background information needed to understand and prioritize risk. Without a clear understanding of what needs protecting, managers within the DIB are often left with “gut feel” determinations (unfounded, qualitative risk analysis) and their own personal experience (subject to bias) to manage risk.
Cognitive bias worsens the myopia associated with risk management by allowing management to drift towards mental structures that have adequately served their organization and its operations up to this point. This can include personal leanings such as:
- Survival bias (“ransomware hasn’t killed us yet, and so it never will”);
- Availability bias (“during my years as a network admin, I learned that the only thing truly stopping attackers is a well-tuned firewall”); or
- The Dunning-Kruger Effect (“Building a response team can’t be that hard. It’s basically just picking up the phone when something happens!”).
These kinds of bias further ingrain emotionally-driven, qualitative analysis into the risk equation, meaning that risk is “downplayed” instead of evaluated and mitigated based on objective management practices.
### False Sense of Risk Management
There is clearly a fiduciary aspect to leadership and management roles, where decisions must be in the best interest in the organization, rather than act in their own interest. An example of this is a case where a “leadership team” consisting of a Chief Information Security Officer (CISO), Chief Information Officer (CIO) and Chief Financial Officer (CFO) refused to provide quantifiable criteria (e.g., risk thresholds) that are needed to assess risk as part of a formal risk management program. Theses quantifiable thresholds exist to help categorize an incident as low, moderate, high, severe or catastrophic so that the appropriate level of management would be involved in the assessment of and approval of risk management decisions. Management refused to take a stand and define thresholds, when directly asked for authoritative guidance that only their roles could provide. This management inaction directly made the organization’s risk management practices nebulous and unquantifiable. The result is a “paper tiger” risk management program that appears impressive, but is ineffectual and not capable of being operationalized.
In situations like the one described above, where the overall approach to risk management is poorly defined, it creates an impediment to legitimate risk management practices, including the traditional 3 Lines of Defense (3LOD) model. 3LOD becomes useless and will create a false sense of risk management, since it incorrectly assumes a viable risk management program exists that clearly defines risk, who can manage it and what options exist for risk management. For those not familiar with the 3LOD model:
1. First line of defense (1LOD) – This function is provided by front line staff and operational management. This is where operational risk decisions are designed to be made.
2. Second line of defense (2LOD) – This function is provided by Governance, Risk Management and Compliance (GRC) functions. This is where oversight and advice exist to support 1LOD in identifying, managing and monitoring risks.
3. Third line of defense (3LOD) – This function is provided by an Internal Audit (IA) function. This function provides a level of independent assurance that the risk management and internal control framework is working as designed.
The traditional 3LOD model misses the need for “0LOD” or the genesis of the organization’s risk management program where the leadership team explicitly establishes and enforces the criteria needed to identify, manage and monitor risks. 1LOD, 2LOD and 3LOD are all negatively impacted by unclear risk management guidance from an organization’s leadership team.
Examples of Management Dysfunction
Fear is a common denominator for these observed management failures within risk management:
- Failing to support an established policy, standard or previous decision by wanting to avoid conflict among the organization’s lines of business (e.g., violate risk management principles for political reasons);
- A desire to “save face” by sticking with a false narrative of the cybersecurity program, since they may be viewed as lying or being incompetent for previous positions;
- Fear of having to ask senior management for money to properly support the program;
- Failing to appropriately understand the situation by not asking questions to avoid “looking dumb” to peers, subordinates or senior leaders; and/or
- Exhibiting an inability to make a decision, by either hoping the situation goes away or that someone else will make the decision.
Risks Associated With Weak, Ineffective and/or Incompetent Management
When you look at the possible risks from the threat associated with weak, ineffective and/or incompetent, it clearly illustrates this as a significant threat (courtesy of the SCF’s [Security & Privacy Risk Management Model (SP-RMM)](https://www.securecontrolsframework.com/sp-rmm)):
- Inability to maintain individual accountability \- a failure to maintain asset ownership and it is not possible to have non-repudiation of actions or inactions.
- Improper assignment of privileged functions \- a failure to implement least privileges.
- Privilege escalation \- access to privileged functions is inadequate or cannot be controlled.
- Unauthorized access \- access is granted to unauthorized individuals, groups or services.
- Lost, damaged or stolen asset(s) \- asset(s) is/are lost, damaged or stolen.
- Loss of integrity through unauthorized changes \- unauthorized changes corrupt the integrity of the system / application / service.
- Business interruption \- increased latency or a service outage that negatively impacts business operations.
- Data loss / corruption \- a failure to maintain the confidentiality of the data (compromise) or data is corrupted (loss).
- Reduction in productivity \- user productivity is negatively affected by the incident.
- Information loss / corruption or system compromise due to technical attack \- malware, phishing, hacking or other technical attack compromise data, systems, applications or services.
- Information loss / corruption or system compromise due to non‐technical attack \- social engineering, sabotage or other non-technical attack compromises data, systems, applications or services.
- Loss of revenue \- a financial loss occurs from either a loss of clients or an inability to generate future revenue.
- Cancelled contract \- a contract is cancelled due to a violation of a contract clause.
- Diminished competitive advantage \- competitive advantage of the organization is jeopardized.
- Diminished reputation \- negative publicity tarnishes the organization's reputation.
- Fines and judgements \- legal and/or financial damages result from statutory / regulatory / contractual non-compliance.
- Unmitigated vulnerabilities \- unmitigated technical vulnerabilities exist without compensating controls or other mitigation actions.
- System compromise \- system / application / service is compromised affects its confidentiality, integrity, availability and/or safety.
- Inability to support business processes \- implemented security /privacy practices are insufficient to support the organization's secure technologies & processes requirements.
- Incorrect controls scoping \- there is incorrect or inadequate controls scoping, which leads to a potential gap or lapse in security / privacy controls coverage.
- Lack of roles & responsibilities \- documented security / privacy roles & responsibilities do not exist or are inadequate.
- Inadequate internal practices \- internal practices do not exist or are inadequate. Procedures fail to meet "reasonable practices" expected by industry standards.
- Inadequate third-party practices \- third-party practices do not exist or are inadequate. Procedures fail to meet "reasonable practices" expected by industry standards.
- Lack of oversight of internal controls \- there is a lack of due diligence / due care in overseeing the organization's internal security / privacy controls.
- Lack of oversight of third-party controls \- there is a lack of due diligence / due care in overseeing security / privacy controls operated by third-party service providers.
- Illegal content or abusive action \- there is abusive content / harmful speech / threats of violence / illegal content that negatively affect business operations.
- Inability to investigate / prosecute incidents \- response actions either corrupt evidence or impede the ability to prosecute incidents.
- Improper response to incidents \- response actions fail to act appropriately in a timely manner to properly address the incident.
- Ineffective remediation actions \- no oversight to ensure remediation actions are correct and/or effective.
- Expense associated with managing a loss event \- financial repercussions from responding to an incident or loss.
- Inability to maintain situational awareness – an inability to detect incidents.
- Lack of a security-minded workforce – the workforce lacks user-level understanding about security & privacy principles.
What Can Be Done To Address This Threat?
Organizations need to take the concept of management being a potential threat seriously by:
- Developing and publishing a risk management program with authoritative guidance on risk management activities;
- Distributing risk management activities across the 3LOD model for risk management to insulate risk decisions against personal bias;
- Providing training for those in management roles to adequately support the organization’s risk management program; and
- Conducting 360 peer reviews specific to risk management practices.
For organizations, it may mean removing unfit individuals from management roles by transferring them to a new role or terminating their employment, since that individual is a liability to the organization.
Employees and contractors need to understand their responsibilities and options:
- Reduce “technical jargon” and provide solutions in a business context that non-technical people can understand; and
- Work with your leadership team to “manage up” by anticipating needs and providing solutions to manage risk.
As an employee, if those legitimate efforts fail to work, the organization may be a lost cause and it is time to self-terminate your employment to find work at an organization that both appreciates your skill set and takes risk management seriously.
About The Authors
If you have any questions about this, please feel free to reach out.
Tom Cornelius is the Senior Partner at [ComplianceForge](https://www.complianceforge.com/), an industry leader in cybersecurity and privacy documentation. He is also the founder of the [Secure Controls Framework](https://www.securecontrolsframework.com/) (SCF), a not-for-profit initiative to help companies identify and manage their cybersecurity and privacy requirements.
Ryan Bonner is the CEO of [DefCERT](https://defcert.com/), a firm providing DFARS, NIST, and CMMC consulting services for government contractors. In addition to private consulting engagements: DefCERT works extensively with NIST Manufacturing Extension Partnership programs, economic development organizations, and managed IT service providers.
- [#3LOD](https://complianceforge.com/blog/tag/3LOD)
- [#CMMC](https://complianceforge.com/blog/tag/CMMC)
- [#CUI](https://complianceforge.com/blog/tag/CUI)
- [#DFARS](https://complianceforge.com/blog/tag/DFARS)
- [#FAR](https://complianceforge.com/blog/tag/FAR)
- [#FCI](https://complianceforge.com/blog/tag/FCI)
- [#Leadership](https://complianceforge.com/blog/tag/Leadership)
- [#Management](https://complianceforge.com/blog/tag/Management)
- [#Risks](https://complianceforge.com/blog/tag/Risks)
- [#Threat](https://complianceforge.com/blog/tag/Threat)
- [Email](mailto:?subject=Cybersecurity%20Management%20Threat%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-management-threat%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-management-threat%2F&title=Cybersecurity%20Management%20Threat%20-%20ComplianceForge&summary=Cybersecurity%20Management%20Threat%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-management-threat%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity CONOPS Guidance
[Skip to main content](https://complianceforge.com/free-guides/cybersecurity-conops#main-content)
# Cybersecurity Concept of Operations (CONOPS)
## The Missing Link of Program-Level Cybersecurity & Data Protection Guidance
A Cybersecurity Concept of Operations ( **CONOPS**), often referred to as s Security CONOPS, is meant to unify actions by providing a "north star" for guidance and decision-making purposes for cybersecurity and data protection stakeholders. A CONOPS can be thought of as a "mini business plan" that can be scaled from the cybersecurity department, all the way down to a specific project or system. The CONOPS addresses the who, what, why, where, when and how guidance to accomplish the stated mission.
From a hierarchical perspective, a CONOPS is subordinate to a CISO-level business plan, but is one level higher than a System Security Plan (SSP). Based on the CONOPS's function to operationalize a busines plan, the CONOPS can provide a significant amount of information necessary to fill out a system/project-specific SSP.
The actionable guidance provided by the CONOPS directly influences People, Processes, Techonologies, Data and Facilities (PPTDF). This guidance is designed to span both business planning and cybersecurity operations to ensure stakeholders are working to achieve the same objectives, where the organization can be compliant, secure and resilient.
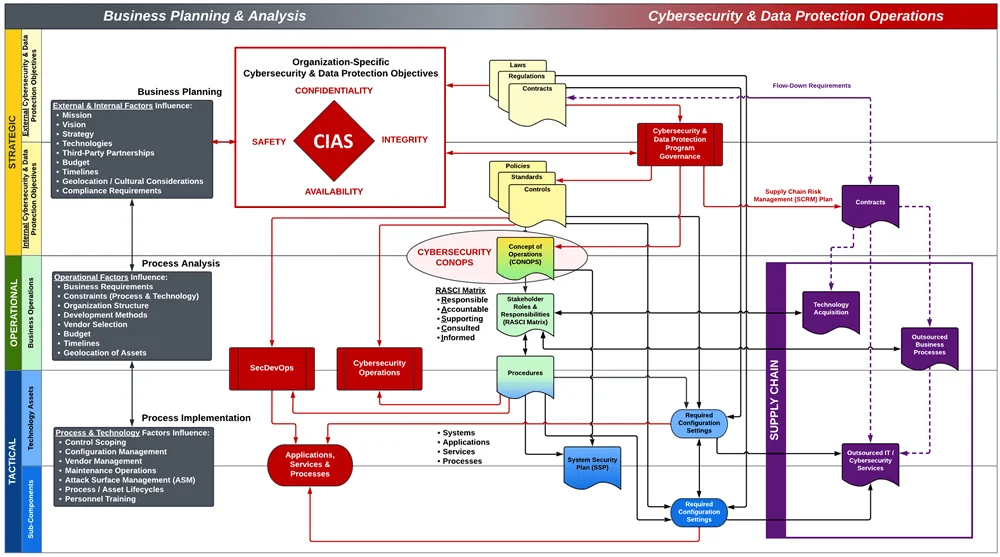
A CONOPS provides user-oriented guidance that describes crucial context from an integrated systems point of view (e.g., mission, operational objectives and overall expectations), without being overly technical or formal. A CONOPS is meant to:
- Benefit stakeholders by establishing a baseline “operational concept” to establish a conceptual, clearly-understood view for everyone involved in the scope of operations described by the CONOPS.
- Record design constraints, the rationale for those constraints and to indicate the range of acceptable solution strategies to accomplish the mission and any stated objectives.
- Contain a conceptual view that illustrates the top-level functionality in the proposed process or system.

A CONOPS is not a set of policies, standards or procedures, but it does compliment and support those documents. A CONOPS straddles the territory between an organization's centrally-managed policies/standards and its decentralized, stakeholder-executed procedures, where a CONOPS serves as expert-level guidance that is meant to run a specific capability or function within an organization's cybersecurity department. An organization's Subject Matter Experts (SMEs) are expected to use a CONOPS as a tool to help communicate user needs and system characteristics to developers, integrators, sponsors, funding decision makers and other stakeholders.
## Cybersecurity CONOPS Documentation Templates
Several ComplianceForge documents are essentially CONOPS documents, where those CONOPS-like documents are (1) more conceptual than procedures and (2) are focused on providing program-level guidance to define and mature a specific capability that is called for by policies and standards (e.g., operate a "risk management program"). Examples of ComplianceForge products that provide program-level guidance to define a function-specific concept of operations include:
- Risk management (e.g., [Risk Management Program ( **RMP**)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/));
- Vulnerability management (e.g., [Vulnerability & Patch Management Program ( **VPMP**)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/));
- Incident response (e.g., [Integrated Incident Response Program ( **IIRP**)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/));
- Business Continuity / Disaster Recovery (e.g., [Continuity of Operations Plan ( **COOP**)](https://complianceforge.com/product/continuity-of-operations-plan/));
- Secure engineering practices (e.g., [Security & Privacy By Design ( **SPBD**)](https://complianceforge.com/product/security-by-design-privacy-by-design/));
- Pre-production testing (e.g., [Information Assurance Program ( **IAP**)](https://complianceforge.com/product/control-validation-testing-information-assurance-template));
- Supply Chain Risk Management (SCRM) (e.g., [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRP SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan "Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRP SIP)")); and
- Configuration management (e.g., [Secure Baseline Configurations ( **SBC**)](https://complianceforge.com/product/secure-baseline-configuration-sbc)).
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[compliance solutions](https://complianceforge.com/compliance-solutions/) [cybersecurity best practices documentation templates](https://complianceforge.com/cybersecurity-templates/)
con ops, conops, conops template, conops concept of operations
## ComplianceForge Cybersecurity Solutions
[Skip to main content](https://complianceforge.com/brands/ComplianceForge?page=2#main-content)

# ComplianceForge
Sort By:Featured ItemsNewest ItemsBest SellingA to ZZ to ABy ReviewPrice: AscendingPrice: Descending
- [](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
#### [Procedures Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST 800-53 R5 Moderate Baseline
Product Walkthrough Video
When you click the image or the link below, it will direct...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
- [](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
#### [Procedures Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST 800-53 R5 HIGH & FedRAMP LOW/MODERATE/HIGH Version
Product Walkthrough Video
When you click the image or the link below,...
$5,995.00 - $10,795.00
[Choose Options](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
- [](https://complianceforge.com/product/continuity-of-operations-plan/)
#### [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
ComplianceForge
Continuity of Operations Plan (COOP) - Disaster Recovery & Business Continuity
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/continuity-of-operations-plan/)
- [](https://complianceforge.com/product/information-assurance-program)
#### [Information Assurance Program (IAP)](https://complianceforge.com/product/information-assurance-program)
ComplianceForge
Cybersecurity & Data Privacy Control Validation Testing
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains...
$4,235.00 - $5,585.00
[Choose Options](https://complianceforge.com/product/information-assurance-program)
- [](https://complianceforge.com/product/secure-baseline-configuration-sbc)
#### [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
ComplianceForge
Secure Baseline Configurations For Technology Assets
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a...
$2,175.00 - $3,525.00
[Choose Options](https://complianceforge.com/product/secure-baseline-configuration-sbc)
- [](https://complianceforge.com/subscription/ncp)
#### [Subscription - NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/subscription/ncp)
ComplianceForge
NIST 800-171 Compliance Program (NCP) - Annual Subscription for Product Updates
This is a subscription service for existing NIST 800-171 Compliance Program (NCP) clients, who have not...
$950.00
[Choose Options](https://complianceforge.com/subscription/ncp)
- [](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
#### [NIST 800-171 System Security Plan (SSP) Template](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
ComplianceForge
NIST 800-171 System Security Plan (SSP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product...
$950.00 - $5,750.00
[Choose Options](https://complianceforge.com/product/nist-800-171-system-security-plan-template/)
- [](https://complianceforge.com/product/cybersecurity-business-plan/)
#### [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
ComplianceForge
Cybersecurity Business Plan (CBP) Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$2,175.00 - $3,525.00
[Choose Options](https://complianceforge.com/product/cybersecurity-business-plan/)
- [](https://complianceforge.com/product/pci-dss-v4-saq-a)
#### [Policies & Standards - PCI DSS v4 SAQ A](https://complianceforge.com/product/pci-dss-v4-saq-a)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) A for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards...
$1,155.00
[Choose Options](https://complianceforge.com/product/pci-dss-v4-saq-a)
- [](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ A-EP](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) A-EP for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council...
$1,155.00
[Choose Options](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ B](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) B for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council...
$1,325.00
[Choose Options](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ B-IP](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) B-IP for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council...
$1,325.00
[Choose Options](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Compliance Insights
[Skip to main content](https://complianceforge.com/blog/?page=7#main-content)
# Blog
[](https://complianceforge.com/blog/cybersecurity-controls-shape-continuous-monitoring/)
In an era where digital threats
are constantly evolving, organizations are increasingly recognizing the
importance of continuous monitoring to safeguard their sensitive/regulated data.
Continuous m
… [read more](https://complianceforge.com/blog/cybersecurity-controls-shape-continuous-monitoring/)
[](https://complianceforge.com/blog/cmmc-document-implement-assess/)
Bottom Line Up Front (BLUF): Time is money when it comes to CMMC compliance efforts:
If you have poorly-crafted documentation, it will cost you more time & money in implementation and assessment.
… [read more](https://complianceforge.com/blog/cmmc-document-implement-assess/)
The intent of this article
is to generate a professional discussion on CMMC that will make its way to the
DoD PMO to hopefully remediate several issues in future releases of that
standard
… [read more](https://complianceforge.com/blog/a-cybersecurity-practitioners-thoughts-on-conflicting-cmmc-guidance/)
[](https://complianceforge.com/blog/nist-800171-cmmc-terms-guide/)
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hie
… [read more](https://complianceforge.com/blog/nist-800171-cmmc-terms-guide/)
[](https://complianceforge.com/blog/nist-sp-80053-vs-fedramp-vs-sp-800171-a-clear-guide/)
NIST SP 800-53 R5 vs FedRAMP R5 vs NIST SP 800-171 R2 vs NIST SP 800-171 R3
Within the Defense Industrial Base (DIB), there is considerable confusion about the concept of "FedRAMP equivalency" as it p
… [read more](https://complianceforge.com/blog/nist-sp-80053-vs-fedramp-vs-sp-800171-a-clear-guide/)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
[gsa oasis+ j](https://complianceforge.com/blog/gsa-oasis-j3-cscrm-deliverables/) [your cmmc requirements guide](https://complianceforge.com/blog/your-cmmc-requirements-guide/)
## NIST 800-171 Rev 3
[Skip to main content](https://complianceforge.com/blog/nist-800171-r3/#main-content)
[](https://complianceforge.com/blog/nist-800171-r3/)
NIST 800-171 Rev 3 was released on 14 May of this year, and it contains significant changes from the NIST 800-171 Rev 2.
ComplianceForge has gone ahead updated its NIST Compliance Program (NCP) to include NIST 800-171 Rev 3. What makes the NCP great is that it makes it less painful to upgrade to the latest version of NIST 800-171 and also provides backwards compatibility with NIST 800-171 Rev 2. This is beneficial, since you can demonstrate coverage for the current version of NIST 800-171 Rev 2, while you implement the new controls from NIST 800-171 Rev 3.
[https://complianceforge.com/product/nist-800-171-compliance-program/](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge is focused on making the documentation side of the NIST SP 800-171 R3 upgrade as painless, as possible. We already have policies, standards and procedures to address all of the requirements for the initial public draft of NIST SP 800-171 R3, so our solutions will be available as soon as the final release of NIST 800-171 R3 is available.
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hierarchical nature of cybersecurity documentation is needed to demonstrate the unique nature of these components, as well as the dependencies that exist.
ComplianceForge created a reference model that is designed to encourage clear communication by defining cybersecurity documentation components and how those are linked. This model is based on industry-recognized terminology from NIST, ISO, ISACA and AICPA to addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, assessment objectives, risks, threats, procedures & metrics. This also addresses what SSPs, POA&Ms and secure configurations are and how those integrate into an organization's existing cybersecurity documentation.
There is a lot of discussion on the initial public draft of NIST SP 800-171 R3 about operational impacts in a transition from -171 R2. Overall, the changes are positive, but there is still change that companies have to address. For those who want a head start, our [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/) solution comes with a year of updates, so when NIST SP 800-171 R3 is released in its final version, those clients will get updated versions of the documentation (with errata as to what has changed). This process helps streamline the documentation management process, so it is clear what has changed and makes it easier to go through change control processes to update documentation.
- NIST 800-171 R3 policies, standards procedures
- NIST 800-161-based Supply Chain Risk Management Plan (SCRM Plan)
- SSP & POA&M Templates
- Risk Assessment Templates
- And More!
- [#CMMC](https://complianceforge.com/blog/tag/CMMC)
- [#DFARS](https://complianceforge.com/blog/tag/DFARS)
- [#NIST 800-171 R3](https://complianceforge.com/blog/tag/NIST+800-171+R3)
- [#Policies](https://complianceforge.com/blog/tag/Policies)
- [#Procedures](https://complianceforge.com/blog/tag/Procedures)
- [#SCRM Plan](https://complianceforge.com/blog/tag/SCRM+Plan)
- [#Standards](https://complianceforge.com/blog/tag/Standards)
- [Email](mailto:?subject=NIST%20800-171%20R3%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fnist-800171-r3%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fnist-800171-r3%2F&title=NIST%20800-171%20R3%20-%20ComplianceForge&summary=NIST%20800-171%20R3%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fnist-800171-r3%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
800 171 r3, nist 800 171 compliance, 800 171 rev 3, nist 171 compliance, nist sp 800 171 rev 3 draft, nist 800 171 r3, nist 800171, nist 800 171 email
## NIST 800-171 Compliance
[Skip to main content](https://complianceforge.com/compliance/nist-800-171#main-content)

# NIST 800-171 R2 & R3 Compliance Documentation For DFARS
ComplianceForge has been on the forefront of developing editable policies, standards, procedures and other templates to address NIST 800-171 compliance since 2016 when it was first released. As Department of Defense (DoD) requirements evolved to include third-party attestation through the Cybersecurity Maturity Model Certification (CMMC), so did ComplianceForge’s solutions, where we offer affordable, editable cybersecurity policies, standards, procedures and other templates to address NIST 800-171 R2 & R3.
NIST 800-171 compliance starts with documentation for the very simple fact that when it comes to cybersecurity compliance, if it is not documented then it does not exist. That is the reality of how audits/assessments work and non-existent or weak documentation can lead to non-compliance. We've been involved in NIST 800-171 compliance since 2016, where we have a long track record of successfully supporting our clients with quality documentation and support.
When it comes to NIST 800-171 compliance, ComplianceForge's editable policies, standards, procedures and other templates are a business accelerator - our products can save you time and significantly reduce the labor costs that are traditionally associated with researching and developing NIST 800-171 policies, standards and procedures on your own or by hiring a consultant to do it for you. These are not "fill in the blanks" templates - while they are expected to be edited for your specific needs, these policies, standards and procedures templates are written to address leading secure practices. ComplianceForge documentation can be scoped to address multiple environments (e.g., on-premises and/or in a hosted environment).
## Editable NIST 800-171 Policies, Standards, Procedures Templates
In addition to battle tested NIST 800-171 R2 documentation solutions, ComplianceForge has [policies, standards, procedures and other documentation](https://complianceforge.com/cmmc-nist-800-171-templates/) (e.g., SCRM plan) necessary to comply with NIST 800-171 R3. This includes mapping procedures down to the Assessment Objective (AO)-level in NIST 800-171A R3 to ensure that there is comprehensive coverage for your compliance needs.
The "NIST 800-171 in a nutshell" graphic show below helps depict NIST 800-171 R3 requirements from Peope, Process, Technology, Data and Facility (PPTDF) perspective. This can help better visualize what the various requirements are (e.g., administrative, technical solutions, configurations, etc.). You can download the [PDF version](https://complianceforge.com/content/pdf/guide-nist-800-171-r3-nutshell.pdf "NIST 800-171 R3 in a nutshell") here and you can read more about the [concept of PPTDF here](https://complianceforge.com/blog/people-processes-technology-data-facilities-pptdf/ "people processes technology data facility").
- **PEOPLE**\- A "people" control is primarily applied to humans (e.g., employees, contractors, third-parties, etc.).
- **PROCESS**\- A "process" control is primarily applied to a manual or automated process.
- **TECHNOLOGY**\- A "technology" control is primarily applied to a system, application and/or service.
- **DATA**\- A "data" control is primarily applied to data (e.g., CUI, CHD, PII, etc.).
- **FACILITY**\- A "facility" control is primarily applied to a physical building (e.g., office, data center, warehouse, home office, etc.).
[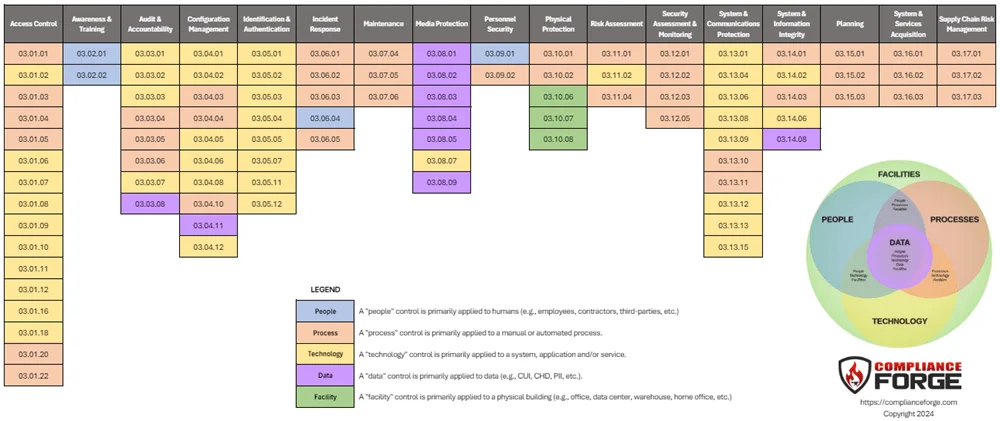](https://complianceforge.com/content/pdf/guide-nist-800-171-r3-nutshell.pdf "NIST 800-171 R3 In A Nutshell")
## NIST 800-171 R3 Documentation Upgrade Path
Sooner, rather than later, the US Government's global supply chain will have to transition to NIST 800-171 R3. ComplianceForge provides a free resource for organizations migrating from NIST 800-171 R2 to R3. This guide provides an Assessment Objective (AO)-level analysis to address differences:
- Over 1/3 are minimal effort (clear, direct mapping);
- Approximately 1/5 are moderate effort (indirect mapping); and
- Approximately 1/2 are significant effort (no clear mapping or new AOs).
This guide also addresses the logical dependencies that exist from "orphaned AOs" that are not in NIST 800-171A R3, but a requirement to demonstrate evidence of due diligence and due care still exists for specific functions (e.g., maintenance operations, roles & responsibilities, inventories, physical security, etc.).
[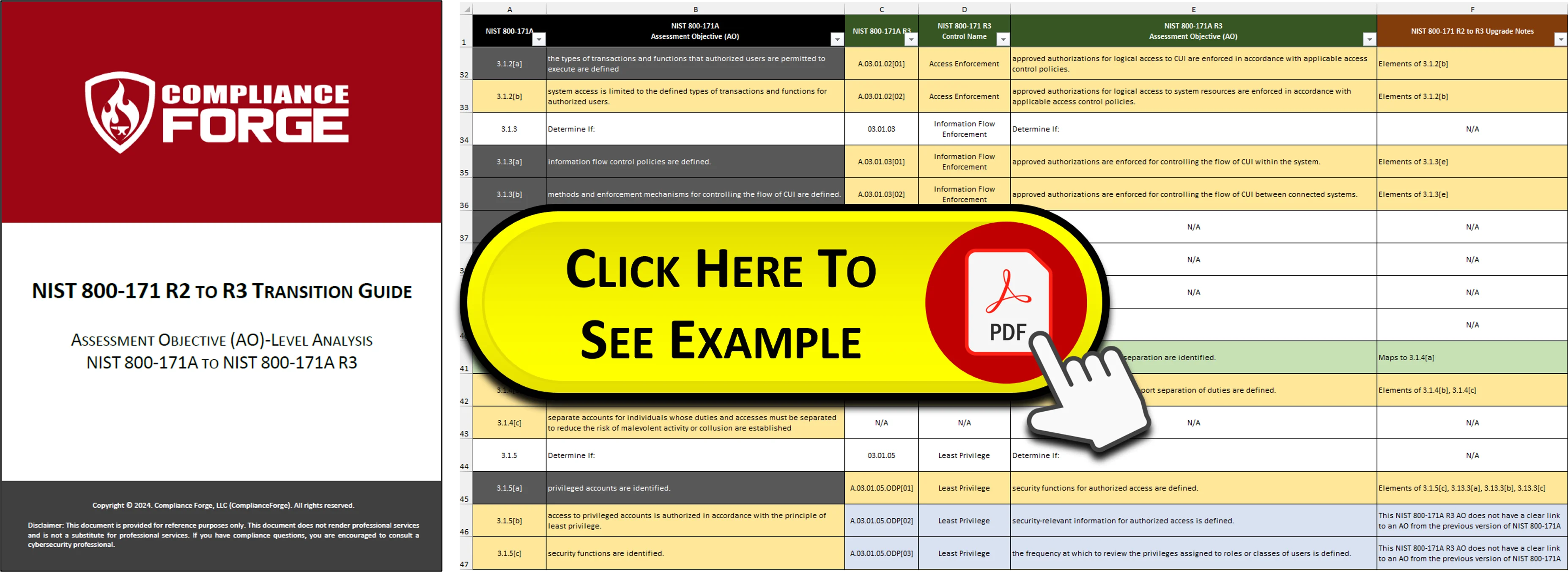](https://complianceforge.com/content/pdf/guide-nist-800-171-r3-transition.pdf "NIST 800-171 R2 to R3 upgrade")
## NIST 800-171 Documentation Done Right - Scalable, Comprehensive & Efficient
ComplianceForge is an industry leader in NIST 800-171 compliance. We specialize in [cybersecurity compliance documentation](https://complianceforge.com/cmmc-nist-800-171-templates/ "NIST 800-171 compliance policy procedures documentation") and our products include the policies, standards, procedures and POA&M/SSP templates that companies (small, medium and large) need to comply with NIST 800-171. We've been writing cybersecurity documentation since 2005 and we've been writing documentation specific to NIST 800-171 since 2016. We are here to help make NIST 800-171 compliance as easy and as affordable as possible!
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hierarchical nature of cybersecurity documentation is needed to demonstrate the unique nature of these components, as well as the dependencies that exist. ComplianceForge created a reference model that is designed to encourage clear communication by defining cybersecurity documentation components and how those are linked. This model is based on industry-recognized terminology from NIST, ISO, ISACA and AICPA to addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, assessment objectives, risks, threats, procedures & metrics. This also addresses what SSPs, POA&Ms and secure configurations are and how those integrate into an organization's existing cybersecurity documentation.
We leverage the **[Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/ "Hierarchical Cybersecurity Governance Framework")** to develop the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care for our clients. This methodology towards documentation acknowledges the interconnectivity that exists between policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. Essentially, ComplianceForge simplified the concept of the hierarchical nature of cybersecurity and privacy documentation that you can see in the downloadable diagram shown below. This helps demonstrate the unique nature of these components, as well as the dependencies that exist. You can download the example to better understand how we write our documentation that links policies all the way down to metrics. This is a great solution for any organization currently using or migrating to a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) platform to help automate their governance practices. Click on the image below to download the PDF:
[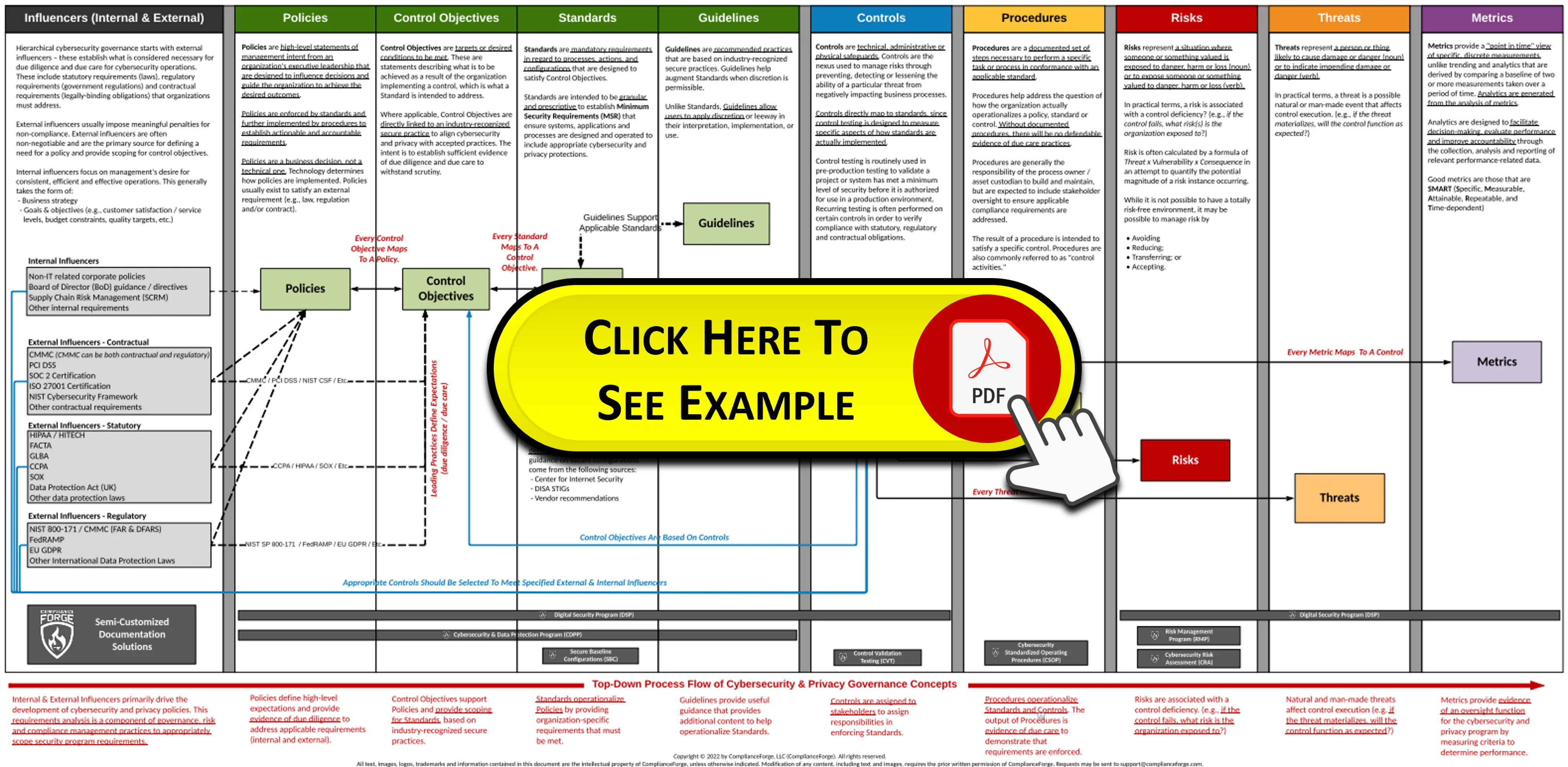](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "NIST 800-171 & CMMC compliance documentation terminology reference example")
## “DIBCAC Battle Tested” Policies, Standards & Procedures
ComplianceForge’s [NIST 800-171 / CMMC documentation](https://complianceforge.com/cmmc-nist-800-171-templates/) has been used successfully by multiple companies during DIBCAC assessments to efficiently and effectively generate the necessary artifact documentation to demonstrate compliance with NIST SP 800-171 controls and NIST SP 800-171A control objectives. This battle tested documentation includes the necessary policies, standards, procedures, SSP, POA&M, Incident Response Plan (IRP) and other documentation that are expected to exist to successfully pass a third-party assessment, be it DIBCAC or a C3PAO.
When you look at NIST 800-171 as it compares to other cybersecurity requirements, it is requiring companies to have a relatively-strong set of cybersecurity controls in place that range from administrative processes to protective technologies. We help customers that range from the Fortune 500 down to small and medium-sized businesses comply with this [DFARS](https://complianceforge.com/compliance/nist-800-171 "dfars cybersecurity requirement") requirement. Our products are scalable, professionally-written and affordable.
## Understanding NIST SP 800-171 vs NIST SP 800-53 vs FedRAMP
The graphic below shows how NIST SP 800-171 R3 (green columns) is significantly less than NIST SP 800-53 R5 moderate baseline (blue columns) and FedRAMP R5 moderate baseline (orange colums). This is an "apples to apples" comparison of control coverage, based on a mapping from NIST SP 800-53 R5, which is the source of the controls from NIST SP 800-171 R3 IPD and FedRAMP R5. The reason we show this is to approach compliance with your eyes wide open to what the requirements actually are.
[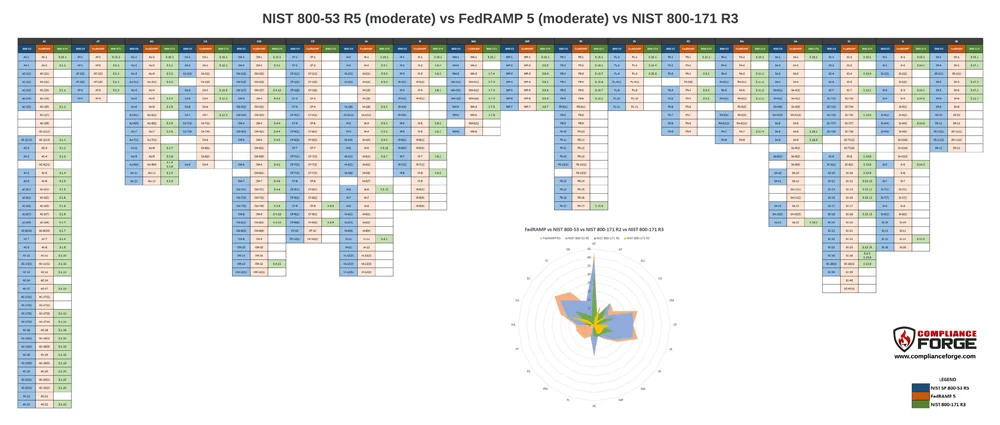](https://complianceforge.com/content/pdf/guide-nist-800-53-vs-fedramp-vs-800-171.pdf "NIST 800-53 vs FedRAMP vs NIST 800-171 R3")
Our NIST 800-171 compliance products are designed to scale for organizations of any size or level of complexity, so we serve businesses of all sizes, from the Fortune 500 all the way to small and medium businesses. The focus of NIST 800-171 is to protect [**Controlled Unclassified Information (CUI)**](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret "Controlled Unclassified Information CUI definition") anywhere it is stored, transmitted and processed.
[](https://complianceforge.com/cmmc-nist-800-171-templates/ "NIST 800-171 CMMC policies standards procedures template")
As a quick summary of your requirements to comply with NIST 800-171, you are expected to have several different "documentation artifacts" to prove that your cybersecurity program exists. The reality with compliance assessments is that if something is not documented, you cannot prove it exists. Given that reality, you need to ensure your company has the proper cybersecurity documentation in place:
- **Cybersecurity policies, standards & procedures;**
- **System Security Plan (SSP)** (requirement #3.12.4); and
- **Plan of Action & Milestones (POA&M)**(requirements #3.12.1, 3.12.2, 3.12.3 & 3.12.4).

## Cybersecurity Maturity Model Certification (CMMC)
The chart below depicts all [**Capability Maturity Model Certification (CMMC)**](https://complianceforge.com/compliance/cmmc "CMMC certified") v2.0 requirements and how they map to other frameworks:
[](https://cmmc-coa.com/ "CMMC center of awesomeness spreadsheet")
[](https://complianceforge.com/product/nist-800-171-compliance-program/ "editable NIST 800-171 policies standards procedures scrm plan")
## NIST 800-171 Scoping Considerations - Free Guide To Reducing Controlled Unclassified Information (CUI)
| | |
| --- | --- |
| [](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "NIST 800-171 scoping criteria")
Click [here](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "NIST 800-171 scoping guidance") for a **FREE GUIDE** | We put together a free guide to help identify what is in scope for NIST 800-171. Once you know what your CUI is, the next step is to scope your environment and this is a valuable guide for those efforts. Not sure what CUI is or if you have CUI on your network? Go to the US government's authoritative source on the matter, the US Archives CUI Registry at [https://www.archives.gov/cui/registry/category-list](https://www.archives.gov/cui/registry "NIST 800-171 CUI definition example").
When you look at NIST 800-171 rev 1 compliance, it has some similarities to the Payment Card Industry Data Security Standard (PCI DSS). That may sound odd to you, but from the perspective of PCI DSS, if scoping is done poorly, a company's entire network may be in-scope as the Cardholder Data Environment (CDE), which means PCI DSS requirements would apply uniformly throughout the entire company. The same holds true for CUI environments. In these scenarios, PCI DSS compliance can be prohibitively expensive or even technically impossible. However, when the network is intelligently-designed with security in mind, the CDE can be a small fraction of the company's network, which makes compliance much more achievable and affordable.
Based on a lack of scoping guidance from the DoD, our assessment of scoping NIST 800-171 is that it should following a similar, structured approach to scoping that is used for PCI DSS compliance. The reason for this is the proposed approach is a reasonable method, based on accepted practices to comply with cybersecurity requirements. This guide is meant to help companies identify assets within scope for NIST 800-171 and potentially find ways to minimize scope through isolation or controlled access. |
## What ComplianceForge Products Apply To NIST 800-171 Rev 2 Compliance?
Complying with the requirements from **[DFARS](https://complianceforge.com/compliance/nist-800-171)** goes beyond just having policies and standards. When you break down the requirements to comply with **[DFARS / NIST 800-171](https://complianceforge.com/compliance/nist-800-171)**, you will see how ComplianceForge's products address a specific DFARS compliance need. In the chart, "NFO" stands for Non-Federal Organization. NFO controls are required for contractors and are called out in Appendix E of NIST 800-171. Aligning with NIST 800-53 is the most straightforward approach to complying with NIST 800-171, based on the official mappings in Appendices D & E of NIST 800-171.
| | | |
| --- | --- | --- |
| **ComplianceForge Product** | **DFARS / NIST 800-171** | **NIST 800-53** |
| NIST 800-171 Compliance Program ( **NCP**), Cybersecurity & Data Protection Program ( **CDPP**) or Digital Security Program ( **DSP**)
\[policies & standards map to all NIST 800-171 rev1 requirements\] | 252.204-7008
252.204-7012
**NIST 800-171 (multiple NFO controls)** | PM-1
\[multiple sections\] |
| Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan ( **C-SRCM SIP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO PS-7** | PS-7
SA-4 |
| Cybersecurity Risk Management Program ( **RMP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO RA-1** | PM-9
RA-1 |
| Cybersecurity Risk Assessment Template ( **CRA**) | 252.204-7008
252.204-7012
**NIST 800-171 3.11.1** | RA-3 |
| Vulnerability & Patch Management Program ( **VPMP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.11.2** | SI-2
SI-3(2) |
| Integrated Incident Response Program ( **IIRP**) | 252.204-7008
252.204-7009
252.204-7010
252.204-7012
**NIST 800-171 3.6.1** | IR-1 |
| Security & Privacy By Design ( **SPBD**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO SA-3** | Privacy Section
SA-3 |
| System Security Plan ( **SSP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.12.4** | PL-2 |
| Cybersecurity Standardized Operating Procedures ( **CSOP**) | 252.204-7008
252.204-7012
**NIST 800-171 (multiple NFO controls)** | PL-7
\[multiple sections\] |
| Continuity of Operations Plan ( **COOP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.6.1** | CP-1
CP-2
IR-4(3)
PM-8 |
| Secure Baseline Configurations ( **SBC**) | 252.204-7008
252.204-7012
**NIST 800-171 3.4.1** | CM-2
CM-6
SA-8 |
| Information Assurance Program ( **IAP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO CA-1** | CA-1
PM-10 |
## Framework Alignment Matters For CMMC 2.0 & NIST 800-171 Compliance!
Many people ask how NIST 800-171 is different from NIST 800-53. In reality, there is no NIST 800-171 vs NIST 800-53, since everything defaults back to NIST 800-53. Our solutions address both DFARS and FAR requirements for protecting Controlled Unclassified Information (CUI) by addressing NIST 800-171 and its corresponding NIST 800-53 requirements.

When it comes to being "audit ready" for a company with NIST 800-171, there is no such thing as "Bronze, Silver or Gold" levels of compliance since a standard is a standard for a reason. This is where documentation is king, since in cybersecurity compliance audits, if it is not documented then it does not exist.
ComplianceForge can provide you with the documentation you need to demonstrate evidence of due care and due diligence to be considered compliant (e.g., policies, standards, procedures, SSP & POA&M). Our affordable solutions range from [**cybersecurity policies & standards**](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-171 compliance policies") documentation, to [**NIST 800-171 compliance checklists**](https://complianceforge.com/nist-800-171-cmmc-policy-templates/ "NIST 800-171 compliance checklist template"), to program-level documentation, such as "turn key" [**incident response**](https://complianceforge.com/digital-cybersecurity-incident-response-program-documentation/ "NIST 800-171 incident response policy IRP"), [**risk management**](https://complianceforge.com/digital-cybersecurity-risk-management/ "NIST 800-171 risk management risk assessment") or [**vulnerability management**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "NIST 800-171 vulnerability management flaw remediation patching policy ") program documents. Our focus is on helping you become audit ready!
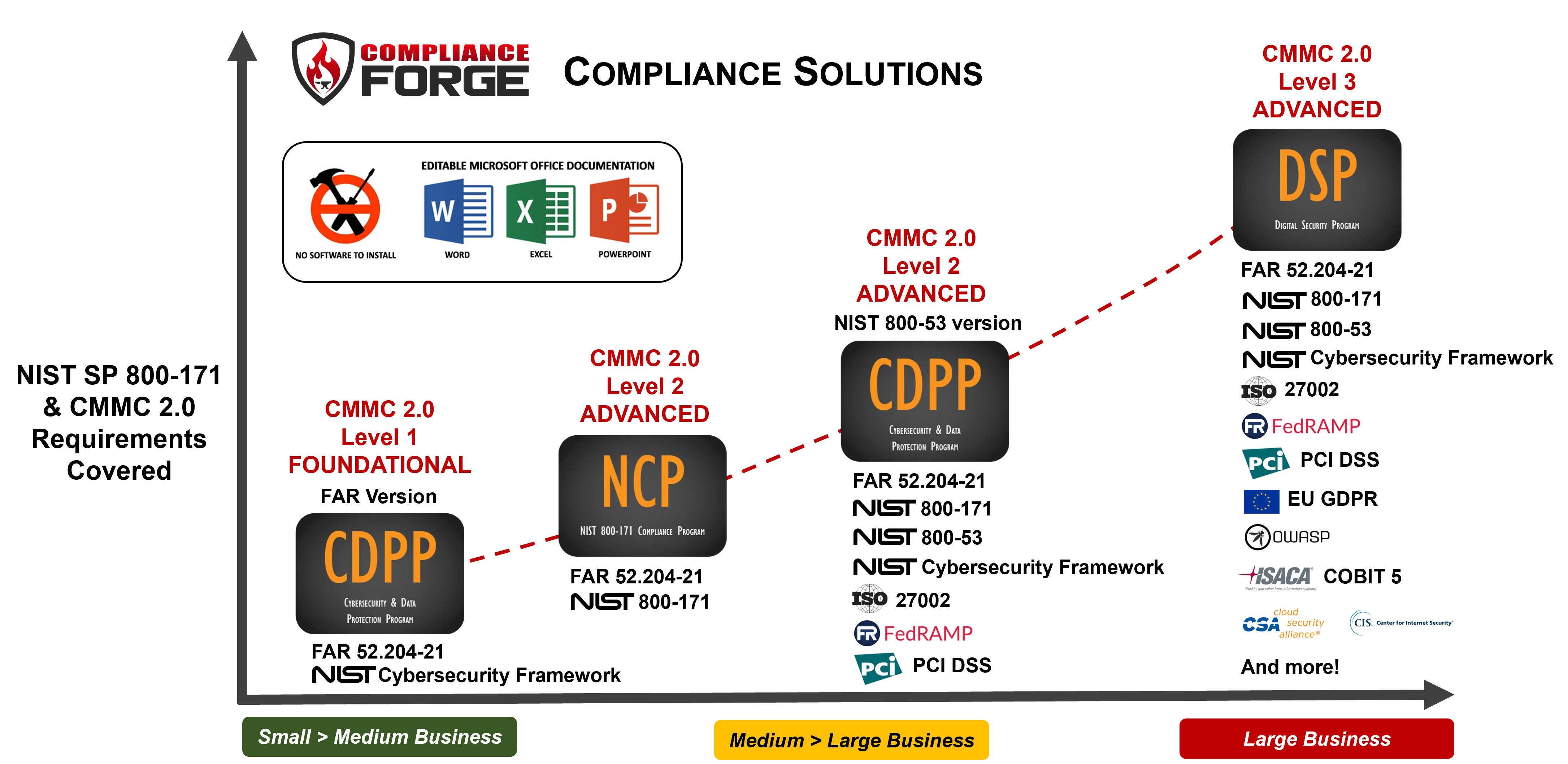
NIST 800-171 is intended to force contractors to adhere with reasonably-expected security requirements that have been in use by the US government for years. NIST 800-171 establishes a basic set of expectations and maps these requirements to NIST 800-53, which is the de facto standard for US government cybersecurity controls. In some ways, this is a good thing since the US government is not reinventing the wheel with new requirements. Instead, the DoD selected moderate-level controls from an existing set of recognized best practices, commonly used throughout the DoD and Federal agencies. In the long run, this will help both the US government and private businesses speak the same language for cybersecurity.
The bottom line is NIST 800-171 creates a standardized and uniform set of requirements for all **Controlled Unclassified Information (CUI)** security needs. This is designed to address common deficiencies in managing and protecting unclassified information by that is being stored, transmitted or processed by private businesses.
## Cost of Non-Compliance With NIST 800-171 (DFARS 252.204-7012)
What can possibly go wrong with non-compliance in a contract with the U.S. Government?
- **Contract Termination**. It is reasonably expected that the U.S. Government will terminate contracts with prime contractors over non-compliance with DFARS / NIST 800-171 requirements since it is a failure to uphold contract requirements. Subcontractor non-compliance will cause a prime contractor to be non-compliant, as a whole.
- **Criminal Fraud**. If a company states it is compliant when it knowingly is not compliant, that is misrepresentation of material facts. This is a criminal act that is defined as any act intended to deceive through a false representation of some fact, resulting in the legal detriment of the person who relies upon the false information (e.g., False Claims Act).
- **Breach of Contract Lawsuits**. Both prime contractors and subcontractors could be exposed legally. A tort is a civil breach committed against another in which the injured party can sue for damages. The likely scenario for a DFARS / NIST 800-171-related tort would be around negligence on behalf of the accused party by not maintaining a specific code of conduct (e.g., DFARS / NIST 800-171 cybersecurity controls).
As you can see from those examples, the cost of non-compliance is quite significant. As always, seek competent legal counsel for any pertinent questions on your specific compliance obligations.
## What Problem Does ComplianceForge Solve?
We sell cybersecurity documentation - policies, standards, procedures and more! Our documentation is meant to help companies become audit-ready!
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive NIST 800-171 compliance documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. ComplianceForge offers NIST 800-171 documentation solutions that can save your organization significant time and money!
- Compliance Requirements \- The reality of non-compliance with NIST 800-171 requirements means lost business and potential fines. In addition to losing contracts, charges of fraud may be leveled on companies that claim to be compliant with NIST 800-171 but cannot provide evidence. Our documentation can help you become and stay compliant with NIST 800-171 where you have documented evidence to prove it!
- Audit Failures \- Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. Our documentation provides mapping to NIST 800-53 and other leading security frameworks to show you exactly what is required to both stay secure and compliant. Being editable documentation, you are able to easily maintain it as your needs or technologies change.
## How Does ComplianceForge Solve It?
We take a holistic approach to creating comprehensive cybersecurity documentation that is both scalable and affordable. This is beyond just generic policies and allows you to build out an audit-ready cybersecurity program for your organization!
- Clear Documentation \- In an audit, clear and concise documentation is half the battle. ComplianceForge provides comprehensive documentation that can prove your NIST 800-171 compliant security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings \- Time is money! Our cybersecurity documentation addresses DFARS and FAR requirements and this can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - We did the heavy lifting. Our documentation is mapped to the NIST 800-53, as well as other leading security frameworks!

## DFARS 252.204-7012 (NIST 800-171 Rev 2) Implications and Federal Acquisition Regulation (FAR)
Many of our clients who need to address **DFARS 252.204-7012** (NIST 800-171) also have to address **FAR 52.204-21**. One common question we receive from clients pertains to aligning with the correct security framework to ensure they have the proper coverage for compliance. This generally revolves around aligning with ISO 27001/27002 or NIST 800-53, since those are the two most [common security frameworks](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf "NIST 800-53 NIST 800-171 ISO 27002 compliance").
The bottom line is that utilizing ISO 27001/27002 as a security framework does not meet the requirements of NIST 800-171. In fact, NIST 800-171 (Appendix D) maps out how the CUI security requirements of NIST 800-171 relate to NIST 800-53 and ISO 27001/27002 security controls. This includes callouts where the ISO 27001/27002 framework does not fully satisfy the requirements of NIST 800-171. Therefore, policies and standards based on NIST 800-53 are what is needed to comply with NIST 800-171. This is important to keep in mind, since FAR changes will require all US government contractors to adopt NIST 800-171 requirements in the near future.
NIST 800-171 isn’t just for Department of Defense (DoD) contractors. Representatives from the National Institute of Standards and Technology (NIST) and DoD officials have recently been putting this information out in webinars and other training seminars on NIST 800-171. This means that only the NIST 800-53 framework is going to meet FAR requirements - ISO 27002 and the NIST Cybersecurity Framework are going to be insufficient in coverage. This coming requirement for FAR cybersecurity compliance is specified on **page v of NIST 800-171**:
_Executive Order 13556, Controlled Unclassified Information, November 4, 2010, establishes that the Controlled Unclassified Information (CUI) Executive Agent designated as the **National Archives and Records Administration (NARA), shall develop and issue such directives as are necessary to implement the CUI Program. Consistent with this tasking and with the CUI Program’s mission to establish uniform policies and practices across the federal government, NARA is issuing a final federal regulation in 2016 to establish the required controls and markings for CUI government-wide. This federal regulation, once enacted, will bind agencies throughout the executive branch to uniformly apply the standard safeguards, markings, dissemination, and decontrol requirements established by the CUI Program.**_
_With regard to federal information systems, requirements in the federal regulation for protecting CUI at the moderate confidentiality impact level will be based on applicable policies established by OMB and applicable government-wide standards and guidelines issued by NIST. The regulation will not create these policies, standards, and guidelines which are already established by OMB and NIST. The regulation will, however, require adherence to the policies and use of the standards and guidelines in a consistent manner throughout the executive branch, thereby reducing current complexity for federal agencies and their nonfederal partners, including contractors._
_In addition to defining safeguarding requirements for CUI within the federal government, NARA has taken steps to alleviate the potential impact of such requirements on nonfederal organizations by jointly developing with NIST, Special Publication 800-171 — and defining security requirements for protecting CUI in nonfederal systems and organizations. This approach will help nonfederal entities, including contractors, to comply with the security requirements using the systems and practices they already have in place, rather than trying to use government-specific approaches. It will also provide a standardized and uniform set of requirements for all CUI security needs, tailored to nonfederal systems, allowing nonfederal organizations to be in compliance with statutory and regulatory requirements, and to consistently implement safeguards for the protection of CUI._
**_Finally, NARA, in its capacity as the CUI Executive Agent, also plans to sponsor in 2017, a single Federal Acquisition Regulation (FAR) clause that will apply the requirements contained in the federal CUI regulation and Special Publication 800-171 to contractors. This will further promote standardization to benefit a substantial number of nonfederal organizations that are attempting to meet the current range and type of contract clauses, where differing requirements and conflicting guidance from federal agencies for the same information gives rise to confusion and inefficiencies. The CUI FAR clause will also address verification and compliance requirements for the security requirements in NIST Special Publication 800-171. Until the formal process of establishing such a FAR clause takes place, the requirements in NIST Special Publication 800-171 may be referenced in federal contracts consistent with federal law and regulatory requirements. If necessary, Special Publication 800-171 will be updated to remain consistent with the federal CUI regulation and the FAR clause._**
## Affordable, Editable NIST 800-171 Compliance Documentation (DFARS 252.204-7012)
We listened to our customers and we created several products that are specific to NIST 800-171 compliance. We had an overwhelming request from companies to help them become NIST 800-171 compliant and most told us they do not know where to start, but they just know that this is a requirement they cannot run from.
The concept is pretty simple - the NIST 800-171 Compliance Criteria (NCC) goes through each NIST 800-171 requirement and maps it to the corresponding NIST 800-53 rev 4 controls. Each of those NIST 800-53 controls is explained as to what reasonably-expected criteria would be to meet that control. Additionally, the NCC provides applicable "best practice" guidance on what steps you need to take in order to comply. That is exactly what you would expect from a dedicated consultant! What do you get if you buy the NCC?
- The NCC is a “consultant in a box” solution that is essentially a NIST 800-171 checklist in an editable Microsoft Excel format.
- The NCC covers all controls in Appendix D of NIST 800-171.
- It also covers Appendix E Non-Federal Organization (NFO) controls, which are required by contractors.
- Each of the NIST 800-171 controls is mapped to its corresponding NIST 800-53 control.
- Each of the NIST 800-53 controls are broken down to identify:
- Reasonably-expected criteria to address the control;
- Applicable compliance guidance;
- Methods to address the requirement; and
- Status of compliance for each control so you can use it for a self-assessment.
- The NCC maps to the [Cybersecurity & Data Protection Program (CDPP)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/ "NIST 800-171 compliance policies") and [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)") products, so they can work in concert together to make it easier to comply with NIST 800-171 since your organization can have NIST-based policies and standards to support NIST 800-171 compliance efforts.
## Background on NIST 800-171 Rev 2 Controls
NIST 800-171 requires private companies to protect the confidentiality of Controlled Unclassified Information (CUI). The CUI requirements within NIST 800-171 are directly linked to NIST 800-53 MODERATE baseline controls and are intended for use by federal agencies in contracts or other agreements established between those agencies and non-federal organizations (e.g., government / DoD contractors). The good news is that ComplianceForge can help you with your compliance needs! We have affordable solutions that range from the NIST 800-171 Compliance Criteria (NCC) all the way to providing you with comprehensive cybersecurity policies and standards, such as the [**NIST 800-53 Cybersecurity & Data Protection Program (CDPP)**](https://complianceforge.com/product/nist-800-53-based-security-documentation-wisp/ "NIST 800-53 Cybersecurity & Data Protection Program for NIST 800-171 compliance").
Appendix D of NIST 800-171 provides a direct mapping of CUI security requirements to the security controls in NIST 800-53 rev4 and ISO/IEC 27001:2013. This security control mapping information can be useful to organizations that wish to demonstrate compliance to the CUI security requirements in the context of their established information security programs, when such programs have been built around the NIST or ISO frameworks. NIST 800-53 has direct mapping, where ISO 27001/27002 has gaps that would have to be filled with enhanced policies and standards.
A central tenant to NIST 800-171 is a need to focus on secure engineering. However, it is important to keep in mind that this expectation for operationalizing security and privacy principles is not limited to NIST 800-171:
- **NIST 800-53** \- SA-8;
- **NIST Cybersecurity Framework** \- PR.IP-2;
- **ISO 27002** \- 14.2.5 & 18.1.4;
- Federal Acquisition Regulations ( **FAR**) 52.204-21 - 4;
- National Industrial Security Program Operating Manual ( **NISPOM**) \- 8-302 & 8-311;
- **SOC2** \- CC3.2;
- Generally Accepted Privacy Principles ( **GAPP**) \- 4.2.3, 6.2.2, 7.2.2 & 7.2.3;
- New York State Department of Financial Service ( **DFS**) \- 23 NYCRR 500.08;
- Payment Card Industry Data Protection Standard ( **PCI DSS**) \- 2.2;
- Center for Internet Security Critical Security Controls ( **CIS CSC**) \- 1.2, 5.9, 6.2, 6.3, 6.4, 6.5, 7.1, 7.2, 7.3, 7.4, 7.5, 7.6, 7.7, 7.8, 8.6, 9.1, 9.2, 9.3, 9.4, 9.5, 9.6, 11.4, 11.5, 11.6, 11.7, 13.4, 13.5 & 16.5; and
- European Union General Data Protection Regulation ( **EU GDPR**) \- 5 & 25.
## Key Assumptions For NIST 800-171 That Impact Scoping
NIST 800-171 states that contractors may limit the scope of the CUI security requirements to those particular systems or components. Isolating CUI into its own security domain by applying architectural design principles or concepts (e.g., implementing subnetworks with firewalls or other boundary protection devices) may be the most cost-effective and efficient approach for non-federal organizations to satisfy the requirements and protect the confidentiality of CUI. Security domains may employ physical separation, logical separation, or a combination of both.
## Is Your Organization Audit Ready for NIST 800-171?
When you "peel back the onion" and prepare for a NIST 800-171 audit, there is a need to address "the how" for certain topics. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW it gets done. We did the heavy lifting and created several program-level documents to address this need and they integrate with either the Cybersecurity & Data Protection Program (CDPP) or Digital Security Program (DSP) to provide your organization with a set of robust documentation to prepare for your audit. This gives you a full stack of documentation that covers your needs for policies, standards, procedures, System Security Plan (SSP) and a Plan of Action & Milestones (POA&M).
## NIST 800-171 Compliance Through A NIST 800-53 Rev5-Based Cybersecurity Program
US Federal agencies require NIST 800-171 compliance for protecting the confidentiality of Controlled Unclassified Information (CUI). The CUI requirements within NIST 800-171 are directly linked to NIST 800-53 MODERATE baseline controls and are intended for use by federal agencies in contracts or other agreements established between those agencies and nonfederal organizations (e.g., government contractors), as it applies to:
- When CUI is resident in nonfederal information systems and organizations;
- When information systems where CUI resides are not used or operated by contractors of federal agencies or other organizations on behalf of those agencies; and
- Where there are no specific safeguarding requirements for protecting the confidentiality of CUI prescribed by the authorizing law, regulation, or government-wide policy for the CUI category or subcategory listed in the CUI Registry
The NIST 800-171 requirements apply to all components of non-federal information systems and organizations that process, store, or transmit CUI, or provide security protection for such components. The good news is that ComplianceForge can help you with your compliance needs!
## Controlled Unclassified Information (CUI) - Understanding NIST 800-53 rev 5 MODERATE Controls
Does your company need to comply with NIST 800-171 requirements for MODERATE baseline controls from NIST 800-53? The good news is our [**NIST 800-53 based Cybersecurity & Data Protection Program (CDPP**](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/ "NIST 800-171 requirements for MODERATE baseline controls from NIST 800-53")) has the documentation you need to comply with MODERATE baseline controls.
The CUI requirements developed from the tailored FIPS Publication 200 security requirements and the NIST 800-53 moderate security control baseline represent a subset of the safeguarding measures necessary for a comprehensive information security program. The strength and quality of such programs in nonfederal organizations depend on the degree to which the organizations implement the security requirements and controls that are expected to be routinely satisfied without specification by the federal government. This includes implementing security policies,
The combination of the basic and derived security requirements captures the intent of FIPS Publication 200 and NIST 800-53, with respect to the protection of the confidentiality of CUI in nonfederal information systems and organizations. Appendix D provides informal mappings of the CUI security requirements to the relevant security controls in NIST 800-53 and ISO/IEC 27001. The mappings are included to promote a better understanding of the CUI security requirements and are not intended to impose additional requirements on nonfederal organizations.
For ease of use, the security requirements are organized into fourteen families. Each family contains the requirements related to the general security topic of the family. The families are closely aligned with the minimum security requirements for federal information and information systems described in FIPS Publication 200. The contingency planning, system and services acquisition, and planning requirements are not included within the scope of this publication due to the aforementioned tailoring criteria.
## What Does NIST 800-171 Require?
NIST 800-171 describes fourteen (14) families of security requirements for protecting the confidentiality of CUI. The families are aligned with the minimum security requirements for federal information and information systems described in Federal Information Processing Standard (FIPS) 200, with exceptions for contingency planning, system, and services acquisition and planning requirements.
Appendix D of NIST 800-171 maps requirements to both NIST 800-53 rev4 and ISO 27002:2013 best practices. Only NIST 800-53 offers complete coverage for NIST 800-171 requirements.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-2-L3)
#### [CMMC Bundle 2: Levels 1-2 (NIST 800-53 Moderate)](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-2-L3)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-171 & CMMC 2.0 Compliance Bundle #2 - ADVANCED CMMC Level 2 (25% discount)
Is your organization looking to achieve CMMC compliance? This is a bundle that includes the following five (5) ComplianceForge products that...
$14,040.00
$10,530.00 - $15,330.00
[Choose Options](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-2-L3)
- [](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-3-level-3)
#### [CMMC Bundle 3: Levels 1-3 (NIST 800-53 High)](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-3-level-3)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-171 & CMMC Compliance Bundle #3 - EXPERT CMMC 2.0 Levels 1-3 (40% discount)
Is your organization looking to acheive CMMC compliance? This is a bundle that includes the following thirteen (13) ComplianceForge...
$39,655.00
$23,793.00 - $28,593.00
[Choose Options](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-3-level-3)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[nist 800](https://complianceforge.com/cybersecurity-templates/nist-800-171-cmmc-compliance/) [begin your compliance journey: nist 800](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-compliance) [contact us](https://complianceforge.com/contact-us/) [buy nist 800](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/) [nist 800](https://complianceforge.com/product/nist-800-171-compliance-program/) [complianceforge](https://complianceforge.com/cart.php) [complianceforge's nist 800](https://complianceforge.com/nist-800-171/nist-800-171-r3-transition-guide/) [complianceforge](https://complianceforge.com/login.php) [discover nist sp 800](https://complianceforge.com/solutions/nist-800-53-r5-moderate-policies-procedures/) [affordable nist cybersecurity solutions by complianceforge](https://complianceforge.com/solutions/nist-csf-policies-standards-procedures/)
nist 800 171 checklist excel, nist 800 53 rev 2, nist 800 171 vs 800 53, nist 800 171 rev 4, nist 800 171 rev 2, cui and 800 53, nist 800 171 compliance for government contractors orange county ca, nist sp 800 171 rev 2, nist 800 171 compliance contractor, nist 800 171 rev 5, nist 800 171 compliance checklist
## Multiple Company Discounts
[Skip to main content](https://complianceforge.com/faq/multiple-company-discount#main-content)
# Multiple Company Discounts
## **Do you need to cover subsidiaries or multiple companies?**
Our licensing model is structured for a single legal entity (e.g., single corporation, LLC, partnership, sole proprietor, state or county government, etc.). This means that if you need to cover subsidiaries or multiple businesses/organizations, it requires buying a license for each of these legal entities that are going to use the product(s). However, we have a pricing structure to provide significant discounts for customers who need to cover multiple entities - up to 70% off!
## **Discount Structure**
We provide a very generous discount for customers that need to cover multiple entities. This discounted pricing is restricted to a defined number of licenses that are covered by the same Purchase Order (PO). Discounted pricing is not applicable to "piecemeal" purchases of products over time.
| | |
| --- | --- |
| **License Quantity** | **Discount (%)** |
| 1 | 0% |
| 2 | 10% |
| 3 | 20% |
| 4 | 30% |
| 5-9 | 40% |
| 10-14 | 50% |
| 15-19 | 60% |
| 20+ | 70% |
### **Example Multiple License Discount Pricing**
The discounts apply for both single products or bundles. As you can see from below, getting significant savings off of an already discounted bundle can equate to tens of thousands of dollars in savings:
| | | | | | |
| --- | --- | --- | --- | --- | --- |
| **Item** | **Unit Price** | **Qty** | **Non-Discounted Total** | **Discount %** | **Discounted Total** |
| CDPP | $1,450 | 3 | $4,350 | 20% | $3,480 |
| NCP | $4,480 | 5 | $22,400 | 40% | $13,440 |
| DSP Bundle #3 (already discounted 45%) | $17,875 | 10 | $178,750 | 50% | $89,375 |
If you have any questions about how to get a customized quote, please contact us so we can help answer your questions.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Policies vs Standards
[Skip to main content](https://complianceforge.com/blog/cybersecurity-policies-vs-standards/#main-content)
[](https://complianceforge.com/blog/cybersecurity-policies-vs-standards/)
What is the difference between a policy and a standard? The differences are:
- 1.Granularity / specificity of requirements; and
- 2.Scope.
A [policy](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure) is a high-level statement of management’s intent that formally establishes requirements to guide decisions and has strategic implications for the entire organization. Policies are intended to come from the CEO or board of directors. A few policy examples are:
- EXAMPLE COMPANY shall ensure all technology platforms used in support of its business operations adhere with industry recognized secure configuration management practices. Current and accurate inventories of technology platforms shall be maintained so applicable secure configuration settings can be enforced on those technology platforms; or
- EXAMPLE COMPANY shall achieve and maintain situational awareness through comprehensive and ongoing monitoring activities to help ensure the security and resilience of its technology infrastructure against both physical and cyber threats. Technology assets shall be configured according to secure configuration management requirements to enable the capture of relevant security event logs. A centralized log analysis capability shall be used to identify anomalous behavior and support incident response operations so that appropriate steps can be taken to remediate potential incidents.
A [standard](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure) is a formally established requirement regarding a process, action or configuration that is meant to be an objective or quantifiable expectation to be met. Standards are granular, clear requirements that support policies. A few standards examples are:
- EXAMPLE COMPANY utilizes the “principle of least privilege,” which states that only the minimum access and functionality necessary to perform an operation should be granted and only for the minimum amount of time necessary. Asset custodians are required to:
- Identify and remove insecure services, protocols and ports;
- Enable only necessary and secure services, protocols and daemons, as required for the function of the system;
- Implement security features for any required services, protocols or daemons that are considered to be insecure (e.g., NetBIOS, Telnet, FTP, etc.);
- Verify services, protocols and ports are documented and properly implemented by examining device settings; and
- Remove all unnecessary functionality, such as:
- Scripts;
- Drivers;
- Features;
- Subsystems;
- File systems; and
- Unnecessary web servers.
- Asset custodians are required to configure all systems, devices and applications to implement automated audit trails for all system components and automatically forward security-related event logs to a centralized log collector or Security Incident Event Management (SIEM) solution to allow EXAMPLE COMPANY security personnel to reconstruct the following events:
- All individual user accesses to sensitive data (e.g., payment card data, SSNs, financial accounts, etc.);
- All actions taken by any individual with root or administrative privileges;
- Access to all audit trails;
- Invalid logical access attempts;
- Use of and changes to identification and authentication mechanisms, including but not limited to:
- Creation of new accounts and elevation of privileges; and
- All changes, additions or deletions to accounts with root or administrative privileges;
- Initialization, stopping or pausing of the audit logs; and
- Creation and deletion of system-level objects.
If you would like to learn more about policies & standards, you can read more about it here - [https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure](https://complianceforge.com/grc/policy-vs-standard-vs-control-vs-procedure).
You can also find additional information about policies, control objectives, guidelines, controls, procedures & metrics with examples here - [https://complianceforge.com/content/pdf/complianceforge-cybersecurity-documentation-template-examples.pdf](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-documentation-template-examples.pdf).
- [#Policy](https://complianceforge.com/blog/tag/Policy)
- [#Standard](https://complianceforge.com/blog/tag/Standard)
- [Email](mailto:?subject=Cybersecurity%20Policies%20vs%20Standards%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-policies-vs-standards%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-policies-vs-standards%2F&title=Cybersecurity%20Policies%20vs%20Standards%20-%20ComplianceForge&summary=Cybersecurity%20Policies%20vs%20Standards%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-policies-vs-standards%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Information Assurance Program
[Skip to main content](https://complianceforge.com/product/information-assurance-program#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/173/1525/complianceforge-information-assurance-program-iap__96179.1740599325.jpg?c=2)
No reviews yet
$4,235.00
(You save)
# Information Assurance Program (IAP)
SKU:P17-IAP-NOUPC:692878856973Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Pre-Production%20Cybersecurity%20Control%20Testing%20Program%20IAP&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Finformation-assurance-program "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Finformation-assurance-program&title=Pre-Production%20Cybersecurity%20Control%20Testing%20Program%20IAP&summary=Pre-Production%20Cybersecurity%20Control%20Testing%20Program%20IAP&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Finformation-assurance-program "Linkedin")

[](https://complianceforge.com/product/information-assurance-program#iap-example)
## Cybersecurity & Data Privacy Control Validation Testing
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the IAP is to help answer common questions we receive.
[](https://complianceforge.com/what-is-the-information-assurance-program-iap/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-information-assurance-program-iap/)
## What Is The **Information Assurance Program (IAP)?**
Is your organization looking for a cybersecurity assurance program? ComplianceForge's Information Assurance Program (IAP) is focused on pre-production testing and based on established processes used by the US Government (e.g., **FISMA**, **DIACAP**, **DIARMF**) to validate the existence and functionality of controls, prior to a system, application or service going into production. In US Government language, this is commonly referred to as Certification & Accreditation ( **CA**) or Security Testing & Evaluation ( **ST&E**). We "civilianized" this concept of CA/ST&E to create a method to enable cybersecurity and privacy personnel to work with your organization's existing System Development Life Cycle ( **SDLC**) / Project Development Life Cycle ( **PDLC**) to ensure privacy and cybersecurity principles are designed and built-into your systems, applications and services!
### **The end state with control validation testing is:**
- Removal of "security roadblocks" by embedding cybersecurity and privacy into the SDLC/PDLC from project kick-off through the "go live" data.
- Having evidence of both cybersecurity and privacy principles being identified and implemented by design (e.g., **EU GDPR compliance**)
- Utilizing a customized control sets that defines **Minimum Security Requirements (MSR)** specific to the project undergoing review.
- A data-centric view across systems, applications, services and third-parties that enables situational awareness of both cybersecurity and privacy risks.
- A **Project Risk Register (PRR)** that tracks risks and the associated remediation actions (e.g., Plan of Action & Milestones (POA&M)).
- A formal method of getting stakeholder accountability for residual risk.
## **What Problems Does The IAP Solve?**
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The IAP is an efficient method to obtain comprehensive system hardening documentation.
- Compliance Requirements - There are numerous requirements (several listed at the top of this page) that require pre-production security testing to be performed and documented. The IAP is designed with compliance in mind, since it focuses on leading "best practices" for ensuring systems, applications and services are verified to address reasonably-expected requirements for cybersecurity and privacy exist and function accordingly.
- Audit Failures - A lack of documented pre-production security testing is a common audit failure. The IAP covers traditional SDLC/PDLC models that include Agile, Waterfall and other approaches to project management. This is designed to integrate with your existing processes to bake in cybersecurity and privacy principles.
- Vendor Requirements - It is getting more common for clients and partners to request evidence of secure processes, including SDLC/PDLC security and privacy efforts. The IAP provides this evidence!
## **How Does the IAP Solve These Problems?**
- Clear Documentation - The IAP provides comprehensive cybersecurity and privacy pre-production testing to prove that your security is more than just a set of policies and standards.
- Time Savings - The IAP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The IAP is written to align your organization with leading practices for secure engineering processes.
## Why Should I Buy The IAP? What Actually Requires "Pre-Production Testing" To Be Performed?
As a CISO or CPO, performing IAP is not only the right thing to do from a security and privacy perspective, but it is serious job security. When things go bad and fingers get pointed, do you have a "get out of jail free card" that you can use? If not, keep reading.
A CISO or CPO should never make the decision to "sign off" and own risk, since it is ultimately a business decision and that director/VP of the business unit should be accepting the risk for their projects, services and vendors needed to operate. It is the responsibility of the CISO and CPO to have a data-centric view of risk from the application, system, service and supply chain perspective. With this understanding of the risks, the CISO and CPO need to educate the business process owners if minimum security requirements are/are not met and if the risk falls within the organization's risk appetite. This is where the CRO role defines what is acceptable risk and works with the business units to get them to hopefully make the correct GO/NO GO decision. If they do choose to do something outside of the risk appetite, the CRO/CISO/CPO has evidence to demonstrate due care in their analysis. A lot of this requires a mature pre-production control validation testing process, which is absent in many organizations beyond a rudimentary security gate for change control.
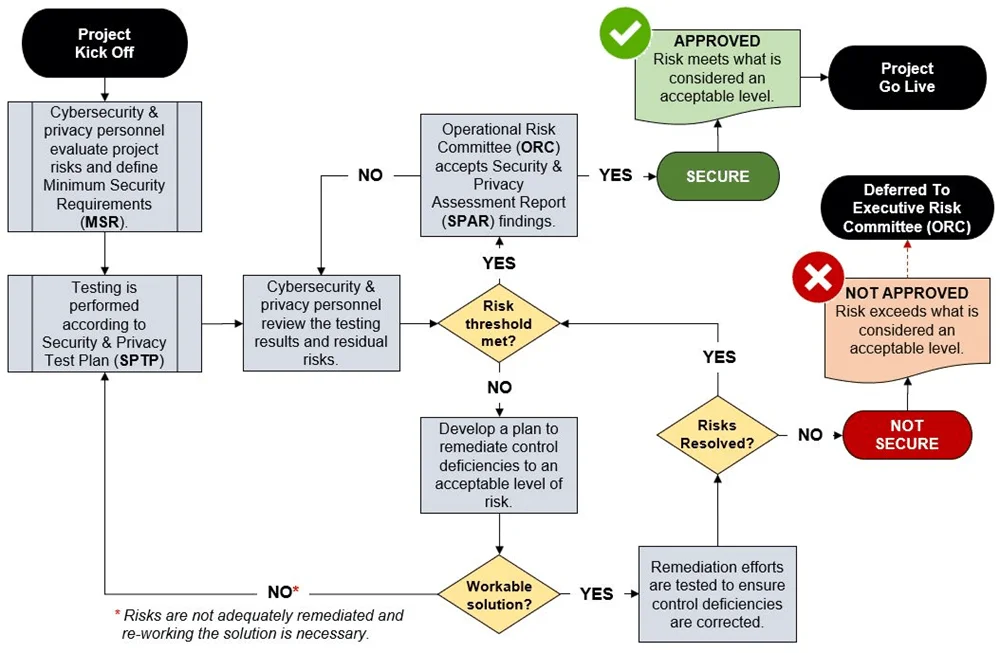
The following are common statutory, regulatory and contractual requirements that expect “pre-production testing” or "information assurance" activities to be performed:
- **ISO 27002** – 14.2.8
- European Union General Data Protection Regulation ( **EU GDPR**) – Article 25
- **NIST 800-171** – 3.12.1, 3.12.3 & Non-Federal Organization (NFO)
- **NIST Cybersecurity Framework** – PR.IP-2, PR.IP-5 & DE.DP-3
- Federal Risk and Authorization Management Program ( **FedRAMP**) – Security Assessment & Authorization (CA) controls
- AICPA Trust Services Principles (TSP) **SOC2** – CC7.4
- Center for Internet Security Critical Security Controls ( **CIS CSC**) – 18.2, 18.4 & 18.8
- Cloud Security Alliance Cloud Controls Matrix ( **CSA CCM**) – CCC-03
- Cloud Computing Compliance Controls Catalogue ( **C5**) – BEI-02
- Monitory Authority of Singapore Technology Risk Management ( **MAS TRM**) Guidelines - 6.0.1, 6.2.2, 6.2.3, 6.2.4, 6.3.4, 6.4.2, 6.4.3, 6.4.4, A.1.1 & A.1.2
- European Union Agency for Network and Information Security ( **ENISA**) Technical Guideline of Security Measures – SO23
- National Industry Security Program Operating Manual ( **NISPOM**) – 8-610 & 8-302
- Criminal Justice Information Services ( **CJIS**) Security Policy – 5.10.4.1, 5.11.1.1, 5.11.1.2, 5.11.2 & 5.13.4.1
- Massachusetts **MA 201 CMR 17.00** – 17.03(2)(d)(B)(i) & 17.03(2)(h)
- New York Department of Financial Services ( **23 NYCRR 500**) – 500.02
- Oregon Consumer Identity Theft Protection Act ( **OCITPA**) – 622(2)(B)(i)-(iv)
- Underwriters Laboratories ( **UL**) 2900-1 – Section 12
- Payment Card Industry Data Security Standard ( **PCI DSS**) – Requirement 6
- Motion Picture Association of America ( **MPAA**) Content Security Program – MS-2.0
## Product Example - IAP
The IAP is based on leading security engineering practices, including NIST 800-160 and NIST 800-37. You get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs. Please review the examples below to see for yourself:
**View Product Examples**
| | | |
| --- | --- | --- |
| [](https://complianceforge.com/content/pdf/example-iap-information-assurance-program.pdf "example control validation testing program") | | [](https://complianceforge.com/content/pdf/example-iap-control-validation-testing-mapping.pdf "example control validation testing NIST 800-37 mapping") |
## Cost Savings Estimate - Information Assurance Program (IAP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 270 internal staff work hours, which equates to a cost of approximately **$24,000** in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work. This assumes you have staff that has performed IA/ST&E work who can even develop this documentation.
- If you hire a consultant to generate this documentation, it would take them an estimated 150 contractor work hours, which equates to a cost of approximately **$48,750**. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- It is approximately 9% of the cost for a consultant or 18% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
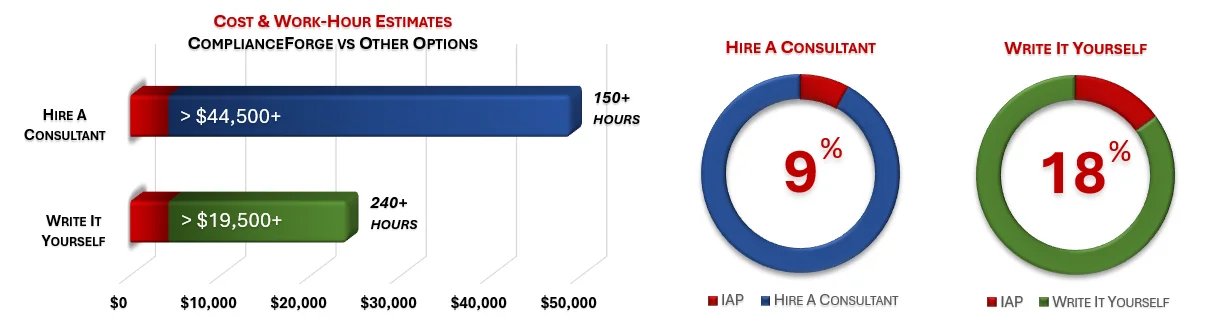
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## What Does the IAP Come With?
The IAP comes with everything you need to stand up a process to do pre-production security & privacy testing:
- Core Word document that is the program-level guidance on the Information Assurance Program (IAP) at your organization;
- Editable Excel spreadsheets that contain mappings to leading practices and other helpful charts to clarify requirements;
- Security & Privacy Test Plan (SPTP) template to document the plan to perform IAP for a specific project;
- Security & Privacy Plan (SPP) is essentially a traditional System Security Plan (SSP) with privacy added into it;
- Project Risk Register (PRR) template to document risks and remediation actions; and
- Security & Privacy Assessment Report (SPAR) template to write up the overall risk report for the project.
All of these documents come together to enable you to hit the ground running with IAP operations!
## What Controls Does the IAP Rely On?
The IAP is very flexible for the control set that you might want to use for IAP. Assuming you do not have something to use "out of the box" we have that covered with the ability to use the [Secure Controls Framework (SCF)](https://www.securecontrolsframework.com/ "Secure Controls Framework security testing evaluation"). If you are not familiar with the SCF, it is a robust set of cybersecurity and privacy controls that maps to over 100 statutory, regulatory and contractual frameworks, so it is a great, free tool for businesses to use! The IAP comes with instructions on paring down the SCF to define just the right "level of effort" for the control set, based on the pertinent compliance needs and risk appetite of your organization.
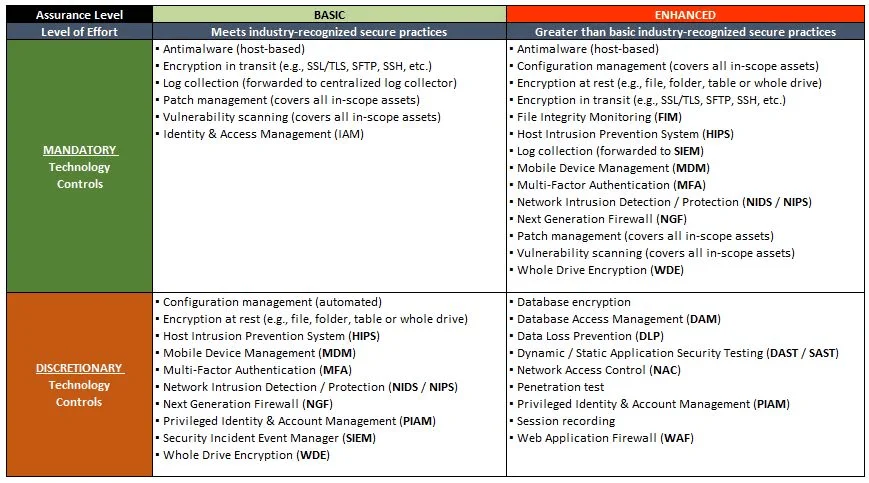
If you have any questions on the IAP, please [contact us](https://complianceforge.com/contact-us/) since we are happy to do a demo or answer your questions in greater detail.
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## DSP Bundle 3
[Skip to main content](https://complianceforge.com/bundle/dsp-bundle-3#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/201/1528/secure-controls-framework-scf-dsp-bundle-3-robust-digital-security-documentation__06964.1740599328.jpg?c=2)
[1 review](https://complianceforge.com/bundle/dsp-bundle-3#product-reviews)
$49,840.00
$27,412.00
(You save
$22,428.00
)
# DSP Bundle 3: Robust Digital Security Documentation
SKU:DSP-B3-NOUPC:692878857178Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=DSP%20Bundle%203%3A%20Robust%20Digital%20Security%20Documentation&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-3 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-3&title=DSP%20Bundle%203%3A%20Robust%20Digital%20Security%20Documentation&summary=DSP%20Bundle%203%3A%20Robust%20Digital%20Security%20Documentation&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-3 "Linkedin")

## Digital Security Plan (DSP) Bundle \#3 - ROBUST DIGITAL SECURITY(45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing the Secure Controls Framework (SCF):
01. [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
02. [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
03. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)
04. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
05. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
06. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
07. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
08. [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
09. [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
10. [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
11. [Secure Engineering & Data Privacy (SEDP)](https://complianceforge.com/product/security-by-design-privacy-by-design/)
12. [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
13. [Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")
This bundle builds on the core documentation that comes in [DSP bundle #2](https://complianceforge.com/bundle/dsp-bundle-2 "DSP Bundle #2") and adds much-needed tactical and operational guidance including a Continuity of Operations Plan (COOP), Secure Baseline Configurations (SBC) to harden your systems, Information Assurance Program (IAP) to govern pre-production security testing, Secure Engineering & Data Privacy (SEDP) to help ensure privacy and cybersecurity principles are designed and managed properly, a Cybersecurity Business Plan (CBP) template to help formalize a strategy for the cybersecurity department, and a Data Protection Program (DPP) that helps accelerate the adoption and implementing of a privacy program at your organization.
The DSP and its corresponding [Cybersecurity Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity Operating Procedures (CSOP)"), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices by providing GRC policies and GRC procedures. Not only do you get the policies, standards, controls, procedures and metrics that form the basis of security and privacy operations, but you get program-level guidance that addresses common areas of compliance and business risk. The end result with this DSP bundle is a comprehensive, customizable, easily-implemented set of documentation that your company needs to establish a scalable, "best in class" cybersecurity and privacy program. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")

## Cost Savings Estimate - DSP Bundle \#3
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 4,100 internal staff work hours, which equates to a cost of approximately **$404,000** staff-related expenses. This is about 36-48 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 3,100 contractor work hours, which equates to a cost of approximately **$969,750**. This is about 24-36 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 7% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.

## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.

## Products Included in DSP Bundle \#3
| | |
| --- | --- |
|  | [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the [**Secure Controls Framework (SCF)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework Policy"), so you can easily align your **policies**, **standards** and **metrics** with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates [NIST CSF policies standards](https://complianceforge.com/product/nist-csf-based-security-documentation-wisp/ "NIST CSF policies standards") |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template")
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
|  | **NIST SP 800-161 Rev 1-Based [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)**
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
|  | [**Secure Engineering & Data Privacy (SEDP)**](https://complianceforge.com/product/security-by-design-privacy-by-design/ "Security & Privacy by Design")
The SPBD addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SPBD provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SPBD is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering. |
|  | [**Continuity of Operations Program (COOP)**](https://complianceforge.com/product/continuity-of-operations-plan/ "Continuity of Operations Program COOP")
The COOP addresses the “how?” questions for how your company plans to respond to disasters to maintain business continuity.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP's policies and standards for disaster recovery and business continuity operations.
- The concept of “continuity operations” spans incident response to disaster recovery to business continuity operations. This is a very common requirement in numerous statutory, regulatory and contractual requirements. The COOP provides your organization with the documentation to prove it addresses both disaster recovery and business continuity.
- The COOP is based on numerous frameworks to provide a holistic approach to DR and BC operations. |
|  | [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configuration template")
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization. |
|  | [**Information Assurance Program (IAP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E). |
|  | [**Cybersecurity Business Plan (CBP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing") **[Information Assurance Program - Control Validation Testing](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")** The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization. |
|  | **[Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")** The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=ducaq1xoxx32)
#### 1 Review [Hide Reviews\ \ Show Reviews](https://complianceforge.com/bundle/dsp-bundle-3\#productReviews-content)
- We've been a ComplianceForge customer for a number of years, and have worked our way through a number of packages - now utilizing the DSP Bundle 3. I've always found the ComplianceForge team great to deal with, and the documentation is especially useful for an organization that has varied compliance needs; in our case ISO 27001, CMMC, NIST and others. It is easily customizable to our needs, integrates with the SCF, and is well worth the investment. Thanks ComplianceForge team!
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## DSP Bundle 1 Overview
[Skip to main content](https://complianceforge.com/bundle/dsp-bundle-1#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/199/1531/secure-controls-framework-scf-dsp-bundle-1-policies-standards-procedures-and-controls__96040.1740599331.jpg?c=2)
[3 reviews](https://complianceforge.com/bundle/dsp-bundle-1#product-reviews)
$16,800.00
$12,600.00
(You save$4,200.00)
# DSP Bundle 1: Policies, Standards, Procedures & Controls
SKU:DSP-B1-NOUPC:692878857154Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=DSP%20Bundle%201%3A%20Policies%2C%20Standards%2C%20Procedures%20%26%20Controls&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-1 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-1&title=DSP%20Bundle%201%3A%20Policies%2C%20Standards%2C%20Procedures%20%26%20Controls&summary=DSP%20Bundle%201%3A%20Policies%2C%20Standards%2C%20Procedures%20%26%20Controls&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fdsp-bundle-1 "Linkedin")
****
## **Digital Security Plan (DSP) Bundle \#1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)**
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing the Secure Controls Framework (SCF):
1. [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
2. [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
## Product Walkthrough Videos
When you click either of the images or links below, they will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the DSP Bundle #1 is and what it includes to help answer common questions we receive.
| | |
| --- | --- |
| [](https://complianceforge.com/digital-security-program-dsp-product-video/ "Watch Video")
[View Product Video](https://complianceforge.com/digital-security-program-dsp-product-video/) | [](https://complianceforge.com/dsp-scf-procedures-template-product-video/ "Watch Video")
[View Product Video](https://complianceforge.com/dsp-scf-procedures-template-product-video/) |
The DSP and its corresponding [Cybersecurity Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity Operating Procedures (CSOP)"), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices by providing GRC policies and GRC procedures. This bundle is focused on the providing the "meat & potatoes" of a cybersecurity and privacy program - the policies, standards, controls, procedures and metrics that form the basis of security and privacy operations. This bundle goes beyond just having cybersecurity policies and standards. The end result with the DSP is a comprehensive, customizable, easily-implemented set of documentation that your company needs to establish a scalable, "best in class" cybersecurity and privacy program. Being Microsoft Word documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")

## Cost Savings Estimate - DSP Bundle \#1
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 1,900 internal staff work hours, which equates to a cost of approximately **$190,000** in staff-related expenses. This is about 12-24 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 1,600 contractor work hours, which equates to a cost of approximately **$520,000**. This is about 9-18 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 2% of the cost for a consultant or 7% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
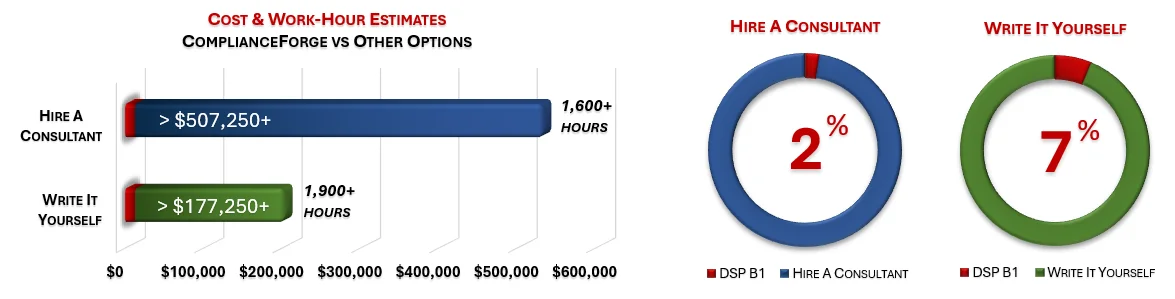
## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.

## Products Included in DSP Bundle \#1
| | |
| --- | --- |
|  | [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the [**Secure Controls Framework (SCF)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework Policy"), so you can easily align your **policies**, **standards** and **metrics** with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template")
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
#### 3 Reviews [Hide Reviews\ \ Show Reviews](https://complianceforge.com/bundle/dsp-bundle-1\#productReviews-content)
- The documents I received puts my company in a fantastic position to be prepared for any audit and future certifications. Thank you for professional work. Well worth the investment.
- Compliance Forge has been an absolute game-changer for our security and compliance program. Their documentation is exceptionally well-structured, easy to customize, and maps seamlessly to major frameworks like NIST, ISO, and PCI-DSS. What truly sets them apart is the depth of thought and practicality built into every product. Compliance Forge helped us build a strong, scalable foundation. Highly recommended for any organization serious about cybersecurity and compliance!
- The DSP and associated documentation has become an invaluable tool in helping us re-align our policies with industry standard frameworks. The 'icing on the cake' is being able to link control objectives with a maturity model from which we can generate actionable metrics on gaps for executive leadership. I have also found the folks at ComplianceForge to be very responsive and helpful with questions and follow up.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[dsp bundle 3: robust digital security documentation](https://complianceforge.com/bundle/dsp-bundle-3) [privacy bundle 2: dsp version (scf alignment)](https://complianceforge.com/bundle/privacy-bundle-2) [c](https://complianceforge.com/bundle/c-scrm-bundle-2/) [cmmc bundle 4: levels 1](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3) [policies & procedures bundle](https://complianceforge.com/bundle/policies-procedures-bundle-iso-27001-27002/) [product comprehensive digital security program](https://complianceforge.com/product/comprehensive-digital-security-program/) [compliance templates](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf) [risk bundle 2: risk, vulnerability & ir management](https://complianceforge.com/bundle/risk-bundle-2)
## Integrated Controls Management
[Skip to main content](https://complianceforge.com/scf/integrated-controls-management/#main-content)
# Integrated Controls Management (ICM) Model
The **Integrated Controls Management (ICM)** is a joint project between ComplianceForge and the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)") and the premise is that controls are central to cybersecurity and privacy operations, as well as the overall business rhythm of an organization. This is supported by the [Cybersecurity & Data Privacy Risk Management Model (C\|P-RMM)](https://securecontrolsframework.com/risk-management-model/ "Cybersecurity & Data Privacy Risk Management Model (C|P-RMM)"), that describes the central nature of controls, where not just policies and standards map to controls, but procedures, metrics, threats and risks, as well.
ICM takes a different approach from the traditional definition of Governance, Risk Management and Compliance (GRC) and/or Integrated Risk Management (IRM), since ICM is controls-centric, where controls are viewed as the nexus, or central pivoting point, for an organization’s cybersecurity and privacy operations.
[](https://complianceforge.com/content/pdf/complianceforge-integrated-controls-management.pdf "integrated controls management overview")
[**OCEG**](https://www.oceg.org/about/what-is-grc/ "OCEG - GRC Definition") defines GRC as, “ _GRC is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity_,” while [**Gartner**](https://www.gartner.com/en/information-technology/glossary/integrated-risk-management-irm "Gartner - GRC & IRM definition") jointly defines GRC/IRM as, " _a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks_."
**ComplianceForge** and [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework"), the developers of the ICM model, define ICM as, “ _a holistic, technology-agnostic approach to cybersecurity and data protection controls to identify, implement and manage secure and compliant practices, covering an organization’s people, processes, technology and data, regardless of how or where data is stored, processed and/or transmitted._”
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity and privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of **Supply Chain Risk Management (SCRM)**.

## Defining What It Means To Be “Secure & Compliant”
Unlike GRC/IRM, ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, ICM helps an organization categorize its applicable controls according to “must have” vs “nice to have” requirements:
- **Minimum Compliance Requirements (MCR)** are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- **Discretionary Security Requirements (DSR)** are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.

Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
## ICM Principles
There are eight (8) principles associated with ICM:
1. Establish Context;
2. Define Applicable Controls;
3. Assign Maturity-Based Criteria;
4. Publish Policies, Standards & Procedures;
5. Assign Stakeholder Accountability;
6. Maintain Situational Awareness;
7. Manage Risk; and
8. Evolve Processes.
ComplianceForge has simplified the concept of "how to GRC" in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
**Integrated Controls Management (ICM) – Overlaid On Integrated Cybersecurity Governance Model (ICGM)**
[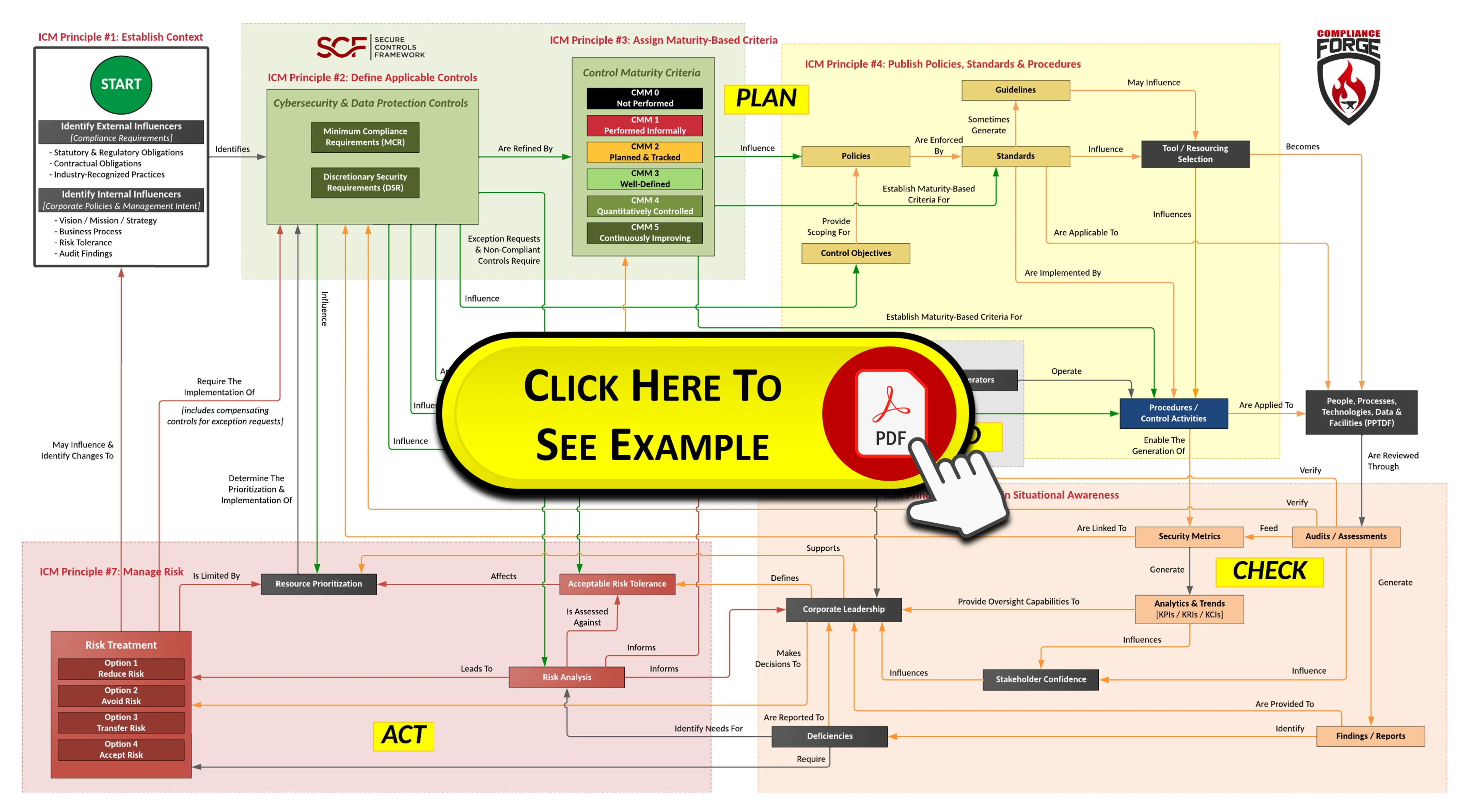](https://complianceforge.com/content/pdf/complianceforge-icm-plan-do-check-act.pdf "Integrated Controls Management how to grc")
### Principle 1: Establish Context
To build and maintain efficient and effective operations, a cybersecurity & privacy program must have a hierarchical vision, mission and strategy that directly supports the organization’s broader strategic objectives and business processes. This process of establishing context involves identifying all applicable external compliance requirements (e.g., laws, regulations and contractual obligations), as well as internal directives (e.g., Board of Directors, corporate policies, etc.). This is a due diligence element of the cybersecurity and privacy program.
### Principle 2: Define Applicable Controls
A tailored control set cybersecurity and data protection controls must exist. This control set needs to be made of Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR). This blend of “must have” and “nice to have” requirements establish an organization’s tailored control set to ensure both secure practices and compliance.
### Principle 3: Assign Maturity-Based Criteria
The cybersecurity & privacy program must assign maturity targets to define organization-specific “what right looks like” for controls. This establishes attainable criteria for people, processes and technology requirements. Tailored maturity level criteria can be used to plan for, budget for and assess against. Maturity targets should support the organization’s need for operational resiliency.
### Principle 4: Publish Policies, Standards & Procedures
Documentation must exist, otherwise an organization’s cybersecurity and data protection practices are unenforceable. Formalizing organization-specific requirements via policies and standards are necessary to operationalize controls. Stakeholders utilize those prescriptive requirements to develop Standardized Operating Procedures (SOP) that enable Individual Contributors (IC) to execute those controls. Policies, standards and procedures provides evidence of due diligence that the organization identified and implemented reasonable steps to address its applicable requirements.
### Principle 5: Assign Stakeholder Accountability
Controls must be assigned to stakeholders to ensure accountability (e.g., business units, teams and/or individuals). These “control owners” may assign the task of executing controls to “control operators” at the IC-level. The documented execution of procedures provides evidence of due care that reasonable practices are being performed.
### Principle 6: Maintain Situational Awareness
Situational awareness must involve more than merely “monitoring controls” (e.g., metrics). While metrics are a point-in-time snapshot into discrete controls’ performance, the broader view of metrics leads to a longer-term trend analysis. When properly tied in with current risk, threat and vulnerability information, this insight provides “situational awareness” that is necessary for organizational leadership to adjust plans to operate within the organization’s risk threshold.
### Principle 7: Manage Risk
Proactive risk management processes must exist across all phases of development/information/system life cycles to address confidentiality, integrity, availability and safety aspects. Risk management must address internal and external factors, including privacy and Supply Chain Risk Management (SCRM) considerations. To manage risk, it requires the organization to clearly define its risk threshold and risk management expectations.
### Principle 8: Evolve Processes
Cybersecurity and data protection measures must adapt and evolve to address business operations and the evolving threat landscape. This requires the adoption of a Plan, Do, Check & Act (PDCA) approach (Deming Cycle) to ensure the organization proactively identifies its requirements, implements appropriate protections, maintains situational awareness to detect incidents, operates a viable capability to respond to incidents and can sustain key business operations, if an incident occurs.
## Plan-Do-Check-Act (PDCA) Approach To GRC
The ICM takes a comprehensive view towards governing a cybersecurity and privacy program. Without an overarching concept of operations for the broader GRC/IRM function, organizations will often find that their governance, risk, compliance and privacy teams are siloed in how they think and operate. These siloed functions and unclear roles often stem from a lack of a strategic understanding of how these specific functions come together to build a symbiotic working relationship between the individual teams that enables quality control over people, processes and technology. The ICM utilizes a **[Plan, Do, Check & Act (PDCA)](https://complianceforge.com/content/pdf/complianceforge-icm-plan-do-check-act.pdf "Plan, Do, Check & Act (PDCA) - PDF")** approach that is a logical way to design a governance structure:
- **Plan**. The overall GRC process beings with planning. This planning will define the policies, standards and controls for the organization. It will also directly influence the tools and services that an organization purchases, since technology purchases should address needs that are defined by policies and standards.
- **Do**. Arguably, this is the most important section for cybersecurity and privacy practitioners. Controls are the “security glue” that make processes, applications, systems and services secure. Procedures (also referred to as control activities) are the processes how the controls are actually implemented and performed. The [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework") can be an excellent starting point for a control set if your organization lacks a comprehensive set of cybersecurity and privacy controls.
- **Check**. In simple terms, this is situational awareness. Situational awareness is only achieved through reporting through metrics and reviewing the results of audits/assessments.
- **Act**. This is essentially risk management, which is an encompassing area that deals with addressing two main concepts (1) real deficiencies that currently exist and (2) possible threats to the organization.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/scf-dsp-procedures-csop/)
#### [Procedures Template - DSP / SCF](https://complianceforge.com/product/scf-dsp-procedures-csop/)
Secure Controls Framework (SCF)
Cybersecurity Standardized Operating Procedures (CSOP) DSP \| SCF Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$6,400.00 - $11,200.00
[Choose Options](https://complianceforge.com/product/scf-dsp-procedures-csop/)
- [](https://complianceforge.com/bundle/c-scrm-bundle-2/)
#### [C-SCRM Bundle 2: DSP version (SCF alignment)](https://complianceforge.com/bundle/c-scrm-bundle-2/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #2 - DSP Version (45% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-2/)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
#### [CMMC Bundle 4: Levels 1-3 (DSP & SCF)](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
Secure Controls Framework (SCF)
NIST 800-171 & CMMC 2.0 Compliance Bundle #4 - EXPERT CMMC 2.0 Levels 1-3 (45% discount)
Is your organization looking to achieve CMMC compliance? This is a bundle that includes the following thirteen (13) ComplianceForge...
$47,490.00
$26,120.00 - $30,920.00
[Choose Options](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3)
- [](https://complianceforge.com/bundle/privacy-bundle-2)
#### [Privacy Bundle 2: DSP version (SCF alignment)](https://complianceforge.com/bundle/privacy-bundle-2)
ComplianceForge
Privacy Bundle #2 - DSP Version (45% discount)
This is a bundle that includes the following twelve (12) ComplianceForge products that are focused on operationalizing the cybersecurity and privacy principles:
Digital Security Program (DSP)
Cybersecurity...
$45,605.00
$25,083.00 - $26,433.00
[Choose Options](https://complianceforge.com/bundle/privacy-bundle-2)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Risk Management Bundle
[Skip to main content](https://complianceforge.com/bundle/risk-bundle-2#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/211/1545/complianceforge-risk-bundle-2-risk-vulnerability-and-ir-management__57975.1740599343.jpg?c=2)
No reviews yet
$8,450.00
$6,338.00
(You save
$2,112.00
)
# Risk Bundle 2: Risk, Vulnerability & IR Management
SKU:RISK-B2-NOUPC:692878857086Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Risk%20Bundle%202%3A%20Risk%2C%20Vulnerability%20%26%20IR%20Management&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-2 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-2&title=Risk%20Bundle%202%3A%20Risk%2C%20Vulnerability%20%26%20IR%20Management&summary=Risk%20Bundle%202%3A%20Risk%2C%20Vulnerability%20%26%20IR%20Management&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-2 "Linkedin")

## Cybersecurity Risk Bundle \#2(25% discount)
This is a bundle that includes the following four (4) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
1. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
2. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
3. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
4. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
## **Why Are These Products Part of The Bundle?**
This bundle is designed for organizations that need a cost-effective and timely solution to obtain risk management documentation and a professional risk assessment template. However, it also adds on vulnerability management and incident response documentation to provide a robust risk management solution for companies that already have policies and standards, but need to enhance how risk is actually managed. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate - Risk Bundle \#2
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 700 internal staff work hours, which equates to a cost of approximately **$70,000** in staff-related expenses. This is about 6-12 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 430 contractor work hours, which equates to a cost of approximately **$141,375**. This is about 4-8 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 4% of the cost for a consultant or 9% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
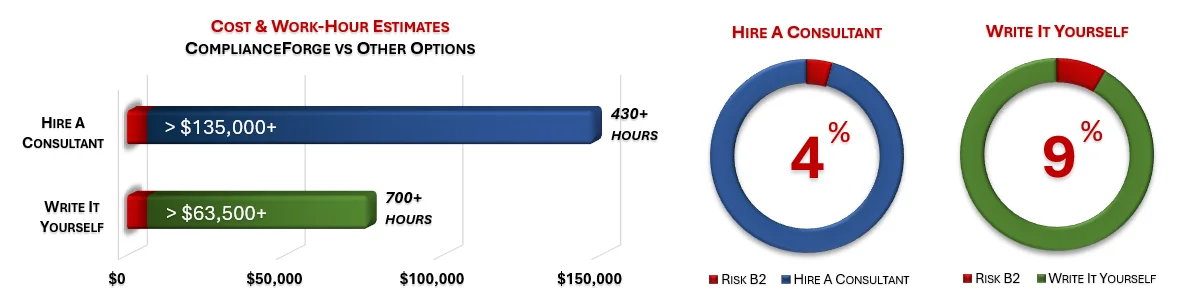
## Products Included in Risk Bundle \#2
| | |
| --- | --- |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Privacy Compliance Bundle
[Skip to main content](https://complianceforge.com/bundle/privacy-bundle-1#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/209/1515/complianceforge-privacy-bundle-1-cdpp-version-iso-or-nist-alignment__88011.1740599315.jpg?c=2)
No reviews yet
$35,485.00
$35,485.00
$23,065.00
(You save
$12,420.00
)
# Privacy Bundle 1: CDPP version (ISO or NIST alignment)
SKU:PRIVACY-B1UPC:692878857185Availability:Email Delivery Within 1-2 Business Days
Framework Version:
(Required)
NIST CSFISO 27001/27002NIST SP 800-53 R5
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Privacy%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-1 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-1&title=Privacy%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&summary=Privacy%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-1 "Linkedin")

## Privacy Bundle \#1 - CDPP Version(35% discount)
This is a bundle that includes the following twelve (12) ComplianceForge products that are focused on operationalizing the cybersecurity and privacy principles:
01. Cybersecurity & Data Protection Program (CDPP) - [NIST CSF](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/ "NIST CSF Policies"), [ISO 27001/2](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/ "ISO 27001 / 2 Policies") or [NIST 800-53 R5 Moderate](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-53 R5 Moderate Policies")
02. Cybersecurity Standardized Operating Procedures (CSOP) - [NIST CSF](https://complianceforge.com/product/nist-csf-procedures-csop/ "NIST CSF Procedures"), [ISO 27001/2](https://complianceforge.com/product/iso-27002-procedures-csop/ "ISO 27001 / 2 Procedures") or [NIST 800-53 R5 Moderate](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/ "NIST 800-53 R5 Moderate Procedures")
03. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
04. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
05. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
06. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
07. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
08. [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
09. [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
10. [Secure Engineering & Data Privacy (SEPD)](https://complianceforge.com/product/security-by-design-privacy-by-design/)
11. [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
12. [Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")
## Focused on EU GDPR & CCPA/CPRA Compliance
This bundle is designed for organizations that need to comply with the European Union General Data Protection Regulation (EU GDPR) and laws like California’s CCPA/CPRA. This is beyond just cybersecurity policies and standards. This is addresses the unique compliance needs for privacy and cybersecurity to manage risk in a coordinated effort. The end result is a comprehensive, customizable, easily implemented set of documentation that your company needs to establish a cybersecurity and privacy program. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate - Privacy Bundle \#1 (Cybersecurity & Data Protection Program (CDPP) version)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 3,100 internal staff work hours, which equates to a cost of approximately **$306,000** in staff-related expenses. This is about 30-48 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 2,000 contractor work hours, which equates to a cost of approximately **$670,750**. This is about 15-24 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 8% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
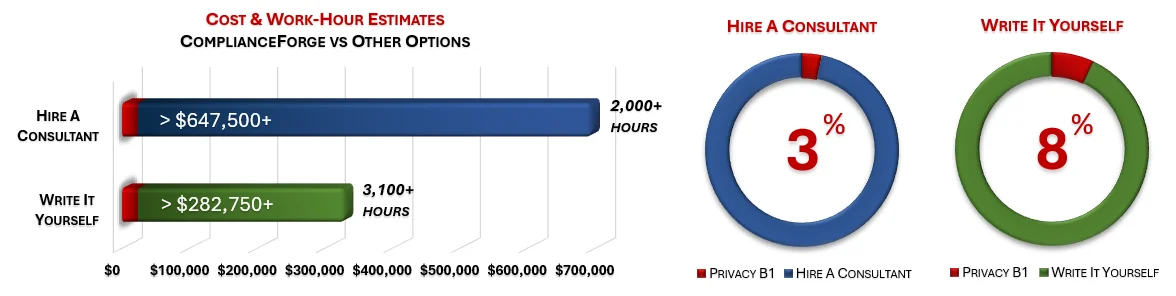
## Products Included in Privacy Bundle \#2
| | |
| --- | --- |
|  | **[Cybersecurity & Data Protection Program (CDPP)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/ "NIST 800-53 CDPP") Selection Between NIST 800-53 / NIST CSF / ISO 27002**
- The CDPP addresses the “why?” and “what?” questions in an audit, since policies and standards form the foundation for your cybersecurity program.
- Under each of the policies are standards that support those policy statements.
- CDPP contains many useful supplemental documentation templates:
- Business Impact Analysis ( **BIA**) template
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- Risk management guidelines
- System hardening guidelines
- and more templates |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - WISP version**](https://complianceforge.com/product/iso-27002-procedures-csop/ "Cybersecurity procedures template NIST 800-53 NIST CSF ISO 27002")
The WISP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
|  | **NIST SP 800-161 Rev 1-Based [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)**
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
|  | [**Secure Engineering & Data Privacy (SEDP)**](https://complianceforge.com/product/security-by-design-privacy-by-design/ "Security & Privacy by Design")
The SEDP addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SEDP provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SEDP is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering. |
|  | [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configuration template")
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization. |
|  | [**Information Assurance Program (IAP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E). |
|  | **[**Cybersecurity Business Plan (CBP)**](https://complianceforge.com/product/cybersecurity-business-plan/ "Cybersecurity Business Plan (CBP)")** The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization. |
|  | **[Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")** The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. |
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=nkakk0bm6oq)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Privacy Bundle 2
[Skip to main content](https://complianceforge.com/bundle/privacy-bundle-2#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/210/1543/complianceforge-privacy-bundle-2-dsp-version-scf-alignment__70924.1740599341.jpg?c=2)
No reviews yet
$45,605.00
$25,083.00
(You save
$20,522.00
)
# Privacy Bundle 2: DSP version (SCF alignment)
SKU:PRIVACY-B2-NOUPC:692878857192Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Privacy%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-2 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-2&title=Privacy%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&summary=Privacy%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fprivacy-bundle-2 "Linkedin")

## Privacy Bundle \#2 - DSP Version(45% discount)
This is a bundle that includes the following twelve (12) ComplianceForge products that are focused on operationalizing the cybersecurity and privacy principles:
01. [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
02. [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
03. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
04. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
05. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
06. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
07. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
08. [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
09. [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
10. [Secure Engineering & Data Privacy (SEDP)](https://complianceforge.com/product/security-by-design-privacy-by-design/)
11. [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
12. [Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")
## Focused on EU GDPR & CCPA/CPRA Compliance
This bundle is designed for organizations that need to comply with the European Union General Data Protection Regulation (EU GDPR) and laws like California’s CCPA/CPRA. This is beyond just cybersecurity policies and standards. This is addresses the unique compliance needs for privacy and cybersecurity to manage risk in a coordinated effort. The end result is a comprehensive, customizable, easily implemented set of documentation that your company needs to establish a cybersecurity and privacy program. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate - Privacy Bundle \#2 (Digital Security Program (DSP) version)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 3,900 internal staff work hours, which equates to a cost of approximately **$386,000** in staff-related expenses. This is about 36-48 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 2,800 contractor work hours, which equates to a cost of approximately **$930,750**. This is about 24-36 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 6% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
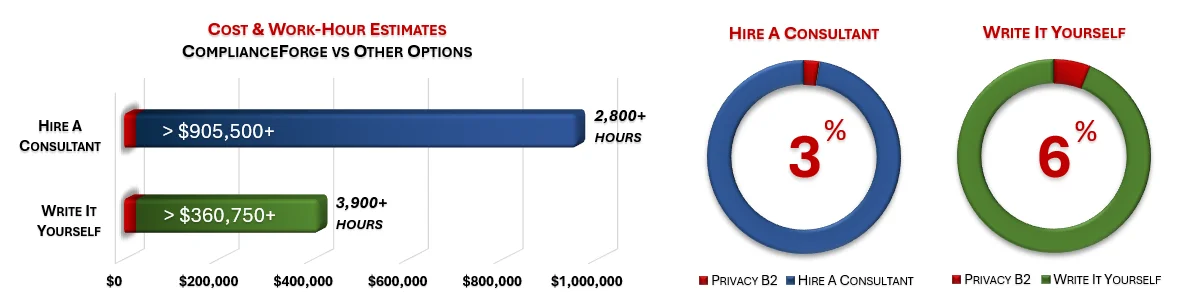
## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.

## Products Included in Privacy Bundle \#2
| | |
| --- | --- |
|  | [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the [**Secure Controls Framework (SCF)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework Policy"), so you can easily align your **policies**, **standards** and **metrics** with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template")
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
|  | **NIST SP 800-161 Rev 1Based [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)**
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
|  | [**Secure Engineering & Data Privacy (SEDP)**](https://complianceforge.com/product/security-by-design-privacy-by-design/ "Security & Privacy by Design")
The SEDP addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SEDP provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SEDP is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering. |
|  | [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configuration template")
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization. |
|  | [**Information Assurance Program (IAP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E). |
|  | **[**Cybersecurity Business Plan (CBP)**](https://complianceforge.com/product/cybersecurity-business-plan/ "Cybersecurity Business Plan (CBP)")** The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization. |
|  | **[Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")** The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=iy8jrcqm29un)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Business Plan
[Skip to main content](https://complianceforge.com/product/cybersecurity-business-plan/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/174/1520/complianceforge-cybersecurity-business-plan-cbp__21568.1740599320.jpg?c=2)
No reviews yet
$2,175.00
(You save)
# Cybersecurity Business Plan (CBP)
SKU:P18-CBP-NOUPC:692878856980Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Edit%20Your%20Cybersecurity%20Business%20Plan%20(CBP)%20for%20Compliance&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-business-plan%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-business-plan%2F&title=Edit%20Your%20Cybersecurity%20Business%20Plan%20(CBP)%20for%20Compliance&summary=Edit%20Your%20Cybersecurity%20Business%20Plan%20(CBP)%20for%20Compliance&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-business-plan%2F "Linkedin")

[](https://complianceforge.com/product/cybersecurity-business-plan/#cbp-example)
## Cybersecurity Business Plan (CBP) Template
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CBP is to help answer common questions we receive.
[](https://complianceforge.com/cyber-security-business-plan-video/ "Watch Video")
[View Product Video](https://complianceforge.com/cyber-security-business-plan-video/)
## What Is The Cybersecurity Business Plan (CBP)?
The **Cybersecurity Business Plan (CBP)**, which some may refer to as a CISO Business Plan, is a business plan template that is specifically tailored for a cybersecurity department that is designed to support an organization's broader technology and business strategies. The CBP is entirely focused at the CISO-level, since it is a department-level planning document.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The CBP contains a template and guidance to develop organization-specific mission, vision, strategy, objectives, etc. in an editable Microsoft Word format. The following content is what you will have in the CBP with examples that you can easily modify for your specific needs:
- Organizational description
- Vision
- Mission
- Strategy
- SWOT analysis
- Definition of success
- Value proposition
- Department-level "elevator pitch"
- Prioritized objectives
- Concept of Operations (CONOPS)
- Mid-term planning
- Long-term planning
- Marketing plan
- Financial plan
- Capability Maturity Model (CMM) target definitions
The CBP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer.
## **What Problems Does The CBP Solve?**
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. On top of that, writing a cybersecurity-specific business plan is a skill that not many CISOs have experience with, so it is an often outsourced or neglected activity.
- Budget Justification \- Having a coherent plan is a valuable tool for a CISO to defend budgets, since it enables the CISO to paint a long-term picture for the cybersecurity department and why the investment makes good business sense.
- CISO Career Protection \- Having a documented business plan is valuable from a CISO's perspective more than just in defending staffing and budget requests. In cases where a viable business plan is rejected from a funding perspective by senior management, a CISO at least has evidence of appropriate due care on their part. In the event of a breach/incident where the CISO is "on the hook" for the blame, a CISO can demonstrate how the CIO/CEO/CXO that rejected the CISO's recommended practices and funding request(s) that could have prevented the incident now own that risk. It is a way to pass risk up the chain of command.
Our customers choose the **Cybersecurity Business Plan (CBP)** because they:
- Have a need for a timely and cost-effective solution to document their cybersecurity strategy and roadmap.
- Need to be able to edit the document to their specific needs.
- Have documentation that is directly linked to best practices, laws and regulations
- Need an affordable solution
## **How Does the CBP Solve These Problems?**
- Clear Documentation \- The CBP provides comprehensive cybersecurity business planning documentation to prove that your security strategy and roadmap exists. This equates to a time saving of considerable staff time and tens of thousands of dollars in either lost productivity or consultant expenses!
- Time Savings \- The CBP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
Being a Microsoft Word document, you have the ability to add/remove/edit content, as needed. We've provided an "80-90% solution" from the perspective of formatting and content, where you merely polish off the specifics that only you would know about your organization and its culture. While we did the heavy lifting in the research and development of this cybersecurity planning document, we estimate that a mid-sized organization should be able to finalize the CBP in about 5-10 hours. That final customization focuses on "owning" the document where you wordsmith the example statements that we provide so that the content of the document is specific to your organization and relates to specifically what you do.
Ideally, your organization's CISO is the individual who will edit/finalize the CBP. Fortunately, the CBP is written in a format that it can be "ghost written" for the CISO by their subordinates (we understand the time constraints many CISOs experience and planning functions are often delegated). In these instances, the CBP can easily be edited and finalized based on the CISO's existing guidance to subordinates. **It is important to understand that goals are not the same thing as a strategy!** It is often the case where there are a lot of good ideas and "shopping lists" for products/initiatives, but there is a lack of a formalized strategy to accomplish a set of goals. This is where the CBP is a valuable resource, since it creates a formal cybersecurity strategy and roadmap!
## Product Example - CBP - Cybersecurity Business Plan Template
The CBP is a fully-editable Microsoft Word document that you can customize for your specific cybersecurity business planning needs. You can see the table of contents below to see everything the CBP covers. Due to the concise nature of the document, we are limited to what content we can share publicly for examples.
**View Product Example**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-cbp-cybersecurity-business-plan-strategy-roadmap.pdf "example cybersecurity business plan strategy roadmap cmmc") |
## Cost Savings Estimate - Cybersecurity Business Plan (CBP) Template
The CBP is affordable when compared to alternatives. The cost is equivalent to about five (5) hours of a cybersecurity professional's time, which is a fraction of the time it would take to create a similar document on its own. When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save over a hundred hours of staff time and the associated cost of lost productivity. Purchasing the CBP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 120 internal staff work hours, which equates to a cost of approximately **$9,000** in staff-related expenses. This is about 1-2 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 80 consultant work hours, which equates to a cost of approximately **$24,000**. This is about 2-4 weeks of development time for a contractor to provide you with the deliverable.
- The CBP is approximately 9% of the cost for a consultant or 24% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CBP the same day you place your order.
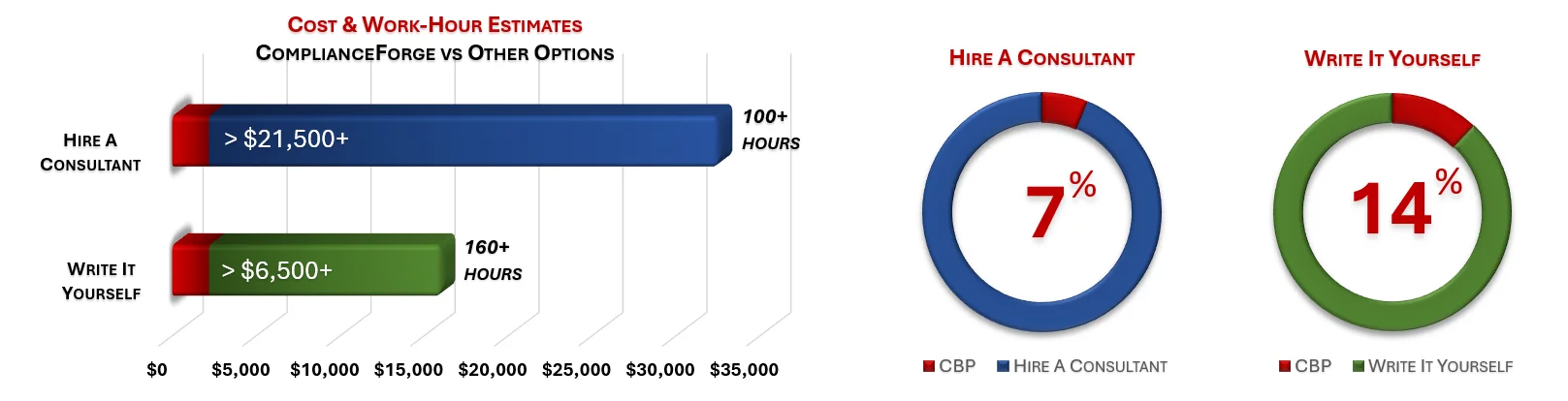
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Template For Creating A Cybersecurity Strategy & Roadmap
ComplianceForge provides businesses with exactly what they need to for cybersecurity planning at a very affordable cost. Similar cybersecurity business planning documentation can be found in Fortune 500 company that have dedicated cybersecurity staff. The architect for the CBP is a former military officer and MBA who has years of experience building cybersecurity business plans and has extensively written on the subject.
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
cyber security business plan, cybersecurity for business, small business cyber security plan, sample small business cyber security plan, cyber security business model, small business cyber security plan example, small business cyber security plan template, cybersecurity in business
## Risk Management Bundle
[Skip to main content](https://complianceforge.com/bundle/risk-bundle-1#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/213/1518/complianceforge-risk-bundle-1-assessing-and-managing-risk__11494.1740599318.jpg?c=2)
No reviews yet
$4,100.00
$3,690.00
(You save$410.00)
# Risk Bundle 1: Assessing & Managing Risk
SKU:RISK-B1-NOUPC:692878857079Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Risk%20Bundle%201%3A%20Assessing%20%26%20Managing%20Risk&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-1 "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-1&title=Risk%20Bundle%201%3A%20Assessing%20%26%20Managing%20Risk&summary=Risk%20Bundle%201%3A%20Assessing%20%26%20Managing%20Risk&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Frisk-bundle-1 "Linkedin")

## Cybersecurity Risk Bundle \#1(10% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing cybersecurity risk management:
1. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
2. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
## Product Walkthrough Videos
When you click either of the images or links below, they will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CDPP Bundle #1c is and what it includes to help answer common questions we receive.
| | |
| --- | --- |
| [](https://complianceforge.com/risk-management-program-rmp-video/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-risk-management-program-rmp/) | [](https://complianceforge.com/what-is-the-cybersecurity-risk-assessment-cra/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-cybersecurity-risk-assessment-cra/) |
## **Why Are These Products Part of The Bundle?**
Is your organization looking for a cybersecurity risk management framework? This bundle is designed for organizations that need a cost-effective and timely solution to obtain risk management documentation and a professional risk assessment template. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate \- Risk Bundle \#1
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 300 internal staff work hours, which equates to a cost of approximately **$30,000** in staff-related expenses. This is about 4-8 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 210 contractor work hours, which equates to a cost of approximately **$68,250**. This is about 3-6 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 5% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
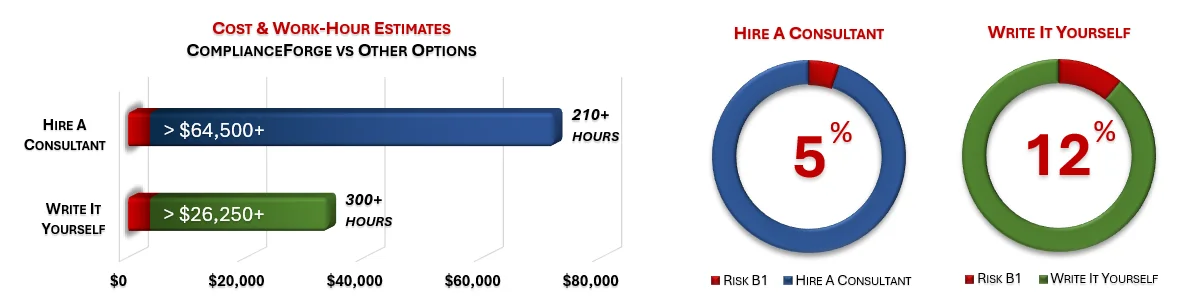
## Products Included in Risk Bundle \#1
| | |
| --- | --- |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the WISP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the WISP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[Cybersecurity Compliance Documentation Bundles](https://complianceforge.com/bundle/dsp-bundle-1) [risk bundle 2: risk, vulnerability & ir management](https://complianceforge.com/bundle/risk-bundle-2) [optimize your risk management program with complianceforge](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/) [compliance templates](https://complianceforge.com/bundle/cdpp-bundle-2-nist-csf) [policies & procedures bundle](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf) [c](https://complianceforge.com/bundle/c-scrm-bundle-2/) [scf risk management model. free guide to risk management](https://complianceforge.com/scf/cybersecurity-data-privacy-risk-management-model/) [Cybersecurity Risk Assessment Template](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
## Efficient CMMC Scoping
[Skip to main content](https://complianceforge.com/blog/efficient-cmmc-scoping/#main-content)
[](https://complianceforge.com/blog/efficient-cmmc-scoping/)
Determining the scope of controls (e.g., assessment boundary) is different than determining control applicability. Do you know the difference?
The Unified Scoping Guide (USG) is a free resource to make control scoping more efficient, regardless of the type of sensitive / regulated data environment. You can download the latest version of the USG for free from: [https://complianceforge.com/free-guides/unified-scoping-guide](https://complianceforge.com/free-guides/unified-scoping-guide)
This helps define the assessment scope boundary of the sensitive/regulated data where it is processed, stored and/or transmitted. This approach is applicable to the following sensitive/regulated data types:
- Controlled Unclassified Information (CUI)
- Federal Contract Information (FCI)
- Personally Identifiable Information (PD)
- Protected Health Information (PHI)
- Cardholder Data (CHD)
- Intellectual Property (IP)
- Attorney-Client Privilege Information (ACPI)
- Student Educational Records (FERPA)
- Export-Controlled Data (ITAR/EAR)
- Critical Infrastructure Information (CII)
- [#cmmc](https://complianceforge.com/blog/tag/cmmc)
- [#control applicability](https://complianceforge.com/blog/tag/control+applicability)
- [#cui](https://complianceforge.com/blog/tag/cui)
- [#doge](https://complianceforge.com/blog/tag/doge)
- [#efficiency](https://complianceforge.com/blog/tag/efficiency)
- [#scoping](https://complianceforge.com/blog/tag/scoping)
- [Email](mailto:?subject=Efficient%20CMMC%20Scoping%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fefficient-cmmc-scoping%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fefficient-cmmc-scoping%2F&title=Efficient%20CMMC%20Scoping%20-%20ComplianceForge&summary=Efficient%20CMMC%20Scoping%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fefficient-cmmc-scoping%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Cybersecurity Compliance Frameworks
[Skip to main content](https://complianceforge.com/reasons-to-buy/compliance/#main-content)
# Cybersecurity Compliance - It Starts With The Framework!
It is important to understand that to "get compliant" with a cybersecurity requirement, it is generally more involved than just addressing a checklist.

With that in mind, selecting a cybersecurity framework is more of a business decision and less of a technical decision. Realistically, the process of selecting a cybersecurity framework must be driven by a fundamental understanding of what your organization needs to comply with from a statutory, regulatory and contractual perspective, since that understanding establishes the minimum set of requirements necessary to (1) not be considered negligent with reasonable expectations for security & privacy; (2) comply with applicable laws, regulations and contracts; and (3) implement the proper controls to secure your systems, applications and processes from reasonable threats. This understanding makes it pretty easy to determine the [appropriate external framework](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf "NIST 800-53 vs ISO 27002 vs NIST CSF") to align with.
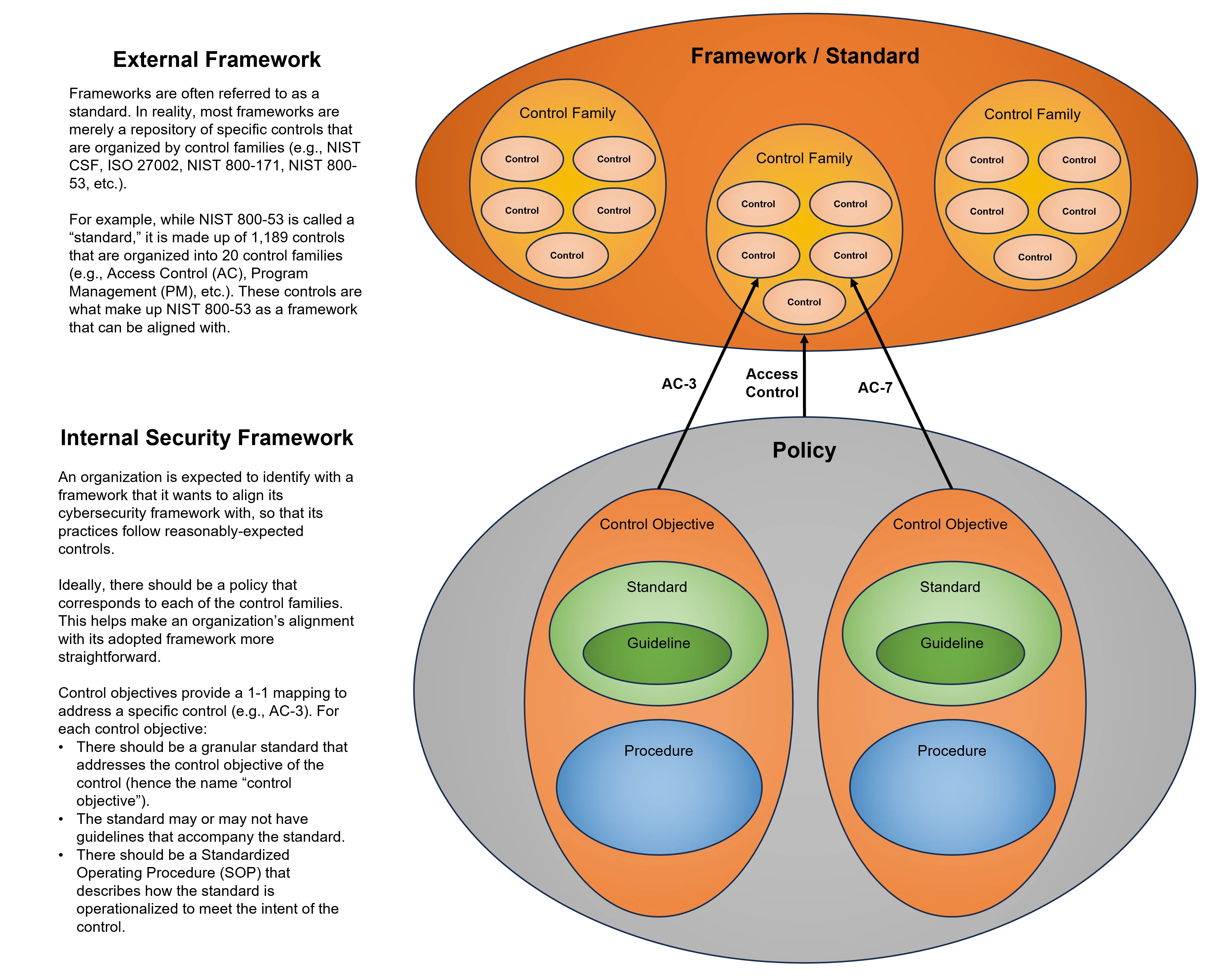
## **Where Do You Fit In The Mandatory Compliance Puzzle?**
A single negligent breach could close your businesses forever, because liability insurance does not cover professional negligence! Below are several examples of how compliance with information security requirements affects common businesses:
| | |
| --- | --- |
|  | ### **HIPAA and PCI DSS Compliance**
**Example #1: Physical Therapist**
Compliance Requirements: HIPAA, PCI DSS & State Breach Laws
**Why?** This physical therapist office deals with electronic Protected Health Information (ePHI) of clients so it falls under HIPAA. The office also accepts co-payments by credit card so it falls under PCI DSS. Since the state requires a breach notification plan, the office must also adhere to state-specific compliance requirements for data breaches. |
| | |
| --- | --- |
|  | ### **PCI DSS and GLBA Compliance**
**Example #2: Certified Public Accountant (CPA)**
Compliance Requirements: GLBA, PCI DSS & State Breach Laws
**Why?** Like most CPAs, this CPA deals with private financial information of clients, so it falls under GLBA. The CPA works for clients that accept credit cards and has access to their QuickBooks accounts (containing cardholder information), so the CPA must meet PCI DSS requirements. Most states waive state-sponsored breach laws if the company is GLBA compliant, so there are no additional requirements by the state. |
| | |
| --- | --- |
|  | ### **GLBA and PCI DSS Compliance in Oregon**
**Example #3: Lawyer**
Compliance Requirements: HIPAA, FACTA, GLBA, PCI DSS & State Breach Laws
**Why?** This law offices deal with Protected Health Information (PHI) for injury claims so its falls under HIPAA as a Business Associate. Since the office also performs real estate closings and is responsible for private financial information, it falls under both FACTA and GLBA. The office accepts payment by credit card so it falls under PCI DSS. This state waives its breach notification law if the law office is GLBA compliant, so there are no additional requirements by the state. |
| | |
| --- | --- |
|  | **PCI DSS Compliance for Level 3 and Level 4 Merchants**
**Example #4: Coffee Shop**
Compliance Requirements: PCI DSS
**Why?** This coffee shop accepts payment by credit and debit cards so it falls under PCI DSS. This specific state does not have any specific laws for breach notification, so the coffee shop only has to focus on PCI DSS compliance. |
| | |
| --- | --- |
|  | ### State Identity Theft Law Compliance
**Example #5: Construction Company**
Compliance Requirements: State Breach Laws
**Why?** The construction company operates in a state that has a law requiring both client and employee Personal Identifying Information (PII) to be protected and for notification in the event of a breach. |
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Vulnerability Management Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/vulnerability-patch-management/#main-content)
# Vulnerability & Patch Management Templates
## Program-level Documentation
Having a proactive patching cadence and vulnerability management program is one of the most common weaknesses that companies face. Spending a small fortune on people and technology does little to reduce your risk if the processes do not exist to maintain those systems, applications and services. The good news is that ComplianceForge developed program-level documentation for businesses to help manage their vulnerability management and patching processes.
## Can You Honestly Answer How Vulnerability Management Is Implemented At Your Organization?
When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as vulnerability management. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW the policies and standards are actually implemented. We did the heavy lifting and created several program-level documents to address this need and the Vulnerability & Patch Management (VPMP) is one of those products.
## Elevate The Way You Approach Vulnerability Management
ComplianceForge currently offers two (2) product2 that is specifically designed to assist companies with vulnerability management:
- [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability & Patch Management Program")
- [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configurations (SBC)")
The Vulnerability & Patch Management Program (VPMP) is program-level documentation that is an essential need for any organization to demonstrate HOW vulnerabilities are actually managed within an organization. Most companies run into issues during audits when the actual practices for vulnerability & patch management are looked at. The VPMP is meant to advance your organization to a mature level of vulnerability management and have the documentation to prove it!
The Secure Baseline Configurations (SBC) is designed to help organizations manage the complex nature of secure baseline configurations for all its technology platforms.
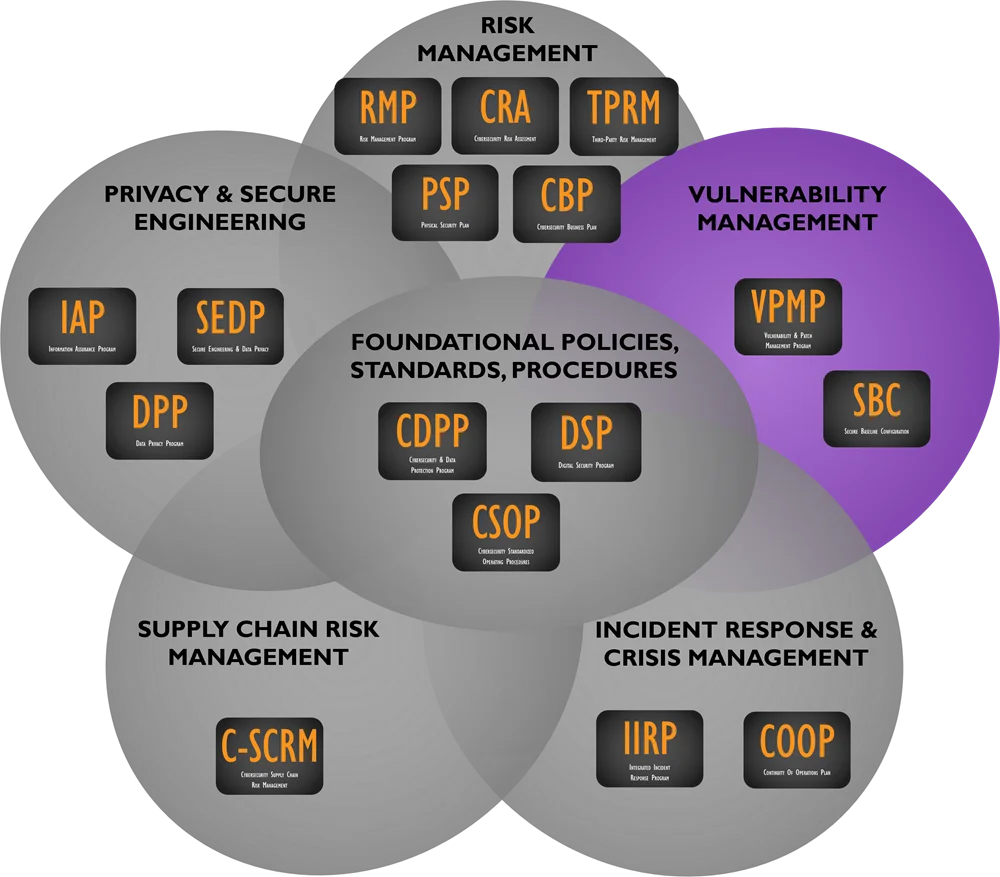
## Browse Our Products
- [](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
#### [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
ComplianceForge
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [](https://complianceforge.com/product/secure-baseline-configuration-sbc)
#### [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
ComplianceForge
Secure Baseline Configurations For Technology Assets
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $3,525.00
[Choose Options](https://complianceforge.com/product/secure-baseline-configuration-sbc)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Incident Response Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/incident-response-program/#main-content)
# Cybersecurity Incident Response Templates
Most companies have requirements to document its incident response processes, but they lack the knowledge and experience to undertake such documentation efforts. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with a compliance requirement. In either situation, it is not a good place to be. The good news is that ComplianceForge developed a viable incident response program that is based on NIST 800-61 guidance, which is the "gold standard" for incident response frameworks. This document is capable of scaling for any sized company.
## Can You Honestly Answer How Incident Response Is Implemented At Your Organization?
When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as incident response. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW the policies and standards are actually implemented. We did the heavy lifting and created several program-level documents to address this need and the Integrated Incident Response Program (IIRP) is one of those products.
## **Professionally-Written, Editable & Easily-Implemented NIST 800-61 Based Incident Response Program**
When you look at **[DFARS](https://complianceforge.com/compliance/nist-800-171 "DFARS incident response 72 hours")** and **[EU GDPR](https://complianceforge.com/international-data-security-laws/eu-gdpr-compliance "eu gdpr 72 hour incident reporting")**, those regulations both have requirements to rapidly respond to and report incidents within 72 hours of discovery. Without a well-designed and efficient incident response program, your organization may very well miss reporting deadlines that can lead to fines, lost contracts and other legal issues.
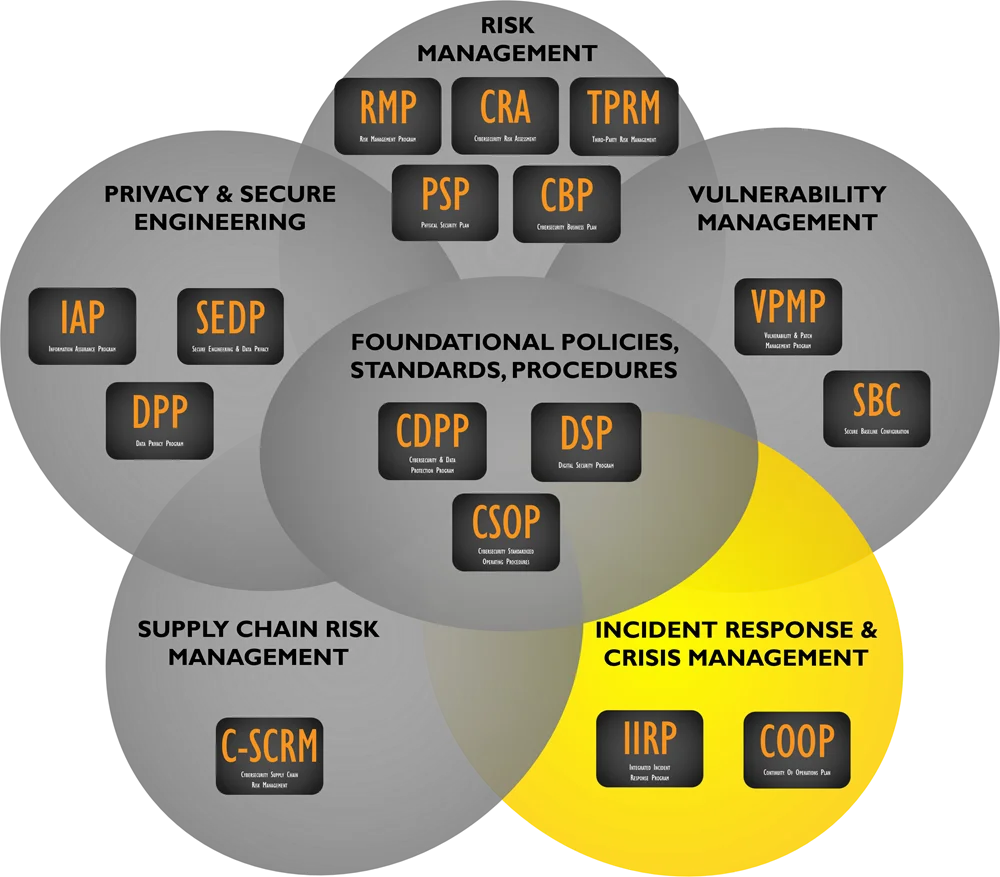
## Browse Our Products
- [](https://complianceforge.com/product/integrated-incident-response-program/)
#### [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/integrated-incident-response-program/)
ComplianceForge
Integrated Incident Response Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/integrated-incident-response-program/)
- [](https://complianceforge.com/product/continuity-of-operations-plan/)
#### [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
ComplianceForge
Continuity of Operations Plan (COOP) - Disaster Recovery & Business Continuity
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$4,235.00 - $9,035.00
[Choose Options](https://complianceforge.com/product/continuity-of-operations-plan/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## NFO Controls Overview
[Skip to main content](https://complianceforge.com/nist-800-171/nfo-controls#main-content)
__
_Editorial: There is a lot of misconception about NFO controls. This page is focused on identifying the underlying requirements associated with NIST SP 800-171 & Cybersecurity Maturity Model Certification (CMMC) compliance. NFOs are a key piece to having appropriate evidence of due diligence and due care to address NIST SP 800-171 and CMMC compliance._
# NIST 800-171 R2 - Non-Federal Organization (NFO) Controls
It might be possible to be "compliant with CMMC 2.0" and be non-compliant with DFARS 252.204-7008/7012 and NIST SP 800-171. By willfully ignoring NFO controls, you can be in a state of non-compliance with both DFARS and NIST SP 800-171, while technically being "CMMC compliant" and that should be a concern for businesses as they work through CMMC compliance efforts:
- DFARS 252.204-7008, _Compliance with Safeguarding Covered Defense Information Controls_, **section (c)(1)** requires contractors to "implement the security requirements specified by NIST SP 800-171"
- DFARS 252.204-7012, _Safeguarding Covered Defense Information and Cyber Incident Reporting_, **section (b)(ii)(A)** requires contractors to have NIST SP 800-171 controls implemented by 1 January 2018.
- NIST SP 800-171, _Protecting CUI in Nonfederal Systems and Organizations_, **Appendix E** identifies that both CUI and NFO controls are required for an organization to "comply" with NIST SP 800-171.
When you really read [**NIST SP 800-171 rev2**](https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final "NIST SP 800-171"), you will see that there are far more than just the 110 controls identified in **Appendix D**. **Appendix E** lists an additional 61 NFO controls that are expected to exist for any organization that stores, transmits or processes CUI. Directly from NIST SP 800-171, NFO controls are "expected to be routinely satisfied by non-federal organizations without specification." If you take a moment to break down the meanings of each of those words you will see:
- **Expected** \- require (someone) to fulfill an obligation
- **Routinely** \- as part of a regular procedure rather than for a special reason
- **Satisfy** \- adequately meet or comply with (a condition, obligation, or demand)
- **Without** \- in the absence of
- **Specification** \- a detailed description of the criteria
Take that one step further to simplify the meaning of NFO control applicability in plain English and **NFO controls are "required to be adequately fulfilled as part of the regular course of business, without the need for additional detailed instructions."** NIST considers NFO controls to be so fundamental to an organization's cybersecurity program that NIST states it does not need to provide additional guidance on the subject. The fundamental concept of NFO controls is that they are considered "business as usual" requirements that any reasonable business should already have in place.
**[NARA's CUI Notice 2020-04](https://www.archives.gov/files/cui/documents/20200616-cui-notice-2020-04-assessing-security-requirements-in-non-fed-info-systems.pdf "NARA ISOO CUI Notice 2020-04")** specifies **[NIST SP 800-171A](https://csrc.nist.gov/publications/detail/sp/800-171a/final "NIST SP 800-171A assessment objectives")** as the authoritative source that assessors use and identifies "specifications" that are the document-based artifacts (e.g., policies, procedures, security plans, security requirements, functional specifications, architectural designs) associated with in-scope systems. The assessment methods include examine, interview and test components. The examine method is the process of reviewing, inspecting, observing, studying, or analyzing assessment objects (e.g., specifications, mechanisms, activities). The purpose of the examine method is to facilitate understanding, achieve clarification, or obtain evidence.
- Within **NIST SP 800-171A** "potential assessment methods and objectives" section, you will consistently find requirements for policies, procedures and other written documentation. The only way to achieve compliance is through appropriate evidence of due diligence and due care, which is accomplished by having appropriate documentation. This can only be achieved with evidence that a reasonable cybersecurity program exists and is maintained, which is the entire point of NFO controls.
- From the **CMMC L2 Assessment Criteria & Methodology**, Assessment Objects (AOs) identify the specific items that will be assessed and include specifications, mechanisms, activities and individuals. "Specifications" are the document-based artifacts (e.g., policies, procedures, security plans, security requirements, functional specifications architectural designs) associated with a system.
The bottom line is without having the documentation evidence that NFO controls fundamentally address:
- You cannot accurately fill out a **Supplier Performance Risk System (SPRS)** self-assessment for the Department of Defense (DoD) without using the AOs from NIST SP 800-171A to evaluate the 110 CUI controls from NIST SP 800-171. The recurring requirement for policies, procedures and other documentation are exactly what the NFO controls from Appendix E of NIST SP 800-171 address.
- You cannot pass a CMMC L1 or L2 assessment (self-attestation or third-party) without the documentation evidence of the due diligence and due care steps taken to address the controls (e.g., policies, standards, procedures, employee training records, etc.). A quote among compliance professionals is that "if it is not documented, then it doesn't exist" and that applies to CMMC for self-assessments or third-party assessments.
## What Is The Actual Requirement For NFO Controls?
The requirement for NFO controls is stipulated in **section 2.1 of NIST SP 800-171**, where it states there are "three fundamental assumptions" to account for:
1. Statutory and regulatory requirements for the protection of CUI are consistent, whether such information resides in federal systems or nonfederal systems including the environments in which those systems operate;
2. Safeguards implemented to protect CUI are consistent in both federal and nonfederal systems and organizations; and
3. The confidentiality impact value for CUI is no less than FIPS 199 moderate.
Where people tend to get confused with this is with the "no less than FIPS 199 moderate" statement:
- When you follow the footnote to the bottom of **page 5 of NIST SP 800-171 rev2**, it states _“the moderate impact value defined in \[ [FIPS 199](https://nvlpubs.nist.gov/nistpubs/fips/nist.fips.199.pdf "NFO FIPS 199")\] may become part of a moderate impact system in \[ [FIPS 200](https://csrc.nist.gov/publications/detail/fips/200/final "NFO FIPS 200")\], which requires the use of the moderate baseline in \[ [SP 800-53](https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final "NFO nist 800-53")\] as the starting point for tailoring actions.”_
- From **page 4 of FIPS 199**, it states _“…the potential impact values assigned to the respective security objectives (confidentiality, integrity, availability) shall be the highest values (i.e., high water mark) from among those security categories that have been determined for each type of information resident...”_
Within the footnotes of **page 6 of NIST SP 800-171 rev2**, NIST highlights the point about what constitutes a “comprehensive security program” for an organization that stores, transmits and/or processes CUI:
- _The security requirements developed from the tailored \[FIPS 200\] security requirements and the \[SP 800-53\] moderate security control baselinerepresent a subset of the safeguarding measures that are necessary for a comprehensive information security program._
- _The strength and quality of such programs in nonfederal organizations depend on the degree to which the organizations implement the security requirements and controls that are expected to be routinely satisfied without specification by the federal government. This includes implementing security policies, procedures, and practices that support an effective risk-based information security program._
- _Nonfederal organizations are encouraged to refer to Appendix E and \[SP 800-53\] for a complete listing of security controls in the moderate baseline deemed out of scope for the security requirements in Chapter Three._

In simple terms, this means the moderate control set of NIST SP 800-53 rev4 is applicable to any organization the stores, transmits and/or processes CUI.

_Note: Unlike CUI and NFO controls, FED and NCO controls are not integral to protecting CUI. The reason for this is CUI and NFO controls are focused on confidentiality requirements, while the FED controls are reserved for US Government usage and NCO controls are focused on integrity and availability. If you can address NCO controls as part of your security program, that is advisable since it focuses on resiliency, but it is not a focus for NIST SP 800-171 or CMMC._
There is a slight "translation error" between NIST SP 800-53 R4 and R5 versions, where there are six NFO controls that are affected. Those six R4 NFOs map to seven R5 controls, where it creates a new NFO requirement for MA-1. However, the other six NFO controls fall under controls that are already associated with a NIST SP 800-171 CUI control. Therefore, 6 of the 7 controls that are NFO controls under R4 become CUI controls under R5:
- CA-3(5) > SC-7(5) \[covered by NIST 800-171 3.13.6\]
- CM-2(1) > CM-2 \[covered by NIST 800-171 3.4.1 & 3.4.2\]
- CM-8(5) > CM-8 \[covered by NIST 800-171 3.4.1 & 3.4.2\]
- MA-4(2) > MA-1 & MA-4 \[partially covered by NIST 800-171 3.7.5\]
- PL-2(3) > PL-2 \[covered by NIST 800-171 3.12.1, 3.12.2, 3.12.3 & 3.12.4\]
- RA-5(1) > RA-5 \[covered by NIST 800-171 3.11.2 & 3.11.3\]
## National Archives and Records Administration (NARA)
**[Executive Order 13556, Controlled Unclassified Information, November 4, 2010](https://obamawhitehouse.archives.gov/the-press-office/2010/11/04/executive-order-13556-controlled-unclassified-information "EO 13556")**, establishes that the National Archives and Records Administration (NARA) is designated as the US government's CUI Executive Agent to develop and issue directives as are necessary to establish uniform policies and practices for a government-wide [**CUI Program**](https://www.archives.gov/cui "NARA CUI program").
Additional insights from **NIST SP 800-171, rev2**:
- page 2:
- NARA plans to sponsor a single FAR clause that will apply the requirements of the federal CUI regulation and NIST Special Publication 800-171 to contractors.
- Nonfederal organizations that collect or maintain information on behalf of a federal agency or that use or operate a system on behalf of an agency, must comply with the requirements in \[FISMA\], including the requirements in \[FIPS 200\] and the security controls in \[SP 800-53\].
- page 3:
- The tailoring criteria described in Chapter Two are not intended to reduce or minimize the federal requirements for the safeguarding of CUI as expressed in the federal CUI regulation.
- Rather, the intent is to express the requirements in a manner that allows for and facilitates the equivalent safeguarding measures within nonfederal systems and organizations and does not diminish the level of protection of CUI required for moderate confidentiality.
## Industry Implications For NFO Controls
What is groundbreaking about the NFO controls within NIST SP 800-171 is that **NIST essentially created a benchmark that define "reasonable" security expectations for private industry**. Interestingly, most people are unaware of that. Particularly, the NFO controls in NIST SP 800-171 sets a precedent for what now constitutes minimum security requirements for non-governmental organizations and the failure to live up to that expectation may be considered negligence on the behalf of an organization.
On the concept of negligence, **DFARS 252.204-7012** calls out as part of the “adequate security” requirements that “the Contractor shall provide adequate security on all covered contractor information systems. To provide adequate security, the Contractor shall implement, at a minimum, the following information security protections… \[NIST SP 800-171\].” That callout is for NIST SP 800-171 and does not mention just CUI controls. For an organization to not meet those requirements (without prior approval from the DoD) would put it in jeopardy of a **False Claims Act (FCA)** violation. However, on **page 6 of NIST 800-171**, NIST does recognize that 100% adoption is not always possible and indicates a Plan of Action & Milestones (POA&M) is a legitimate tool to identify and manage instances of non-compliance through compensating controls: _“Nonfederal organizations may not have the necessary organizational structure or resources to satisfy every security requirement and may implement alternative, but equally effective, security measures to compensate for the inability to satisfy a requirement.”_
As defined on **the first page of Appendix E of NIST SP 800-171**, NFO controls are _"expected to be routinely satisfied by non-federal organizations without specification."_ In this context, the term "without specification" means that NIST approaches these NFO requirements as basic expectations that do not need a detailed description, since they are fundamental components of any organization’s security program. As a case in point, an organization cannot legitimately implement a security program without policies and procedures, which are requirements that the “-1” NFO controls (e.g., AC-1, AT-1, AU-1, etc.) address as “basic expectations” for an organization to have.
Without the NFO controls (e.g., foundational policies & governance), it is not feasible for an organization to have appropriate evidence of due care and due diligence to withstand external scrutiny in an audit. These are assumed requirements, such as when you rent a car at the airport, you do not need to specify a car that is:
- In working condition,
- Has four (4) inflated tires, and
- Is safe to operate.
Furthermore, NIST lists additional assumptions for the basic security program expectations that nonfederal entities:
- Have information technology infrastructures in place, and are not necessarily developing or acquiring systems specifically for processing, storing, or transmitting CUI;
- Have specific safeguarding measures in place to protect their information which may also be sufficient to satisfy the security requirements;
- May not have the necessary organizational structure or resources to satisfy every security requirement and may implement alternative, but equally effective, security measures to compensate for the inability to satisfy a requirement; and
- Can implement a variety of potential security solutions directly or using external service providers (e.g., managed services) to satisfy security requirements.
## Learn More About NFO & CUI Controls
ComplianceForge has several options for editable, professionally-written and affordable [NIST SP 800-171 and Cybersecurity Maturity Model Certification (CMMC) documentation](https://complianceforge.com/cmmc-nist-800-171-templates/). This ranges from policies to standards, procedures, SSP templates, POA&M templates, and much more!
There are 61 total NFO controls in Appendix E of NIST SP 800-171 R2, which maintain their original control numbering from NIST SP 800-53:
- AC-1
- AT-1
- AT-4
- AU-1
- CA-1
- CA-2(1)
- CA-3
- CA-3(5)
- CA-7(1)
- CA-9
- CM-1
- CM-2(1)
- CM-2(7)
- CM-3(2)
- CM-8(5)
- CM-9
- IA-1
- IR-1
- IR-8
- MA-1
- MA-4(2)
- MP-1
- PE-1
- PE-6(1)
- PE-8
- PE-16
- PL-1
- PL-2(3)
- PL-4
- PL-4(1)
- PL-8
- PS-1
- PS-6
- PS-7
- PS-8
- RA-1
- RA-5(1)
- RA-5(2)
- SA-1
- SA-2
- SA-3
- SA-4
- SA-4(1)
- SA-4(2)
- SA-4(9)
- SA-4(10)
- SA-5
- SA-9
- SA-9(2)
- SA-10
- SA-11
- SC-1
- SC-7(3)
- SC-7(4)
- SC-20
- SC-21
- SC-22
- SC-39
- SI-1
- SI-4(5)
- SI-16
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
[nist 800](https://complianceforge.com/cybersecurity-templates/nist-800-171-cmmc-compliance/) [easy nist 800](https://complianceforge.com/compliance/nist-800-171) [begin your compliance journey: nist 800](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-compliance) [editable cmmc & nist 800](https://complianceforge.com/compliance-solutions/cmmc-nist-800-171-templates/)
cmmc controls list, nist 171, nist special publication 800 171a, nist 800 171 controls, nist sp 800 171, sp 800 171
## Incident Response Program
[Skip to main content](https://complianceforge.com/product/integrated-incident-response-program/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/119/1539/complianceforge-integrated-incident-response-program-iirp__43574.1740599338.jpg?c=2)
No reviews yet
$2,175.00
(You save)
# Integrated Incident Response Program (IIRP)
SKU:P08-IIRP-NOUPC:692878856874Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Editable%20Incident%20Response%20Program%20Templates%20for%20Compliance&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fintegrated-incident-response-program%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fintegrated-incident-response-program%2F&title=Editable%20Incident%20Response%20Program%20Templates%20for%20Compliance&summary=Editable%20Incident%20Response%20Program%20Templates%20for%20Compliance&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fintegrated-incident-response-program%2F "Linkedin")

[](https://complianceforge.com/product/integrated-incident-response-program/#IIRP-example)
## Integrated Incident Response Program
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the IIRP is to help answer common questions we receive.
[](https://complianceforge.com/integrated-incident-response-program-iirp-product-video/ "Watch Video")
[View Product Video](https://complianceforge.com/integrated-incident-response-program-iirp-product-video/)
## What Is The Integrated Incident Response Program (IIRP)?
The Integrated Incident Response Program (IIRP) can serve as the cornerstone element in your organization's incident response capability. The reality is that incidents do not care if your responders are or are not prepared and generally with incident response operations if you fail to plan you plan to fail. What matters most is appropriate leadership that is capable of directing response operations in an efficient and effective manner. This is where the IIRP is an invaluable resource for cybersecurity and privacy leaders to have a viable plan to respond to cybersecurity and privacy-related incidents.
The IIRP is an editable Microsoft Word document, but it also comes with Microsoft Excel, PowerPoint and Visio templates that contain the program-level documentation and process flows to establish a mature Integrated Incident Response Program.
- This product addresses the “how?” questions for how your company manages cybersecurity incident response.
- This product helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents, so that your company can train on likely scenarios and tailor plans specific to your needs.
- The IIRP helps address the fundamental expectations when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team (ISIRT) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise (IoC).
- Identifies and defines sources of evidence.
## What Problems Does The IIRP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation (e.g., Integrated Incident Response Program documentation) means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The NIST 800-61-based IIRP is an efficient method to obtain a comprehensive incident response program for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented incident response program. Requirements range from PCI DSS to NIST 800-171 to EU GDPR. The IIRP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected incident response activities.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The IIRP is easy to maintain and customize for your organization, since it is Microsoft Office-based documentation that you can edit for your needs and keep current as things change in your environment.
- Vendor Requirements \- It is very common for clients and partners to request evidence of an incident response program. The IIRP provides this evidence!
Can you honestly answer how incident response is documented at your organization? When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as incident response. While policies and standards are designed to describe why something is required and what needs to be done, many companies fail to create documentation to address how the policies and standards are actually implemented.
We did the heavy lifting and created several program-level documents to address this need and the Integrated Incident Response Program (IIRP) is one of those products. This is specifically designed to provide you with the ability to hit the ground running with incident response. From laying the foundation of how to classify incidents, to responding to events, and providing tabletop exercise material, the IIRP can quickly mature your incident response capabilities.
Most companies have requirements to document its incident response processes, but they lack the knowledge and experience to undertake such documentation efforts. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with a compliance requirement. In either situation, it is not a good place to be. The good news is that ComplianceForge developed a viable incident response program that is based on NIST 800-61 guidance, which is the "gold standard" for incident response frameworks. This document is capable of scaling for any sized company.
## How Does The IIRP Solve These Problems?
- Clear Documentation - The IIRP provides comprehensive documentation to prove that your incident response program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The IIRP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The NIST-based IIRP is written to align your organization with leading practices for incident response.
## Product Example - Integrated Incident Response Program (IIRP)
The IIRP addresses program-level guidance on HOW to actually manage incident response operations, including forensics and reporting. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW incident response is actually managed. The IIRP provides this middle ground between high-level policies and the actual procedures of how Incident Response Plans (IRPs) are executed by those individual contributors task with incident response duties. The IIRP comes with a wealth of guidance, including scenario-based guidance, example IRPs, how to identify both Indicators of Exposure (IoE) and Indicators of Compromise (IoC) and more!
**View Product Examples**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-iirp-integrated-incident-response-program.pdf "example Integrated Incident Response Program") |
## Cost Savings Estimate - Integrated Incident Response Program (IIRP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the VPMP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 240 internal staff work hours, which equates to a cost of approximately **$22,000** in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 125 consultant work hours, which equates to a cost of approximately **$40,625**. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The VPMP is approximately 5% of the cost for a consultant or 10% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the VPMP the same day you place your order.
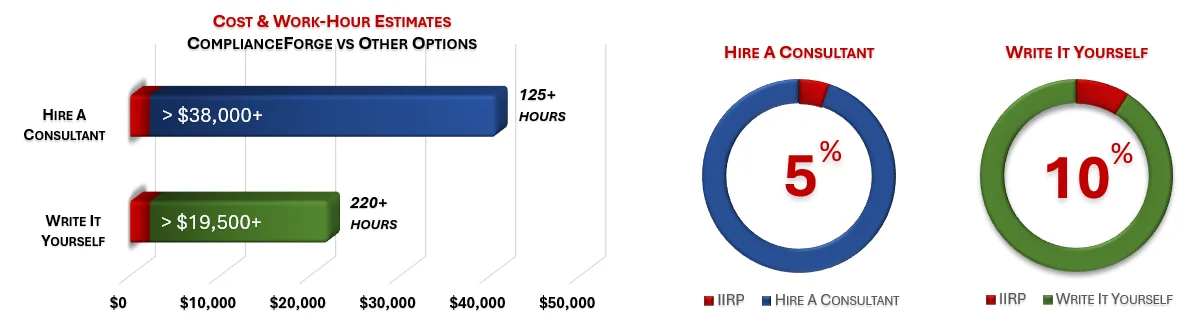
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
### 
## Cybersecurity Incident Response Documentation

## Professionally-Written, Editable & Easily-Implemented NIST 800-61 Based Incident Response Program
The IIRP operates at the strategic level to provide guidance to your organization's incident responders. It provides the overall framework that governs incident response across the enterprise with a focus on repeatable processes and sustainable operations. The IIRP breaks down the management of incident response into phases:
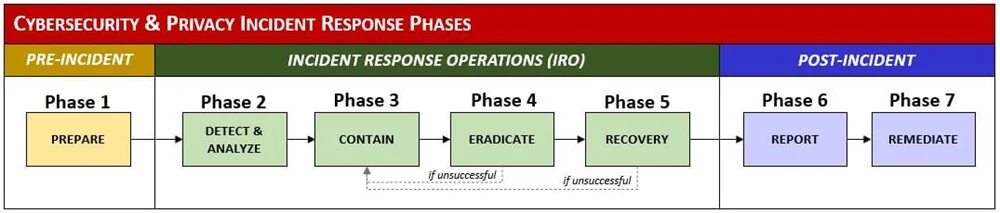
- **Pre-Incident**
- Phase 1 - Prepare
- **Incident Response Operations**
- Phase 2 - Detect & Analyze
- Phase 3 - Contain
- Phase 4 - Eradicate
- Phase 5 - Recovery
- **Post Incident**
- Phase 6 - Report
- Phase 7 - Remediate
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=4tvhmy4qw5a6)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
cybersecurity incident response plan template, nist incident response, incident response nist, incident handling program, cyber incident response plan nist, incident response plan template nist, incident response policy template, nist cyber incident response plan template, incident response documentation template, cyber security incident response template
## Cybersecurity Governance Framework
[Skip to main content](https://complianceforge.com/grc/hierarchical-cybersecurity-governance-framework/#main-content)
# ComplianceForge Reference Model
## Hierarchical Cybersecurity Governance Framework (HCGF)
The ComplianceForge Reference Model is commonly referred to as the **[Hierarchical Cybersecurity Governance Framework™](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")** ( **HCGF**). This reference model is designed to encourage clear communication by clearly defining cybersecurity and privacy documentation components and how those are linked. This comprehensive view identifies the primary documentation components that are necessary to demonstrate evidence of due diligence and due care. The HCGF addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics.
The Secure Controls Framework (SCF) fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant. ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
[](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "complianceforge reference model - hierarchical cybersecurity governance framework")
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
cybersecurity governance, cybersecurity governance risk and compliance, hcgf, compliance governance framework, grc framework, cybersecurity compliance framework, information security governance framework, compliance forge
## Cybersecurity Procedures Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/standardized-operating-procedures/#main-content)

# Editable Cybersecurity Procedures Templates
Documented procedures are one of the most overlooked requirements in cybersecurity compliance, but procedures are also a minimum expectation that an auditor is going to look for. For anyone who has written procedures, the answer for why companies routinely fail to maintain procedures is clear - it can take considerable time and effort to properly document processes. Part of that is tied to a lack of best practices around what good procedures look like - every organization tends to do something different, based on internal staff preferences or auditor pressure. This leads to a lack of standardization across departments and business functions, which can be an issue when trying to maintain "what right looks like" if a benchmark does not exist.

One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.)
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations
- Procedures are by their very nature de-centralized, where control implementation at the control level is defined to explain how the control is addressed.
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.
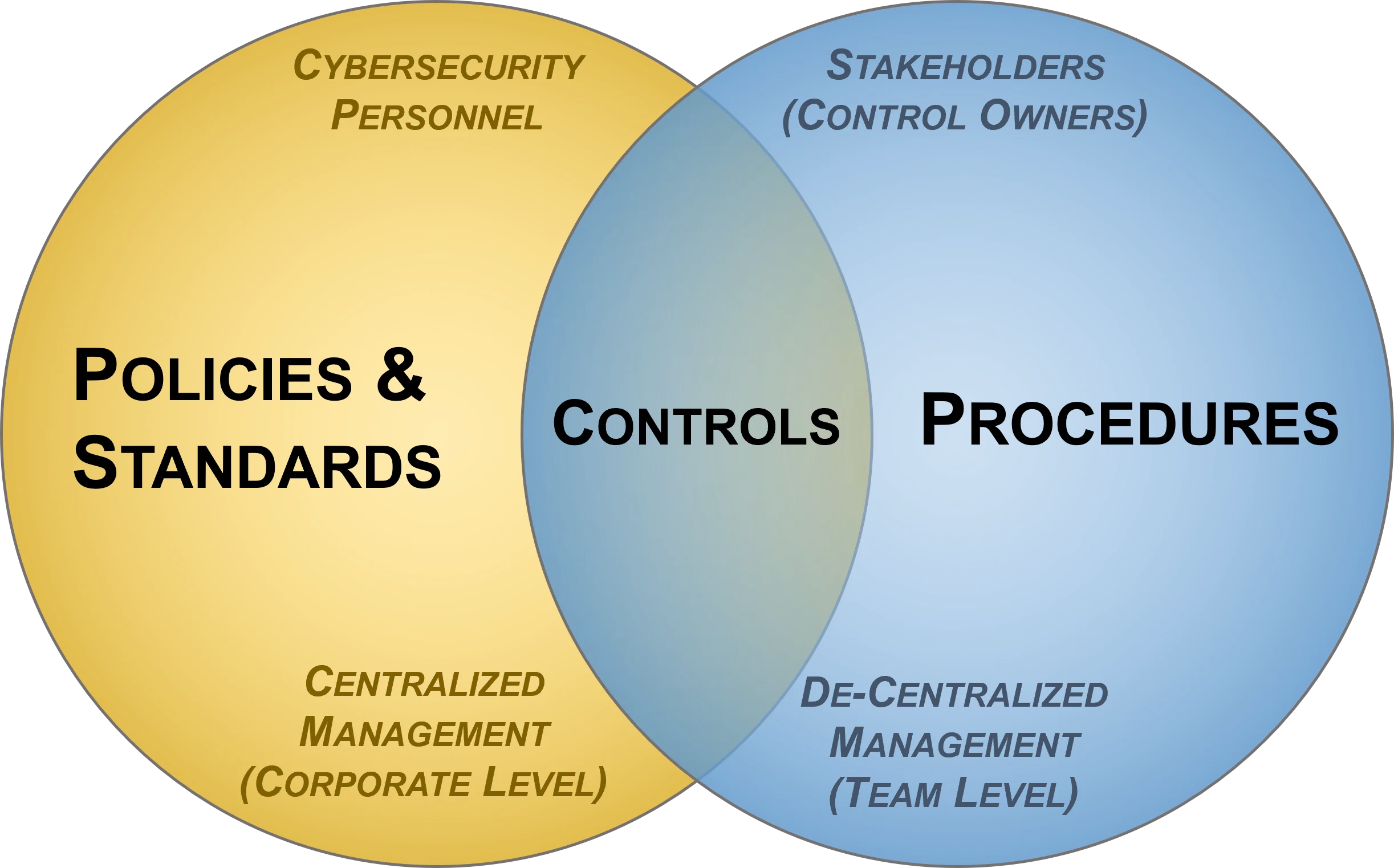
## Procedures Operationalize Cybersecurity Policies & Standards
We leverage the [Operationalizing Cybersecurity Planning Model](https://complianceforge.com/free-guides/operationalizing-cybersecurity-planning-model "Operationalizing Cybersecurity Planning Model") in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
[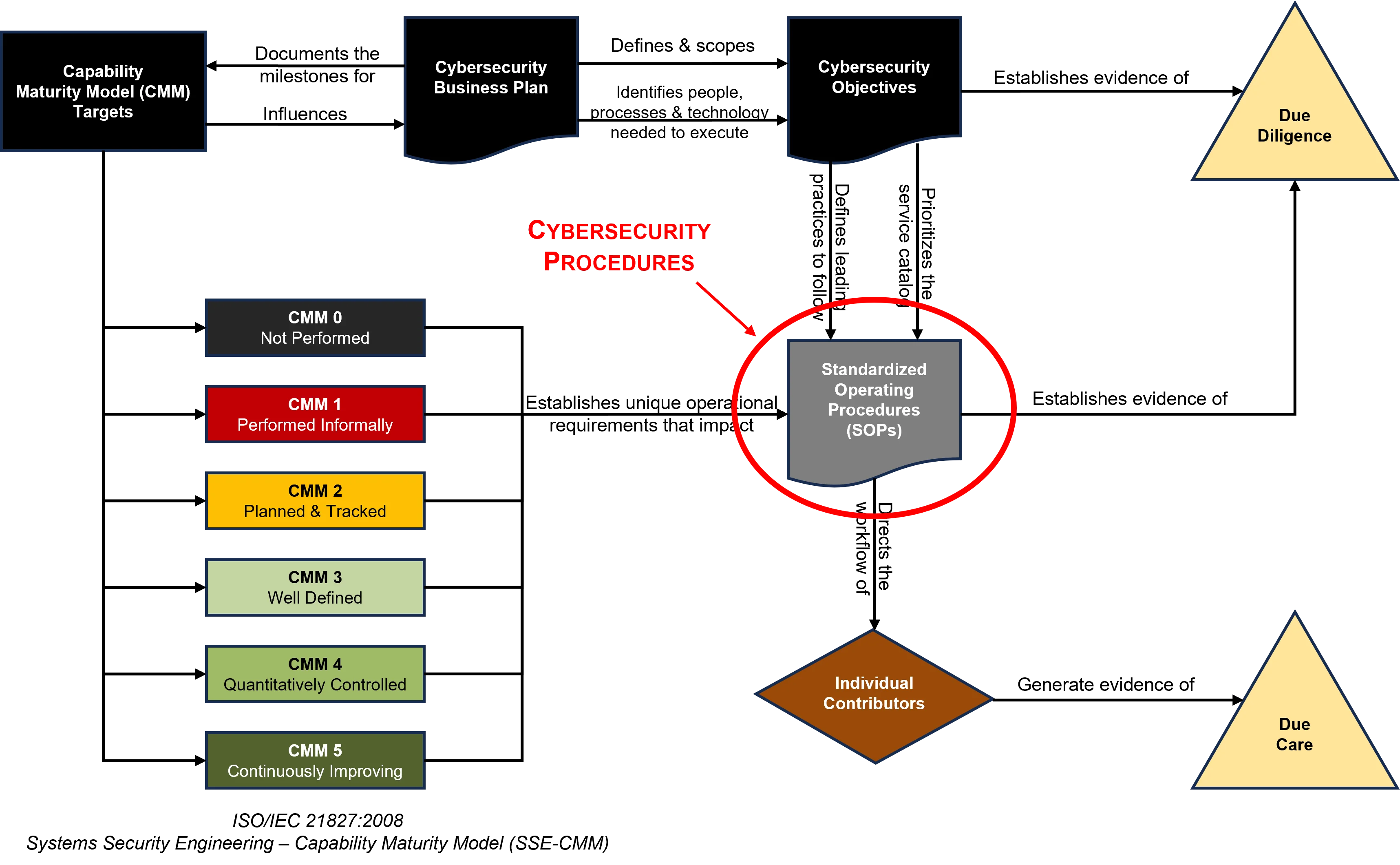](https://complianceforge.com/content/pdf/complianceforge-operationalizing-cybersecurity-planning-model.pdf "Operationalizing Cybersecurity Planning Model")
## What Can Be Done To Make Writing Procedures Easier?
The good news is that ComplianceForge developed a standardized template for procedures and control activity statements, the Cybersecurity Standardized Operating Procedures (CSOP).
Given the difficult nature of writing templated procedure statements, we aimed for approximately a **"80% solution"** since it is impossible to write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
Take a look at an [example](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-documentation-template-examples.pdf "Example Procedures Template") to see for yourself. We even provide a matrix to help identify the likely stakeholders for these procedures. There are five (5) versions of the CSOP:
- [CSOP - Digital Security Program (DSP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "SCF Procedures Template") (directly maps to the Secure Controls Framework (SCF))
- [CSOP - NIST 800-53 R5](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/ "NIST 800-53 Procedures Template")
- [CSOP - ISO 27002](https://complianceforge.com/product/iso-27002-procedures-csop/ "ISO 27001 27002 Procedures Template")
- [CSOP - NIST Cybersecurity Framework](https://complianceforge.com/product/nist-csf-procedures-csop/ "NIST CSF Procedures Template")
- [CSOP - NIST 800-171 (part of the NIST 800-171 Compliance Program (NCP))](https://complianceforge.com/product/nist-800-171-compliance-program/)
## Procedure Documentation Expectations
Procedures should be both clearly-written and concise, where procedure documentation is meant to provide evidence of due diligence that standards are complied with. Well-managed procedures are critical to a security program, since procedures represents the specific activities that are performed to protect systems and data. The diagram shown below helps visualize the linkages in documentation that involve written procedures:
- **CONTROL OBJECTIVES** exist to support **POLICIES**
- **STANDARDS** are written to support **CONTROL OBJECTIVES**
- **PROCEDURES** are written to implement the requirements that **STANDARDS** establish
- **CONTROLS** exist as a mechanism to assess/audit both the existence of **PROCEDURES / STANDARDS** and how well their capabilities are implemented and/or functioning
- **METRICS** exist as a way to measure the performance of **CONTROLS**
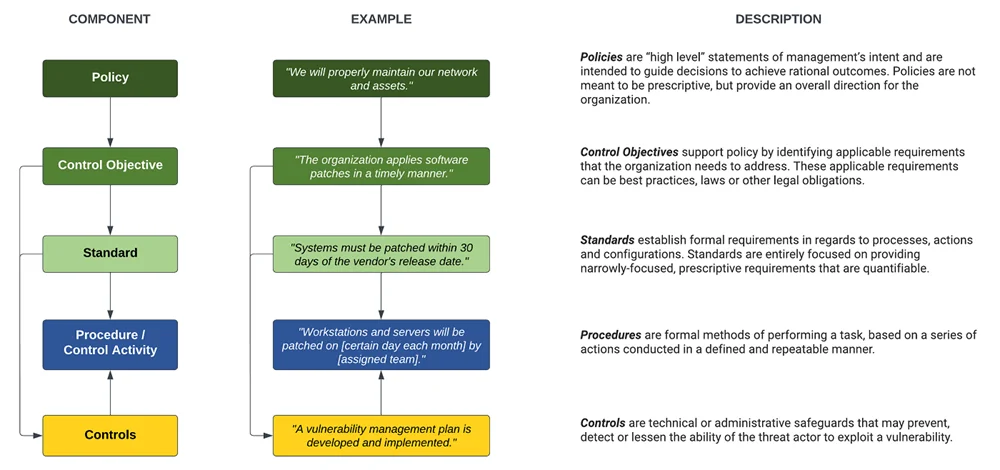
## What Can Go Wrong If I Do Not Have Written Procedures?
What can possibly go wrong with non-compliance with a law, regulation or contract?
- **Contract Termination**. It is reasonably expected that the other party will terminate contracts over non-compliance with major cybersecurity and privacy requirements since it is a failure to uphold contract requirements. Subcontractor non-compliance may also cause a prime contractor to be non-compliant, as a whole.
- **Criminal Fraud**. If a company states it is compliant when it knowingly is not compliant, that is misrepresentation of material facts. This is a criminal act that is defined as any act intended to deceive through a false representation of some fact, resulting in the legal detriment of the person who relies upon the false information (e.g., False Claims Act).
- **Breach of Contract Lawsuits**. Both prime contractors and subcontractors could be exposed legally. A tort is a civil breach committed against another in which the injured party can sue for damages. The likely scenario for a non-compliance related tort would be around negligence on behalf of the accused party by not maintaining a specific code of conduct (e.g., no documented procedures).
- **Fines**. The Federal Trade Commission (FTC) has authority to investigate and fine companies found to have poor security programs. In addition to fines, companies can be forced to pay for recurring, annual audits to demonstrate cybersecurity program effectiveness.
Below is a short list of statutory and regulatory requirements, as well as leading cybersecurity frameworks, that EXPECT every organization documents and maintains cybersecurity-related procedures. If you need to address one or more of those frameworks, then you need to maintain documented procedures.
- SOC 2
- CIS CSC 7
- Criminal Justice Information Services (CJIS)
- COBIT5
- COSO
- ENISA
- EU GDPR
- FedRAMP
- FFIEC
- HIPAA
- ISO 27001
- ISO 27002
- ISO 27018
- ISO 29100
- ISO 39100
- New Zealand Information Security Manual (NZISM)
- NIST Cybersecurity Framework
- NIST 800-53
- NIST 800-160
- NIST 800-171
- NY DFS 23 NYCRR 500
- PCI DSS
- UK Cyber Essentials
- UL 2900-1
## Browse Our Products
- [](https://complianceforge.com/product/scf-dsp-procedures-csop/)
#### [Procedures Template - DSP / SCF](https://complianceforge.com/product/scf-dsp-procedures-csop/)
Secure Controls Framework (SCF)
Cybersecurity Standardized Operating Procedures (CSOP) DSP \| SCF Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$6,400.00 - $11,200.00
[Choose Options](https://complianceforge.com/product/scf-dsp-procedures-csop/)
- [](https://complianceforge.com/product/nist-csf-procedures-csop/)
#### [Procedures Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST Cybersecurity Framework 2.0
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/nist-csf-procedures-csop/)
- [](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
#### [Procedures Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) ISO 27001 / ISO 27002
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-procedures-csop/)
- [](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
#### [Procedures Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST 800-53 R5 Moderate Baseline
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a...
$4,700.00 - $9,500.00
[Choose Options](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/)
- [](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
#### [Procedures Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
ComplianceForge
Cybersecurity Standardized Operating Procedures (CSOP) NIST 800-53 R5 HIGH & FedRAMP LOW/MODERATE/HIGH Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website...
$5,995.00 - $10,795.00
[Choose Options](https://complianceforge.com/product/procedures-nist-800-53-fedramp-high/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## CMMC Requirements Guide
[Skip to main content](https://complianceforge.com/blog/your-cmmc-requirements-guide/#main-content)
[](https://complianceforge.com/blog/your-cmmc-requirements-guide/)
A common issue facing many front-line IT / cybersecurity practitioners is that they do not know where to start with CMMC, let alone what path they need to follow to pass a CMMC assessment. There is an enormous amount of "What is CMMC?" guidance on LinkedIn, webinars and on the Internet in general, but there is a lack of practical guidance of HOW you are actually supposed to "do CMMC" in realistic terms.
The CMMC Kill Chain is designed to provide a roadmap that would be usable for (1) anyone starting out or (2) anyone wanting to double check their approach. You can read more about it here - [https://complianceforge.com/nist-800-171/nist-800-171-cmmc-kill-chain/](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-kill-chain/).
To learn more about the requirements for CMMC and how to comply with it, you can read more about it here - [https://complianceforge.com/compliance/cmmc](https://complianceforge.com/compliance/cmmc).
- [#CMMC](https://complianceforge.com/blog/tag/CMMC)
- [#CMMC Kill Chain](https://complianceforge.com/blog/tag/CMMC+Kill+Chain)
- [Email](mailto:?subject=Your%20CMMC%20Requirements%20Guide%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fyour-cmmc-requirements-guide%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fyour-cmmc-requirements-guide%2F&title=Your%20CMMC%20Requirements%20Guide%20-%20ComplianceForge&summary=Your%20CMMC%20Requirements%20Guide%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fyour-cmmc-requirements-guide%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## C-SCRM Bundle 2
[Skip to main content](https://complianceforge.com/bundle/c-scrm-bundle-2/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/324/1461/C-SCRM_Bundle_2__99133.1740598482.png?c=2)
No reviews yet
$49,840.00
$27,412.00
(You save
$22,428.00
)
# C-SCRM Bundle 2: DSP version (SCF alignment)
SKU:C-SCRM-B2-NOUPC:692878857109Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=C-SCRM%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-2%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-2%2F&title=C-SCRM%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&summary=C-SCRM%20Bundle%202%3A%20DSP%20version%20(SCF%20alignment)&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-2%2F "Linkedin")

## Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle \#2 - DSP Version(45% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk Management (C-SCRM):
01. [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
02. [Cybersecurity Standardized Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/)
03. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)
04. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
05. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
06. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
07. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
08. [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
09. [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
10. [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
11. [Secure Engineering & Data Privacy (SEDP)](https://complianceforge.com/product/security-by-design-privacy-by-design/)
12. [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
13. [Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")
## NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
This bundle is designed for organizations that need to comply with the European Union General Data Protection Regulation (EU GDPR) and the pending California Consumer Privacy Act (CCPA). This is beyond just cybersecurity policies and standards and a standard SCRM plan. This is addresses the unique compliance needs for privacy and cybersecurity to manage risk in a coordinated effort. The end result is a comprehensive, customizable, easily implemented set of documentation that your company needs to establish a cybersecurity and privacy program. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate - Privacy Bundle \#2 (Digital Security Program (DSP) version)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 3,000 internal staff work hours, which equates to a cost of approximately **$404,000** in staff-related expenses. This is about 40-60 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 4,100 contractor work hours, which equates to a cost of approximately **$969,750**. This is about 30-48 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 7% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
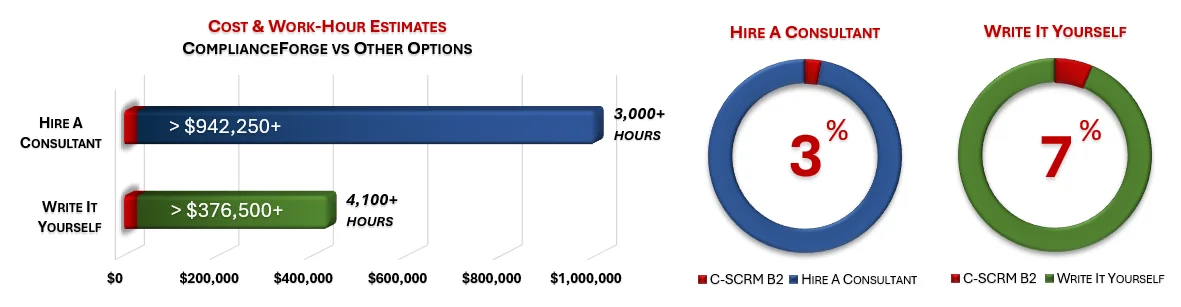
## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.

## Products Included in C-SCRM Bundle \#2 (DSP version)
The Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle 1 uses the Cybersecurity & Data Protection Program (CDPP) and C-SCRM Bundle #2 uses the Digital Security Program (DSP). **The DSP is targeted for larger, enterprise environments**, but more differences between the CDPP and DSP can be read about [here](https://complianceforge.com/faq/dsp-vs-wisp). The CDPP comes in either NIST CSF, ISO 27001/2 or NIST 800-53 moderate.
| | |
| --- | --- |
|  | [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "Digital Security Program (DSP)")
The DSP addresses more than just the “why?” and “what?” questions in an audit, since in addition to the core policies and standards that form the foundation for your cybersecurity program, the DSP comes with controls and metrics!
- Most popular product for organizations that need to address multiple compliance obligations and cannot be locked into a single framework (e.g., NIST 800-53, ISO 27002 or NIST Cybersecurity Framework).
- Maps to over 100 statutory, regulatory and contractual cybersecurity and privacy frameworks to create a hybrid approach to cybersecurity policies, standards, controls and metrics.
- Provides 1-1 mapping with the [**Secure Controls Framework (SCF)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework Policy"), so you can easily align your **policies**, **standards** and **metrics** with the controls you use from the SCF!
- DSP contains many useful supplemental documentation templates:
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- and many more templates |
|  | **NIST SP 800-161 Rev 1-Based [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)**
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable C-SCRM implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - DSP Version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template")
The DSP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the CDPP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
|  | [**Secure Engineering & Data Privacy (SEDP)**](https://complianceforge.com/product/security-by-design-privacy-by-design/ "Security & Privacy by Design")
The SEDP addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SEDP provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SEDP is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering. |
|  | [**Continuity of Operations Program (COOP)**](https://complianceforge.com/product/continuity-of-operations-plan/ "Continuity of Operations Program COOP")
The COOP addresses the “how?” questions for how your company plans to respond to disasters to maintain business continuity.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP's policies and standards for disaster recovery and business continuity operations.
- The concept of “continuity operations” spans incident response to disaster recovery to business continuity operations. This is a very common requirement in numerous statutory, regulatory and contractual requirements. The COOP provides your organization with the documentation to prove it addresses both disaster recovery and business continuity.
- The COOP is based on numerous frameworks to provide a holistic approach to DR and BC operations. |
|  | [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configuration template")
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization. |
|  | [**Information Assurance Program (IAP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E). |
|  | **[Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/ "Cybersecurity Business Plan (CBP)") [Information Assurance Program - Control Validation Testing](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")** The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization. |
|  | **[Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")** The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=ng97qgj48736)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Policy Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/policies-standards-controls/#main-content)
# Editable Cybersecurity & Data Privacy Policies & Standards Templates
The foundation for an organization's cybersecurity and privacy program is its policies and standards. These components form the alignment with leading practices to help ensure applicable statutory, regulatory and contractual requirements for cybersecurity and privacy are addressed. From these policies and standards, procedures and other program-level guidance provide the specific details of how these policies and standards are implemented.
## Do You Need To Align With A Specific Cybersecurity Framework?
There are a lot of choices to pick from when selecting a cybersecurity framework. If you are not sure what works best for you, you can read more [here](https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf). The most common frameworks are [NIST 800-53](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/), [ISO 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/), the [NIST Cybersecurity Framework](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/) and the [Secure Controls Framework (SCF)](https://complianceforge.com/product/comprehensive-digital-security-program/). To do NIST CSF, ISO 27002 or NIST SP 800-53 properly, it takes more than just a set of policies and standards. While those are foundational to building a cybersecurity program aligned with that framework, there is a need for program-specific guidance that helps operationalize those policies and standards (e.g., risk management program, third-party management, vulnerability management, etc.). It is important to understand what is required to comply with NIST CSF vs ISO 27002 vs NIST SP 800-53, since there are significantly different levels of expectation.
It is important to understand that picking a cybersecurity framework is more of a business decision and less of a technical decision. Realistically, the process of selecting a cybersecurity framework must be driven by a fundamental understanding of what your organization needs to comply with from a statutory, regulatory and contractual perspective, since that understanding establishes the minimum set of requirements necessary to:
1. Not be considered negligent with reasonable expectations for cybersecurity & data protection;
2. Comply with applicable laws, regulations and contractual obligations; and
3. Implement the proper controls to secure your systems, applications and processes from reasonable threats, based on your specific business case and industry practices.
This understanding makes it easy to determine where on the "framework spectrum" (shown below) you need to focus for selecting a set of cybersecurity principles to follow. This process generally leads to selecting the NIST Cybersecurity Framework, ISO 27002, NIST SP 800-53 or SCF as a starting point.

## Documentation Done Right
| | |
| --- | --- |
| [](https://complianceforge.com/content/pdf/start-here-cybersecurity-documentation-overview.pdf "Guide To Understanding Cybersecurity & Data Protection Documentation") | Effective cybersecurity and data protection is a team effort involving the participation and support of every user that interacts with your company’s data and/or systems, it is a necessity for your company’s cybersecurity & data protection requirements to be made available to all users in a format that they can understand. That means your company must publish those requirements in some manner, generally in either PDF format or published to an internal source (e.g., wiki, SharePoint, Jira, GRC, etc.). Our goal is to make that process as efficient, cost-effective and scalable, as possible.
Since words have meanings, it is important to provide examples from industry-recognized sources for the proper use of these terms that make up cybersecurity & privacy documentation. Simply because you have heard a term used in one manner for the last decade, it does not mean that is correct. That is why we wrote the following guide to help explain how cybersecurity and data protection documentation is meant to be developed, based on authoritative definitions of the components that make up documentation (e.g., policies, standards, procedures, controls, etc.).
As a "rule of thumb" to understand how documentation ages, if your cybersecurity policies, standards and procedures are old enough to start kindergarten (4-5 years old) then it is time to perform a thorough refresh / update cycle. Cybersecurity and privacy are evolving fields and your documentation needs to be current to address these new requirements and threats. |
## What Is The "Best" Cybersecurity Framework For Your Needs?
The concept of a "best" cybersecurity framework is misguided, since the most appropriate framework to align with is entirely dependent upon your business model. The applicable laws, regulations and contractual obligations that your organiation must comply with will most often point you to one of four (4) starting points to kick off the discussion about " **_Which framework is most appropriate for our needs?_**":
- **NIST Cybersecurity Framework (NIST CSF)**;
- **ISO 27001/27002**;
- **NIST SP 800-53** (moderate or high baselines); or
- **Secure Controls Framework (SCF)**(or a similar metaframework).
[](https://complianceforge.com/content/pdf/start-here-cybersecurity-framework-selection.pdf "Cybersecurity Frameworks NIST CSF vs ISO 27001 27001 vs NIST 800171 vs NIST 800-53 vs SCF")
## ComplianceForge Sells More Than Just Policies & Standards
While policies, standards and procedures form the foundation of any cybersecurity and data protection program, there are many other components that build off of those documents:
- Foundational Policies, Standards & Procedures;
- Risk Management;
- Vulnerability Management;
- Incident Response & Crisis Management;
- Supply Chain Risk Management; and
- Privacy & Secure Engineering.

## Comprehensive Coverage
Give us a [call or send us an email](https://complianceforge.com/contact-us/ "Contact ComplianceForge.com")\- we are happy to help you find the right solution for your needs!
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) Policy Template - Editable Policies & Standards
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## CMMC Compliance Templates
[Skip to main content](https://complianceforge.com/compliance/cmmc-dfars0252-204-7021#main-content)

# Editable CMMC Policies, Standards & Procedures Templates
ComplianceForge has been on the forefront of developing editable policies, standards, procedures and other templates to address NIST 800-171 compliance since 2016 when it was first released. As Department of Defense (DoD) requirements evolved to include third-party attestation through the Cybersecurity Maturity Model Certification (CMMC), so did ComplianceForge’s solutions, where we offer affordable, editable cybersecurity policies, standards, procedures and other templates to address CMMC 2.0 Levels 1, 2 and 3.
We field a lot of questions regarding NIST 800-171 and CMMC compliance. The information on this page relates to the common questions of what CMMC is, how CMMC relates to NIST 800-171 and what ComplianceForge products address both NIST 800-171 and CMMC requirements. With the release of CMMC 2.0 that takes the focus of CMMC back to NIST SP 800-171 controls. NIST 800-171 R3 is expected to be finalized in early 2024, which will require a "CMMC 3.0" release to follow those changes from NIST.
When it comes to CMMC compliance, ComplianceForge's editable policies, standards, procedures and other templates are a business accelerator - our products can save you time and significantly reduce the labor costs that are traditionally associated with researching and developing CMMC policies, standards and procedures on your own or by hiring a consultant to do it for you. These are not "fill in the blanks" templates - while they are expected to be edited for your specific needs, these policies, standards and procedures templates are written to address leading secure practices. ComplianceForge documentation can be scoped to address multiple environments (e.g., on-premises and/or in a hosted environment).
**ComplianceForge is an industry-leader in NIST 800-171 compliance documentation and have been evolving our DFARS-specific cybersecurity solutions since 2016.** We specialize in [cybersecurity compliance documentation](https://complianceforge.com/cmmc-nist-800-171-templates/ "NIST 800-171 compliance policy procedures documentation") and our products include the policies, standards, procedures and POA&M/SSP templates that companies (small, medium and large) need to comply with NIST 800-171. We've been writing cybersecurity documentation since 2005 and we are here to help make NIST 800-171 compliance as easy and as affordable as possible. Essentially, CMMC is the DoD's requirement for the Defense Industrial Base (DIB) to obtain a third-party assessment that NIST 800-171 controls are implemented.
[](https://complianceforge.com/cmmc-nist-800-171-templates/ "editable NIST 800-171 CMMC policies standards procedures template")
## “DIBCAC Battle Tested” CMMC 2.0 Policies, Standards & Procedures Templates
ComplianceForge’s [NIST 800-171 / CMMC documentation](https://complianceforge.com/cmmc-nist-800-171-templates/) has been used successfully by multiple companies during DIBCAC assessments to efficiently and effectively generate the necessary artifact documentation to demonstrate compliance with NIST SP 800-171 controls and NIST SP 800-171A control objectives. This battle tested documentation includes the necessary policies, standards, procedures, SSP, POA&M, Incident Response Plan (IRP) and other documentation that are expected to exist to successfully pass a third-party assessment, be it DIBCAC or a C3PAO.
Complying with NIST SP 800-171 & CMMC can be hard enough without arguing over terminology. Terminology pertaining to cybersecurity documentation is often abused, so a simplified concept of the hierarchical nature of cybersecurity documentation is needed to demonstrate the unique nature of these components, as well as the dependencies that exist. ComplianceForge created a reference model that is designed to encourage clear communication by defining cybersecurity documentation components and how those are linked. This model is based on industry-recognized terminology from NIST, ISO, ISACA and AICPA to addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, assessment objectives, risks, threats, procedures & metrics. This also addresses what SSPs, POA&Ms and secure configurations are and how those integrate into an organization's existing cybersecurity documentation. Click on the image below to download the PDF:
[](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "NIST 800-171 & CMMC compliance documentation terminology reference example")
## NIST 800-171 R3 Documentation Upgrade Path
Sooner, rather than later, the US Government's global supply chain will have to transition to NIST 800-171 R3.
[](https://complianceforge.com/product/nist-800-171-compliance-program/ "NIST 800-171 Compliance Program | nist 800-171 r2 and r3 policies standards procedures scrm plan templates")
ComplianceForge provides a free resource for organizations migrating from NIST 800-171 R2 to R3. This guide provides an Assessment Objective (AO)-level analysis to address differences:
- Over 1/3 are minimal effort (clear, direct mapping);
- Approximately 1/5 are moderate effort (indirect mapping); and
- Approximately 1/2 are significant effort (no clear mapping or new AOs).
This guide also addresses the logical dependencies that exist from "orphaned AOs" that are not in NIST 800-171A R3, but a requirement to demonstrate evidence of due diligence and due care still exists for specific functions (e.g., maintenance operations, roles & responsibilities, inventories, physical security, etc.).
[](https://complianceforge.com/content/pdf/guide-nist-800-171-r3-transition.pdf "NIST 800-171 R2 to R3 upgrade")
## CMMC v2.0 (DFARS 252.204-7021) Overview
CMMC is a vehicle the US Government is using to implement a tiered approach to audit contractor compliance with NIST SP 800-171, based on five different levels of maturity expectations. DoD contractors have been required to comply with NIST 800-171 since January 1, 2018. In the past two years, the DoD grappled with the low rate of NIST 800-171 compliance across the Defense Industrial Base (DIB) and CMMC was created to remedy that systemic issue of non-compliance by both primes and their subs. Interestingly, when NIST 800-171 was initially launched, the DoD would not accept any form of 3rd-party audit for evidence of NIST 800-171 compliance, but that is exactly what CMMC does, so a lot has changed in the past two years from how NIST 800-171 adoption was initially envisioned.
Think of CMMC as a procurement gate that a contractor must pass to even be eligible to bid on, win or participate on a contract - without a valid CMMC certification (Level 1 through 5), the prime and/or sub will be barred from the contract. It is conservatively-estimated that between 200,000 - 300,000 organizations will be in scope for CMMC, with many of those not being considered traditional defense contractors. The reason for that is the trickle-down effect of third-parties that have the ability to impact the confidentiality and/or integrity of Controlled Unclassified Information (CUI) where it is stored, transmitted and/or processed. This trickle-down will impact small organizations from IT support to bookkeepers and even janitorial support services, in addition to component manufacturers that fall in the supply chain.
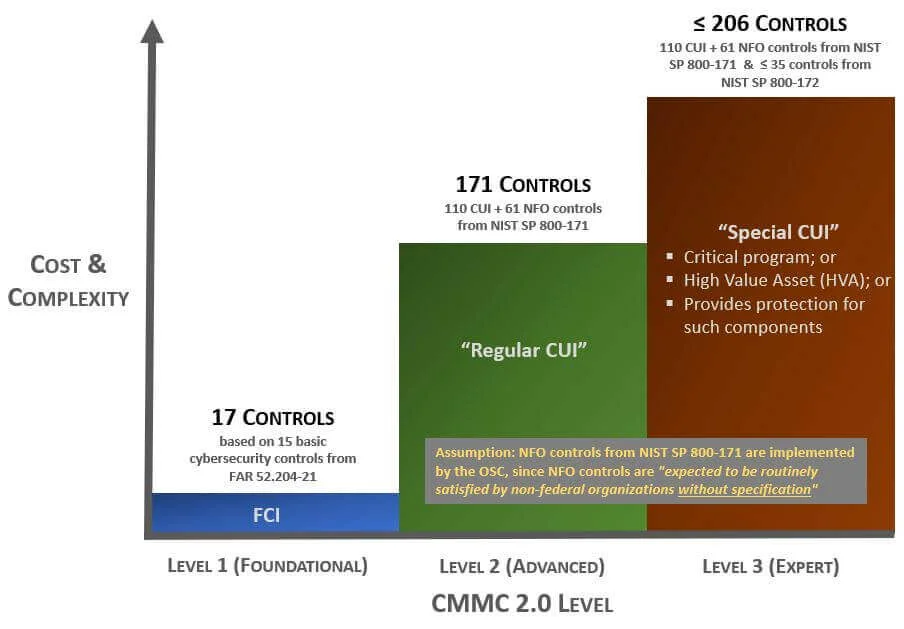
| | |
| --- | --- |
| If you are new to CMMC and want to get a neutral explanation of what it is without any Fear, Uncertainty & Doubt (FUD) marketing, you can click on the image to the right to read the " [Defense Acquisitions: DOD’s Cybersecurity Maturity Model Certification Framework](https://www.everycrsreport.com/files/2020-12-18_R46643_bf3182622b0855147dd209bff5e9e9c6a0217b71.pdf "Defense Acquisitions: DOD’s Cybersecurity Maturity Model Certification Framework")" from the Congressional Research Services (CRS). This document is meant to help educate members of Congress on CMMC, so it is about as neutral as anyone could expect an overview to be.
The CRS report to Congress is loaded with references that you can use to verify information for yourself. It is a really good guide to understand the history and some of the challenges pertaining to CMMC, so it is a worthwhile document to read. | [](https://www.everycrsreport.com/files/2020-12-18_R46643_bf3182622b0855147dd209bff5e9e9c6a0217b71.pdf "Defense Acquisitions: DOD’s Cybersecurity Maturity Model Certification Framework") |
## **Downloadable Excel Spreadsheet - CMMC 2.0 Crosswalk**
On 18 March 2020, the US Department of Defense (DoD) released version 1.02 of the CMMC. We took those requirements and made those into a user-friendly requirements matrix that indicates the requirements an organization faces from CMMC level 1 through level 5. We also provide mappings that show how ComplianceForge's products support each CMMC requirement. In the downloadable CMMC v2.0 requirements mapping matrix shown below, you can see how all **CMMC 2.0 Level 1-3 requirements** are supported by various ComplianceForge products.
[](https://cmmc-coa.com/ "CMMC awesomeness spreadsheet")
That downloadable Excel spreadsheet for CMMC v1.02 provides crosswalk mapping to the following frameworks:
- **FAR 52.204-21;**
- **NIST 800-171 Rev 2 & Rev 3;**
- **NIST 800-171B;**
- **NIST 800-53 Rev 5;**
- **CERT RMM v1.2;**
- **ISO 27002;**
- **NIST Cybersecurity Framework;**
- **CIS Critical Security Controls v7.1; and**
- **Secure Controls Framework (SCF).**
It also provides mappings to the following ComplianceForge products:
- [**NIST 800-171 Compliance Program (NCP);**](https://complianceforge.com/product/nist-800-171-compliance-program/ "NIST 800-171 Compliance Program CMMC 1 CMMC 2 CMMC 3")
- [**NIST 800-53 Cybersecurity & Data Protection Program (CDPP); and**](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/ "CMMC compliance NIST 800-53 moderate policies standards")
- [**Digital Security Program (DSP)**](https://complianceforge.com/product/comprehensive-digital-security-program/ "DSP CMMC 4 CMMC 5 secure controls framework")
## New To CMMC? Use The "CMMC Kill Chain" To Build A Project Plan
A common issue facing many front-line IT/cybersecurity practitioners is that they do not know where to start with CMMC, let alone what path they need to follow to pass a CMMC assessment. There is an enormous amount of "What is CMMC?" guidance on LinkedIn, webinars and on the Internet in general, but there is a lack of practical guidance of HOW you are actually supposed to "do CMMC" in realistic terms. The [**CMMC Kill Chain**](https://complianceforge.com/nist-800-171/cmmc-kill-chain/) is designed to provide a roadmap that would be usable for (1) anyone starting out or (2) anyone wanting to double check their approach. You can also download it by clicking on the image below to get a PDF version of the graphic and description.
[](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-kill-chain/ "CMMC Kill Chain")
## Cybersecurity Maturity Model Certification (CMMC) v2.0 Requirements - Understanding The People, Processes & Technology Connections
As you can see in the downloadable infographic below, the responsibilities associated with CMMC spread far beyond just the cybersecurity team. Having a clear understanding of who "owns" certain CMMC controls now will payoff significantly as you prepare for your CMMC audit, since these are primarily not "cybersecurity" controls and many are owned by the business process owner or the IT asset custodians.
## CMMC Scoping Considerations - Free Guide To Reducing [Controlled Unclassified Information (CUI)](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret "Controlled Unclassified Information CUI definition")
| | | |
| --- | --- | --- |
| [](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "Unified Scoping Guide (USG) | CUI Scoping Guide | CMMC Scoping Guide | NIST 800-171 Scoping Guide")
Click [here](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "Unified Scoping Guide (USG) | CUI Scoping Guide | CMMC Scoping Guide | NIST 800-171 Scoping Guide") for a **FREE GUIDE** | | We put together a free guide to help identify what is in scope for NIST 800-171 Rev 2 & Rev 3. Once you know what your CUI is, the next step is to scope your environment and this is a valuable guide for those efforts. Not sure what CUI is or if you have CUI on your network? Go to the US government's authoritative source on the matter, the US Archives CUI Registry at [https://www.archives.gov/cui](https://www.archives.gov/cui "NARA CUI Archives").
When you look at NIST 800-171 rev 1 compliance, it has some similarities to the Payment Card Industry Data Security Standard (PCI DSS). That may sound odd to you, but from the perspective of PCI DSS, if scoping is done poorly, a company's entire network may be in-scope as the Cardholder Data Environment (CDE), which means PCI DSS requirements would apply uniformly throughout the entire company. The same holds true for CUI environments. In these scenarios, PCI DSS compliance can be prohibitively expensive or even technically impossible. However, when the network is intelligently-designed with security in mind, the CDE can be a small fraction of the company's network, which makes compliance much more achievable and affordable.
Based on a lack of scoping guidance from the DoD, our assessment of scoping NIST 800-171 is that it should following a similar, structured approach to scoping that is used for PCI DSS compliance. The reason for this is the proposed approach is a reasonable method, based on accepted practices to comply with cybersecurity requirements. This guide is meant to help companies identify assets within scope for NIST 800-171 and potentially find ways to minimize scope through isolation or controlled access. |
## What ComplianceForge Products Apply To CMMC 2.0?
Complying with the requirements from **[DFARS](https://complianceforge.com/compliance/nist-800-171)** goes beyond just having policies and standards. When you break down the requirements to comply with **[DFARS / NIST 800-171](https://complianceforge.com/compliance/nist-800-171)**, you will see how ComplianceForge's products address a specific DFARS compliance need. In the chart, "NFO" stands for Non-Federal Organization. NFO controls are required for contractors and are called out in Appendix E of NIST 800-171. Aligning with NIST 800-53 is the most straightforward approach to complying with NIST 800-171, based on the official mappings in Appendices D & E of NIST 800-171.
| | | |
| --- | --- | --- |
| **ComplianceForge Product** | **DFARS / NIST 800-171** | **NIST 800-53** |
| Cybersecurity & Data Protection Program ( **CDPP**) or
Digital Security Program ( **DSP**)
\[policies & standards map to all NIST 800-171 Rev 2 & Rev 3 requirements\] | 252.204-7008
252.204-7012
**NIST 800-171 (multiple NFO controls)** | PM-1
\[multiple sections\] |
| Vendor Compliance Program ( **VCP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO PS-7** | PS-7
SA-4 |
| Cybersecurity Risk Management Program ( **RMP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO RA-1** | PM-9
RA-1 |
| Cybersecurity Risk Assessment Template ( **CRA**) | 252.204-7008
252.204-7012
**NIST 800-171 3.11.1** | RA-3 |
| Vulnerability & Patch Management Program ( **VPMP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.11.2** | SI-2
SI-3(2) |
| Integrated Incident Response Program ( **IIRP**) | 252.204-7008
252.204-7009
252.204-7010
252.204-7012
**NIST 800-171 3.6.1** | IR-1 |
| Security & Privacy By Design ( **SPBD**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO SA-3** | Privacy Section
SA-3 |
| System Security Plan ( **SSP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.12.4** | PL-2 |
| Cybersecurity Standardized Operating Procedures ( **CSOP**) | 252.204-7008
252.204-7012
**NIST 800-171 (multiple NFO controls)** | PL-7
\[multiple sections\] |
| Continuity of Operations Plan ( **COOP**) | 252.204-7008
252.204-7012
**NIST 800-171 3.6.1** | CP-1
CP-2
IR-4(3)
PM-8 |
| Secure Baseline Configurations ( **SBC**) | 252.204-7008
252.204-7012
**NIST 800-171 3.4.1** | CM-2
CM-6
SA-8 |
| Information Assurance Program ( **IAP**) | 252.204-7008
252.204-7012
**NIST 800-171 NFO CA-1** | CA-1
PM-10 |
## CMMC Policies, Standards & Procedures Done Right - Designed To Be Scalable, Comprehensive & Efficient
We leverage the **[Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework")** to develop the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care for our clients. This methodology towards documentation acknowledges the interconnectivity that exists between policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. This documentation model works well with **NIST 800-171, NIST 800-53, ISO 27002, NIST CSF, FedRAMP, CIS CSC Top 20, PCI DSS, Secure Controls Framework (SCF)** and other control frameworks.
Essentially, ComplianceForge simplified the concept of the hierarchical nature of cybersecurity and privacy documentation that you can see in the downloadable diagram shown below. This helps demonstrate the unique nature of these components, as well as the dependencies that exist. You can download the example to better understand how we write our documentation that links policies all the way down to metrics. This is a great solution for any organization currently using or migrating to a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) platform to help automate their governance practices.
[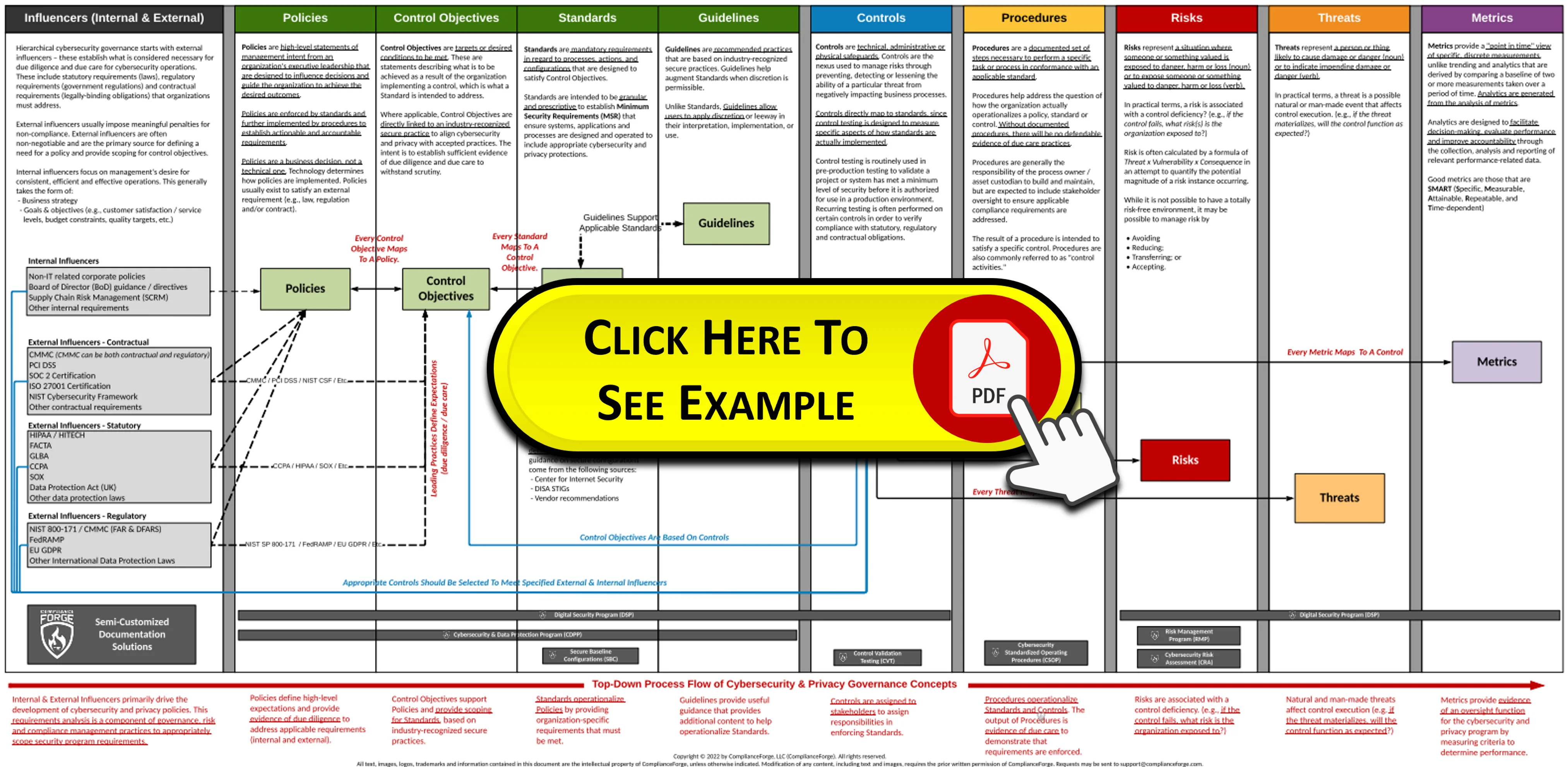](https://complianceforge.com/content/Hierarchical-Cybersecurity-Governance-Framework.pdf "Hierarchical Cybersecurity Governance Framework")
## **How Should I Prepare For A CMMC Assessment?**
Based on version 2.0 of the CMMC, there were 3 levels and each has its own specific set of controls that will be in scope for a CMMC audit. Each level of CMMC maturity has increasing expectations:
- CMMC Level 1: 17 Level 1 controls that are based on 15 basic cybersecurity controls from FAR 52.204-21;
- CMMC Level 2: 110 CUI controls from NIST SP 800-171; and
- CMMC Level 3: 110 CUI controls from NIST SP 800-171 + up to 35 controls from NIST SP 800-172.
**[NIST SP 800-171A](https://csrc.nist.gov/publications/detail/sp/800-171a/final "NIST 800-171A CMMC audit")**, _Assessing Security Requirements for Controlled Unclassified Information_, is the underlying set of Assessment Objectives (AOs) that serve as the basis for the criteria used by a C3PAO when evaluating against a CMMC requirement that is directly mapped to a NIST 800-171 Rev 2 or Rev 3 control. Until final guidance on what C3PAOs will use for the assessment, the main focus of CMMC audit preparation should be on clear, concise documentation (e.g., CMMC/NIST 800-171 specific policies, standards, procedures, SSP, POA&M, etc.). The reason for this is from a financial perspective, you will be paying a 3PAO an hourly rate (likely $300/hr +/- $100) and the longer it takes an auditor to review and understand your environment, the more billable hours will accumulate. Therefore, clear and concise documentation can potentially save tens of thousands of dollars in future C3PAO audit-related costs.
One thing to keep in mind as you prepare for a CMMC assessment - in the audit world there are two constants:
- **Time is money**; and
- **Nothing exists unless it is documented**.
A documentation review will likely occur before the C3PAO conducts any staff interviews, so the more questions you can address by clear documentation, the less your staff will have to fill in the blanks with auditor questions. This is really where good documentation is half the battle in an audit! Expect your C3PAO to start their assessment by:
- Performing a thorough review of your **[System Security Plan (SSP)](https://complianceforge.com/product/nist-800-171-system-security-plan-ssp-poam-template/ "SSP template")** to understand the who/what/when/where/how/why of your CUI environment;
- Assessing your [**Plan of Action & Milestones (POA&M)**](https://complianceforge.com/product/nist-800-171-system-security-plan-ssp-poam-template/ "POA&M template") to understand what controls are not addressed (if applicable) and how your compensating controls exist to remediate the risk of non-compliance on a certain control; and
- Evaluating your **[policies, standards and procedures](https://complianceforge.com/cmmc-nist-800-171-templates/ "CMMC NIST 800-171 policies standards procedures")** to see if those line up with the SSP and if that documentation supports all the requirements of NIST 800-171 / CMMC.
## **If I Comply With CMMC, Am I Therefore Compliant With NIST 800-171?**
No. By itself, passing a CMMC audit does not mean you are compliant with NIST 800-171. If you look in **Appendix D** of NIST 800-171 Rev 2, you will see it contains 110 **Controlled Unclassified Information (CUI)** controls and in **Appendix E** there are also 63 **Non-Federal Organization (NFO)** controls. While NIST 800-171 is primarily focused on protecting CUI wherever it is stored, transmitted and processed, your organization still needs to comply with both the CUI and NFO controls.
For some reason, CMMC only focuses on CUI controls and does not have NFO controls in scope for the CMMC audits. While this is financially beneficial to contractors to have less controls in scope for an audit, it also lulls most contractors into a false sense of compliance where they focus on the 110 CUI controls and ignore the 63 NFO controls. To reiterate that point, to be considered “NIST 800-171 compliant” you need to comply with both the CUI and NFO controls. Therefore, having a CMMC Level 1, 2, 3, 4 or 5 certification does not mean you are actually compliant with NIST 800-171 and that can run your organization afoul through a violation of the **[False Claims Act (FCA)](https://www.justice.gov/sites/default/files/civil/legacy/2011/04/22/C-FRAUDS_FCA_Primer.pdf)**, since you are required to comply with NIST 800-171. **CMMC is merely a 3rd party validation check to see if a basic level of compliance is being done as part of the contracting process.**
## CMMC vs NIST 800-171 vs NIST 800-53 Requirements - NIST Did Not Re-Invent The Wheel
Many people ask how NIST 800-171 is different from NIST 800-53. In reality, there is no NIST 800-171 vs NIST 800-53, since everything defaults back to NIST 800-53. Our solutions address both DFARS and FAR requirements for protecting **Controlled Unclassified Information (CUI)** by addressing NIST 800-171 and its corresponding NIST 800-53 requirements.

When it comes to being "audit ready" for a company with NIST 800-171, there is no such thing as "Bronze, Silver or Gold" levels of compliance since a standard is a standard for a reason. This is where documentation is king, since in cybersecurity compliance audits, if it is not documented then it does not exist. ComplianceForge can provide you with the documentation you need to demonstrate evidence of due care and due diligence to be considered compliant (e.g., policies, standards, procedures, SSP & POA&M). Our affordable solutions range from [**cybersecurity policies & standards**](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-171 compliance policies") documentation, to [**NIST 800-171 compliance checklists**](https://complianceforge.com/nist-800-171-compliance-documentation/ "NIST 800-171 compliance checklist template"), to program-level documentation, such as "turn key" [**incident response**](https://complianceforge.com/digital-cybersecurity-incident-response-program-documentation/ "NIST 800-171 incident response policy IRP"), [**risk management**](https://complianceforge.com/digital-cybersecurity-risk-management/ "NIST 800-171 risk management risk assessment") or [**vulnerability management**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "NIST 800-171 vulnerability management flaw remediation patching policy ") program documents. Our focus is on helping you become audit ready!
NIST 800-171 is intended to force contractors to adhere with reasonably-expected security requirements that have been in use by the US government for years. NIST 800-171 establishes a basic set of expectations and maps these requirements to NIST 800-53, which is the de facto standard for US government cybersecurity controls. In some ways, this is a good thing since the US government is not reinventing the wheel with new requirements. Instead, the DoD selected moderate-level controls from an existing set of recognized best practices, commonly used throughout the DoD and Federal agencies. In the long run, this will help both the US government and private businesses speak the same language for cybersecurity.
The bottom line is NIST 800-171 creates a standardized and uniform set of requirements for all **Controlled Unclassified Information (CUI)** security needs. This is designed to address common deficiencies in managing and protecting unclassified information by that is being stored, transmitted or processed by private businesses.
## Cost of Non-Compliance With Cybersecurity Maturity Model Certification (CMMC)
What can possibly go wrong with non-compliance in a contract with the U.S. Government?
- **Contract Termination**. It is reasonably expected that the U.S. Government will terminate contracts with prime contractors over non-compliance with DFARS / NIST 800-171 requirements since it is a failure to uphold contract requirements. Subcontractor non-compliance will cause a prime contractor to be non-compliant, as a whole.
- **Criminal Fraud**. If a company states it is compliant when it knowingly is not compliant, that is misrepresentation of material facts. This is a criminal act that is defined as any act intended to deceive through a false representation of some fact, resulting in the legal detriment of the person who relies upon the false information (e.g., False Claims Act).
- **Breach of Contract Lawsuits**. Both prime contractors and subcontractors could be exposed legally. A tort is a civil breach committed against another in which the injured party can sue for damages. The likely scenario for a DFARS / NIST 800-171-related tort would be around negligence on behalf of the accused party by not maintaining a specific code of conduct (e.g., DFARS / NIST 800-171 cybersecurity controls).
As you can see from those examples, the cost of non-compliance is quite significant. As always, seek competent legal counsel for any pertinent questions on your specific compliance obligations.
## What Problem Does ComplianceForge Solve?
We sell cybersecurity documentation - policies, standards, procedures and more! Our documentation is meant to help companies become audit-ready!
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive NIST 800-171 compliance documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. ComplianceForge offers NIST 800-171 documentation solutions that can save your organization significant time and money!
- Compliance Requirements \- The reality of non-compliance with NIST 800-171 requirements means lost business and potential fines. In addition to losing contracts, charges of fraud may be leveled on companies that claim to be compliant with NIST 800-171 but cannot provide evidence. Our documentation can help you become and stay compliant with NIST 800-171 where you have documented evidence to prove it!
- Audit Failures \- Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. Our documentation provides mapping to NIST 800-53 and other leading security frameworks to show you exactly what is required to both stay secure and compliant. Being editable documentation, you are able to easily maintain it as your needs or technologies change.
## How Does ComplianceForge Solve It?
We take a holistic approach to creating comprehensive cybersecurity documentation that is both scalable and affordable. This is beyond just generic policies and allows you to build out an audit-ready cybersecurity program for your organization!
- Clear Documentation \- In an audit, clear and concise documentation is half the battle. ComplianceForge provides comprehensive documentation that can prove your NIST 800-171 compliant security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings \- Time is money! Our cybersecurity documentation addresses DFARS and FAR requirements and this can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - We did the heavy lifting. Our documentation is mapped to the NIST 800-53, as well as other leading security frameworks!
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
united states department of defense, national institute of standards and technology, computer security, federal acquisition regulation, controlled unclassified information, cybersecurity maturity model certification, regulatory compliance, fedramp, under secretary of defense for acquisition and sustainment, defense industrial base, contract, chief information officer, organization, supply chain, certification, cmmc framework, cmmc requirements, cmmc certification, cmmc compliance, cybersecurity maturity model, cmmc compliance requirements, information security, audit, risk, federal register, rulemaking, vulnerability, federally funded research and development centers, document, accounting, code of federal regulations, nist, level, cybersecurity, department of defense, cybersecurity requirements, defense federal acquisition, cmmc level, nist special publication, mil website, poa, defense contractors, cmmc model, cmmc, configuration management, subcontractor, classified information, access control, risk assessment, risk management, authentication, cybersecurity maturity, cmmc certified, cmmc assessment, cmmc assessor, infrastructure, communication, law, accreditation, policy, file sharing, hygiene, accountability, comptia, patch, regulation, cloud computing, critical infrastructure, asset, cmmc compliant, cmmc certification levels, cmmc compliance checklist, international organization for standardization, defense information systems agency, international traffic in arms regulations, managed services, threat, general data protection regulation, complexity, gap analysis, federal information processing standards, checklist, encryption, expert, research
[editable cmmc & nist 800](https://complianceforge.com/compliance-solutions/cmmc-nist-800-171-templates/) [cmmc kill chain. build a prioritized cmmc project plan](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-kill-chain/) [your cmmc requirements guide](https://complianceforge.com/blog/your-cmmc-requirements-guide/) [begin your compliance journey: nist 800](https://complianceforge.com/nist-800-171/nist-800-171-cmmc-compliance) [nist 800](https://complianceforge.com/cybersecurity-templates/nist-800-171-cmmc-compliance/) [easy nist 800](https://complianceforge.com/compliance/nist-800-171) [contact us](https://complianceforge.com/contact-us/) [example cmmc & nist cybersecurity documentation templates](https://complianceforge.com/example-cybersecurity-documentation/) [affordable cybersecurity templates for compliance standards](https://complianceforge.com/cybersecurity-templates/policies-standards-controls/) [complianceforge](https://complianceforge.com/login.php)
cmmc, cmmc compliance, cmmc requirements, cmmc compliance requirements
## GRC Policies and Procedures
[Skip to main content](https://complianceforge.com/governance-risk-compliance-grc-content/#main-content)

# GRC Content - Policies, Standards & Procedures
At ComplianceForge, we've been writing documentation and supporting GRC initiatives since 2005. We have [cybersecurity & data protection policies, standards, procedures and more that are specifically designed to be imported in and used by GRC solutions](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/). The information on this page is meant to pass on logical, worthwhile concepts pertaining to Governance, Risk Management & Compliance ( **GRC**) / Integrated Risk Management ( **IRM**) that you can professionally benefit from. Please note that we use the terms GRC and IRM synonymously, since they essentially function the same when you look beyond marketing semantics.
GRC can be a costly and labor-intensive endeavor, so what justifies the investment? Essentially, GRC functions help avoid negligence, with the added benefit of improved IT/cyber/privacy operating effectiveness. The reality of the situation is your company invests in cybersecurity and privacy as a necessity. This necessity is driven in large part by laws, regulations and contractual requirements that it is legally-obligated to comply with. It is also driven by the desire to protect its public image from damaging acts that happen when cybersecurity and privacy practices are ignored. Regardless of the specific reason, those charged with developing, implementing and running your organization’s cybersecurity and data protection program must do so in a reasonable manner that would withstand scrutiny that could take the form of an external auditor, regulator or prosecuting attorney.
| | | |
| --- | --- | --- |
|  | | _**How fast would you drive your car if you didn’t have any brakes?**_ Think about that for a moment - you would likely drive at a crawl in first gear and even then you would invariably have accidents as you bump into objects and other vehicles to slow down. Brakes on a vehicle actually allow you to drive fast, in addition to safely navigating dangers on the road!
While it is not the most flattering analogy, GRC is akin to the brakes on your car, where they enable a business’ operations to go fast and avoid catastrophic accidents. Without those "brakes", an accident is a certainty! These brakes that enable a business’ operations to stay within the guardrails are its cybersecurity policies, standards and procedures. These requirements constitute “reasonable practices” that the organization is required to implement and maintain to avoid being negligent. |
## Integrated Controls Management (ICM) = "How To GRC Playbook"
The premise of **Integrated Controls Management (ICM)** is that controls are central to cybersecurity and privacy operations, as well as the overall business rhythm of an organization. ICM takes a different approach from the traditional definition of **Governance, Risk Management and Compliance (GRC)** and/or **Integrated Risk Management (IRM)**, since ICM is controls-centric, where controls are viewed as the nexus, or central pivoting point, for an organization’s cybersecurity and privacy operations.
The premise is that controls are central to cybersecurity and privacy operations, as well as the business rhythms of the organization. Without properly defining controls thresholds, an organization’s overall cybersecurity and privacy program is placed in jeopardy as the baseline practices are not anchored to clear requirements. Furthermore, understanding and clarifying the difference between "compliant" versus "secure" enhances risk management discussions.
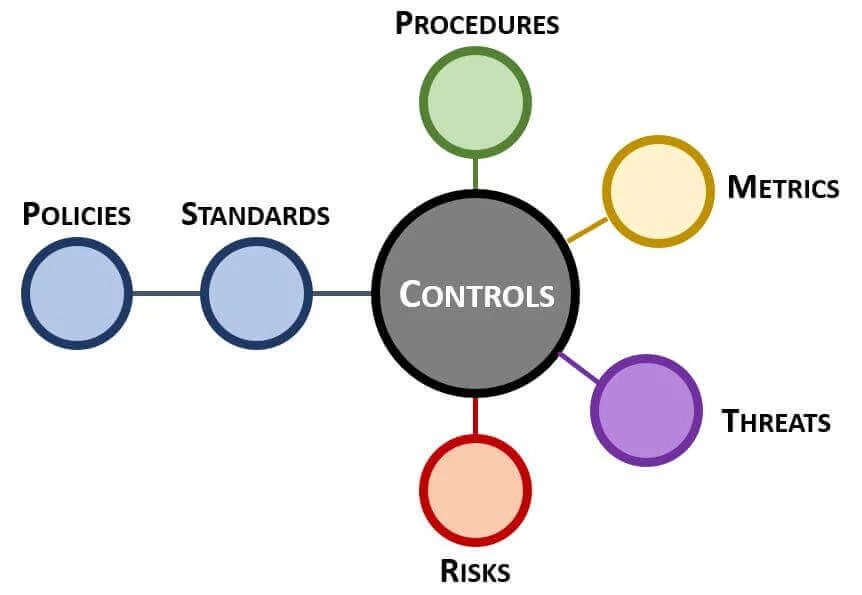
[**OCEG**](https://www.oceg.org/about/what-is-grc/ "GRC definition") defines GRC as, “ _GRC is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity_,” while [**Gartner**](https://www.gartner.com/en/information-technology/glossary/integrated-risk-management-irm "GRC & IRM definition") jointly defines GRC/IRM as, " _a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks_." **ComplianceForge** and [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework"), the developers of the ICM model, define ICM as, “ _a holistic, technology-agnostic approach to cybersecurity and data protection controls to identify, implement and manage secure and compliant practices, covering an organization’s people, processes, technology and data, regardless of how or where data is stored, processed and/or transmitted._”
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity and privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of **[Cybersecurity Supply Chain Risk Management (C-SCRM)](https://complianceforge.com/cybersecurity-supply-chain-risk-management/)**.
[](https://complianceforge.com/content/pdf/complianceforge-integrated-controls-management.pdf "ICM Overview")
## GRC Is a Plan, Do, Check & Act (PDCA) Adventure!
GRC most often deals with legally-binding requirements, so it is important to understand that negligence is situationally-dependent. For example, an intoxicated driver who gets behind the wheel acting negligently. However, when sober, that same individual is a champion race car driver who is highly-skilled and would not be considered incompetent in any regard. In this example, driving intoxicated constitutes a negligent act and shows that negligence has nothing to do with being incompetent. The point is to demonstrate that an organization can employ many highly-competent personnel, but even competent people can behave in a negligent manner. GRC fundamentally exists to help an organization avoid circumstances that could be construed as negligent acts.
Considering how business practices continuously evolve, so must cybersecurity practices. The Plan, Do, Check & Act ( **PDCA**) process enables the GRC function to continuously evaluate risks, threats and performance trends, so that the organization's leadership can take the necessary steps to minimize risk by modifying how people, processes and technology work together to keep everything both secure and operational. The PDCA approach (also referred to as the Deming Cycle) is a logical way to conceptualize how GRC works:
- **Plan**. The overall GRC process beings with planning. This planning will define the policies, standards and controls for the organization. It will also directly influence the tools and services that an organization purchases, since technology purchases should address needs that are defined by policies and standards.
- **Do**. Arguably, this is the most important section for cybersecurity and privacy practitioners. Controls are the “security glue” that make processes, applications, systems and services secure. Procedures (also referred to as control activities) are the processes how the controls are actually implemented and performed. The [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework") can be an excellent starting point for a control set if your organization lacks a comprehensive set of cybersecurity and privacy controls.
- **Check**. In simple terms, this is situational awareness. Situational awareness is only achieved through reporting through metrics and reviewing the results of audits/assessment.
- **Act**. This is essentially risk management, which is an encompassing area that deals with addressing two main concepts (1) real deficiencies that currently exist and (2) possible threats to the organization.
## GRC Always Begins With Defining What It Means To Be “Secure & Compliant”
Unlike GRC/IRM, ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, ICM helps an organization categorize its applicable controls according to “must have” vs “nice to have” requirements:
- **Minimum Compliance Requirements (MCR)** are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- **Discretionary Security Requirements (DSR)** are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.
Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.

## Integrated Controls Management Utilizes A Principles-Based Approach To Operationalizing The Model
There are eight (8) principles associated with ICM:
1. Establish Context
2. Define Applicable Controls
3. Assign Maturity-Based Criteria
4. Publish Policies, Standards & Procedures
5. Assign Stakeholder Accountability
6. Maintain Situational Awareness
7. Manage Risk
8. Evolve Processes
ComplianceForge has simplified the concept of "how to GRC" in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
**Integrated Controls Management (ICM) – Overlaid On Integrated Cybersecurity Governance Model (ICGM)**
[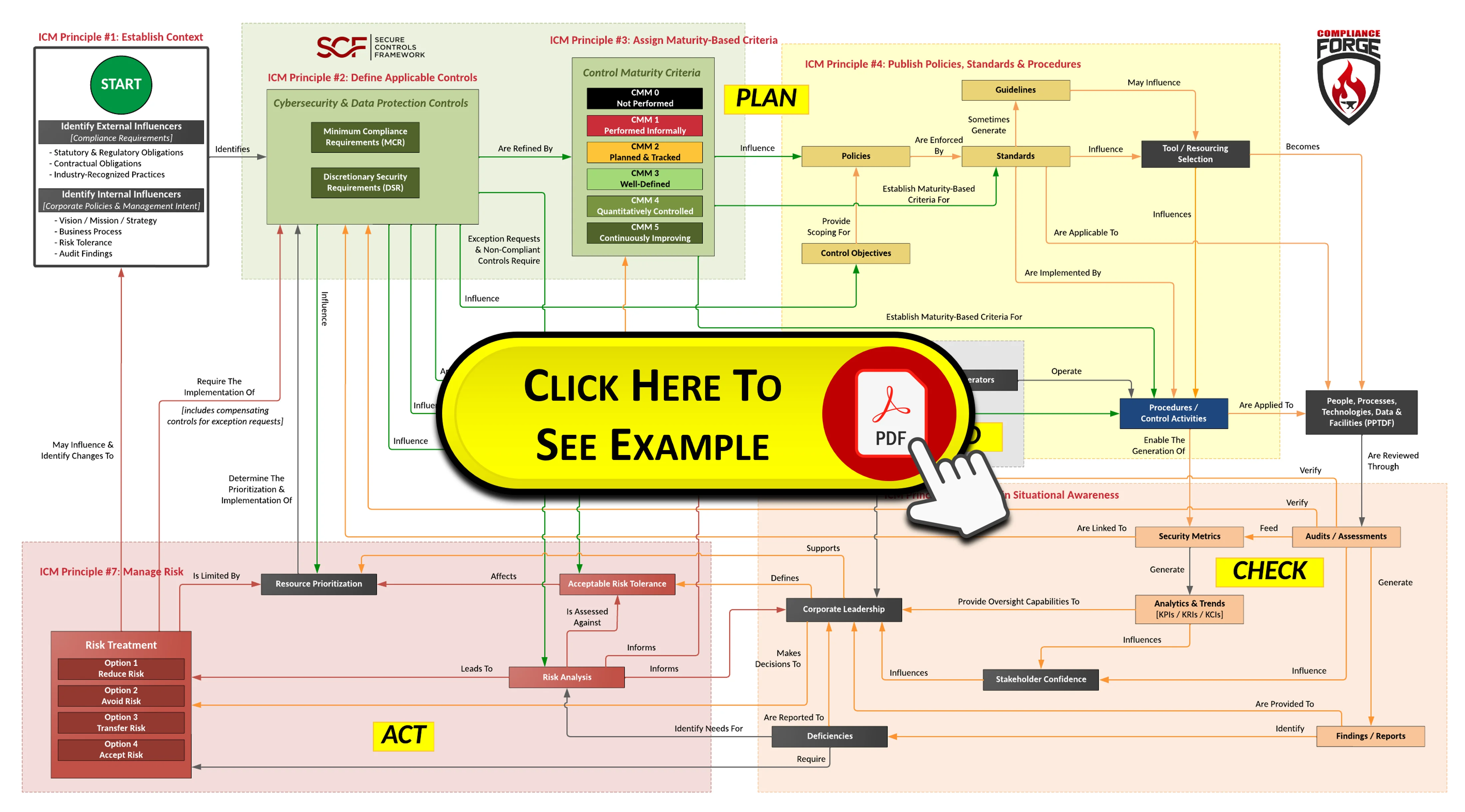](https://complianceforge.com/content/pdf/complianceforge-icm-plan-do-check-act.pdf "integrated controls management - plan do check act")
### Principle 1: Establish Context
To build and maintain efficient and effective operations, a cybersecurity & privacy program must have a hierarchical vision, mission and strategy that directly supports the organization’s broader strategic objectives and business processes. This process of establishing context involves identifying all applicable external compliance requirements (e.g., laws, regulations and contractual obligations), as well as internal directives (e.g., Board of Directors, corporate policies, etc.). This is a due diligence element of the cybersecurity and privacy program.

### Principle 2: Define Applicable Controls
A tailored control set cybersecurity and data protection controls must exist. This control set needs to be made of Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR). This blend of “must have” and “nice to have” requirements establish an organization’s tailored control set to ensure both secure practices and compliance.
### Principle 3: Assign Maturity-Based Criteria
The cybersecurity & privacy program must assign maturity targets to define organization-specific “what right looks like” for controls. This establishes attainable criteria for people, processes and technology requirements. Tailored maturity level criteria can be used to plan for, budget for and assess against. Maturity targets should support the organization’s need for operational resiliency.
### Principle 4: Publish Policies, Standards & Procedures
Documentation must exist, otherwise an organization’s cybersecurity and data protection practices are unenforceable. Formalizing organization-specific requirements via policies and standards are necessary to operationalize controls. Stakeholders utilize those prescriptive requirements to develop Standardized Operating Procedures (SOP) that enable Individual Contributors (IC) to execute those controls. Policies, standards and procedures provides evidence of due diligence that the organization identified and implemented reasonable steps to address its applicable requirements.
### Principle 5: Assign Stakeholder Accountability
Controls must be assigned to stakeholders to ensure accountability (e.g., business units, teams and/or individuals). These “control owners” may assign the task of executing controls to “control operators” at the IC-level. The documented execution of procedures provides evidence of due care that reasonable practices are being performed.
### Principle 6: Maintain Situational Awareness
Situational awareness must involve more than merely “monitoring controls” (e.g., metrics). While metrics are a point-in-time snapshot into discrete controls’ performance, the broader view of metrics leads to a longer-term trend analysis. When properly tied in with current risk, threat and vulnerability information, this insight provides “situational awareness” that is necessary for organizational leadership to adjust plans to operate within the organization’s risk threshold.
### Principle 7: Manage Risk
Proactive risk management processes must exist across all phases of development/information/system life cycles to address confidentiality, integrity, availability and safety aspects. Risk management must address internal and external factors, including privacy and Supply Chain Risk Management (SCRM) considerations. To manage risk, it requires the organization to clearly define its risk threshold and risk management expectations.
### Principle 8: Evolve Processes
Cybersecurity and data protection measures must adapt and evolve to address business operations and the evolving threat landscape. This requires the adoption of a Plan, Do, Check & Act (PDCA) approach (Deming Cycle) to ensure the organization proactively identifies its requirements, implements appropriate protections, maintains situational awareness to detect incidents, operates a viable capability to respond to incidents and can sustain key business operations, if an incident occurs.
## Chicken vs Egg Debate: The Logical Order of GRC Functions
**Which comes first?** Governance, Risk or Compliance? This has been a hotly-debated topic since GRC was first coined [nearly 20 years ago](https://www.oceg.org/about/what-is-grc/). There is a logical order to GRC processes that has to be understood to avoid siloes and an improperly scoped security program. First off, it is necessary to level-set on the terminology of what GRC functions do:
- Governance. Structures the organization’s controls to align with business goals and applicable statutory, regulatory, contractual and other obligations. Develops necessary policies and standards to ensure the proper implementation of controls.
- Risk Management. Identifies, quantifies and manages risk to information and technology assets, based on the organization’s operating model.
- Compliance. Oversight of control implementation to ensure the organization’s applicable statutory, regulatory, contractual and other obligations are adequately met. Conducts control validation testing and audits/assessments.
When establishing GRC practices, what is described below is the precedence of how (1) compliance influences (2) governance, which influences (3) risk management. This addresses the "GRC chicken vs egg" debate.
### Compliance
The genesis of GRC is to first identify applicable [statutory, regulatory and contractual obligations](https://complianceforge.com/free-guides/statutory-vs-regulatory-vs-contractual-compliance) that the organization must adhere to, as well as internal business requirements (e.g., Board of Director directives). This is a compliance function that identifies statutory, regulatory and contractual obligations. It is a due diligence exercise to identify what the organization is reasonably required to comply with from a cybersecurity and data protection perspective. This process involves interfacing with various Lines of Business ( **LOB**) to understand how the organization operates, including geographic considerations. Generally, Compliance needs to work with the legal department, contracts management, physical security and other teams to gain a comprehensive understanding of compliance needs.
Compliance is the “source of truth” for statutory, regulatory and contractual obligations. With that knowledge, Compliance informs Governance about the controls that apply to applicable laws, regulations and frameworks, so that Governance can determine the appropriate policies and standards that must exist. Compliance may identify requirements to adhere to a specific industry framework (e.g., [NIST CSF](https://complianceforge.com/solutions/nist-csf), [ISO 27002](https://complianceforge.com/solutions/iso-27001-27002), [NIST 800-53](https://complianceforge.com/solutions/nist-sp-800-53-r5-moderate), etc.), but organizations are usually able to pick the framework that best fits their needs on their own. This is often where various compliance obligations exceeds what a single framework can address, so the organization has to leverage some form of [metaframework](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/) (e.g., framework of frameworks).
Compliance defines the controls necessary to meet the organization’s specific needs (e.g., MCR + DSR) and publishes one or more control sets (e.g., specific to a project/contract/law/regulation or organization-wide controls). This control set(s) can be considered an organization's Minimum Security Requirements ( **MSR**) that will be used:
- By the Governance team to develop appropriate policies, standards and other information (e.g., program-level guidance, [CONOPS documents](https://complianceforge.com/free-guides/cybersecurity-conops), etc.; and
- By the Risk Management team to assess risk.
Since not all controls are weighted equally, it is vitally important that personnel who represent the Risk Management function are involved in developing an assigned weight for each control (e.g., the presence of a fully-patched border firewall should be considered a more important control than end user awareness posters). This weighting of cybersecurity and data protection controls is necessary to ensure the results of risk assessments accurate support the intent of the organization's risk tolerance threshold. That threshold is meant to establish a benchmark for defining acceptable and unacceptable risk.
### Governance
Based on these controls, Governance has a few key functions:
- Develop policies and standards to meet those compliance obligations (defined by applicable control objectives); and
- Assign ownership of those controls to the applicable stakeholders involved in the affected business processes. This process often requires a documented Responsibility, Accountability, Supportive, Consulted, and Informed **(RASCI)** chart to ensure the organizational model supports effective implementation and oversight of the assigned controls.
Personnel representing the Governance function must work directly with the stakeholders (e.g., control owners and control operators) who are directly responsible for implementing and operating their assigned cybersecurity and data protection controls. Those stakeholders are expected to develop and operate Standardized Operating Procedures ( **SOP**) to ensure control implementation is performed according to the company’s performance requirements, as established in the organization’s cybersecurity and data protection standards. The operation of those SOPs generates evidence of due care that reasonable practices are in place and operating accordingly. Generating deliverables is an expected output from executing procedures.
The development and implementation of the policies and standards is evidence of due diligence that the organization's compliance obligations are designed to address applicable administrative, technical and physical security controls. It is important to ensure that policies and standards document what the organization is doing, as the policies and standards are often the mechanisms by which outside regulators measure implementation and maturity of the control. [Cybersecurity and data protection documentation](https://complianceforge.com/example-cybersecurity-documentation) is generally comprised of six (6) main parts:
1. Policies establish management’s intent;
2. Control Objectives identify leading practices (mapped to requirements from laws, regulations and frameworks);
3. Standards provide quantifiable requirements;
4. Controls identify desired conditions that are expected to be met (requirements from laws, regulations and frameworks);
5. Procedures / Control Activities establish how tasks are performed to meet the requirements established in standards and to meet controls; and
6. Guidelines are recommended, but not mandatory.

### Risk Management
From a trickle-down perspective, while Risk Management logically follows both Compliance and Governance functions in establishing a GRC program, Risk Management is crucial for the organization to maintain situational awareness and remain both secure and compliant. Risk Management serves as the primary "canary in the coal mine" to identify instances of non-compliance that lead to the improper management of risks and exposure of the organization to threats, since ongoing risk assessments generally occur more frequently than internal/external audits that Compliance may oversee.
Risk Management activities addresses both due diligence and due care obligations to identify, assess and remediate control deficiencies:
- Risk Management must align with Governance practices for exception management (e.g., compensating controls).
- Compliance must evaluate findings from risk assessments and audits/assessments (both internal and external) to determine if adjustments to the organization’s cybersecurity and data protection controls (e.g., MCR + DSR) are necessary, based on business process changes, technology advancements and/or an evolution of the organization's risk threshold.
While Risk Management personnel do not perform the actual remediation actions (that is the responsibility of the control owner), Risk Management assists in determining the appropriate risk treatment options:
- Reduce the risk to an acceptable level;
- Avoid the risk;
- Transfer the risk to another party; or
- Accept the risk.
One key consideration for GRC, especially Risk Management, is that the appropriate level of organizational management makes the risk management decision. This is why risks need to be ranked, so that the appropriate levels of management can be designated as "approved authorities" to make a risk treatment determination. For example, a project manager should not be able to accept a "high risk" that should be made by a VP or some other executive. By formally-assigning risk to individuals and requiring those in managerial roles to own their risk management decisions, it can help the organization maintain its target risk threshold.
These GRC processes can be visualized in the diagram shown below that depicts the interrelated nature of GRC functions (click on image for a PDF):
[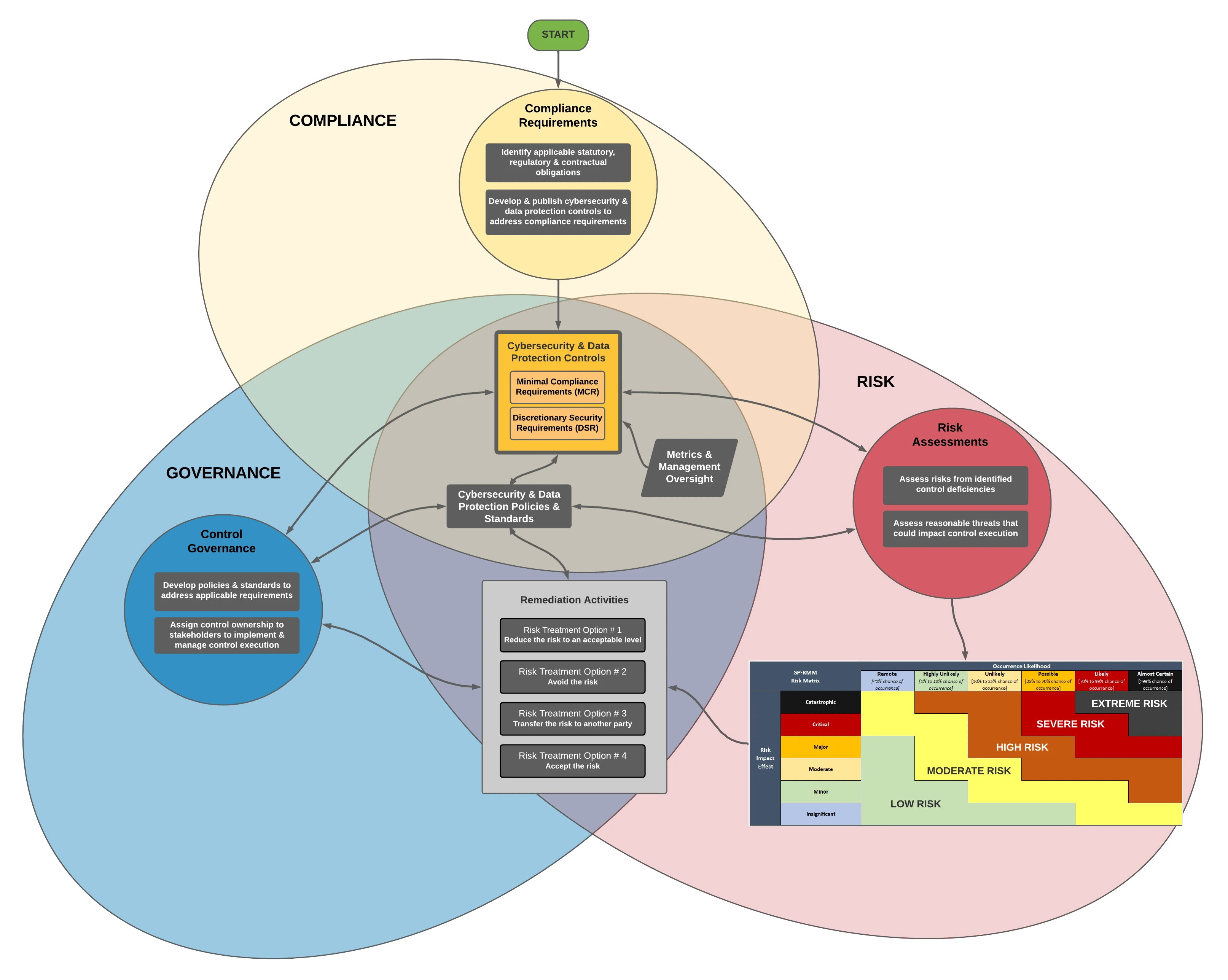](https://complianceforge.com/content/pdf/grc-fundamentals.pdf "what is governance risk and compliance | grc fundamentals")
## If GRC Is Not Documented, It Doesn’t Exist
Once a GRC program is implemented, it requires regular and on-going reassessment of Governance, Risk Management and Compliance activities to maintain both an appropriate balance between these processes and effective operations. Similar to a three-legged stool, if one leg is too short or too long, the program will be unbalanced, wobble and not operate as needed. However, the greatest threat to GRC is organizational leadership, since it requires strong and active support of senior leaders to ensure secure and compliant practices are implemented and maintained. This is where there are some positive and negative aspects to documentation, depending on what side of the argument choose to defend. In reality, documentation is neither "good" nor "bad" since it merely exists to tell a story. However, you can see below how certain stakeholders could think documentations is "good" or "bad" based on their position:
- The ”bad” part of documenting GRC practices, is that it is not at all uncommon to hear of situations where cybersecurity practitioners are instructed to leave things off risk registers, not put things in email for fear of eDiscovery, etc. Foremost, that is an abysmal failure in leadership that should either be reported or you should seriously consider changing employment, since that type of shadow governance is both unethical and will lead to root issues never being resolved. GRC exists to “fix the puzzle” so deficiencies must be documented in order for the appropriate management function to evaluate the risk and determine the appropriate next steps. If you fail to do that harder right, then you are part of the problem.
- The ”good” part of documenting GRC practices is having appropriate evidence of due diligence and due care. This can be your “get out of jail free card” if an incident occurs and fingers get pointed for where blame should be assigned. GRC should never “own” risk, since when GRC is properly implemented, the Governance function identifies and assigns control ownership to the appropriate stakeholders. By documenting findings and elevating risk management decisions to the appropriate level, you are part of the solution and are fulfilling the intent of what you are paid to accomplish.
## Garbage In = Garbage Out (GIGO)
There are a lot of wonderful tools to help automate GRC functions, but it is immensely important to understand that GRC itself is a process. You cannot reasonably expect a GRC solution to dictate what your processes are going to be – those tools exist to automate your existing processes, so if you have bad processes today, automating that will only makes those bad practices faster. This is the “garbage in = garbage out” issue that plagues many GRC implementations.
GIGO is especially true with Risk Management. This often exists in GRC tools, but it is especially true for those using Commercial Off The Shelf ( **COTS**) risk management tools. The reason for this is the risk catalog in COTS tools often have little to no tie-in to the organization’s actual cybersecurity and privacy controls, let alone its policies and standards. This often leads to Risk Management teams "going rogue" making up their own risks that have no legitimate tie in - it just looks impressive and analysts are kept busy. This is where removing siloes and avoiding working in a vacuum is critical, since Risk Management decisions must be directly tied to controls. For example, an organization that is basely implementing policies and standards to align with the NIST Cybersecurity Framework (NIST CSF) that has a vendor risk questionnaire that far exceeds NIST CSF by a few hundred controls. If the risk questions are appropriate, that could indicate that Compliance is incorrect with its assessment of needs for security and privacy controls. However, we most often see this with Risk Management teams going rogue and simply making things up, since it makes an impressive list of risk questions to ask vendors.
## GRC Is A Puzzle So Please Be Part of The Solution
Ask yourself one question: **_If there was a major data breach today and all eyes focused on your company, when the dust settles and root causes are investigated, would your company’s leadership and its technology stakeholders be considered negligent for failing to implement “reasonable” security and privacy practices?_** Now, as a GRC professional, look at your specific role and the responsibilities you have for helping keep data and technology secure. Are you part of the solution or the problem?
We want to help you be part of the solution! [Contact us](https://complianceforge.com/contact-us/) if you have any GRC-related questions that we can help answer?
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/scf-dsp-procedures-csop/)
#### [Procedures Template - DSP / SCF](https://complianceforge.com/product/scf-dsp-procedures-csop/)
Secure Controls Framework (SCF)
Cybersecurity Standardized Operating Procedures (CSOP) DSP \| SCF Version
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$6,400.00 - $11,200.00
[Choose Options](https://complianceforge.com/product/scf-dsp-procedures-csop/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
organization, productivity, risk, policy, risk management, regulatory compliance, governance, audit, risk assessment, security information and event management, internal audit, internal control, governance risk and compliance, strategy, regulation, hazard, servicenow, cloud computing, automation, stakeholder, strategic management, chief information officer, mitigation, analytics, corporate governance, operational risk, accounting, law, information security, workflow, ethics, cyberattack, transparency, uncertainty, general data protection regulation, committee of sponsoring organizations of the treadway commission, visibility, openpages, intelligence, vulnerability, culture, leadership, system, efficiency, enterprise risk management, landscape, it risk management, operational risk management, asset, discipline, integrity, usability, financial risk, data security, safety, evaluation, collaboration, reputation, risk appetite, data breach, national institute of standards and technology, occupational safety and health, complexity, corporate social responsibility, international organization for standardization, grc market, grc solution, grc strategy, grc capability model, enterprise grc, grc program, grc tool, diligent grc, grc cyber security, risk and compliance software, servicenow grc module, grc risk management, grc compliance software, oracle grc, grc in cyber security, grc service now, grc services, implementation, return on investment, business continuity planning, chief risk officer, chief compliance officer, adoption, adherence, document, single source of truth, board of directors, change management, concept, infrastructure, gartner, user experience, organizational culture, effectiveness, resource, corporation, chief executive officer, supply chain, accessibility, server, payment card industry data security standard, data management, research, data collection, understanding, ownership, confidence, cobit, nist cybersecurity framework, interface, appetite, measurement, knowledge, certification, isaca, grc platform, grc software, grc tools, expense, chief financial officer, customer, sustainability, user, simulation, business process, it risk, scalability, behavior, natural disaster, audit trail, truth, reputational damage, code of conduct, curve, resource management, fraud, scenario planning, value, grc policies, grc technology, it service management, operational efficiency, data center, natural language processing, machine learning, internet of things, benchmarking, innovation, energy, failure, outsourcing, vendor, contract, grc software solution, servicenow grc, best grc tools, metricstream grc, compliance manager grc, training, climate, iso 31000, data analysis, climate change, machine, cyber resilience, methodology, data governance
governance risk and compliance, grc governance risk compliance, governance risk compliance, grc compliance, governance risk and compliance framework, grc framework
## Continuity of Operations Plan
[Skip to main content](https://complianceforge.com/product/continuity-of-operations-plan/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/172/1541/complianceforge-continuity-of-operations-plan-coop__99813.1740599339.jpg?c=2)
No reviews yet
$4,235.00
(You save)
# Continuity of Operations Plan (COOP)
SKU:P14-COOP-NOUPC:692878856942Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Editable%20COOP%20Template%20for%20Business%20Continuity%20Planning&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcontinuity-of-operations-plan%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcontinuity-of-operations-plan%2F&title=Editable%20COOP%20Template%20for%20Business%20Continuity%20Planning&summary=Editable%20COOP%20Template%20for%20Business%20Continuity%20Planning&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcontinuity-of-operations-plan%2F "Linkedin")

[](https://complianceforge.com/product/continuity-of-operations-plan/#coop-example)
## Continuity of Operations Plan (COOP) - Disaster Recovery & Business Continuity
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the COOP is to help answer common questions we receive.
[](https://complianceforge.com/continuity-of-operations-video/ "Watch COOP Video")
[View Product Video](https://complianceforge.com/continuity-of-operations-video/)
## What Is The Continuity of Operations Plan (COOP)?
Is your organization looking for a Continuity Of Operations Plan template? The COOP is designed to provide a holistic approach to both disaster recovery and business continuity. Our COOP template address (1) pre-disaster preparedness, (2) disaster recovery operations, (3) business continuity operations and (4) post-disaster activities.
- The COOP addresses the “how?” questions in an audit, since BC/DR guidance provides the means for how your organization's BC/DR-related policies and standards are actually implemented.
- The COOP provides the underlying BC/DR guidance that must be documented, as many stipulated by statutory, regulatory and contractual requirements.
## What Problems Does The COOP Solve?
- Lack of In House Security Experience - Writing disaster recovery / business continuity documentations is a skill that most cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive BC/DR documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The COOP is an efficient method to obtain comprehensive business continuity and disaster recovery documentation for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented disaster recovery and business continuity processes. The COOP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements (see bottom of page for a complete listing).
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The COOP provides a cost-effective and efficient manner to obtain BC/DR documentation.
- Vendor Requirements - It is very common for clients and partners to request evidence of a disaster recovery and business continuity capabilities. The COOP can provide evidence that you need!
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The COOP is in an editable Microsoft Word format.
## How Does The COOP Solve These Problems?
- Clear Documentation - The COOP provides a comprehensive template for your BC/DR operations to help prove that your recovery capabilities exist. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The COOP can provide your organization with a templated solution that requires minimal resources to fine tune for your organization's specific BC/DR needs.
- Alignment With Leading Practices - The COOP is written based on leading frameworks for BC/DR guidance.
The COOP takes a holistic approach to Business Continuity / Disaster Recovery (BC/DR) that utilizes a phased approach to preparing for and responding to incidents. It takes a phased approach incorporates incident response and BC/DR components to create a centralized and strategic approach to emergency management that can scale to deal with the size and scope of disasters and recovery efforts.

- Phase 1 – Prepare
- Phase 2 – React
- Phase 3 – Recover
- Phase 4 – Transition
- Phase 5 – Review & Improve
These phases overlap from incident response at a tactical level (IRPs and DRPs) to intermediate and long-term recovery efforts at a strategic level (BCPs):
- Incident Response Plans (IRPs)
- Disaster Recovery Plans (DRPs)
- Business Continuity Plans (BCPs)
The COOP can stand alone or be paired with other specialized products we offer. At the heart of it, the COOP provides an organization with clear disaster recovery and business continuity documentation that is cohesive and manageable.
The value of the COOP comes from having well-constructed documentation that establishes the clear requirements to protect your organization from disasters. The COOP can help you become audit ready in a fraction of the time and cost to do it yourself or hire a consultant to come on-site and write it for you. The entire concept of this COOP is focused on two things:
1. Providing written BC/DR documentation to walk your team members through the steps they need to plan for, respond to and recover from disasters; and
2. Help your company be audit ready with the appropriate level of due diligence evidence that allows you to demonstrate your organization meets its obligations.

## Product Example - Continuity of Operations Plan (COOP)
The COOP addresses program-level guidance on HOW to actually plan for and respond to both business continuity and disaster recovery (BC/DR) operations. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW BC/DR is actually planned and managed. The COOP provides this middle ground between high-level policies and the actual procedures of how BC/DR is executed by those individual contributors task with BC/DR duties. The COOP comes with a wealth of guidance, including scenario-based guidance, an After Action Review (AAR) template, Lines of Business (LOB) reconstitution steps and more!
**View Product Examples**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-coop-continuity-of-operations-program.pdf "example continuity of operations plan - business continuity plan - disaster recovery plan") |
## Cost Savings Estimate - Continuity of Operations Plan (COOP) Template
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the COOP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 200 internal staff work hours, which equates to a cost of approximately **$18,000** in staff-related expenses. This is about 3-6 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 120 consultant work hours, which equates to a cost of approximately **$39,000**. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- The COOP is approximately 11% of the cost for a consultant or 24% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the COOP the same day you place your order.
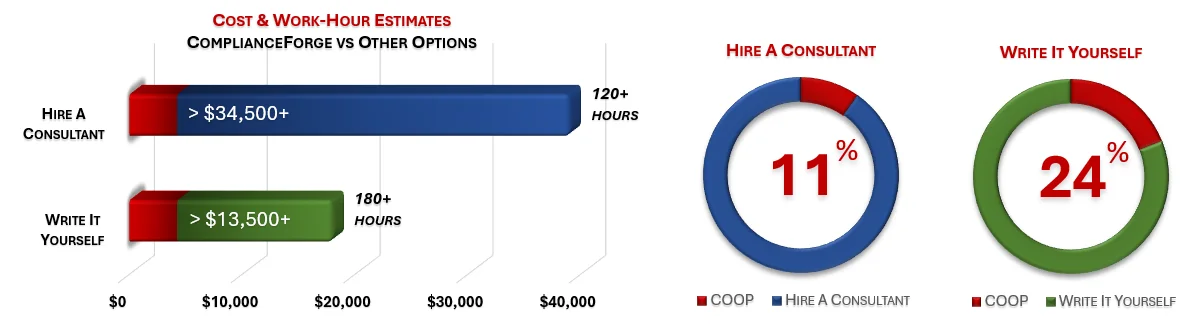
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Comprehensive Documentation To Address Contingency Operations

## Best Practices For The COOP
We developed the COOP based on the following leading practices:
- The National Institute of Standards and Technology (NIST):
- NIST 800-34: Contingency Planning Guide for Federal Information Systems
- NIST 800-37: Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach
- NIST 800-39: Managing Cybersecurity Risk: Organization, Mission and Information System View
- NIST 800-50: Building An Information Technology Security Awareness and Training Program
- NIST 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
- NIST 800-84: Guide To Test, Training and Exercise Programs for IT Plans and Capabilities
- NIST 800-171: Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations
- NIST 800-181: National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework
- NIST IR 7298: Glossary of Key Cybersecurity Terms
- NIST IR 8179: Criticality Analysis Process Model: Prioritizing Systems and Components \[draft\]
- NIST Framework for Improving Critical Cybersecurity (Cybersecurity Framework)
- The International Organization for Standardization (ISO):
- ISO 15288: Systems and Software Engineering -- System Life Cycle Processes
- ISO 22301: Societal Security – Business Continuity Management Systems – Requirements
- ISO 27002: Information Technology -- Security Techniques -- Code of Practice for Cybersecurity Controls
- Other Frameworks:
- Federal Emergency Management Agency Incident Command System (FEMA ICS)
- FEMA Natural Disaster Recovery Framework (FEMA NDRF)
- FEMA National Response Framework (FEMA NRF)
- Cloud Security Alliance Cloud Controls Matrix (CSA CCM)
- Center for Internet Security Critical Security Controls (CIS CSC)
- Control Objectives for Information and Related Technologies (COBIT)
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
- European Union Regulation 2016/279 (General Data Protection Regulation (EU GDPR))
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=1jiqd7lhe0fe)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
continuity of operations, continuity of operations solutions, continuity of operations plan template, continuity of operations planning, continuity of operations plan for business, continuity of operations software
## DSP Version 2022.3 Release
[Skip to main content](https://complianceforge.com/blog/dsp-version-20223-release/#main-content)
[](https://complianceforge.com/blog/dsp-version-20223-release/)
ComplianceForge is pleased to announce the release of version 2022.3 of the Digital Security Program (DSP). There is some new content and minor refinement of the risk catalog to standardize wording improve readability and it also includes a new Evidence Request List (ERL) to help standardize naming for evidence artifacts. The DSP contains 1-1 mapping to the Secure Controls Framework (SCF) so you can have policies, control objectives, standards and more to support your implementation of the SCF!
New mapping in this version includes:
- Australian Government Information Security Manual (ISM) September 2022
- BSI Standard 200-1
- California Privacy Rights Act (CPRA) - November 2022 version
- Cybersecurity Capability Maturity Model (C2M2) v2.1
- Illinois Biometric Information Privacy Act (PIPA)
- Illinois Identity Protection Act (IPA)
- ISO 27017:2015
- ISO 27001:2022
- Japan Information System Security Management and Assessment Program (ISMAP)
- New Zealand NZISM 3.6
- Shared Assessments SIG 2023
- US Centers for Medicare & Medicaid Services MARS-E Document Suite, Version 2.0.
Learn more about this premium GRC content at [https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/)
- [#Digital Security Program](https://complianceforge.com/blog/tag/Digital+Security+Program)
- [#DSP](https://complianceforge.com/blog/tag/DSP)
- [#SCF](https://complianceforge.com/blog/tag/SCF)
- [#Secure Controls Framework](https://complianceforge.com/blog/tag/Secure+Controls+Framework)
- [Email](mailto:?subject=DSP%20version%202022.3%20release%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fdsp-version-20223-release%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fdsp-version-20223-release%2F&title=DSP%20version%202022.3%20release%20-%20ComplianceForge&summary=DSP%20version%202022.3%20release%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fdsp-version-20223-release%2F "Linkedin")
Request Quote
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## C-SCRM Bundle 1
[Skip to main content](https://complianceforge.com/bundle/c-scrm-bundle-1/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/323/1486/C-SCRM_Bundle_1__62886.1740598596.png?c=2)
No reviews yet
$39,720.00
$39,720.00
$23,832.00
(You save$15,888.00)
# C-SCRM Bundle 1: CDPP version (ISO or NIST alignment)
SKU:C-SCRM-B1UPC:692878857093Availability:Email Delivery Within 1-2 Business Days
Framework Version:
(Required)
NIST CSFISO 27001/27002NIST SP 800-53 R5
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=C-SCRM%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&body=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-1%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-1%2F&title=C-SCRM%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&summary=C-SCRM%20Bundle%201%3A%20CDPP%20version%20(ISO%20or%20NIST%20alignment)&source=https%3A%2F%2Fcomplianceforge.com%2Fbundle%2Fc-scrm-bundle-1%2F "Linkedin")

## Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle \#1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk Management (C-SCRM):
01. Cybersecurity & Data Protection Program (CDPP) - [NIST CSF](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/ "NIST CSF Policies"), [ISO 27001/2](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/ "ISO 27001 / 2 Policies") or [NIST 800-53 R5 Moderate](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-53 R5 Moderate Policies")
02. Cybersecurity Standardized Operating Procedures (CSOP) - [NIST CSF](https://complianceforge.com/product/nist-csf-procedures-csop/ "NIST CSF Procedures"), [ISO 27001/2](https://complianceforge.com/product/iso-27002-procedures-csop/ "ISO 27001 / 2 Procedures") or [NIST 800-53 R5 Moderate](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/ "NIST 800-53 R5 Moderate Procedures")
03. [NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan)
04. [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
05. [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/)
06. [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
07. [Integrated Incident Response Program (IIRP)](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/)
08. [Continuity of Operations Plan (COOP)](https://complianceforge.com/product/continuity-of-operations-plan/)
09. [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
10. [Information Assurance Program (IAP)](https://complianceforge.com/product/control-validation-testing-information-assurance-template)
11. [Secure Engineering & Data Privacy (SEDP)](https://complianceforge.com/product/security-by-design-privacy-by-design/)
12. [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
13. [Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")
## NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
ComplianceForge developed an editable template for a C-SCRM Strategy and Implementation Plan (SIP). This is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the ground running" with C-SCRM operations that are aligned with **NIST SP 800-161 Rev 1**, which is the current "gold standard" for authoritative C-SCRM guidance.
The reality is organizations depend on a global supply chain to provide a variety of products and services that enable the achievement of its strategic and operational objectives. Given the global scope of identifying cybersecurity and data protection risks, threats and vulnerabilities throughout the supply chain are complicated due to the information asymmetry that exists between acquiring enterprises and their suppliers and service providers:
- Acquirers often lack visibility and understanding of how acquired technology is developed, integrated and deployed and how the services that they acquire are delivered.
- Acquirers with inadequate or absent C-SCRM processes, procedures and practices may experience increased exposure cybersecurity risks throughout the supply chain.
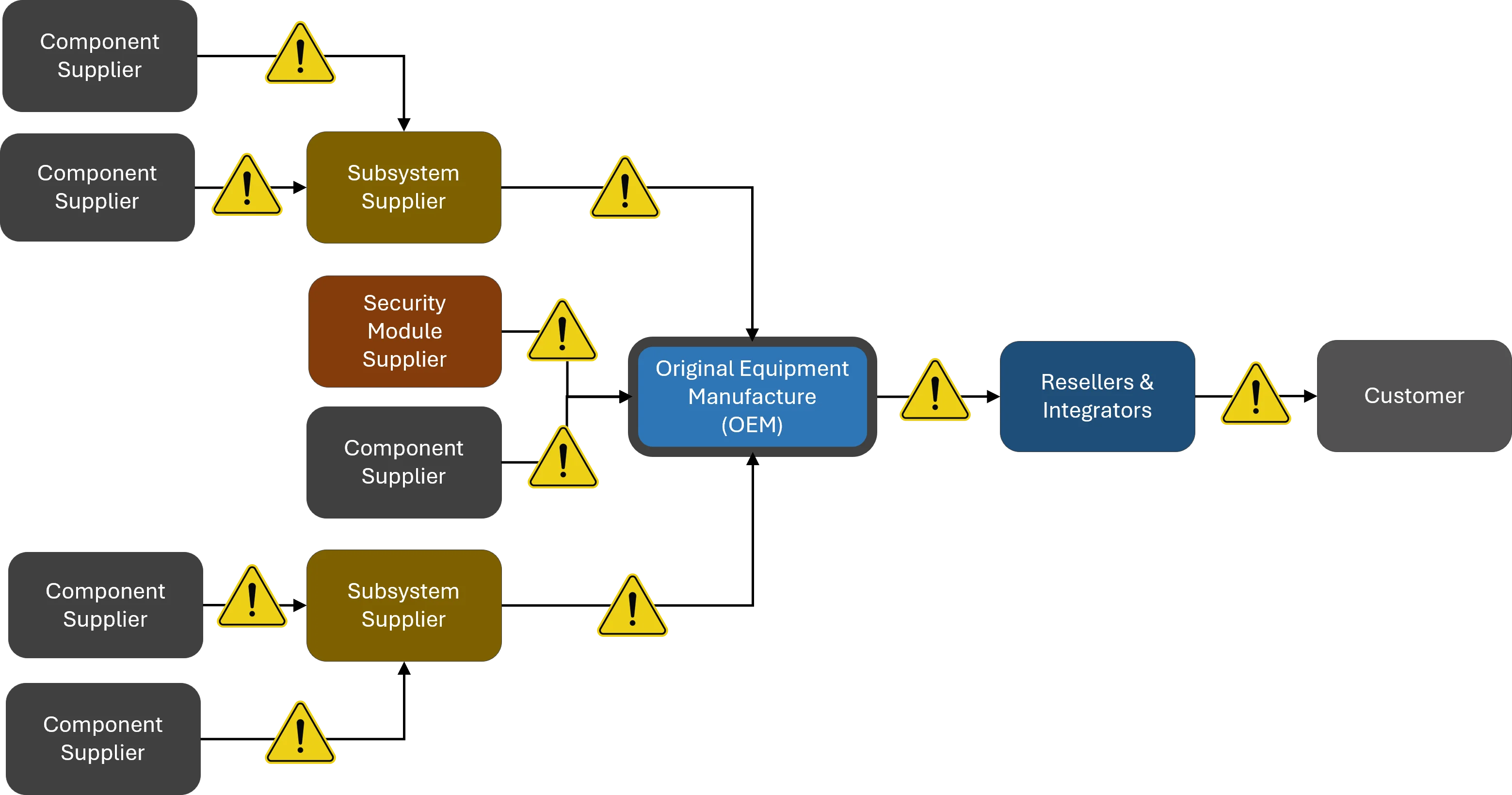
## Reducing Risk Is Central To Supply Chain Risk Management
Having a Supply Chain Risk Management (C-SCRM SIP) is focused on minimizing risk to your company, your partners and your customers. There is traditionally low level-risk (tactical) that is focused on weaknesses pertaining to routine systems and data. There is mid-level risk (operational) that is focused on weaknesses pertaining to business process. There is also high-level (strategic) risk that impacts at an organizational level. Having a secure vendor relationship can address risk at all three of these levels.
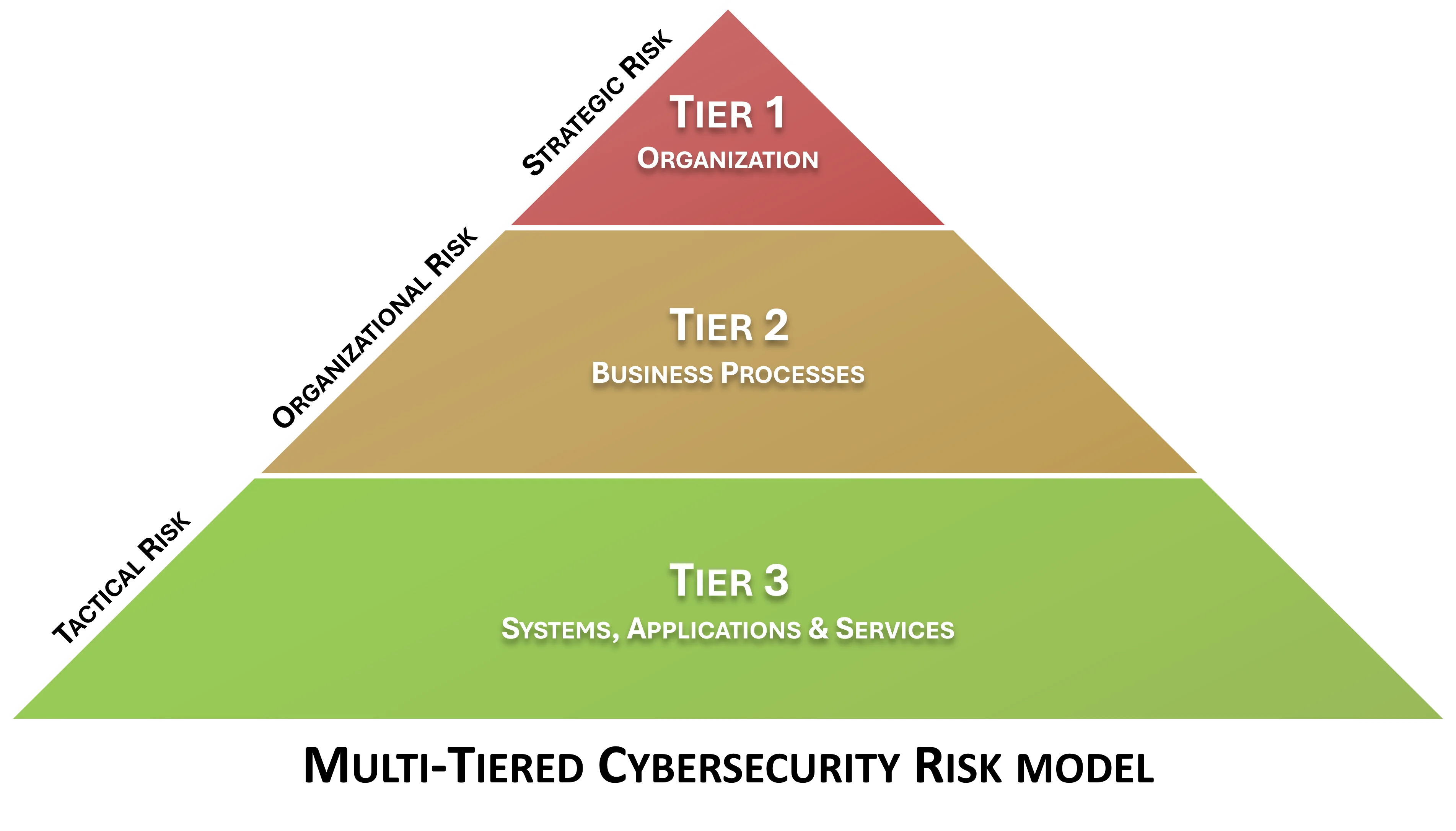
The **C-SCRM SIP** product is designed to implement a C-SCRM Program, as well as deliver an efficient and cost-effective method to develop a C-SCRM strategy and implement actionable steps to operationalize the C-SCRM strategy. Suppliers, Integrators and Service Providers ( **SISP**) are in scope for C-SCRM operations, where the term SISP includes Original Equipment Manufacturers ( **OEMs**), vendors, contractors, consultants and other entities that make up the supply chain. This scope of operations for the C-SCRM SIP includes all entities that:
- Transmit, process and/or store an organization's, or its clients’, data across the SISP's systems, applications and/or services;
- Manufacture products or product components used in an organization's operations and/or products; and/or
- Provide services for an organization's operations and/or service offerings.
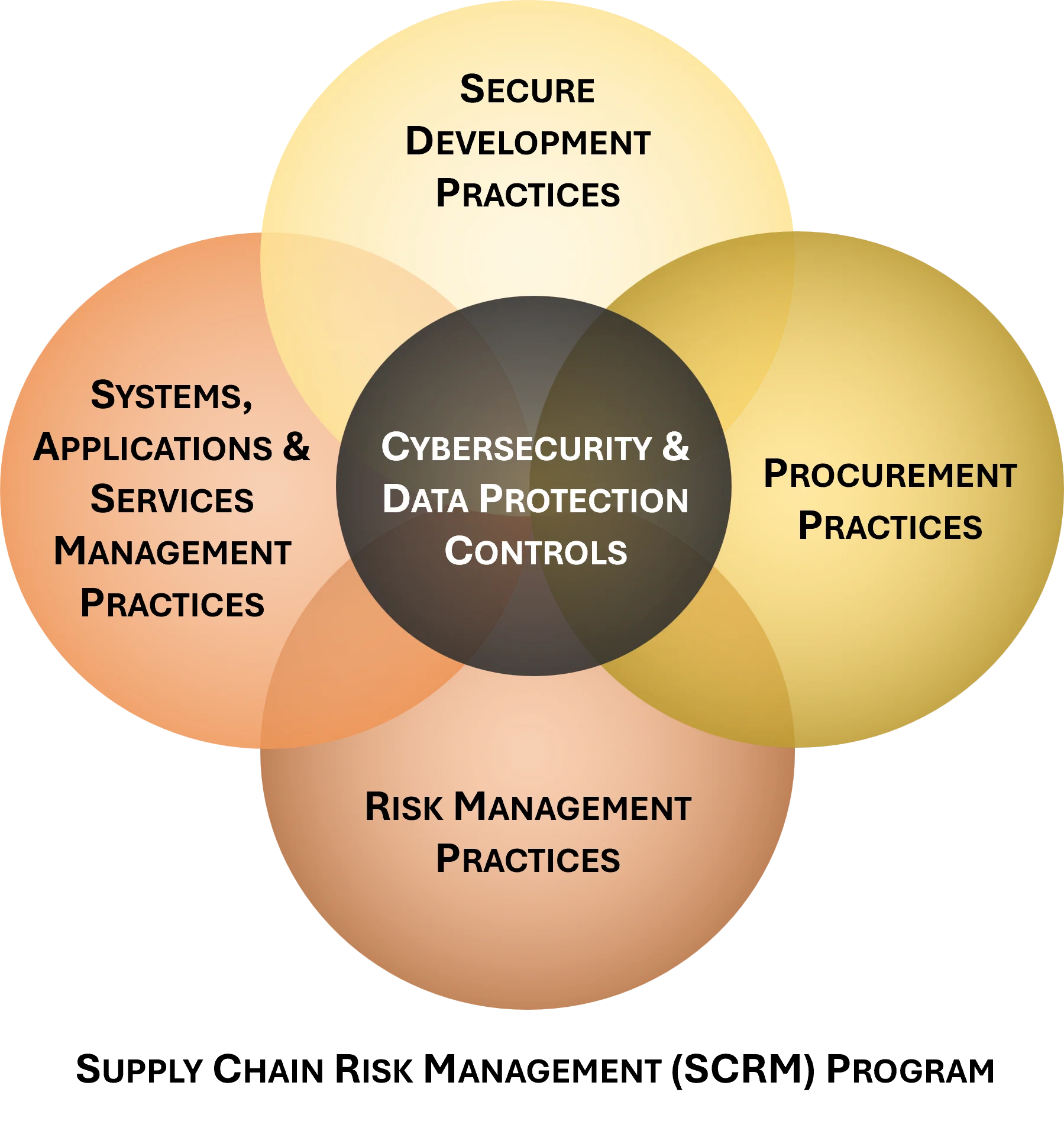
Product highlights of the C-SCRM SIP include:
- Country-based risk guidance to determine minimum management decision levels for conducting operations in or contracting with suppliers from countries that pose a legitimate C-SCRM threat.
- The prioritized implementation plan contains mappings for NIST SP 800-161 R1 controls to each C-SCRM implementation phase.
- Professionally-written, editable documentation template that leverages industry-recognized "best practices" for C-SCRM.
- Cost-effective solution to quickly generate documentation for a C-SCRM strategy and implementation plan.
- Example flow-down contract requirements for suppliers, vendors, subcontractors, etc. (DFARS/CMMC, ISO 27001, NIST CSF, NIST 800-53, FAR, PCI DSS, and EU GDPR/CCPA).
## NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
This bundle is designed for organizations that need to comply with the European Union General Data Protection Regulation (EU GDPR) and the pending California Consumer Privacy Act (CCPA). This is beyond just cybersecurity policies and standards and a standard SCRM plan. This is addresses the unique compliance needs for privacy and cybersecurity to manage risk in a coordinated effort. The end result is a comprehensive, customizable, easily implemented set of documentation that your company needs to establish a cybersecurity and privacy program. Being Microsoft Word and Excel documents, you have the ability to make edits, as needed. Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Cost Savings Estimate - C-SCRM Bundle \#1 (Cybersecurity & Data Protection Program (CDPP) version)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing this bundle from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 3,700 internal staff work hours, which equates to a cost of approximately **$369,000** in staff-related expenses. This is about 30-40 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 2,500 contractor work hours, which equates to a cost of approximately **$823,500**. This is about 18-30 months of development time for a contractor to provide you with the deliverable.
- This bundle is approximately 3% of the cost for a consultant or 6% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
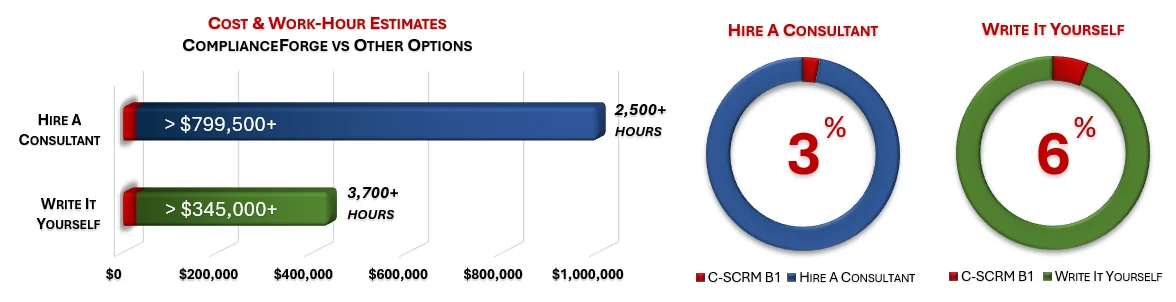
## Products Included in C-SCRM Bundle \#1 (CDPP version)
The Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle 1 uses the Cybersecurity & Data Protection Program (CDPP) and C-SCRM Bundle #2 uses the Digital Security Program (DSP). The DSP is targeted for larger, enterprise environments, but more differences between the CDPP and DSP can be read about [here](https://complianceforge.com/faq/dsp-vs-wisp). The CDPP comes in either NIST CSF, ISO 27001/2 or NIST 800-53 moderate.
| | |
| --- | --- |
|  | **[Cybersecurity & Data Protection Program (CDPP)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/ "NIST 800-53 CDPP LOW MODERATE HIGH BASELINES") (NIST CSF, ISO 27001 & 27002 or NIST SP 800-53 Moderate version)**
Framework-specific cybersecurity policies & standards in an editable Microsoft Word format.
- The CDPP addresses the “why?” and “what?” questions in an audit, since policies and standards form the foundation for your cybersecurity program.
- Under each of the policies are standards that support those policy statements.
- CDPP contains many useful supplemental documentation templates:
- Business Impact Analysis ( **BIA**) template
- Data classification & handling guidelines
- Data retention guidelines
- Rules of behavior (acceptable use)
- Risk management guidelines
- System hardening guidelines
- and more templates |
|  | **NIST SP 800-161 Rev 1-Based [Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/nist-800-161-cscrm-strategy-implementation-plan)**
The C-SCRM SIP is focused on helping companies manage their supply chain securely by establishing a C-SCRM Program that can operational a C-SCRM strategy through a viable C-SCRM implementation plan. This is important from an Executive Order (EO), Supply Chain Risk Management (SCRM), NIST SP 800-171 and CMMC perspective, due to the "flow down" of compliance requirements to service providers, contractors, suppliers, etc. The C-SCRM SIP is a way to help manage technology-related supply chain risk and inform organizations within the supply chain what their requirements are. |
|  | [**Cybersecurity Standardized Operating Procedures Template (CSOP) - CDPP version**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity procedures template NIST 800-53 NIST CSF ISO 27002")
The CDPP version of the CSOP is a template for procedures. This is an expectation that companies have to demonstrate HOW cybersecurity controls are actually implemented.
- This is an editable Microsoft Word document.
- Given the difficult nature of writing templated procedure statements, we aimed for approximately a "80% solution" since it is impossible write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who/what/when/where/why/how to make it complete.
- The CSOP is mapped to leading frameworks to help with mapping compliance requirements. |
|  | [**Integrated Incident Response Program (IIRP)**](https://complianceforge.com/product/cybersecurity-integrated-incident-response-program-iirp/ "Incident response plan template")
The IIRP addresses the “how?” questions for how your company manages cybersecurity incidents.
- This is primarily an editable Microsoft Word document, but it comes with Microsoft Excel and Microsoft Visio templates.
- In summary, this addresses fundamental needs when it comes to incident response requirements:
- Defines the hierarchical approach to handling incidents.
- Categorizes eleven different types of incidents and four different classifications of incident severity.
- Defines the phases of incident response operations, including deliverables expected for each phase.
- Defines the Integrated Security Incident Response Team ( **ISIRT**) to enable a unified approach to incident response operations.
- Defines the scientific method approach to incident response operations.
- Provides guidance on how to write up incident reports (e.g., lessons learned).
- Provides guidance on forensics evidence acquisition.
- Identifies and defines Indicators of Compromise ( **IoC**).
- Identifies and defines sources of evidence.
- The IIRP contains “tabletop exercise” scenarios, based on the categories of incidents.
- This helps provide evidence of due care in how your company handles cybersecurity incidents.
- The IIRP is based on industry-leading practices for incident response. |
|  | [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "risk management program template")
The RMP addresses the “how?” questions for how your company manages risk.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for managing cybersecurity risk.
- In summary, this addresses fundamental needs when it comes to risk management requirements:
- How risk is defined.
- Who can accept risk.
- How risk is calculated by defining potential impact and likelihood.
- Necessary steps to reduce risk.
- Risk considerations for vulnerability management.
- The RMP is based on leading frameworks, such as **NIST 800-37, NIST 800-39, ISO 31010** and **COSO 2013**. |
|  | [**Cybersecurity Risk Assessment (CRA) Template**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "cybersecurity risk assessment template")
The CRA supports the RMP product in answering the “how?” questions for how your company manages risk.
- This contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- The CRA directly supports the Risk Management Program (RMP), as well as the CDPP/DSP's policies and standards, for managing cybersecurity risk. It does this by enabling your company to produce risk assessment reports. |
|  | [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability patch management program")
The VPMP addresses the “how?” questions for how your company manages technical vulnerabilities and patch management operations.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for managing vulnerabilities.
- In summary, this addresses fundamental needs when it comes to vulnerability management requirements:
- Who is responsible for managing vulnerabilities.
- What is in scope for patching and vulnerability management.
- Defines the vulnerability management methodology.
- Defines timelines for conducting patch management operations.
- Considerations for assessing risk with vulnerability management.
- Vulnerability scanning and penetration testing guidance. |
|  | [**Secure Engineering & Data Privacy (SEDP)**](https://complianceforge.com/product/security-by-design-privacy-by-design/ "Security & Privacy by Design")
The SEDP addresses the “how?” questions for how your company ensures both security and privacy principles are operationalized.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP and DSP policies and standards for ensuring secure engineering and privacy principles are operationalized on a daily basis.
- The concept of “secure engineering” is mandatory in numerous statutory, regulatory and contractual requirements. The SEDP provides a “paint by numbers” approach to ensure your company has evidence of both due care and due diligence for operationalizing security and privacy principles.
- The SEDP is based on numerous industry frameworks, but the core is NIST 800-160, which is the de facto standard on secure engineering. |
|  | [**Continuity of Operations Program (COOP)**](https://complianceforge.com/product/continuity-of-operations-plan/ "Continuity of Operations Program COOP")
The COOP addresses the “how?” questions for how your company plans to respond to disasters to maintain business continuity.
- This is an editable Microsoft Word document that provides program-level guidance to directly supports the CDPP's policies and standards for disaster recovery and business continuity operations.
- The concept of “continuity operations” spans incident response to disaster recovery to business continuity operations. This is a very common requirement in numerous statutory, regulatory and contractual requirements. The COOP provides your organization with the documentation to prove it addresses both disaster recovery and business continuity.
- The COOP is based on numerous frameworks to provide a holistic approach to DR and BC operations. |
|  | [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configuration template")
The SBC addresses the “how?” questions for how your company securely configures its technology assets, such as system hardening according to CIS Benchmarks, DISA STIGs or vendor recommendations.
- This is an editable Microsoft Word document that provides program-level guidance to direct systems administrators, third-parties and other asset custodians on the expectation to harden operating systems, applications and services.
- The hardening of systems is a basic requirement, but most organization struggle with a way to document the requirements they are using to secure their assets. This is where the SBC comes into play.
- The SBC leverages multiple sources for "industry best practices" and you are able to select what works best for your organization. |
|  | [**Information Assurance Program (IAP)**](https://complianceforge.com/product/control-validation-testing-information-assurance-template "Information Assurance Program - Control Validation Testing")
The IAP addresses the “how?” questions for how your company performs pre-production testing to ensure that both cybersecurity and privacy principles are built-in by default.
- This is an editable Microsoft Word document that provides program-level guidance to conduct pre-production testing that ties in with existing SDLC/PDLC processes.
- The IAP leverages multiple sources for "industry best practices" and is based on practices used by the US Government for Information Assurance (IA) and Security Testing & Evaluation (ST&E). |
|  | **[Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/ "Cybersecurity Business Plan (CBP)")** The CBP is a cybersecurity-focused business planning template to document your organization's cybersecurity strategy and roadmap.
- This is an editable Microsoft Word document that provides an easy-to-follow template to build out a cybersecurity strategy and a roadmap to improve the cybersecurity practices of your organization.
- The CBP is focused on helping organizations create, maintain and leverage a security strategy and roadmap for organizational cybersecurity improvement.
- This is a CISO-level product to accelerate the adoption and implementing of cybersecurity & data protection program at your organization. |
|  | **[Data Protection Program (DPP)](https://complianceforge.com/data-privacy-program-dpp/ "Data Protection Program (DPP) ")** The DPP is a solution to accelerate the adoption and implementing of a privacy program at your organization.
- It is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers.
- The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
- This is designed for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
- At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. |
Please note that if you want a customized bundle, we are happy to create one for you. Just [contact us](https://complianceforge.com/contact-us/) with your needs and we will generate a quote for you.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=te0re8tmauy1)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
[c](https://complianceforge.com/bundle/c-scrm-bundle-2/) [nist 800](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan) [privacy bundle 1: cdpp version (iso or nist alignment)](https://complianceforge.com/bundle/privacy-bundle-1) [supply chain risk management (scrm) templates](https://complianceforge.com/cybersecurity-templates/supply-chain-risk-management/) [c](https://complianceforge.com/blog/cscrm-strategy-implementation-plan/) [c](https://complianceforge.com/blog/tag/C-SCRM) [c](https://complianceforge.com/blog/tag/c-scrm) [risk bundle 2: risk, vulnerability & ir management](https://complianceforge.com/bundle/risk-bundle-2)
## CMMC Compliance Guide
[Skip to main content](https://complianceforge.com/blog/cmmc-document-implement-assess/#main-content)
[](https://complianceforge.com/blog/cmmc-document-implement-assess/)
**Bottom Line Up Front (BLUF): Time is money when it comes to CMMC compliance efforts**:
- If you have poorly-crafted documentation, it will cost you more time & money in implementation and assessment.
- If you do not follow a prioritized implementation plan for NIST 800-171 controls, you will likely have to redo work that will cost you both time and money.
- If you pick an assessor without the technical competence to evaluate your specific environment and/or who lacks a reasonable audit background, that could jeopardize your CMMC assessment and contract opportunities.
**How To Do NIST 800-171 / CMMC**
At ComplianceForge, we are routinely asked for the "easy button" approach to NIST 800-171 & Cybersecurity Maturity Model Certification (CMMC). The reality is that while there is no silver bullet to make NIST 800-171 & CMMC less demanding, there are proven approaches that are efficient and can save you time and money to implement NIST 800-171 controls and generate the evidence necessary to pass a CMMC assessment. ComplianceForge has worked with several third-parties that we trust to refer our clients to for NIST 800-171 & CMMC compliance needs.
From a high-level perspective, your journey to passing a CMMC assessment is a three-part process that builds off the previous part:
1. Documentation. You need quality documentation to provide evidence of due diligence that your NIST 800-171 & CMMC program exists and comprehensively addresses all requirements. This includes policies, standards, procedures, System Security Plan (SSP), Plan of Action & Milestones (POA&M), Supply Chain Risk Management (SCRM) plan, etc.
2. Implementation. While there are Organizations Seeking Assessment (OSA) that have highly-capable internal IT and cybersecurity personnel who can implement all NIST 800-171 controls without outside assistance, most of the Defense Industrial Base (DIB) relies on third-party expertise (e.g., consultants).
3. Assessment. Where the rubber meets the road on NIST 800-171 & CMMC compliance is with a CMMC Third-Party Assessor Organization (C3PAO). Selecting the right assessor requires significant due diligence on your part to ensure that C3PAO’s assessment team has appropriate audit experience and technical competencies to fairly assess your unique scenario.

**It All Starts With Documentation For NIST 800-171 & CMMC Compliance**
ComplianceForge has quite a few options for NIST 800-171 & CMMC and selecting the right option depends on the focus of your compliance efforts. This primarily comes down to determining if you just need to comply with NIST 800-171 & CMMC or if you have other compliance obligations that you need to address:
- Our most straightforward approach to just NIST 800-171 & CMMC Level 2 compliance is the [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/). This is the most cost-effective and efficient solution we offer and the NCP contains all the policies, standards, procedures, SSP/POA&M, SCRM Plan and other templates that you will need to pass a CMMC assessment.
- If you need to “speak NIST 800-53” for other contracts (e.g., FedRAMP, RMF, FISMA, etc.) then [CMMC bundle #2](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-2-L3) is a great option to address the moderate baseline of NIST 800-53 R5. Since that is straight NIST 800-53 terminology/taxonomy, that might be overkill for organizations that just need to comply with NIST 800-171 & CMMC. Similar to CMMC bundle #2, we also offer a high baseline version of NIST 800-53 R5 with [CMMC bundle #3](https://complianceforge.com/bundle/nist-800-171-cmmc-bundle-3-level-3).
- If you need “the whole enchilada” with robust compliance for complex compliance requirements that go far beyond just NIST 800-171 & CMMC, then [CMMC bundle #4](https://complianceforge.com/bundle/nist-800-171-cmmc-2-bundle-4-level-3) is the best option. This is designed for an enterprise-class environment, especially one that is going to leverage a GRC platform to help manage documentation. The coverage and scalability is unmatched in the industry.
Documentation needs for NIST 800-171 & CMMC expand beyond just policies, standards and procedures. This is where documentation solutions from ComplianceForge can save your organization from hundreds to thousands of hours. You can contact ComplianceForge at 855-205-8437 or [support@complianceforge.com](mailto:support@complianceforge.com).
**Implementing Policies & Standards, Along With Tailoring Procedures & SSP Templates**
The DIB faces a wide range of competencies from consultants, Managed Service Providers (MSPs) and Managed Security Service Providers (MSSP) who are vying for OSAs’ consulting budgets. It is common for quality consultants, MSPs/MSSPs to have a backlog of work where they cannot start working with new clients for at least 3-4 months, so that is something to keep in mind for your timeline considerations.
We work with several quality CMMC practitioners, but we want to highlight [How To GRC](https://howtogrc.com/) (HTGRC) due to their expertise with implementing ComplianceForge documentation, specifically the [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/) and [Digital Security Program (DSP)](https://complianceforge.com/secure-controls-framework-scf-compliance-bundles/). HTGRC is a cybersecurity firm focused on designing and implementing cost effective and scalable cybersecurity programs. HTGRC provides CMMC and NIST SP 800-171 readiness assessments, advisory and audit preparation along with continuous compliance management.
David Driggers is the Senior Partner at HTGRC and his team has considerable experience implementing and tailoring ComplianceForge products and the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/). HTGRC can help automate ComplianceForge policies, standards and procedures in a Governance, Risk & Compliance (GRC) solution, where they can provide expert-level implementation and support for both [CMMC+](https://cmmcplus.com/) and [SCF Connect](https://scfconnect.com/) that can make managing evidence artifacts more efficient. You can contact HTGRC at 907-299-7775 or [learn@howtogrc.com](mailto:learn@howtogrc.com).
HowToGRC offers the following NIST 800-171 & CMMC related services:
- [CMMC Kill Chain](https://complianceforge.com/nist-800-171/cmmc-kill-chain/) implementation.
- Developing a tailored cybersecurity program for NIST 800-171 & CMMC
- Tailoring & implementation consulting services for ComplianceForge products (e.g., DSP, CDPP, CSOP, etc.).
- Governance, Risk & Compliance (GRC) platform integration.
Note: there are other great CMMC Practitioners that we work with. You can find many listed at: [https://www.cmmc-coa.com/cmmc-practitioners](https://www.cmmc-coa.com/cmmc-practitioners).
**You Need A Common-Sense C3PAO With Audit Experience & Technical Competence**
If you’ve ever been through ISO 27001, SOC 2 or PCI DSS assessments, you know that not all assessors/auditors are the same. That is why it is incredibly important to do your homework to select a C3PAO that has both the technical competencies and auditor experience necessary to provide a fair CMMC assessment.
ComplianceForge has worked with [Cybersec Investments](https://cybersecinvestments.com/) on CMMC-related topics for several years and we are very comfortable with recommending clients to them for their C3PAO needs. Cybersec Investments has already performed several assessments through the Department of Defense (DoD)’s Joint Surveillance Voluntary Assessment Program (JSVA), so they are leading the field as a C3PAO.
Fernando Machado is the Managing Principal & Chief Information Security Officer for Cybersec Investments. He is a Certified CMMC Assessor (CCA), Certified CMMC Professional (CCP) and was a member of the CMMC Accreditation Body’s Standards Management Industry Working Group (IWG). You can Cybersec Investments at 800-960-8802 or [info@cybersecinvestments.com](mailto:info@cybersecinvestments.com).
- [#C3PAO](https://complianceforge.com/blog/tag/C3PAO)
- [#CCA](https://complianceforge.com/blog/tag/CCA)
- [#CCP](https://complianceforge.com/blog/tag/CCP)
- [#cmmc compliance](https://complianceforge.com/blog/tag/cmmc+compliance)
- [#cmmc policy templates](https://complianceforge.com/blog/tag/cmmc+policy+templates)
- [#ComplianceForge](https://complianceforge.com/blog/tag/ComplianceForge)
- [#Cybersec Investments](https://complianceforge.com/blog/tag/Cybersec+Investments)
- [#Digital Security Program](https://complianceforge.com/blog/tag/Digital+Security+Program)
- [#How To GRC](https://complianceforge.com/blog/tag/How+To+GRC)
- [#JSCA](https://complianceforge.com/blog/tag/JSCA)
- [#NIST 800-171 Compliance Program](https://complianceforge.com/blog/tag/NIST+800-171+Compliance+Program)
- [#nist 800-171 policy templates](https://complianceforge.com/blog/tag/nist+800-171+policy+templates)
- [#SCF Connect](https://complianceforge.com/blog/tag/SCF+Connect)
- [#Secure Controls Framework](https://complianceforge.com/blog/tag/Secure+Controls+Framework)
- [Email](mailto:?subject=CMMC%3A%20Document%2C%20Implement%20%26%20Assess%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcmmc-document-implement-assess%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcmmc-document-implement-assess%2F&title=CMMC%3A%20Document%2C%20Implement%20%26%20Assess%20-%20ComplianceForge&summary=CMMC%3A%20Document%2C%20Implement%20%26%20Assess%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcmmc-document-implement-assess%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Digital Security Program
[Skip to main content](https://complianceforge.com/product/comprehensive-digital-security-program/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/103/1533/secure-controls-framework-scf-policy-standards-controls-and-metrics-template-dsp-scf__71153.1740599332.jpg?c=2)
[4 reviews](https://complianceforge.com/product/comprehensive-digital-security-program/#product-reviews)
$10,400.00
(You save)
# Digital Security Program (DSP)
SKU:P02-DSP-NOUPC:692878856744Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Digital%20Security%20Program%20(DSP)&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcomprehensive-digital-security-program%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcomprehensive-digital-security-program%2F&title=Digital%20Security%20Program%20(DSP)&summary=Digital%20Security%20Program%20(DSP)&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcomprehensive-digital-security-program%2F "Linkedin")

[](https://complianceforge.com/product/comprehensive-digital-security-program/#dsp-example-section)
## Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the DSP is to help answer common questions we receive.
[](https://complianceforge.com/digital-security-program-dsp-product-video/ "Watch Video")
[View Product Video](https://complianceforge.com/digital-security-program-dsp-product-video/)
## What Is The Digital Security Program (DSP)?
The DSP is an enterprise-class solution for cybersecurity & data privacy documentation consisting of thirty-three (33) domains that defines a modern, digital security program. Specifically:
- Policies
- Control objectives
- Standards
- Guidelines
- Controls ( [Secure Controls Framework](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework"))
- Metrics
Nested within these thirty-three (33) policies are the control objectives, standards, guidelines, metrics & more that enable you to govern your cybersecurity & data privacy program. The DSP was developed to meet the need for growing organizations that want to avoid being locked into alignment with a single framework or have complex compliance requirements that span multiple frameworks. This approach is a "best in class" hybrid framework structure that provides you with the ability to align with multiple frameworks in an efficient and scalable manner.
The DSP leverages the [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework"), which is a metaframework that map to over 100 cybersecurity & data privacy laws, regulations and frameworks. The SCF's integration into the DSP provides mapped risks, threats, maturity criteria and much more to make it the most robust solution on the market!


The DSP's policies & standards have direct, 1-1 mapping to the SCF's controls. The DSP leverages several key SCF components to provide “more than just policies & standards” by incorporating maturity criteria, a threat catalog, a risk catalog and more! The DSP provides invaluable content to operationalize several of the SCF's notable capabilities:
- [Cybersecurity & Data Privacy (C\|P) Principles](https://securecontrolsframework.com/domains-principles/ "SCF Security and Privacy Principles")
- [Data Privacy Management Principles (DPMP)](https://securecontrolsframework.com/data-privacy-management-principles/ "SCF Data Privacy Management Principles")
- [Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/ "SCF Cybersecurity Capability Maturity Model")
- [Cybersecurity & Data Privacy Risk Management Model (C\|P-RMM)](https://securecontrolsframework.com/risk-management-model/ "SCF Risk Management Model")
## What Problems Does The DSP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The DSP is an efficient method to obtain comprehensive security policies, standards, controls and metrics for your organization!
- Compliance Requirements - Nearly every organization, regardless of industry, is required to have formally-documented security policies and standards. Requirements range from PCI DSS to HIPAA to NIST 800-171. The DSP is designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The DSP's standards provides mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements \- It is very common for clients and partners to request evidence of a security program and this includes policies and standards. The DSP provides this evidence!
## How Does the DSP Solve These Problems?
- Clear Documentation \- The DSP provides comprehensive documentation to prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings \- The DSP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices - The DSP is written to support over one hundred laws, regulations and industry frameworks!
The DSP and its corresponding [Cybersecurity Operating Procedures (CSOP)](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Cybersecurity Operating Procedures (CSOP)"), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. They cover GRC policies, GRC standards, GRC metrics and more. The following documents are valuable resources to justify purchasing the DSP to advance your GRC practices:
- [ComplianceForge Reference Model – Hierarchical Cybersecurity Governance Framework](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Hierarchical Cybersecurity Governance Framework") – Level setting on how the various types of documentation support each other. This provides insights into the definitions used, since there is a tendency within the industry to abuse definitions around policy, standard, procedure, etc. This is the hierarchical structure we follow to build our content so it is scalable and based on industry practices.
- [Integrated Controls Management (ICM)](https://complianceforge.com/free-guides/integrated-controls-management/ "Integrated Controls Management (ICM) Model - How To GRC Playbook") \- This is a "how to GRC playbook" that can help you establish the steps necessary to design, build and implement viable GRC processes. These are the steps we will tell you to follow if we were brought in to provide professional services. This helps explain further integration between the policies and standards within the DSP, corresponding procedures within the CSOP and controls from the SCF.
- [Instructions & Best Practices For Using The DSP](https://complianceforge.com/content/pdf/start-here-digital-security-program-dsp.pdf "Guide To Using the Digital Security Program") – This is a "start here" guide for using the DSP that provides a baseline for what the DSP's documentation components are and how to tailor the DSP for your specific needs.
- [Security Metrics Reporting Model (SMRM)](https://complianceforge.com/free-guides/security-metrics-reporting-model/ "Security Metrics Reporting Model (SMRM)") – This is the metrics model we developed as a way to leverage the built-in metrics that come as part of the DSP.
- [DSP & CSOP Content Examples](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-documentation-template-examples.pdf "ComplianceForge Documentation Examples") \- This is a content example that shows two side-by-side examples from policies all the way to metrics.
- [Unified Scoping Guide (USG)](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "Unified Scoping Guide (USG)") – Understanding control applicability is important and this scoping guide is designed to address any type of sensitive or regulated data so the appropriate controls can be applied.
Similar to our framework-specific Cybersecurity & Data Protection Program (CDPP) products, the DSP provides alignment with the underlying cybersecurity standards that must be complied with, as stipulated by statutory, regulatory and contractual requirements. However, the DSP provides _robust coverage_ for over **100 laws, regulations and other cybersecurity and privacy frameworks**. The DSP is essentially a "superset" of ISO 27002, NIST CSF, NIST 800-171, NIST 800-53 and other frameworks for organizations that do not want to be locked into alignment with just one framework \[ _scroll to the bottom of the page to see a list of everything the DSP currently maps to\]_.
[](https://scfconnect.com/ "SCF Connect | SCF GRC solution")
## Accelerating Your Business - Mapped To Over 100 Leading Cybersecurity & Data Privacy Laws, Regulations & Frameworks!
Leveraging the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)"), the DSP maps over 100 cybersecurity and data privacy laws, regulations and frameworks! This includes the most common statutory, regulatory and contractual requirements that are expected from a cybersecurity & data protection program. The DSP provides the necessary policies, control objectives, standards, guidelines and metrics to operationalize the SCF for your organization!
[](https://securecontrolsframework.com/ "Secure Controls Framework policies standards procedures metrics")
## Cybersecurity & Data Privacy Policies, Standards, Controls & Metrics For A Modern Company - Hierarchical & Scalable!
ComplianceForge provides organizations with exactly what they need to protect themselves - professionally written cybersecurity policies, control objectives, standards, controls, procedures and guidelines at a very affordable cost. The DSP can be found in medium and large organizations that range from Fortune 500 companies, to US and international government agencies, universities and other organizations that have complex compliance requirements and need an efficient, scalable solution for their **Governance, Risk & Compliance (GRC)** needs.
The Digital Security Program (DSP) is footnoted to provide authoritative references for the statutory, regulatory and contractual requirements that need to be addressed. Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the DSP does this from a cybersecurity perspective.
The [**Cybersecurity Standardized Operating Procedures (CSOP)**](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "SCF Procedures") is available that provides mapped procedures to the DSP's standards. This is a 1-1 mapping with a procedure for each standard.
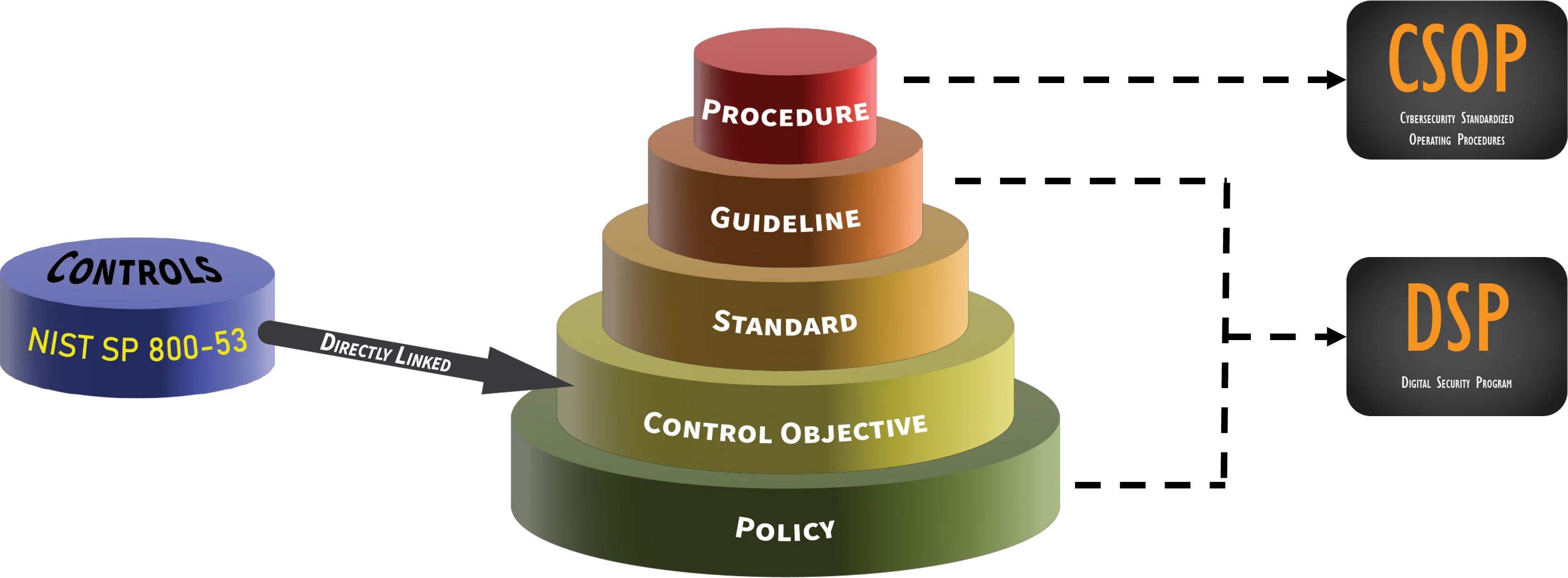
## Operationalize Cybersecurity & Data Privacy By Design
It is possible to visualize the **Digital Security Program (DSP)** as a buffet of cybersecurity and privacy policies, standards, controls and metrics. Once you determine what statutory, regulatory and contractual obligations are applicable to your organization, it is straightforward to identify a customized control set that is specific to your unique compliance obligations. This idea of building in cybersecurity and privacy requirements into your governance program is Security by Design (SbD) and Privacy by Design (PbD), where the obligations are understood before projects/initiatives commence, so that secure solutions can be designed, implemented and maintained. The DSP forms the cornerstone of your security and privacy program.
| | | |
| --- | --- | --- |
|  | **Security by Design (SbD)** requirements come from numerous sources. In this context, some of the most important cybersecurity frameworks are:
- Cybersecurity Maturity Model Certification (CMMC)
- International Organization for Standardization (ISO)
- National Institute for Standards & Technology (NIST)
- US Government (HIPAA, FedRAMP, DFARS, FAR & FTC Act)
- Information Systems Audit and Control Association (ISACA)
- Cloud Security Alliance (CSA)
- Center for Internet Security (CIS)
- Open Web Application Security Project (OWASP)
- Payment Card Industry Data Security Standard (PCI DSS)
- European Union General Data Protection Regulation (EU GDPR) | 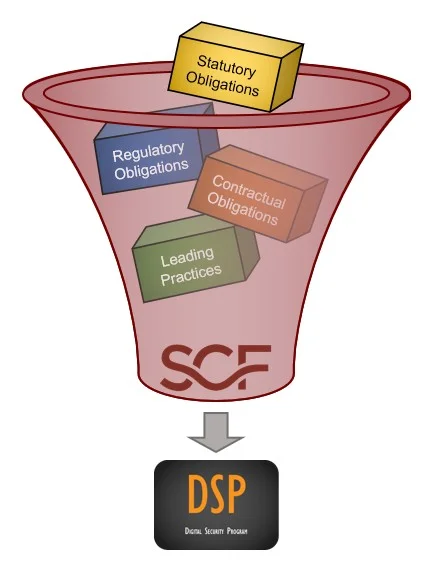 |
|  | Similar to SbD, **Privacy by Design (PbD)** requirements come from numerous sources. In this context, some of the most important privacy frameworks are:
- Generally Accepted Privacy Principles (GAPP)
- Fair Information Practice Principles (FIPPs)
- Organization for the Advancement of Structured Information Standards (OASIS)
- International Organization for Standardization (ISO)
- National Institute for Standards & Technology (NIST)
- Information Systems Audit and Control Association (ISACA)
- European Union General Data Protection Regulation (EU GDPR)
- US Government (OMB, HIPAA & FTC Act) |
## Understanding "How To GRC" With The Digital Security Program (DSP) & Secure Controls Framework (SCF)
ComplianceForge, in conjunction with the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)"), literally wrote the book on "how to do GRC" by establishing the [**Integrated Controls Management (ICM)**](https://complianceforge.com/free-guides/integrated-controls-management/ "Integrated Controls Management (ICM)") that is a principle-based approach to Governance, Risk & Compliance (GRC) operations. The ICM Overview document (shown below) is a great starting place to understand how the DSP can help your organization to designing, implementing and managing a security and privacy program that incorporates requirements to be both secure and compliant. This approach leverages the "Deming Cycle" of Plan, Do, Check and Act (PDCA) for continuous improvement.
Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
- Statutory \- these are US state, federal and international laws.
- Regulatory \- these are requirements from regulatory bodies or governmental agencies.
- Contractual \- these are requirements that are stipulated in contracts, vendor agreements, etc.
- Industry-Recognized Practices \- these are requirements that are based on an organization’s specific industry, where "industry norms" are established for what constitutes reasonable practices.
There are eight (8) principles associated with ICM that are fully-supported by the DSP to develop, implement and maintain a secure and compliant security and privacy program:
1. Establish Context
2. Define Applicable Controls
3. Assign Maturity-Based Criteria
4. Publish Policies, Standards & Procedures
5. Assign Stakeholder Accountability
6. Maintain Situational Awareness
7. Manage Risk
8. Evolve Processes
[](https://complianceforge.com/content/pdf/complianceforge-integrated-controls-management.pdf "Integrated Controls Management Overview")
The structure of the Digital Security Program is scalable to make it is easy to add or remove policy sections, as your business needs change. The same concept applies to standards – you can simply add/remove content to meet your specific needs. The DSP addresses the “why?” and “what?” questions, since policies and standards form the foundation for your cybersecurity program. The following two documents shown below are well worth the time to make a pot of coffee and read through, since you will be able to understand both the structure of the documentation and how you can customize it for your specific needs.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the DSP! While the DSP does come in Microsoft Word like the CDPP, the included Excel version of the DSP comes with the following content so it is easy to import into a GRC/IRM solution:
- Policy statements
- Policy intent
- Control objectives
- Standards
- Guidance
- Controls ( [Secure Controls Framework](https://complianceforge.com/product/dsp-cybersecurity-standardized-operating-procedures-csop/ "Secure Controls Framework"))
- Risk catalog
- Threat catalog
- [Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/ "Security & Privacy Capability Maturity Model Criteria") criteria
- Metrics - including suggested [Key Performance Indicators (KPIs) & Key Risk Indicators (KRIs)](https://complianceforge.com/free-guides/security-metrics-reporting-model/ "DSP & SCF metrics")
- Indicators of Compromise (IoC)
- Indicators of Exposure (IoC)
- Target Audience Applicability
- Scoping - Basic or Enhanced Requirement
- Recommended roles / teams with responsibility for each standard.

The DSP is our recommended solution if you are currently using or plan to use a **Governance, Risk & Compliance (GRC)** or **Integrated Risk Management (IRM)** solution. The DSP is ready to import into your GRC/IRM instance, since it comes in both Microsoft Word and Excel formats. This makes the import from Excel straightforward and that allows you to then do you any customization and collaboration directly from your GRC portal.
| | | |
| --- | --- | --- |
| **Guide To Using The DSP & SCF** | | **Understanding "How To GRC"** |
| [](https://complianceforge.com/content/pdf/start-here-digital-security-program-dsp.pdf "Getting Started With The DSP & SCF") | | [](https://complianceforge.com/content/pdf/complianceforge-hierarchical-cybersecurity-governance-framework.pdf "Understanding How To GRC") |
## Example Digital Security Program (DSP)
Our customers choose the **Digital Security Program (DSP)** because they need a scalable and comprehensive solution. The DSP is a hybrid, "best in class" approach to cybersecurity documentation that covers dozens of statutory, regulatory and contractual frameworks to create a comprehensive set of cybersecurity policies, standards, controls and metrics. The DSP has a 1-1 mapping relationship with the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)") so it maps to over 100 leading practices! To understand the differences between the DSP and CDPP, please visit [here](https://complianceforge.com/faq/dsp-vs-wisp "Differences Between DSP and CDPP") for more details.
**View Product Examples**
| | | |
| --- | --- | --- |
| [](https://complianceforge.com/content/pdf/example-dsp-digital-security-program.pdf "Example Digital Security Program - Operationalize Secure Controls Framework") | | [](https://complianceforge.com/content/pdf/example-dsp-grc-import-ready-policies-standards-controls-metrics.pdf "SCF Digital Security Program cybersecurity best practices mapping") |
## What Is Included With The DSP?
## Cost Savings Estimate For The Digital Security Program (DSP) - A Fraction Of The Time & Expense
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DSP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 900 internal staff work hours, which equates to a cost of approximately **$90,000** in staff-related expenses. This is about 12-24 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 800 consultant work hours, which equates to a cost of approximately **$260,000**. This is about 6-12 months of development time for a contractor to provide you with the deliverable.
- The DSP is approximately 4% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the DSP the same day you place your order.
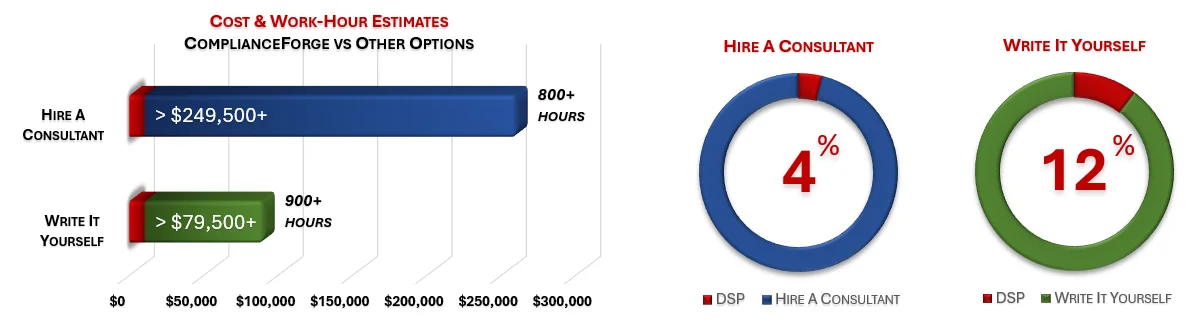
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
## 33 Domains - One Policy For Each Domain
The DSP contains thirty-three (33) unique domains that cover a modern cybersecurity & privacy program. Each of these 33 policies are supported by standards that provide the granular requirements necessary to enforce these standards (examples of what these policy and standards look like are available in the next section below this chart). The 32 policies that make up the DSP are:
| | | | |
| --- | --- | --- | --- |
| **Policy**
**#** | **DSP Policy** | **Identifier** | **DSP Policy Intent** |
| **1** | **Security & Privacy Governance** | **GOV** | The Security & Privacy (GOV) policy is focused on helping an organization specify the development of an organization’s security and privacy programs, including criteria to measure success, to ensure ongoing leadership engagement and risk management. |
| **2** | **Artificial Intelligence & Autonomous Technologies** | **AAT** | The Artificial Intelligence & Autonomous Technologies (AAT) domain is designed to minimize emergent properties or unintended consequences through stringent governance practices that result in AI and autonomous technologies that are reliable, safe, fair, secure, resilient, transparent, explainable and privacy-enhanced. |
| **3** | **Asset Management** | **AST** | The Asset Management (AST) policy is focused on helping an organization ensure technology assets are properly managed throughout the lifecycle of the asset, from procurement through disposal, ensuring only authorized devices are allowed to access the organization’s network and to protect the organization’s data that is stored, processed or transmitted on its assets. |
| **4** | **Business Continuity & Disaster Recovery** | **BCD** | The Business Continuity & Disaster Recovery (BCD) policy is focused on helping an organization establish processes that will help the organization recover from adverse situations with the minimal impact to operations, as well as provide the ability for e-discovery. |
| **5** | **Capacity & Performance Planning** | **CAP** | The Capacity & Performance Planning (CAP) policy is focused on helping an organization prevent avoidable business interruptions caused by capacity and performance limitations by proactively planning for growth and forecasting, as well as requiring both technology and business leadership to maintain situational awareness of current and future performance. |
| **6** | **Change Management** | **CHG** | The Change Management (CHG) policy is focused on helping an organization ensure both technology and business leadership proactively manage change. This includes the assessment, authorization and monitoring of technical changes across the enterprise so as to not impact production systems uptime, as well as allow easier troubleshooting of issues. |
| **7** | **Cloud Security** | **CLD** | The Cloud Security (CLD) policy is focused on helping an organization govern the use of private and public cloud environments (e.g., IaaS, PaaS and SaaS) to holistically manage risks associated with third-party involvement and architectural decisions, as well as to ensure the portability of data to change cloud providers, if needed. |
| **8** | **Compliance** | **CPL** | The Compliance (CPL) policy is focused on helping an organization ensure controls are in place to be aware of and comply with applicable statutory, regulatory and contractual compliance obligations, as well as internal company standards. |
| **9** | **Configuration Management** | **CFG** | The Configuration Management (CFG) policy is focused on helping an organization establish and maintain the integrity of systems. Without properly documented and implemented configuration management controls, security features can be inadvertently or deliberately omitted or rendered inoperable, allowing processing irregularities to occur or the execution of malicious code. |
| **10** | **Continuous Monitoring** | **MON** | The Continuous Monitoring (MON) policy is focused on helping an organization establish and maintain ongoing situational awareness across the enterprise through the centralized collection and review of security-related event logs. Without comprehensive visibility into infrastructure, operating system, database, application and other logs, the organization will have “blind spots” in its situational awareness that could lead to system compromise, data exfiltration, or unavailability of needed computing resources. |
| **11** | **Cryptographic Protections** | **CRY** | The Cryptographic Protections (CRY) policy is focused on helping an organization ensure the confidentiality of the organization’s data through implementing appropriate cryptographic technologies to protect systems and data. |
| **12** | **Data Classification & Handling** | **DCH** | The Data Classification & Handling (DCH) policy is focused on helping an organization ensure that technology assets, both hardware and media, are properly classified and measures implemented to protect the organization’s data from unauthorized disclosure, regardless if it is being transmitted or stored. Applicable statutory, regulatory and contractual compliance requirements dictate the minimum safeguards that must be in place to protect the confidentiality, integrity and availability of data. |
| **13** | **Embedded Technology** | **EMB** | The Embedded Technology (EMB) policy is focused on helping an organization specify the development, proactive management and ongoing review of security embedded technologies, including hardening of the “stack” from the hardware, to firmware, software, transmission and service protocols used for Internet of Things (IoT) and Operational Technology (OT) devices. |
| **14** | **Endpoint Security** | **END** | The Endpoint Security (END) policy is focused on helping an organization ensure that endpoint devices are appropriately protected from security threats to the device and its data. Applicable statutory, regulatory and contractual compliance requirements dictate the minimum safeguards that must be in place to protect the confidentiality, integrity, availability and safety considerations. |
| **15** | **Human Resources Security** | **HRS** | The Human Resources Security (HRS) policy is focused on helping an organization create a security and privacy-minded workforce and an environment that is conducive to innovation, considering issues such as culture, reward and collaboration. |
| **16** | **Identification & Authentication** | **IAC** | The Identification & Authentication (IAC) policy is focused on helping an organization implement the concept of “least privilege” through limiting access to the organization’s systems and data to authorized users only. |
| **17** | **Incident Response** | **IRO** | The Incident Response (IRO) policy is focused on helping an organization establish and maintain a capability to guide the organization’s response when security or privacy-related incidents occur and to train users how to detect and report potential incidents. |
| **18** | **Information Assurance** | **IAO** | The Information Assurance (IAO) policy is focused on helping an organization ensure the adequately of security and controls are appropriate in both development and production environments. |
| **19** | **Maintenance** | **MNT** | The Maintenance (MNT) policy is focused on helping an organization ensure that technology assets are properly maintained to ensure continued performance and effectiveness. Maintenance processes apply additional scrutiny to the security of end-of-life or unsupported assets. |
| **20** | **Mobile Device Management** | **MDM** | The Mobile Device Management (MDM) policy is focused on helping an organization govern risks associated with mobile devices, regardless if the device is owned by the organization, its users or trusted third-parties. Wherever possible, technologies are employed to centrally manage mobile device access and data storage practices. |
| **21** | **Network Security** | **NET** | The Network Security (NET) policy is focused on helping an organization ensure sufficient security and privacy controls are architected to protect the confidentiality, integrity, availability and safety of the organization’s network infrastructure, as well as to provide situational awareness of activity on the organization’s networks. |
| **22** | **Physical & Environmental Security** | **PES** | The Physical & Environmental Security (PES) policy is focused on helping an organization minimize physical access to the organization’s systems and data by addressing applicable physical security controls and ensuring that appropriate environmental controls are in place and continuously monitored to ensure equipment does not fail due to environmental threats. |
| **23** | **Privacy** | **PRI** | The Privacy (PRI) policy is focused on helping an organization align privacy engineering decisions with the organization’s overall privacy strategy and industry-recognized leading practices to secure Personal Information (PI) that implements the concept of privacy by design and by default. |
| **24** | **Project & Resource Management** | **PRM** | The Project & Resource Management (PRM) policy is focused on helping an organization ensure that security-related projects have both resource and project/program management support to ensure successful project execution. |
| **25** | **Risk Management** | **RSK** | The Risk Management (RSK) policy is focused on helping an organization ensure that security and privacy-related risks are visible to and understood by the business unit(s) that own the assets and / or processes involved. The security and privacy teams only advise and educate on risk management matters, while it is the business units and other key stakeholders who ultimately own the risk. |
| **26** | **Secure Engineering & Architecture** | **SEA** | The Secure Engineering & Architecture (SEA) policy is focused on helping an organization align cybersecurity engineering and architecture decisions with the organization’s overall technology architectural strategy and industry-recognized leading practices to secure networked environments. |
| **27** | **Security Operations** | **OPS** | The Security Operations (OPS) policy is focused on helping an organization ensure appropriate resources and a management structure exists to enable the service delivery of cybersecurity operations. |
| **28** | **Security Awareness & Training** | **SAT** | The Situational Awareness & Training (SAT) policy is focused on helping an organization develop a security and privacy-minded workforce through continuous education activities and practical exercises, in order to refine and improve on existing training. |
| **29** | **Technology Development & Acquisition** | **TDA** | The Technology Development & Acquisition (TDA) policy is focused on helping an organization ensure that security and privacy principles are implemented into any products/solutions that are either developed internally or acquired to make sure that the concepts of “least privilege” and “least functionality” are incorporated. |
| **30** | **Third-Party Management** | **TPM** | The Third-Party Management (TPM) policy is focused on helping an organization ensure that security and privacy risks associated with third-parties are minimized and enable measures to sustain operations should a third-party become defunct. |
| **31** | **Threat Management** | **THR** | The Threat Management (THR) policy is focused on helping an organization establish a capability to proactively identify and manage technology-related threats to the security and privacy of the organization’s systems, data and business processes. |
| **32** | **Vulnerability & Patch Management** | **VPM** | The Vulnerability & Patch Management (VPM) policy is focused on helping an organization proactively manage the risks associated with technical vulnerability management that includes ensuring good patch and change management practices are utilized. |
| **33** | **Web Security** | **WEB** | The Web Security (WEB) policy is focused on helping an organization address the risks associated with Internet-accessible technologies by hardening devices, monitoring system file integrity, enabling auditing, and monitoring for malicious activities. |
## Before You "Can Move The Needle" You Need A Needle - Metrics Are Included In The DSP!
The DSP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer.
In addition to being a hybrid model that is made up of leading security frameworks, we also added in features that are not available in the Cybersecurity & Data Protection Program (CDPP), namely mapped controls and metrics. This equates to a potential time savings of hundreds of hours, based on how much work goes into not only creating controls and worthwhile metrics, but mapping those back into your organizations policies and standards.
One special aspect of the DSP is while it comes in Microsoft Word format, it also comes in Microsoft Excel so that it is easy to import into a GRC solution (e.g., [SCFConnect](https://scfconnect.com/ "SCFConnect - SCF GRC Solution"), [Ostendio](https://ostendio.com/ "Ostendio MyVCM - Digital Security Program Integration"), [ZenGRC (RiskOptics)](https://reciprocitylabs.com/ "ZenGRC Digital Security Program Integration"), [SimpleRisk](https://www.simplerisk.com/ "SimpleRisk - Secure Controls Framework Integration"), LogicGate, Ignyte Assurance Platform, Archer, RSAM, MetricStream, etc.)! This is an ideal solution for companies that either currently use a GRC solution or are exploring the use of one. The time savings can equate to a saving of tens of thousands of dollars in customizing "out of the box" documentation from these tools.
If you are interested in learning more, there is a product walk-through video and other helpful documentation, so keep reading or [contact us](https://complianceforge.com/contact-us/ "Contact ComplianceForge") so we can help answer your specific questions.
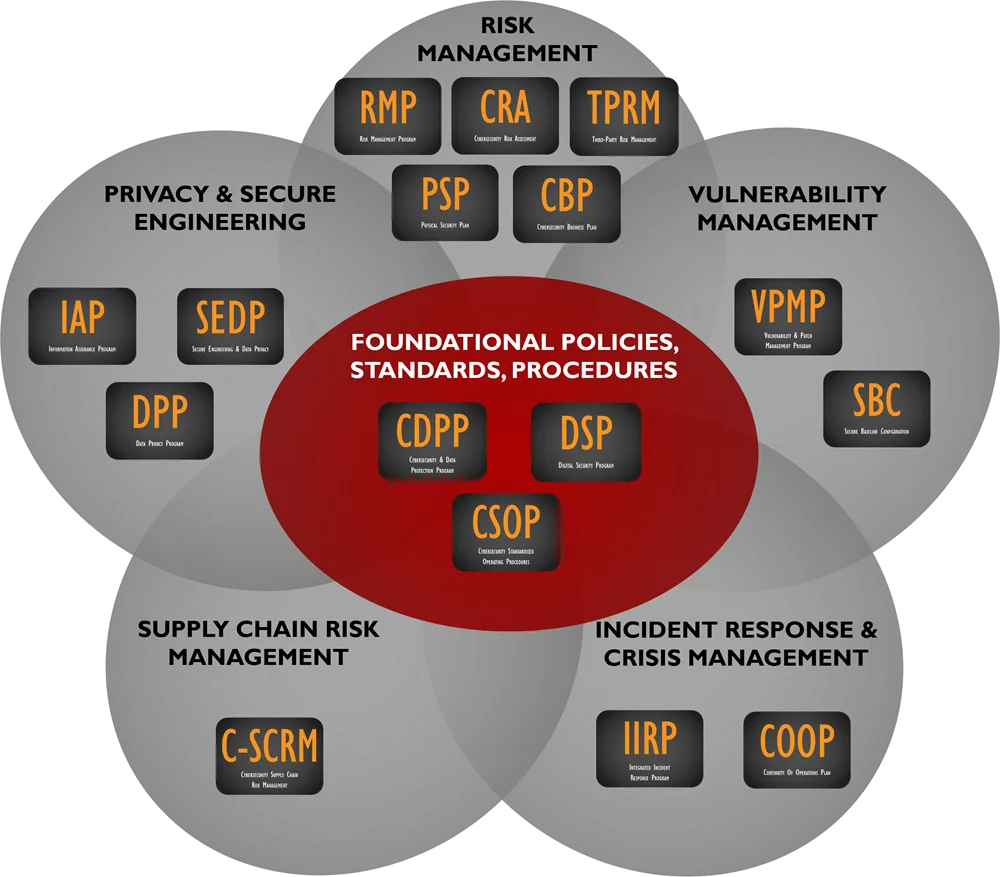
## Digital Security - The Evolution of Security
If you are reading this, you are likely familiar with how “IT Security,” “Information Security,” and “Cybersecurity” are used interchangeably by most people. However, these terms do have meaning and as you “peel back the onion” on terminology you will see that “Digital Security” is the new leading terminology to describe the entire security ecosystem. This term has evolved to be all-encompassing, since it addresses technology, information, physical security, privacy and safety.
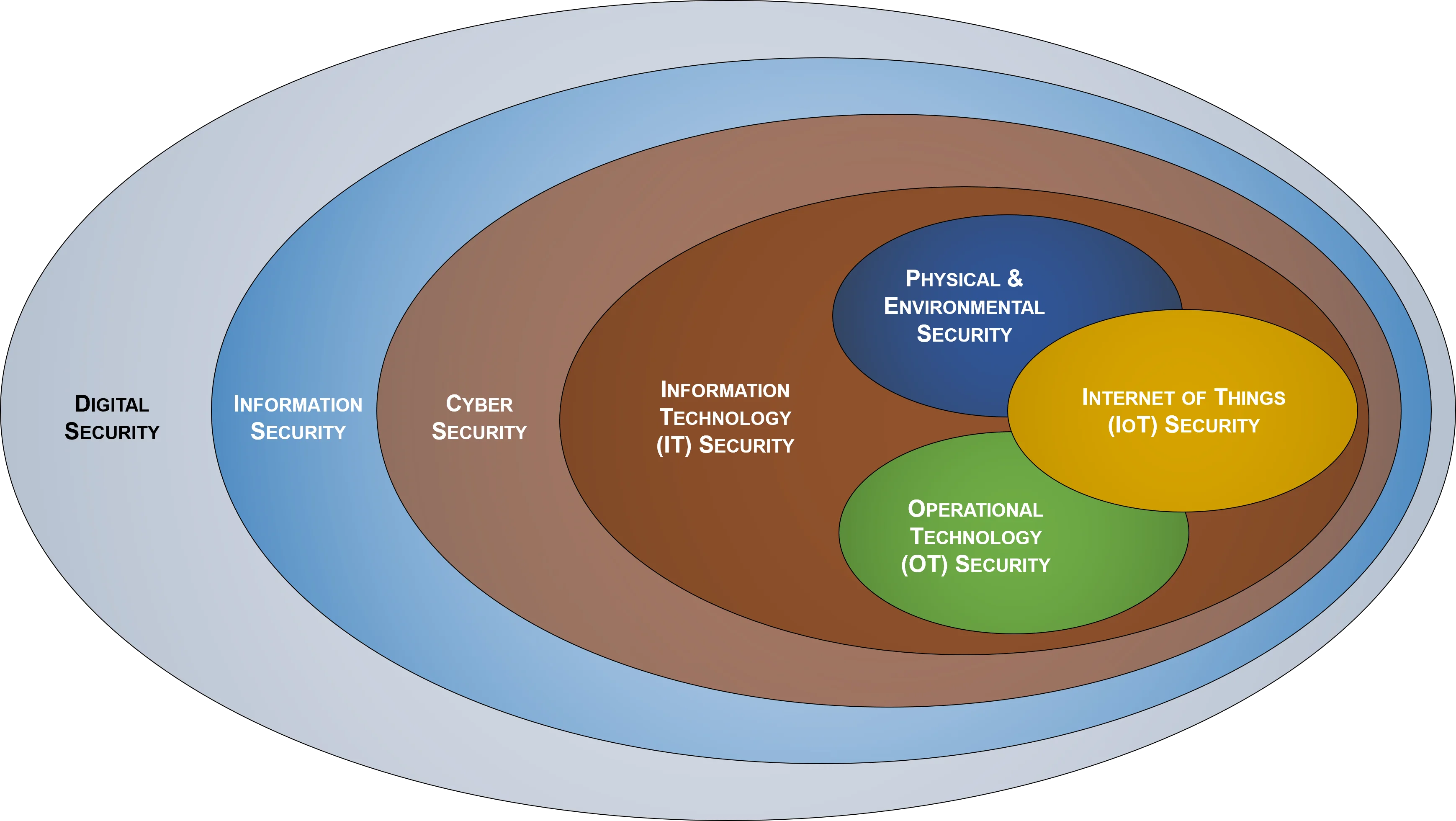
## Product Hierarchy & Interactions
The diagram below helps visualize how the DSP exists at a strategic level to define the "what" and "why" requirements to be secure and compliant. Those foundational policies and standards influence every other component of your cybersecurity and data protection program.

## Safety Component - One Benefit of Thinking Digital
For years, the “CIA Triad” stood as the foundation for what a security program was designed to address – the Confidentiality, Integrity and Availability of both systems and data. That has now changed, since there are real-world safety considerations from Operational Technology (OT) and the Internet of Things (IoT). This has caused the evolution of the CIA Triad into the Confidentiality, Integrity, Availability and Safety (CIAS) model.
The DSP is designed around the CIAS model by adopting the best of leading security frameworks.

## Steps To Using The DSP To Obtain CMM4 Maturity (Metrics-Driven)
It is a simple fact that technology and cybersecurity departments are not revenue-generating. These cost centers must continuously demonstrate value to justify current and future budgets. While many boards of directors and executive management provide initial security budget funding based on Fear, Uncertainty & Doubt (FUD), there is an eventual need to demonstrate a Security Return on Investment (SROI). Without this return on investment, budgets are hard to justify and capabilities suffer.
The most common ways for a security program to justify budget needs is through metrics reporting. The DSP can help you leverage the Systems Security Engineering Capability Maturity Model (SSE-CMM) with the Secure Control Framework's [Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/ "Cybersecurity & Data Privacy Capability Maturity Model (C|P-CMM)"). We avoided re-inventing the wheel and simply created an enterprise-class product that can help your organization rapidly advance its capability maturity to a CCM 4 levell or beyond!
[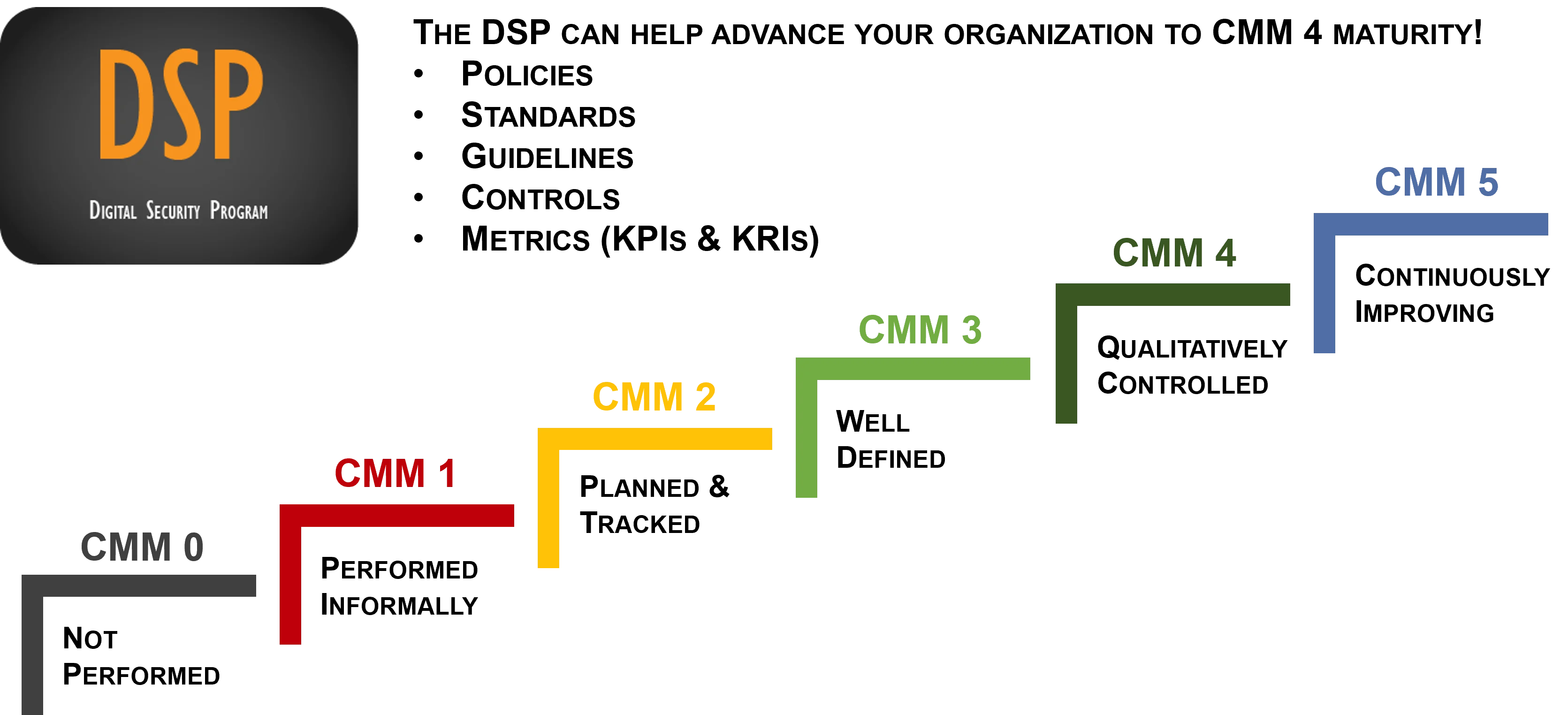](https://www.securecontrolsframework.com/sp-cmm "DSP SCF Capability Maturity Model SSE-CMM")
## Hierarchical Approach - Built To Scale & Evolve With Your Business
Our experience has proven that when it comes to Information Security policies, a standard is a standard for a reason. With that in mind, our Cybersecurity & Data Protection Program (CDPP) is based on industry-recognized best practices and Information Security standards so that you can meet your legal requirements. Unlike some competitor sites that offer “Bronze, Silver or Gold” packages that may leave you critically exposed, we offer a comprehensive Information Security solution to meet your specific compliance requirements. Why is this? It is simple - in the real world, compliance is penalty-centric. Courts have established a track record of punishing businesses for failing to perform “reasonably expected” steps to meet compliance with known standards.
The Cybersecurity & Data Protection Program (CDPP) follows a hierarchical approach to how the structure is designed so that standards map to control objectives and control objectives map to policies. This allows for the standards to be logically grouped to support the policies.

## Security Metrics Reporting Model
The ComplianceForge [**Security Metrics Reporting Model™ (SMRM)**](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-metrics-reporting-model.pdf "Cybersecurity Metrics Reporting Model (CMRM)") takes a practical view towards implementing a sustainable metrics reporting capability. At the end of the day, executive management (e.g., CIO, CEO, Board of Directors (BoD), etc.) want an answer to a relatively-straightforward question: **“Are we secure?”** In order for a CISO to honestly provide an answer, it requires a way for the CISO to measure and quantify an “apples and oranges” landscape where processes and technologies lack both uniform risk weighting and abilities to capture metrics. The SMRM helps solve this aspect of dissimilarity by utilizing a weighted approach to metrics that generate Key Performance Indexes (KPXs) as a way to logically-organize and report individual metrics. Using KPX enables the SMRM to provide a reasonable and defendable answer.
[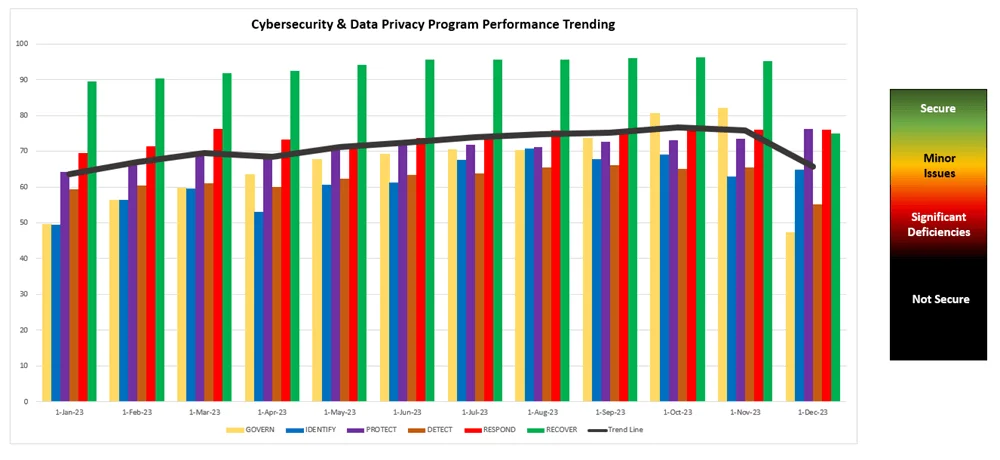](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-metrics-reporting-model.pdf "cybersecurity metrics reporting model template")
The “Are we secure?” question is best answered as a numerical score. This quantifiable score is used to visualize the score against a numerical spectrum to provides context, based on the risk profile of the organization. The numerical score would land between “not secure” and “secure” on the spectrum, according to a baseline score definition that would be specific to the organization. This can provide long-term trending to evaluate the direct impact of certain security initiatives. The SMRM can be automated in a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) platform, but it comes as a Microsoft Excel spreadsheet as part of ComplianceForge’s Digital Security Program (DSP). The “Are we secure?” question can be both tracked to display trending and drilled down into KPXs, or individual metrics, to identify why the score changed.
[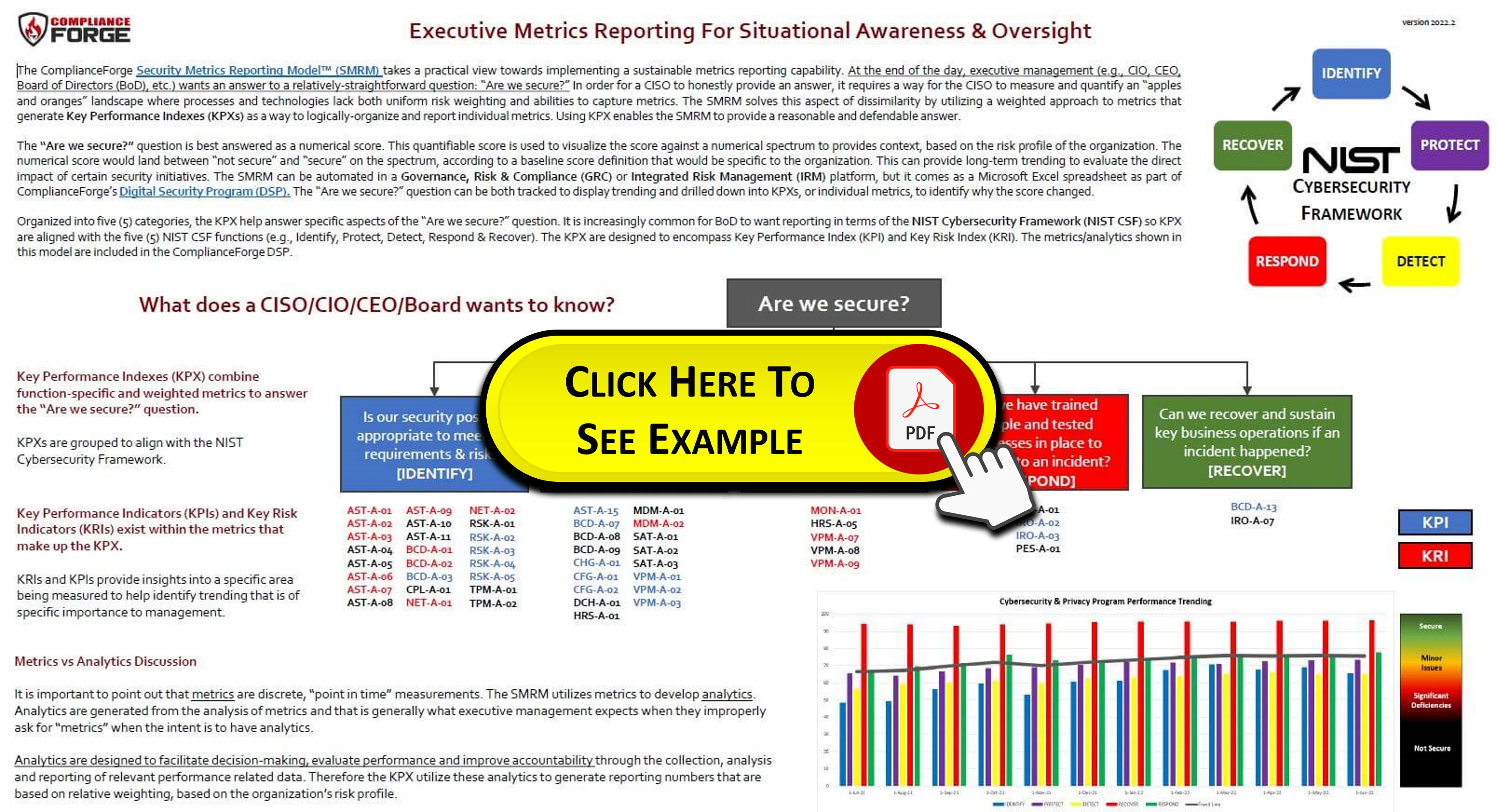](https://complianceforge.com/content/pdf/complianceforge-cybersecurity-metrics-reporting-model.pdf "Cybersecurity Metrics Reporting Model")
Key Performance Index (KPX) is essentially a term that we use to normalize the various metrics in each category. One area of contention with metrics is defining what a KPI or KRI is since people tend to butcher the terminology. Our approach to defining those terms are shown below:
**Key Performance Indexes (KPXs)**
KPXs are logical groupings of KPIs that allow an organization to monitor an index of metrics about a specific capability or team.
- KPXs are used to answer the question, _**“Is the XYZ capability operating effectively?”**_ where that capability is an aggregation of multiple individual metrics.
- KPXs may be weighted to highlight risk-heavy topics of concern.
- KPXs may be nested underneath other KPXs to report the hierarchical nature of metrics that help answer the question of “Are we secure?”
KPIs and KRIs are not hierarchical metrics, but are individual metrics that are deemed important to monitor, based on the specific risk or value associated with that metric:
**Key Performance Indicators (KPIs)**
- KPIs are “rearward facing” and focus on historical trending to evaluate performance.
- KPIs should not be weighted.
- KPIs are indicators that enable an organization to monitor its progress towards achieving its defined performance targets.
- KPIs are used to answer the question, _**“Are we achieving our desired levels of performance?”**_ for a specific control.
**Key Risk Indicators (KRIs)**
- KRIs are “forward facing” and focus on identifying a future-looking trend that impacts risk.
- KRIs should not be weighted.
- KRIs are indicators that enable an organization to define its risk profile and monitor changes to that profile.
- KRIs are used to answer the question, _**“Are we within our desired risk tolerance level?”**_ for a specific control.
The metrics shown in this model are included in DSP. ComplianceForge does not sell the SMRM, KPIs, KRIs on their own, since the metrics are part of the DSP solution. With the 1-1 mapping relationship between the DSP and the Secure Controls Framework (SCF), the DSP can help operationalize the SCF controls in a meaningful and efficient manner, so that is something to consider for organizations that want to fully adopt the SCF as its control structure and maximize its effectiveness.
Being transparent on the subject, the entire point of a "canned solution" for metrics is to provide a starting point where someone else does the heavy lifting for you to get to a 70-80% solution that someone within your organization can then run with to customize for your specific needs. This is where ComplianceForge is a business accelerator - we enable you to hit the ground running with your cybersecurity documentation that can takes months or years to create on your own. The "heavy lifting" of the equation is what we provide, not the finalized metrics product. That is really where the demarcation is between what ComplianceForge offers for metrics and how an organization would customize the remaining since you have the organization-specific knowledge side of the metrics equation that cannot be templatized.
## More Examples
While nearly all organizations have “security policies” in place, it is a sad reality that many are outdated, improperly scoped, and inadvertently add to technical debt. Quite simply, most security policies were never designed to scale as the organization grows or technologies evolve and are more of a liability than benefit. If that is your organization, the DSP can be a “quick win” to dramatically advance the maturity of your security program.
The DSP is a different animal – it is built to scale and adapt to the needs of the organization. The modular nature of the DSP means that each policy has its own standards, all the way down to controls and metrics. This hierarchical nature makes mapping metrics to policies a breeze, due to the logical organization of the documentation.
[](https://complianceforge.com/content/pdf/example-dsp-grc-import-ready-policies-standards-controls-metrics.pdf "Digital Security Program Example")
\[click to see an example of the Excel content\]
### “GOLDILOCKS” CONTROLS – NOT TOO BIG AND NOT TOO SMALL. JUST RIGHT.
The DSP uses the NIST Cybersecurity Controls Framework (CSF) version 1.1 for its metrics reporting model, so the controls are aligned with a leading framework for expected security controls. Key controls are identified from this control set and metrics are mapped to these controls. Again, being Excel it is editable for your needs.
[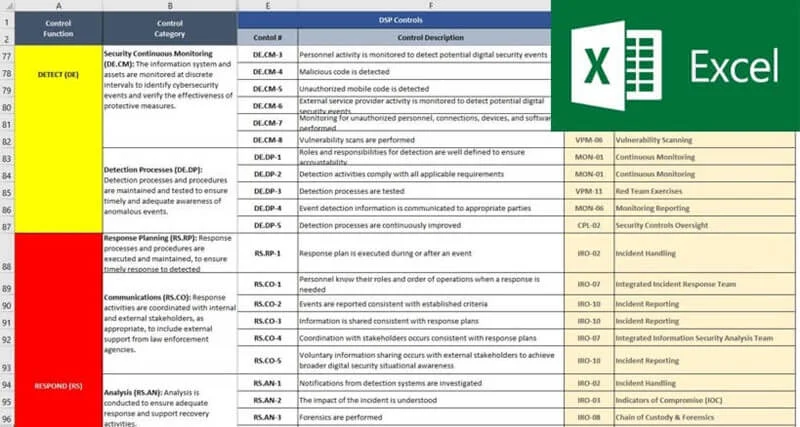](https://complianceforge.com/content/pdf/example-dsp-grc-import-ready-policies-standards-controls-metrics.pdf "Digital Security Program NIST Cybersecurity Framework Control Alignment")
\[click to see an example of the Excel content\]
## Creating A Cybersecurity Program Based On Multiple Leading Frameworks Is Achievable With A Metaframework!
The DSP uses the latest version of the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)") for mapping to leading cybersecurity & data privacy laws, regulations and frameworks. The DSP comes with an Excel spreadsheet that provides the mapping for the standards to these references. The DSP currently maps to well over 100 frameworks that includes mapped coverage of the following cybersecurity and data privacy-related statutory, regulatory and contractual frameworks:
| | | | | |
| --- | --- | --- | --- | --- |
| **Geography** | **Framework** | **Source** | **Authoritative Source - Statutory / Regulatory / Contractual Framework** | **Version** |
| Universal | AICPA
TSC 2017
(SOC 2) | AICPA | Service Organization Control - Trust Services Criteria (TSC) - SOC2 | 2017 |
| Universal | BSI
Standard 200-1 | BSI | Standard 200-1 | 2022 |
| Universal | CIS
CSC
v8.0 | CIS | Critical Security Controls (CSC) | 8.0 |
| Universal | COBIT
2019 | ISACA | Control Objectives for Information and Related Technologies (COBIT) | 2019 |
| Universal | COSO
v2017 | COSO | Committee of Sponsoring Organizations (COSO) 2017 Framework | 2017 |
| Universal | CSA
CCM
v4 | CSA | Cloud Controls Matrix (CCM) | v4 |
| Universal | CSA
IoT SCF
v2 | CSA | CSA IoT Security Controls Framework v2 | v2 |
| Universal | ENISA
v2.0 | EU | European Union Agency for Network and Information Security (ENISA) | 2.0 |
| Universal | GAPP | AICPA | Generally Accepted Privacy Principles (GAPP) | N/A |
| Universal | IEC 62443-4-2 | IEC | IEC 62443-4-2:2019 - Security for industrial automation and control systems
Part 4-2: Technical security requirements for IACS components | 2019 |
| Universal | ISO
22301
v2019 | ISO | 22301 - Security and resilience — Business continuity management systems — Requirements | 2019 |
| Universal | ISO
27001
v2013 | ISO | 27001 - Information Security Management Systems (ISMS) - Requirements | 2013 |
| Universal | ISO
27001
v2022 | ISO | 27001 - Information Security Management Systems (ISMS) - Requirements | 2022 |
| Universal | ISO
27002
v2013 | ISO | 27002 - Code of Practice for Information Security Controls | 2013 |
| Universal | ISO
27002
v2022 | ISO | 27002 - Information security, cybersecurity and privacy protection - Information security controls | 2022 |
| Universal | ISO
27017
v2015 | ISO | 27017 - Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services | 2015 |
| Universal | ISO
27018
v2014 | ISO | 27018 - Code of Practice for PI in Public Clouds Acting as PI Processors | 2014 |
| Universal | ISO
27701
v2019 | ISO | 27701 - Security techniques - Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management — Requirements and guidelines | 2019 |
| Universal | ISO
29100
v2011 | ISO | 29100 - Privacy Framework | 2011 |
| Universal | ISO
31000
v2009 | ISO | 31000 - Risk Management | 2009 |
| Universal | ISO
31010
v2009 | ISO | 31010 - Risk Assessment Techniques | 2009 |
| Universal | MITRE
ATT&CK
10 | MITRE | MITRE ATT&CK - NIST 800-53 mappings | N/A |
| Universal | MPA
Content Security Program
v5.1 | MPA | MPA Content Security Best Practices Common Guidelines | 5.1 |
| Universal | NIAC
Insurance Data Security Model Law (MDL-668) | NAIC | Insurance Data Security Model Law (MDL-668) | N/A |
| Universal | NIST Privacy Framework
v1.0 | NIST | NIST Privacy Framework | 1.0 |
| Universal | NIST
SSDF | NIST | Secure Software Development Framework (SSDF):
Mitigating the Risk of Software Vulnerabilities by Adopting a Secure Software Development Framework (SSDF) | N/A |
| Universal | NIST
800-37
rev 2 | NIST | SP 800-37 - Guide for Applying the RMF to Federal Information Systems rev2 | 2 |
| Universal | NIST
800-39 | NIST | SP 800-39 - Managing Information Security Risk | N/A |
| Universal | NIST
800-53
rev4 | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations | 4 |
| Universal | NIST
800-53 rev4
\[low\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (low baseline) | 4 |
| Universal | NIST
800-53 rev4
\[moderate\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (moderate baseline) | 4 |
| Universal | NIST
800-53 rev4
\[high\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations (high baseline) | 4 |
| Universal | NIST
800-53
rev5 | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations | 5 |
| Universal | NIST
800-53
rev5
\[privacy\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations
Privacy Baseline | 5 |
| Universal | NIST
800-53
rev5
\[low\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations
Low Baseline | 5 |
| Universal | NIST
800-53
rev5
\[moerate\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations
Moderate Baseline | 5 |
| Universal | NIST
800-53
rev5
\[high\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations
High Baseline | 5 |
| Universal | NIST
800-53
rev5
\[NOC\] | NIST | SP 800-53 - Security and Privacy Controls for Information Systems and Organizations
Select Not Otherwise Categorized (NOC) controls | 5 |
| Universal | NIST
800-63B
\[partial mapping\] | NIST | SP 800-63B - Digital Identity Guidelines (partial mapping) | June 2017 |
| Universal | NIST
800-82 rev2
Low Impact
ICS Overlay | NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST
800-82 rev2
Moderate Impact
ICS Overlay | NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST
800-82 rev2
High Impact
ICS Overlay | NIST | NIST SP 800-82 - Guide to Industrial Control Systems (ICS) Security | rev 2 |
| Universal | NIST
800-160 | NIST | NIST SP 800-160 - Systems Security Engineering | N/A |
| Universal | NIST
800-161
rev 1 | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-161
rev 1
C-SCRM Baseline | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-161
rev 1
Flow Down | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-161
rev 1
Level 1 | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-161
rev 1
Level 2 | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-161
rev 1
Level 3 | NIST | NIST SP 800-161 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations | rev 1 |
| Universal | NIST
800-171
rev 2 | NIST | SP 800-171 - Protecting CUI in Nonfederal Systems and Organizations | 2 |
| Universal | NIST
800-171A | NIST | SP 800-171A - Assessing Security Requirements for Controlled Unclassified Information | N/A |
| Universal | NIST
800-172 | NIST | SP 800-172 - Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations: Enhanced Security Requirements for Critical Programs and High Value Assets | N/A |
| Universal | NIST
800-218
v1.1 | NIST | SP 800-218 - Secure Software Development Framework (SSDF) Version 1.1: | v1.1 |
| Universal | NIST
CSF
v1.1 | NIST | Cybersecurity Framework (CSF) | 1.1 (Apr 19) |
| Universal | NIST
CSF
v2.0 IPD | NIST | Cybersecurity Framework (CSF) 2.0 Initial Public Draft (IPD) | 2.0 IPD |
| Universal | OWASP
Top 10
v2021 | OWASP | Top 10 Most Critical Web Application Security Risks | 2021 |
| Universal | PCI DSS
v3.2 | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) | 3.2 |
| Universal | PCIDSS
v4.0 | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) | 4.0 |
| Universal | PCIDSS
v4.0
SAQ A | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ A | 4.0 |
| Universal | PCIDSS
v4.0
SAQ A-EP | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ A-EP | 4.0 |
| Universal | PCIDSS
v4.0
SAQ B | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ B | 4.0 |
| Universal | PCIDSS
v4.0
SAQ B-IP | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ B-IP | 4.0 |
| Universal | PCIDSS
v4.0
SAQ C | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ C | 4.0 |
| Universal | PCIDSS
v4.0
SAQ C-VT | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ C-VT | 4.0 |
| Universal | PCIDSS
v4.0
SAQ D Merchant | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ D Merchant | 4.0 |
| Universal | PCIDSS
v4.0
SAQ D Service Provider | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ D Service Provider | 4.0 |
| Universal | PCIDSS
v4.0
SAQ P2PE | PCI SSC | Payment Card Industry Data Security Standard (PCI DSS) - SAQ P2PE | 4.0 |
| Universal | Shared Assessments SIG 2023 | Shared Assessments | Shared Assessments Standard Information Gathering Questionnaire (SIG) | 2023 |
| Universal | SWIFT
CSF
v2023 | SWIFT | SWIFT Customer Security Controls Framework | 2021 |
| Universal | TISAX
ISA v5.1.0 | TISAX | TISAX ISA | 5.1.0 |
| Universal | UL
2900-1 | UL | 2900-1 - Software Cybersecurity for Network-Connectable Products | N/A |
| Universal | UN
R155 | United Nations | UN Regulation No. 155 | N/A |
| US | US
C2M2
v2.1 | Federal | Cybersecurity Capability Maturity Model v2.1 | 2.1 |
| US | US CERT
RMM
v1.2 | Federal | CERT Resilience Management Model | 1.2 |
| US | US
CISA
CPG
v2022 | Federal | CISA Cross-Sector Cybersecurity Performance Goals (CPG) | 2022 |
| US | US
CJIS Security Policy 5.9 | Federal | US DOJ / FBI - Criminal Justice Information Services (CJIS) Security Policy | 5.9 |
| US | US
CMMC 2.0
Level 1 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US
CMMC 2.0
Level 2 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US
CMMC 2.0
Level 3 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 1.02 |
| US | US
CMMC 2.1 (draft)
Level 1 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US
CMMC 2.1 (draft)
Level 2 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US
CMMC 2.1 (draft)
Level 3 | Federal | Cybersecurity Maturity Model Certification (CMMC) | 2.1 draft |
| US | US
CMS
MARS-E v2.0 | Federal | US Centers for Medicare & Medicaid Services MARS-E Document Suite, Version 2.0 | 2.0 |
| US | US
COPPA | Federal | Children's Online Privacy Protection Act (COPPA) | N/A |
| US | US
DFARS
Cybersecurity | Federal | Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7008 - 7012 | 252.204-7008 |
| US | US
FACTA | Federal | Fair & Accurate Credit Transactions Act (FACTA) / Fair Credit Reporting Act (FCRA) | N/A |
| US | US
FAR
52.204-21 | Federal | Federal Acquisition Regulation (FAR) | 52.204-21 |
| US | US
FAR
Section 889 | Federal | Federal Acquisition Regulation (FAR) - Section 889 | 889 |
| US | US
FDA
21 CFR Part 11 | Federal | Food & Drug Administration (FDA) | 21 CFR Part 11 |
| US | US
FedRAMP | Federal | Federal Risk and Authorization Management Program (FedRAMP) | R4 |
| US | US
FedRAMP
\[low\] | Federal | Federal Risk and Authorization Management Program (FedRAMP) (low baseline) | R4 |
| US | US
FedRAMP
\[moderate\] | Federal | Federal Risk and Authorization Management Program (FedRAMP) (moderate baseline) | R4 |
| US | US
FedRAMP
\[high\] | Federal | Federal Risk and Authorization Management Program (FedRAMP) (high baseline) | R4 |
| US | US
FedRAMP
\[LI-SaaS\] | Federal | Federal Risk and Authorization Management Program (FedRAMP) (Li-SAAS) baseline) | R4 |
| US | US
FedRAMP
R5 | Federal | Federal Risk and Authorization Management Program (FedRAMP) R5 | R5 |
| US | US
FedRAMP
R5
(low) | Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (low baseline) | R5 |
| US | US
FedRAMP
R5
(moderate) | Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (moderate baseline) | R5 |
| US | US
FedRAMP
R5
(high) | Federal | Federal Risk and Authorization Management Program (FedRAMP R5) (high baseline) | R5 |
| US | US
FedRAMP
R5
(LI-SaaS) | Federal | Federal Risk and Authorization Management Program (FedRAM R5P) (Li-SAAS) baseline) | R5 |
| US | US
FERPA | Federal | Family Educational Rights and Privacy Act (FERPA) | N/A |
| US | US
FFIEC | Federal | Federal Financial Institutions Examination Council (FFIEC) | N/A |
| US | US
FINRA | Federal | Financial Industry Regulatory Authority (FINRA) | N/A |
| US | US
FTC Act | Federal | Federal Trade Commission (FTC) Act | N/A |
| US | US
GLBA
CFR 314 | Federal | Gramm Leach Bliley Act (GLBA) | CFR 314 |
| US | US
HIPAA | Federal | Health Insurance Portability and Accountability Act (HIPAA) | N/A |
| US | HIPAA - HICP
Small Practice | Federal | Health Industry Cybersecurity Practices (HICP) - Small Practice | N/A |
| US | HIPAA - HICP
Medium Practice | Federal | Health Industry Cybersecurity Practices (HICP) - Medium Practice | N/A |
| US | HIPAA - HICP
Large Practice | Federal | Health Industry Cybersecurity Practices (HICP) - Large Practice | N/A |
| US | US
IRS 1075 | Federal | Internal Revenue Service (IRS) 1075 | N/A |
| US | ITAR
Part 120
\[limited\] | Federal | International Traffic in Arms Regulation (ITAR) \[limited to Part 120\] | N/A |
| US | US
NERC
CIP | Federal | North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) | N/A |
| US | US
NISPOM | Federal | National Industrial Security Program Operating Manual (NISPOM) | N/A |
| US | US
NNPI
(unclass) | Federal | Naval Nuclear Propulsion Information (NNPI) | N/A |
| US | US
NSTC
NSPM-33 | Federal | National Science & Technology Council (NSTC) NSPM-33 | N/A |
| US | US
Privacy Shield | Federal | Privacy Shield | N/A |
| US | US
SEC
Cybersecurity Rule | Federal | Cybersecurity Final Rule (Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure) - 17 CFR Parts 229, 232, 239, 240, and 249 | N/A |
| US | US
SOX | Federal | Sarbanes Oxley Act (SOX) | N/A |
| US | US
SSA
EIESR
v8.0 | Federal | Social Security Administration (SSA) Electronic Information Exchange Security Requirements | 8.0 |
| US | StateRAMP
Low
Category 1 | State | StateRAMP Low (Category 1) | N/A |
| US | StateRAMP
Low+
Category 2 | State | StateRAMP Low+ (Category 2) | N/A |
| US | StateRAMP
Moderate
Category 3 | State | StateRAMP Moderate (Category 3) | N/A |
| US | US - AK
PIPA | State | AK - Alaska Personal Information Protection Act (PIPA) | N/A |
| US | US - CA
SB327 | State | CA - SB327 | N/A |
| US | US-CA
CPRA
(Nov 2022) | State | California Privacy Rights Act (CPRA) - November 2022 version | November 2022 |
| US | US - CA
SB1386 | State | CA - SB1386 | N/A |
| US | US - CO
Colorado Privacy Act | State | CO - Colorado Privacy Act | N/A |
| US | US - IL
BIPA | State | Illinois Biometric Information Privacy Act (PIPA) | N/A |
| US | US - IL
IPA | State | Illinois Identity Protection Act (IPA) | N/A |
| US | US - IL
PIPA | State | IL - Illinois Personal Information Protection Act (PIPA) | N/A |
| US | US - MA
201 CMR 17.00 | State | MA - 201 CMR 17.00 | N/A |
| US | US - NV
SB220 | State | NV - SB220 | N/A |
| US | US - NY
DFS
23 NYCRR500 | State | NY - NY DFS 23NYCRR500 | N/A |
| US | US - NY
SHIELD Act
S5575B | State | NY - SHIELD Act (SB S5575B) | N/A |
| US | US - OR
646A | State | OR - ORS 646A | N/A |
| US | US - SC
Insurance Data Security Act | State | SC - South Carolina Insurance Data Security Act | N/A |
| US | US - TX
BC521 | State | TX - BC521 | N/A |
| US | US-TX
Cybersecurity Act | State | TX - Cybersecurity Act | N/A |
| US | US-TX DIR Control Standards 2.0 | State | TX - DIR Security Control Standards Catalog | 2.0 |
| US | US-TX
TX-RAMP | State | TX - Texas Risk & Authorization Management Program (TX-RAMP) | N/A |
| US | US-TX
SB820 | State | TX - 2019 - SB820 | N/A |
| US | US-VA
CDPA
2023 | State | Virginia Consumer Data Protection Act | 2023 |
| US | US-VT
Act 171 of 2018 | State | VT - Act 171 of 2018 (Data Broker Registration Act) | N/A |
| EMEA | EMEA
EU
EBA
GL/2019/04 | EU | European Banking Authority (EBA) Guidelines on ICT and security risk management | N/A |
| EMEA | EMEA
EU
DORA | EU | EU Digital Operational Resilience Act (DORA) | 2023 |
| EMEA | EMEA
EU ePrivacy
\[draft\] | EU | ePrivacy Directive | draft |
| EMEA | EMEA
EU
GDPR | EU | General Data Protection Regulation (GDPR) | N/A |
| EMEA | EMEA
EU
NIS2 | EU | ENISA NIS2 (Directive (EU) 2022/2555) | N/A |
| EMEA | EMEA
EU
PSD2 | EU | Second Payment Services Directive (PSD2) | N/A |
| EMEA | EMEA
EU
EU-US Data Privacy Framework | EU | EU-US Data Privacy Framework | N/A |
| EMEA | EMEA
Austria | Austria | Federal Act concerning the Protection of Personal Data (DSG 2000) | N/A |
| EMEA | EMEA
Belgium | Belgium | Act of 8 December 1992 | N/A |
| EMEA | EMEA
Czech Republic | Czech Republic | Act No. 101/2000 on the Protection of Personal Data | N/A |
| EMEA | EMEA
Denmark | Denmark | Act on Processing of Personal Data (Act No. 429 of May 31, 2000) | N/A |
| EMEA | EMEA
Finland | Finland | Personal Data Act (986/2000) | N/A |
| EMEA | EMEA
France | France | 78 17 / 2004 8021 - Information Technology, Data Files & Civil Liberty | N/A |
| EMEA | EMEA
Germany | Germany | Federal Data Protection Act | N/A |
| EMEA | EMEA
Germany
C5:2020 | Germany | Cloud Computing Compliance Controls Catalogue (C5) | 2020 |
| EMEA | EMEA
Greece | Greece | Protection of Individuals with Regard to the Processing of Personal Data (2472/1997) | N/A |
| EMEA | EMEA
Hungary | Hungary | Informational Self-Determination and Freedom of Information (Act CXII of 2011) | N/A |
| EMEA | EMEA
Ireland | Ireland | Data Protection Act (2003) | N/A |
| EMEA | EMEA
Israel
CDMO
v1.0 | Israel | Cybersecurity Methodology for an Organization | 1.0 |
| EMEA | EMEA
Israel | Israel | Protection of Privacy Law, 5741 – 1981 | N/A |
| EMEA | EMEA
Italy | Italy | Personal Data Protection Code | N/A |
| EMEA | EMEA
Kenya
DPA 2019 | Kenya | Kenya Data Protection Act | 2019 |
| EMEA | EMEA
Luxembourg | Luxembourg | Protection of Personals with Regard to the Processing of Personal Data | N/A |
| EMEA | EMEA
Netherlands | Netherlands | Personal Data Protection Act | N/A |
| EMEA | EMEA
Nigeria
DPR 2019 | Nigeria | Nigeria Data Protection Regulation | 2019 |
| EMEA | EMEA
Norway | Norway | Personal Data Act | N/A |
| EMEA | EMEA
Poland | Poland | Act of 29 August 1997 on the Protection of Personal Data | N/A |
| EMEA | EMEA
Portugal | Portugal | Act on the Protection of Personal Data | N/A |
| EMEA | EMEA
Qatar
PDPPL | Qatar | Personal Data Privacy Protection Law (PDPPL) | N/A |
| EMEA | EMEA
Russia | Russia | Federal Law of 27 July 2006 N 152-FZ | N/A |
| EMEA | EMEA
Saudi Arabia
Critical Security Controls | Saudi Arabia | Saudi Arabian Monetary Authority - Cyber Security Framework | Version 1.0
(May 2017) |
| EMEA | EMEA
Saudi Arabia
SACS-002 | Saudi Arabia | SACS-002 - Third Party Cybersecurity Standard | N/A |
| EMEA | EMEA
Saudi Arabia
SAMA CSFv1.0 | Saudi Arabia | Saudi Arabian Monetary Authoirty (SAMA) Cyber Security Framework (CSF) | 2017 v1 |
| EMEA | EMEA
Saudi Arabia
ECC-1 2018 | Saudi Arabia | Essential Cybersecurity Controls (ECC – 1 : 2018) | 2018 |
| EMEA | EMEA
Saudi Arabia
OTCC-1 2022 | Saudi Arabia | Operational Technology Cybersecurity Controls (OTCC -1: 2022) | 2022 |
| EMEA | EMEA
Serbia
87/2018 | Servia | Act of 9 November 2018 on Personal Data Protection (Official Gazette No. 87/18) | N/A |
| EMEA | EMEA
Slovak Republic | Slovak Republic | Protection of Personal Data (122/2013) | N/A |
| EMEA | EMEA
South Africa | South Africa | Protection of Personal Information Act (POPIA) | N/A |
| EMEA | EMEA
Spain | Spain | Royal Decree 1720/2007 (protection of personal data) | N/A |
| EMEA | EMEA
Spain
CCN-STIC 825 | Spain | ICT Security Guide CCN-STIC 825 | N/A |
| EMEA | EMEA
Sweden | Sweden | Personal Data Act | N/A |
| EMEA | EMEA
Switzerland | Switzerland | Federal Act on Data Protection (FADP) | N/A |
| EMEA | EMEA
Turkey | Turkey | Regulation on Protection of Personal Data in Electronic Communications Sector | N/A |
| EMEA | EMEA
UAE | UAE | Data Protection Law No. 1 of 2007 | N/A |
| EMEA | EMEA
UK
CAF v3.1 | United Kingdom | Cyber Assessment Framework | 3.1 |
| EMEA | EMEA
UK
CAP 1850 | United Kingdom | Cyber Assessment Framework (CAF) for Aviation Guidance (CAP1850) | N/A |
| EMEA | EMEA
UK
Cyber Essentials | United Kingdom | Cyber Essentials | N/A |
| EMEA | EMEA
UK
DPA | United Kingdom | Data Protection Act | N/A |
| EMEA | EMEA
UK
GDPR | United Kingdom | UK General Data Protection Regulation | N/A |
| APAC | APAC
Australia
Essential 8
ML 1 | Australia | Australia Essential Eight | N/A |
| APAC | APAC
Australia
Essential 8
ML 2 | Australia | Australia Essential Eight | N/A |
| APAC | APAC
Australia
Essential 8
ML 3 | Australia | Australia Essential Eight | N/A |
| APAC | APAC
Australia
Privacy Act | Australia | Privacy Act of 1998 | N/A |
| APAC | APAC
Australia
ISM 2022 | Australia | Australian Government Information Security Manual (ISM) | December 2022 |
| APAC | APAC
Australia
IoT Code of Practice | Australia | Australia - Code of Practice - Securing the Internet of Things for Consumers | N/A |
| APAC | APAC
Australia
Prudential Standard CPS 234 | Australia | Prudential Standard CPS 234 Information Security | N/A |
| APAC | APAC
Australia
Privacy Principles | Australia | Australia Privacy Principles | N/A |
| APAC | APAC
China
DNSIP | China | Decision on Strengthening Network Information Protection | N/A |
| APAC | APAC
Hong Kong | Hong Kong | Personal Data Ordinance | N/A |
| APAC | APAC
India
ITR | India | Information Technology Rules (Privacy Rules) | N/A |
| APAC | APAC
Indonesia | Indonesia | Government Regulation No. 82 of 2012 | N/A |
| APAC | APAC
Japan
APPI | Japan | Act on the Protection of Personal Information | June 2020 |
| APAC | APAC
Japan
ISMAP | Japan | Japan Information System Security Management and Assessment Program (ISMAP) | N/A |
| APAC | APAC
Malaysia | Malaysia | Personal Data Protection Act of 2010 | N/A |
| APAC | APAC
New Zealand Health ISF | New Zealand | NZ Health Information Security Framework | N/A |
| APAC | APAC
New Zealand
NZISM 3.6 | New Zealand | New Zealand Information Security Manual (NZISM) | 3.6 |
| APAC | APAC
New Zealand Privacy Act of 2020 | New Zealand | Privacy Act of 2020 | 2020 |
| APAC | APAC
Philippines | Philippines | Data Privacy Act of 2012 | N/A |
| APAC | APAC
Singapore | Singapore | Personal Data Protection Act of 2012 | N/A |
| APAC | APAC
Singapore
Cyber Hygiene Practice | Singapore | Cyber Hygiene Practice | N/A |
| APAC | APAC
Singapore MAS
TRM 2021 | Singapore | Monitory Authority of Singapore (MAS) Technology Risk Management (TRM) Guidelines | 2021 |
| APAC | APAC
South Korea | South Korea | Personal Information Protection Act | N/A |
| APAC | APAC
Taiwan | Taiwan | Personal Data Protection Act | N/A |
| Americas | Americas
Argentina | Argentina | Protection of Personal Law No. 25,326 | N/A |
| Americas | Americas
Argentina
Reg 132/2018 | Argentina | Protection of Personal Data - MEN-2018-147-APN-PTE | N/A |
| Americas | Americas
Bahamas | Bahamas | Data Protection Act | N/A |
| Americas | Americas
Bermuda
BMA CCC | Bermuda | Bermuda Monetary Authority Cyber Code of Conduct | N/A |
| Americas | Americas
Brazil | Brazil | General Data Protection Law (LGPD) | N/A |
| Americas | Americas
Canada
CSAG | Canada | Office of the Superintendent of Financial Institutions Canada (OSFI) - Cyber Security Self-Assessment Guidance | N/A |
| Americas | Americas
Canada
OSFI B-13 | Canada | B-13 | N/A |
| Americas | Americas
Canada
PIPEDA | Canada | Personal Information Protection and Electronic Documents Act (PIPEDA) | N/A |
| Americas | Americas
Chile | Chile | Act 19628 - Protection of Personal Data | N/A |
| Americas | Americas
Colombia | Colombia | Law 1581 of 2012 | N/A |
| Americas | Americas
Costa Rica | Costa Rica | Protection of the Person in the Processing of His Personal Data | N/A |
| Americas | Americas
Mexico | Mexico | Federal Law on Protection of Personal Data held by Private Parties | N/A |
| Americas | Americas
Peru | Peru | Personal Data Protection Law | N/A |
| Americas | Americas
Uruguay | Uruguay | Law No. 18,331 - Protection of Personal Data and Action "Habeas Data" | N/A |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=jk2bybu1hs4n)
#### 4 Reviews [Hide Reviews\ \ Show Reviews](https://complianceforge.com/product/comprehensive-digital-security-program/\#productReviews-content)
- The power of the DSP is its straightforward, streamlined elegance. Highly recommend!
- Recently purchased the DSP package since we are an international organization who have numerous compliance requirements including military/government. We are very please with the documentation and level of detail that has been provided. It will most certainly save us money in the long run and will get us up to speed quicker than had we manually created everything from scratch.
- No one else is doing this. Does it for the most popular Frameworks. Highly recommended. Prompt service and customer support. Through and systematic subject treatment. Links to Standards, Baselines and Controls.
- Recently purchased DSP and supplemental documentation and very satisfied with the contents.
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
niac compliant forging, digital security controls, dsp security, comprehensive digital security plan, custom security program, comprehensive security program, digital security policy, scf trm, dsp full form
[iframe](https://www.google.com/recaptcha/api2/bframe?hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz)
## Data Privacy Program
[Skip to main content](https://complianceforge.com/product/data-privacy-program-dpp/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/329/1453/P10-DPP__72282.1740598475.png?c=2)
No reviews yet
$3,300.00
(You save)
# Data Privacy Program (DPP)
SKU:P10-DPP-NOUPC:692878856898Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Affordable%20Data%20Privacy%20Program%20(DPP)%20for%20Compliance%20Success&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fdata-privacy-program-dpp%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fdata-privacy-program-dpp%2F&title=Affordable%20Data%20Privacy%20Program%20(DPP)%20for%20Compliance%20Success&summary=Affordable%20Data%20Privacy%20Program%20(DPP)%20for%20Compliance%20Success&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fdata-privacy-program-dpp%2F "Linkedin")
[](https://complianceforge.com/product/data-privacy-program-dpp/#examples)
## Data Privacy Program (DPP) - Editable Privacy Program Template
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the DPP is to help answer common questions we receive.
[](https://complianceforge.com/data-privacy-program/ "Watch Video")
[View Product Video](https://complianceforge.com/data-privacy-program/)
## What Is The Data Protection Program (DPP)?
The Data Privacy Program (DPP) is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers. The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD). ComplianceForge designed the DPP for cybersecurity and privacy personnel who are tasked with "privacy compliance" for their organization. This involves advising privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. If you take a look through the table of contents in the example listed below, you will see coverage for reasonable privacy program expectations:
- Stakeholder identification and accountability structure
- Applicable privacy-specific laws, regulations and frameworks
- Concept of Operations (CONOPS) - mission, vision, strategy and multi-year roadmap to operationalize the privacy program
- Targeted privacy maturity level
- Organization-specific criteria to meet privacy management principles
- Data classification and handling guidelines
- And more!
The DPP is a one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The DPP is capable of scaling for any sized company.
- The DPP is an editable Microsoft Word document that providers program-level guidance to directly supports your company's policies and standards for ensuring secure engineering and privacy principles are operationalized.
- This product addresses the “how?” questions for how your company ensures privacy principles are operationalized.
## What Problems Does The DPP Solve?
- Lack of In House Security Experience \- Writing cybersecurity & privacy documentation is a skill that most cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive data privacy documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The DPP is an efficient method to obtain comprehensive guidance documentation to implement privacy principles within your organization!
- Compliance Requirements \- Requirements such as EU GDPR require companies that store, process or transmit the personal data of EU citizens to ensure that both cybersecurity and privacy principles are built into processes by default. Can you prove how privacy principles are implemented at your organization?
- Audit Failures \- Cybersecurity and privacy documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The DPP provide mapping to leading privacy frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements \- It is becoming more common for clients and partners to request evidence of a privacy program and this includes policies, standards and procedures. With EU GDPR, vendors and other partners will be expected to demonstrate evidence of compliance with the EU GDPR.
## How Does The DPP Solve These Problems?
- Clear Documentation \- The DPP provides a comprehensive approach to operationalizing privacy principles. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings \- The DPP can provide your organization with a templated solution that requires minimal resources to fine tune for your organization's specific privacy needs.
- Alignment With Leading Practices - The DPP is written to support leading cybersecurity and privacy frameworks!
The DPP is a "Rosetta Stone" approach to privacy principles. Based on our experience, we understand that most smaller-to-medium-sized businesses lack the knowledge and experience to undertake such privacy program documentation efforts. That means businesses are faced to either outsource the work to expensive privacy consultants, write it themselves or ignore the requirement in hopes of not getting in trouble for being non-compliant. To solve this issue, ComplianceForge chose to leverage the [Secure Controls Framework Data Privacy Management Principles (SCF DPMP)](https://securecontrolsframework.com/data-privacy-management-principles/ "Secure Controls Framework Data Privacy Management Principles (SCF DPMP)") as an efficient way to align with an assortment of "privacy principles" that organizations are faced with.
When you look at a comparison of privacy-relevant laws, regulations and frameworks, you will see a wide variety of expectations. The SCF DPMP's solution to the apples-to-oranges comparison was to create a metaframework of privacy principles that covers nineteen (19) privacy frameworks to provide the ability to demonstrate adherence to multiple privacy principles.
[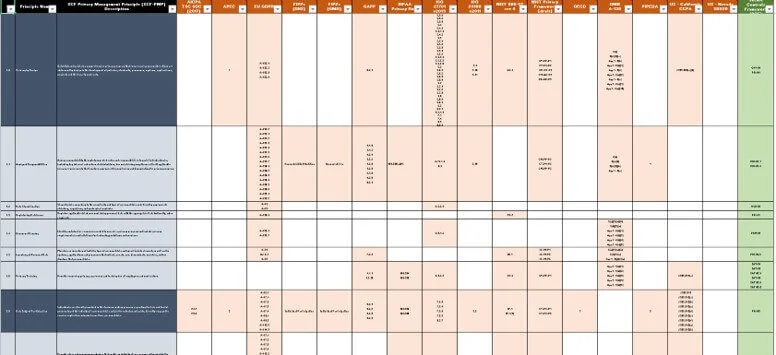](https://securecontrolsframework.com/data-privacy-management-principles/ "SCF Privacy Management Principles")
The SCF DPMP is a “Rosetta Stone” of data privacy management principles that maps to the following privacy practices:
01. AICPA’s Trust Services Criteria ( **TSC**) (2017)
02. Asia-Pacific Economic Cooperation ( **APEC**)
03. California Privacy Rights Act ( **CPRA**)
04. European Union General Data Protection Regulation ( **EU GDPR**)
05. Fair Information Practice Principles - Department of Homeland Security ( **DHS FIPPs**)
06. Fair Information Practice Principles - Office of Management and Budget ( **OMB FIPPs**)
07. Generally Accepted Privacy Principles ( **GAPP**)
08. HIPAA Privacy Rule
09. ISO/IEC 27701:2019
10. ISO/IEC 29100:2011
11. Nevada SB820
12. NIST SP 800-53 R4
13. NIST SP 800-53 R5
14. NIST Privacy Framework v1.0
15. OASIS Privacy Management Reference Model ( **PMRM**)
16. Organization for Economic Co-operation and Development ( **OECD**)
17. Office of Management and Budget ( **OMB**) \- Circular A-130
18. Personal Information Protection and Electronic Documents Act ( **PIPEDA**)
19. Privacy by Design ( **PbD**) – The 7 Foundational Principles
## Product Example - Data Privacy Program (DPP)
The DPP addresses program-level guidance on HOW to actually manage privacy principles, so that secure processes are designed and implemented across your organizationt. Policies & standards are absolutely necessary to an organization, but they fail to describe HOW privacy principles are actually planned and managed. The DPP provides this middle ground between high-level policies and the actual procedures of how developers, PMs, system integrators and system admins do their jobs to design, implement and maintain technology solutions while applying applicable data protection controls in their day-to-day operations.
**View Product Example**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-dpp-data-protection-program.pdf "security and privacy by design - operationalize privacy by design and security by design") |
## Cost Savings Estimate - Data Protection Program (DPP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DPP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 120 internal staff work hours, which equates to a cost of approximately **$20,000** in staff-related expenses. This is about 4-8 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 80 consultant work hours, which equates to a cost of approximately **$39,000**. This is about 2-3 months of development time for a contractor to provide you with the deliverable.
- The DPP is approximately 8% of the cost for a consultant or 17% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the DPP the same day you place your order.
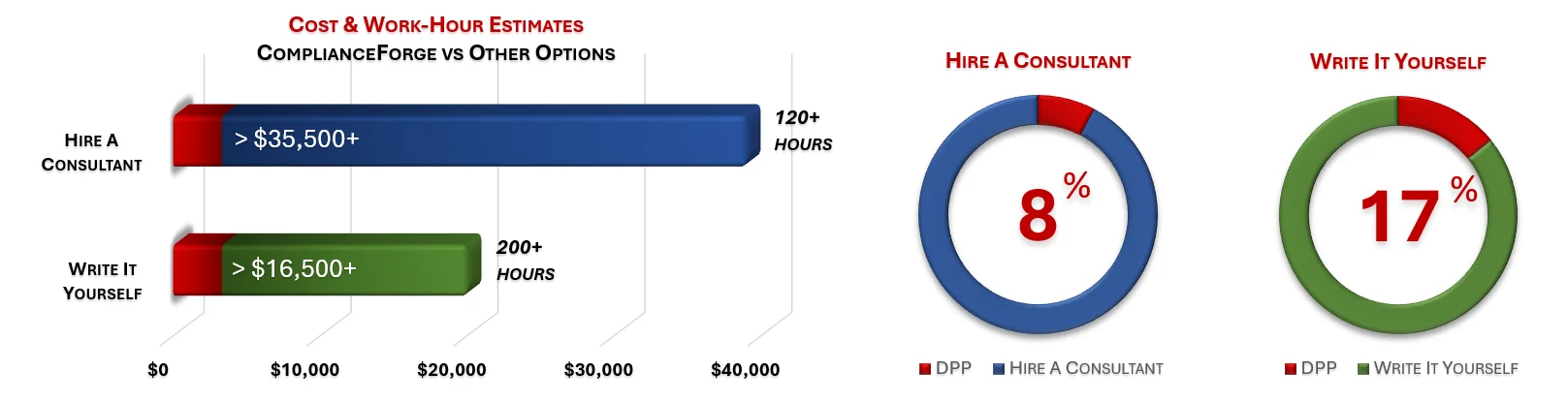
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Cybersecurity By Design & Data Privacy By Design - Data Protection Program Documentation
| | | |
| --- | --- | --- |
| ## 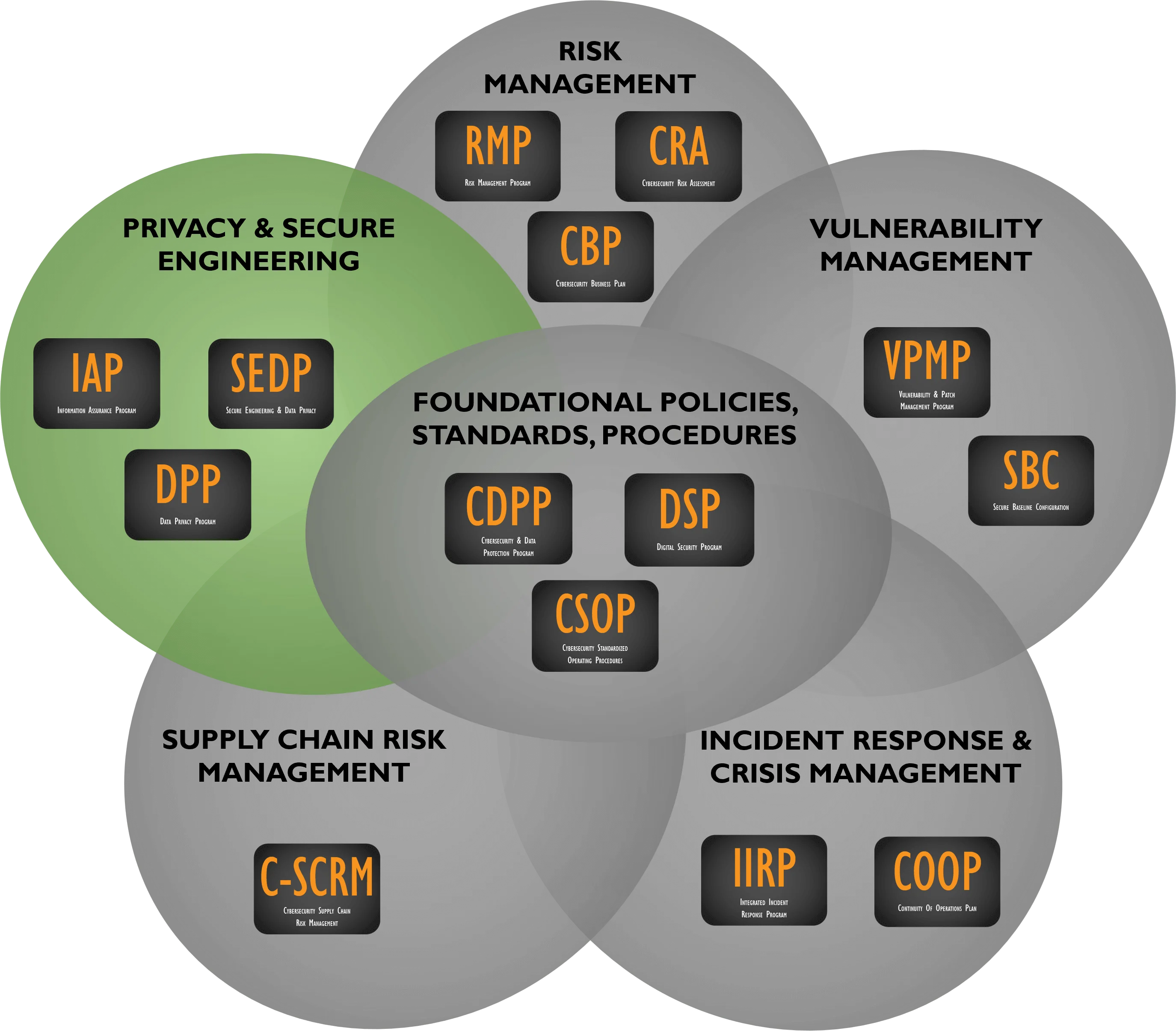 | | The DPP can serve as a foundational element in your organization's privacy program. It can stand alone or be paired with other specialized products we offer.
Cybersecurity and privacy do not need to be hard. The **Security Engineering & Data Privacy (SEDP)** document is meant to simplify how security and privacy can be operationalized in a “paint by numbers” approach. This product is comprised of editable Microsoft Word and Excel documentation so you can customize it for your specific needs.
Please keep in mind that security & privacy engineering principles are widely expected activities:
- European Union General Data Protection Regulation (EU GDPR)
- NIST 800-53
- NIST Cybersecurity Framework
- ISO 27002
- Defense Federal Acquisition Regulations Supplement (DFARS) 252.204-7012 (NIST 800-171)
- Federal Acquisition Regulations (FAR) 52.204-21 - 4
- National Industrial Security Program Operating Manual (NISPOM)
- SOC2
- New York State Department of Financial Service (DFS)
- Payment Card Industry Data Protection Standard (PCI DSS)
- Center for Internet Security Critical Security Controls (CIS CSC)
- Generally Accepted Privacy Principles (GAPP) |
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=ogtd1pwi6ct0)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
privacy program development, data protection program, data privacy program, gdpr dpp solutions, privacy program management, dpp, data privacy compliance program
## NIST CSF Procedures Template
[Skip to main content](https://complianceforge.com/product/nist-csf-procedures-csop/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/326/1450/P12-P13-CSOP__95252.1740598471.png?c=2)
No reviews yet
$4,700.00
(You save)
# Procedures Template - NIST CSF 2.0
SKU:P12-CSOP-CDPP-CSF-NOUPC:692878857208Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Editable%20NIST%20CSF%202.0%20Procedures%20Compliance%20Template&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fnist-csf-procedures-csop%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fnist-csf-procedures-csop%2F&title=Editable%20NIST%20CSF%202.0%20Procedures%20Compliance%20Template&summary=Editable%20NIST%20CSF%202.0%20Procedures%20Compliance%20Template&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fnist-csf-procedures-csop%2F "Linkedin")

[](https://complianceforge.com/product/nist-csf-procedures-csop/#examples)
## Cybersecurity Standardized Operating Procedures (CSOP) NIST Cybersecurity Framework 2.0
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CSOP is to help answer common questions we receive.
[](https://complianceforge.com/what-is-the-nist-csf-version-of-the-csop/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-nist-csf-version-of-the-csop/)
## What Is The Cybersecurity Standardized Operating Procedures (CSOP)?
The CSOP contains editable procedure statements in an editable Microsoft Word format:
- The CSOP addresses the “how?” questions in an audit, since procedures provide the means for how your organization's policies and standards are actually implemented.
- The CSOP provides the underlying cybersecurity procedures that must be documented, as may be stipulated by statutory, regulatory and contractual requirements.
- The procedure statements in the CSOP can be cut & pasted into other tools (e.g., wiki page) or left in a single document. There is no wrong answer for how procedures are maintained, since every organization is unique in the tools used and the location of users.
Given the difficult nature of writing templated procedure statements, we aimed for approximately a **"80% solution"** since it is impossible to write a 100% complete cookie cutter procedure statement that can be equally applied across multiple organizations. What this means is ComplianceForge did the heavy lifting and you just need to fine-tune the procedure with the specifics that only you would know to make it applicable to your organization. It is pretty much filling in the blanks and following the helpful guidance that we provide to identify the who / what / when / where / why / how to make it complete.
Take a look at the example to see for yourself. We even provide a matrix to help identify the likely stakeholders for these procedures.

Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product!
## What Problems Does The CSOP Solve?
- Lack of In House Security Experience - Writing cybersecurity procedures is a skill that most cybersecurity professionals simply are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive procedure documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The CSOP is an efficient method to obtain comprehensive security procedures for your organization!
- Compliance Requirements \- Nearly every organization, regardless of industry, is required to have formally-documented security procedures. Requirements range from PCI DSS to HIPAA to NIST 800-171. The CSOPis designed with compliance in mind, since it focuses on leading security frameworks to address reasonably-expected security requirements.
- Audit Failures - Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. The CSOP's procedures provide mapping to leading security frameworks to show you exactly what is required to both stay secure and compliant.
- Vendor Requirements - It is very common for clients and partners to request evidence of a security program and this includes policies, standards and procedures.
Our customers choose the **CDPP Cybersecurity Standardized Operating Procedures (CSOP)** because they:
- Have a need for comprehensive cybersecurity procedures to address their compliance needs.
- Need to be able to edit the document to their specific technology, staffing and other considerations.
- Have documentation that is directly linked to leading frameworks (e.g., NIST 800-53, NIST 800-171, ISO 27002, HIPAA and others).
- Need an affordable and timely solution to address not having procedures.
## How Does The CSOP Solve These Problems?
- Clear Documentation - The CSOP provides a comprehensive template for your procedures to help prove that your security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings - The CSOP can provide your organization with a templated solution that requires minimal resources to fine tune for your organization's specific procedural needs.
- Alignment With Leading Practices - The CSOP is written to support over two dozen leading frameworks!
Until now, developing a template to provide worthwhile cybersecurity procedures is somewhat of a "missing link" within the cybersecurity documentation industry. The good news is that ComplianceForge solved this issue with the **Cybersecurity Standardized Operating Procedures (CSOP)** product. We are the only provider to have an affordable and comprehensive procedures template! Our CSOP can save a business several hundred hours of work in developing control activities / procedure statements, so the CSOP is worth checking out! The focus of a control activity is to mitigate risks and assist in compliance with cybersecurity policies, while the CSOP procedure statements assist in the implementation of cybersecurity policies & standards to create secure baseline configurations that enhance the cybersecurity stance of the organizaion.
## Comprehensive NIST Cybersecurity Framework 2.0 Procedures Template
We currently offer several versions of the CSOP.
- There is a Digital Security Program (DSP) version that is tailored for the DSP and the Secure Controls Framework.
- There are four Cybersecurity & Data Protection Program (CDPP) versions:
- **[NIST Cybersecurity Framework](https://complianceforge.com/product/iso-27002-procedures-csop/ "NIST Cybersecurity Framework")**
- **[ISO 27001 / 27002](https://complianceforge.com/product/nist-800-53-moderate-procedures-csop/ "ISO 27001 / 27002")**
- **[NIST 800-53 rev5 (low & moderate baselines)](https://complianceforge.com/standardized-operating-procedures/ "NIST 800-53 rev5 (Low & Moderate)")**
- **[NIST 800-53 rev5 (low, moderate & high baselines)](https://complianceforge.com/procedures-nist-800-53-fedramp-high/ "NIST 800-53 rev5 (Low, Moderate & High)")**
Identifying the right one is pretty straightforward, since if you purchase the DSP, you will want the DSP version. If you purchase a CDPP, you just order the version of the CSOP that corresponds to the version of the CDPP you purchased. The main differences are around content, where we tailor the content to meet the framework's coverage. If that is confusing, please give us a call and we can help explain the differences.
## Procedures Operationalize Policies & Standards - This Is A Key Concept To Being Both Secure & Compliant
We leverage the [Operationalizing Cybersecurity Planning Model](https://complianceforge.com/free-guides/operationalizing-cybersecurity-planning-model "Operationalizing Cybersecurity Planning Model") in creating a practical view towards implementing cybersecurity requirements. Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know (1) how they fit into day-to-day operations, (2) what their priorities are and (3) what is expected from them in their duties. When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve.
One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.).
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations.
- Procedures are by their very nature de-centralized, where control implementation at the team-level is defined to explain how the control is addressed (e.g., network team, desktop support, HR, procurement, etc.).
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.

The central focus of any procedure should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. **SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.**
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:

## Product Example - CSOP (NIST CSF Procedures)
Our customers choose the framework-specific **Cybersecurity Standardized Operating Procedures (CSOP)** because they:
- Have a need for comprehensive cybersecurity procedures to address their compliance needs.
- Need to be able to edit the document to their specific technology, staffing and other considerations.
- Have documentation that is directly linked to NIST 800-53, NIST 800-171, ISO 27002, HIPAA and other frameworks.
- Need an affordable and timely solution to address not having procedures.
Don't take our word for it - take a look at the example below to see for yourself the level of professionalism and detail that went into it.
**View Product Example**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-csop-nist-cybersecurity-framework-csf-procedures.pdf "nist cybersecurity framework procedures example") |
## Cost Savings Estimate - Cybersecurity Standardized Operating Procedures (CSOP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CDPP CSOP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 680 internal staff work hours, which equates to a cost of approximately **$60,000** in staff-related expenses. This is about 6-18 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 400 consultant work hours, which equates to a cost of approximately **$130,000**. This is about 3-6 months of development time for a contractor to provide you with the deliverable.
- The CDPP CSOP is approximately 4% of the cost for a consultant or 8% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CDPP CSOP the same day you place your order.
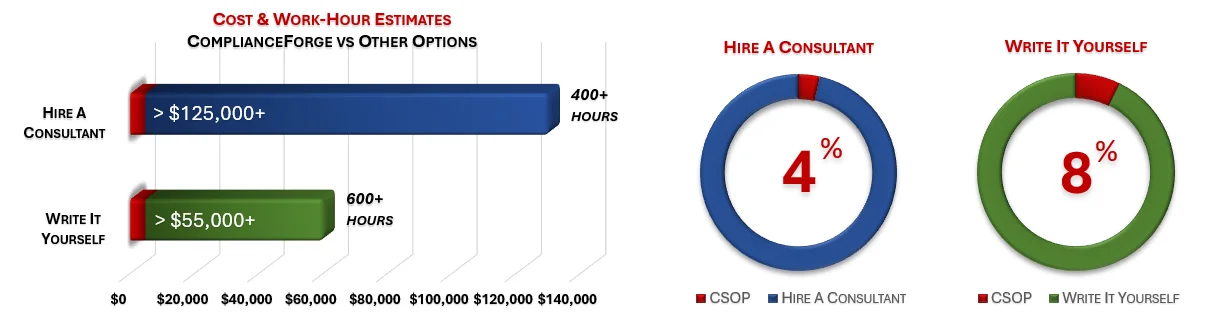
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Alignment With The NIST NICE Framework
One very special aspect of the CDPP and DSP versions of the CSOP is that it leverages the **NIST NICE Cybersecurity Workforce Framework**. NIST released the NICE framework in 2017 with purpose of streamlining cybersecurity roles and responsibilities. We adopted this in the CSOP framework since work roles have a direct impact procedures. By assigning work roles, the CSOP helps direct the work of employees and contractors to minimize assumptions about who is responsible for certain cybersecurity and privacy tasks.

The CSOP uses the work roles identified in the NIST NICE Cybersecurity Workforce Framework to help make assigning the tasks associated with procedures/control activities more efficient and manageable. Keep in mind these are merely recommendations and are fully editable for every organization – this is just a helpful point in the right direction!
The CSOP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer.
At the heart of it, the CSOP provides an organization with clear cybersecurity procedures that can scale to meet the needs and complexity of any team. The procedures are mapped to leading frameworks, so it is straightforward to have procedures that directly link to requirements from NIST 800-171, ISO 27002, NIST 800-53 and many other common cybersecurity and privacy-related statutory, regulatory and contractual frameworks!
The value of the CSOP comes from having well-constructed procedure statements that can help you become audit ready in a fraction of the time and cost to do it yourself or hire a consultant to come on-site and write it for you. The entire concept of this cybersecurity procedures template is focused on two things:
1. Providing written procedures to walk your team members through the steps they need to meet a requirement to keep your organization secure; and
2. Help your company be audit ready with the appropriate level of due diligence evidence that allows you to demonstrate your organization meets its obligations.

## What Is The Cybersecurity Standardized Operating Procedures (CSOP)?
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The CDPP versions of the CSOP contains procedure statements in an editable Microsoft Word format:
- The CSOP addresses the “how?” questions in an audit, since procedures provide the means for how your organization's policies and standards are actually implemented.
- The CSOP provides the underlying cybersecurity procedures that must be documented, as many are stipulated by statutory, regulatory and contractual requirements.
- The procedure statements in the CSOP can be cut & pasted into other tools (e.g., wiki page) or left in a single document. There is no wrong answer for how procedures are maintained, since every organization is unique in the tools used and the location of users.
## Standardized Process Criteria - Helps Identify The Who/What/Where/When/How For Procedures
Your customization will be to help "fill in the blanks" with specific process owners, process operators, where additional documentation can be found, applicable service obligations (e.g., SLAs), and what technology/tools your team has available. We've done the heavy lifting and you just need to fill in the blanks.
- **Process Owner**:
- This is name of the individual or team accountable for the procedure being performed.
- Example: Chief Information Security Officer (CISO) / Cybersecurity Director.
- **Process Operator**:
- This is the name of the individual or team responsible to perform the actual task.
- Example: SOC Analyst / Risk Analyst / Network Admin.
- **Occurrence**:
- This is the annual, semi-annual, quarterly, monthly, bi-weekly, weekly, daily, continuous or as needed cadence for how often the procedure needs to be performed.
- Example: Quarterly vulnerability scans / Monthly software patches / Annual risk assessments.
- **Scope of Impact**:
- Purely internal processes;
- Purely external processes (e.g., outsourced vendor processes); or
- Scope covers both internal processes and external ones.
- System;
- Application;
- Process
- Team;
- Department;
- User;
- Client;
- Vendor;
- Geographic region; or
- The entire company
- This is the scope of the procedure:
- It also that affects the potential impact from the process, which can be one or more of the following:
- **Location of Additional Documentation**:
- This is where additional documentation is stored or can be found. You might want to reference a Wiki, SharePoint site, or other documentation repository.
- **Performance Target**:
- This addresses targeted timelines for the process to be completed (e.g., Service Level Agreements).
- Not all processes have SLAs or targeted timelines
- **Technology in Use**:
- Splunk for a Security Incident Event Manager (SIEM) solution to collect logs;
- McAfee ePO for centralized antimalware management; or
- Tripwire Enterprise for File Integrity Monitoring (FIM).
- This addresses the applications/systems/services that are available to perform the procedure.
- Examples:

## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
[iframe](https://www.google.com/recaptcha/api2/anchor?ar=1&k=6LcjX0sbAAAAACp92-MNpx66FT4pbIWh-FTDmkkz&co=aHR0cHM6Ly9jb21wbGlhbmNlZm9yZ2UuY29tOjQ0Mw..&hl=en&v=GUGrl5YkSwqiWrzO3ShIKDlu&size=normal&cb=c0n3uxk1xtbg)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Secure Baseline Configurations
[Skip to main content](https://complianceforge.com/product/secure-baseline-configuration-sbc#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/214/1509/complianceforge-secure-baseline-configurations-sbc__12159.1740599310.jpg?c=2)
No reviews yet
$2,175.00
(You save)
# Secure Baseline Configurations (SBC)
SKU:P16-SBC-NOUPC:692878856966Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Secure%20Baseline%20Configurations%20(SBC)&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fsecure-baseline-configuration-sbc "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fsecure-baseline-configuration-sbc&title=Secure%20Baseline%20Configurations%20(SBC)&summary=Secure%20Baseline%20Configurations%20(SBC)&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fsecure-baseline-configuration-sbc "Linkedin")

[](https://complianceforge.com/product/secure-baseline-configuration-sbc#sbc-example)
## Secure Baseline Configurations For Technology Assets
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the SBC is to help answer common questions we receive.
[](https://complianceforge.com/what-is-the-secure-baseline-configuration-sbc/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-secure-baseline-configuration-sbc/)
## What Is The Secure Baseline Configurations (SBC)?
The **Secure Baseline Configurations (SBC)** is a documentation solution to efficiently document what constitutes a "hardened" system in your organization. This is applicable to operating systems, applications and services.
Many IT and cyber professionals mistakenly focus only on hardening the operating system (e.g., Windows 10) and fail to document all the technology platforms that require secure configurations (e.g., applications, HVAC systems, mobile devices, VoIP, etc.). The SBC does not re-invent the wheel, but leverages leading practices such as **CIS Benchmarks** and **DISA STIGs**. Unless it is a small organization with just a few laptops and a server, it is not feasible to say " _we harden everything according to CIS Benchmarks_". since CIS does not contain a complete coverage for all technology platforms and the same weakness can be said for using the DISA STIGs. This is where the SBC brings together a variety of options for hardening and creating technical security standards that include CIS, DISA, OEM recommendations and more!
## **What Problems Does The SBC Solve?**
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. The CVT is an efficient method to obtain comprehensive system hardening documentation.
- Compliance Requirements \- There are numerous requirements (several listed at the top of this page) that require secure configurations to be developed and implemented. The SBC is designed with compliance in mind, since it focuses on leading "best practices" for securing systems, applications and services to address reasonably-expected security requirements for hardening.
- Audit Failures \- A lack of documented secure hardening requirements is a common audit failure. The SBC covers a wide array of common technologies that can both make an organization secure and compliant.
- Vendor Requirements \- It is very common for clients and partners to request evidence of a security program, including secure configurations. The SBC provides this evidence!
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product!
## **How Does the SBC Solve These Problems?**
- Clear Documentation \- The SBC provides comprehensive hardened baseline configuration documentation to prove that your security is more than just a set of policies and standards.
- Time Savings \- The SBC can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices \- The SBC is written to align your organization with CIS Benchmarks, DISA STIGs and more!
The SBC addresses a common control to reduce risk, the need for ensuring that systems, applications and services are hardened according to recommended practices.
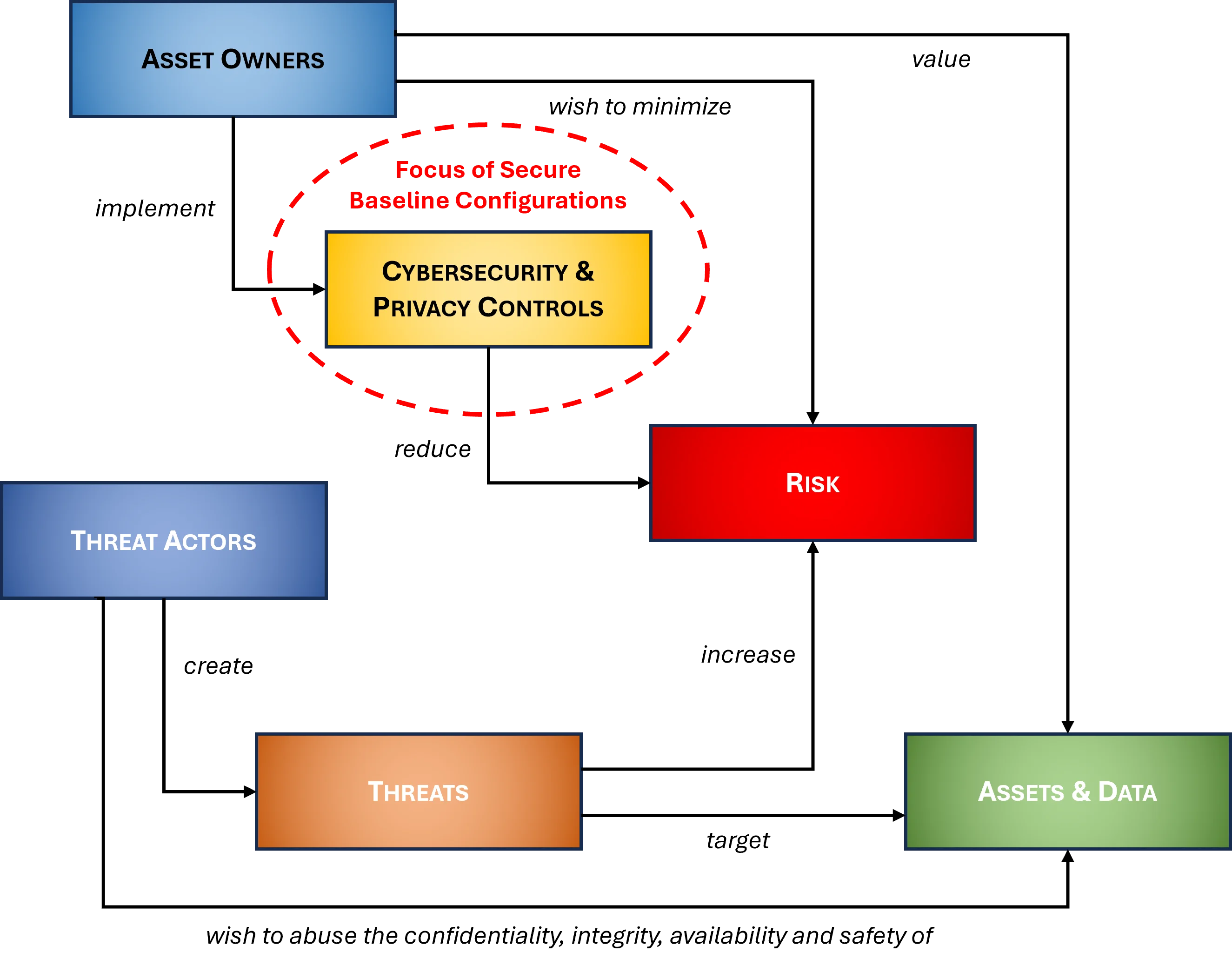
The SBC provides a way to efficiently manage all of these common technology platforms to document and educate system/network admins and other system integrators about what "secure configurations" and "cybersecurity baselines" are at your organization:
- **Server-class systems**
- Microsoft
- Linux
- Unix
- Other
- **Workstation-class systems**
- Microsoft
- Apple
- Linux
- **Network devices**
- Firewalls
- Routers
- Wireless Access Points (WAPs) & controllers
- Multi-Function Devices (MFDs)
- Voice & Video over Internet Protocol (VVoIP)
- **Mobile devices**
- Apple
- Google
- Windows
- **Databases**
- Microsoft SQL
- MySQL
- Oracle
- PostgreSQL
- IBM DB2
- MongoDB
- **Major applications**
- Microsoft Active Directory (AD)
- Microsoft Exchange
- Microsoft SharePoint
- Microsoft Internet Information Services (IIS)
- Domain Naming Services (DNS)
- Apache Tomcat
- Apache HTTP server
- VMware
- Centralized log management (e.g., SIEM)
- Intrusion Detection / Prevention Systems (IDS/IPS)
- **Minor applications**
- Microsoft Office
- Microsoft Internet Explorer (IE)
- Google Chrome
- Mozilla Firefox
- Apple Safari
- Adobe
- AJAX
- .NET
- WordPress
- **Cloud-based applications**
- Microsoft Office 365
- Microsoft Azure
- Amazon Web Services (AWS)
- Google Cloud Computing
- Docker
- Kubernetes
- **Embedded technology**
- Microsoft Windows-based devices
- Heating, Ventilation & Air Conditioning (HVAC)
- Physical Access Control (PAC)
- Video surveillance
- Burglar / fire alarm systems
## Why Should I Buy The SBC? What Actually Requires "Secure Configurations" To Be Documented?
The following are common statutory, regulatory and contractual requirements that expect “secure configurations” or "system hardening" for an organization's technology assets. If your organization is in scope for any of those, you should buy the SBC:
- AICPA Trust Services Principles (TSP) **SOC2** – CC7.1 & CC8.1
- Center for Internet Security Critical Security Controls ( **CIS CSC**) – 5.1, 5.2, 5.3, 5.5, 6.2, 8.3, 8.4, 8.5, 8.6, 9.1, 9.2, 11.1, 14.8, 15.6, 15.7, 15.8 & 15.9
- **COBIT 5** \- BAI10.02
- Cloud Security Alliance Cloud Controls Matrix ( **CSA CCM**) – GRM-01 & IVS-07
- **ISO 27002** – 14.1.1
- Motion Picture Association of America ( **MPAA**) Content Security Program – DS-1.5, DS-1.12, DS-3.3, DS-3.5, DS-3.7, DS-3.8, DS-6.5, DS-6.9, DS-6.10, DS-7.3 & DS-7.8
- **NIST 800-37** \- I-2
- **NIST 800-53** / **FedRAMP** \- CM-2, CM-6 & SA-8
- **NIST 800-160** \- 3.4.7 & 3.4.8
- **NIST 800-171** – 3.4.1 & 3.4.2
- **NIST Cybersecurity Framework** – PR.IP-1 & PR.IP-3
- Payment Card Industry Data Security Standard ( **PCI DSS**) – 1.1, 1.1.1 & 2.2-2.2.4
- National Industry Security Program Operating Manual ( **NISPOM**) – 8-202, 8-311 & 8-610
- Criminal Justice Information Services ( **CJIS**) Security Policy – 5.7.1, 5.7.1.1, 5.7.2 & 5.13.4
- Cloud Computing Compliance Controls Catalog ( **C5**) – RB-22
## Product Example - SBC
When you buy the SBC, you get fully-editable Microsoft Word and Excel documents that you can customize for your specific needs. The example below provides a good look at what you will get when you purchase the SBC.
**View Product Examples**
| |
| --- |
| [](https://complianceforge.com/content/pdf/example-sbc-secure-baseline-configurations.pdf "example system hardening guide secure baseline configurations") |
## Cost Savings Estimate - Secure Baseline Configurations (SBC)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 110 internal staff work hours, which equates to a cost of approximately **$10,000** in staff-related expenses. This is about 1-3 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 60 contractor work hours, which equates to a cost of approximately **$19,500**. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- It is approximately 11% of the cost for a consultant or 22% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the documentation the same day you place your order.
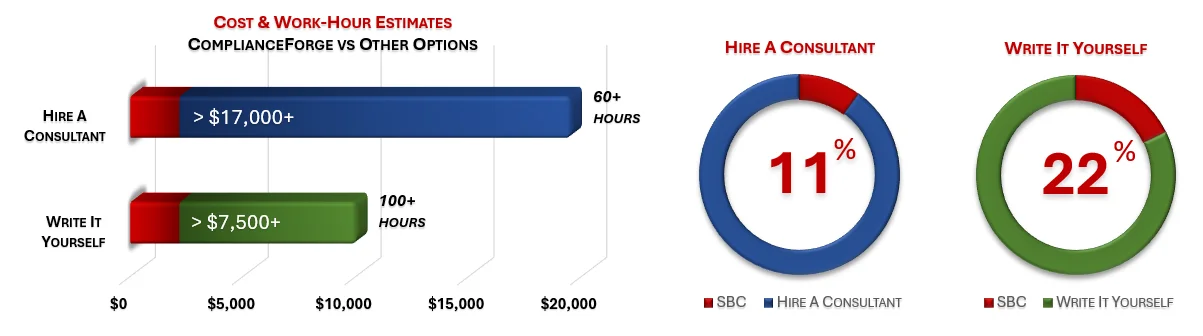
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.
## Reviews
How do you rate this product?
Required
1
2
3
4
5
Write a headline for your review here:
Required
Write your review here:
Required
Enter your name: (optional)
reCAPTCHA
Recaptcha requires verification.
I'm not a robot
reCAPTCHA
[Privacy](https://www.google.com/intl/en/policies/privacy/) \- [Terms](https://www.google.com/intl/en/policies/terms/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
cybersecurity baseline, configuration baseline, baseline configuration, hardening baseline configuration, security baseline, baseline requirements
reCAPTCHA
## C-SCRM Templates
[Skip to main content](https://complianceforge.com/compliance-solutions/tprm-scrm-templates/#main-content)
# Cybersecurity Supply Chain Risk Management (C-SCRM) Templates
ComplianceForge developed an editable template for a C-SCRM strategy and implementation plan that is based on NIST SP 800-161 Rev 1, which is the current "gold standard" for authoritative C-SCRM guidance. This is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the ground running" with C-SCRM operations.

## NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
[NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan "NIST SP 800-161 Rev 1 - Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)") product highlights of the C-SCRM SIP include:
- Country-based risk guidance to determine minimum management decision levels for conducting operations in or contracting with suppliers from countries that pose a legitimate C-SCRM threat.
- The prioritized implementation plan contains mappings for NIST SP 800-161 R1 controls to each C-SCRM implementation phase.
- Professionally-written, editable documentation template that leverages industry-recognized "best practices" for C-SCRM.
- Cost-effective solution to quickly generate documentation for a C-SCRM strategy and implementation plan.
- Example flow-down contract requirements for suppliers, vendors, subcontractors, etc. (DFARS/CMMC, ISO 27001, NIST CSF, NIST 800-53, FAR, PCI DSS, and EU GDPR/CCPA).
To properly manage supply chain-related threats, organizations must evaluate country-based threats posed by its supply chain. This review must cover the geographic concerns where your products, services and support originate from or transit through:
- Transmit, process and/or store your company's or its clients’, data across the SISP's systems, applications and/or services;
- Manufacture products or product components used in your company's operations and/or products; and/or
- Provide services for your company's operations and/or products.
Within the C-SCRM SIP from ComplianceForge, geographic-specific threat management criteria is refined by guidance from:
- Priority Watch List & Watch List
- Corruption Perceptions Index
- Notorious Markets List
- Designated State Sponsors of Terrorism
- EAR / ITAR restrictions
- Potentially hostile data localization laws
## NIST SP 800-161 Rev 1 Cybersecurity Supply Chain Risk Management Strategy & Implementation Plan (C-SCRM SIP)
At the heart of operationalizing C-SCRM is NIST SP 800-161, which is the "gold standard" for C-SCRM practices. ComplianceForge developed an editable template for a C-SCRM Strategy and Implementation Plan (SIP). This is fully-editable documentation (e.g., Word, Excel, PowerPoint, etc.) that can enable your organization to "hit the ground running" with C-SCRM operations that are aligned with **NIST SP 800-161 Rev 1.**
The reality is organizations depend on a global supply chain to provide a variety of products and services that enable the achievement of its strategic and operational objectives. Given the global scope of identifying cybersecurity and data protection risks, threats and vulnerabilities throughout the supply chain are complicated due to the information asymmetry that exists between acquiring enterprises and their suppliers and service providers:
- Acquirers often lack visibility and understanding of how acquired technology is developed, integrated and deployed and how the services that they acquire are delivered.
- Acquirers with inadequate or absent C-SCRM processes, procedures and practices may experience increased exposure cybersecurity risks throughout the supply chain.

ComplianceForge offers two bundles of documentation to address "near turnkey" documentation to operationalize Cybersecurity Supply Chain Risk Management (C-SCRM). Each bundle includes twelve (12) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk Management (C-SCRM):
- Cybersecurity policies & standards (Digital Security Program (DSP) or Cybersecurity Data Protection Program (CDPP) versions)
- Cybersecurity Standardized Operating Procedures (CSOP) (corresponding DSP or CDPP version)
- NIST 800-161 R1-based Cybersecurity Supply Chain Risk Management Strategy and Implementation Plan (CSCRM-SIP)
- Risk Management Program (RMP)
- Cybersecurity Risk Assessment Template (CRA)
- Vulnerability & Patch Management Program (VPMP)
- Integrated Incident Response Program (IIRP)
- Continuity of Operations Plan (COOP)
- Secure Baseline Configurations (SBC)
- Information Assurance Program (IAP)
- Secure Engineering & Data Privacy (SEDP)
- Cybersecurity Business Plan (CBP)
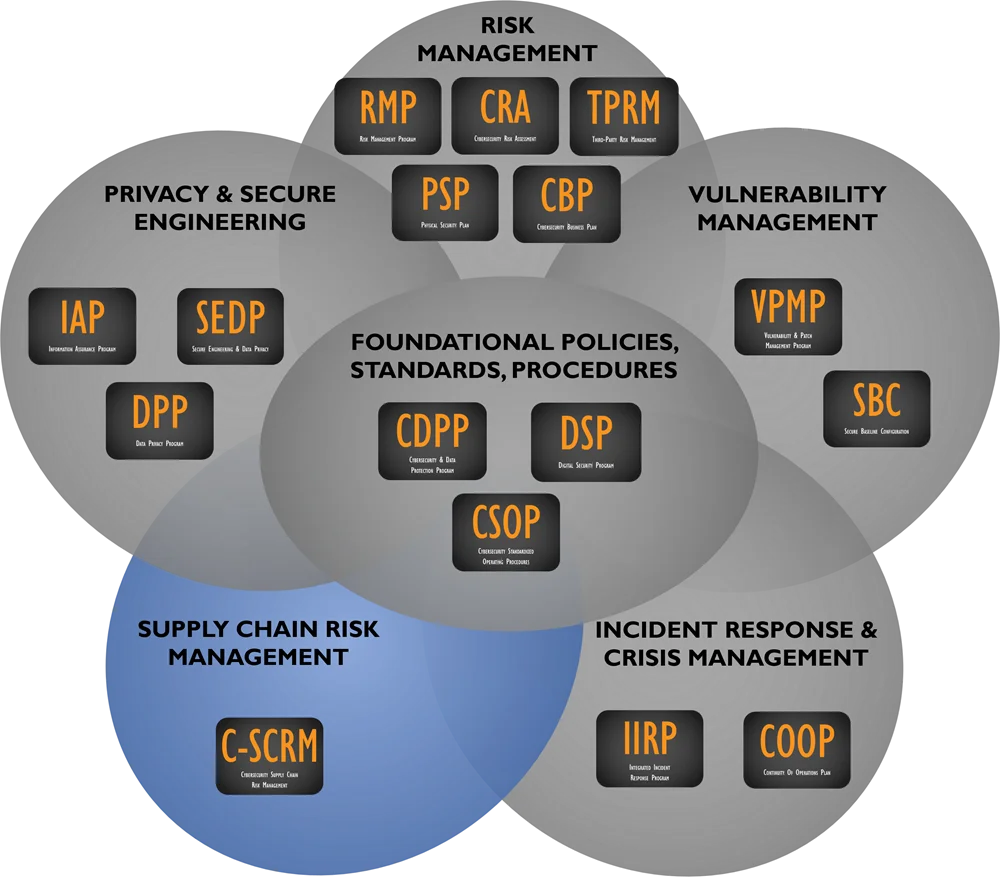
## Browse Our Products
- [](https://complianceforge.com/bundle/c-scrm-bundle-1/)
#### [C-SCRM Bundle 1: CDPP version (ISO or NIST alignment)](https://complianceforge.com/bundle/c-scrm-bundle-1/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #1 - CDPP Version (40% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk...
$39,720.00
$39,720.00
$23,832.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-1/)
- [](https://complianceforge.com/bundle/c-scrm-bundle-2/)
#### [C-SCRM Bundle 2: DSP version (SCF alignment)](https://complianceforge.com/bundle/c-scrm-bundle-2/)
ComplianceForge
Cybersecurity Supply Chain Risk Management (C-SCRM) Bundle #2 - DSP Version (45% discount)
This is a bundle that includes the following thirteen (13) ComplianceForge products that are focused on operationalizing Cybersecurity Supply Chain Risk...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/c-scrm-bundle-2/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## Cybersecurity Risk Management
[Skip to main content](https://complianceforge.com/cybersecurity-templates/cybersecurity-risk-management/#main-content)
# Cybersecurity & Data Privacy Risk Management Templates
Identifying and managing risk is a part of business. We work hard to develop products that assist clients with removing the Fear, Uncertainty & Doubt (FUD) factor that clouds many cybersecurity risk decisions. These products are editable Microsoft Word & Excel templates, so if you can use Microsoft Office products, then you can use these risk management solutions!
## Can You Honestly Answer HOW Risk Is Implemented At Your Organization?
When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as risk management. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW the policies and standards are actually implemented. We did the heavy lifting and created several program-level documents to address this need and the Risk Management Program (RMP) is one of those products.
## Risk Management Doesn't Have To Be Hard
ComplianceForge currently offers two (2) products that are specifically designed to assist companies with cybersecurity risk management:
- [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "Cybersecurity Risk Management Program")
- [**Cybersecurity Risk Assessment Template (CRA)**](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "Cybersecurity Risk Assessment Template (CRAT)")
The [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "Risk Management Program (RMP)") is program-level documentation that is an essential need for any organization to demonstrate HOW risk is actually managed within an organization. Most companies run into issues during audits when the actual practices for risk management are looked at. The RMP is meant to advance your organization to a mature level of risk management and have the documentation to prove it!
The [Cybersecurity Risk Assessment Template (CRA)](https://complianceforge.com/product/cybersecurity-information-security-risk-assessment-template/ "Cybersecurity Risk Assessment Template (CRAT)") supports the Risk Management Program (RMP), but it is a stand-alone product that consists of Microsoft Word and Excel templates that enable any organization to conduct repeatable and quality risk assessments. If you can use Microsoft Office products, then you can follow the guidance in the CRA to create your own quality risk assessments. The Cybersecurity Risk Assessment Template (CRA) addresses natural, man-made and cybersecurity risks to provide a robust risk assessment template. The cybersecurity controls used in the template are from NIST 800-171, which is based on leading NIST 800-53 and ISO 27002 controls.
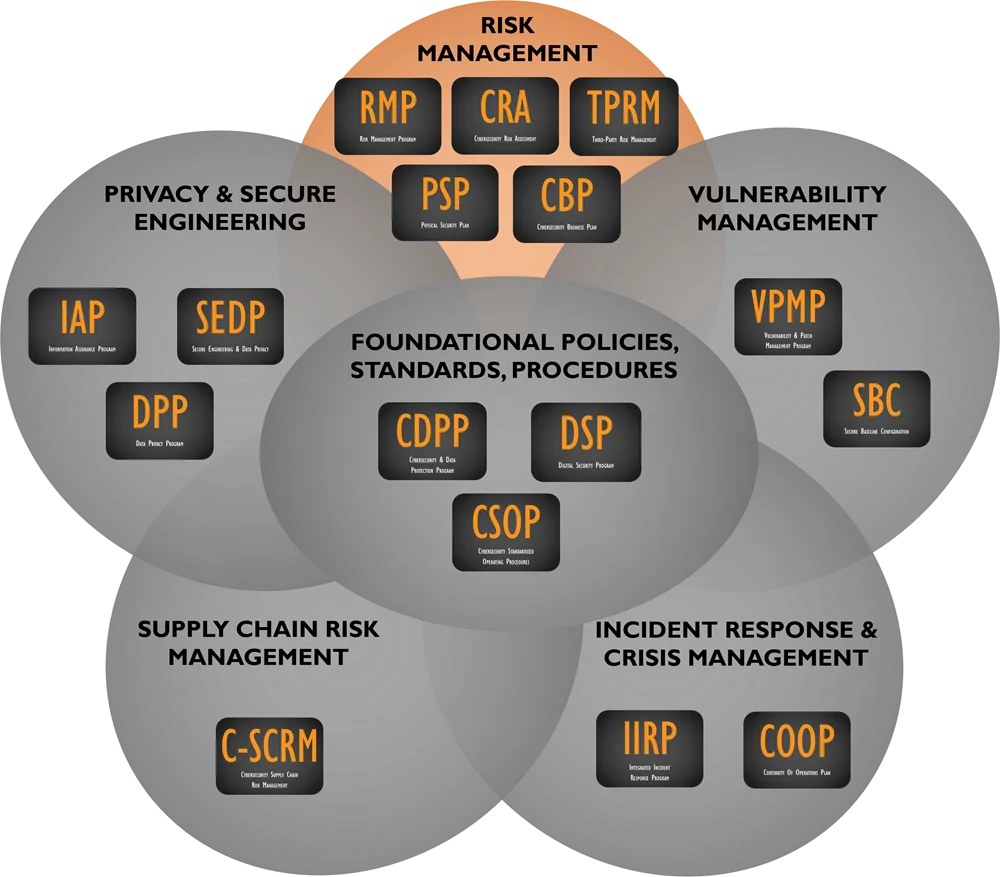
## Browse Our Products
- [](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
#### [Risk Management Program (RMP)](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
ComplianceForge
Cybersecurity Risk Management Program (RMP)
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/)
- [](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
#### [Cybersecurity Risk Assessment (CRA) Template](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
ComplianceForge
Cybersecurity Risk Assessment Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about...
$1,925.00 - $6,725.00
[Choose Options](https://complianceforge.com/product/cybersecurity-risk-assessment-template/)
- [](https://complianceforge.com/product/cybersecurity-business-plan/)
#### [Cybersecurity Business Plan (CBP)](https://complianceforge.com/product/cybersecurity-business-plan/)
ComplianceForge
Cybersecurity Business Plan (CBP) Template
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $3,525.00
[Choose Options](https://complianceforge.com/product/cybersecurity-business-plan/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Cybersecurity Materiality Insights
[Skip to main content](https://complianceforge.com/blog/cybersecurity-materiality-key-controls/#main-content)
[](https://complianceforge.com/blog/cybersecurity-materiality-key-controls/)
There is a "materiality ecosystem" that exists within modern cybersecurity risk management discussions. The process begins with determining what constitutes materiality for an organization. This is organization-specific and is primarily based on a clearly-defined financial threshold. It is common practice for companies to identify "key controls" to help prioritize cybersecurity efforts and a worthwhile is to evaluate those key controls from a materiality perspective. That may confirm the accuracy of the concept of key controls or it may require changes, where this activity should be all a part of due diligence and due care in GRC operations.
Defining materiality is an executive leadership determination, not a cybersecurity determination. Often, cybersecurity teams incorrectly hypothesize what “should be material” through the myopic perspective of the cybersecurity department. However, those cybersecurity-led definitions are often incorrect and are not material to the organization, much to the frustration of legal counsel that sometimes have to reprimand cybersecurity practitioners for incorrectly labeling incidents as material. For example, while a $5 million dollar incident may appear material (e.g., it is a significant sum), that financial amount may not come close to the actual materiality threshold for a prosperous organization.
This graphic can be downloaded from: [https://complianceforge.com/content/pdf/guide-risk-vs-threat-vs-vulnerability-ecosystem.pdf](https://complianceforge.com/content/pdf/guide-risk-vs-threat-vs-vulnerability-ecosystem.pdf)
[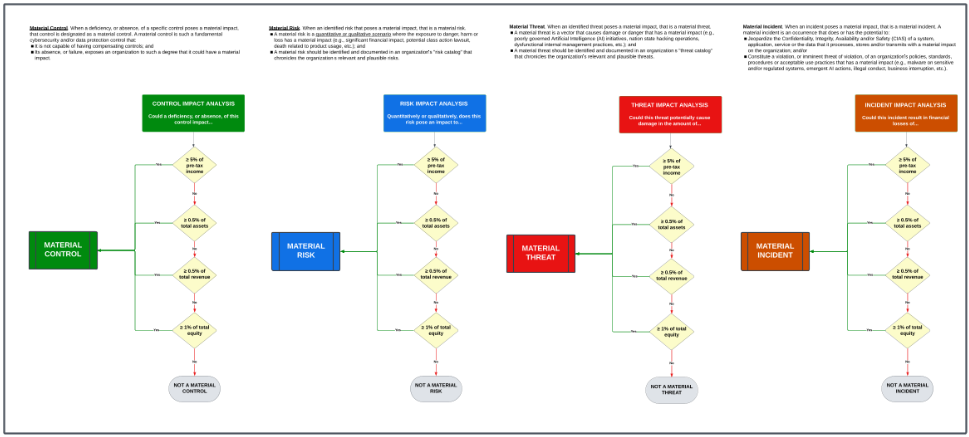](https://complianceforge.com/content/pdf/guide-risk-vs-threat-vs-vulnerability-ecosystem.pdf)
Once the materiality threshold is clearly defined, it then requires a look at an organization’s risk and threat management practices to identify those specific risks and threats that could lead to a material incident. Ideally, this means reviewing established risk and threat catalogs to identify known risks and threats that have material implications.
In the end, the due diligence activities performed to define material risk and material threats assist with broader incident response operations. This prior work assists the organization in defining material incidents, or at least pre-determined criteria associated with incidents, that would elevate incident response activities to the proper organizational leadership, due to the existence of a material incident (e.g., external reporting requirements, reputation damage control, etc.). During incident triage is not the correct time to develop incident threshold categories to determine materiality, due to requirements such as the US Securities and Exchange Commission (SEC) requires public companies to disclose material incidents within 72 hours.
You can learn more about cybersecurity risk management and materiality here: [https://complianceforge.com/grc/cybersecurity-risk-management-materiality/](https://complianceforge.com/grc/cybersecurity-risk-management-materiality/)
- [#cybersecurity](https://complianceforge.com/blog/tag/cybersecurity)
- [#key controls](https://complianceforge.com/blog/tag/key+controls)
- [#materiality](https://complianceforge.com/blog/tag/materiality)
- [#SEC security rule](https://complianceforge.com/blog/tag/SEC+security+rule)
- [Email](mailto:?subject=Cybersecurity%20Materiality%20%26%20Key%20Controls%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-materiality-key-controls%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-materiality-key-controls%2F&title=Cybersecurity%20Materiality%20%26%20Key%20Controls%20-%20ComplianceForge&summary=Cybersecurity%20Materiality%20%26%20Key%20Controls%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fcybersecurity-materiality-key-controls%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## PCI DSS Compliance Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/pci-dss-compliance/#main-content)
# PCI DSS Compliance Templates
Accepting payment cards spans industries, even businesses that would not necessarily consider themselves to be a "merchant" in terms of traditional brick & mortar retailers. However, any company that accepts payment via debit and/or credit cards must comply with the Payment Card Industry Data Security Standard (PCI DSS). Some businesses choose to segment off the cardholder environment and manage it by its own unique policies and standards. Other businesses address PCI DSS requirements as part of its overall policies and standards. Either way works and ComplianceForge offers solutions for both approaches!
## What Self-Assessment Questionnaire (SAQ) Type Are You?
SAQs are requirements for smaller merchants and service providers that are not required to submit a Report on Compliance (ROC). It is designed as a self-validation tool to assess security for cardholder data that uses a series of yes-or-no questions for each applicable PCI DSS requirement.
There are different questionnaires available to meet different merchant environments. Merchants are required to identify the SAQ that best describes how it accept payment cards. Some organizations may even need to fill out different SAQs, based on different methods of accepting payment (e.g., SAQ A for its website and SAQ C for its "brick & mortar" store locations). If you are not sure which questionnaire applies to you, contact your merchant services provider for assistance or review the official PCI Security Standards Council's guidance on "assessing the security of your cardholder data" to help determine the appropriate SAQ type for your organization **- [SAQ Instructions and Guidelines.](https://docs-prv.pcisecuritystandards.org/SAQ%20(Assessment)/Instructions%20%26%20Guidance/SAQ-Instructions-Guidelines-PCI-DSS-v4-0.pdf "PCI DSS v4 SAQ types")**
ComplianceForge sells its PCI DSS Policies & Standards based on the SAQ type (shown below):
| | | | |
| --- | --- | --- | --- |
| **SAQ Type** | **Method of Accepting Payment Cards** | **E-Commerce** | **In-Person** |
| **A** | Card-not-present merchants (e-commerce or mail/telephone-order) that have fully outsourced all cardholder data functions to PCI DSS compliant third-party service providers, with no electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises.
Not applicable to face-to-face channels. | Yes | No |
| **A-EP** | E-commerce merchants who outsource all payment processing to PCI DSS validated third parties, and who have a website(s) that doesn’t directly receive cardholder data but that can impact the security of the payment transaction. No electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises.
Applicable only to e-commerce channels. | Yes | No |
| **B** | Merchants using only:
- Imprint machines with no electronic cardholder data storage; and/or
- Standalone, dial-out terminals with no electronic cardholder data storage.
Not applicable to e-commerce channels. | No | Yes |
| **B-IP** | Merchants using only standalone, PTS-approved payment terminals with an IP connection to the payment processor, with no electronic cardholder data storage.
Not applicable to e-commerce channels. | No | Yes |
| **C** | Merchants with payment application systems connected to the Internet, no electronic cardholder data storage.
Not applicable to e-commerce channels. | No | Yes |
| **C-VT** | Merchants who manually enter a single transaction at a time via a keyboard into an Internet-based virtual terminal solution that is provided and hosted by a PCI DSS validated third-party service provider. No electronic cardholder data storage.
Not applicable to e-commerce channels. | No | Yes |
| **D** (Merchant) | All merchants not included in descriptions for the above types. | Yes | Yes |
| **D** (Service Provider) | All service providers defined by a payment card brand as eligible to complete a SAQ. | N/A | N/A |
You can click on the matrix below for a downloadable PDF that shows the PCI DSS v4 controls as they apply to the SAQ levels:
[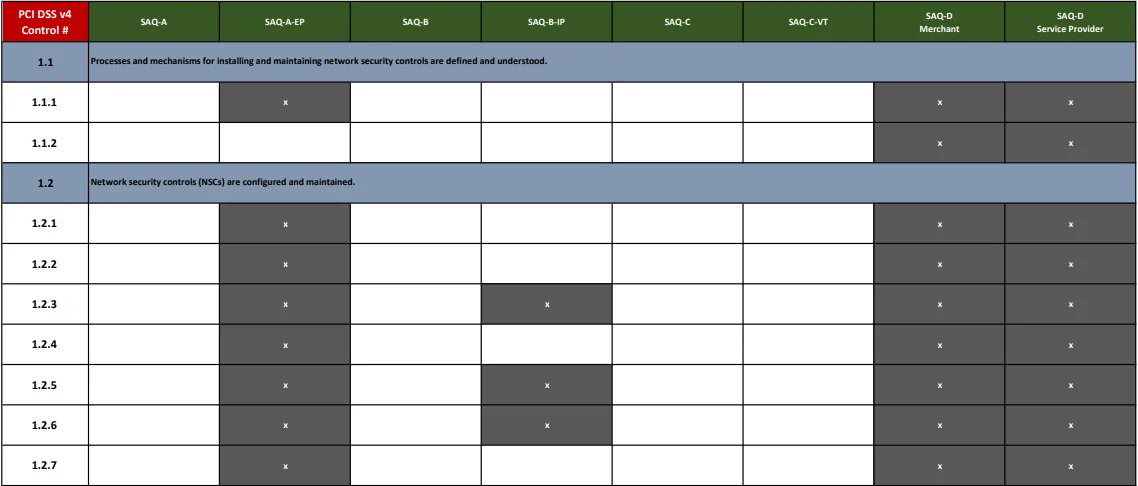](https://complianceforge.com/content/pdf/example-pci-dss-4-mapping.pdf "PCI DSS v4 SAQ policies & standards")
## PCI DSS Policies & Standards
For the SAQ types that were listed above, ComplianceForge offers the following PCI DSS v4.0 cybersecurity policies & standards templates:
## Browse Our Products
- [](https://complianceforge.com/product/pci-dss-v4-saq-a)
#### [Policies & Standards - PCI DSS v4 SAQ A](https://complianceforge.com/product/pci-dss-v4-saq-a)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) A for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,155.00
[Choose Options](https://complianceforge.com/product/pci-dss-v4-saq-a)
- [](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ A-EP](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) A-EP for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,155.00
[Choose Options](https://complianceforge.com/product/saq-a-ep-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ B](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) B for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,325.00
[Choose Options](https://complianceforge.com/product/saq-b-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ B-IP](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) B-IP for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,325.00
[Choose Options](https://complianceforge.com/product/saq-b-ip-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ C](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) C for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,625.00
[Choose Options](https://complianceforge.com/product/saq-c-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ C-VT](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) C-VT for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies &...
$1,625.00
[Choose Options](https://complianceforge.com/product/saq-c-vt-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ D (Merchant)](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) D-Merchant for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity Policies...
$1,870.00
[Choose Options](https://complianceforge.com/product/saq-d-merchant-pci-dss-v4-0-policies-standards/)
- [](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
#### [Policies & Standards - PCI DSS v4 SAQ D (Service Provider)](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
ComplianceForge
Note: This version is specific to Self-Assessment Questionnaire (SAQ) D-Service Provider for PCI DSS v4.0. If you are not sure what SAQ level you need, please review the official PCI Standards Council site.
PCI DSS v4.0 - Cybersecurity...
$1,870.00
[Choose Options](https://complianceforge.com/product/saq-d-service-provider-pci-dss-v4-0-policies-standards/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## Vulnerability Management Templates
[Skip to main content](https://complianceforge.com/cybersecurity-templates/vulnerability-patch-management/#main-content)
# Vulnerability & Patch Management Templates
## Program-level Documentation
Having a proactive patching cadence and vulnerability management program is one of the most common weaknesses that companies face. Spending a small fortune on people and technology does little to reduce your risk if the processes do not exist to maintain those systems, applications and services. The good news is that ComplianceForge developed program-level documentation for businesses to help manage their vulnerability management and patching processes.
## Can You Honestly Answer How Vulnerability Management Is Implemented At Your Organization?
When you "peel back the onion" and prepare for an audit, there is a need to address "the how" for certain topics, such as vulnerability management. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW the policies and standards are actually implemented. We did the heavy lifting and created several program-level documents to address this need and the Vulnerability & Patch Management (VPMP) is one of those products.
## Elevate The Way You Approach Vulnerability Management
ComplianceForge currently offers two (2) product2 that is specifically designed to assist companies with vulnerability management:
- [**Vulnerability & Patch Management Program (VPMP)**](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/ "Vulnerability & Patch Management Program")
- [**Secure Baseline Configurations (SBC)**](https://complianceforge.com/product/secure-baseline-configuration-sbc "Secure Baseline Configurations (SBC)")
The Vulnerability & Patch Management Program (VPMP) is program-level documentation that is an essential need for any organization to demonstrate HOW vulnerabilities are actually managed within an organization. Most companies run into issues during audits when the actual practices for vulnerability & patch management are looked at. The VPMP is meant to advance your organization to a mature level of vulnerability management and have the documentation to prove it!
The Secure Baseline Configurations (SBC) is designed to help organizations manage the complex nature of secure baseline configurations for all its technology platforms.

## Browse Our Products
- [](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
#### [Vulnerability & Patch Management Program (VPMP)](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
ComplianceForge
Vulnerability & Patch Management Program
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $6,975.00
[Choose Options](https://complianceforge.com/product/vulnerability-patch-management-program-vpmp/)
- [](https://complianceforge.com/product/secure-baseline-configuration-sbc)
#### [Secure Baseline Configurations (SBC)](https://complianceforge.com/product/secure-baseline-configuration-sbc)
ComplianceForge
Secure Baseline Configurations For Technology Assets
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief...
$2,175.00 - $3,525.00
[Choose Options](https://complianceforge.com/product/secure-baseline-configuration-sbc)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Integrated Controls Management
[Skip to main content](https://complianceforge.com/free-guides/integrated-controls-management/#main-content)
# Operationalizing GRC & IRM Technologies
The **Integrated Controls Management (ICM)** is a joint project between ComplianceForge and the [Secure Controls Framework (SCF)](https://securecontrolsframework.com/ "Secure Controls Framework (SCF)") and the premise is that controls are central to cybersecurity and privacy operations, as well as the overall business rhythm of an organization. This is supported by the [Cybersecurity & Data Privacy Risk Management Model (C\|P-RMM)](https://securecontrolsframework.com/risk-management-model/ "Cybersecurity & Data Privacy Risk Management Model (C|P-RMM)"), that describes the central nature of controls, where not just policies and standards map to controls, but procedures, metrics, threats and risks, as well.
ICM takes a different approach from the traditional definition of Governance, Risk Management and Compliance (GRC) and/or Integrated Risk Management (IRM), since ICM is controls-centric, where controls are viewed as the nexus, or central pivoting point, for an organization’s cybersecurity and privacy operations.
[](https://complianceforge.com/content/pdf/complianceforge-integrated-controls-management.pdf "integrated controls management - how to grc")
[**OCEG**](https://www.oceg.org/about/what-is-grc/ "OCEG - GRC Definition") defines GRC as, “ _GRC is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity_,” while [**Gartner**](https://www.gartner.com/en/information-technology/glossary/integrated-risk-management-irm "Gartner - GRC & IRM Definition") jointly defines GRC/IRM as, " _a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks_."
**ComplianceForge** and [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework (SCF)"), the developers of the ICM model, define ICM as, “ _a holistic, technology-agnostic approach to cybersecurity and data protection controls to identify, implement and manage secure and compliant practices, covering an organization’s people, processes, technology and data, regardless of how or where data is stored, processed and/or transmitted._”
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity and privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of **Supply Chain Risk Management (SCRM)**.

## Defining What It Means To Be “Secure & Compliant”
Unlike GRC/IRM, ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, ICM helps an organization categorize its applicable controls according to “must have” vs “nice to have” requirements:
- **Minimum Compliance Requirements (MCR)** are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- **Discretionary Security Requirements (DSR)** are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.

Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
## ICM Principles
There are eight (8) principles associated with ICM:
1. Establish Context;
2. Define Applicable Controls;
3. Assign Maturity-Based Criteria;
4. Publish Policies, Standards & Procedures;
5. Assign Stakeholder Accountability;
6. Maintain Situational Awareness;
7. Manage Risk; and
8. Evolve Processes.
ComplianceForge has simplified the concept of "how to GRC" in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
**Integrated Controls Management (ICM) – Overlaid On Integrated Cybersecurity Governance Model (ICGM)**
[](https://complianceforge.com/content/pdf/complianceforge-icm-plan-do-check-act.pdf "plan do check act cybersecurity controls")
### Principle 1: Establish Context
To build and maintain efficient and effective operations, a cybersecurity & privacy program must have a hierarchical vision, mission and strategy that directly supports the organization’s broader strategic objectives and business processes. This process of establishing context involves identifying all applicable external compliance requirements (e.g., laws, regulations and contractual obligations), as well as internal directives (e.g., Board of Directors, corporate policies, etc.). This is a due diligence element of the cybersecurity and privacy program.
### Principle 2: Define Applicable Controls
A tailored control set cybersecurity and data protection controls must exist. This control set needs to be made of Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR). This blend of “must have” and “nice to have” requirements establish an organization’s tailored control set to ensure both secure practices and compliance.
### Principle 3: Assign Maturity-Based Criteria
The cybersecurity & privacy program must assign maturity targets to define organization-specific “what right looks like” for controls. This establishes attainable criteria for people, processes and technology requirements. Tailored maturity level criteria can be used to plan for, budget for and assess against. Maturity targets should support the organization’s need for operational resiliency.
### Principle 4: Publish Policies, Standards & Procedures
Documentation must exist, otherwise an organization’s cybersecurity and data protection practices are unenforceable. Formalizing organization-specific requirements via policies and standards are necessary to operationalize controls. Stakeholders utilize those prescriptive requirements to develop Standardized Operating Procedures (SOP) that enable Individual Contributors (IC) to execute those controls. Policies, standards and procedures provides evidence of due diligence that the organization identified and implemented reasonable steps to address its applicable requirements.
### Principle 5: Assign Stakeholder Accountability
Controls must be assigned to stakeholders to ensure accountability (e.g., business units, teams and/or individuals). These “control owners” may assign the task of executing controls to “control operators” at the IC-level. The documented execution of procedures provides evidence of due care that reasonable practices are being performed.
### Principle 6: Maintain Situational Awareness
Situational awareness must involve more than merely “monitoring controls” (e.g., metrics). While metrics are a point-in-time snapshot into discrete controls’ performance, the broader view of metrics leads to a longer-term trend analysis. When properly tied in with current risk, threat and vulnerability information, this insight provides “situational awareness” that is necessary for organizational leadership to adjust plans to operate within the organization’s risk threshold.
### Principle 7: Manage Risk
Proactive risk management processes must exist across all phases of development/information/system life cycles to address confidentiality, integrity, availability and safety aspects. Risk management must address internal and external factors, including privacy and Supply Chain Risk Management (SCRM) considerations. To manage risk, it requires the organization to clearly define its risk threshold and risk management expectations.
### Principle 8: Evolve Processes
Cybersecurity and data protection measures must adapt and evolve to address business operations and the evolving threat landscape. This requires the adoption of a Plan, Do, Check & Act (PDCA) approach (Deming Cycle) to ensure the organization proactively identifies its requirements, implements appropriate protections, maintains situational awareness to detect incidents, operates a viable capability to respond to incidents and can sustain key business operations, if an incident occurs.
## Plan-Do-Check-Act (PDCA) Approach To GRC
The ICM takes a comprehensive view towards governing a cybersecurity and privacy program. Without an overarching concept of operations for the broader GRC/IRM function, organizations will often find that their governance, risk, compliance and privacy teams are siloed in how they think and operate. These siloed functions and unclear roles often stem from a lack of a strategic understanding of how these specific functions come together to build a symbiotic working relationship between the individual teams that enables quality control over people, processes and technology. The ICM utilizes a **[Plan, Do, Check & Act (PDCA)](https://complianceforge.com/content/pdf/complianceforge-icm-plan-do-check-act.pdf "Plan, Do, Check & Act (PDCA) - PDF")** approach that is a logical way to design a governance structure:
- **Plan**. The overall GRC process beings with planning. This planning will define the policies, standards and controls for the organization. It will also directly influence the tools and services that an organization purchases, since technology purchases should address needs that are defined by policies and standards.
- **Do**. Arguably, this is the most important section for cybersecurity and privacy practitioners. Controls are the “security glue” that make processes, applications, systems and services secure. Procedures (also referred to as control activities) are the processes how the controls are actually implemented and performed. The [**Secure Controls Framework (SCF)**](https://www.securecontrolsframework.com/ "Secure Controls Framework") can be an excellent starting point for a control set if your organization lacks a comprehensive set of cybersecurity and privacy controls.
- **Check**. In simple terms, this is situational awareness. Situational awareness is only achieved through reporting through metrics and reviewing the results of audits/assessments.
- **Act**. This is essentially risk management, which is an encompassing area that deals with addressing two main concepts (1) real deficiencies that currently exist and (2) possible threats to the organization.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
[complianceforge: grc resources for cybersecurity success](https://complianceforge.com/governance-risk-compliance-grc-content/)
what is icm, controls management, icm business continuity, integrated governance risk and compliance, integrated risk management grc, integrated controls
## Supply Chain Risk Management
[Skip to main content](https://complianceforge.com/blog/supply-chain-risk-management/#main-content)
[](https://complianceforge.com/blog/supply-chain-risk-management/)
**Cybersecurity Supply Chain Risk Management (C-SCRM)**
is the process of identifying, assessing and mitigating risks in an
organization's supply chain that could impact the security and integrity of an
organization's products, services and operations.
C-SCRM includes risks associated with the use of third-party
vendors, software and other components that make up an organization's broader
technology infrastructure. Effective C-SCRM involves identifying potential
vulnerabilities and threats in the supply chain and implementing measures to
reduce or eliminate those risks. This includes conducting risk assessments,
implementing cybersecurity controls and regularly monitoring the supply chain
for evolving threats and potential vulnerabilities.
C-SCRM also involves working closely with suppliers and
vendors to ensure that those Third-Party Service Providers (TSP) meet an
organization's cybersecurity and privacy requirements to prevent the
introduction of additional risks to the organization.
There is a lot of invaluable
information on the Internet about what C-SCRM is from authoritative sources,
such as the US National Institute of Standards and Technology (NIST), the US
Department of Homeland Security (DHS), the Cybersecurity & Infrastructure
Security Agency (CISA), the US National Counterintelligence and Security Center
(NCSC) and many others. It is important to understand that NIST is the
authoritative source on C-SCRM-related matters and provides authoritative
guidance on the subject for the US Government:
- Section 1323 of the Secure Technology Act tasked
NIST with identifying and recommending development of "supply chain risk
management standards, guidelines, and practices for executive agencies to use
when assessing and developing mitigation strategies to address supply chain
risks..."
- Section 201.301(d) of the Federal Acquisition
Supply Chain Security Act (FASCSA) requires the Federal Acquisition Security
Council (FASC) to consultation with NIST and participate in FASC activities as
a member to advise the FASC on NIST standards and guidelines issued under 40
U.S.C. 11331, including ensuring that any recommended orders do not conflict
with such standards and guidelines.
NIST has several publications and
sites that directly frame or support SCRM:
- NIST SP 800-161, Supply Chain Risk Management
Practices for Federal Information Systems and Organizations
- NIST IR 8276, Key Practices in Cyber Supply
Chain Risk Management: Observations from Industry
- NIST IR 8286, Integrating Cybersecurity and
Enterprise Risk Management (ERM)
- NIST's guidance on Executive Order (EO) 14028
Keep in mind that the NIST
publications are merely guidance and there is no formal implementation guidance
for C-SCRM.
If you are interested in implementing an SCRM
plan, we provide a product we call the C-SCRM Strategy & implementation
Plan (C-SCRM SIP), and you can learn more about it from this link – [www.complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan](https://complianceforge.com/product/nist-800-161-cscrm-strategy-implementation-plan).
- [#SCRM](https://complianceforge.com/blog/tag/SCRM)
- [#Supply Chain Risk Management](https://complianceforge.com/blog/tag/Supply+Chain+Risk+Management)
- [Email](mailto:?subject=Supply%20Chain%20Risk%20Management%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fsupply-chain-risk-management%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fsupply-chain-risk-management%2F&title=Supply%20Chain%20Risk%20Management%20-%20ComplianceForge&summary=Supply%20Chain%20Risk%20Management%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fsupply-chain-risk-management%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
## CMMC Procedures Templates
[Skip to main content](https://complianceforge.com/blog/need-procedures-for-cmmc/#main-content)
Need procedures for CMMC? ComplianceForge released the NIST SP 800-53 R5 version of the Cybersecurity Standardized Operating Procedures (CSOP) template. Low, moderate, high and privacy baseline-mapped procedures template!

[https://complianceforge.com/standardized-operating-procedures/](https://complianceforge.com/standardized-operating-procedures/)
The CSOP even comes with mapping to the granular NIST SP 800-171A assessment criteria, which is what NIST SP 800-171 and CMMC assessments are supposed to use for CUI-related controls.
- [#CMMC procedures](https://complianceforge.com/blog/tag/CMMC+procedures)
- [#CSOP](https://complianceforge.com/blog/tag/CSOP)
- [#editable procedures](https://complianceforge.com/blog/tag/editable+procedures)
- [#NIST 800-171 procedures](https://complianceforge.com/blog/tag/NIST+800-171+procedures)
- [#NIST 800-53 procedures](https://complianceforge.com/blog/tag/NIST+800-53+procedures)
- [#procedures](https://complianceforge.com/blog/tag/procedures)
- [#procedures template](https://complianceforge.com/blog/tag/procedures+template)
- [#SOP](https://complianceforge.com/blog/tag/SOP)
- [Email](mailto:?subject=%E2%80%8BNeed%20procedures%20for%20CMMC%3F%20-%20ComplianceForge&body=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fneed-procedures-for-cmmc%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fneed-procedures-for-cmmc%2F&title=%E2%80%8BNeed%20procedures%20for%20CMMC%3F%20-%20ComplianceForge&summary=%E2%80%8BNeed%20procedures%20for%20CMMC%3F%20-%20ComplianceForge&source=https%3A%2F%2Fcomplianceforge.com%2Fblog%2Fneed-procedures-for-cmmc%2F "Linkedin")
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
## NIST 800-171 Compliance
[Skip to main content](https://complianceforge.com/complianceforge-nist-800-171-cmmc/#main-content)

# ComplianceForge - NIST 800-171 & CMMC
Sort By:Featured ItemsNewest ItemsBest SellingA to ZZ to ABy ReviewPrice: AscendingPrice: Descending
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [](https://complianceforge.com/bundle/cmmc-bundle-1)
#### [CMMC Bundle 1: Level 1 (CMMC 2.0 L1 & FAR 52.204-21)](https://complianceforge.com/bundle/cmmc-bundle-1)
ComplianceForge - NIST 800-171 & CMMC
CMMC 2.0 Level 1 - CMMC 2.0 L1 & FAR 52.204-21 Policies, Standards & Procedures - CMMC Level 1 (20% discount)
This bundle is as streamlined as we've been able to make...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/cmmc-bundle-1)
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
## Unified Scoping Guide
[Skip to main content](https://complianceforge.com/free-guides/unified-scoping-guide#main-content)

[](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "Unified Scoping Guide | CUI Scoping Guide | CMMC Scoping Guide | NIST 800-171 Scoping Guide")
# Unified Scoping Guide (USG)
## Zone-Based Model To Apply A Data-Centric Security Approach For Scoping Sensitive & Regulated Data
The Unified Scoping Guide (USG) is a free resource that is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This model categorizes system components according to several factors:
- Whether sensitive data is being stored, processed or transmitted;
- The functionality that the system component provides (e.g. access control, logging, antimalware, etc.); and
- The connectivity between the system and the sensitive data environment.
This is an evolution of the CUI Scoping Guide that ComplianceForge previously published. This new version is updated to reflect the DoD's CMMC 2.0 Level 2 Scoping Guidance that includes [Controlled Unclassified Information (](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret) [CUI](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret) [)](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret) scoping considerations, but expands on the model to address a broader category of sensitive and regulated data. This document can be used to help companies define what is in scope to comply with NIST SP 800-171 and appropriately prepare for a CMMC assessment, since a significant step towards becoming NIST SP 800-171 compliant and being able to pass a CMMC assessment is understanding the scope of the [CUI](https://complianceforge.com/unclassified-vs-classified-uui-vs-cui-vs-confidential-vs-secret-vs-top-secret) environment.
The Unified Scoping Guide (USG) is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This approach is applicable to the following sensitive data types:
| | |
| --- | --- |
| - Controlled Unclassified Information (CUI)
- Personally Identifiable Information (PII)
- Cardholder Data (CHD)
- Attorney-Client Privilege Information (ACPI)
- Export-Controlled Data (ITAR / EAR) | - Federal Contract Information (FCI)
- Protected Health Information (PHI)
- Intellectual Property (IP)
- Student Educational Records (FERPA)
- Critical Infrastructure Information (CII) |
[](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "Unified Scoping Guide (USG) | CUI Scoping Guide | CMMC Scoping Guide | NIST 800-171 Scoping Guide")
## Zone-Based Approach To Implementing Data-Centric Security
When viewing scoping, there are nine (9) zones for sensitive data compliance purpose.
[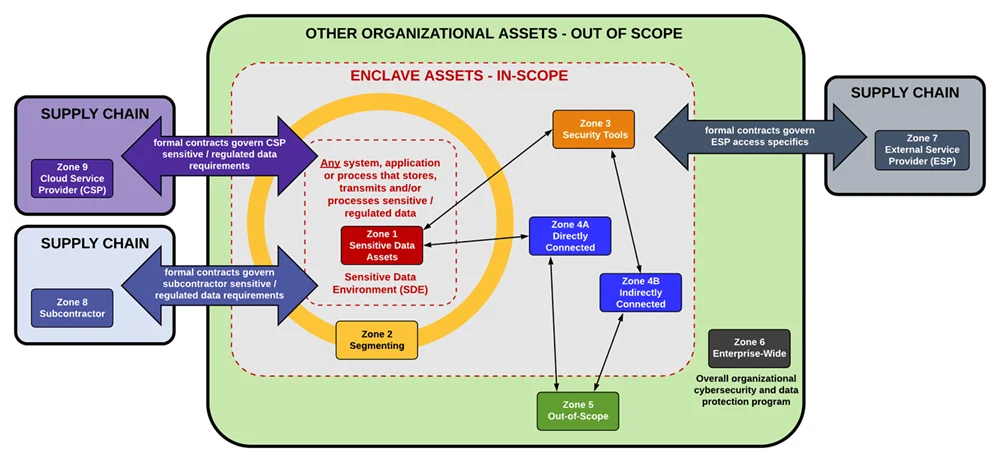](https://complianceforge.com/content/pdf/unified-scoping-guide-usg.pdf "NIST 800-171 Scoping Guide | CUI Scoping Guide")
1. Sensitive Data Assets: The first zone contains systems, services and applications that directly store, transmit and/or process sensitive data.
2. Segmenting: The second zone contains “segmenting systems” that provide access (e.g., firewall, hypervisors, etc.).
3. Security Tools: The third zone contains “security tools” that directly impact the integrity of category 1 and 2 assets (e.g., Active Directory, centralized antimalware, vulnerability scanners, IPS/IDS, etc.).
4. Connected. The fourth zone contains connected systems. These are systems, embedded technologies, applications or services that have some direct or indirect connection into the sensitive data environment. Systems, embedded technologies, applications and services that may impact the security of (for example, name resolution or web redirection servers) the sensitive data environment are always in scope. Essentially, it something can impact the security of sensitive data, it is in scope.
5. Out-of-Scope. The fifth zone contains out-of-scope systems that are completely isolated from the sensitive data systems.
6. Enterprise-Wide. The sixth zone addresses the organization’s overall corporate security program (cyber and physical).
7. External Service Provider. The seventh zone addresses supply-chain security with the “flow down” of contractual requirements to External Service Providers (ESPs) that can directly or indirectly influence the sensitive data environment. ESPs are third-party organizations that provide services to the organizations.
8. Subcontractors. The eighth zone addresses subcontractors, which are third-party organizations that are party to the actual execution of the contract where the subcontractor may create, access, receive, store and/or transmit regulated data (sensitive data).
9. Cloud Service Provider. The nineth zone addresses CSPs, which are a specialized form of ESP. An ESP is a CSP when it offers “cloud computing services” that enable ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction
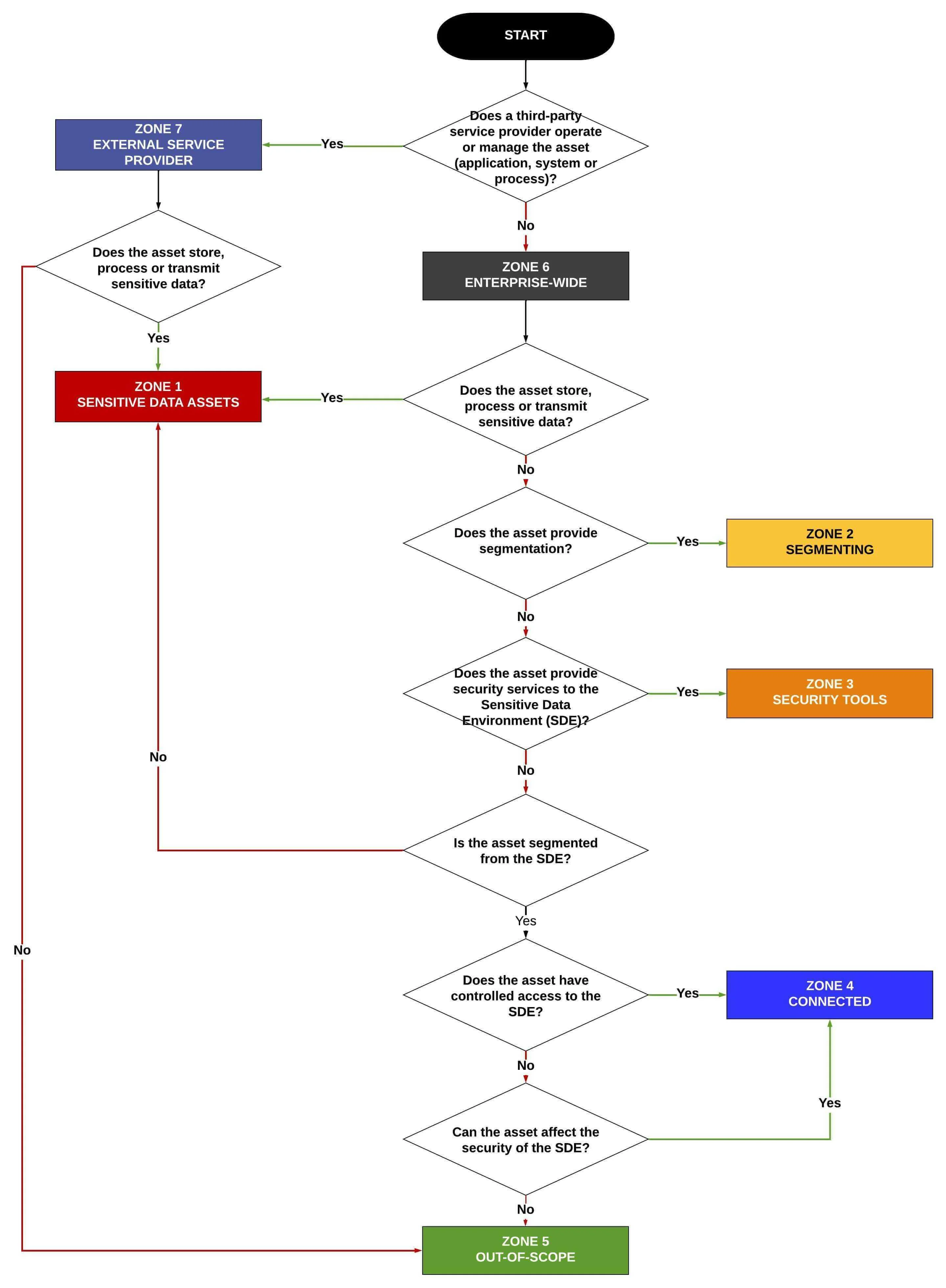
**Zone 1**: All systems, applications and services that store, transmit and/or process sensitive data are Category 1 devices. These systems that interact with sensitive data are the main assets that sensitive data are trying to protect
**Zone 2**: All network devices or hypervisors that provide segmentation functions are Category 2 devices. This category involves systems that provide segmentation and prevent "sensitive data contamination" from the sensitive data environment to uncontrolled environments. Typically, these are firewalls or segmentation technology that implement some form of Access Control List (ACL) to restrict logical access into and out of the sensitive data environment. This can also include Zero Trust Architecture (ZTA) components that provide micro-segmentation services
Note: If network segmentation is in place and is being used to reduce the scope of an assessment, expect the assessor to verify that the segmentation is adequate to reduce the scope of the assessment. the more detailed the documentation your assessor will require to adequately review the implemented segmenting solution.
**Zone 3**: All systems that provide security-related services or IT-enabling services that may affect the security of the sensitive data environment are Category 3 devices. There are systems that can impact configurations, security services, logging, etc. that can be in a dedicated security subnet or on the corporate LAN.
These include, at a minimum:
- Identity and Directory Services (Active Directory, LDAP);
- Domain Name Systems (DNS);
- Network Time Systems (NTP);
- Patch management systems;
- Vulnerability & patch management systems;
- Anti-malware management systems;
- File Integrity Management (FIM) systems;
- Data Loss Prevention (DLP) systems;
- Performance monitoring systems;
- Cryptographic key management systems;
- Remote-access or Virtual Private Network (VPN) systems;
- Multi-factor Authentication (MFA) systems;
- Mobile Device Management (MDM) systems;
- Log management and Security Incident Event Management (SIEM) systems; and
- Intrusion Detection Systems/ Intrusion Prevention Systems (IDS/IPS).
**Zone 4**: Any system that has some capability to communicate with systems, applications or services within the sensitive data environment is a Category 4 device. A “connected” system, embedded technologies, application or service should be considered in scope for since it is not completely isolated. If it can potentially impact the security of sensitive data, it is in scope.
There are two sub-categories of connected devices:
- Directly Connected; and
- Indirectly Connected.
**Zone 4A**: This sub-category addresses any system that is “connected to” the sensitive data environment is considered a directly-connected system. Any system outside of the sensitive data environment that is capable of communicating with a system that stores, transmits or processes sensitive data (e.g., asset within the sensitive data environment) is a Category 4A device.
Note: For systems outside of the sensitive data environment that have periodic controlled and managed outbound connections from the sensitive data environment that do not involve the transfer of regulated data (sensitive data), there is a case to argue that the system could be ruled out-of-scope since it cannot have an impact on the security of sensitive data. In cases like this, some form of Data Loss Prevention (DLP) tool may be warranted to act as a compensating control to further demonstrate how the asset would be out-of-scope.
**Zone 4B**: This sub-category addresses any system that does not have any direct access to sensitive data systems (e.g., not interacting with the sensitive data environment). Any system that has access to Connected or Segmenting systems and that could affect the security of the sensitive data environment is a Category 4B device.
An example of an indirectly connected system would be that of an administrator's workstation that can administer a security device (Active Directory, firewall, etc.) or upstream system that feeds information to connected systems (e.g. patching system, DNS, etc.). In the case of a user directory, an administrator could potentially grant himself/herself (or others) rights to systems in the sensitive data environment, therefore breaching the security controls applicable to the sensitive data environment.
**Zone 5**: Any system, application or service that is not a sensitive data-contaminated, segmenting or connected system is a Category 5 asset. These assets are considered out-of-scope for sensitive data. These out-of-scope assets must be completely isolated (no connections whatsoever) from sensitive data systems, though they may interact with connected systems (and can even reside in the same network zone with connected systems).
Four (4) tests must be considered to confirm that a system is out-of-scope and considered a Category 5 asset. This amounts to ensuring that the asset does not fall under the previously defined categories:
1. System components do NOT store, process, or transmit sensitive data.
2. System components are NOT on the same network segment or in the same subnet or VLAN as systems, applications or processes that store, process, or transmit sensitive data.
3. System component cannot connect to or access any system in the sensitive data environment.
4. System component cannot gain access to the sensitive data environment, nor impact a security control for a system, embedded technologies, application or service in the sensitive data environment via an in-scope system.
**Zone 6**: This category addresses enterprise-wide security controls that exist outside of just the sensitive data environment. Within this category are the corporate-wide security practices that affect both cyber and physical security, including security-related policies, standards and procedures that affect the entire organization.
**Zone 7**: Sensitive data in the supply chain needs to be taken seriously and this category addresses External Service Providers (ESPs). The formal contracts between your organization its ESPs dictate the logical and physical access those ESP have to the organization’s facilities, systems and data. The “flow down” considerations of sensitive data must be addressed with each ESP to clearly identify the ESPs’ ability to directly or indirectly influence the sensitive data environment.
Examples of ESPs that may have sensitive data flow down requirements:
- Bookkeepers;
- Human Resource (HR) recruiters;
- Payroll providers;
- Educational training providers;
- IT service providers / cybersecurity consultants / Managed Service Provider (MSP);
- Business process consultants;
- Project Managers (PMs);
- Document destruction providers; and
- Janitorial services and environmental control management.
**Zone 8**: This category addresses subcontractors necessary to perform the in-scope contract. While a subcontractor is a third-party, a subcontractor is party to the actual execution of the contract where the subcontractor may create, access, receive, store and/or transmit sensitive data.
**Zone 9**: This category addresses ESP providing cloud computing services that enable ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. A CSP can be identified by its function, since the cloud model is composed of five (5) essential characteristics, three (3) service models and four (4) deployment models:
**Essential Characteristics**:
1. On-demand self-service;
2. Broad network access;
3. Resource pooling;
4. Rapid elasticity; and
5. Measured service.
**Service Models**:
1. Software as a Service (SaaS);
2. Platform as a Service (PaaS); and
3. Infrastructure as a Service (IaaS).
**Deployment Models**:
1. Private cloud;
2. Community cloud;
3. Public cloud; and
4. Hybrid cloud.
## Scoping Is A Due Diligence Activity
Failure to adequately perform due diligence in scoping activities may lead to every system, application and service in your organization to be considered in scope and require applicable statutory, regulatory and/or contractual controls. The old adage of “if you fail to plan, you plan to fail” is very applicable in this scenario, so taking the time to document assets and data flows is of the utmost importance to ensure an accurate understanding of the people, processes and technology involved exists.
?In practical terms, security and data protection controls exist to protect an organization’s data. Requirements for asset management do not primarily exist to protect the inherent value of the asset, but the data it contains, since assets are merely data containers. Assets, such as laptops, servers and network infrastructure are commodities that can be easily replaced, but data residing on those devices cannot. This concept of being data-centric is crucial to understand when developing, implementing and governing a cybersecurity and privacy program, since it provides guidelines to establish the scope for control applicability.
This model categorizes system components according to several factors:
- Whether sensitive data is being stored, processed or transmitted;
- The functionality that the system component provides (e.g. access control, logging, antimalware, etc.); and
- The connectivity between the system and the sensitive data environment.

The model utilizes eight (8) zones to categorize system components, based on the interaction with sensitive data. This model highlights the different types of risks associated with each zone. This approach makes it evident which systems, applications and services must be appropriately protected, due to the risk posed to sensitive data. The Sensitive Data Environment (SDE) encompasses the people, processes and technologies that store, process and transmit sensitive data:
- Store – When sensitive data is inactive or at rest (e.g., located on electronic media, system component memory, paper).
- Process – When sensitive data is actively being used by a system component (e.g., entered, edited, manipulated, printed, viewed).
- Transmit – When sensitive data is being transferred from one location to another (e.g., data in motion).
This guide is not endorsed by any statutory or regulatory body. This is merely an unofficial model that [ComplianceForge](https://complianceforge.com/) compiled to help organizations comply with their cybersecurity and data privacy compliance needs.
## Segmentation Considerations
It is important to understand that without adequate network segmentation (e.g., a flat network) the entire network would be expected to be in scope for an assessment. Network segmentation should be viewed as a very beneficial process to isolate system components that store, process or transmit sensitive data from systems that do not. Adequate network segmentation may reduce the scope of the SDE and overall reduce the scope of an assessment. It is important to point out that Zero Trust Architecture (ZTA) still has scoping requirements and is not a “magic bullet” to eliminate scoping requirements. Examples of mechanisms that provide controlled access include firewalls, routers, hypervisors, micro-segmentation (e.g., ZTA), etc.
To eliminate ambiguity surrounding the term “segmentation” in terms of sensitive data enclave scoping, this guide uses one of the two following terms:
- Isolation – No logical access. This is achieved when network traffic between two assets is not permitted.
- Controlled Access – Logical access is permitted. This is achieved when access between assets is restricted to defined parameters.
- Controlled access is more common than isolation.
- Restrictions may include logical access control, traffic type (e.g., port, protocol or service), the direction from which the connection is initiated (e.g., inbound, outbound), etc.
## Rationalizing Data Scoping Recommendations
When evaluating the available guidance that exists to perform appropriate scoping activities, the Payment Card Industry Data Security Standard (PCI DSS) reigns, due to its long-established and internationally-recognized practices for protecting cardholder data (e.g., credit and debit cards). PCI DSS v1.0 was first published in 2004, so it has nearly two decades of guidance for “what looks right” to scope environments that require the implementation of PCI DSS controls to protect the confidentiality and integrity of cardholder data. The Payment Card Industry Security Standards Council (PCI SSC) publishes an [authoritative scoping guide](https://www.pcisecuritystandards.org/documents/Guidance-PCI-DSS-Scoping-and-Segmentation_v1.pdf) for merchants to leverage for PCI DSS compliance efforts. This PCI SSC scoping guidance is based on real-world threats and practical lessons-learned on how segmentation can be used to minimize scoping, due to limiting the ability of threats to negatively impact cardholder data.
Since PCI DSS is data-centric, that scoping guidance can be directly applied to other forms of data that require protection. This guide leveraged the outstanding concepts that PCI Resources published in its PCI DSS Scoping Model and Approach\[2\] by applying that scoping methodology to other types of sensitive data.
PCI DSS is a well-established and widely-adopting standard for protecting cardholder data (e.g., credit and debit cards). PCI DSS v1.0 was first published in 2004, so there is nearly two decades of guidance for “what looks right” to scope environments that require the implementation of PCI DSS controls to protect the confidentiality and integrity of cardholder data. From the perspective of PCI DSS, if scoping is done poorly, an organization’s entire network may be in-scope, which means PCI DSS requirements would apply uniformly throughout the entire company’s network. In these scenarios, PCI DSS compliance can be prohibitively expensive or even technically impossible. However, when the network is intelligently designed with security in mind, the Cardholder Data Environment (CDE) can be a small fraction of the company's network, which makes compliance much more achievable and affordable.
When you look at sensitive data compliance scoping, it has some similarities to PCI DSS:
- PCI DSS is focused on protecting the confidentiality and integrity of cardholder data, which is where credit/debit card data is stored, processed and transmitted.
- Statutory, regulatory and contractual obligations to protect sensitive data require controls to be implemented on the applicable environment(s) (e.g., system, application, service, etc.) where the sensitive data is stored, processed or transmitted. This is how PCI DSS applies its controls from a scoping perspective.
- Cardholder data is considered “infectious” from the perspective of scoping. Without proper segmentation and clear business processes, other forms of sensitive data can “infect” the entire network and greatly expand the scope of compliance and audits.
## What This Guide Does Address
Identifying and addressing the people, processes and technologies around sensitive data is a necessary part of any cybersecurity and data protection (privacy) program. This guide focuses on categorizing the system components that comprise a company's computing environment and helps with the following:
- Assists in determining which system components fall in and out of scope.
- Facilitates constructive communication between your company and an assessor/regulator by providing a reasonable methodology to describe your technology infrastructure and sensitive data environment.
- Provides a means to categorize the various different types of assets, each with a different risk profile associated with it.
- Provides a starting point to potentially reduce the scope of sensitive data by re-architecting technologies to isolate and control access to the sensitive data environment.
This model categorizes system components according to several factors:
- Whether sensitive data is being stored, processed or transmitted;
- The functionality that the system component provides (e.g. access control, logging, antimalware, etc.); and
- The connectivity between the system and the Sensitive Data Environment (SDE).
## What This Guide Does Not Address
This guide does not define which statutory, regulatory and/or contractual controls are required for each category. Since every organization is different, it is up to each organization and its assessor to determine the nature, extent and effectiveness of each control to adequately mitigate the risks to sensitive data.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-800-171-compliance-program/)
#### [NIST 800-171 Compliance Program (NCP)](https://complianceforge.com/product/nist-800-171-compliance-program/)
ComplianceForge - NIST 800-171 & CMMC
NIST 800-171 R2 & R3 / CMMC 2.0 Compliance Made Easier!
The NCP is editable & affordable cybersecurity documentation to address your NIST 800-171 R2 / R3 and CMMC 2.0 Levels 1-2 compliance needs.
When you click the image or the link below, it...
$8,950.00
$5,300.00 - $10,100.00
[Choose Options](https://complianceforge.com/product/nist-800-171-compliance-program/)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
cmmc 20 scoping guide, cmmc scoping guide, cui scope, unified compliance framework, cmmc scoping guidance
## FAR 52.204-21 Compliance
[Skip to main content](https://complianceforge.com/compliance/far-52.204-21#main-content)
# FAR 52.204-21 Compliance - Policies & Procedures
| | |
| --- | --- |
|  | If you are new to **Federal Acquisition Regulation (FAR) 52.204-21**, it is a contract clause (52.204-21) to the FAR “for the basic safeguarding of contractor information systems that process, store, or transmit Federal contract information."
FAR 52.204-21 imposes a set of fifteen (15) basic cybersecurity controls for contractor information systems upon which “Federal contract information” is stored, processed or transmitted. Federal contract information is defined as information provided by or generated for the Government under a contract to develop or deliver a product or service for the US Government. These FAR cybersecurity controls also form the basis for the [**Cybersecurity Maturity Model Certification (CMMC)**](https://complianceforge.com/compliance/cmmc) Level 1 that is focused on protecting **Federal Contract Information (FCI)** and **Covered Contractor Information Systems (CCIS)**. |
## NIST 800-171 & CMMC Compliance Implications for FAR 52.204-21
There are changes coming that will affect FAR 52.204-21 that are disclosed in **NIST 800-171** ( **[page v](https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-171r1.pdf#page=7 "NIST 800-171 FAR 52.204-21 compliance")**) that indicate FAR is going to adopt NIST 800-171 cybersecurity requirements to protect government data (e.g., Controlled Unclassified Information or Controlled Technical Information). In the end, this means that complying with the US Government's cybersecurity requirements will be considerably more than just the 15 basic controls currently listed in FAR 52.204-21.
The Department of Defense (DoD) states in the CMMC Model Main document that Level 1 organizations "may only be able to perform these practices in an ad-hoc manner and may or may not rely on documentation, process maturity is not assessed for Level 1." This makes it appear that Level 1 organizations have no documentation requirements. However, that is actually incorrect when you look at how Level 1 organizations are focused on protecting Federal Contract Information (FCI) and Covered Contractor Information Systems (CCIS).
FAR 52.204-21 specifically calls out in section (b)(1) that contractors “_shall apply the following basic safeguarding requirements and procedures to protect CCIS_” in regards to the fifteen FAR cybersecurity requirements that form the basis for CMMC Level 1 practices. Given the underlying FAR requirements for Level 1 CMMC organizations, FAR 52.204-21(b)(1) calls out the need for:
- Procedures; and
- Applying the requirements.
In practical terms, this means in order to comply with FAR 52.204-21, any organization going through a Level 1 CMMC assessment is reasonably-expected to have documented policies, standards and procedures that document how the FAR requirements are implemented. Without documented evidence of due care and due diligence, the contractor could be considered negligent and could be within scope for a False Claims Act (FCA) violation.
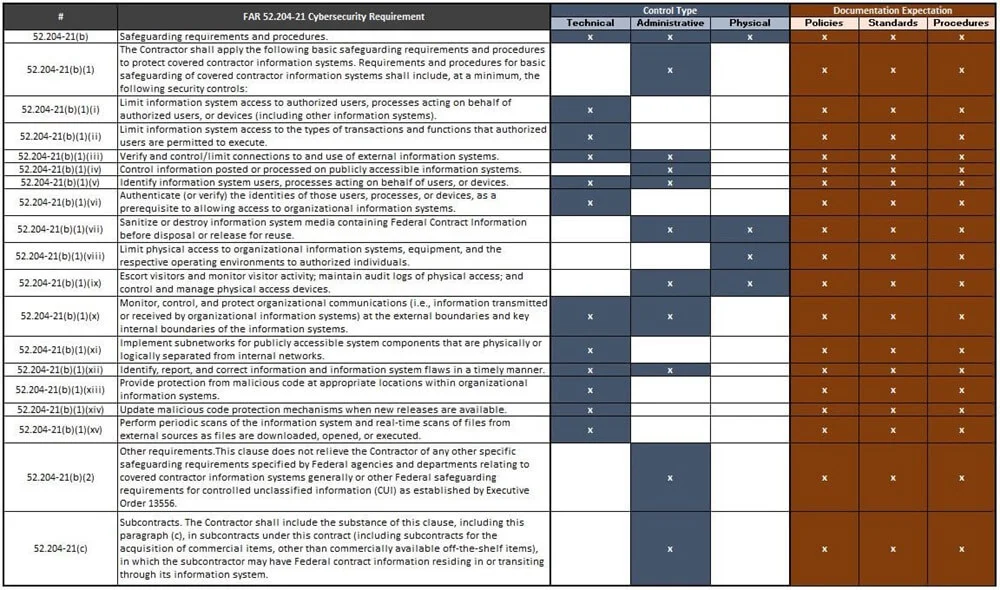
## **FAR vs DFARS - ISO 27002, NIST Cybersecurity Framework or NIST 800-53 Frameworks - What Is The Best Approach?**
The bottom line is that utilizing the NIST Cybersecurity Framework or ISO 27001/27002 as a security framework does not directly meet the requirements of NIST 800-171. In fact, NIST 800-171 (Appendix D) maps out how the CUI security requirements of NIST 800-171 relate to NIST 800-53 and ISO 27001/27002 security controls. This includes callouts where the ISO 27001/27002 framework does not fully satisfy the requirements of NIST 800-171.
Essentially, this means that only the NIST 800-53 framework is going to meet FAR requirements of NIST 800171 - ISO 27002 and the NIST Cybersecurity Framework are going to be insufficient in coverage.

## Cost of Non-Compliance With FAR 52.204-21
**What can possibly go wrong with non-compliance in a contract with the U.S. Government?**
- **Contract Termination**. It is reasonably expected that the U.S. Government will terminate contracts with prime contractors over non-compliance with FAR requirements since it is a failure to uphold contract requirements. Subcontractor non-compliance will cause a prime contractor to be non-compliant, as a whole.
- **Criminal Fraud**. If a company states it is compliant when it knowingly is not compliant, that is misrepresentation of material facts. This is a criminal act that is defined as any act intended to deceive through a false representation of some fact, resulting in the legal detriment of the person who relies upon the false information.
- **Breach of Contract Lawsuits**. Both prime contractors and subcontractors could be exposed legally. A tort is a civil breach committed against another in which the injured party can sue for damages. The likely scenario for a FAR-related tort would be around negligence on behalf of the accused party by not maintaining a specific code of conduct (e.g., FAR cybersecurity controls).
As you can see from those examples, the cost of non-compliance is quite significant. As always, seek competent legal counsel for any pertinent questions on your specific compliance obligations.
## Affordable, Editable FAR 52.204-21 Compliance Documentation
ComplianceForge is a niche cybersecurity company that specializes in compliance-related documentation. We are a leading provider for FAR 52.204-21 compliance documentation, where we serve clients from small businesses through the Fortune 500 with our FAR 52.204-21 compliance products.
**What Problem Does ComplianceForge Solve?**
- Lack of In House Security Experience \- Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. Tasking your security analysts and engineers to write comprehensive FAR 52.204-21 compliance documentation means you are actively taking them away from protecting and defending your network, which is not a wise use of their time. ComplianceForge offers FAR 52.204-21 documentation solutions that can save your organization significant time and money!
- Compliance Requirements \- The reality of non-compliance with FAR 52.204-21 requirements means lost business and potential fines. In addition to losing contracts, charges of fraud may be leveled on companies that claim to be compliant with FAR 52.204-21 but cannot provide evidence. Our documentation can help you become and stay compliant with FAR 52.204-21 where you have documented evidence to prove it!
- Audit Failures \- Security documentation does not age gracefully like a fine wine. Outdated documentation leads to gaps that expose organizations to audit failures and system compromises. Our documentation provides mapping to NIST 800-53 and other leading security frameworks to show you exactly what is required to both stay secure and compliant. Being editable documentation, you are able to easily maintain it as your needs or technologies change.
**How Does ComplianceForge Solve It?**
- Clear Documentation \- In an audit, clear and concise documentation is half the battle. ComplianceForge provides comprehensive documentation that can prove your FAR 52.204-21 compliant security program exists. This equates to a time saving of hundreds of hours and tens of thousands of dollars in staff and consultant expenses!
- Time Savings \- Time is money! Our cybersecurity documentation addresses DFARS and FAR requirements and this can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
- Alignment With Leading Practices \- We did the heavy lifting. Our documentation is mapped to the NIST 800-53, as well as other leading security frameworks!

## Comprehensive FAR 52.204-21 Compliance Documentation
ComplianceForge has FAR 52.204-21 compliance documentation that applies if you are a prime or sub-contractor. These current, fifteen (15) basic cybersecurity requirements for FAR include:
- Limit access to authorized users.
- Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Verify controls on connections to external information systems.
- Impose controls on information that is posted or processed on publicly accessible information systems.
- Identify information system users and processes acting on behalf of users or devices.
- Authenticate or verify the identities of users, processes, and devices before allowing access to an information system.
- Sanitize or destroy information system media containing Federal contract information before disposal, release, or reuse.
- Limit physical access to information systems, equipment, and operating environments to authorized individuals.
- Escort visitors and monitor visitor activity, maintain audit logs of physical access, control and manage physical access devices.
- Monitor, control, and protect organizational communications at external boundaries and key internal boundaries of information systems.
- Implement sub networks for publicly accessible system components that are physically or logically separated from internal networks.
- Identify, report, and correct information and information system flaws in a timely manner.
- Provide protection from malicious code at appropriate locations within organizational information systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the information system and real-time scans of files from scans of files from external sources as files are downloaded, opened, or executed.
## Is Your Organization "Audit Ready" for FAR 52.204-21?
When you "peel back the onion" and prepare for a FAR 52.204-21 audit, there is a need to address "the how" for certain topics. While policies and standards are designed to describe WHY something is required and WHAT needs to be done, many companies fail to create documentation to address HOW it gets done. We did the heavy lifting and created several program-level documents to address this need and they integrate with either the Cybersecurity & Data Protection Program (CDPP) or Digital Security Program (DSP) to provide your organization with a set of robust documentation to prepare for your audit.
One thing to keep in mind is that while the current requirements are quite basic, there is a a pending change with FAR to compel all US government contractors, not just DoD contractors, to comply with **NIST 800-171**.
## Address FAR 52.204-21 Compliance With The NIST-based Cybersecurity & Data Protection Program (CDPP)
The NIST version of the **[Cybersecurity & Data Protection Program (CDPP)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/ "NIST 800-53 rev5 Cybersecurity Policies & Standards for FAR 52.204-21 compliance")** is a comprehensive set of IT security policies and standards that is based on the **National Institute of Standards & Technology (NIST) 800-53 rev5** framework and it can help your organization become compliant with FAR 52.204-21 requirements
This NIST-based CDPP is a comprehensive, customizable, easily-implemented Microsoft Word document that contains the NIST 800-53 rev5-based policies, control objectives, standards and guidelines that your company needs to establish a robust cybersecurity program. Being a Microsoft Word document, you have the ability to make edits to suit your company's specific needs.
NIST 800-53 is the de facto standard for cybersecurity requirements that is issued by the US government. Therefore, government agencies, defense contractors, telecom service providers, health care providers, financial companies or any organizations that contract with the government tend to adopt NIST-based best practices over all other frameworks, based on regulatory requirements.
## Browse Our Products
- [](https://complianceforge.com/product/comprehensive-digital-security-program/)
#### [Digital Security Program (DSP)](https://complianceforge.com/product/comprehensive-digital-security-program/)
Secure Controls Framework (SCF)
Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics.
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different...
$10,400.00 - $15,200.00
[Choose Options](https://complianceforge.com/product/comprehensive-digital-security-program/)
- [](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST CSF 2.0](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) Policy Template - Editable Policies & Standards
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-csf-policies-standards-cdpp/)
- [](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
#### [Policy & Standards Template - ISO 27001 / 27002](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
ComplianceForge ISO 27001 & 27002 Compliance Documentation Templates
ISO 27001 & 27002 Policy Template UPDATED FOR ISO 27001:2022 & 27002:2022
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/iso-27001-27002-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (moderate)](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST 800-53 Rev5 Policy Template LOW & MODERATE BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video...
$1,980.00 - $6,780.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-moderate-policies-standards-cdpp/)
- [](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
#### [Policy & Standards Template - NIST 800-53 R5 (high)](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
ComplianceForge NIST 800-53 Compliance Documentation Templates
NIST SP 800-53 Rev5 Policy Template LOW, MODERATE & HIGH BASELINE
Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough...
$2,970.00 - $7,770.00
[Choose Options](https://complianceforge.com/product/nist-800-53-r5-high-policies-standards-cdpp/)
- [](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
#### [Policies & Procedures Bundle - NIST CSF 2.0](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
ComplianceForge NIST Cybersecurity Framework Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #1A - NIST CSF 2.0 (20% discount)
This is a bundle that includes the following two (2) ComplianceForge products that are focused on operationalizing the NIST Cybersecurity...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/policies-procedures-bundle-nist-csf)
- [](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (Moderate)](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4a (40% discount)
Is your organization looking for NIST cybersecurity documentation? This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on...
$40,670.00
$24,402.00 - $29,202.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4a-nist-80053)
- [](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
#### [Compliance Templates - NIST 800-53 R5 (High)](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
ComplianceForge NIST 800-53 Compliance Documentation Templates
Cybersecurity & Data Protection Program (CDPP) Bundle #4b - Low, Moderate & High Baselines (40% discount)
This is a bundle that includes the following fourteen (14) ComplianceForge products that are focused on operationalizing NIST SP...
$42,955.00
$25,773.00 - $30,573.00
[Choose Options](https://complianceforge.com/bundle/cdpp-bundle-4b-nist-80053)
- [](https://complianceforge.com/bundle/cmmc-bundle-1)
#### [CMMC Bundle 1: Level 1 (CMMC 2.0 L1 & FAR 52.204-21)](https://complianceforge.com/bundle/cmmc-bundle-1)
ComplianceForge - NIST 800-171 & CMMC
CMMC 2.0 Level 1 - CMMC 2.0 L1 & FAR 52.204-21 Policies, Standards & Procedures - CMMC Level 1 (20% discount)
This bundle is as streamlined as we've been able to make it for those needing to demonstrate compliance with...
$6,680.00
$5,344.00 - $10,144.00
[Choose Options](https://complianceforge.com/bundle/cmmc-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-1)
#### [DSP Bundle 1: Policies, Standards, Procedures & Controls](https://complianceforge.com/bundle/dsp-bundle-1)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #1 - SCF-Aligned Policies, Standards & Procedures (25% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following two (2) ComplianceForge...
$16,800.00
$12,600.00 - $17,400.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-1)
- [](https://complianceforge.com/bundle/dsp-bundle-2)
#### [DSP Bundle 2: Enhanced Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-2)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #2 - ENHANCED DIGITAL SECURITY (35% Discount)
Is your organization looking ofr enterprise cybersecurity documentation? This is a bundle that includes the following seven (7) ComplianceForge products that are...
$29,485.00
$19,165.00 - $23,965.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-2)
- [](https://complianceforge.com/bundle/dsp-bundle-3)
#### [DSP Bundle 3: Robust Digital Security Documentation](https://complianceforge.com/bundle/dsp-bundle-3)
Secure Controls Framework (SCF)
Digital Security Plan (DSP) Bundle #3 - ROBUST DIGITAL SECURITY (45% Discount)
Is your organization looking for enterprise cybersecurity documentation? This is a bundle that includes the following thirteen (13) ComplianceForge products that are...
$49,840.00
$27,412.00 - $32,212.00
[Choose Options](https://complianceforge.com/bundle/dsp-bundle-3)
- [**C-SCRM & NIST 800-161 R1** \\
For many cybersecurity practitioners, even those well versed in NIST 800-171 and Cybersecurity Matur...](https://complianceforge.com/blog/cscrm-nist-800161-r1/)
- [**Secure Software Development Attestation** \\
Can you tell the difference in these secure software development attestation forms? There isn't one...](https://complianceforge.com/blog/secure-software-development-attestation/)
- [**NIST 800-171 R3 ODPs** \\
ComplianceForge released NIST 800-171 R3 documentation updated to address DoD-provided Organization-...](https://complianceforge.com/blog/nist-800171-r3-odps/)
- [**SCF Training & Certifications** \\
ComplianceForge is a Licensed Content Provider (LCP) for the Secure Controls Framework (SC...](https://complianceforge.com/blog/scf-training-certifications/)
* * *
Request Quote
We use cookies (and other similar technologies) to collect data to improve your shopping experience.By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://www.complianceforge.com/privacy/).
SettingsReject allAccept All Cookies
Error 404 (Not Found)!!1
**404.** That’s an error.
The requested URL was not found on this server. That’s all we know.
far clause 52204 21, far 52204 21, 52204 21, far 52204 2
## Cybersecurity Risk Assessment
[Skip to main content](https://complianceforge.com/product/cybersecurity-risk-assessment-template/#main-content)
[](https://cdn11.bigcommerce.com/s-g93hfm7/images/stencil/1280x1280/products/86/1521/complianceforge-cybersecurity-risk-assessment-cra-template__75272.1740599321.jpg?c=2)
No reviews yet
$1,925.00
(You save)
# Cybersecurity Risk Assessment (CRA) Template
SKU:P06-CRA-NOUPC:692878856850Availability:Email Delivery Within 1-2 Business Days
Documentation Customization:
(Required)
Choose OptionsNone - No customization needed5 hours (10% discount - $270/hr)10 hours (15% discount - $255/hr)20 hours (20% discount - $240/hr)
Formal Company Name (e.g., ACME Business Solutions, Inc.):
(Required)
Common Company Name (e.g., ACME):
(Required)
Logo Upload (optional):
Optional
Maximum file size is
**15000KB**,
file types are **bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff**
Single Entity License:
(Required)
Non-Transferable, Single-Entity License (licensed for use by a single legal entity, as defined in ComplianceForge's Terms & Conditions))
Current Stock:
Adding to cart… The item has been added
Add To Quote
- [Email](mailto:?subject=Cybersecurity%20Risk%20Assessment%20Template%20for%20Compliance&body=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-risk-assessment-template%2F "Email")
- Print
- [Linkedin](https://www.linkedin.com/shareArticle?mini=true&url=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-risk-assessment-template%2F&title=Cybersecurity%20Risk%20Assessment%20Template%20for%20Compliance&summary=Cybersecurity%20Risk%20Assessment%20Template%20for%20Compliance&source=https%3A%2F%2Fcomplianceforge.com%2Fproduct%2Fcybersecurity-risk-assessment-template%2F "Linkedin")

[](https://complianceforge.com/product/cybersecurity-risk-assessment-template/#cra-example)
## Cybersecurity Risk Assessment Template
## Product Walkthrough Video
When you click the image or the link below, it will direct you to a different page on our website that contains a short product walkthrough video designed to give a brief overview about what the CRA is to help answer common questions we receive.
[](https://complianceforge.com/what-is-the-cybersecurity-risk-assessment-cra/ "Watch Video")
[View Product Video](https://complianceforge.com/what-is-the-cybersecurity-risk-assessment-cra/)
## What Is The Cybersecurity Risk Assessment (CRA) Template?
The CRA serves as a key element in your organization's cybersecurity risk program. It can stand alone or be paired with other specialized products we offer.
Most companies have requirements to perform risk assessments, but they lack the knowledge and experience to undertake such assessments. That means businesses are faced to either outsource the work to expensive consultants or they ignore the requirement and hope they do not get in trouble for being non-compliant with a compliance requirement. In either situation, it is not a good place to be. The good news is that we created an affordable solution for businesses to conduct their own information security risk assessments.
If you can use Microsoft Word and Excel, then you can perform a risk assessment by simply following the instructions and editing the template to suit your specific requirements. While this is a template, we did the hard work of creating the formatting, bringing together the correct scope of information that needs to be assessed, and we built the calculations to make your work as simple as selecting from a few drop-down answers!
The technical controls selected for the CRA are the cybersecurity controls from the Secure Controls Framework (SCF), so the requirements are based on leading practices for risk management.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The RMP is an editable Microsoft Word document that providers program-level guidance to directly supports your organization's policies and standards for managing cybersecurity risk. Unfortunately, most companies lack a coherent approach to managing risks across the enterprise:
- The CRA is an editable risk assessment template that you use to create risk assessments.
- It contains both an editable Microsoft Word document and Microsoft Excel spreadsheet that allows for professional-quality risk assessments.
- Included is an example risk assessment that can be used as a guide.
- The CRA supports the [**Risk Management Program (RMP)**](https://complianceforge.com/product/cybersecurity-risk-management-program-rmp/ "Risk Management Program") product in answering the “how?” questions for how your company manages risk.
- You do not need the RMP to generate risk assessments with the CRA.
- The RMP just tells the rest of the story for how risk is managed at your organization.
- Where the RMP lays the groundwork for how risk is to be managed, the CRA is a template that allows you to product the end product of risk management, which is a professional-quality risk assessment report.
## What Problems Does The CRA Solve?
- Lack of In House Security Experience - Many organizations lack internal staff who can come up with quality risk assessments. The CRA is an affordable solution for managers or IT staff to conduct quality risk assessments.
- Compliance Requirements - Most organizations run into trouble in audits when asked to provide evidence of risk assessments being performed. The CRA provides a template to conduct repeatable risk assessments in a very professional format. The CRA provides this evidence!
- Audit Failures - It is very common for clients and partners to request evidence of a risk assessments. Clients and partners often ask to see evidence of risk assessments so they can also understand your risks. The CRA provides this evidence!
- Vendor Requirements - Requirements such as PCI DSS, HIPAA, MA 201 CMR 17.00 and NIST 800-171 establish a mandate to conduct risk assessments. The CRA addresses these compliance requirements!
## How Does The CRA Solve These Problems?
- Clear Documentation - The CRA provides the comprehensive documentation to prove that your risk program exists.
- Time Savings - You can start assessing risk as soon as you receive the CRA. Orders are generally delivered the same business day!
- Alignment With Leading Practices - The CRA covers natural and man-made risks, as well as risk associated with the absence or state of cybersecurity controls (as defined by NIST 800-171). This creates a quality scope for a cybersecurity risk assessment.
Need to perform an information security risk assessment? This is a pretty common requirement that can seem like an insurmountable obstacle, since most people are not trained on how to perform a risk assessment or they lack a simple tool that is comprehensive enough to meet their needs. This is where our **Cybersecurity Risk Assessment Template** comes into play - we developed a simple Microsoft Excel template to walk you through calculating risk and a corresponding Word template to report on that risk. If you can use Word and Excel, you can successfully use our templates to perform a risk assessment. We even give you a completely filled-out example risk assessment, so that you can use that as a reference.
## Product Example - Cybersecurity Risk Assessment (CRA) Template
The CRA provides you a format to produce high-quality risk assessment reports, based on the Risk Management Program's (RMP) structure of managing risk. The CRA provides a high-quality template to actually perform the risk assessments that are called for by policies, standards and procedures. This allows your organization to have a risk assessment template that is repeatable and looks professional.
**View Product Examples**
| | | |
| --- | --- | --- |
| [](https://complianceforge.com/content/pdf/example-cra-risk-assessment-template.pdf "example cybersecurity risk assessment report") | | [](https://complianceforge.com/content/pdf/example-cra-risk-assessment-calculation-worksheets.pdf "cybersecurity risk assessment worksheet example") |
## Cost Savings Estimate - Cybersecurity Risk Assessment (CRA) Template
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the CRA from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 100 internal staff work hours, which equates to a cost of approximately **$10,000** in staff-related expenses. This is about 2-3 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 70 consultant work hours, which equates to a cost of approximately **$22,750**. This is about 1-2 months of development time for a contractor to provide you with the deliverable.
- The CRA is approximately 8% of the cost for a consultant or 19% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CRA the same day you place your order.
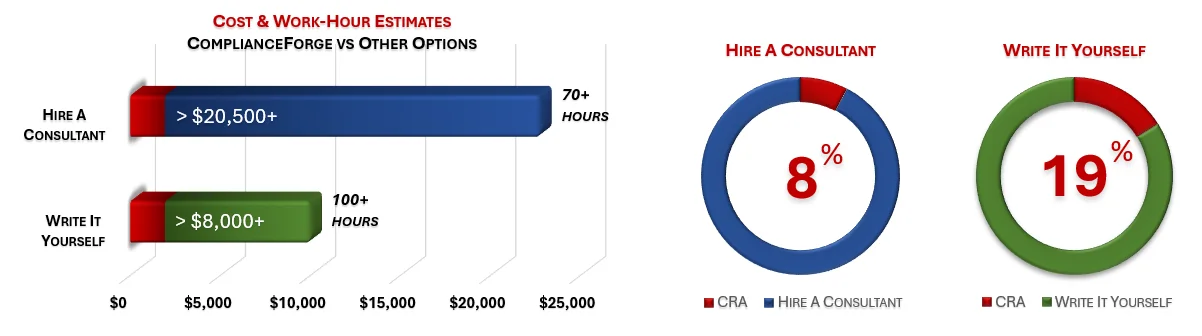
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

## Common Scenarios That Require Information Security Risk Assessments
If you fall in scope for any of these compliance requirements, you have to perform risk assessments and you need this template:
- **Payment Card Industry Data Security Standard (PCI DSS)** \- Section # 12.3.1 (PCI DSS v4) requires companies to perform a formal risk assessment!
- **Massachusetts MA 201 CMR 17.00** \- Section # 17.03(2)(b) requires companies to "identify & assess" reasonably-forseeable internal and external risks!
- **Oregon Identity Theft Protection Act** \- Section 646A.622(2)(d)(B)(ii) requires companies to assess risks in information processing, transmission & storage!
- **Health Insurance Portability and Accountability Act (HIPAA)** \- Security Rule (Section 45 C.F.R. §§ 164.302 – 318) requires companies to conduct an accurate & thorough assessment of potential risks!
- **Gramm-Leach-Bliley Act** \- Safeguard Rule requires company to identify and assess risks to customer information!
- **NIST 800-171** \- Protecting CUI in Nonfederal Information Systems and Organizations - Section 3.11 requires risks to be periodically assessed!
Given that we designed this risk assessment template based on industry-recognized best practices, you can use our template to address those information security risk assessment requirements. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks - NIST 800‐30 (Risk Management Guide for Information Technology Systems), NIST 800‐37 (Guide for Applying the Risk Management Framework to Federal Information Systems) & NIST 800‐39 (Managing Information Security Risk).

## Risk Assessment Template Contents
Our latest version of the **Cybersecurity Risk Assessment Template** includes:
- Section for assessing both natural & man-made risks.
- Section for assessing reasonably-expected cybersecurity controls. The CRA uses the Secure Controls Framework (SCF) control set, so as a metaframework it is applicable to over 100 cybersecurity laws, regulations and frameworks, including NIST 800-53, NIST 800-171 and ISO 27001/27002!
- Section for assessing Capability Maturity Model (CMM) - built into cybersecurity control assessment portion of the risk assessment.
- Blank templates in Microsoft Word & Excel formats.
- Fully filled-out example of the templates that you can edit in Microsoft Word & Excel
## Graph Depicting Natural & Man-Made Risks
The Excel-based worksheet comes with graphs showing before & after risk levels. These are just embedded into the report to provide a good visual. The calculations from the worksheets make it easy to show raw risk scores and also weighted scores, which take into consideration the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk.
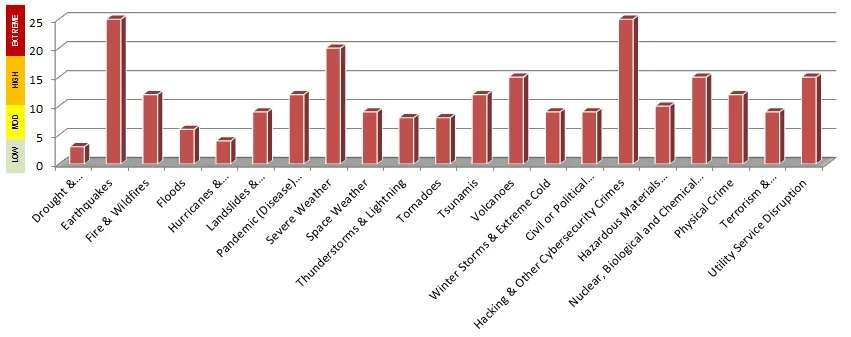
## Risk Assessment Matrix
The calculations show raw risk scores and also take into account weighting factors, such as the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk. The CRA utilizes a 6x6 risk assessment matrix. The CRA is able to show both the raw risk score, as well as the final score when compensating controls are taken into consideration.
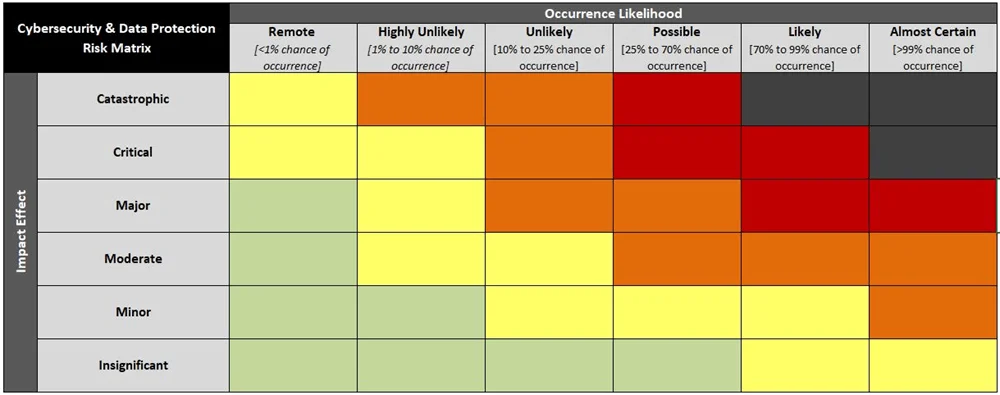
## Optional Professional Services (Add On)
ComplianceForge offers optional professional services to customize purchased documentation. Professional services are not required to customize ComplianceForge documentation. However, some clients want our subject matter expertise to help customize their documentation to meet their specific business needs. If you have any questions about our professional services, please contact us at: [www.complianceforge.com/contact-us/](https://complianceforge.com/contact-us/ "Contact Us").
We offer our professional services in bundles of: five (5), ten (10) & twenty (20) hours.
Purchased professional service hours will expire after 120 days (4 months) from the time of purchase before they expire.